Operationalizing Threat Intelligence Doug Cooke Director PreSales Canada






- Slides: 27

Operationalizing Threat Intelligence Doug Cooke Director Pre-Sales, Canada April 2016. Mc. Afee Confidential

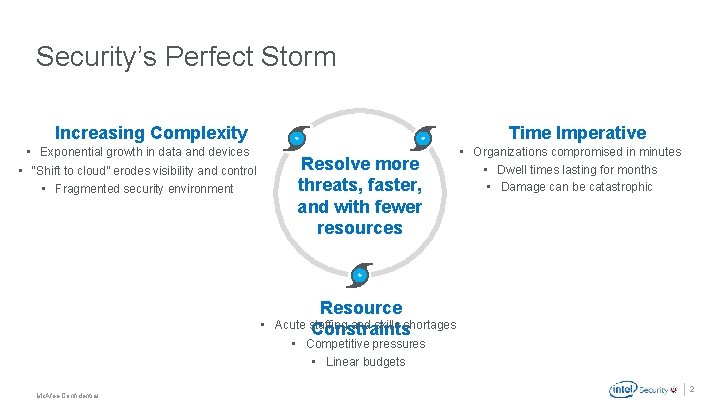
Security’s Perfect Storm Increasing Complexity Time Imperative • Exponential growth in data and devices • “Shift to cloud” erodes visibility and control • Fragmented security environment Resolve more threats, faster, and with fewer resources • • Organizations compromised in minutes • Dwell times lasting for months • Damage can be catastrophic Resource Acute staffing and skills shortages Constraints • Competitive pressures • Linear budgets . Mc. Afee Confidential 2

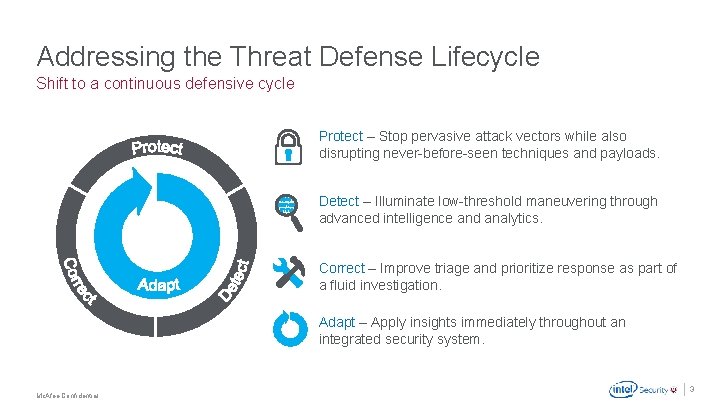
Addressing the Threat Defense Lifecycle Shift to a continuous defensive cycle Protect – Stop pervasive attack vectors while also disrupting never-before-seen techniques and payloads. Detect – Illuminate low-threshold maneuvering through advanced intelligence and analytics. Correct – Improve triage and prioritize response as part of a fluid investigation. Adapt – Apply insights immediately throughout an integrated security system. . Mc. Afee Confidential 3

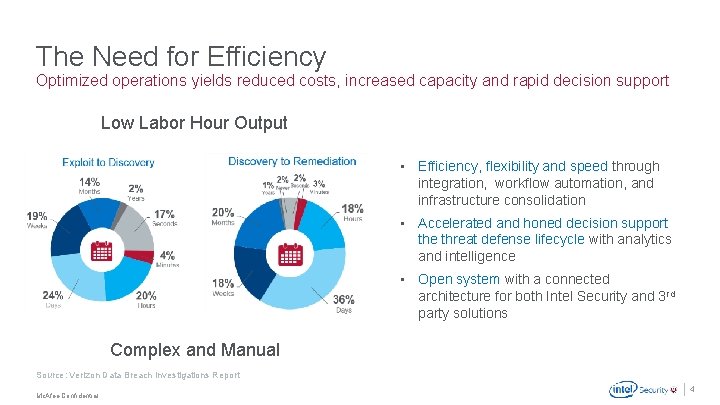
The Need for Efficiency Optimized operations yields reduced costs, increased capacity and rapid decision support Low Labor Hour Output • Efficiency, flexibility and speed through integration, workflow automation, and infrastructure consolidation • Accelerated and honed decision support the threat defense lifecycle with analytics and intelligence • Open system with a connected architecture for both Intel Security and 3 rd party solutions Complex and Manual Source: Verizon Data Breach Investigations Report. Mc. Afee Confidential 4

