Outline Announcement Authentication Cryptography Authentication Quiz 3 at











- Slides: 37

Outline • Announcement • Authentication – Cryptography – Authentication • Quiz #3 at the end of today’s class 9/25/2020 COP 5611 - Operating Systems 1

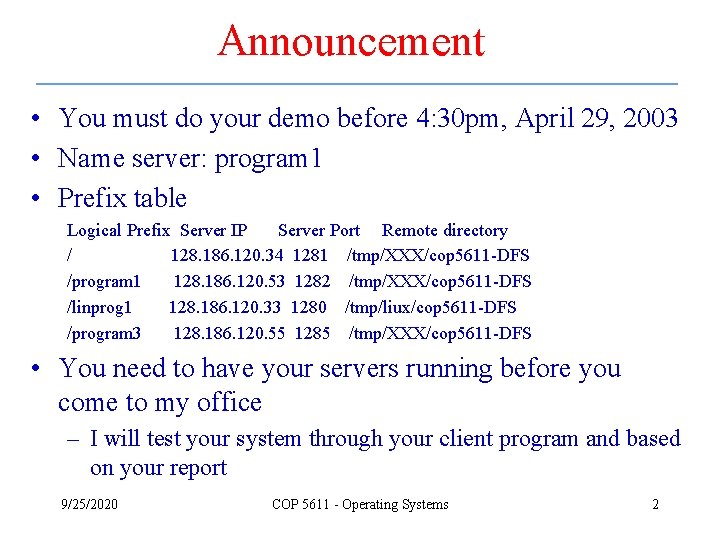
Announcement • You must do your demo before 4: 30 pm, April 29, 2003 • Name server: program 1 • Prefix table Logical Prefix Server IP Server Port Remote directory / 128. 186. 120. 34 1281 /tmp/XXX/cop 5611 -DFS /program 1 128. 186. 120. 53 1282 /tmp/XXX/cop 5611 -DFS /linprog 1 128. 186. 120. 33 1280 /tmp/liux/cop 5611 -DFS /program 3 128. 186. 120. 55 1285 /tmp/XXX/cop 5611 -DFS • You need to have your servers running before you come to my office – I will test your system through your client program and based on your report 9/25/2020 COP 5611 - Operating Systems 2

Introduction • The fundamental problem to security in distributed systems is the use of cryptographic techniques – Access matrix model can be used to prevent unauthorized accesses if the users that claimed to be are true – However, in distributed systems, the user authentication becomes a big problem 9/25/2020 COP 5611 - Operating Systems 3

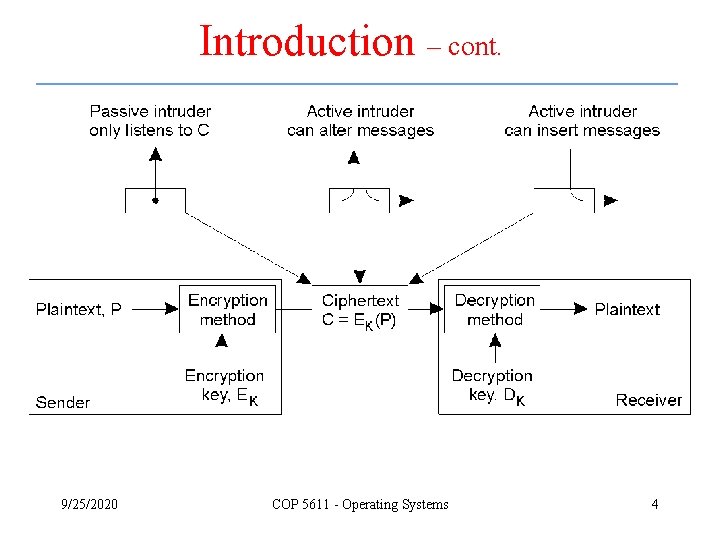
Introduction – cont. 9/25/2020 COP 5611 - Operating Systems 4

Potential Threats • A threat to a system in which an intruder can have access to only the ciphertext is called a ciphertextonly attack • A threat to a system in which an intruder can have access to both ciphertext and a considerable amount of corresponding plaintext is called a known-plaintext attack • A threat to a system in which an intruder can obtain ciphertext corresponding to plaintext of his choice is referred to as a chosen-plaintext attack 9/25/2020 COP 5611 - Operating Systems 5

