Operational Security Learning Topics Introduction Critical Information Threat












- Slides: 15

Operational Security

Learning Topics �Introduction �Critical Information �Threat �OPSSEC measures �What to look for �Identifying threats

Introduction �Operations security (OPSEC) is a process that identifies critical information to determine if: � friendly actions can be observed by adversary intelligence systems �information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce adversary exploitation of friendly critical information

Importance �“Loose Lips Sink Ships” �Any priority information that could be useful to the enemy needs to be regulated �In this new technological era, information can pass by the click of a button

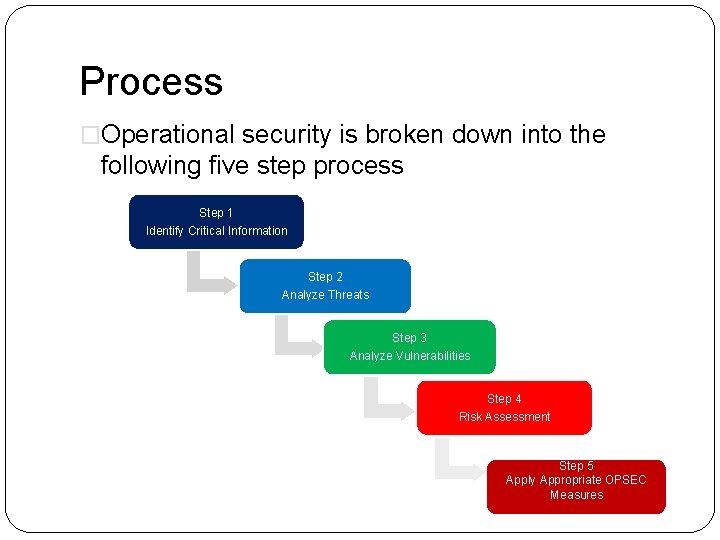
Process �Operational security is broken down into the following five step process Step 1 Identify Critical Information Step 2 Analyze Threats Step 3 Analyze Vulnerabilities Step 4 Risk Assessment Step 5 Apply Appropriate OPSEC Measures

1. Identification Critical Information �Identifying information needed by an adversary, which focuses the remainder of the OPSEC process on protecting vital information, rather than attempting to protect all classified or sensitive unclassified information

2. Analysis of Threats �Analysis of Threats: the research and analysis of intelligence, counterintelligence, and open source information to identify likely adversaries and/or planned operations

3. Analysis of Vulnerabilities �Examining each aspect of the planned operation to identify OPSEC indicators that could reveal critical information and then comparing those indicators with the adversary’s intelligence collection capabilities identified in the previous action

4. Assessment of Risk �First, planners analyze the vulnerabilities identified in the previous action and identify possible OPSEC measures for each vulnerability �Second, specific OPSEC measures are selected for execution based upon a risk assessment done by the commander and staff

5. Application of Appropriate OPSEC Measures �The command implements the OPSEC measures selected in the assessment of risk action or, in the case of planned future operations and activities, includes the measures in specific OPSEC plans

Need To Know � It is possible and not unprecedented for spouses and family members of US military personnel to be targeted for intelligence collection �When being deployed do not give out any critical information that the enemy could use against you

Types of Information Examples of Critical Information The following examples may help you in defining parameters for your communications. It is important to remember that there are many more examples than those listed below: 1. Detailed information about the mission of assigned units 2. Details concerning locations and times of unit deployments 3. Personnel transactions that occur in large numbers (e. g. , pay information, power of attorney, wills or deployment information) 4. References to trend in unit morale or personnel problems

Identifying Threats �In today’s society you have to be extremely careful on how your passing information �If it is sensitive information you have to make sure you use secure channels

Conclusion �“Loose Lips Sink Ships” �Make sure you are passing information the correct way �Avoid posting critical information to social media sights �Avoid the use of cell phones and emails for passing critical information �Do not even pass critical information to your family

Resources �Operational Security http: //www. marines. mil/unit/13 thmeu/Pages/Oper ational. Security. aspx �Marine Parents http: //www. marineparents. com/deployment/opsec. asp