Outline n n n Introduction of Mobile Ad


Outline n n n Introduction of Mobile Ad hoc Networks (MANET) Challenges and Attacks Solutions From Ad hoc Network to RFID Open problems 2
Introduction of wired and wireless networks (1) n Wired networks n n n Fixed network topology and routing infrastructure Enough network resources High reliability and low packets loss ratio Routing protocols update periodically such as Link. State (global) and Distance Vector (local) Wireless networks n Access Point n n n Limited bandwidth Median reliability and packets loss ratio Others the same with wired network 3
Introduction of wired and wireless networks (2) n Mobile Ad hoc network n n n Research in the 1970 s with DARPA PRNet and the SURAN projects Formed by the engagement of mobile nodes and without using a pre-existing infrastructure Routes between nodes may contain multiple hops Dynamic topology and limited resources Sensor network n n n A type of Ad hoc network A powerful node : clusterhead Other powerless nodes : sensors 4
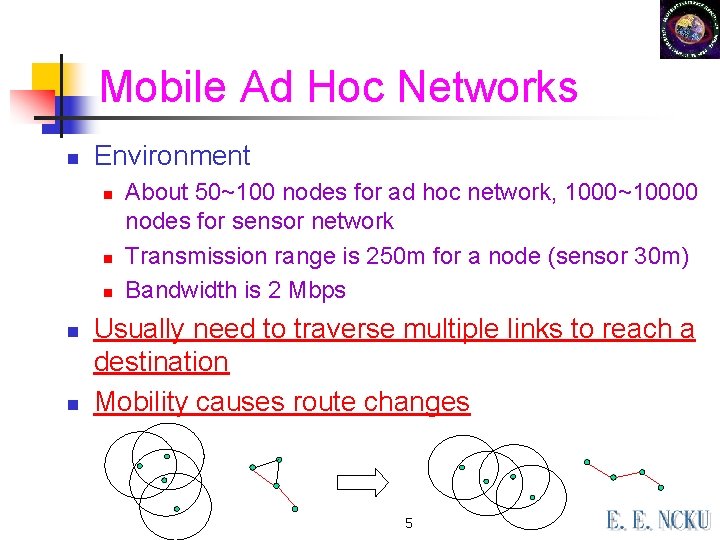
Mobile Ad Hoc Networks n Environment n n n About 50~100 nodes for ad hoc network, 1000~10000 nodes for sensor network Transmission range is 250 m for a node (sensor 30 m) Bandwidth is 2 Mbps Usually need to traverse multiple links to reach a destination Mobility causes route changes 5

Why need Ad Hoc Networks ? n n n Ease of deployment Speed of deployment Decreased dependence on infrastructure 6

Many Applications n Personal area networking n n Military environments n n soldiers, tanks, planes Civilian environments n n cell phone, laptop, ear phone, wrist watch taxi cab network, meeting rooms, sports stadiums, boats, small aircraft Emergency operations n search-and-rescue, policing and fire fighting 7