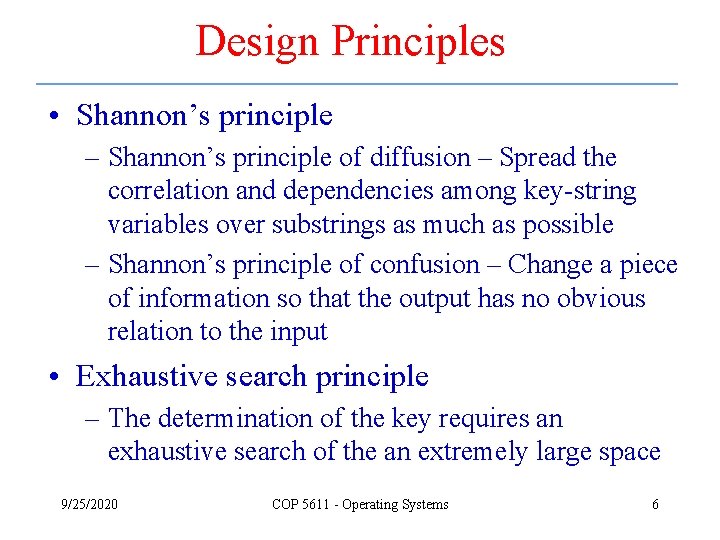
Design Principles • Shannon’s principle – Shannon’s principle of diffusion – Spread the correlation and dependencies among key-string variables over substrings as much as possible – Shannon’s principle of confusion – Change a piece of information so that the output has no obvious relation to the input • Exhaustive search principle – The determination of the key requires an exhaustive search of the an extremely large space 9/25/2020 COP 5611 - Operating Systems 6

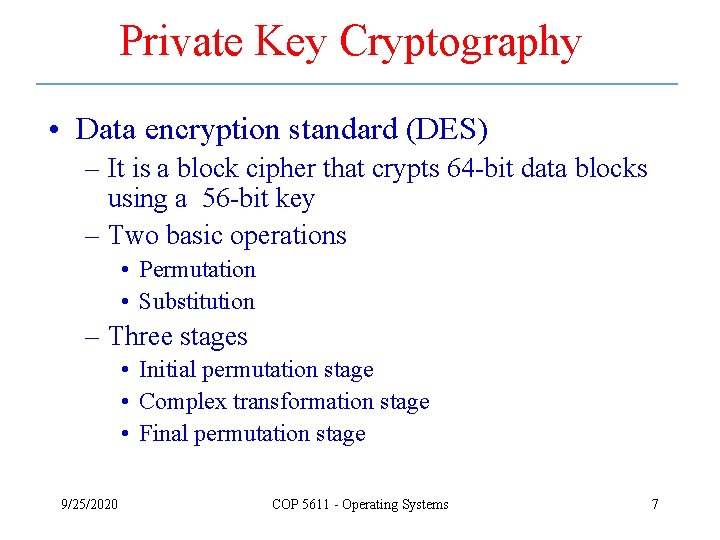
Private Key Cryptography • Data encryption standard (DES) – It is a block cipher that crypts 64 -bit data blocks using a 56 -bit key – Two basic operations • Permutation • Substitution – Three stages • Initial permutation stage • Complex transformation stage • Final permutation stage 9/25/2020 COP 5611 - Operating Systems 7

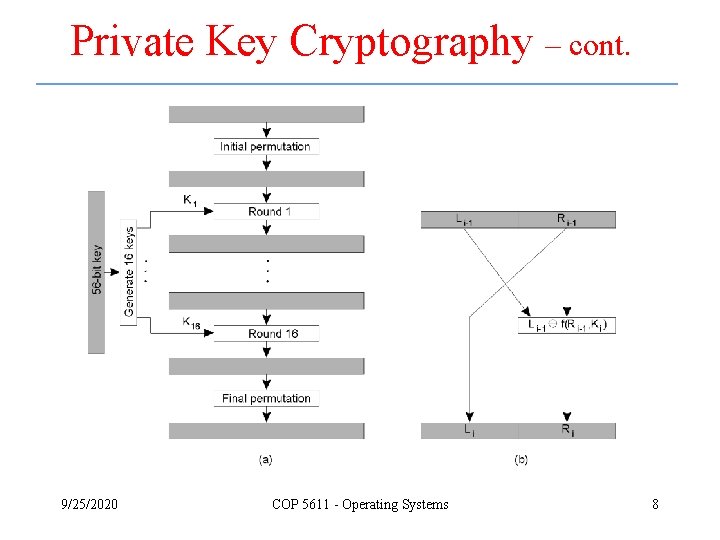
Private Key Cryptography – cont. 9/25/2020 COP 5611 - Operating Systems 8

