OTHER OPERATING SYSTEM COMPONENTS CGS 3763 Operating System

















![Free-Space Management • Bit vector (n blocks) 0 1 2 n-1 … bit[i] = Free-Space Management • Bit vector (n blocks) 0 1 2 n-1 … bit[i] =](https://slidetodoc.com/presentation_image/6676ddf952ef661cecbd347f0784feb5/image-41.jpg)















- Slides: 88

OTHER OPERATING SYSTEM COMPONENTS CGS 3763 - Operating System Concepts UCF, Spring 2004 1

REVEIW FROM CHAPTER 3 • Service - a task performed by the operating system • Component - a portion of the operating system program which performs a specific set of services • Structure - The way in which components are organized to create an operating system 2

OS COMPONENTS • Process Management • Memory Management (RAM) • Networking • File Management • I/O Management • Secondary/Tertiary Storage Management • Protection 3

COMPONENTS: Process Management • A process is a program in execution. A process needs certain resources, including CPU time, memory, files, and I/O devices, to accomplish its task. • The operating system is responsible for the following activities in connection with process management. – – Process creation and deletion. Process scheduling, suspension and resumption. Deadlock handling Providing mechanisms for: • process synchronization • interprocess communication 4

COMPONENTS: Memory Management • Memory is a large array of words or bytes, each with its own address. It is a repository of quickly accessible data shared by the CPU and I/O devices. • The operating system is responsible for the following activities in connections with memory management: – Keep track of free memory – Determine if free memory sufficient for a new process – Keep track of used memory and to which process that memory is allocated. – Allocate and deallocate memory space as needed. 5

COMPONENTS: Networking • A distributed or loosely coupled system is a collection of processors that do not share memory or a clock. • The processors in the system are connected through a communication network. • Operating system is responsible for: – Managing communication via a network • name resolution, routing strategies, protocols, etc. – Sharing of data with remote systems • distributed file systems – Sharing computations & processes • coordination of distributed processes & resources • scheduling, communication, synchronization & deadlock 6

OS COMPONENTS • Process Management • Memory Management (RAM) • Networking • File Management • I/O Management • Secondary/Tertiary Storage Management • Protection 7

COMPONENTS: File Management • A file is a collection of related information defined by its creator. Commonly, files represent programs (both source and object forms) and data. • The operating system is responsible for the following activities in connections with file management: – File creation and deletion. – Directory creation and deletion. – Support of primitives for manipulating files and directories. – Mapping files onto secondary storage. 8

File Concept • Contiguous logical address space • Types: – Data: numeric, character, binary – Program: executable / object • File Structure – None - sequence of words, bytes – Simple record structure • Lines , Fixed length, Variable length – More complex structures • Formatted document • Relocatable load file • Structure determined by OS or Application 9

File Attributes • Name – only information kept in human-readable form. • Type – needed for systems that support different types (see extension examples). • Location – pointer to file location on device. • Size – current file size. • Protection – controls who can do reading, writing, executing. • Time, date, and user identification – data for protection, security, and usage monitoring. • Information about files are kept in the directory structure, which is maintained on the disk. 10

File Types – Name, Extension 11

File Operations • Create / Delete • Append / Truncate • Access data inside the file: – Read – Write – Reposition within file • Open File Table Operations – Open(Fi) – search the directory structure on disk for entry Fi, and move the contents of entry to memory. – Close (Fi) – move the contents of entry Fi in memory to directory structure on disk. 12

Access Methods • Sequential Access – Cannot skip around • must continue forward or start over (rewind) • similar to cassette tape • Direct Access – Able to go directly to information in a file • similar to Audio CD – Location specified by offset from start of file – Significantly faster than sequential access 13

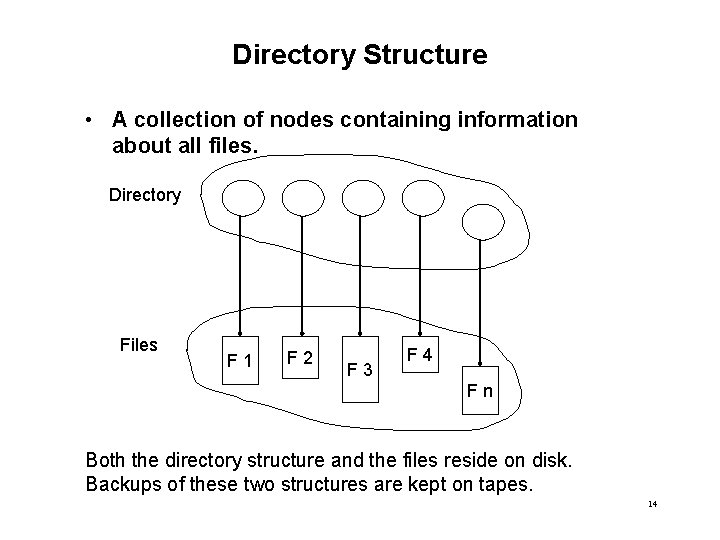
Directory Structure • A collection of nodes containing information about all files. Directory Files F 1 F 2 F 3 F 4 Fn Both the directory structure and the files reside on disk. Backups of these two structures are kept on tapes. 14

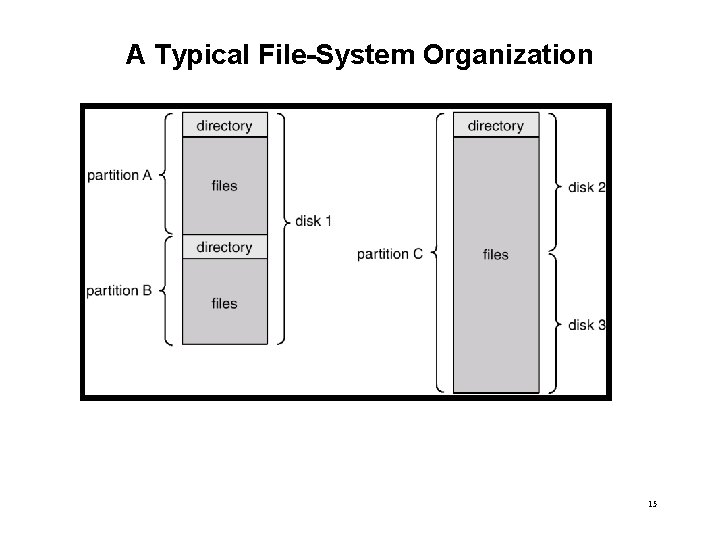
A Typical File-System Organization 15

Information in a Device Directory • Name • Type • Address • Current length • Maximum length • Date last accessed (for archival) • Date last updated (for dump) • Owner ID (who pays) • Protection information (discuss later) 16

Operations Performed on Directory • Search for a file • Add a file • Remove a file • List a directory • Rename a file • Traverse the file system – Move from one directory to another 17