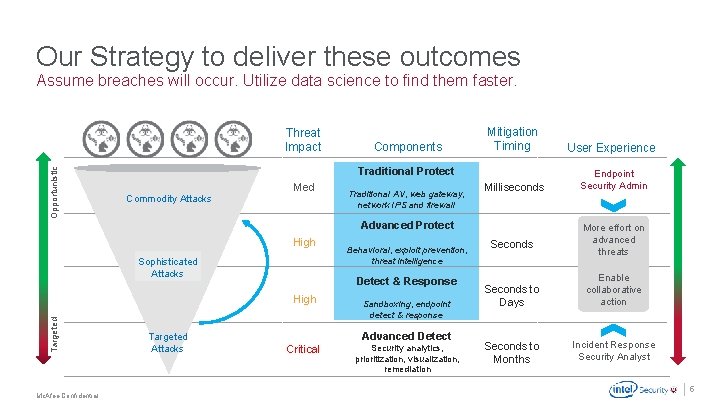
Our Strategy to deliver these outcomes Assume breaches will occur. Utilize data science to find them faster. Opportunistic Threat Impact User Experience Milliseconds Endpoint Security Admin Traditional Protect Commodity Attacks Med Traditional AV, web gateway, network IPS and firewall Advanced Protect High Sophisticated Attacks Targeted Attacks Behavioral, exploit prevention, threat intelligence Detect & Response High Targeted Components Mitigation Timing Sandboxing, endpoint detect & response Advanced Detect Critical Security analytics, prioritization, visualization, remediation Seconds More effort on advanced threats Seconds to Days Enable collaborative action Seconds to Months Incident Response Security Analyst. Mc. Afee Confidential 5

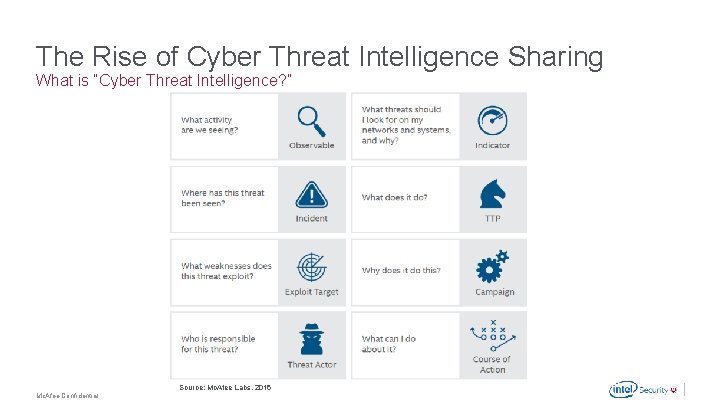
The Rise of Cyber Threat Intelligence Sharing What is “Cyber Threat Intelligence? ” Source: Mc. Afee Labs, 2016 Mc. Afee Confidential .

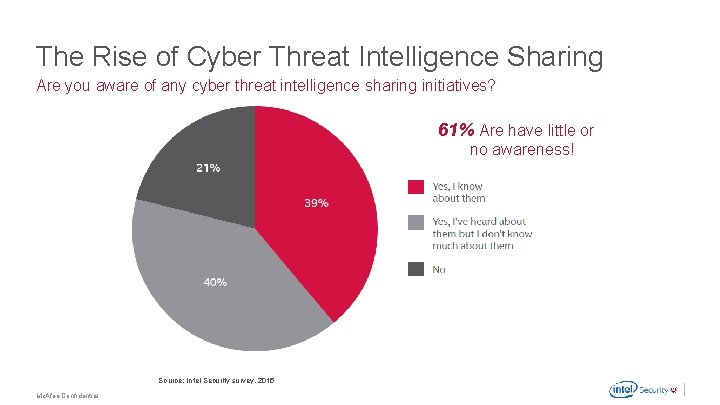
The Rise of Cyber Threat Intelligence Sharing Are you aware of any cyber threat intelligence sharing initiatives? 61% Are have little or no awareness! Source: Intel Security survey, 2015 Mc. Afee Confidential .

The Rise of Cyber Threat Intelligence Sharing How valuable is cyber threat intelligence sharing to your organization? 59% Very Valuable Source: Intel Security survey, 2015 Mc. Afee Confidential .