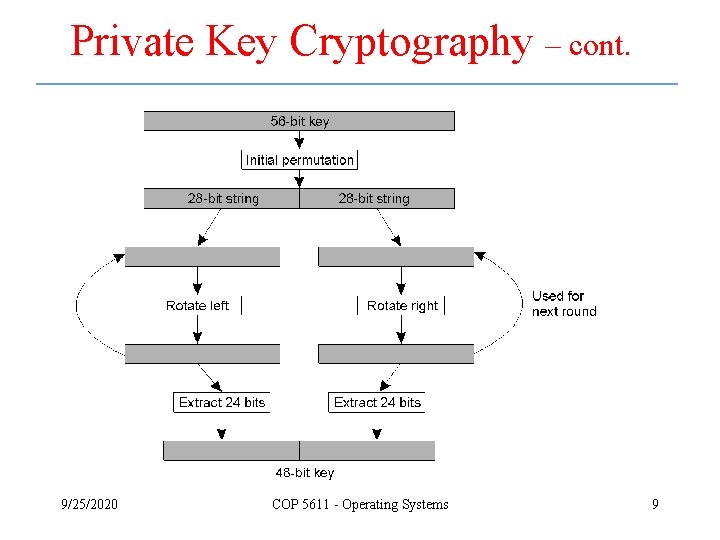
Private Key Cryptography – cont. 9/25/2020 COP 5611 - Operating Systems 9

Private Key Cryptography – cont. 9/25/2020 COP 5611 - Operating Systems 10

Public Key Cryptography • Private key cryptography and conventional cryptographic techniques require the distribution of secret keys – Known as the key distribution problem • Public key cryptography solves the key distribution problem by making the encryption procedure and the associated key available in the public domain 9/25/2020 COP 5611 - Operating Systems 11

Public Key Cryptography – cont. • Now it is possible for two users to have a secure communication even they have not communicated before • Implementation issues – One-way functions 9/25/2020 COP 5611 - Operating Systems 12

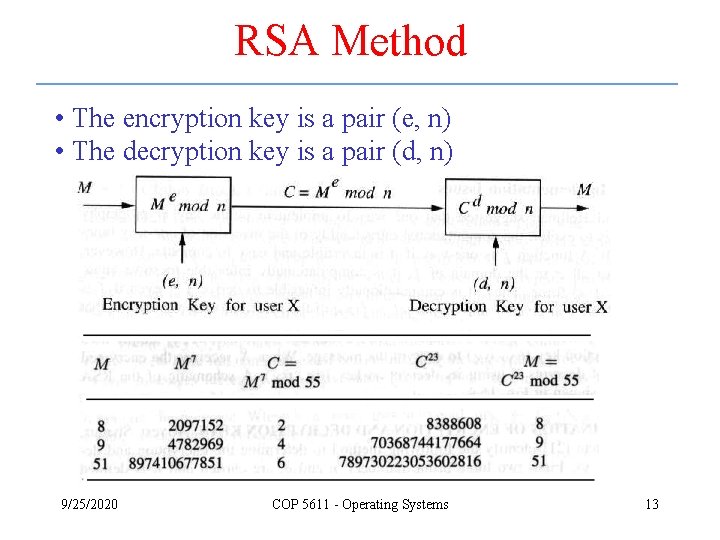
RSA Method • The encryption key is a pair (e, n) • The decryption key is a pair (d, n) 9/25/2020 COP 5611 - Operating Systems 13

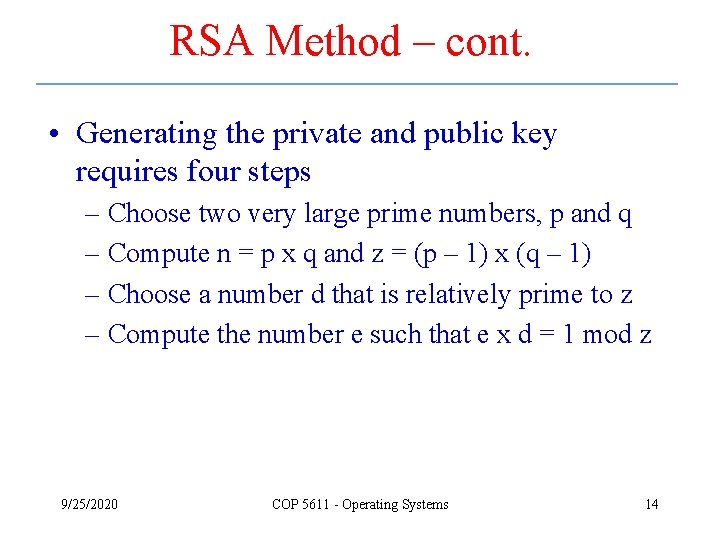
RSA Method – cont. • Generating the private and public key requires four steps – Choose two very large prime numbers, p and q – Compute n = p x q and z = (p – 1) x (q – 1) – Choose a number d that is relatively prime to z – Compute the number e such that e x d = 1 mod z 9/25/2020 COP 5611 - Operating Systems 14