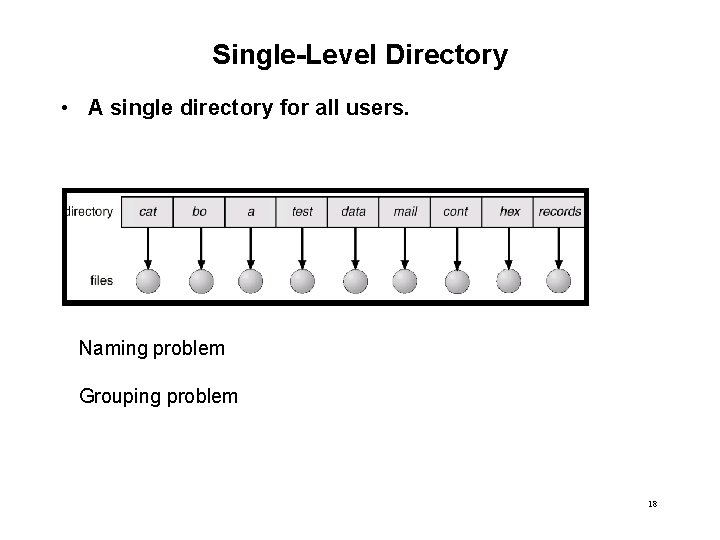
Single-Level Directory • A single directory for all users. Naming problem Grouping problem 18

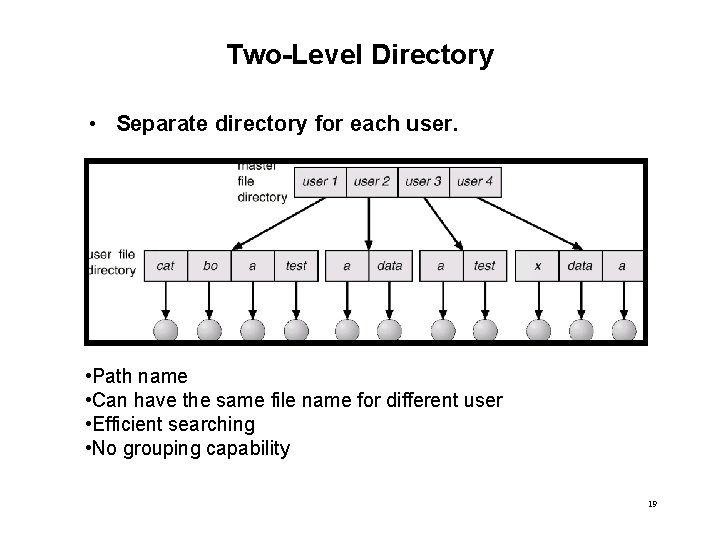
Two-Level Directory • Separate directory for each user. • Path name • Can have the same file name for different user • Efficient searching • No grouping capability 19

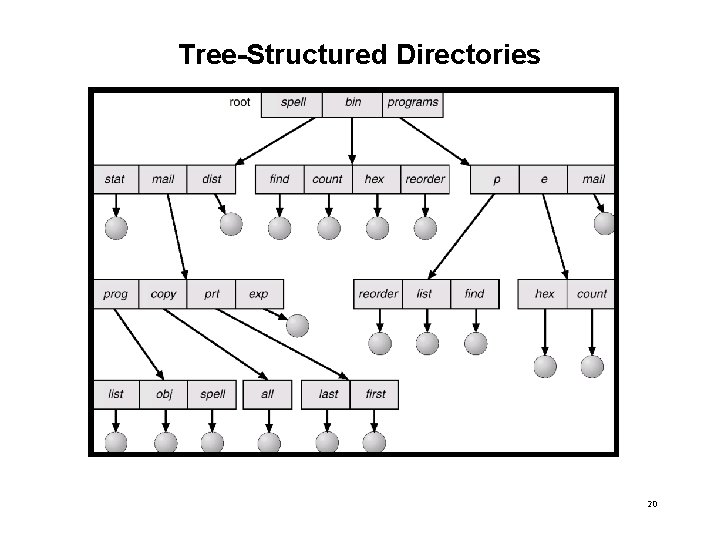
Tree-Structured Directories 20

Tree-Structured Directories (Cont. ) • Efficient searching • Grouping Capability • Path Name: – Absolute (from root) – Relative (from current directory) • Same file name can be used in different directories – Each file uniquely identified by its full path name 21

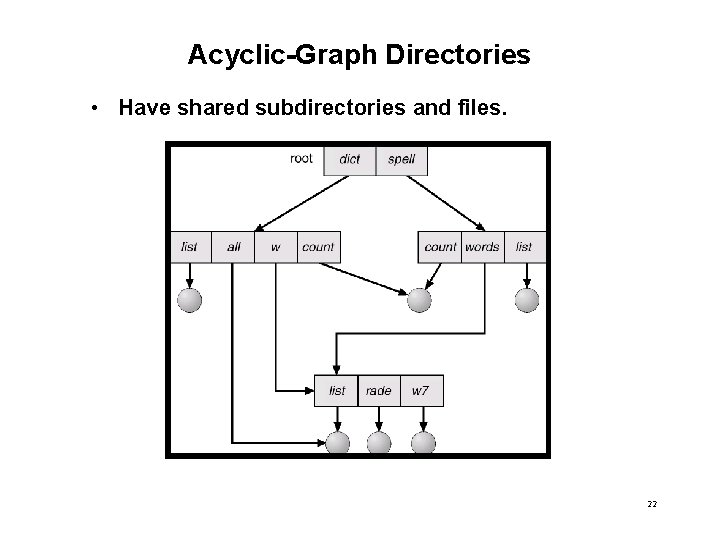
Acyclic-Graph Directories • Have shared subdirectories and files. 22

File Sharing • Sharing of files on multi-user systems is desirable. • Sharing may be done through a protection scheme. • On distributed systems, files may be shared across a network. • Network File System (NFS) is a common distributed file-sharing method. 23

Protection • File owner/creator should be able to control: – what can be done – by whom • Types of access – – – Read Write Execute Append Delete List 24

File Management Implementation • File System Structure • File System Implementation • Directory Implementation • Allocation Methods • Free-Space Management • Other Issues – – Efficiency and Performance Recovery Log-Structured File Systems Network File Systems (NFS) 25

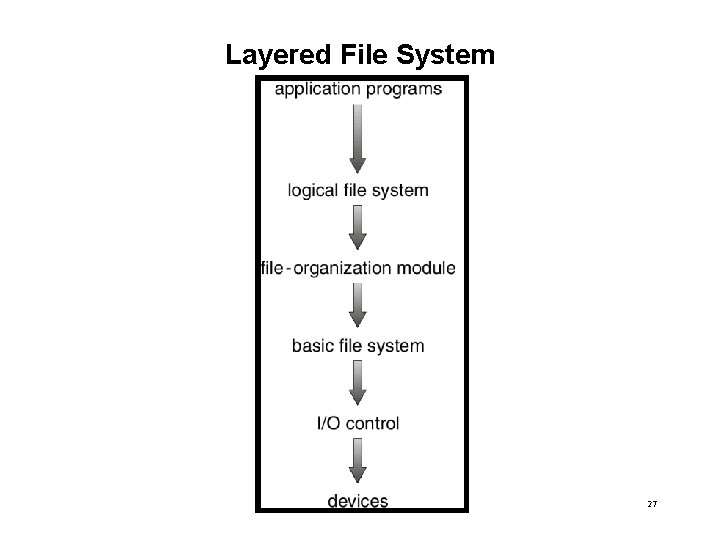
File-System Structure • What is a file? – Logical storage unit – Collection of related information – Has a structure specific to its purpose • File Control Block – storage structure consisting of information about an open file. • File system resides on secondary storage (disks). • File system organized into layers. 26