Microcosmic Variations n Fully Symmetric Environment n n all nodes have identical capabilities and responsibilities Differ Capabilities n n n transmission ranges and radios battery life at different nodes processing capacity speed of movement only some nodes may route packets some nodes may act as leaders of nearby 8 nodes (e. g. , clusterhead)
Cosmic Variations n Traffic characteristics may differ in different ad hoc networks n n bit rate reliability requirements unicast / multicast / geocast May co-exist (and co-operate) with an infrastructure-based network 9
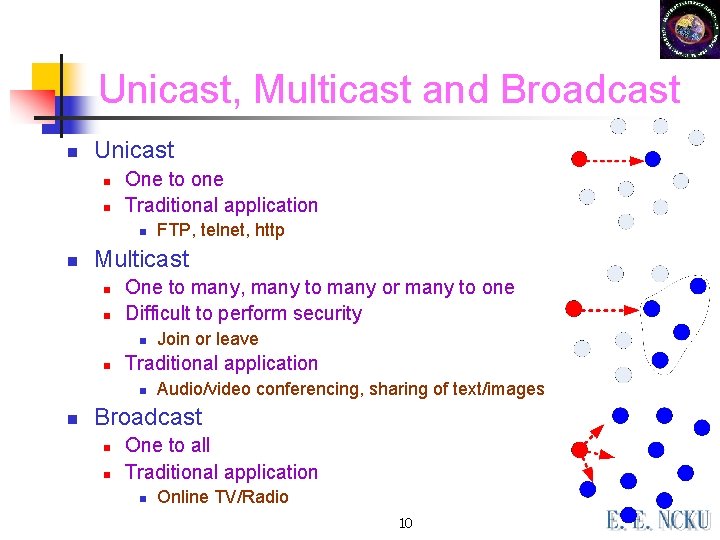
Unicast, Multicast and Broadcast n Unicast n n One to one Traditional application n n Multicast n n One to many, many to many or many to one Difficult to perform security n n Join or leave Traditional application n n FTP, telnet, http Audio/video conferencing, sharing of text/images Broadcast n n One to all Traditional application n Online TV/Radio 10