Authentication • In distributed systems, authentication means verifying the identity of communicating entities to each other – The assumption is that the communication network is not secure in that an intruder can copy and play back a message on the network – The textbook called it “interactive secure connections” 9/25/2020 COP 5611 - Operating Systems 15

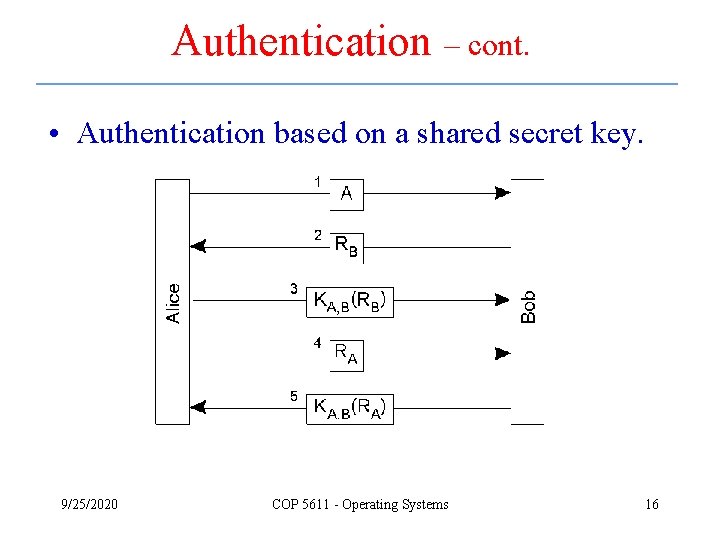
Authentication – cont. • Authentication based on a shared secret key. 9/25/2020 COP 5611 - Operating Systems 16

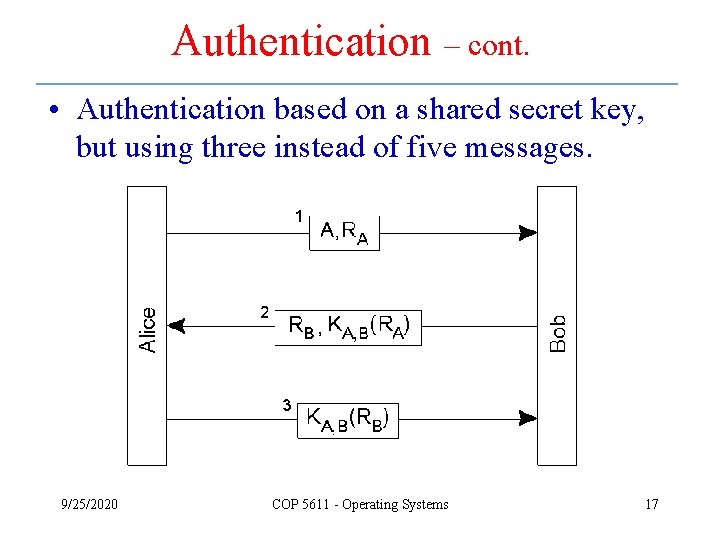
Authentication – cont. • Authentication based on a shared secret key, but using three instead of five messages. 9/25/2020 COP 5611 - Operating Systems 17

Authentication – cont. • The reflection attack. 9/25/2020 COP 5611 - Operating Systems 18

Authentication Using a Key Distribution Center • The principle of using a KDC. 9/25/2020 COP 5611 - Operating Systems 19

Authentication Using a Key Distribution Center – cont. • Using a ticket and letting Alice set up a connection to Bob. 9/25/2020 COP 5611 - Operating Systems 20

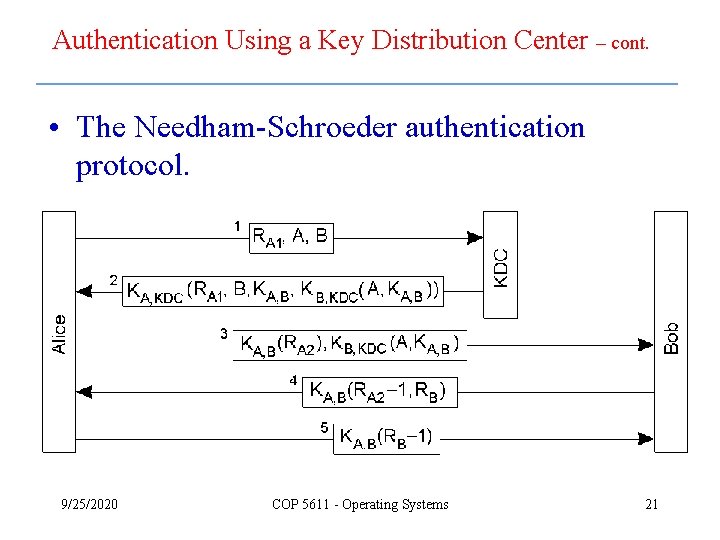
Authentication Using a Key Distribution Center – cont. • The Needham-Schroeder authentication protocol. 9/25/2020 COP 5611 - Operating Systems 21

