Operations Security OPSEC 301 371 1050 Introduction Standard






























- Slides: 33

Operations Security (OPSEC) 301 -371 -1050

Introduction Ø Ø Ø Ø Ø Standard Application Objectives Regulations and Guidance OPSEC Definition Indicators Definition Identify Threat Capabilities The OPSEC Process Define OPSEC Review, Assessment, and Survey

Standard Implement OPSEC measures based on unit indicators and vulnerabilities; protect unit essential elements of friendly information against threat collection efforts and prevented compromise. .

Application Operations security awareness and execution is crucial to Army success. OPSEC is applicable to all personnel and all Army missions and supporting activities on a daily basis.

Objectives • • • Understand the OPSEC concept, process, and analytical methodology Apply OPSEC to establish and maintain Essential Secrecy concerning Command Capabilities, Intentions and Activities Define OPSEC review, assessment, & survey

Regulations & Guidance v v Operations Security is a national program. Regulatory guidance for OPSEC is contained in: n n n NSDD 298 DOD Dir 5205. 2 CJCS Inst 3213. 01 and JOPES CJCS MOP 30 AR 530 -1

OPSEC Definition OPSEC is a process of analyzing friendly actions pursuant to military operations and other activities to— 1. 2. 3. Identify those friendly actions that can be observed by the threat. Determine indicators that the threat might obtain that could be interpreted or pieced together to derive critical information in time to be useful. Select and execute measures that eliminate or reduce to an acceptable level the vulnerabilities of friendly actions to the threat exploitation.

Indicators - Definition Indicators are data derived from open sources or from detectable actions that the threat can piece together or interpret to reach conclusions or official estimates concerning friendly intentions, capabilities, or activities. They are also activities that result from military operations.

3 Types of Indicators 1. 2. 3. Profile - show activities are normally conducted. Profiles are developed by looking at all aspects of friendly operations from the viewpoint of the threat. Deviation - highlight contrasts to normal activity, help the threat gain appreciation about intentions, preparations, time, and place. Tip-Off - draws attention to information that otherwise might pass unnoticed.

Identify Threat Capabilities The threat consists of multiple and overlapping collection efforts targeted against all sources of Army information.

The OPSEC process 1. 2. 3. 4. 5. Identify Critical Information Threat Analysis Vulnerability Analysis Risk Assessment Implement OPSEC Countermeasures

1. Identify Critical Information v v Determine what needs protection Identify critical information in a variety of situations (ask “If known by the threat, what would be the mission impact” Identify friendly force profiles Avoid setting patterns

Critical Information can be. . . o Information or data n o An activity, event or operation n o Comm, Verbal, Printed, Non-Verbal, Detectable & Observable Activities Logistics, Movement, Training & Testing Classified or unclassified n n Anything that could hinder or prevent mission accomplishment Facts about our protective measures

The Essential Elements of Friendly Information (EEFI) o o “What key questions about friendly intentions and military capabilities are likely to be asked by adversary officials and intelligence systems” Answers to the EEFI are critical information n EXAMPLE: What specific network security procedures are used by the command? n Anything that will answer this question is critical information

2. Analysis of Threat v v Identify OPSEC vulnerabilities. Identify OPSEC indicators.

Threat Characteristics o o Capabilities Motivation Intent History of Action (Probability)

Information Collection o All nations collect Groups collect All sources are exploited Increasing collection sophistication Increasing collection capability o Increasing lethality is the result o o

How is the information collected? It is Multi-disciplined. o o o HUMINT (Human Intelligence) SIGINT (Signals Intelligence) IMINT (Imagery Intelligence) MASINT (Measurement and Signatures Intelligence) OSINT (Open Source)

3. Vulnerability Analysis v v v Identify and discuss Indicators Identify and discuss vulnerabilities Describe the elements of a vulnerability

Vulnerabilities o o o Visualize the Operation Identify Critical Information & location in your operation/systems Compare threat capabilities to Critical Information

Select Possible Protective Measures o o o Action Control - Indicator Countermeasures - Collection System Counter Analysis - Analyst

4. Risk Assessment v v v Understand the concept of risk. Assess the degree of risk. Understand the difference between Risk management vice risk avoidance

