Other Security Issues MultiLayer Security Firewalls Total Security


- Slides: 19

Other Security Issues Multi-Layer Security Firewalls Total Security Intrusion Detection Trust

Multi-Layer Security z Security Can be Applied at Multiple Layers Simultaneously y. Application layer security for database, email, etc. y. Transport layer: SSL y. Internet layer: IPsec (Chapter 9, Module F) y. Data link layer: PPTP, L 2 TP (Module F) y. Physical layer: locks 2

Multi-Layer Security 3 z Applying security at 2 or more layers is good y. If security is broken at one layer, the communication will still be secure z However, y. Security slows down processing y. Multi-Layer security slows down processing at each layer

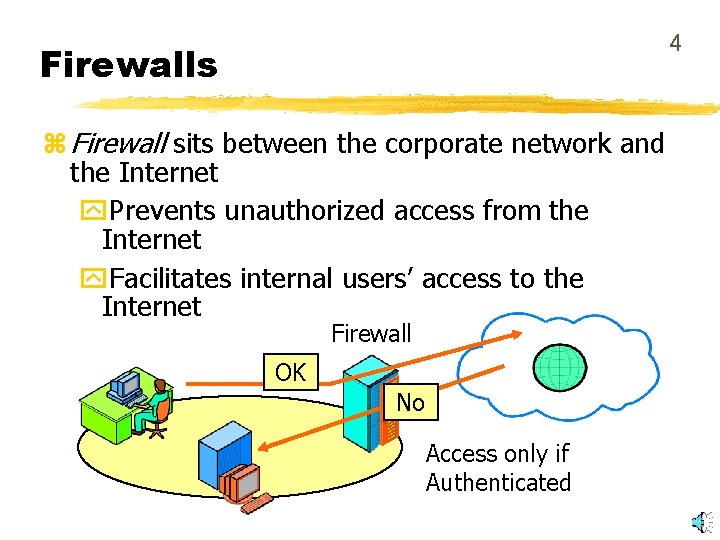
4 Firewalls z Firewall sits between the corporate network and the Internet y. Prevents unauthorized access from the Internet y. Facilitates internal users’ access to the Internet Firewall OK No Access only if Authenticated

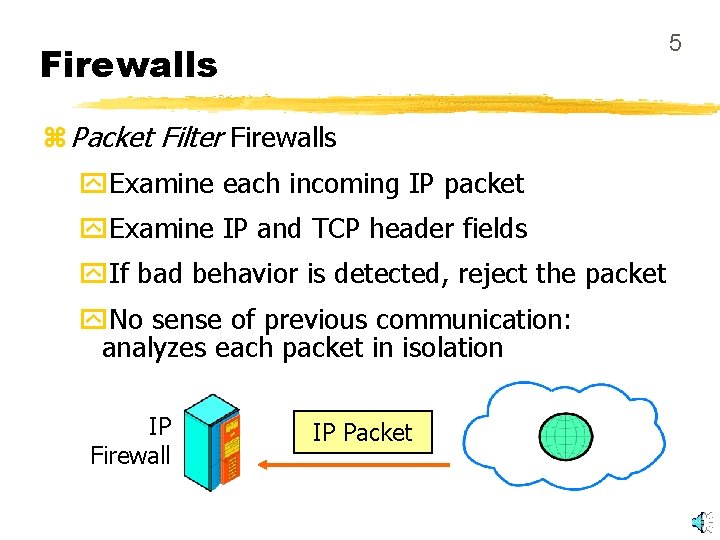
5 Firewalls z Packet Filter Firewalls y. Examine each incoming IP packet y. Examine IP and TCP header fields y. If bad behavior is detected, reject the packet y. No sense of previous communication: analyzes each packet in isolation IP Firewall IP Packet

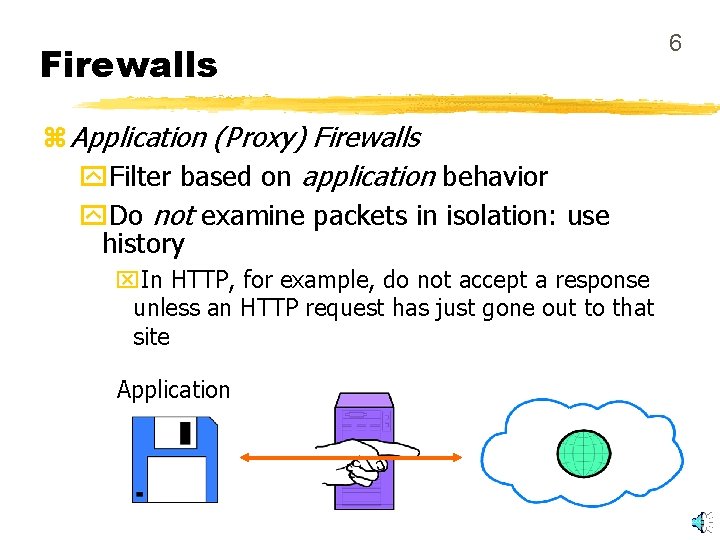
Firewalls z Application (Proxy) Firewalls y. Filter based on application behavior y. Do not examine packets in isolation: use history x. In HTTP, for example, do not accept a response unless an HTTP request has just gone out to that site Application 6