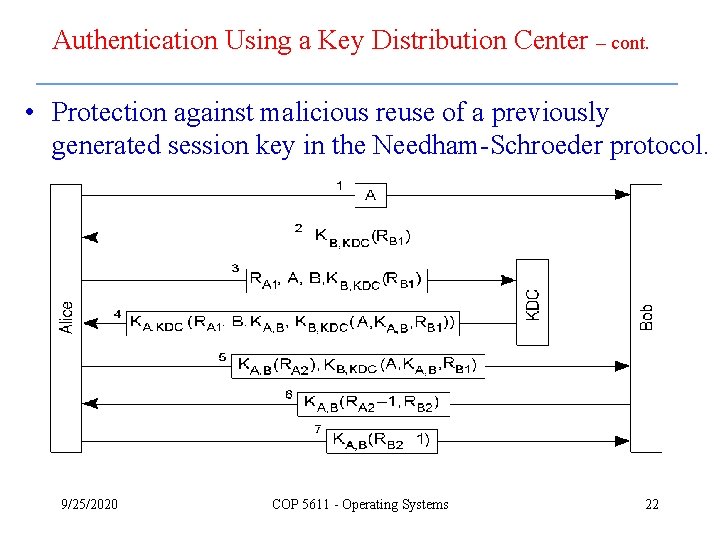
Authentication Using a Key Distribution Center – cont. • Protection against malicious reuse of a previously generated session key in the Needham-Schroeder protocol. 9/25/2020 COP 5611 - Operating Systems 22

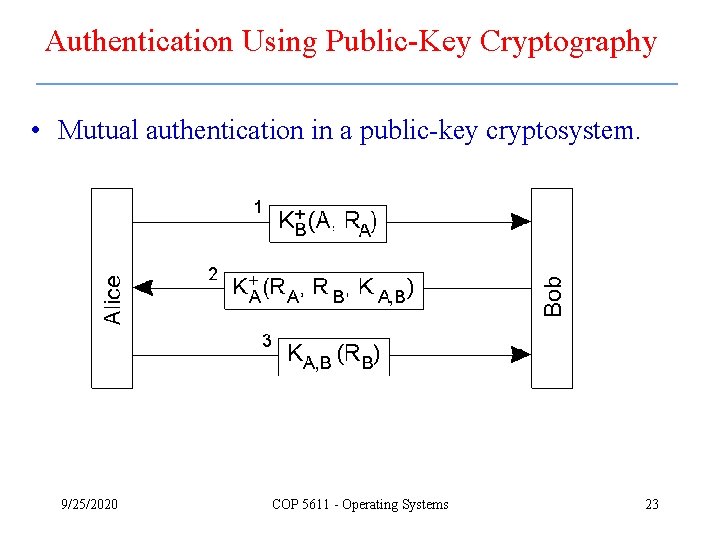
Authentication Using Public-Key Cryptography • Mutual authentication in a public-key cryptosystem. 9/25/2020 COP 5611 - Operating Systems 23

Message Integrity and Confidentiality • Message integrity means that messages are protected against modification • Confidentiality ensures that messages cannot be intercepted and read by eavesdroppers • Digital signatures – A user cannot forge the signature of other users – A sender of a signed message cannot deny the validity of his signature on the message – A recipient of a signed message cannot modify the signature in the message 9/25/2020 COP 5611 - Operating Systems 24

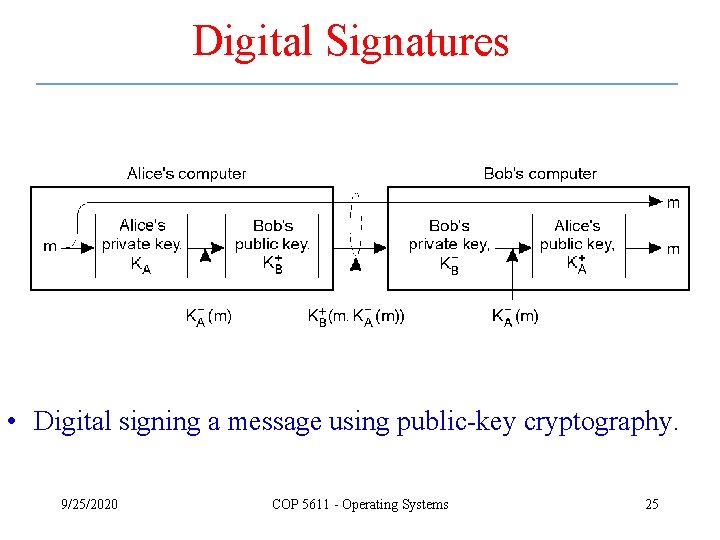
Digital Signatures • Digital signing a message using public-key cryptography. 9/25/2020 COP 5611 - Operating Systems 25

