Operating Systems hchgaoxidian edu cn Operating Systems Contents







































- Slides: 68

Operating Systems 软件学院 高海昌 hchgao@xidian. edu. cn

Operating Systems Contents ³ 1. Introduction ** ³ 2. Processes and Threads ******* ³ 3. Deadlocks ** ³ 4. Memory Management ***** ³ 5. Input/Output *** ³ 6. File Systems **** ³ 8. Multiple Processor Systems * ³ 9. Security ** Gao Haichang , Software School, Xidian University 2

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 3

Operating Systems Threats 机密性 篡改 Security goals and threats Gao Haichang , Software School, Xidian University 4

Operating Systems Intruders Common Categories 1. Casual prying (窥探) by nontechnical users 2. Snooping by insiders 3. Determined attempt to make money 4. Commercial or military espionage Gao Haichang , Software School, Xidian University 5

Accidental Data Loss Operating Systems Common Causes Acts of God 1. - fires, floods, wars Hardware or software errors 2. - CPU malfunction, bad disk, program bugs Human errors 3. - data entry, wrong tape mounted Gao Haichang , Software School, Xidian University 6

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 7

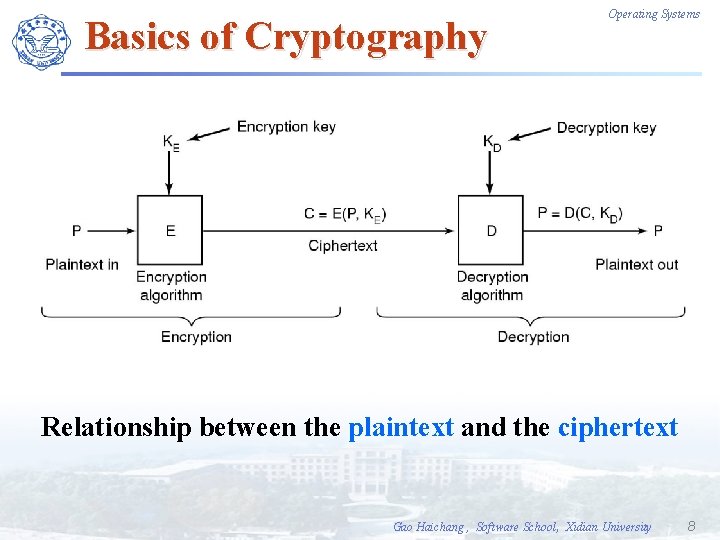
Basics of Cryptography Operating Systems Relationship between the plaintext and the ciphertext Gao Haichang , Software School, Xidian University 8

Secret-Key Cryptography Operating Systems F Monoalphabetic substitution 单字符替换 ³ each letter replaced by different letter A B C D E F G…… ATTACK Q W E R T Y U…… QZZQEA F Given the encryption key, easy to find decryption key F Secret-key crypto called symmetric-key crypto Gao Haichang , Software School, Xidian University 9

Public-Key Cryptography Operating Systems Q 1: How much is 314159265358979 x 314159265358979 ? Q 2: What is the square root of 3912571506419387090594828508241? F All users pick a public key/private key pair ³ publish the public key ³ private key not published F Public key is the encryption key, private key is the decryption key ³ RSA, slow than symmetric cryptography Gao Haichang , Software School, Xidian University 10

One-Way Functions Operating Systems F Function such that given formula for f(x) ³ easy to evaluate y = f(x) F But given y, ³ computationally infeasible to find x Gao Haichang , Software School, Xidian University 11

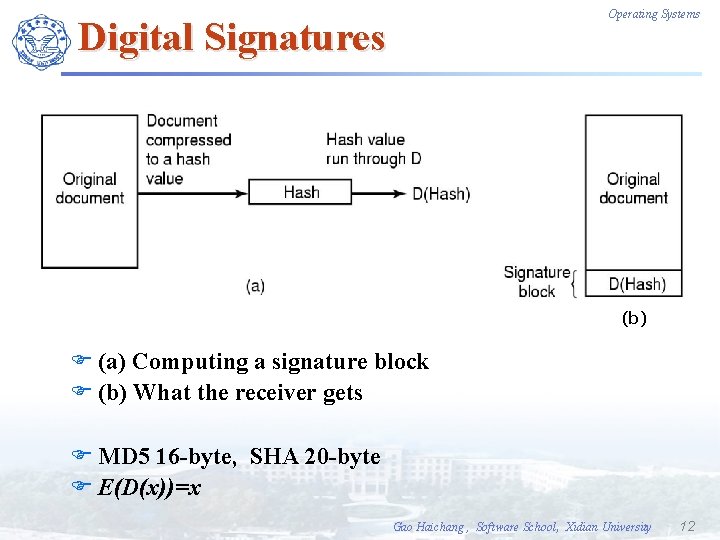
Operating Systems Digital Signatures (b) F (a) Computing a signature block F (b) What the receiver gets F MD 5 16 -byte, SHA 20 -byte F E(D(x))=x Gao Haichang , Software School, Xidian University 12

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 13

User Authentication Operating Systems Basic Principles. Authentication must identify: 1. Something the user knows 2. Something the user has 3. Something the user is This is done before user can use the system Gao Haichang , Software School, Xidian University 14

Operating Systems Authentication Using Passwords (a) A successful login (b) Login rejected after name entered (c) Login rejected after name and password typed Gao Haichang , Software School, Xidian University 15

How crackers break in Operating Systems F How a cracker broke into LBL a U. S. Dept. of Energy research lab ³ Ping / telnet / dnsquery / passwd / packet sniffer ³ Gao Haichang , Software School, Xidian University 16