Layered File System 27

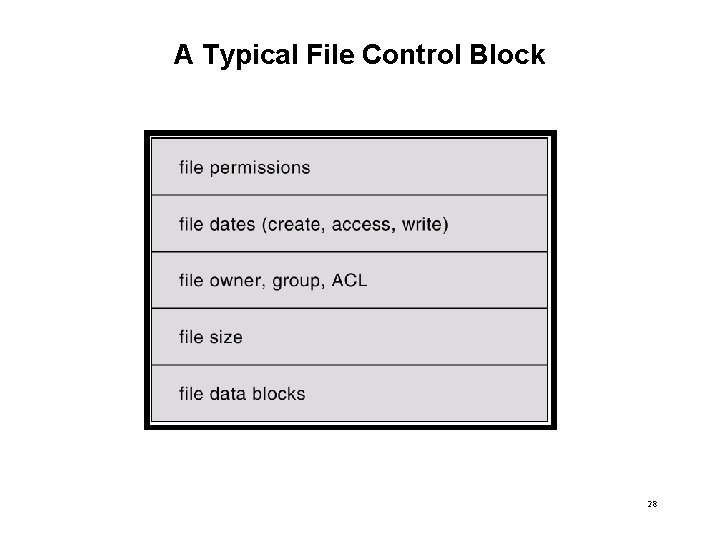
A Typical File Control Block 28

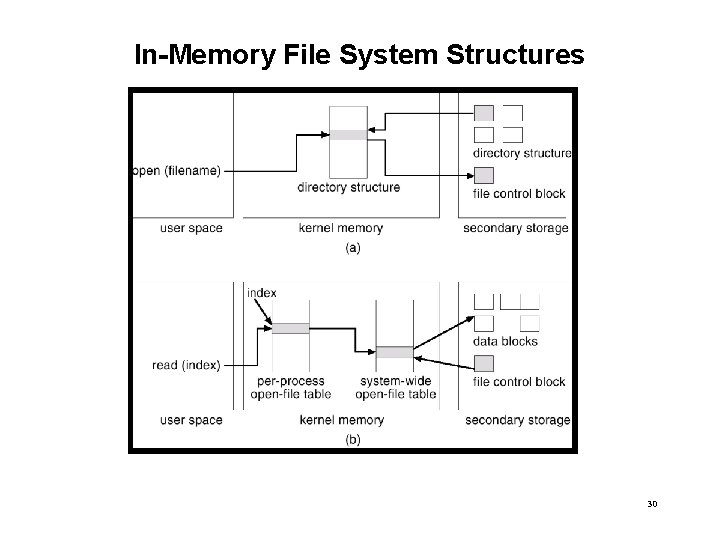
In-Memory File System Structures • The following figure illustrates the necessary file system structures provided by the operating systems. • Figure 12 -3(a) refers to opening a file. • Figure 12 -3(b) refers to reading a file. 29

In-Memory File System Structures 30

Directory Implementation • Linear list of file names with pointer to the data blocks. – simple to program – time-consuming to execute • Hash Table – linear list with hash data structure. – decreases directory search time – collisions – situations where two file names hash to the same location – fixed size 31

Allocation Methods • An allocation method refers to how disk blocks are allocated for files: – Contiguous allocation – Linked allocation – Indexed allocation 32

Contiguous Allocation • Each file occupies a set of contiguous blocks on the disk. • Simple – only starting location (block #) and length (number of blocks) are required. • Random access. • Wasteful of space (dynamic storage-allocation problem). • Files cannot grow. 33

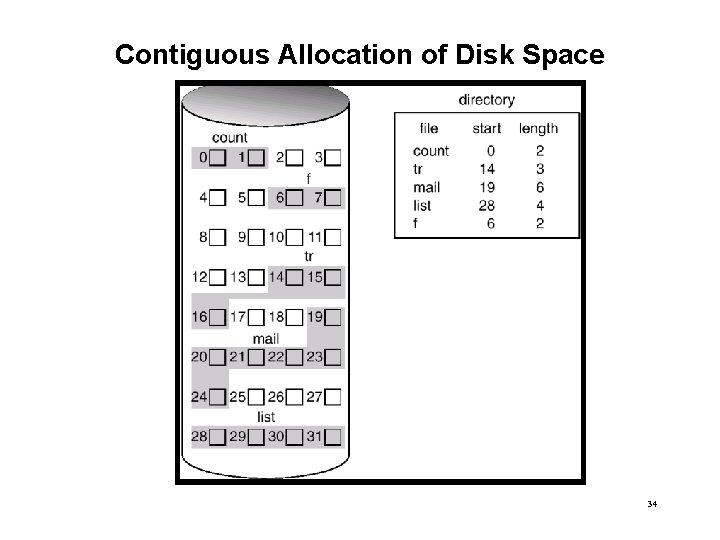
Contiguous Allocation of Disk Space 34

Linked Allocation • Each file is a linked list of disk blocks – blocks may be scattered anywhere on the disk. • Simple – need only starting address • Free-space management system – no waste of space • No random access • Mapping required • File Allocation Table is variation – Does allow Random Access 35