Ad hoc Routing Protocols n Why not use existing protocols ? n Node mobility n n n New protocol criteria must satisfy n n n link failure / repair repeatedly Rate of link failure / repair ∝ movement route stability despite mobility energy consumption Flooding based routing n Unicast, Multicast routing protocols 11
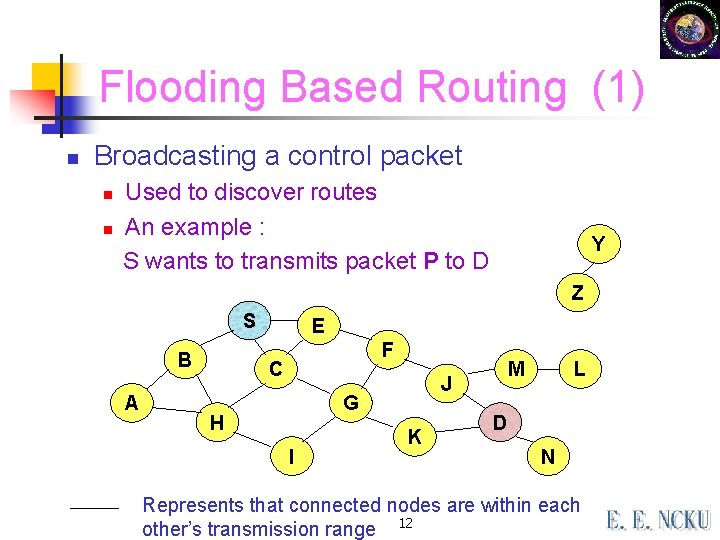
Flooding Based Routing (1) n Broadcasting a control packet n n Used to discover routes An example : S wants to transmits packet P to D Y Z S B A E F C G H I M J K L D N Represents that connected nodes are within each other’s transmission range 12
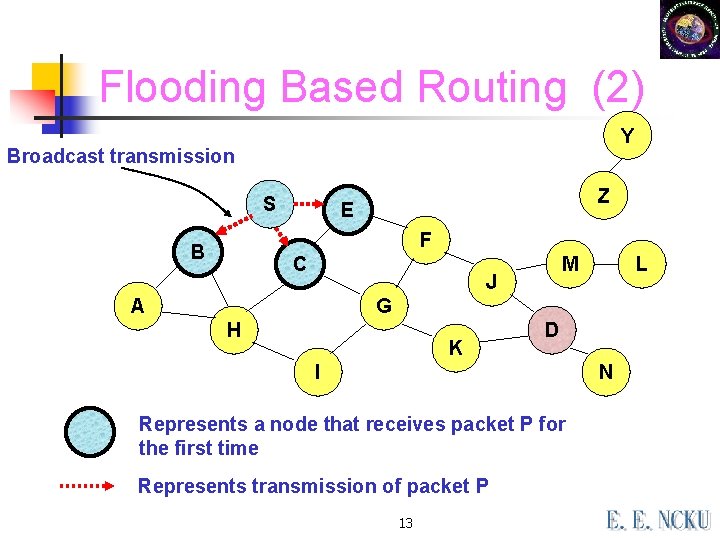
Flooding Based Routing (2) Y Broadcast transmission S Z E F B C M J A L G H K D I N Represents a node that receives packet P for the first time Represents transmission of packet P 13
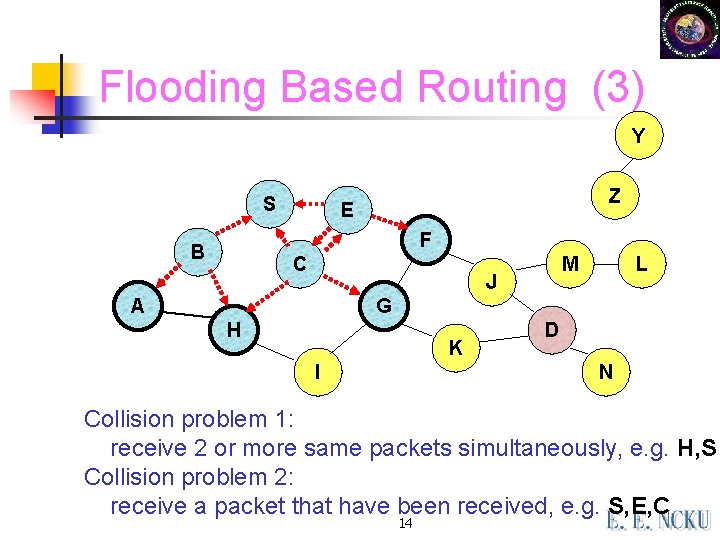
Flooding Based Routing (3) Y S Z E F B C M J A L G H K I D N Collision problem 1: receive 2 or more same packets simultaneously, e. g. H, S Collision problem 2: receive a packet that have been received, e. g. S, E, C 14
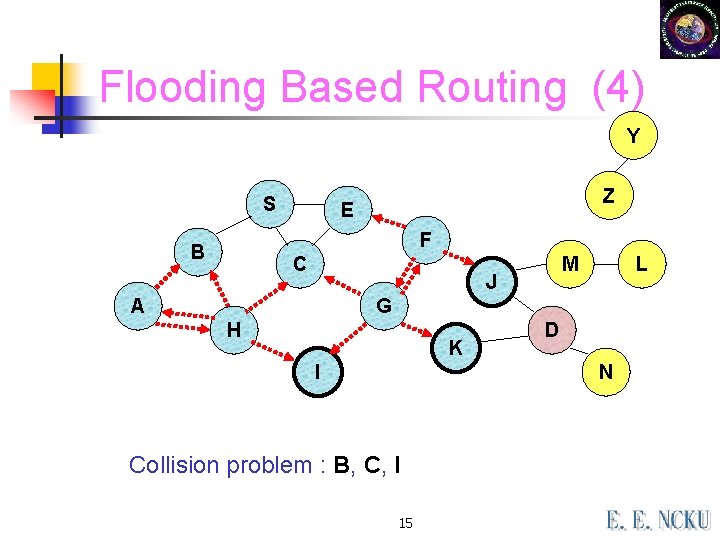