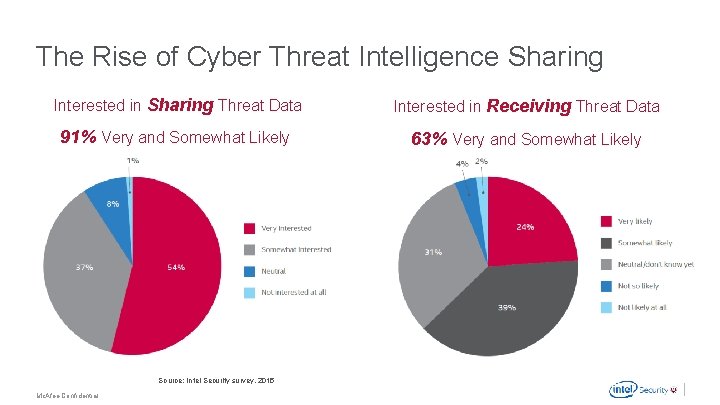
The Rise of Cyber Threat Intelligence Sharing Interested in Sharing Threat Data Interested in Receiving Threat Data 91% Very and Somewhat Likely 63% Very and Somewhat Likely Source: Intel Security survey, 2015 Mc. Afee Confidential .

The Rise of Cyber Threat Intelligence Sharing Why companies don’t share cyber threat intelligence • Company policy – Companies often have blanket policies that don’t take into account what is being shared, e. g. hashes vs. PII. • Catching bad guys – It could interfere with ongoing investigations. Some allow exploits to succeed while monitoring them—in order to gain more information about who is behind the attack. If the threat data is shared with a CTI community and the attackers participate in that community, they could be alerted that their activities have been identified. • Concerns over legality – Legal and trust frameworks for sharing cyber threat information are not well established, making it easy for risk-averse corporate lawyers to say no or to set up highly restrictive policies to limit sharing. • Concerns over privacy – Global laws and norms make sharing an extremely complicated landscape. Regulations regarding the sharing of personal information are not always fully understood. To avoid fines and penalties, many err on the side of caution. • Lack of exchange standards – Until recently, established and widelyaccepted technical standards have not existed except in focused areas like incidence response. Mc. Afee Confidential .

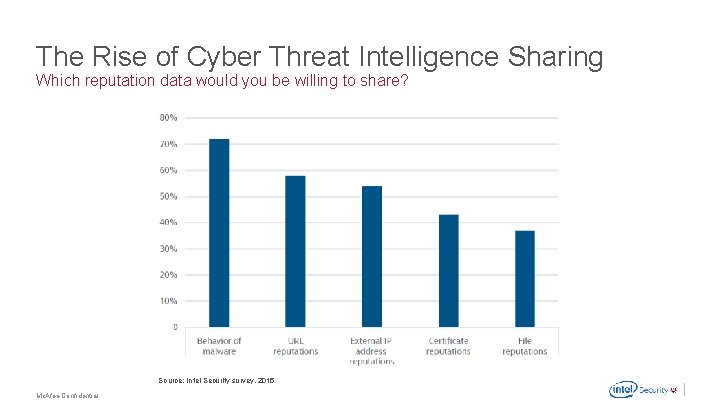
The Rise of Cyber Threat Intelligence Sharing Which reputation data would you be willing to share? Source: Intel Security survey, 2015 Mc. Afee Confidential .

The Rise of Cyber Threat Intelligence Sharing The future of cyber threat intelligence sharing • Legal frameworks –The US Cybersecurity Information Sharing Act (CISA) provides, in part, legal foundations for sharing between government and the private sector and between private sector organizations. It provides liability protection extending to private entities. It could become a model for global information sharing legislation. • Increased community sharing – With standard threat data representations, communities of cooperation will be able to review and examine malicious events, attacks, and tools in a much more coordinated fashion than has been possible in the past. • Integrated automation – The automated creation, import, and export of standardized CTI is critical for an organization to take advantage of a CTI exchange. Stopping attacks in real time (or near real time) will require automated tools and processes. • Innovative CTI organizations and services – Whole businesses and sharing organization like the Cyber Threat Alliance will arise whose only mission is to enrich the data around individual threats. . Mc. Afee Confidential