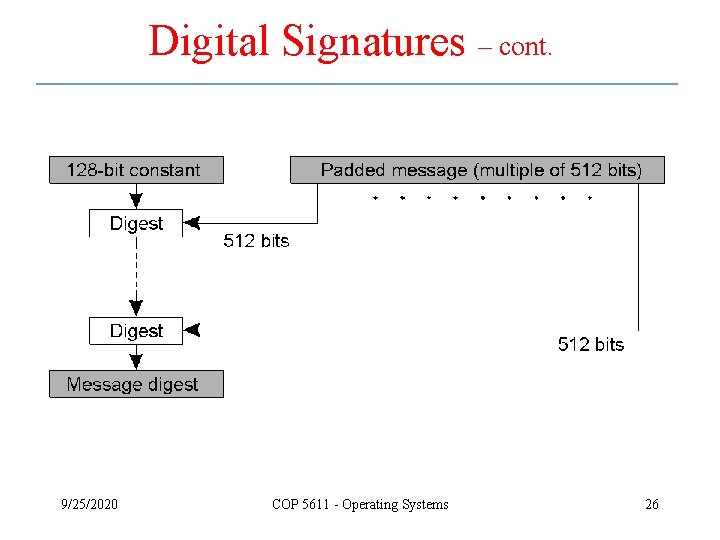
Digital Signatures – cont. 9/25/2020 COP 5611 - Operating Systems 26

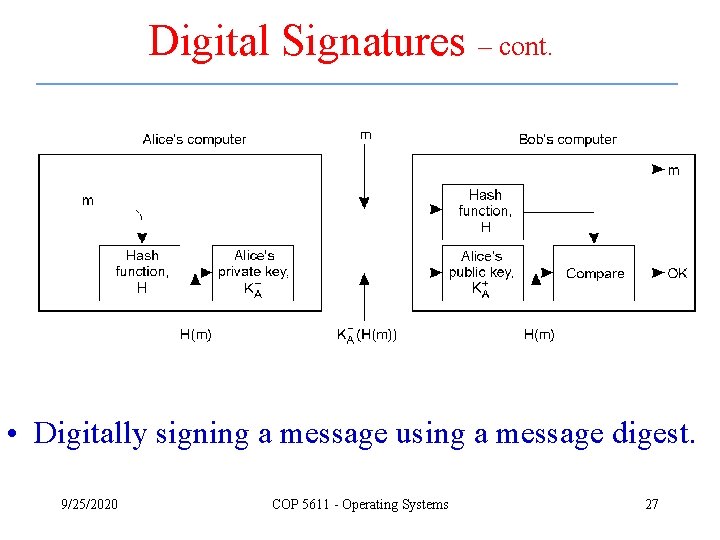
Digital Signatures – cont. • Digitally signing a message using a message digest. 9/25/2020 COP 5611 - Operating Systems 27

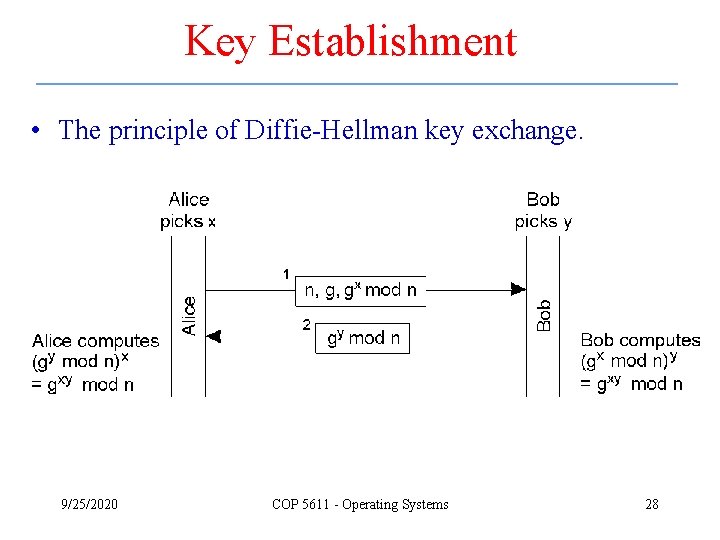
Key Establishment • The principle of Diffie-Hellman key exchange. 9/25/2020 COP 5611 - Operating Systems 28