Flooding Based Routing (4) Y S Z E F B C M J A L G H K I D N Collision problem : B, C, I 15
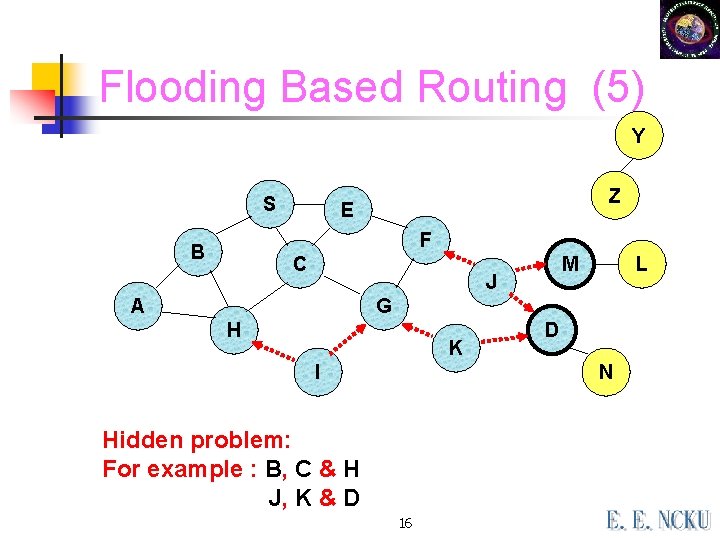
Flooding Based Routing (5) Y S Z E F B C M J A L G H K I D N Hidden problem: For example : B, C & H J, K & D 16
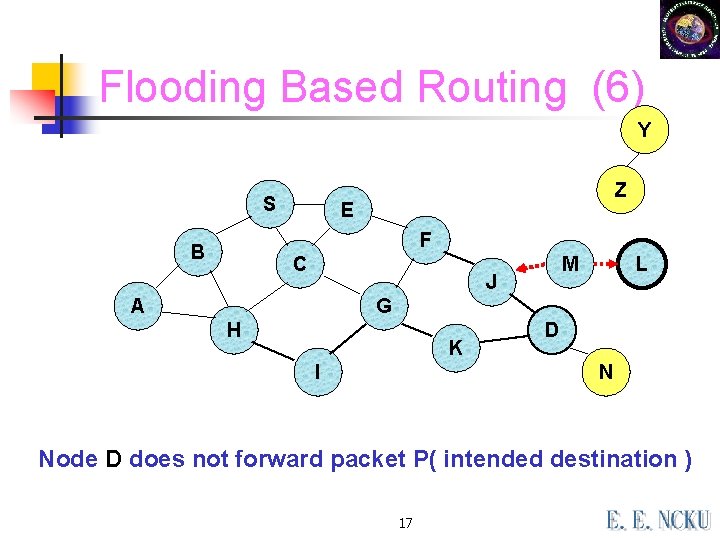
Flooding Based Routing (6) Y S Z E F B C M J A L G H K I D N Node D does not forward packet P( intended destination ) 17
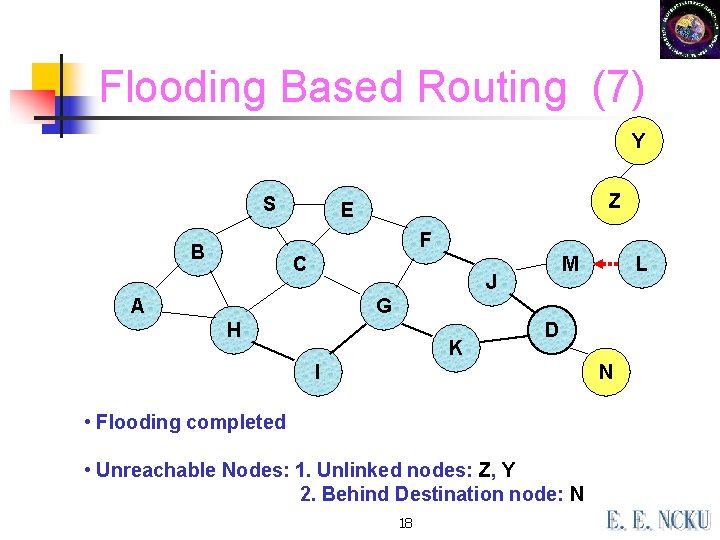
Flooding Based Routing (7) Y S Z E F B C M J A L G H K D I N • Flooding completed • Unreachable Nodes: 1. Unlinked nodes: Z, Y 2. Behind Destination node: N 18
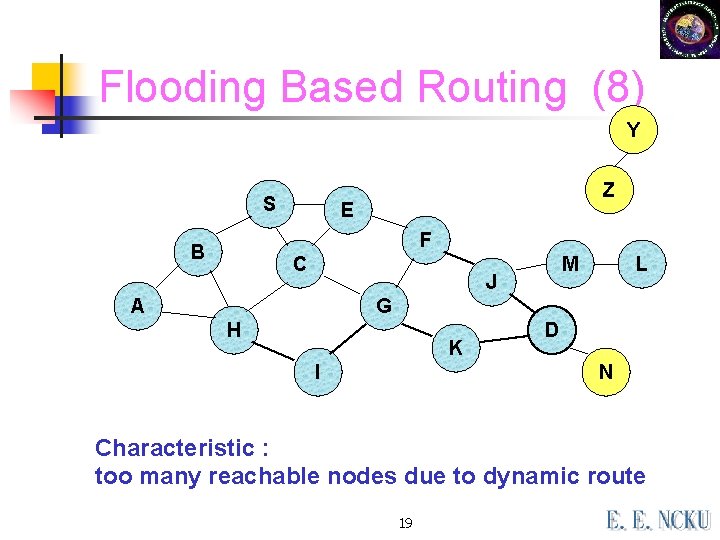
Flooding Based Routing (8) Y S Z E F B C M J A L G H K I D N Characteristic : too many reachable nodes due to dynamic route 19
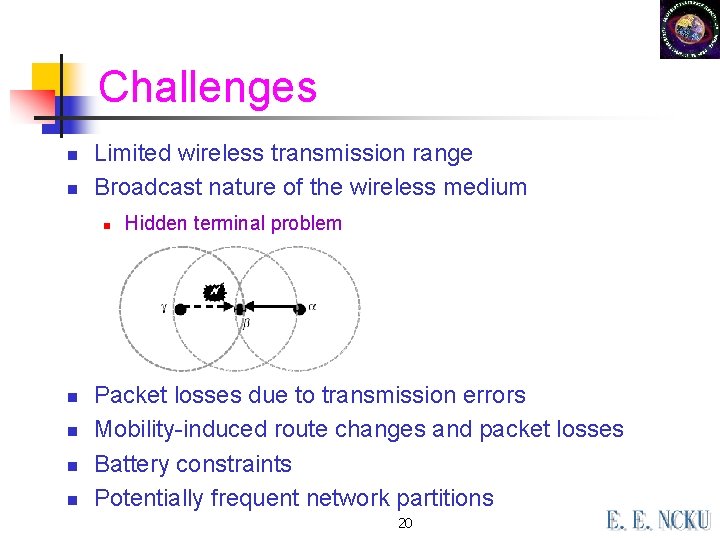
Challenges n n Limited wireless transmission range Broadcast nature of the wireless medium n n n Hidden terminal problem Packet losses due to transmission errors Mobility-induced route changes and packet losses Battery constraints Potentially frequent network partitions 20

