OSP 431 Security Design with Claims Based Authentication


OSP 431 Security Design with Claims. Based Authentication Israel Vega, Nathan Miller



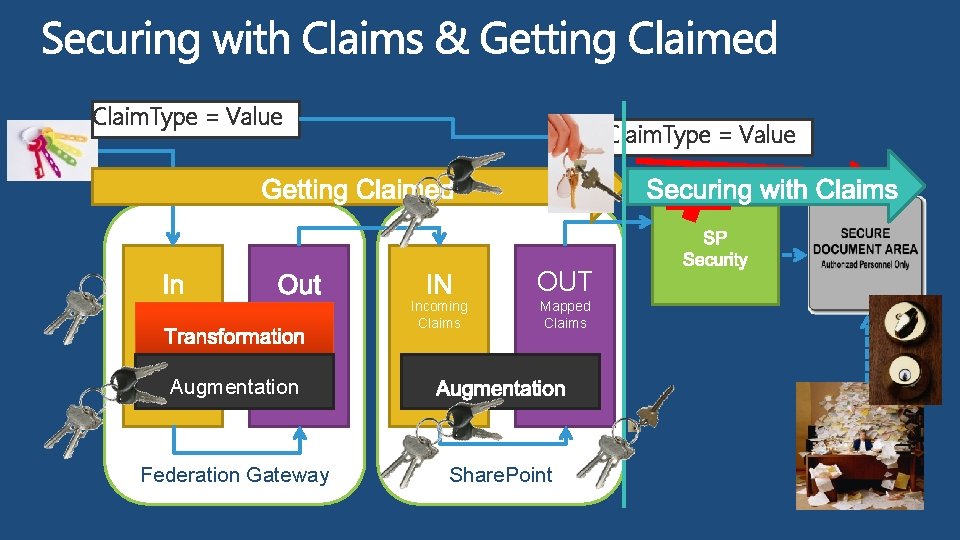
Claim. Type = Value OUT Incoming Claims Mapped Claims Augmentation Federation Gateway Share. Point


Key Point: Federation relationships are based on trust
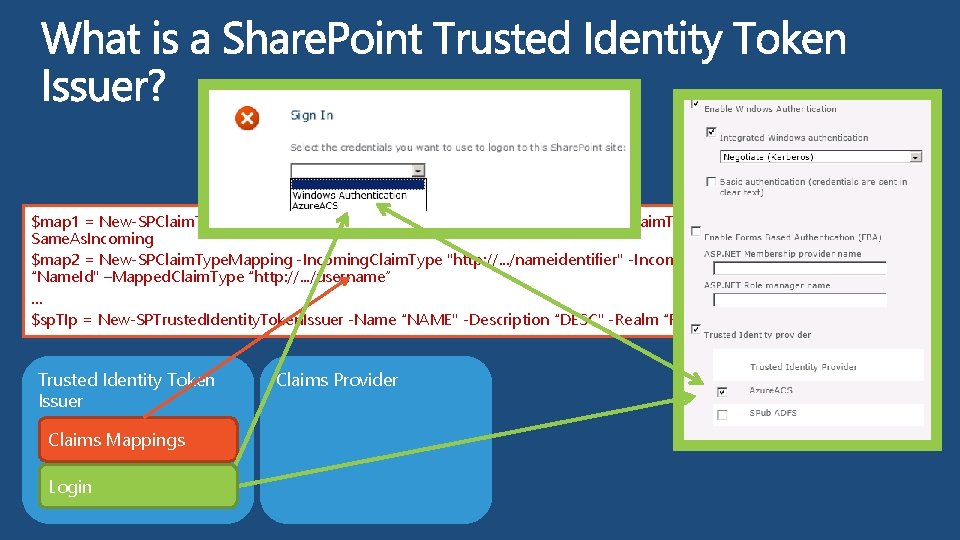
$map 1 = New-SPClaim. Type. Mapping -Incoming. Claim. Type "http: //. . . /upn" -Incoming. Claim. Type. Display. Name "UPN" Same. As. Incoming $map 2 = New-SPClaim. Type. Mapping -Incoming. Claim. Type "http: //. . . /nameidentifier" -Incoming. Claim. Type. Display. Name “Name. Id" –Mapped. Claim. Type “http: //. . . /username” … $sp. TIp = New-SPTrusted. Identity. Token. Issuer -Name “NAME" -Description “DESC" -Realm “REALM” -Claims. Mappings $map 1 …" Trusted Identity Token Issuer Claims Mappings Login Claims Provider
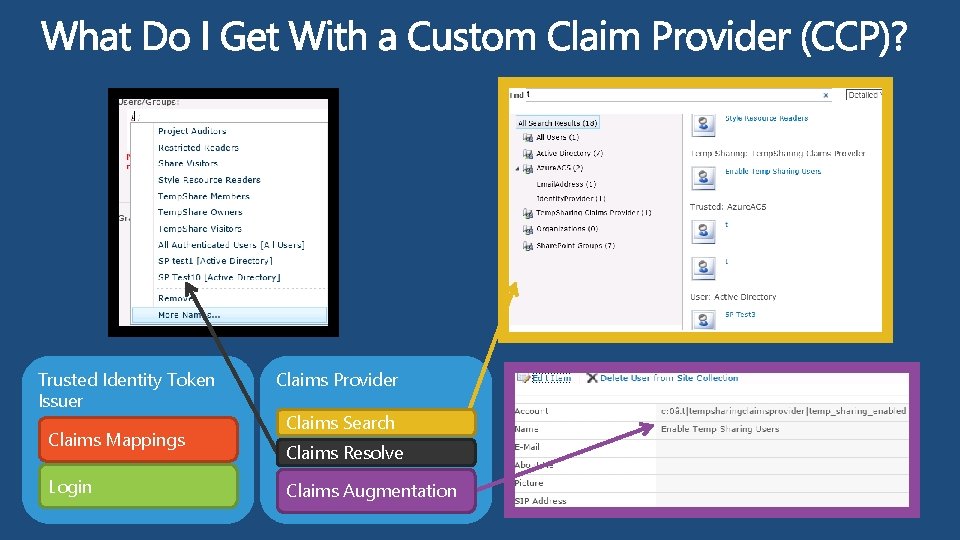
Trusted Identity Token Issuer Claims Mappings Login Claims Provider Claims Search Claims Resolve Claims Augmentation
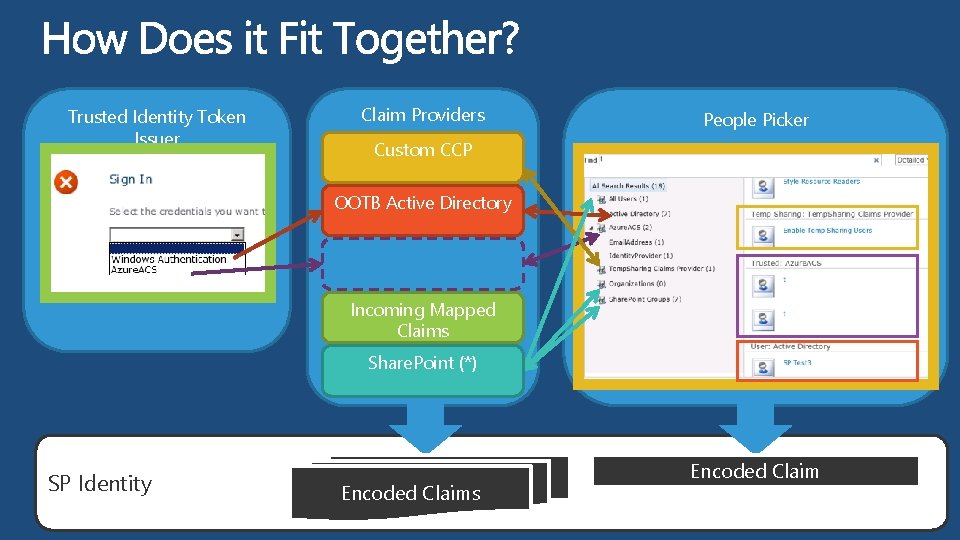
Trusted Identity Token Issuer Claim Providers People Picker Custom CCP OOTB Active Directory Incoming Mapped Claims Share. Point (*) SP Identity Encoded Claims Encoded Claim
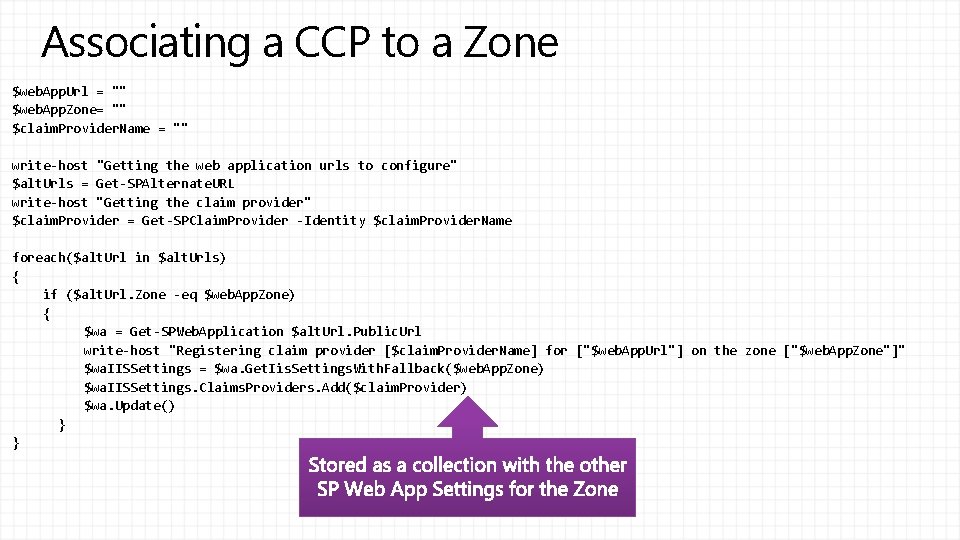
Associating a CCP to a Zone $web. App. Url = "" $web. App. Zone= "" $claim. Provider. Name = "" write-host "Getting the web application urls to configure" $alt. Urls = Get-SPAlternate. URL write-host "Getting the claim provider" $claim. Provider = Get-SPClaim. Provider -Identity $claim. Provider. Name foreach($alt. Url in $alt. Urls) { if ($alt. Url. Zone -eq $web. App. Zone) { $wa = Get-SPWeb. Application $alt. Url. Public. Url write-host "Registering claim provider [$claim. Provider. Name] for ["$web. App. Url"] on the zone ["$web. App. Zone"]" $wa. IISSettings = $wa. Get. Iis. Settings. With. Fallback($web. App. Zone) $wa. IISSettings. Claims. Providers. Add($claim. Provider) $wa. Update() } }
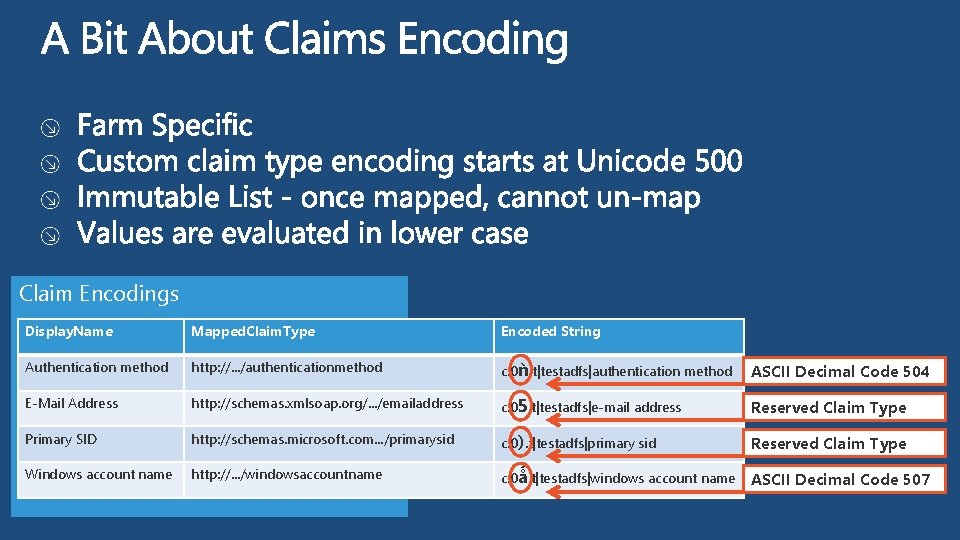
Claim Encodings Display. Name Mapped. Claim. Type Encoded String Authentication method http: //. . . /authenticationmethod c: 0ǹ. t|testadfs|authentication method ASCII Decimal Code 504 E-Mail Address http: //schemas. xmlsoap. org/. . . /emailaddress c: 05. t|testadfs|e-mail address Reserved Claim Type Primary SID http: //schemas. microsoft. com. . . /primarysid c: 0). t|testadfs|primary sid Reserved Claim Type Windows account name http: //. . . /windowsaccountname c: 0ǻ. t|testadfs|windows account name ASCII Decimal Code 507
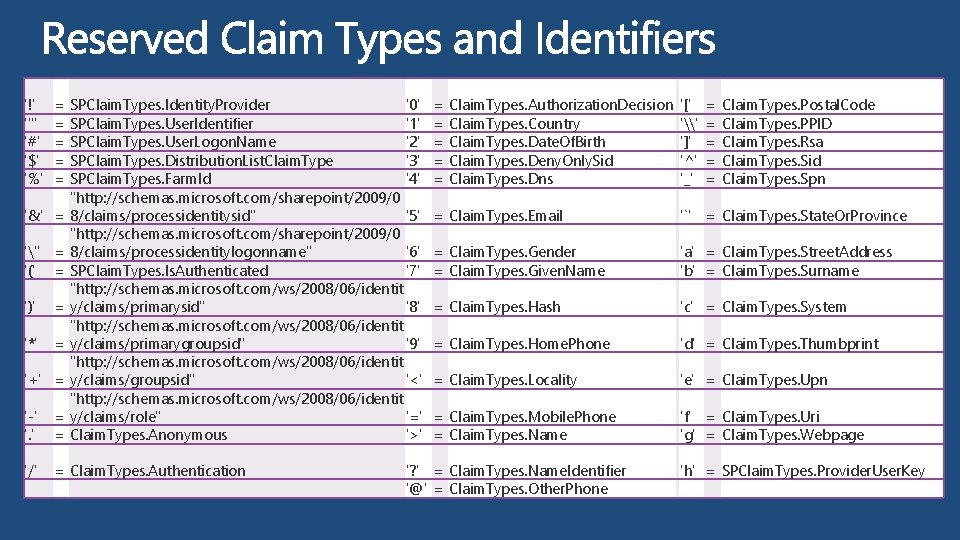
'!' '"' '#' '$' '%' = = = '&' = ''' = '(' = ')' = '*' = '+' = SPClaim. Types. Identity. Provider '0' SPClaim. Types. User. Identifier '1' SPClaim. Types. User. Logon. Name '2' SPClaim. Types. Distribution. List. Claim. Type '3' SPClaim. Types. Farm. Id '4' "http: //schemas. microsoft. com/sharepoint/2009/0 8/claims/processidentitysid" '5' "http: //schemas. microsoft. com/sharepoint/2009/0 8/claims/processidentitylogonname" '6' SPClaim. Types. Is. Authenticated '7' "http: //schemas. microsoft. com/ws/2008/06/identit y/claims/primarysid" '8' "http: //schemas. microsoft. com/ws/2008/06/identit y/claims/primarygroupsid" '9' "http: //schemas. microsoft. com/ws/2008/06/identit y/claims/groupsid" '<' "http: //schemas. microsoft. com/ws/2008/06/identit y/claims/role" '=' Claim. Types. Anonymous '>' '-' '. ' = = '/' = Claim. Types. Authentication = = = Claim. Types. Authorization. Decision Claim. Types. Country Claim. Types. Date. Of. Birth Claim. Types. Deny. Only. Sid Claim. Types. Dns '[' '\' ']' '^' '_' = = = Claim. Types. Postal. Code Claim. Types. PPID Claim. Types. Rsa Claim. Types. Sid Claim. Types. Spn = Claim. Types. Email '`' = Claim. Types. State. Or. Province = Claim. Types. Gender = Claim. Types. Given. Name 'a' = Claim. Types. Street. Address 'b' = Claim. Types. Surname = Claim. Types. Hash 'c' = Claim. Types. System = Claim. Types. Home. Phone 'd' = Claim. Types. Thumbprint = Claim. Types. Locality 'e' = Claim. Types. Upn = Claim. Types. Mobile. Phone = Claim. Types. Name 'f' = Claim. Types. Uri 'g' = Claim. Types. Webpage '? ' = Claim. Types. Name. Identifier '@' = Claim. Types. Other. Phone 'h' = SPClaim. Types. Provider. User. Key

Trusted Provider CCP Search CCP Resolve CCP Augmentation
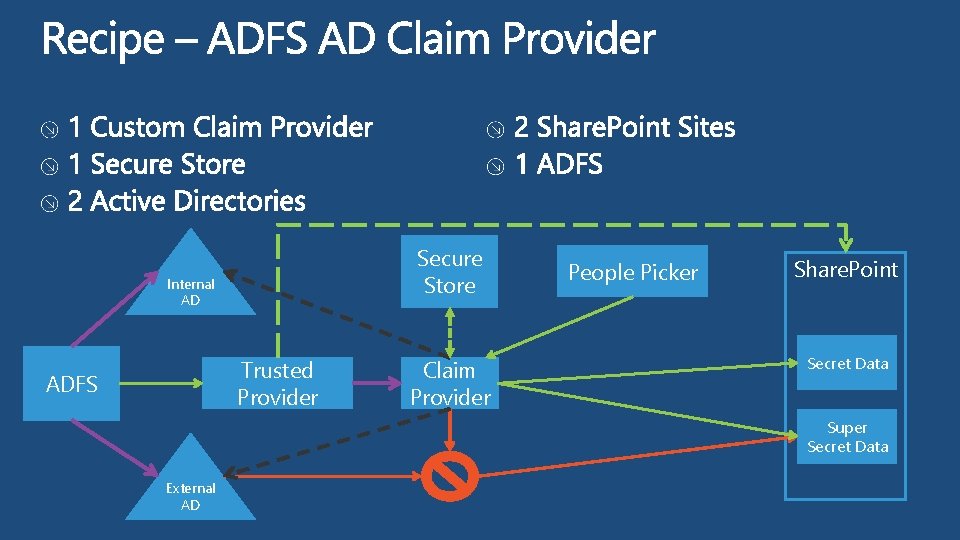
Secure Store Internal AD Trusted Provider ADFS Claim Provider People Picker Share. Point Secret Data Super Secret Data External AD

Demo ADFS/AD Claim Provider Nephophobia (cloud fear, cloud phobia, fear of clouds, phobia of clouds)
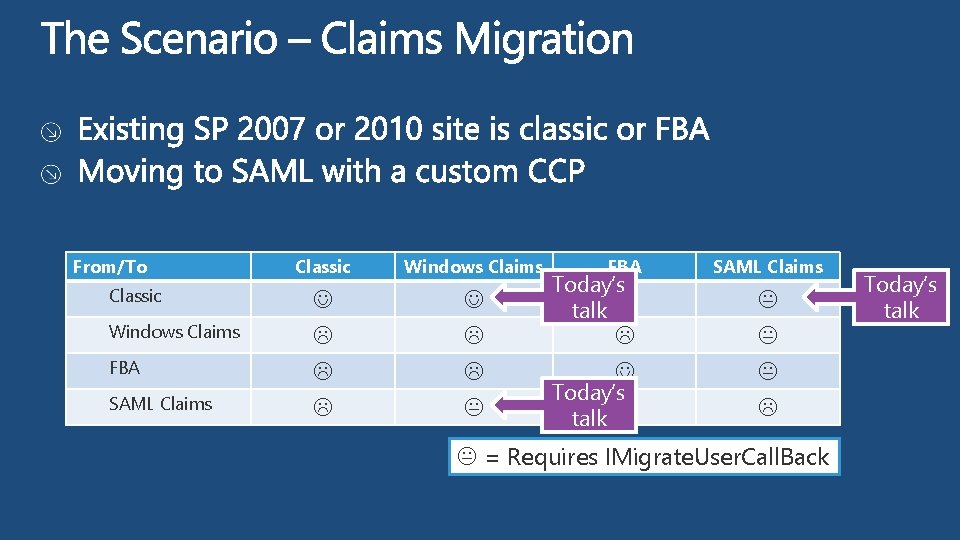
From/To Classic Windows Claims FBA SAML Claims Classic Windows Claims FBA Today’s talk SAML Claims = Requires IMigrate. User. Call. Back Today’s talk
Code Snippets Claims Migration Scenarios The penguin is the only bird who can swim, but cannot fly