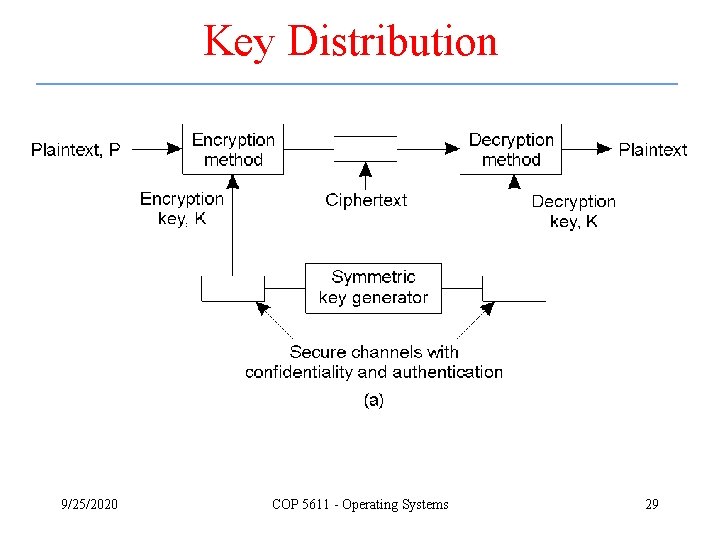
Key Distribution 9/25/2020 COP 5611 - Operating Systems 29

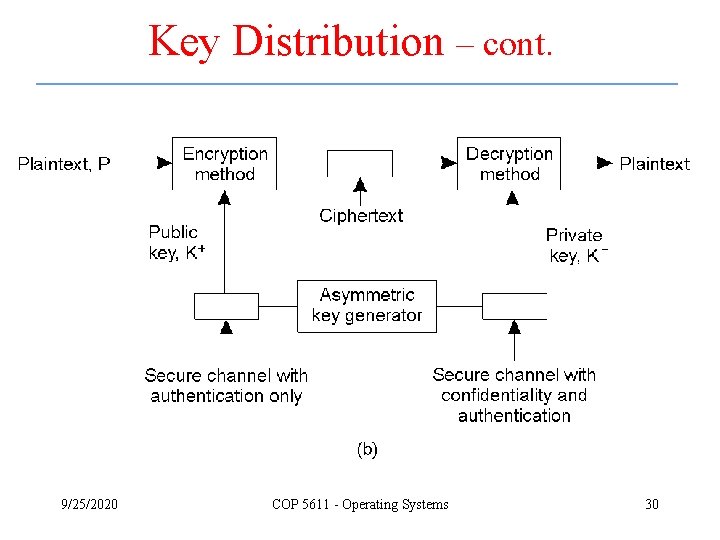
Key Distribution – cont. 9/25/2020 COP 5611 - Operating Systems 30

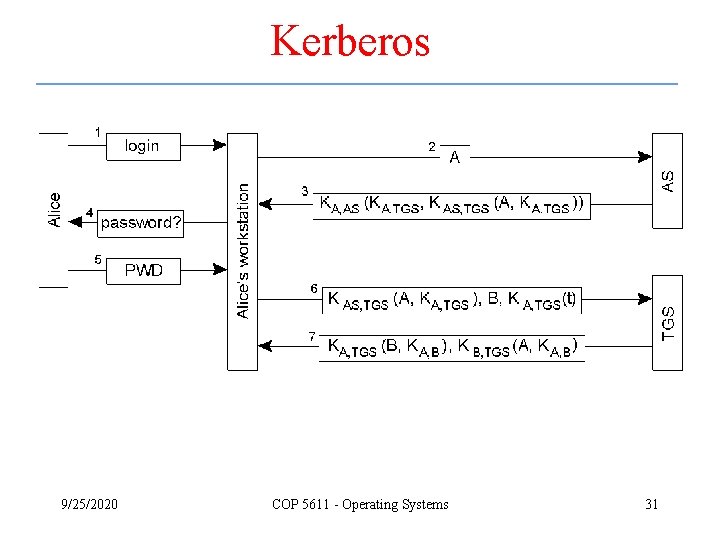
Kerberos 9/25/2020 COP 5611 - Operating Systems 31

Kerberos – cont. • Setting up a secure channel in Kerberos. 9/25/2020 COP 5611 - Operating Systems 32