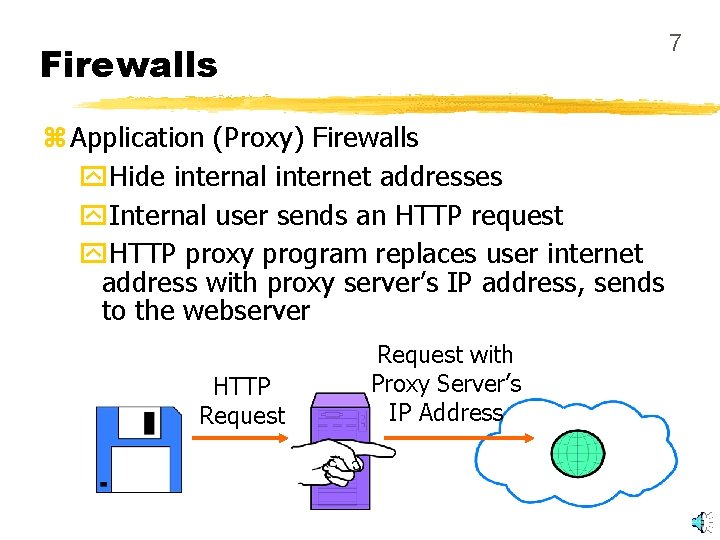
7 Firewalls z Application (Proxy) Firewalls y. Hide internal internet addresses y. Internal user sends an HTTP request y. HTTP proxy program replaces user internet address with proxy server’s IP address, sends to the webserver HTTP Request with Proxy Server’s IP Address

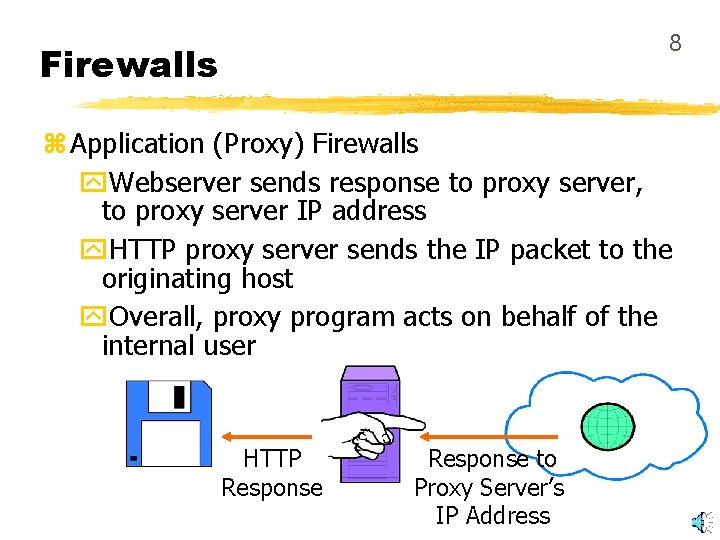
8 Firewalls z Application (Proxy) Firewalls y. Webserver sends response to proxy server, to proxy server IP address y. HTTP proxy server sends the IP packet to the originating host y. Overall, proxy program acts on behalf of the internal user HTTP Response to Proxy Server’s IP Address

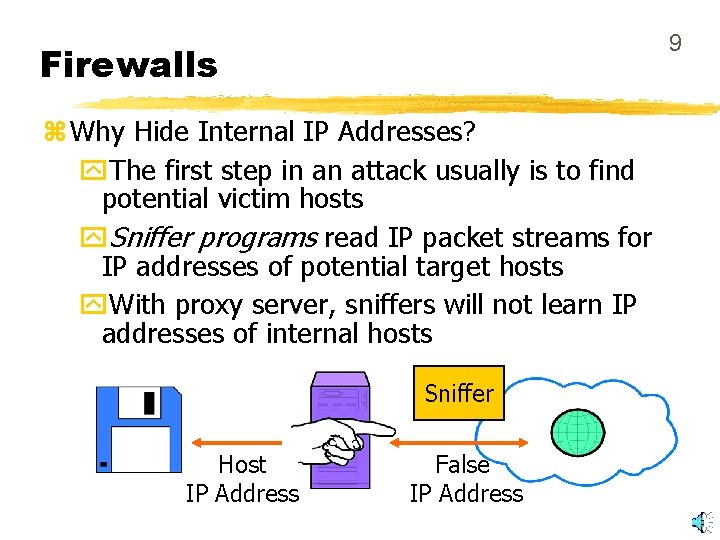
9 Firewalls z Why Hide Internal IP Addresses? y. The first step in an attack usually is to find potential victim hosts y. Sniffer programs read IP packet streams for IP addresses of potential target hosts y. With proxy server, sniffers will not learn IP addresses of internal hosts Sniffer Host IP Address False IP Address

Firewalls z Application Firewalls y. Need a separate program (proxy) for each application y. Not all applications have rules that allow filtering 10

Total Security 11 z Network Security is Only Part z Server Security y. Hackers can take down servers with denial-of -service attack y. Hacker can log in as root user and take over the server y. Steal data, lock out legitimate users, etc.