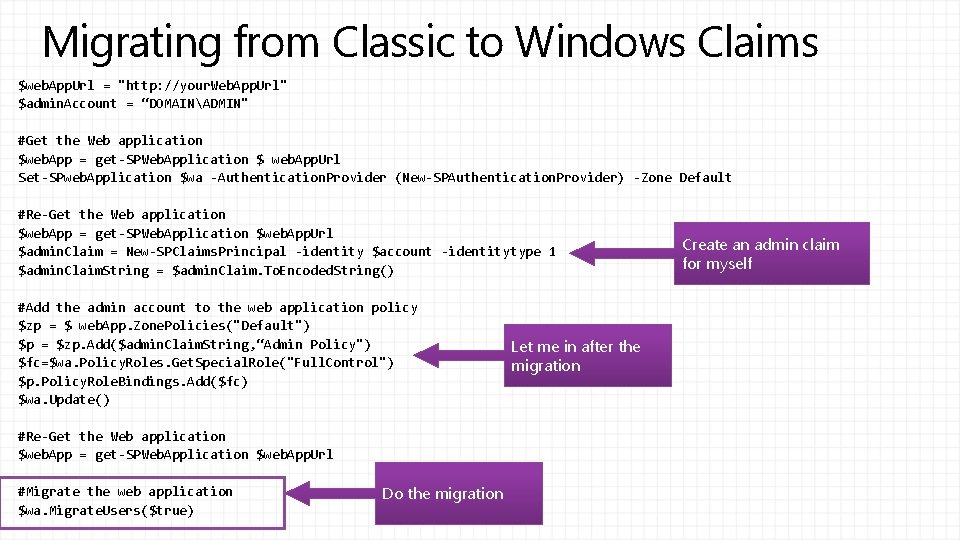
Migrating from Classic to Windows Claims $web. App. Url = "http: //your. Web. App. Url" $admin. Account = “DOMAINADMIN" #Get the Web application $web. App = get-SPWeb. Application $ web. App. Url Set-SPweb. Application $wa -Authentication. Provider (New-SPAuthentication. Provider) -Zone Default #Re-Get the Web application $web. App = get-SPWeb. Application $web. App. Url $admin. Claim = New-SPClaims. Principal -identity $account -identitytype 1 $admin. Claim. String = $admin. Claim. To. Encoded. String() #Add the admin account to the web application policy $zp = $ web. App. Zone. Policies("Default") $p = $zp. Add($admin. Claim. String, “Admin Policy") $fc=$wa. Policy. Roles. Get. Special. Role("Full. Control") $p. Policy. Role. Bindings. Add($fc) $wa. Update() #Re-Get the Web application $web. App = get-SPWeb. Application $web. App. Url #Migrate the web application $wa. Migrate. Users($true) Do the migration Let me in after the migration Create an admin claim for myself
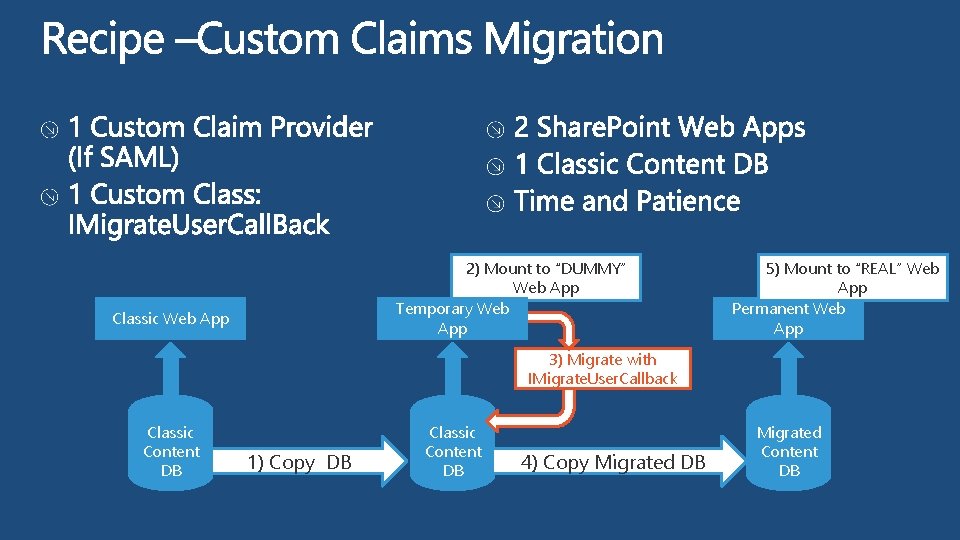
2) Mount to “DUMMY” Web App Temporary Web App Classic Web App 5) Mount to “REAL” Web App Permanent Web App 3) Migrate with IMigrate. User. Callback Classic Content DB 1) Copy DB Classic Content DB 4) Copy Migrated DB Migrated Content DB
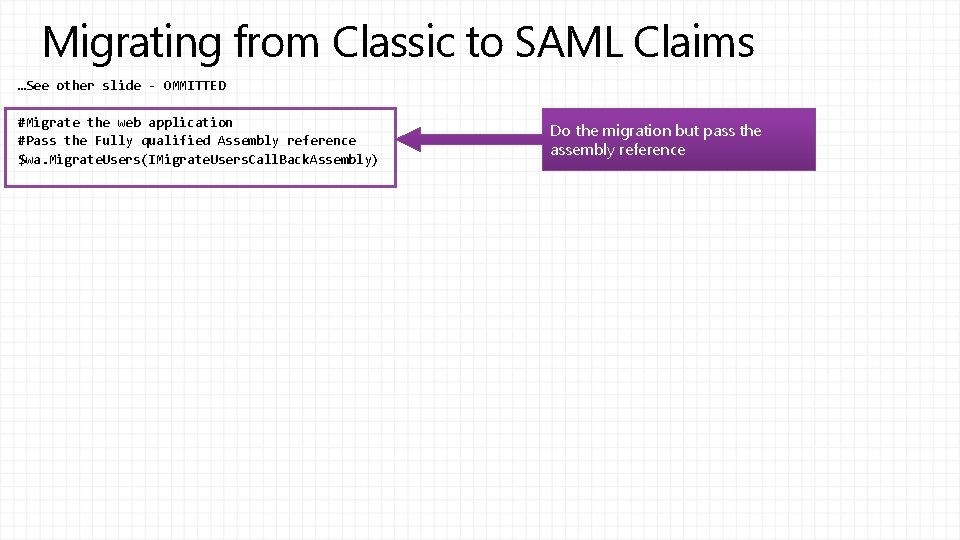
Migrating from Classic to SAML Claims …See other slide - OMMITTED #Migrate the web application #Pass the Fully qualified Assembly reference $wa. Migrate. Users(IMigrate. Users. Call. Back. Assembly) Do the migration but pass the assembly reference
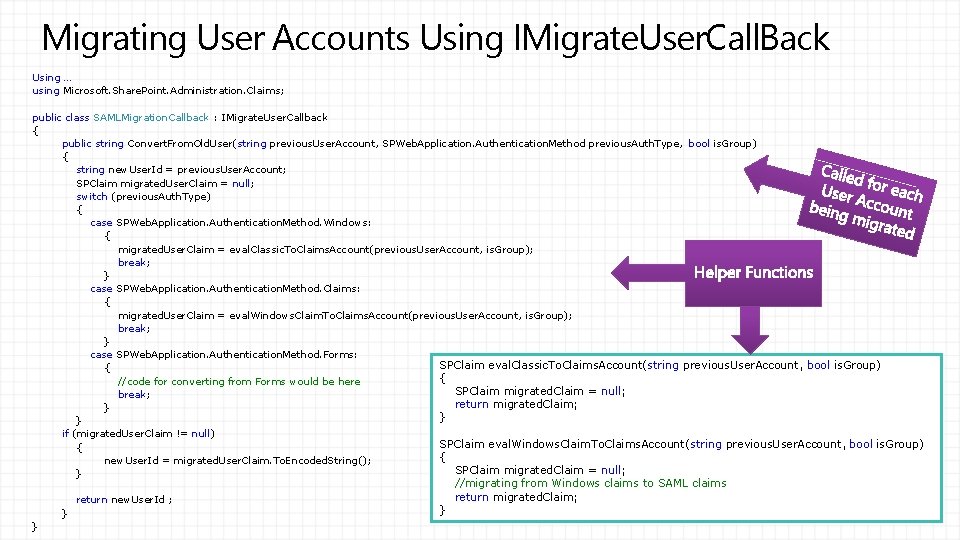