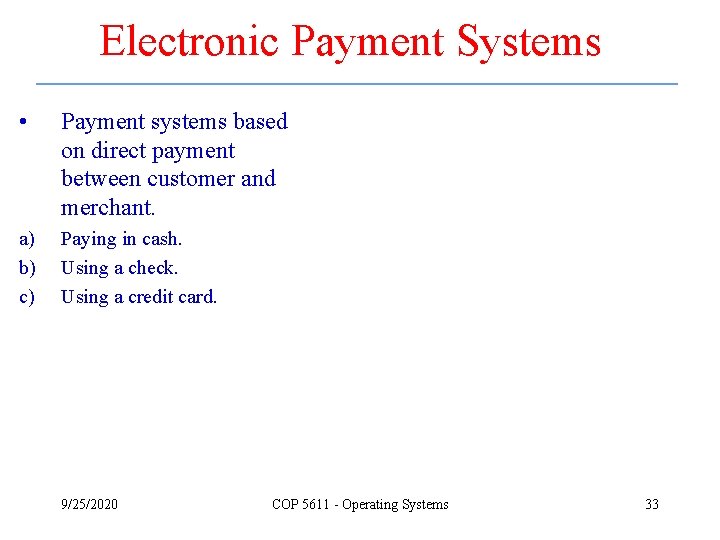
Electronic Payment Systems • Payment systems based on direct payment between customer and merchant. a) b) c) Paying in cash. Using a check. Using a credit card. 9/25/2020 COP 5611 - Operating Systems 33

Electronic Payment Systems – cont. • Payment systems based on money transfer between banks. a) Payment by money order. b) Payment through debit order. 9/25/2020 COP 5611 - Operating Systems 34

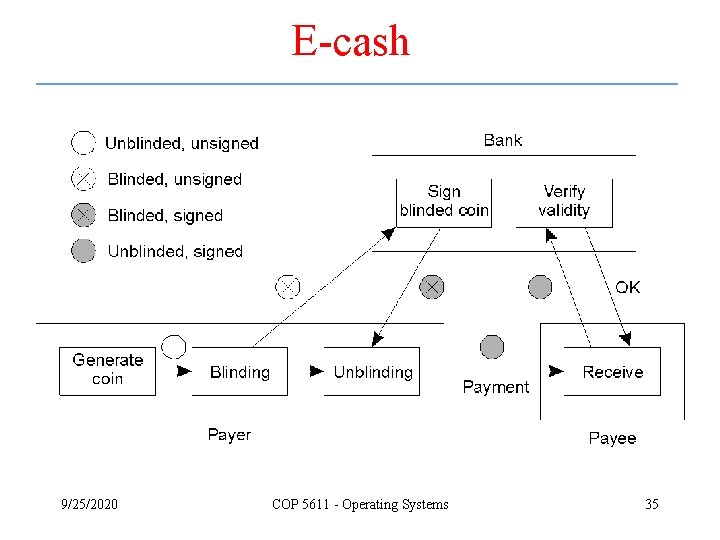
E-cash 9/25/2020 COP 5611 - Operating Systems 35

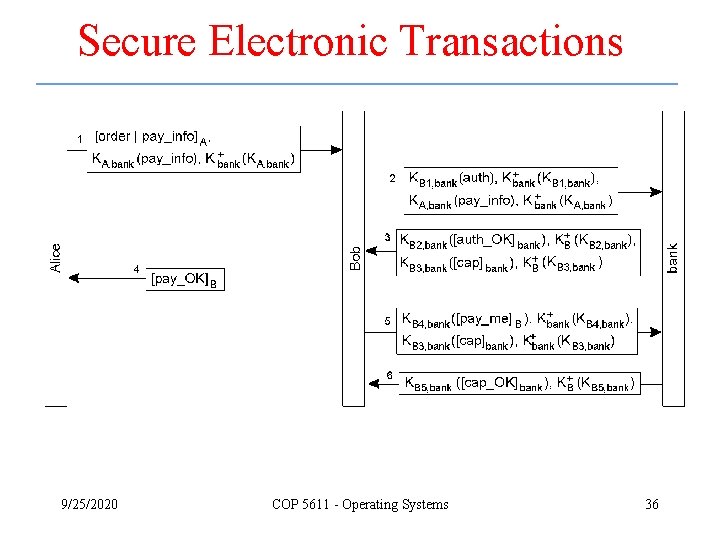
Secure Electronic Transactions 9/25/2020 COP 5611 - Operating Systems 36

Summary • Cryptography is a fundamental problem in security of distributed systems – Based on private keys – Based on public keys • Authentication in distributed systems • There are still a lot of challenges and research issues in this area 9/25/2020 COP 5611 - Operating Systems 37