Founding Members . Mc. Afee Confidential 13

. Mc. Afee Confidential 14

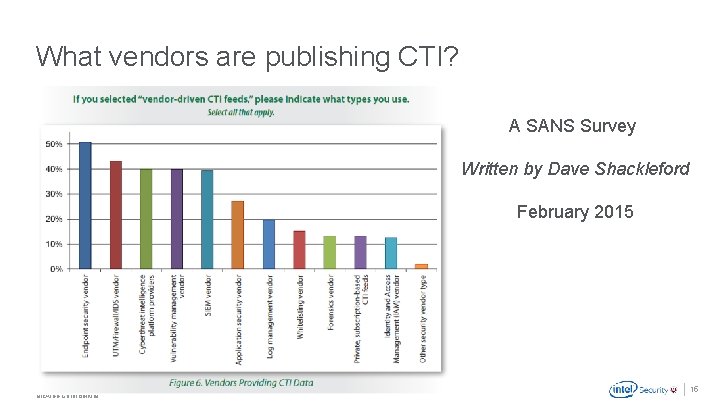
What vendors are publishing CTI? A SANS Survey Written by Dave Shackleford February 2015 . Mc. Afee Confidential 15

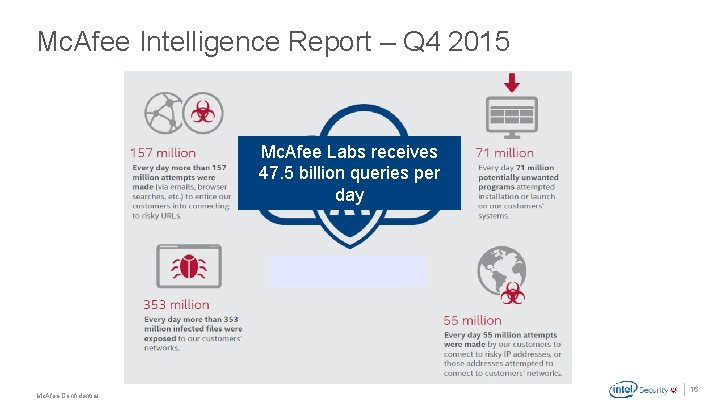
Mc. Afee Intelligence Report – Q 4 2015 Mc. Afee Labs receives 47. 5 billion queries per day . Mc. Afee Confidential 16

Reputation Databases 101001110110101 11001001001 10100111011010 1110010010011010 Past performance is an indicator of future results! . Mc. Afee Confidential 17

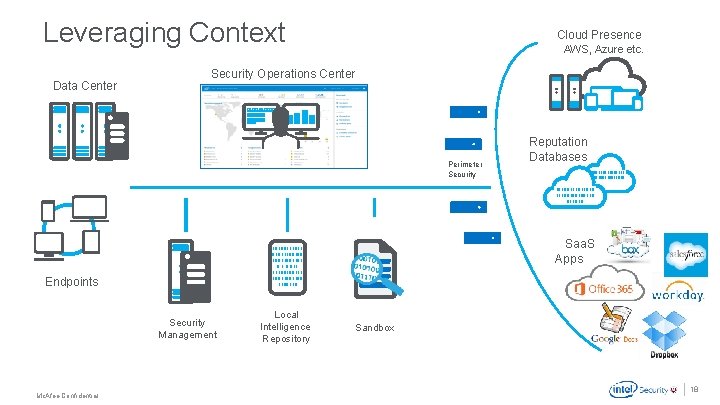
Leveraging Context Data Center Cloud Presence AWS, Azure etc. Security Operations Center Perimeter Security Reputation Databases 10100111011010111 00100100110100111011010 1110010010011010 Saa. S Apps 10100111011 01011100100 1001101 0 011 11100100111 1001100110 Endpoints Security Management Local Intelligence Repository Sandbox . Mc. Afee Confidential 18

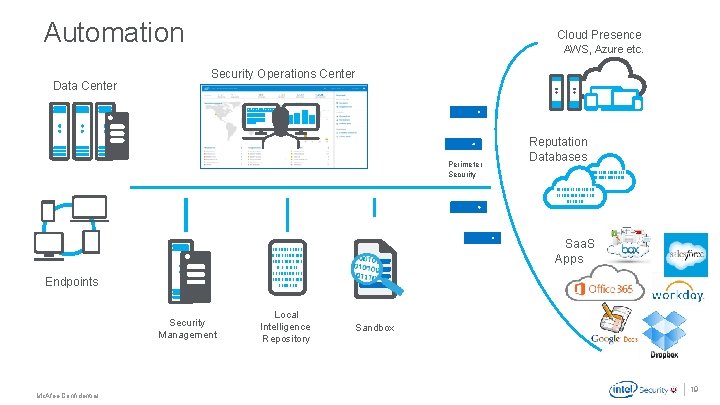
Automation Data Center Cloud Presence AWS, Azure etc. Security Operations Center Perimeter Security Reputation Databases 10100111011010111 00100100110100111011010 1110010010011010 Saa. S Apps 10100111011 01011100100 1001101 0 011 11100100111 1001100110 Endpoints Security Management Local Intelligence Repository Sandbox . Mc. Afee Confidential 19