Total Security z Server Security y. Occasionally, weakness are discovered in server operating systems y. This knowledge is quickly disseminated y. Known security weaknesses 12

Total Security 13 z Server Security y. Server operating system (SOS) vendors create patches y. Many firms do not download patches y. This makes them vulnerable to hackers, who quickly develop tools to probe for and then exploit known weaknesses

Total Security 14 z Client PC Security y. Known security weaknesses exist but patches are rarely downloaded y. Users often have no passwords or weak passwords on their computer y. Adversaries take over client PCs and can therefore take over control over SSL, other secure communication protocols

Total Security z Application Software y. May contain viruses x. Must filter incoming messages y. Database and other applications can add their own security with passwords and other protections 15

Total Security z Managing Users y. Often violate security procedures, making technical security worthless y. Social engineering: attacker tricks user into violating security procedures 16

Intrusion Detection 17 z Intrusion detection software to detect and report intrusions as they are occurring z Needed y. Lets organization stop intruders so that intruders do not have unlimited time to probe for weaknesses y. Helps organization assess security threats y. Audit logs list where intruder has been: vital in legal prosecution

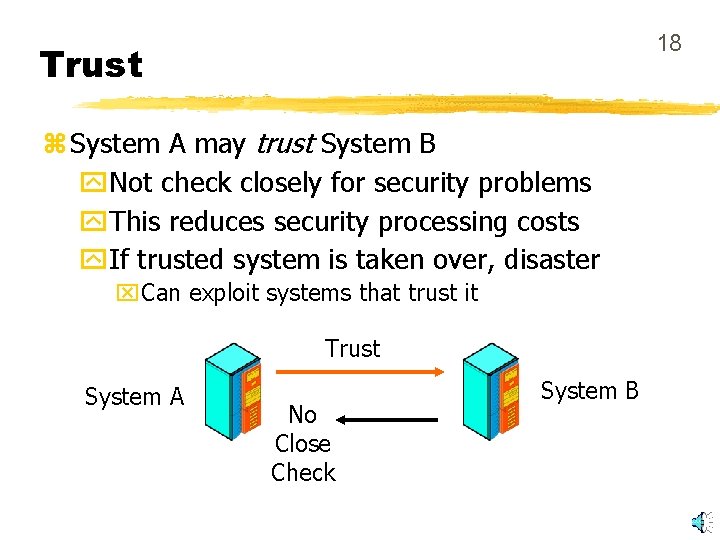
18 Trust z System A may trust System B y. Not check closely for security problems y. This reduces security processing costs y. If trusted system is taken over, disaster x. Can exploit systems that trust it Trust System A No Close Check System B

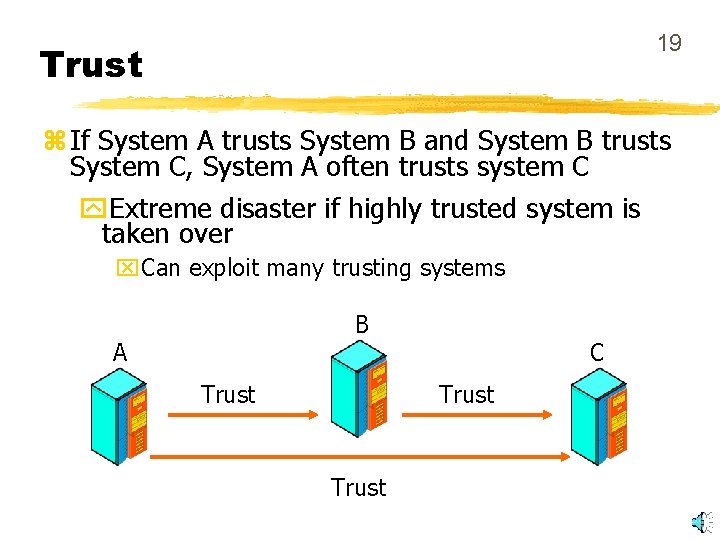
19 Trust z If System A trusts System B and System B trusts System C, System A often trusts system C y. Extreme disaster if highly trusted system is taken over x. Can exploit many trusting systems B A Trust C Trust