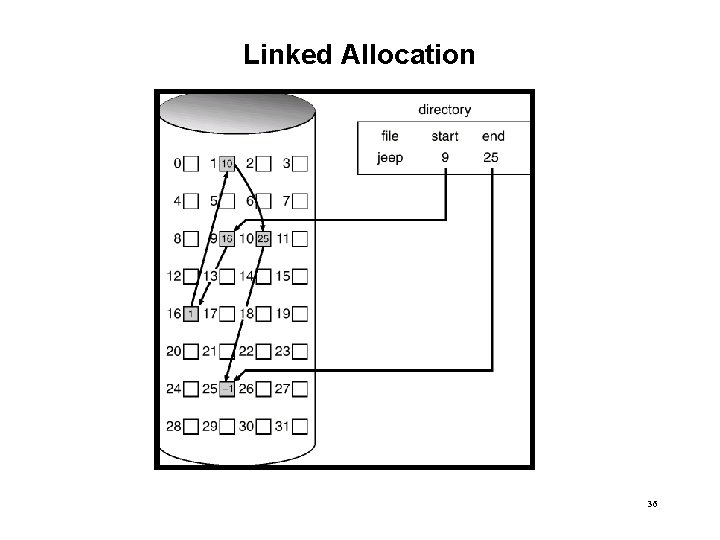
Linked Allocation 36

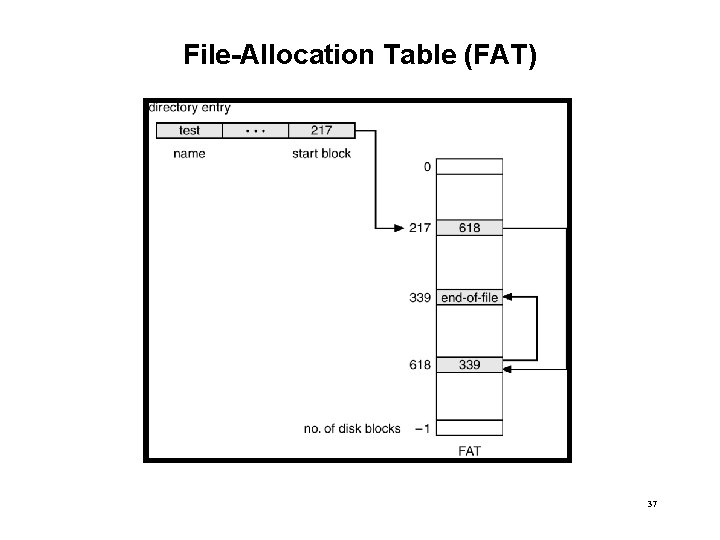
File-Allocation Table (FAT) 37

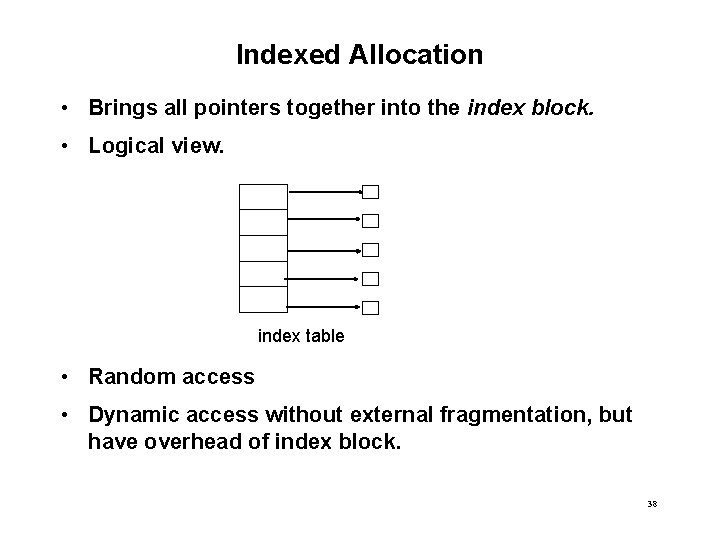
Indexed Allocation • Brings all pointers together into the index block. • Logical view. index table • Random access • Dynamic access without external fragmentation, but have overhead of index block. 38

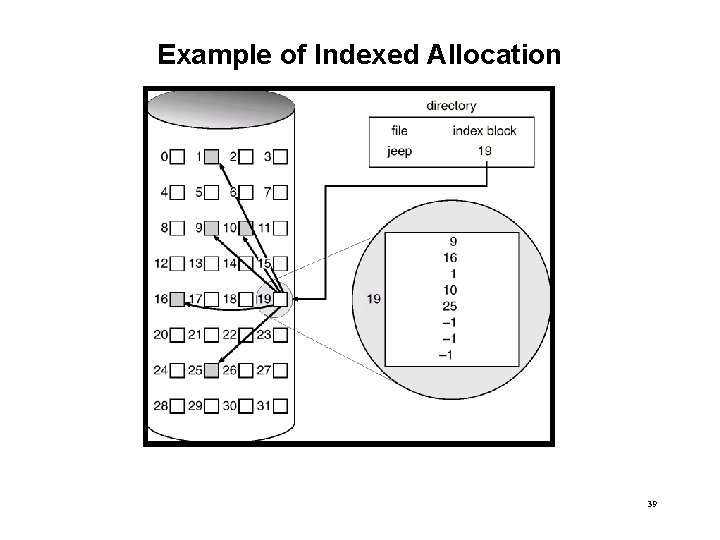
Example of Indexed Allocation 39

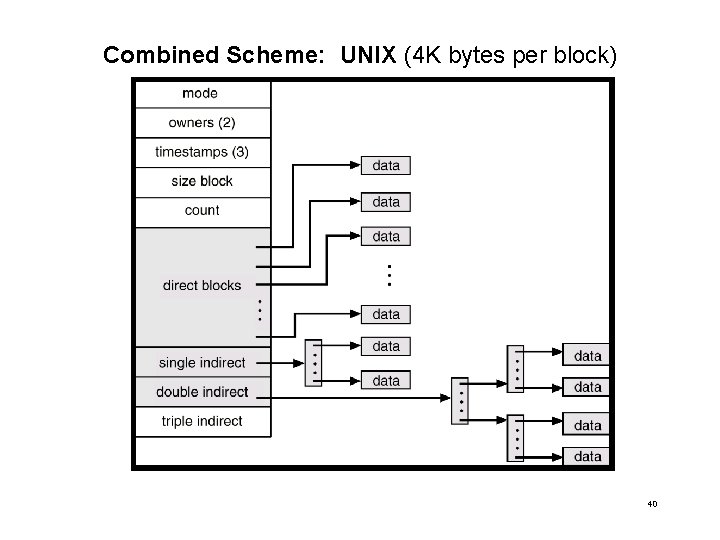
Combined Scheme: UNIX (4 K bytes per block) 40
![FreeSpace Management Bit vector n blocks 0 1 2 n1 biti Free-Space Management • Bit vector (n blocks) 0 1 2 n-1 … bit[i] =](https://slidetodoc.com/presentation_image/6676ddf952ef661cecbd347f0784feb5/image-41.jpg)
Free-Space Management • Bit vector (n blocks) 0 1 2 n-1 … bit[i] = 0 block[i] free 1 block[i] occupied – Easy to get contiguous files – Need to protect bit map 41

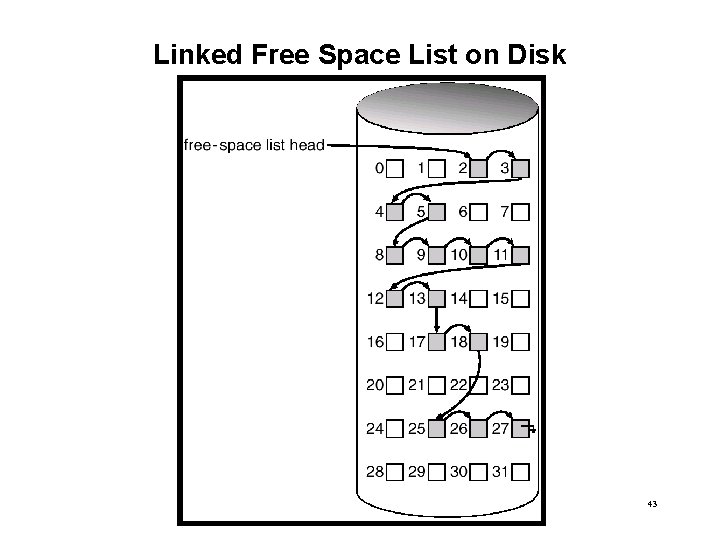
Free-Space Management (cont. ) • Linked list (free list) – Cannot get contiguous space easily – No waste of space – Need to protect pointer to free list 42

Linked Free Space List on Disk 43

OS COMPONENTS • Process Management • Memory Management (RAM) • Networking • File Management • I/O Management • Secondary/Tertiary Storage Management • Protection 44

COMPONENTS: I/O System Management • The I/O system consists of: – A buffer-caching system – A general device-driver interface – Drivers for specific hardware devices • Operating System is responsible for hiding the peculiarities of I/O devices from the user or application – – – Keyboard & Mouse Monitor, Printer Network Interface Card or Modem Joystick, webcam, sound cards Disks and other storage devices 45

I/O Hardware • Incredible variety of I/O devices • Common concepts – Port – Bus (daisy chain or shared direct access) – Controller (host adapter) • I/O instructions control devices • Devices have addresses, used by – Direct I/O instructions – Memory-mapped I/O 46