Security Challenges Passive attack : does not disrupt the operation of the protocol, but tries to discover valuable information by listening to traffic n Eavesdropping n n Active attacks : injects arbitrary packets and tries to disrupt the operation of the protocol 1. Modification of routing information a. b. c. 2. 3. 4. 5. Redirection by changing the route sequence number Redirection with modified hop count Denial of Service (Do. S) attacks with modified source routes Impersonation of routing information Fabrication routing information Dropping routing information Denial of Service 21
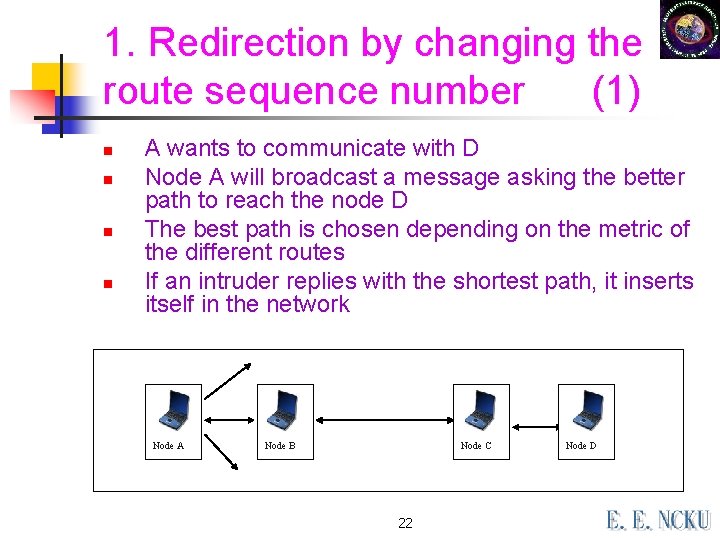
1. Redirection by changing the route sequence number (1) n n A wants to communicate with D Node A will broadcast a message asking the better path to reach the node D The best path is chosen depending on the metric of the different routes If an intruder replies with the shortest path, it inserts itself in the network Node A Node B Node C 22 Node D
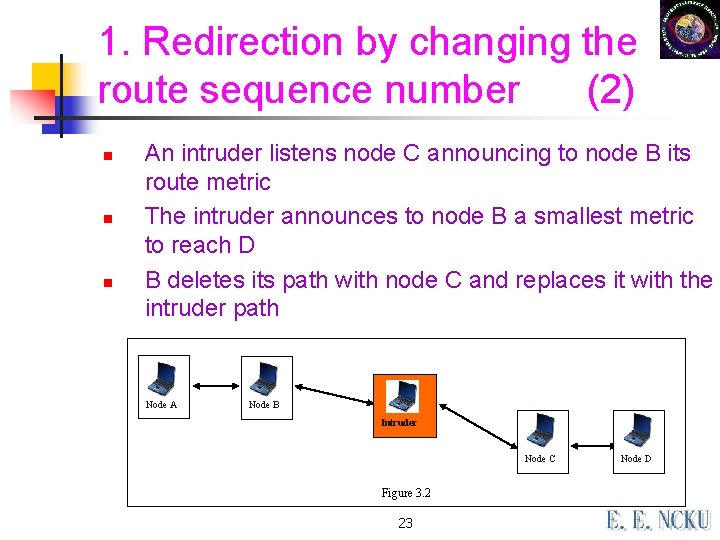
1. Redirection by changing the route sequence number (2) n n n An intruder listens node C announcing to node B its route metric The intruder announces to node B a smallest metric to reach D B deletes its path with node C and replaces it with the intruder path Node A Node B Intruder Node C Figure 3. 2 23 Node D
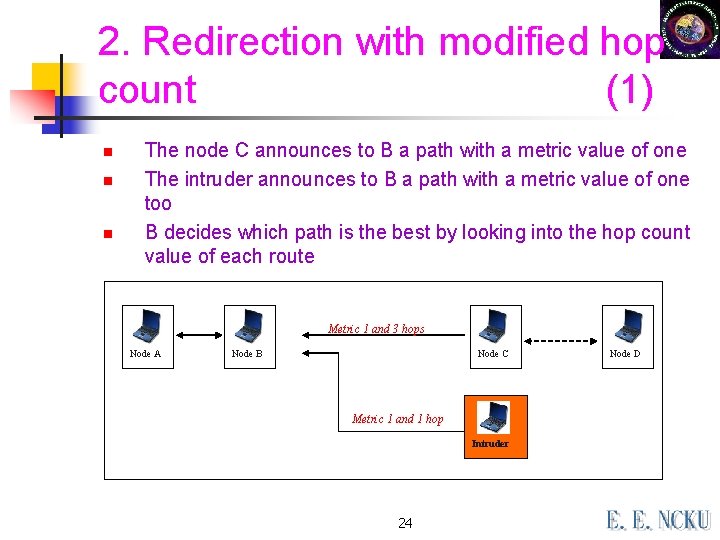
2. Redirection with modified hop count (1) n n n The node C announces to B a path with a metric value of one The intruder announces to B a path with a metric value of one too B decides which path is the best by looking into the hop count value of each route Metric 1 and 3 hops Node A Node B Node C Metric 1 and 1 hop Intruder 24 Node D
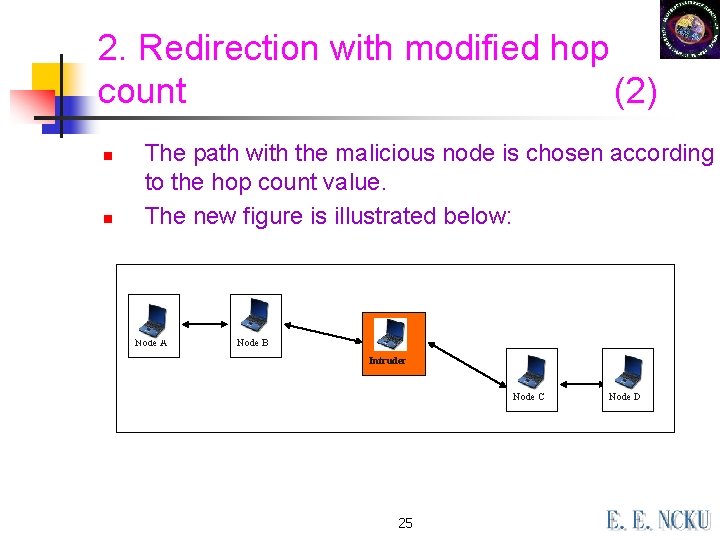
2. Redirection with modified hop count (2) n n The path with the malicious node is chosen according to the hop count value. The new figure is illustrated below: Node A Node B Intruder Node C 25 Node D