Migrating User Accounts Using IMigrate. User. Call. Back Using … using Microsoft. Share. Point. Administration. Claims; public class SAMLMigration. Callback : IMigrate. User. Callback { public string Convert. From. Old. User(string previous. User. Account, SPWeb. Application. Authentication. Method previous. Auth. Type, bool is. Group) { string new. User. Id = previous. User. Account; SPClaim migrated. User. Claim = null; switch (previous. Auth. Type) { case SPWeb. Application. Authentication. Method. Windows: { migrated. User. Claim = eval. Classic. To. Claims. Account(previous. User. Account, is. Group); break; } case SPWeb. Application. Authentication. Method. Claims: { migrated. User. Claim = eval. Windows. Claim. To. Claims. Account(previous. User. Account, is. Group); break; } case SPWeb. Application. Authentication. Method. Forms: SPClaim eval. Classic. To. Claims. Account(string previous. User. Account, bool is. Group) { { //code for converting from Forms would be here SPClaim migrated. Claim = null; break; return migrated. Claim; } } } if (migrated. User. Claim != null) SPClaim eval. Windows. Claim. To. Claims. Account(string previous. User. Account, bool is. Group) { { new. User. Id = migrated. User. Claim. To. Encoded. String(); SPClaim migrated. Claim = null; } return new. User. Id ; } } } //migrating from Windows claims to SAML claims return migrated. Claim;
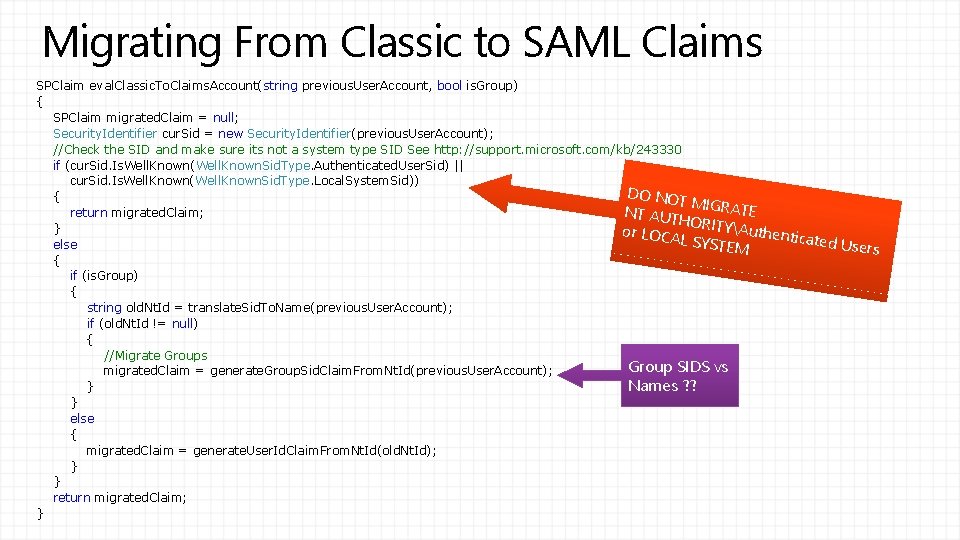