Optimized Threat Intelligence Use Case. Mc. Afee Confidential 20

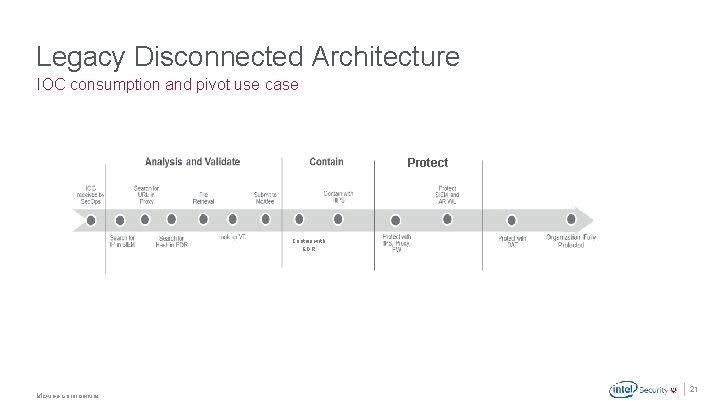
Legacy Disconnected Architecture IOC consumption and pivot use case Protect Contain with EDR . Mc. Afee Confidential 21

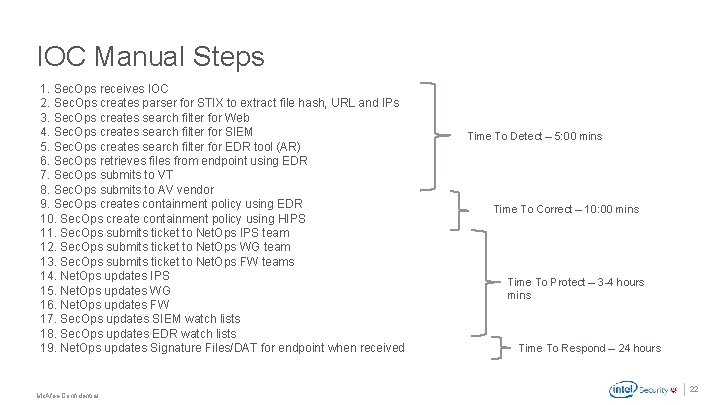
IOC Manual Steps 1. Sec. Ops receives IOC 2. Sec. Ops creates parser for STIX to extract file hash, URL and IPs 3. Sec. Ops creates search filter for Web 4. Sec. Ops creates search filter for SIEM 5. Sec. Ops creates search filter for EDR tool (AR) 6. Sec. Ops retrieves files from endpoint using EDR 7. Sec. Ops submits to VT 8. Sec. Ops submits to AV vendor 9. Sec. Ops creates containment policy using EDR 10. Sec. Ops create containment policy using HIPS 11. Sec. Ops submits ticket to Net. Ops IPS team 12. Sec. Ops submits ticket to Net. Ops WG team 13. Sec. Ops submits ticket to Net. Ops FW teams 14. Net. Ops updates IPS 15. Net. Ops updates WG 16. Net. Ops updates FW 17. Sec. Ops updates SIEM watch lists 18. Sec. Ops updates EDR watch lists 19. Net. Ops updates Signature Files/DAT for endpoint when received Time To Detect – 5: 00 mins Time To Correct – 10: 00 mins Time To Protect – 3 -4 hours mins Time To Respond – 24 hours . Mc. Afee Confidential 22

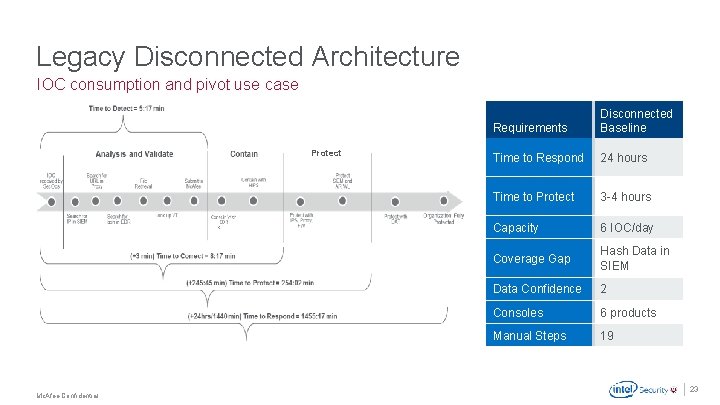
Legacy Disconnected Architecture IOC consumption and pivot use case Protect ED R Requirements Disconnected Baseline Time to Respond 24 hours Time to Protect 3 -4 hours Capacity 6 IOC/day Coverage Gap Hash Data in SIEM Data Confidence 2 Consoles 6 products Manual Steps 19 . Mc. Afee Confidential 23