3. Denial of Service (Do. S) attacks with modified source routes (1) A malicious node is inserted in the network thanks to one of the previous technique. n n n The malicious node changes packet headers it receives The packets will not reach the destination The transmission is aborted The following figure illustrates Do. S attacks 26
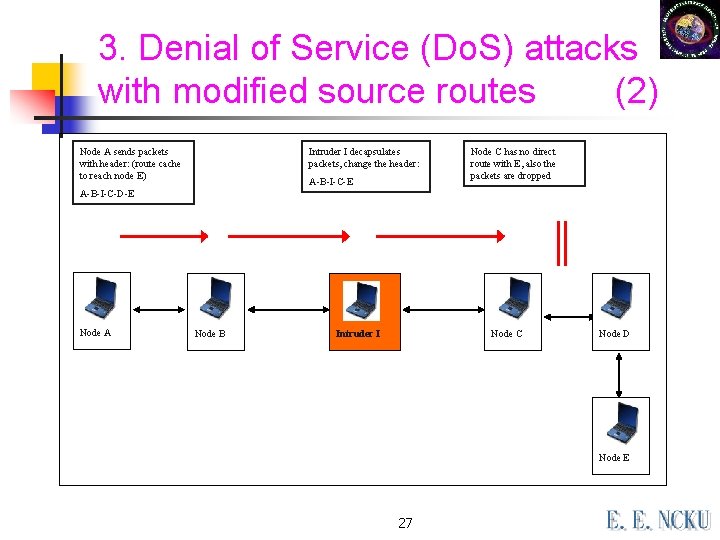
3. Denial of Service (Do. S) attacks with modified source routes (2) Node A sends packets with header: (route cache to reach node E) Intruder I decapsulates packets, change the header: A-B-I-C-E Node C has no direct route with E, also the packets are dropped A-B-I-C-D-E Node A Node B Intruder I Node C Node D Node E 27
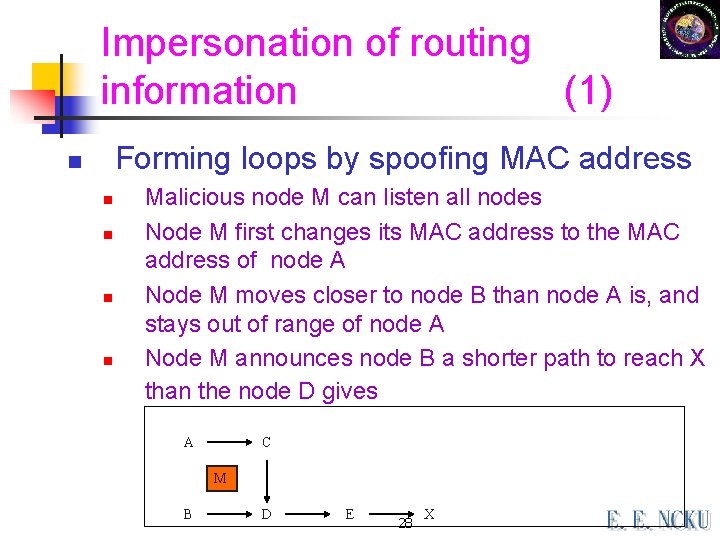
Impersonation of routing information (1) Forming loops by spoofing MAC address n n n Malicious node M can listen all nodes Node M first changes its MAC address to the MAC address of node A Node M moves closer to node B than node A is, and stays out of range of node A Node M announces node B a shorter path to reach X than the node D gives A C M B D E 28 X
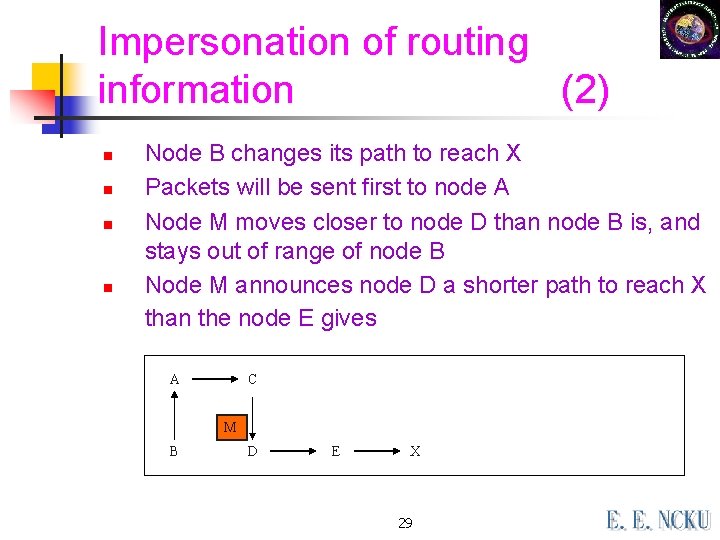
Impersonation of routing information (2) n n Node B changes its path to reach X Packets will be sent first to node A Node M moves closer to node D than node B is, and stays out of range of node B Node M announces node D a shorter path to reach X than the node E gives A C M B D E X 29