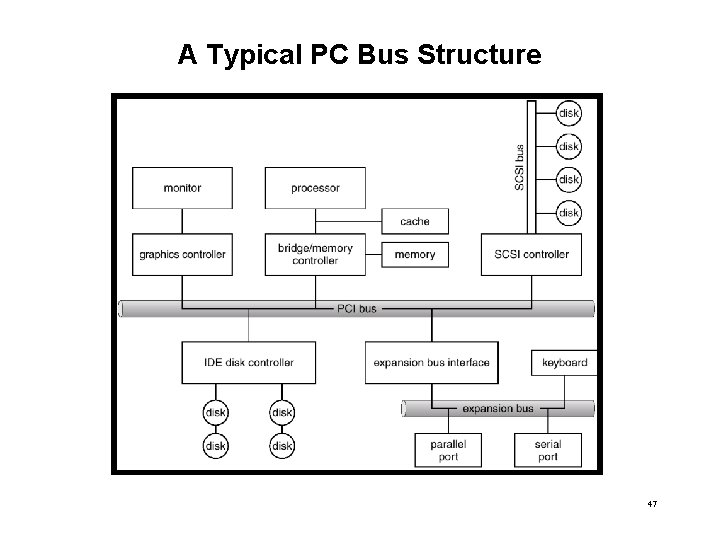
A Typical PC Bus Structure 47

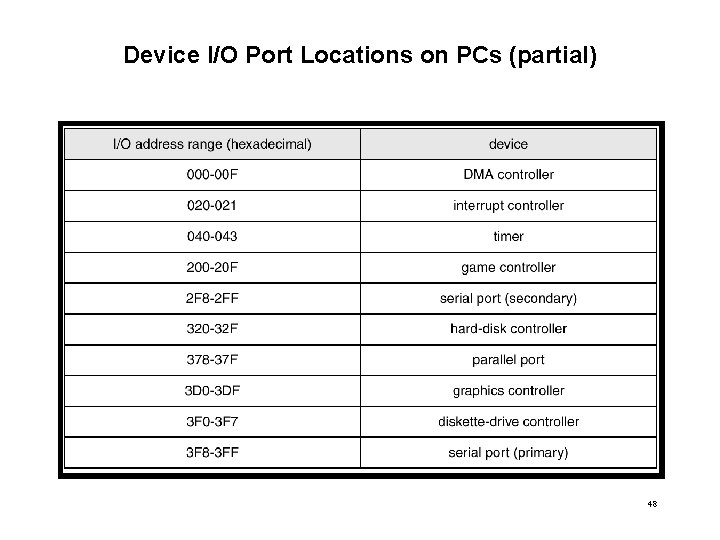
Device I/O Port Locations on PCs (partial) 48

Interrupts • CPU Interrupt request line triggered by I/O device • Interrupt handler receives interrupts • Maskable to ignore or delay some interrupts • Interrupt vector to dispatch interrupt to correct handler – Based on priority – Some unmaskable • Interrupt mechanism also used for exceptions 49

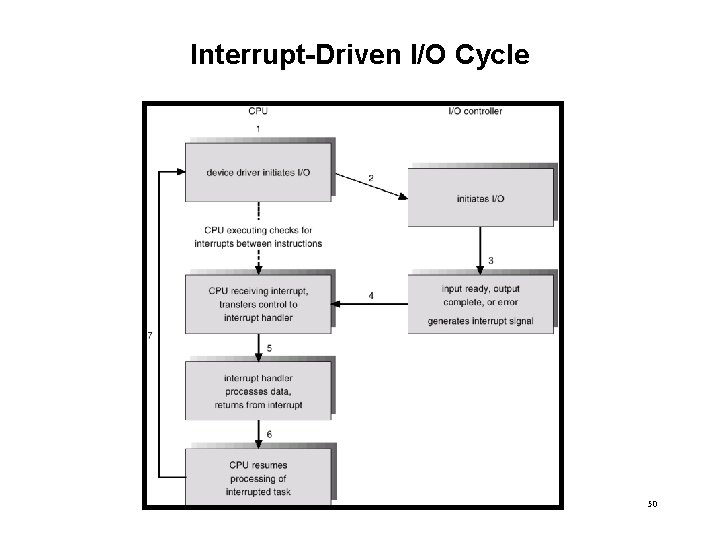
Interrupt-Driven I/O Cycle 50

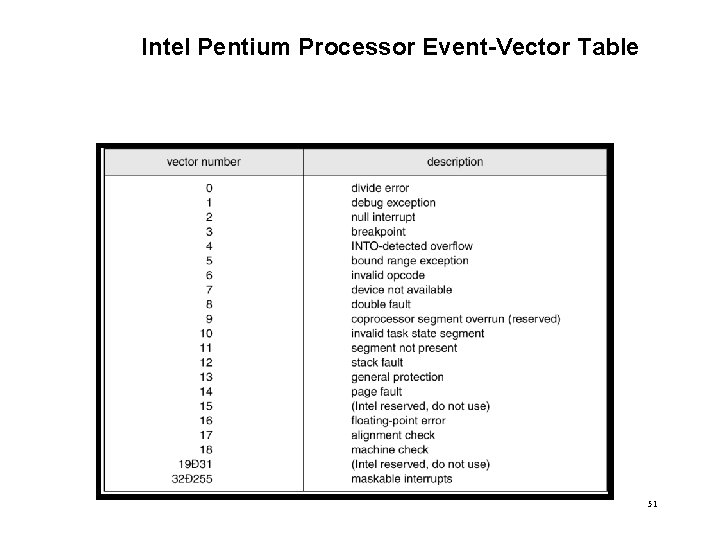
Intel Pentium Processor Event-Vector Table 51

Direct Memory Access • Used to avoid programmed I/O for large data movement • Requires DMA controller • Bypasses CPU to transfer data directly between I/O device and memory 52

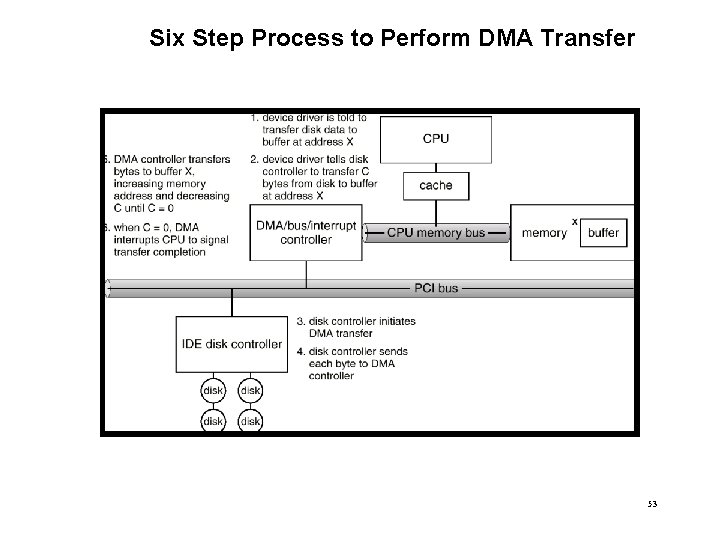
Six Step Process to Perform DMA Transfer 53

