Opportunistic OffPath Content Discovery in InformationCentric Networks Onur











- Slides: 26

Opportunistic Off-Path Content Discovery in Information-Centric Networks Onur Ascigil, Vasilis Sourlas, Ioannis Psaras, and George Pavlou Department of Electronic and Electrical Engineering, University College London, UK

Outline • Content discovery in Information-centric Networks (ICN) • Opportunistic Content Discovery • Evaluation • Future Work & Conclusions

Content Discovery in ICN

Content Discovery in ICN: ICN Features • Information-centric Networking (ICN) features • Naming of content • e. g. , /ucl/ee/onur/lanman_presentation 2016. ppt • Network Storage • Ubiquitous caching • Stateful Forwarding • Request (i. e, Interest) leaves breadcrumbs, which the data follows • Routing on names: • Mostly focused on locating the content on-path, at origin or a designated cache • Disclaimer: ignoring scalability issues in this talk • Goal: integrate content delivery as a native network feature • Is it achieved?

Content Discovery in ICN • Find a nearby (ideally nearest!) copy of the content • Difficult to achieve without significant ``overhead’’ in practice • Why? • Volatile nature of content in the caches: • Contents of caches may change at very short time-scales • Request-to-cache routing • Mostly focused on routing requests to the content origin • Search content on-path (i. e. , along the shortest or default path) • Existing Solutions for Content Discovery: • Opportunistic on-path • Coordinated off-path

Content Discovery in ICN: Request Routing • Opportunistic on-path: limited gain • Caching: Content is cached on-path as it travels to the user from the content origin • Request routing: Route requests to content origin & retrieve content opportunistically from on-path caches • E. g. , Barebones NDN • with default forwarding strategy • Coordinated off-path: coordination and communication overhead • Caching: content is assigned to off-path caches according to predefined rules • Request routing: adheres to the same rules in order to retrieve contents from caches in a coordinated manner • E. g. , Hash routing: • a hash function determines both the placement of content and routing of requests by mapping content identifiers to cache nodes • E. g. , Coordinate content placement and routing with the control plane: • advertise cache contents in the control plane and direct requests to caches