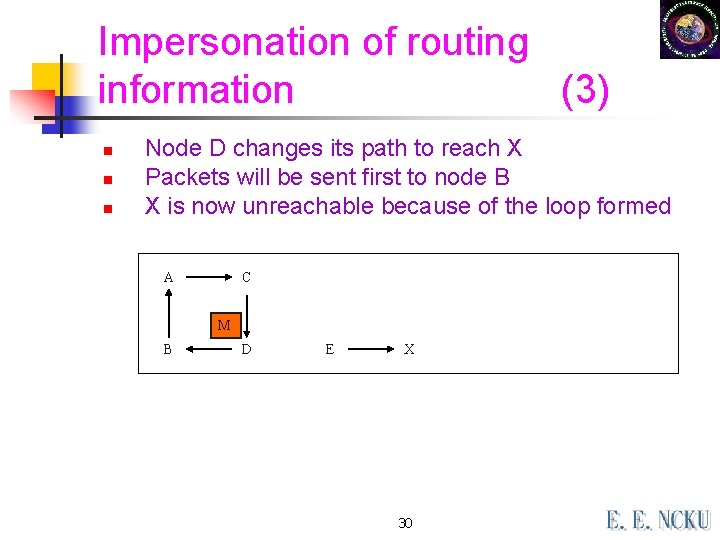
Impersonation of routing information (3) n n n Node D changes its path to reach X Packets will be sent first to node B X is now unreachable because of the loop formed A C M B D E X 30
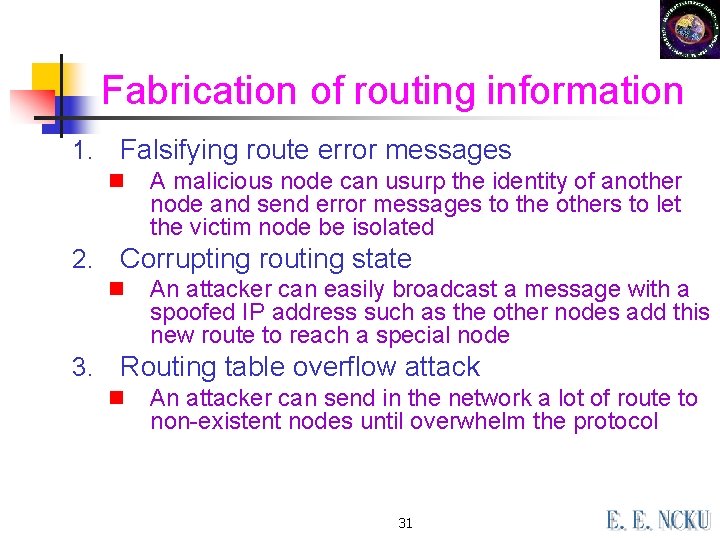
Fabrication of routing information 1. Falsifying route error messages n 2. Corrupting routing state n 3. A malicious node can usurp the identity of another node and send error messages to the others to let the victim node be isolated An attacker can easily broadcast a message with a spoofed IP address such as the other nodes add this new route to reach a special node Routing table overflow attack n An attacker can send in the network a lot of route to non-existent nodes until overwhelm the protocol 31
Fabrication of routing information (cont. ) 4. Replay attack n An attacker sends old advertisements to a node which always update its routing table with stale routes 5. Black hole or worm hole attack n Black hole attack p n An attacker advertises a zero metric route for all destinations and all the nodes around it will route packets towards it Worm hole attack p An attacker records packets at one location in the network, and tunnels them to another location 32