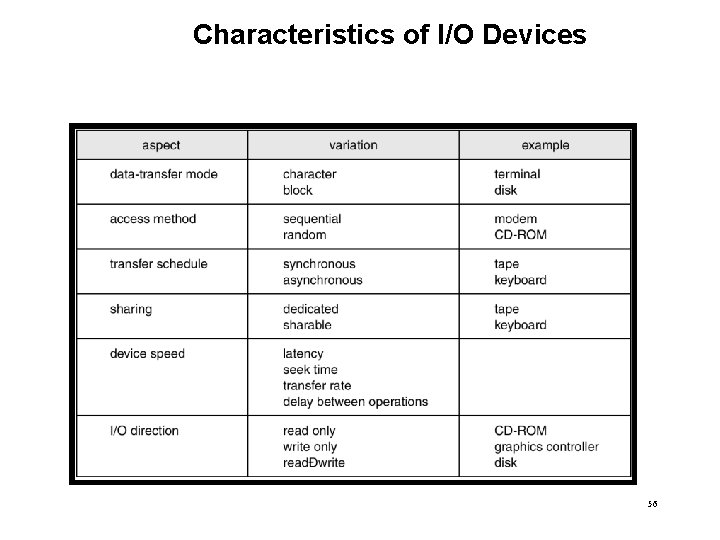
Application I/O Interface • I/O system calls encapsulate device behaviors in generic classes • Device-driver layer hides differences among I/O controllers from kernel • Devices vary in many dimensions – – – Character-stream or block Sequential or random-access Sharable or dedicated Speed of operation read-write, read only, or write only 54

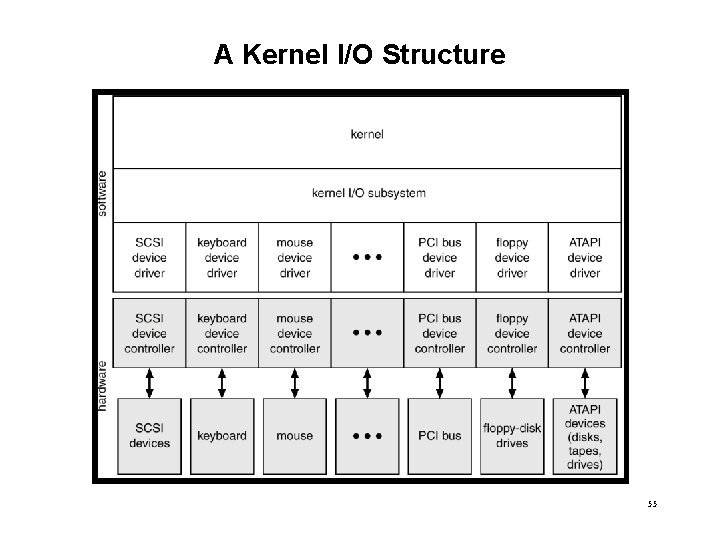
A Kernel I/O Structure 55

Characteristics of I/O Devices 56

Kernel I/O Subsystem • Scheduling – Some I/O request ordering via per-device queue – Some OSs try fairness • Buffering - store data in memory while transferring between devices – To cope with device speed mismatch – To cope with device transfer size mismatch – To maintain “copy semantics” 57

Kernel I/O Subsystem • Caching - fast memory holding copy of data – Always just a copy – Key to performance • Spooling - hold output for a device – If device can serve only one request at a time – i. e. , Printing • Device reservation - provides exclusive access to a device – System calls for allocation and deallocation – Watch out for deadlock 58

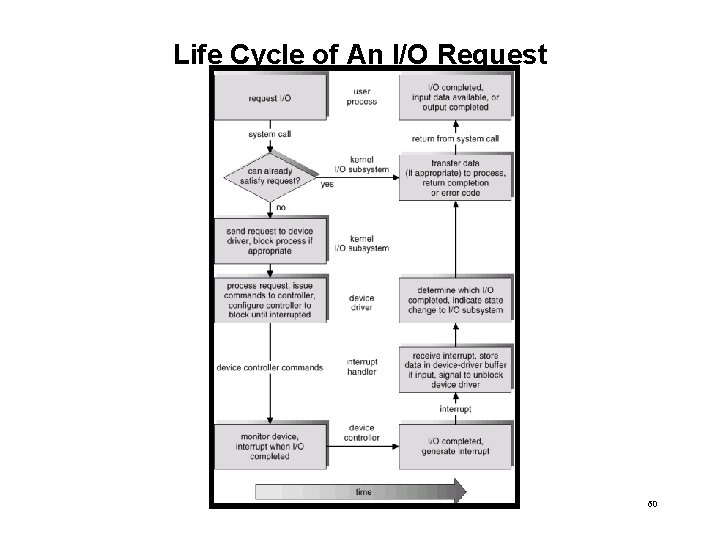
I/O Requests to Hardware Operations • Consider reading a file from disk for a process: – – – Determine device holding file Translate name to device representation Physically read data from disk into buffer Make data available to requesting process Return control to process 59

Life Cycle of An I/O Request 60

Performance • I/O a major factor in system performance: – – Demands CPU to execute device driver, kernel I/O code Context switches due to interrupts Data copying Network traffic especially stressful 61

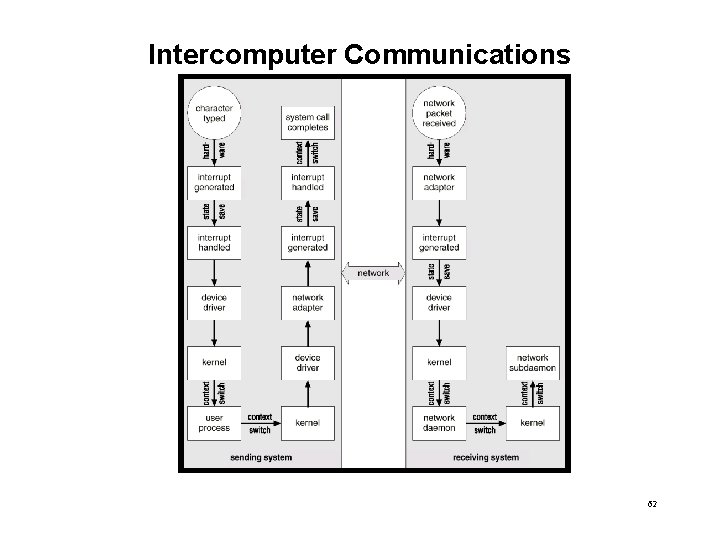
Intercomputer Communications 62

Improving Performance • Reduce number of context switches – Front End or other special purpose communications processor • Reduce data copying • Reduce interrupts by using large transfers, smart controllers, polling • Use DMA • Balance CPU, memory, bus, and I/O performance for highest throughput 63

OS COMPONENTS • Process Management • Memory Management (RAM) • Networking • File Management • I/O Management • Secondary/Tertiary Storage Management • Protection 64

COMPONENTS: Storage Management • Since main memory (primary storage) is volatile and too small to accommodate all data and programs permanently, the computer system must provide secondary storage to back up main memory. • Most modern computer systems use disks as the principle on-line storage medium, for both programs and data. • The operating system is responsible for the following activities in connection with disk management: – Disk free space management – Storage allocation – Disk scheduling 65

Mass-Storage Systems • Disk Structure • Disk Scheduling • Disk Management • Swap-Space Management • RAID Structure • Large Capacity Storage Systems 66