Opportunistic Content Discovery

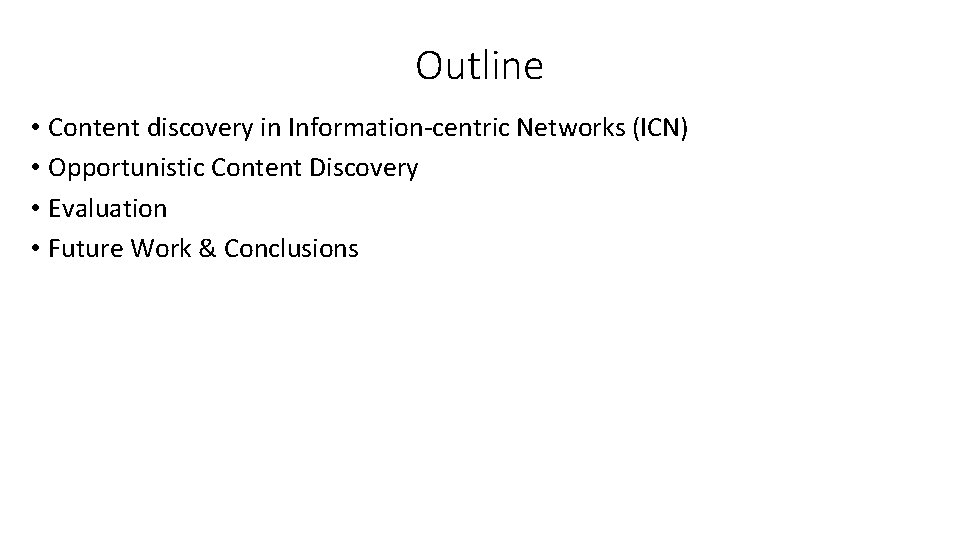
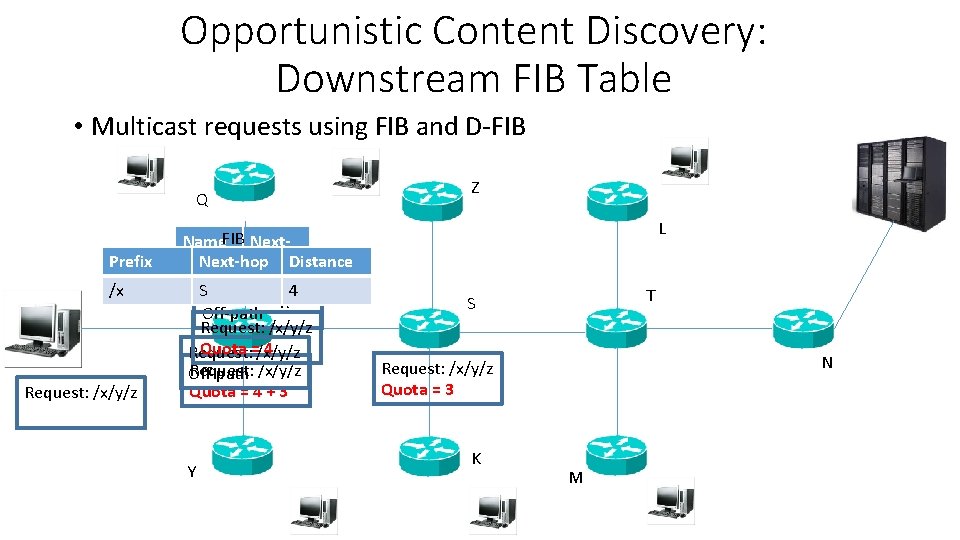
Opportunistic Content Discovery • Stateful forwarding of data packets: data packets leave breadcrumbs • Downstream FIB table (D-FIB) Prefix FIB Next-hop /facebook T R Name H 2 D-FIB Next-hop /…. /x. mpg Request: /facebook/user/x. mpg Prefix H 1 S Request: T /facebook/user/x. mpg Request: FIB /facebook/user/x. mpg Prefix Next-hop S FIB Next-hop /facebook T /facebook U D-FIB Next-hop Name /…. /x. mpg U T … Data: 10010101…

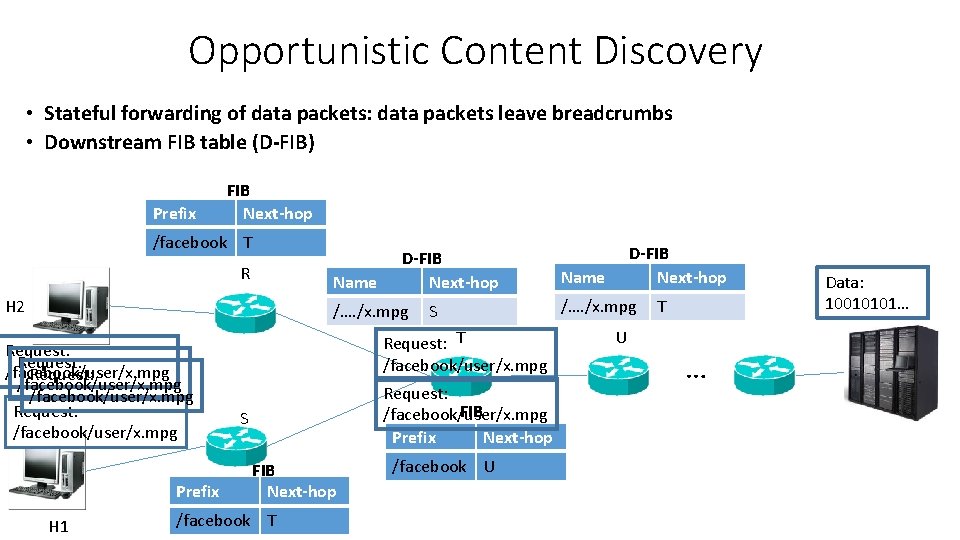
Opportunistic Content Discovery: Downstream FIB Table • Caches trails of data packets towards users • LRU policy • An exact match table