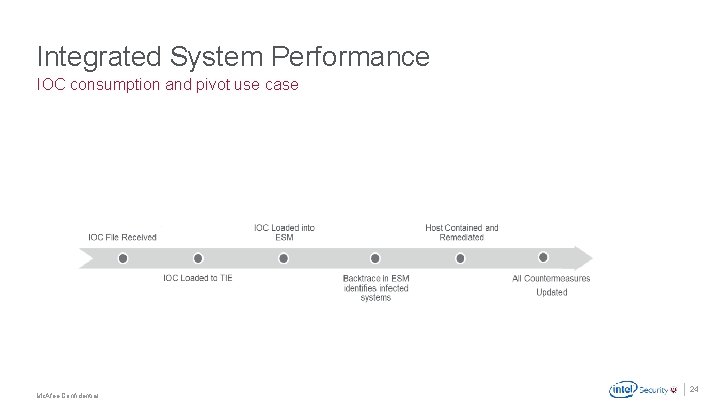
Integrated System Performance IOC consumption and pivot use case . Mc. Afee Confidential 24

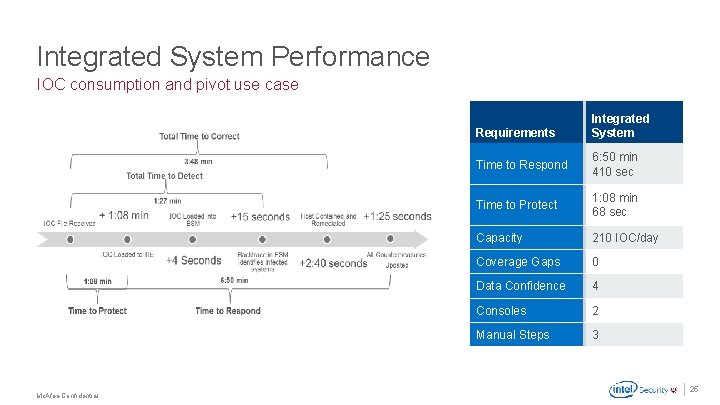
Integrated System Performance IOC consumption and pivot use case Requirements Integrated System Time to Respond 6: 50 min 410 sec Time to Protect 1: 08 min 68 sec Capacity 210 IOC/day Coverage Gaps 0 Data Confidence 4 Consoles 2 Manual Steps 3 . Mc. Afee Confidential 25

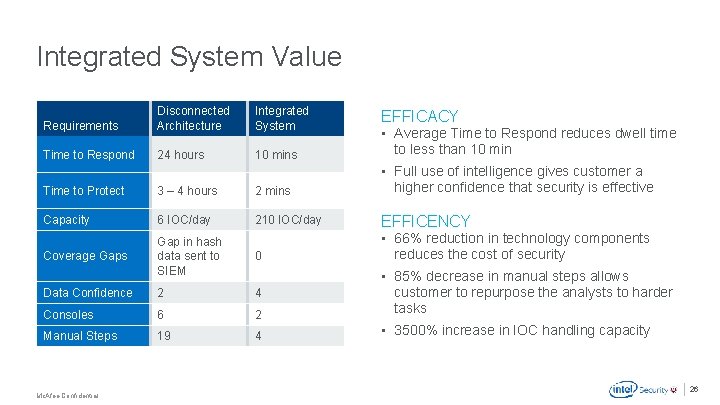
Integrated System Value Requirements Disconnected Architecture Integrated System Time to Respond 24 hours 10 mins • Average Time to Respond reduces dwell time to less than 10 min EFFICACY Time to Protect 3 – 4 hours 2 mins • Full use of intelligence gives customer a higher confidence that security is effective Capacity 6 IOC/day 210 IOC/day EFFICENCY Coverage Gaps Gap in hash data sent to SIEM 0 Data Confidence 2 4 Consoles 6 2 • 85% decrease in manual steps allows customer to repurpose the analysts to harder tasks Manual Steps 19 4 • 3500% increase in IOC handling capacity • 66% reduction in technology components reduces the cost of security . Mc. Afee Confidential 26

27