Overview CSSE 490 Computer Security Mark Ardis RoseHulman














- Slides: 18

Overview CSSE 490 Computer Security Mark Ardis, Rose-Hulman Institute March 8, 2004 1

Acknowledgements Many of these slides came from Matt Bishop, author of Computer Security: Art and Science 2

Web 1: Getting Started (1/3) n n n Due Friday, March 12 Subscribe to rhit. csse. security Publishing n n Reply to the article entitled "My Home Town" Include a website describing your home town. 3

Web 1: Getting Started (2/3) n Reviewing n n Read some of the postings by your fellow students and follow the links to the websites. Review at least 3 of those websites n n n Assign a score for each of the key attributes Give your justification for those scores Reply to the original posting about that site with your review 4

Web 1: Getting Started (3/3) n Review Scores (0 -5 for each, where 0 is worst and 5 is best) n n n Accuracy Completeness Up-to-date Ease of Use Links 5

Overview of Course Website http: //www. rose-hulman. edu/class/csse 490/csse 490 -security/index. html 6

Chapter 1: Introduction n n n Components of computer security Threats Policies and mechanisms The role of trust Assurance Operational Issues Human Issues 7

Basic Components n Confidentiality n n Integrity n n n Keeping data and resources hidden Data integrity (integrity) Origin integrity (authentication) Availability n Enabling access to data and resources 8

Classes of Threats n Disclosure - unauthorized access n n Deception - acceptance of false data n n Modification, spoofing, repudiation of origin, denial of receipt Disruption - interruption of correct operation n n Snooping Modification Usurpation - unauthorized control n Modification, spoofing, delay, denial of service 9

Policies and Mechanisms n Policy says what is, and is not, allowed n n n This defines “security” for the site/system/etc. Mechanisms enforce policies Composition of policies n If policies conflict, discrepancies may create security vulnerabilities 10

Goals of Security n Prevention n n Detection n n Prevent attackers from violating security policy Detect attackers’ violation of security policy Recovery n n Stop attack, assess and repair damage Continue to function correctly even if attack succeeds 11

Trust and Assumptions n n Underlie all aspects of security Policies n n n Unambiguously partition system states Correctly capture security requirements Mechanisms n n Assumed to enforce policy Support mechanisms work correctly 12

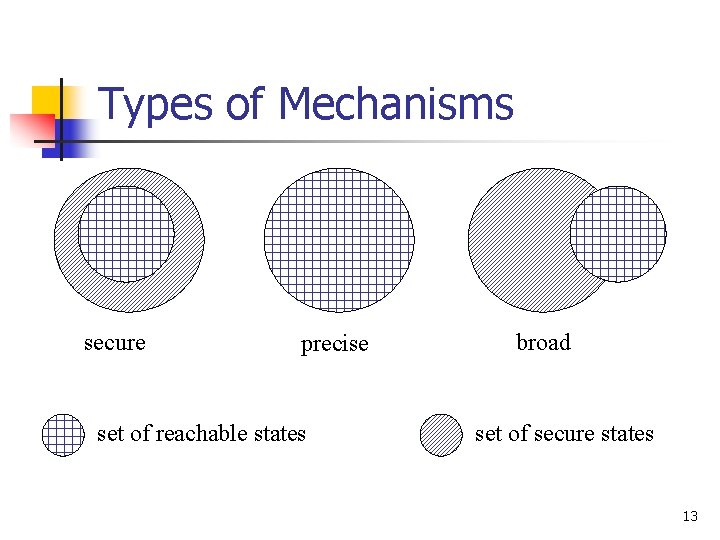
Types of Mechanisms secure precise set of reachable states broad set of secure states 13

Assurance n Specification n Design n n Requirements analysis Statement of desired functionality How system will meet specification Implementation n Programs/systems that carry out design 14

Operational Issues n Cost-Benefit Analysis n n Risk Analysis n n n Is it cheaper to prevent or recover? Should we protect something? How much should we protect this thing? Laws and Customs n n Are desired security measures illegal? Will people do them? 15

Human Issues n Organizational Problems n n n Power and responsibility Financial benefits People problems n n Outsiders and insiders Social engineering 16

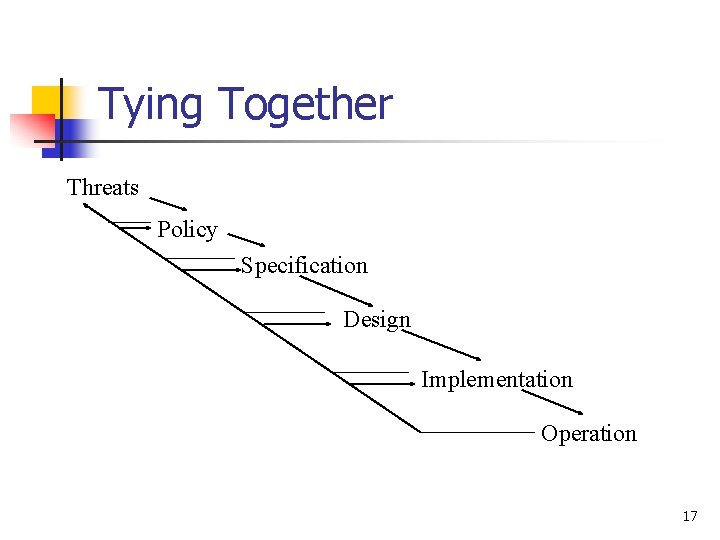
Tying Together Threats Policy Specification Design Implementation Operation 17

Key Points n Policy defines security, and mechanisms enforce security n n n Confidentiality Integrity Availability Trust and knowing assumptions Importance of assurance The human factor 18