Opportunistic Content Discovery: Routing using D-FIB & FIB • Goal: • improve cache hits • Reduce latency in obtaining content • limit overhead and reduce the number of requests reaching the content origin • Each request is associated with a Total Forwarding Counter (TFC) value • spend it on sending a copy of a request downstream • spend it on following the FIB table towards the content origin (upstream) • spend it on both (multicast) • TFC is initially set by the access router • New Forwarding Strategies based on D-FIB • Determines how TFC quota is spent at each router

Opportunistic Content Discovery: Downstream FIB Table • Multicast requests using FIB and D-FIB Q Prefix /x Request: /x/y/z Z L Name. FIB Next-hop Distance SRequest: /x/y/z Q, /x/y/z Y 4 R Off-path Request: /x/y/z Quota =/x/y/z 4 Request: /x/y/z Off-path Quota = 4 + 3 Y T S N Request: /x/y/z Quota = 3 K M

Opportunistic Content Discovery: Forwarding Strategies • Check Content Store, if no matching content, then: • Lookup FIB and D-FIB • If D-FIB returns no entries, follow FIB (forward upstream) • If D-FIB returns one or more entries, then the forwarding strategy decides what action to perform • Two simple strategies: • ALL strategy: Send a copy of the request to all the next-hops in the D-FIB entry • the cache is closer (number of hops) than the content origin • ONE strategy: Send a copy of the request to only one next-hop in the D-FIB entry • Freshest entry which is closer than the content origin

Performance Evaluation

Evaluation • Implemented our approach in ndn. SIM — an ns-3 based simulator • Performance metrics: • Cache hit ratio: percentage of the interests that have been satisfied • Off-path/on-path • The minimum hop distance: number of hops traveled by the (first) data arriving at the user from a responding router or the content origin for each successful request • The mean traffic overhead: the mean number of hops that the initiated Data packets travel in the network • Variables: • Cache size at each node • D-FIB size w. r. t. content population size • Initial Quota

Evaluation: Scenario • Using a Rocket. Fuel topology: AS 4755 VSNL (India) • 191 nodes: 148 edge, 39 gateway, and 4 backbone routers • 242 bi-directional links • Request rate: 100 requests/sec • Randomly select an edge router • Content Population: 10, 000 • One chunk per item • One content server • attached to a randomly chosen edge router • our results comparing performance of on-path/off-path is best-case scenario • Popularity of the items determined by a Zipf law of exponents • Zipf parameter z: 0. 7 • Quota: Shortest path length + 3 • Duration: 1 hour (following an hour of warm-up phase)

