OS System Attack InjectionDirectory TraversalRaceTruncate Error attacks Notes










- Slides: 15

OS System Attack: Injection/Directory Traversal/Race/Truncate Error attacks Notes on these slides are primarily from: slides provided with the textbook: Foundations of Security: Neil Daswani et al. ©Neil Daswani , ISBN-13: 978 -1590597842. This is a recommended textbook for the course. MAWC – Radford University 2010

Input size validation is good, but not enough … • Input size validation against Buffer Overflow Attack • Need to also validate “type” of input. • Just validating the size isn’t enough!! • Examples (next): OS injection; HTTP injection (incl. form-tampering), SQL injection; . MAWC – Radford University 2010

"Injection" Often, one program generates a string that is later run as code by others: - A program that generates html. - A GUI interface generates a "scp" command. - A program that generates database queries. If any of these programs accept userinput and splice it into the string, then (when that string is later run as code) shenanigans may ensue. MAWC – Radford University 2010

OS Command Injection See next slide: Touch. java: • Ask the user for a filename $fname. • Create a string "touch ~/tmp/" + $fname and write string to a file (script). • Ask the OS to run that shell-script. Script thinks the file will be inside tmp/. But a clever user can circumvent! What happen if user type the following: junk 1. txt; rm junk*. txt; echo You got hacked! Even worse: hacker may delete all your files using: junk 1. txt; rm –R ~ Defense Measure: check input data type – not allow to enter ‘; ’ character MAWC – Radford University 2010

Touch. java import java. io. *; /** A program to illustrate system-call injection, * from user input. */ class Touch { final static private String BASE_DIR = "/home/cshing/tmp/"; final static private String SCRIPT_NAME = "foo. sh "; public static void main( String[] _ ) throws java. io. IOException { System. out. println( "What file inside " + BASE_DIR + " do you want to update? " ); String fname = new java. util. Scanner( System. in ). next. Line (); String command = "touch " + BASE_DIR + fname; System. out. println( "About to execute: `" + command + "`"); run. As. Shell. Script( command ); } static void run. As. Shell. Script( String cmd ) throws java. io. IOException { File. Writer script. Writer = new File. Writer( new File( SCRIPT_NAME ) ); script. Writer. write( "#! /bin/shn" ); script. Writer. write( cmd + "n" ); script. Writer. close(); Runtime. get. Runtime(). exec( "chmod u+x " + SCRIPT_NAME ); Runtime. get. Runtime(). exec( SCRIPT_NAME ); // N. B. Any output gets sent to the *exec*'s stdout, not our stdout. } } foo. sh: #! /bin/sh touch /home/cshing/tmp/junk 1 MAWC – Radford University 2010

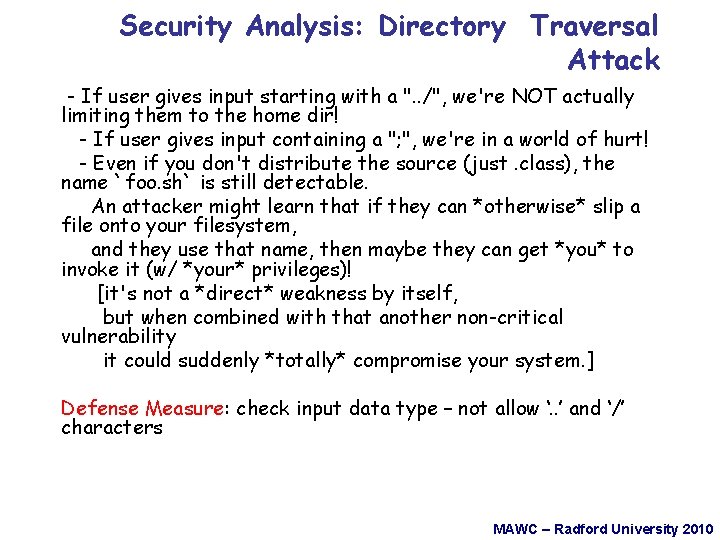
Security Analysis: Directory Traversal Attack - If user gives input starting with a ". . /", we're NOT actually limiting them to the home dir! - If user gives input containing a "; ", we're in a world of hurt! - Even if you don't distribute the source (just. class), the name `foo. sh` is still detectable. An attacker might learn that if they can *otherwise* slip a file onto your filesystem, and they use that name, then maybe they can get *you* to invoke it (w/ *your* privileges)! [it's not a *direct* weakness by itself, but when combined with that another non-critical vulnerability it could suddenly *totally* compromise your system. ] Defense Measure: check input data type – not allow ‘. . ’ and ‘/’ characters MAWC – Radford University 2010

Solutions to OS injection attack: Validate input data type • (1) Blacklisting: disallow bad chars – Scan input for single-quote char etc. , and eliminate them (or, quote them). But also, remember to also check for double-quote; newline; backslash. Forgetting to blacklist or quote even a single bad character may cause problems. Example slide provided with the textbook: Foundations of Security: Neil Daswani et al. ©Neil Daswani , ISBN-13: 978 -1590597842 MAWC – Radford University 2010