Dropping routing information n A malicious node just drops a routing packets that it received The influence on normal networking is less Unless the position of a malicious node is on single path 33

Security issues summary A lot of different threats for the ad-hoc routing protocols A new routing protocol should be created respecting the following rules n n Focus first on the topology discovery rather than the data forwarding Able to detect a malicious node and react in consequence 34

Solutions to problems in ad-hoc routing n n n Protocol enhancements Secure protocols Intrusion detection for Ad hoc network 35

Protocol enhancements Techniques to enhance security of existing routing protocols 3 Examples: n n n Security-Aware ad-hoc Routing, SAR Secure Routing Protocol, SRP The Selfish Node, TSN 36

Secure protocols Instead of extending current protocols, create new protocols with higher security requirements Two examples n n Authenticated Routing for Ad-hoc Networks, ARAN Secure Position Aided Ad hoc Routing, SPAAR 37
![Intrusion Detection [Zhang 00 Mobicom] n Detection of abnormal routing table updates n n Intrusion Detection [Zhang 00 Mobicom] n Detection of abnormal routing table updates n n](http://slidetodoc.com/presentation_image_h2/cff94d0d2dd1075d4a6c7f46ad5a1d7d/image-38.jpg)
Intrusion Detection [Zhang 00 Mobicom] n Detection of abnormal routing table updates n n n Similar abnormal behavior may be detected at other protocol layers n n n Uses “training” data to determine characteristics of normal routing table updates Efficacy of this approach is not evaluated, and is debatable For instance, at the Media Access Control (MAC) layer, normal behavior may be characterized for access patterns by various hosts Abnormal behavior may indicate intrusion Solutions proposed in [Zhang 00 Mobicom] are preliminary, not enough detail provided 38
![Preventing Traffic Analysis [Jiang 00 iaas, Jiang 00 tech] n n Even with encryption, Preventing Traffic Analysis [Jiang 00 iaas, Jiang 00 tech] n n Even with encryption,](http://slidetodoc.com/presentation_image_h2/cff94d0d2dd1075d4a6c7f46ad5a1d7d/image-39.jpg)
Preventing Traffic Analysis [Jiang 00 iaas, Jiang 00 tech] n n Even with encryption, an eavesdropper may be able to identify the traffic pattern in the network Traffic patterns can give away information about the mode of operation n n Attack versus retreat Traffic analysis can be prevented by presenting “constant” traffic pattern independent of the underlying operational mode n May need insertion of dummy traffic to achieve this 39

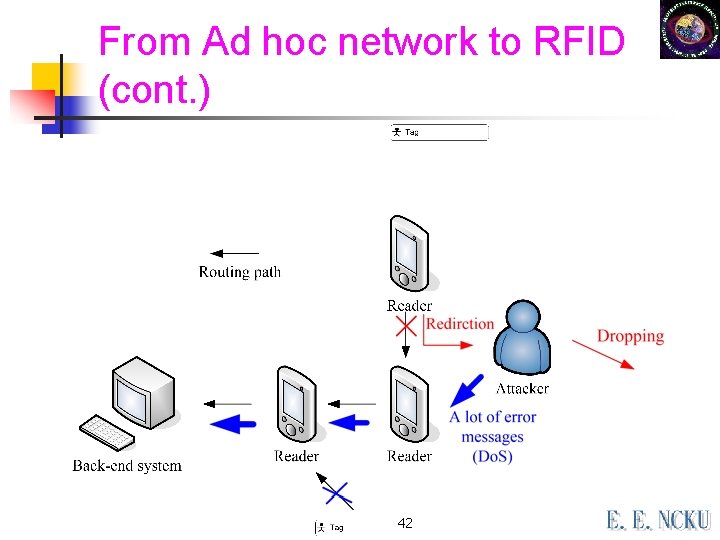
From Ad hoc network to RFID n n In a mall, it is impossible to connect every readers by wiring. So, the architecture of readers is the same as ad hoc network. Besides, due to the hardware constraint, we should sum up the items by back-end system and compare with the value of shopping car. Because of the architecture, there also some problems in RFID system. n n Modification Impersonation Fabrication Dropping 40

From Ad hoc network to RFID (cont. ) n Do. S n In a mall, an attacker can achieve Do. S attack by interfering the RFID readers which are wireless connected. n n Let the item information cannot reach to the back-end system. Let the back-end system crush by sending readers error messages. 41
From Ad hoc network to RFID (cont. ) 42

Summary Different environments require different solutions n n n Different requirements depending on situation Available infrastructure? Solutions exist, but all have drawbacks, one has to decide which security aspects are most important n n Confidentiality? Availability? Throughput? 43

Open Problems (1) n Security n How can I trust you to forward my packets without tampering? n n Need to be able to detect tampering How do I know you are what you claim to be ? n n Authentication issues Hard to guarantee access to a certification authority 44

Open Problems n (2) Other issues received much less attention Other interesting problems: n n n Address assignment problem Media Access Control (MAC) protocols Improving interaction between protocol layers Distributed algorithms for MANET Qo. S issues Applications for MANET 45

Q&A Thanks for your attention ! 46
- Slides: 46