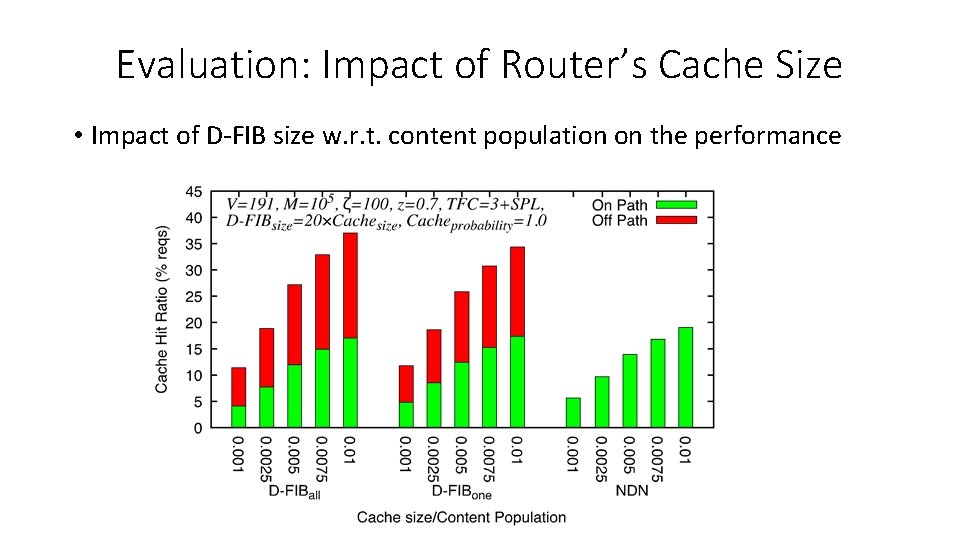
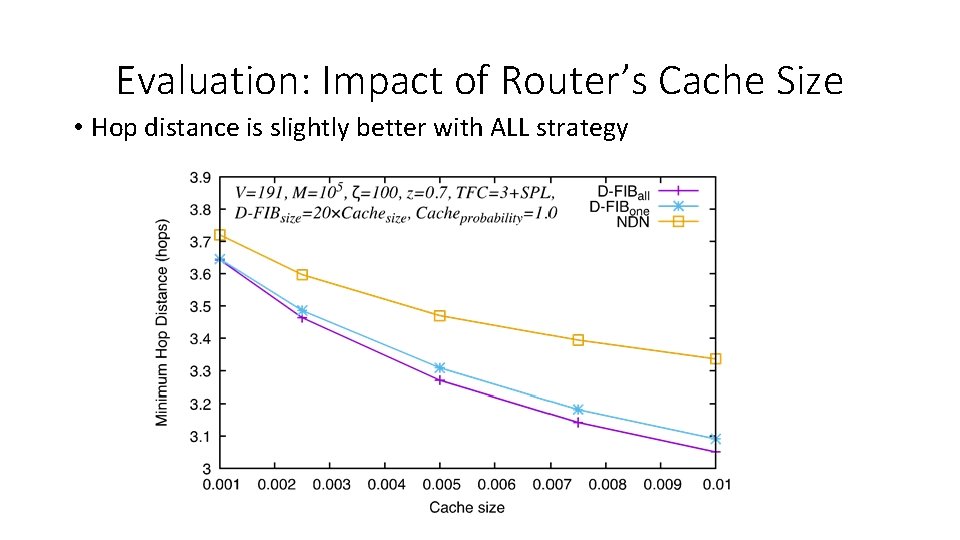
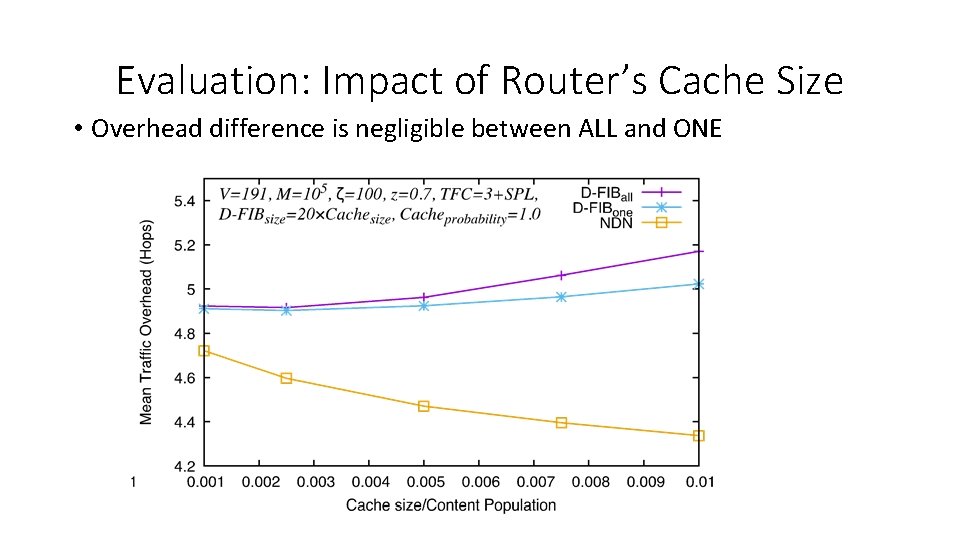
Evaluation: Impact of Router’s Cache Size • Impact of D-FIB size w. r. t. content population on the performance

Evaluation: Impact of Router’s Cache Size • Hop distance is slightly better with ALL strategy

Evaluation: Impact of Router’s Cache Size • Overhead difference is negligible between ALL and ONE