Solutions (2) • 2) Whitelisting: only allow safe chars (and flat-out reject other chars)- better method: follow principle of fail safe defaults. In this case, only limit the possible inputs to certain characters. However, this may not always be user friendly (Peter O'Toole and Mötley Crüe can't use your site). Example. Limit character set on codepage <meta http-equiv=“Content-Type” content=“text/html; charset=iso-8859 -1”> Example slide provided with the textbook: Foundations of Security: Neil Daswani et al. ©Neil Daswani , ISBN-13: 978 -1590597842 MAWC – Radford University 2010

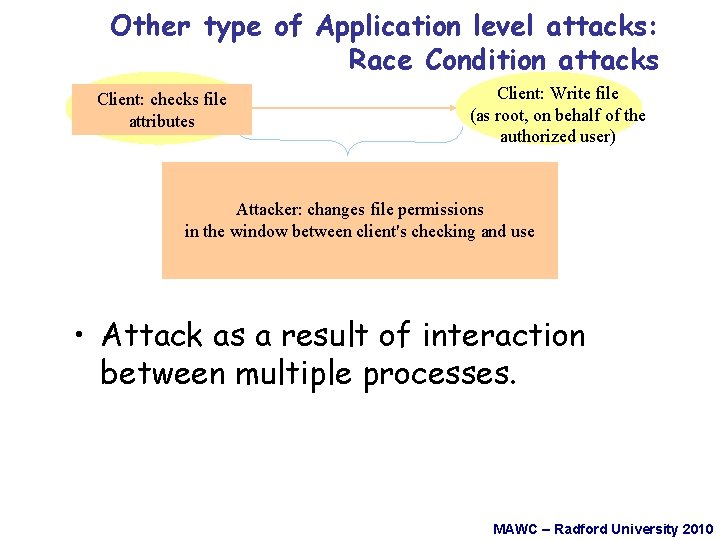
Other type of Application level attacks: Race Condition attacks Client: thefile user Client: verify checks could attributes write file X Client: Write file (as root, on behalf of the authorized user) 1. Attacker deletes file(name) X 2. Creates symbolic linkfile from X to privileged file Attacker: changes permissions /etc/passwd) in the(e. g. window between client's checking and use This requires only directory-write privileges • Attack as a result of interaction between multiple processes. MAWC – Radford University 2010

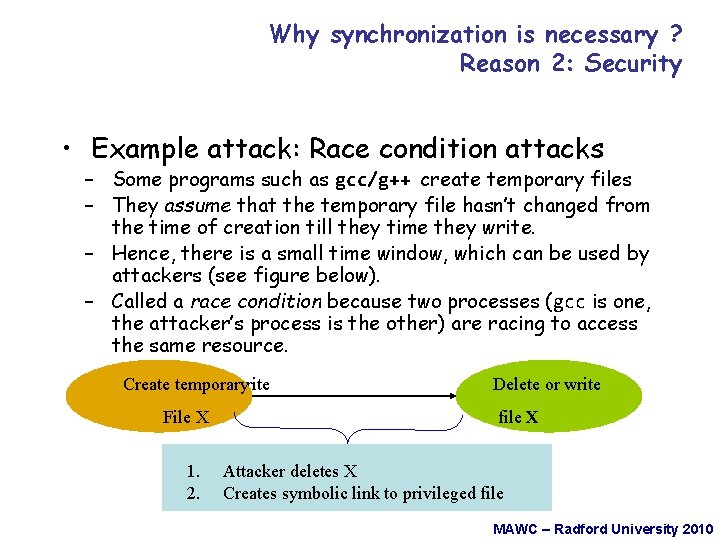
Why synchronization is necessary ? Reason 2: Security • Example attack: Race condition attacks – Some programs such as gcc/g++ create temporary files – They assume that the temporary file hasn’t changed from the time of creation till they time they write. – Hence, there is a small time window, which can be used by attackers (see figure below). – Called a race condition because two processes (gcc is one, the attacker’s process is the other) are racing to access the same resource. Check Create if user temporary can write file X File X 1. 2. Write file Delete or write X file X Attacker deletes X Creates symbolic link to privileged file MAWC – Radford University 2010

Race Attack Defense • https: //ieeexplore. ieee. org/document /5207635 • https: //www. usenix. org/legacy/public ations/library/proceedings/sec 05/te ch/full_papers/borisov_html /races. html MAWC – Radford University 2010

Truncation Error Attack • Unix root has user ID=0. Network file system daemon/service accepts a signed integer user ID. If !=0, then converts it to a 2 byte unsigned user ID. – Attacker enters 17 bit user ID=0 x 10000, it is truncated to 2 byte unsigned value x 0000=0. Attacker is granted root access privilege. MAWC – Radford University 2010

Security In Action • Secure by Design – Threat Modelling: identify threats using Data flow diagram • Secure by Default: only install software features used by most users by default • Secure in Deployment: patch software MAWC – Radford University 2010

Security Principles • Use least privilege: give users least amount of privileges to get job done for the least amount of time • Defense in depth: layer defense • Fail safe & plan on failure- white listing • Secure defaults • Separation of duty: e. g. debugger elevate privilege • Don’t mix code with data: XSS attack • Zero knowledge: don’t show detailed error messages MAWC – Radford University 2010

Security Principles (Cont. ) • • • Learn from mistakes Minimize your attack surface Backward compatibility gives grief Assume external systems insecure Security feature not equal secure feature • Never depend on security through obscurity • Fix security issue correctly MAWC – Radford University 2010