Disk Structure • Disk drives are addressed as large 1 -dimensional arrays of logical blocks, where the logical block is the smallest unit of transfer. • The 1 -dimensional array of logical blocks is mapped into the sectors of the disk sequentially. – Sector 0 is the first sector of the first track on the outermost cylinder. – Mapping proceeds in order through that track, then the rest of the tracks in that cylinder, and then through the rest of the cylinders from outermost to innermost. 67

Disk Scheduling • The operating system is responsible for using hardware efficiently — for the disk drives, this means having a fast access time and disk bandwidth. • Access time has two major components – Seek time is the time for the disk are to move the heads to the cylinder containing the desired sector. – Rotational latency is the additional time waiting for the disk to rotate the desired sector to the disk head. • Minimize seek time • Seek time seek distance • Disk bandwidth is the total number of bytes transferred, divided by the total time between the first request for service and the completion of the last transfer. 68

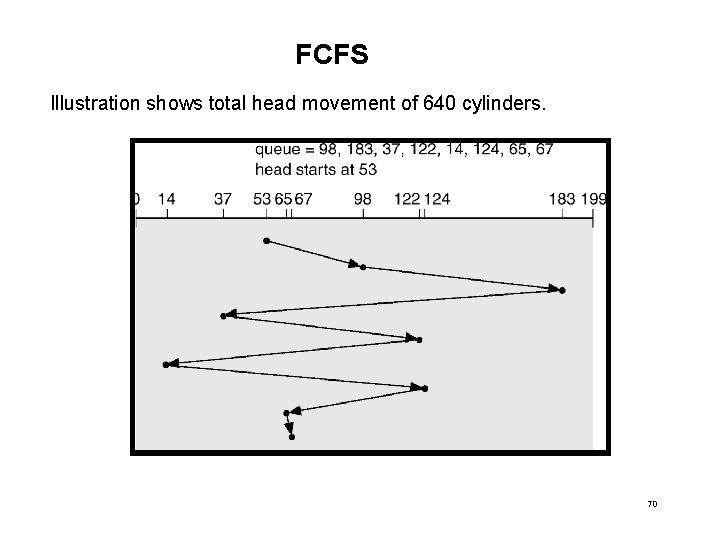
Disk Scheduling (Cont. ) • Several algorithms exist to schedule the servicing of disk I/O requests. • We illustrate them with a request queue (0 -199). 98, 183, 37, 122, 14, 124, 65, 67 Head pointer 53 69

FCFS Illustration shows total head movement of 640 cylinders. 70

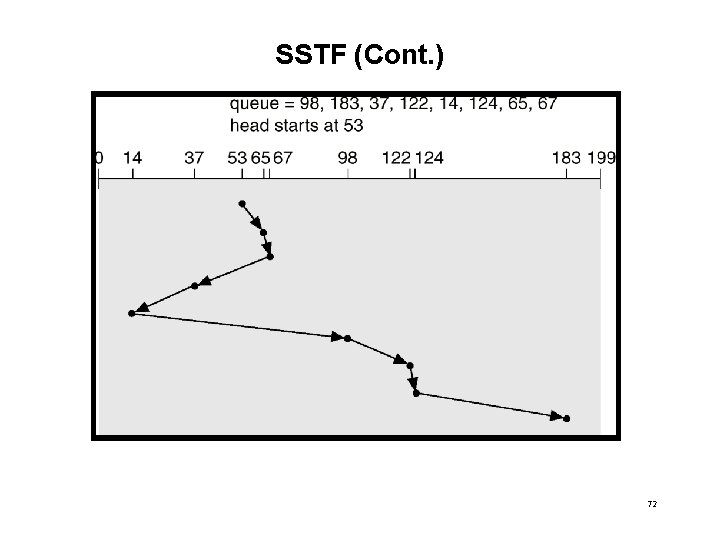
SSTF • Selects the request with the minimum seek time from the current head position. • SSTF scheduling is a form of SJF scheduling; may cause starvation of some requests. • Illustration shows total head movement of 236 cylinders. 71

SSTF (Cont. ) 72

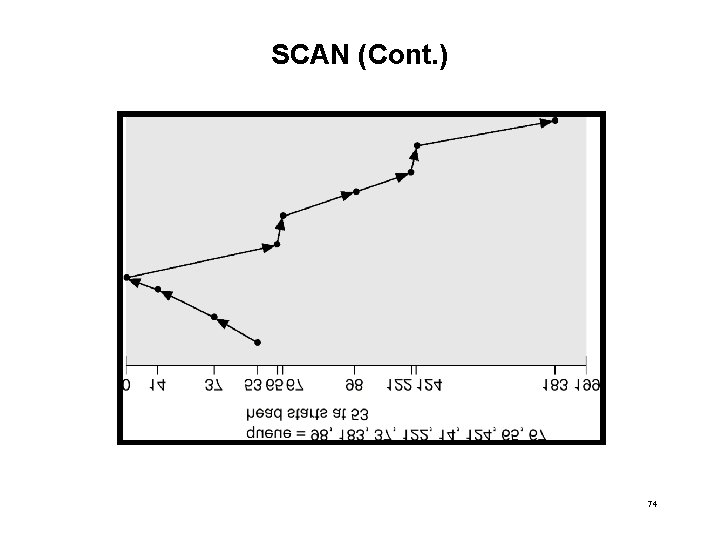
SCAN • The disk arm starts at one end of the disk, and moves toward the other end, servicing requests until it gets to the other end of the disk, where the head movement is reversed and servicing continues. • Sometimes called the elevator algorithm. • Illustration shows total head movement of 208 cylinders. 73

SCAN (Cont. ) 74

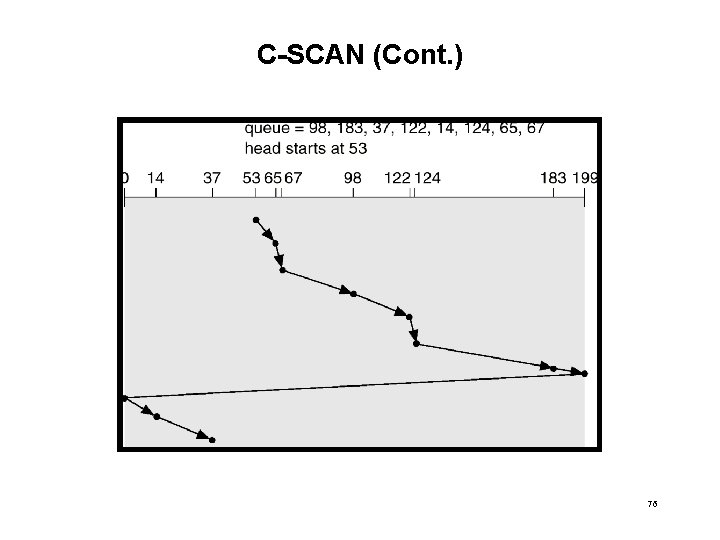
C-SCAN • Provides a more uniform wait time than SCAN. • The head moves from one end of the disk to the other. servicing requests as it goes. When it reaches the other end, however, it immediately returns to the beginning of the disk, without servicing any requests on the return trip. • Treats the cylinders as a circular list that wraps around from the last cylinder to the first one. 75