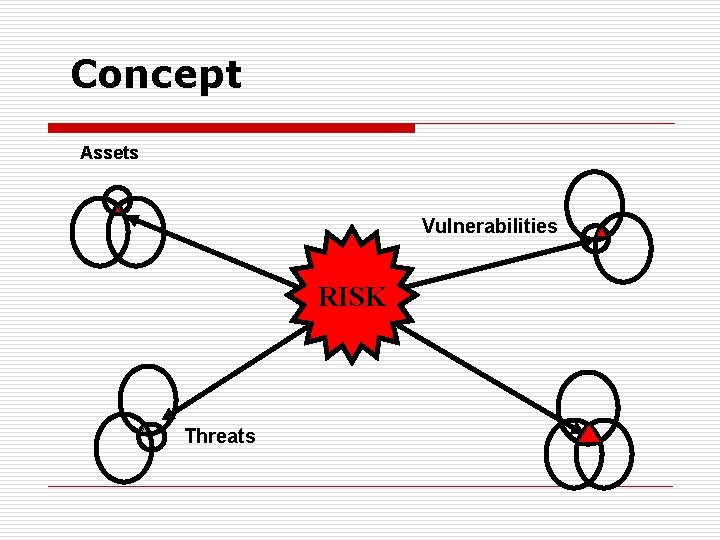
Concept Assets Vulnerabilities RISK Threats

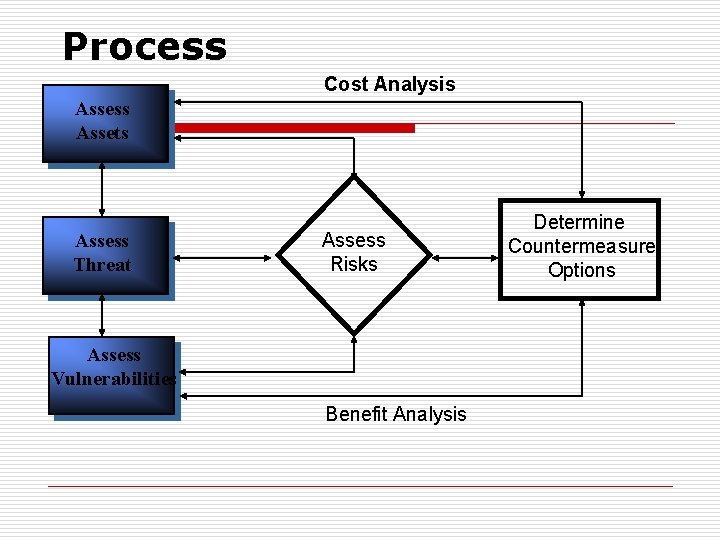
Process Cost Analysis Assess Assets Assess Threat Assess Risks Assess Vulnerabilities Benefit Analysis Determine Countermeasure Options

THE COMMANDER CONSIDERS. . . o o o Mission Accomplishment Combat Effectiveness vs Efficiency • Cannot avoid all risks • Military activities have inherent risks • Must manage the risks that cannot be avoided

5. Implement OPSEC Measures o o Identify means to implement countermeasures Evaluate the effectiveness of OPSEC program

OPSEC is Implemented via. . . o o Orders Annexes Plans The Commander

OPSEC Review, Assessment, and Survey

OPSEC Review OPSEC review is an evaluation of a document to ensure protection of sensitive or critical information.

OPSEC Assessment OPSEC assessment is an analysis of an operation, activity, exercise, or support function to determine the overall OPSEC posture and to evaluate the degree of compliance of subordinate organizations with the published OPSEC plan or OPSEC program.

OPSEC Survey OPSEC survey is a method to determine if there is adequate protection of critical information during planning, preparations, execution, and post-execution phases of any operation or activity. It analyzes all associated functions to identify sources of information, what they disclose, and what can be derived from the information.

REMAIN ALERT

Summary Ø Ø Ø Ø Ø Standard Application Objectives Regulations and Guidance OPSEC Definition Indicators Definition Identify Threat Capabilities The OPSEC Process Define OPSEC Review, Assessment, and Survey