Migrating From Classic to SAML Claims SPClaim eval. Classic. To. Claims. Account(string previous. User. Account, bool is. Group) { SPClaim migrated. Claim = null; Security. Identifier cur. Sid = new Security. Identifier(previous. User. Account); //Check the SID and make sure its not a system type SID See http: //support. microsoft. com/kb/243330 if (cur. Sid. Is. Well. Known(Well. Known. Sid. Type. Authenticated. User. Sid) || cur. Sid. Is. Well. Known(Well. Known. Sid. Type. Local. System. Sid)) DO NOT { MIGRAT E return migrated. Claim; NT AUT H O R I T Y } Authen or LOCA ticated L S Y else STEM { if (is. Group) { string old. Nt. Id = translate. Sid. To. Name(previous. User. Account); if (old. Nt. Id != null) { //Migrate Groups Group SIDS vs migrated. Claim = generate. Group. Sid. Claim. From. Nt. Id(previous. User. Account); Names ? ? } } else { migrated. Claim = generate. User. Id. Claim. From. Nt. Id(old. Nt. Id); } } return migrated. Claim; } Users
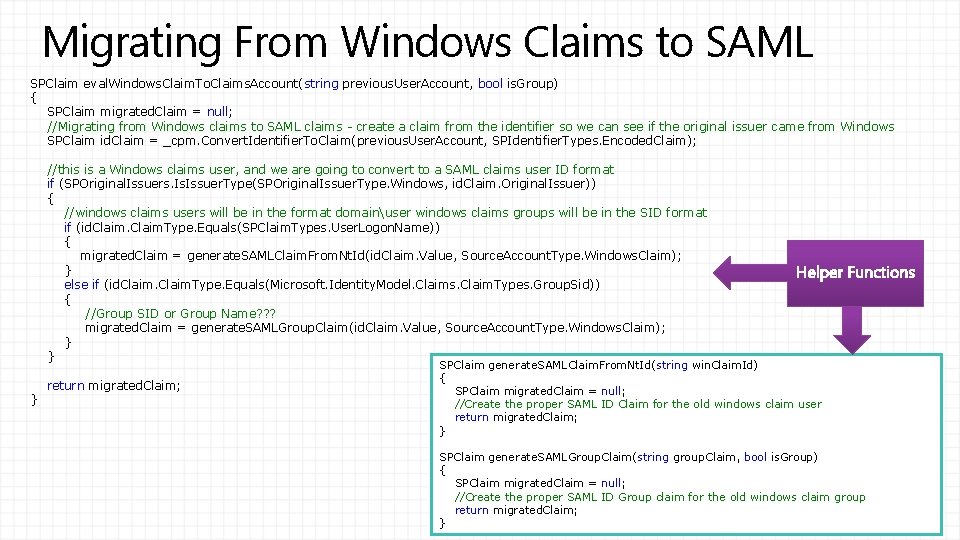
Migrating From Windows Claims to SAML SPClaim eval. Windows. Claim. To. Claims. Account(string previous. User. Account, bool is. Group) { SPClaim migrated. Claim = null; //Migrating from Windows claims to SAML claims - create a claim from the identifier so we can see if the original issuer came from Windows SPClaim id. Claim = _cpm. Convert. Identifier. To. Claim(previous. User. Account, SPIdentifier. Types. Encoded. Claim); //this is a Windows claims user, and we are going to convert to a SAML claims user ID format if (SPOriginal. Issuers. Issuer. Type(SPOriginal. Issuer. Type. Windows, id. Claim. Original. Issuer)) { //windows claims users will be in the format domainuser windows claims groups will be in the SID format if (id. Claim. Type. Equals(SPClaim. Types. User. Logon. Name)) { migrated. Claim = generate. SAMLClaim. From. Nt. Id(id. Claim. Value, Source. Account. Type. Windows. Claim); } else