C-SCAN (Cont. ) 76

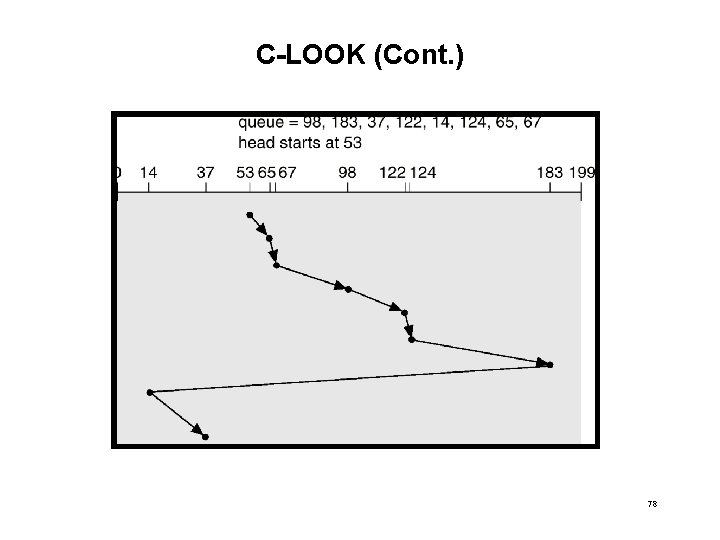
C-LOOK • Version of C-SCAN • Arm only goes as far as the last request in each direction, then reverses direction immediately, without first going all the way to the end of the disk. 77

C-LOOK (Cont. ) 78

Selecting a Disk-Scheduling Algorithm • SSTF is common and has a natural appeal • SCAN and C-SCAN perform better for systems that place a heavy load on the disk. • Performance depends on the number and types of requests. • Requests for disk service can be influenced by the file -allocation method. • The disk-scheduling algorithm should be written as a separate module of the operating system, allowing it to be replaced with a different algorithm if necessary. • Either SSTF or LOOK is a reasonable choice for the default algorithm. 79

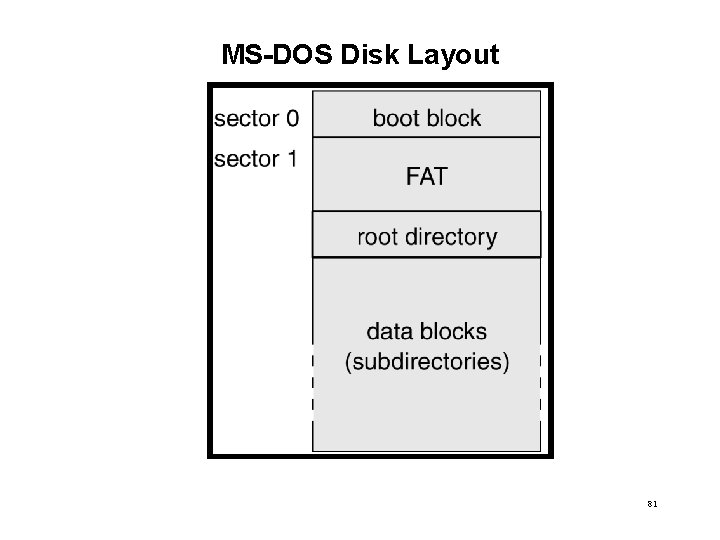
Disk Management • Low-level formatting, or physical formatting — Dividing a disk into sectors that the disk controller can read and write. • To use a disk to hold files, the operating system still needs to record its own data structures on the disk. – Partition the disk into one or more groups of cylinders. – Logical formatting or “making a file system”. • Boot block initializes system. – The bootstrap is stored in ROM. – Bootstrap loader program. • Methods such as sector sparing used to handle bad blocks. 80

MS-DOS Disk Layout 81

Swap-Space Management • Swap-space — Virtual memory uses disk space as an extension of main memory. • Swap-space can be carved out of the normal file system, or, more commonly, it can be in a separate disk partition. 82

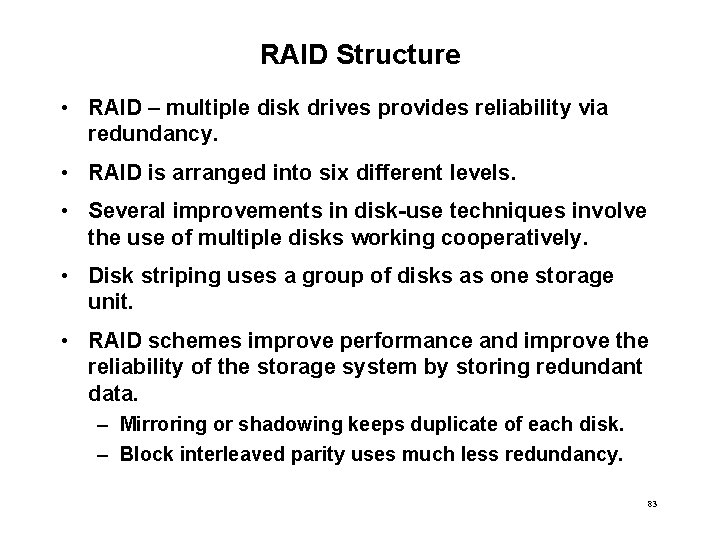
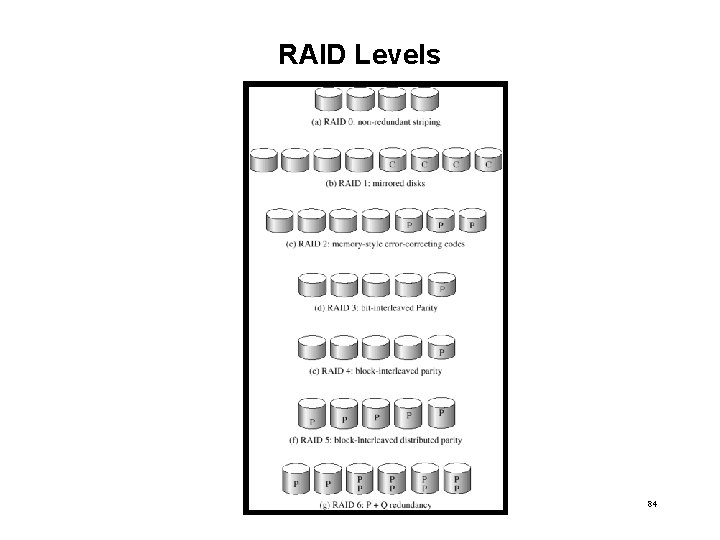
RAID Structure • RAID – multiple disk drives provides reliability via redundancy. • RAID is arranged into six different levels. • Several improvements in disk-use techniques involve the use of multiple disks working cooperatively. • Disk striping uses a group of disks as one storage unit. • RAID schemes improve performance and improve the reliability of the storage system by storing redundant data. – Mirroring or shadowing keeps duplicate of each disk. – Block interleaved parity uses much less redundancy. 83

RAID Levels 84

Network-Attached Storage 85

Storage-Area Network 86

OS COMPONENTS • Process Management • Memory Management (RAM) • Networking • File Management • I/O Management • Secondary/Tertiary Storage Management • Protection 87

OS COMPONENTS: Protection • Protection refers to a mechanism for controlling access by programs, processes, or users to both system and user resources. • The OS through its protection mechanisms must: – distinguish between authorized and unauthorized usage. – specify the security controls to be imposed on system resources. – provide a means of enforcement. 88