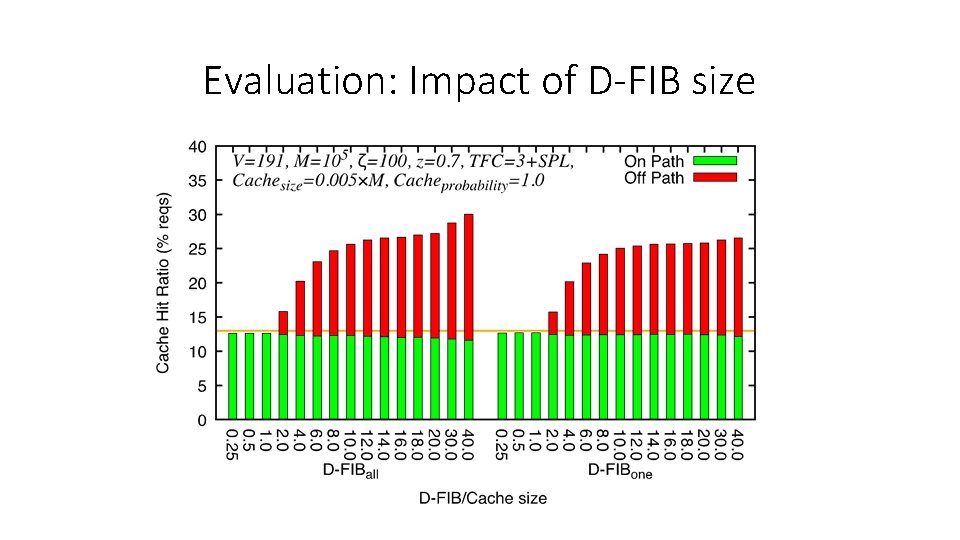
Evaluation: Impact of D-FIB size

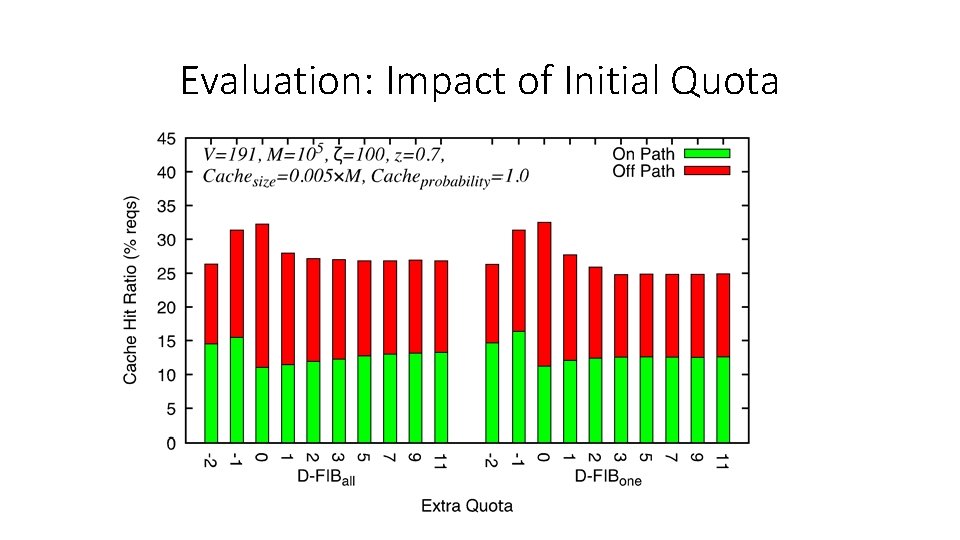
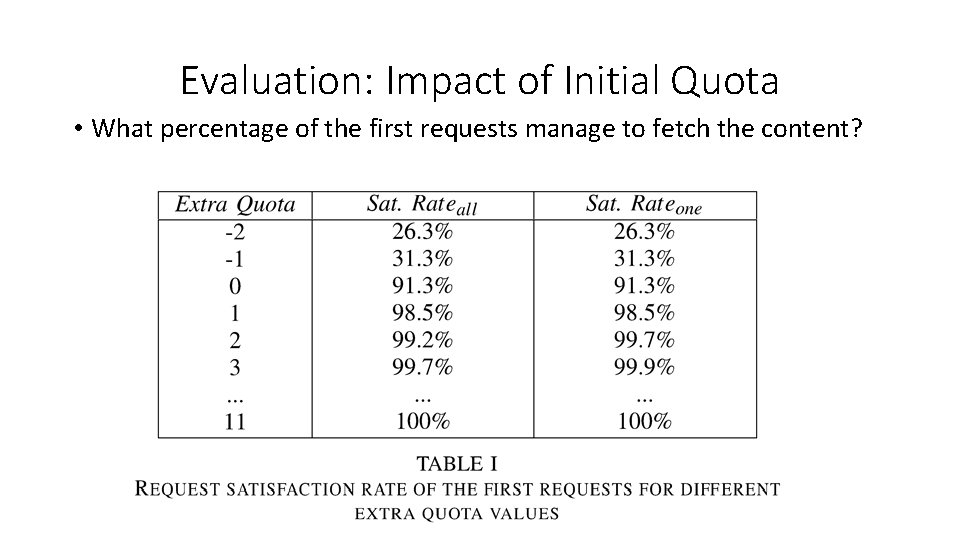
Evaluation: Impact of Initial Quota