if (id. Claim. Type. Equals(Microsoft. Identity. Model. Claims. Claim. Types. Group. Sid)) { //Group SID or Group Name? ? ? migrated. Claim = generate. SAMLGroup. Claim(id. Claim. Value, Source. Account. Type. Windows. Claim); } } } return migrated. Claim; SPClaim generate. SAMLClaim. From. Nt. Id(string win. Claim. Id) { SPClaim migrated. Claim = null; //Create the proper SAML ID Claim for the old windows claim user return migrated. Claim; } SPClaim generate. SAMLGroup. Claim(string group. Claim, bool is. Group) { SPClaim migrated. Claim = null; //Create the proper SAML ID Group claim for the old windows claim group return migrated. Claim; }
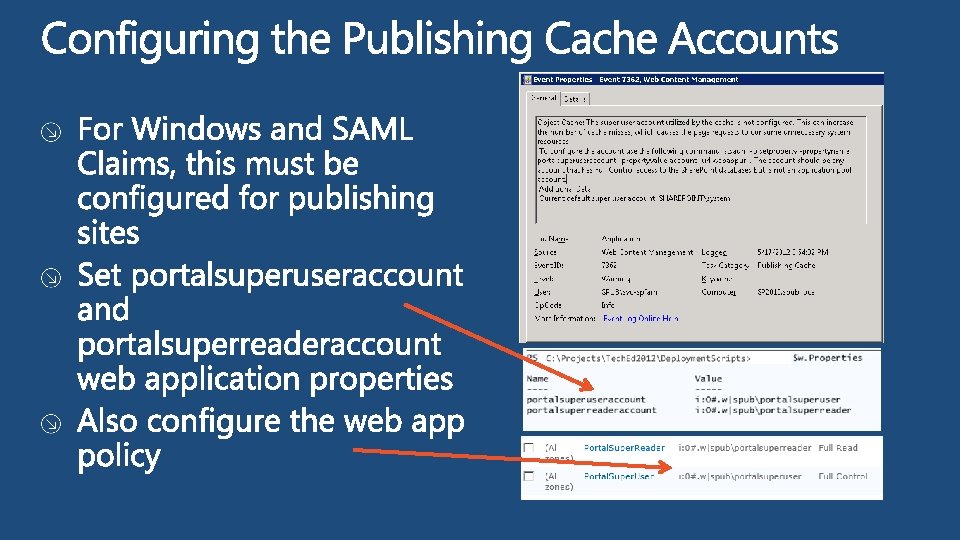
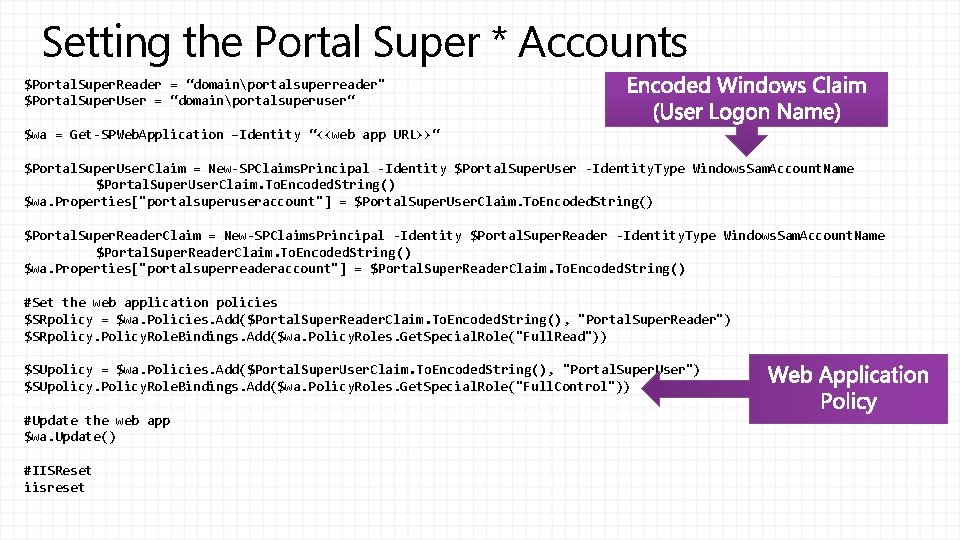
Setting the Portal Super * Accounts $Portal. Super. Reader = “domainportalsuperreader" $Portal. Super. User = “domainportalsuperuser“ $wa = Get-SPWeb. Application –Identity “<<web app URL>>“ $Portal. Super. User. Claim = New-SPClaims. Principal -Identity $Portal. Super. User -Identity. Type Windows. Sam. Account. Name $Portal. Super. User. Claim. To. Encoded. String() $wa. Properties["portalsuperuseraccount"] = $Portal. Super. User. Claim. To. Encoded. String() $Portal. Super. Reader. Claim = New-SPClaims. Principal -Identity $Portal. Super. Reader -Identity. Type Windows. Sam. Account. Name $Portal. Super. Reader. Claim. To. Encoded. String() $wa. Properties["portalsuperreaderaccount"] = $Portal. Super. Reader. Claim. To. Encoded. String() #Set the web application policies $SRpolicy = $wa. Policies. Add($Portal. Super. Reader. Claim. To. Encoded. String(), "Portal. Super. Reader") $SRpolicy. Policy. Role. Bindings. Add($wa. Policy. Roles. Get. Special. Role("Full. Read")) $SUpolicy = $wa. Policies. Add($Portal. Super. User. Claim. To. Encoded. String(), "Portal. Super. User") $SUpolicy. Policy. Role. Bindings. Add($wa. Policy. Roles. Get. Special. Role("Full. Control")) #Update the web app $wa. Update() #IISReset iisreset
Fun with Claims The value of Claims Based Auth. N and Auth. Z Reindeers like to eat bananas

Trusted Provider CCP Search CCP Resolve CCP Augmentation
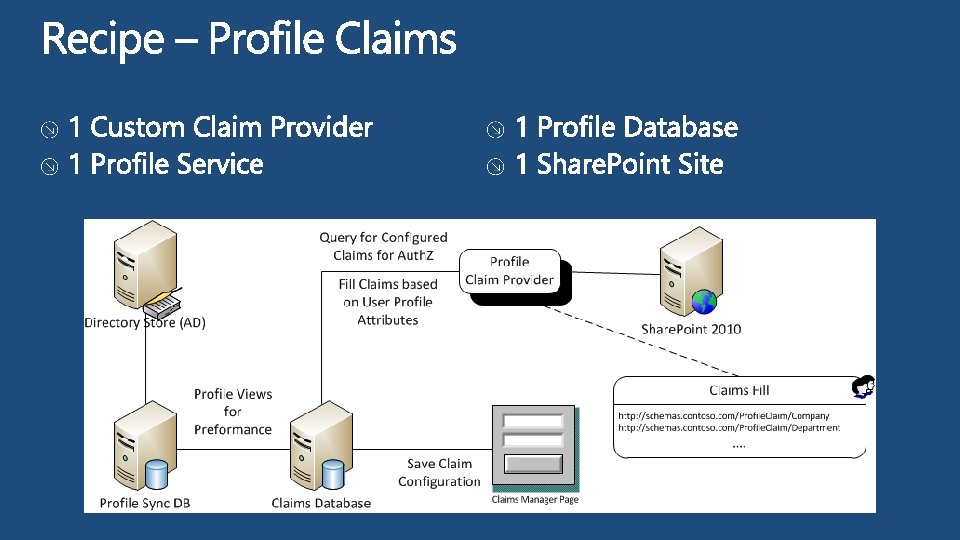
Profile Claim Provider It is possible to lead a cow upstairs but not upstairs

Trusted Provider CCP Search CCP Resolve CCP Augmentation
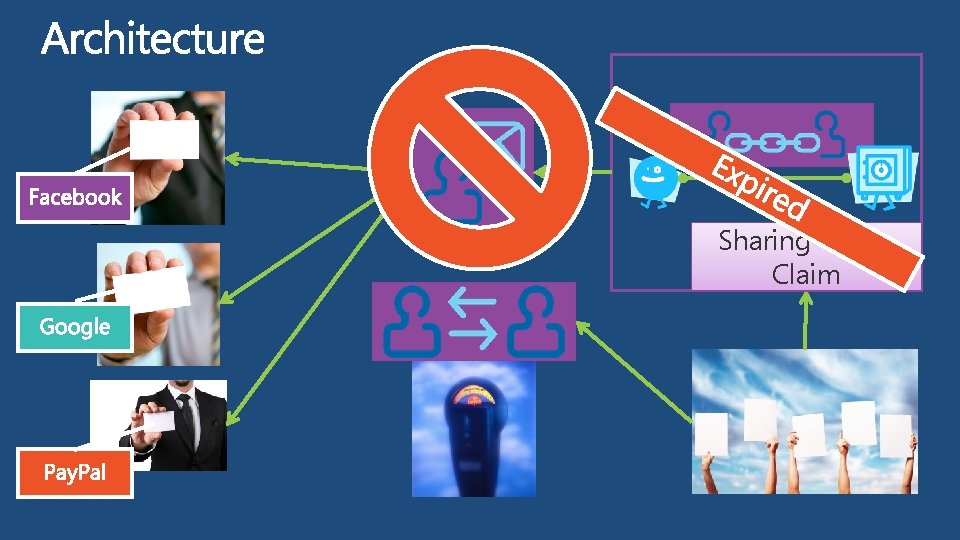
Sharing Token Claim


Demo Temp. Share Claim Provider The sentence "The quick brown fox jumps over a lazy dog. " uses every letter of the alphabet!

* http: //blogs. technet. com/b/speschka/archive/2011/03/29/how-to-get-all-user-claims-at-claims-augmentation-time-insharepoint-2010. aspx


AZR 78 -HOL | Introduction to Access Control Service SIA 01 -TLC | Microsoft Identity and Access Find us later at: Share. Point TLC Booth Ask the Experts
http: //blogs. msdn. com/entdev - Demo code http: //blogs. technet. com/b/speschka/ - Share. Point CBA Resources

Learning Connect. Share. Discuss. Microsoft Certification & Training Resources http: //europe. msteched. com www. microsoft. com/learning Tech. Net Resources for IT Professionals Resources for Developers http: //microsoft. com/technet http: //microsoft. com/msdn

Evaluations Submit your evals online http: //europe. msteched. com/sessions

- Slides: 44