Evaluation: Impact of Initial Quota • What percentage of the first requests manage to fetch the content?

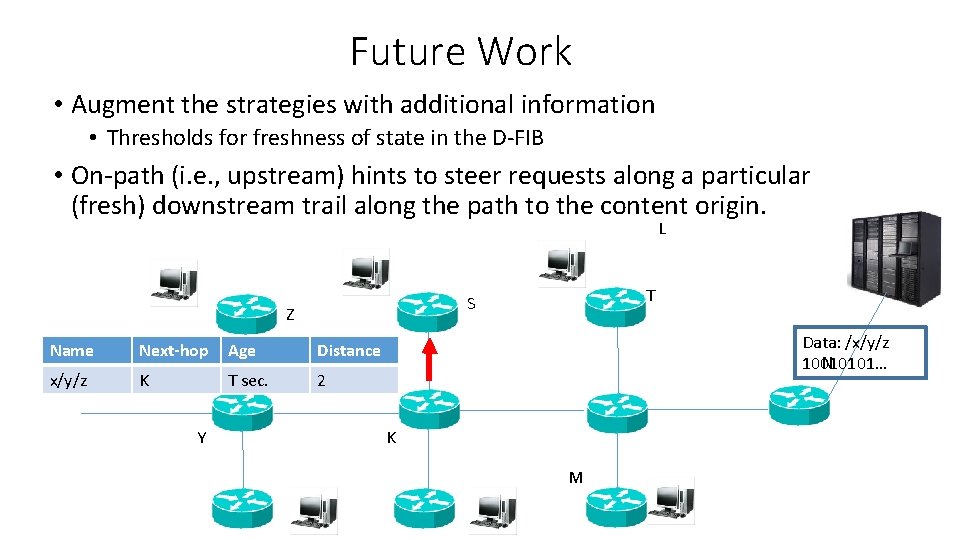
Future Work • Augment the strategies with additional information • Thresholds for freshness of state in the D-FIB • On-path (i. e. , upstream) hints to steer requests along a particular (fresh) downstream trail along the path to the content origin. L Z Name Next-hop Age Distance x/y/z K T sec. 2 Y T S Data: /x/y/z N 10010101… K M

Conclusions • Opportunistic scheme to discover content using two simple yet effective strategies • Reduces load on the content origin • Improves cache hits • Adds little overhead • Basic framework with opportunities to augment with more sophisticated forwarding strategies

Thank you for listening! Questions?

Backup slides

Zipf Distribution • Requests are generated in the network with rate r = {r 1, . . . , r. M}, where rm denotes the aggregate incoming request rate (in requests per second) for content item m 2 M. The request rate for each item is determined by its popularity. Here we approximate the popularity of the items by a Zipf law of exponents z [20]. In that way the aggregate incoming request rate (in requests per second) for an information item m 2 M is given by: rm=z· 1/kz ,