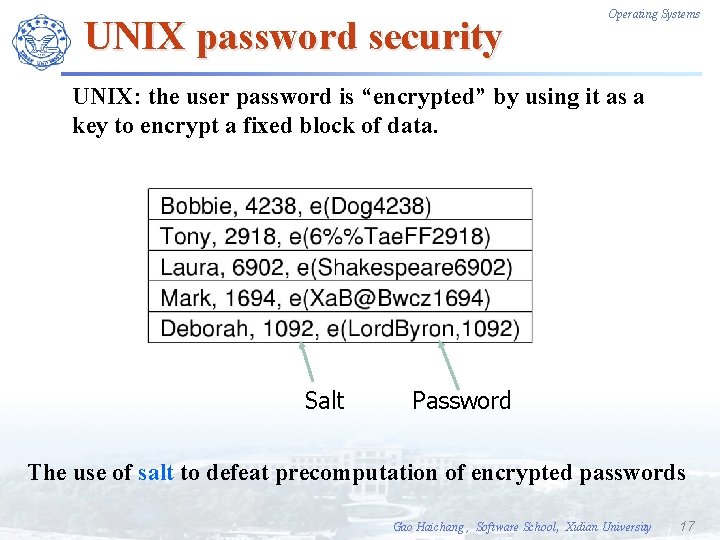
UNIX password security Operating Systems UNIX: the user password is “encrypted” by using it as a key to encrypt a fixed block of data. Salt Password The use of salt to defeat precomputation of encrypted passwords Gao Haichang , Software School, Xidian University 17

One-Time passwords Operating Systems F One way function y=f(x) ³ given x it is easy to find y, but given y it is computational infeasible to find x. ³ The input and output should be the same length, i. e. 128 bits ³ pi-1 = f(pi) p 0 = f(p 1), p 1 = f(p 2), p 2 = f(p 3), p 3 = f(p 4) p 1 = f(f(s)))), p 2 = f(f(f(s))), p 3 = f(f(s)) , p 4 = f(s) F Challenge-Response authentication ³ client get r, send f(r, k) Gao Haichang , Software School, Xidian University 18

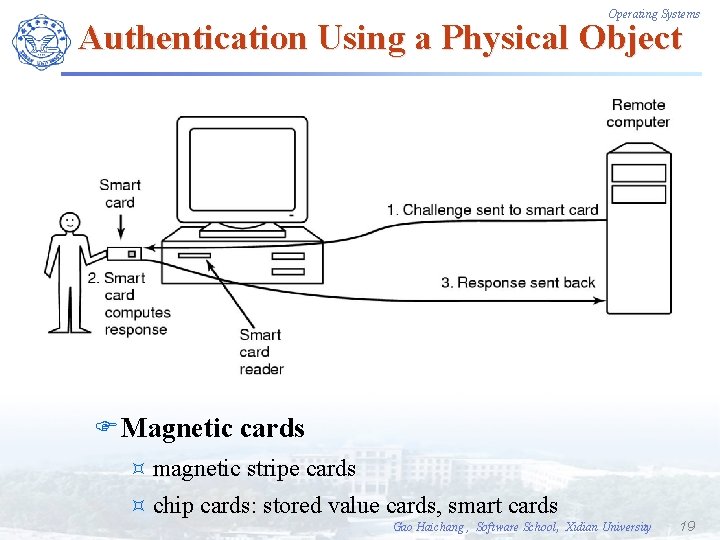
Operating Systems Authentication Using a Physical Object F Magnetic cards ³ magnetic ³ chip stripe cards: stored value cards, smart cards Gao Haichang , Software School, Xidian University 19

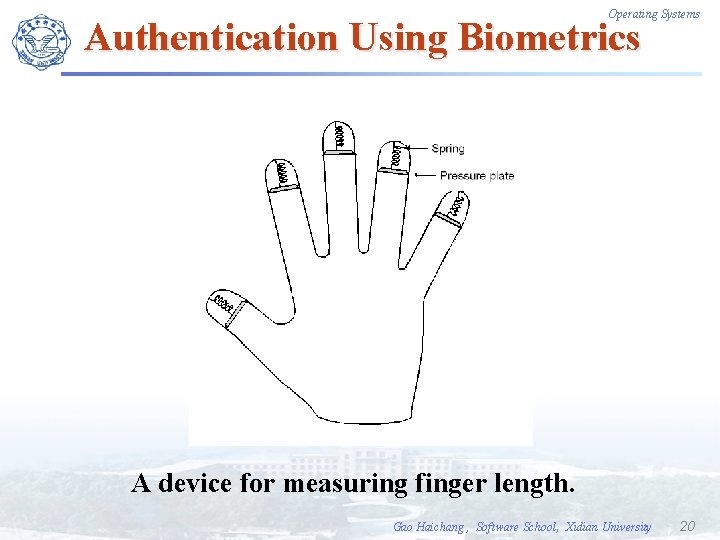
Operating Systems Authentication Using Biometrics A device for measuring finger length. Gao Haichang , Software School, Xidian University 20

Countermeasures Operating Systems 对策 F Limiting times when someone can log in F Automatic callback at number prespecified F Limited number of login tries F A database of all logins F Simple login name/password as a trap ³ security personnel notified when attacker bites Gao Haichang , Software School, Xidian University 21

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 22

Operating Systems Trojan Horses F Free program made available to unsuspecting user ³ Actually contains code to do harm F Place altered version of utility program on victim's computer ³ trick user into running that program Gao Haichang , Software School, Xidian University 23

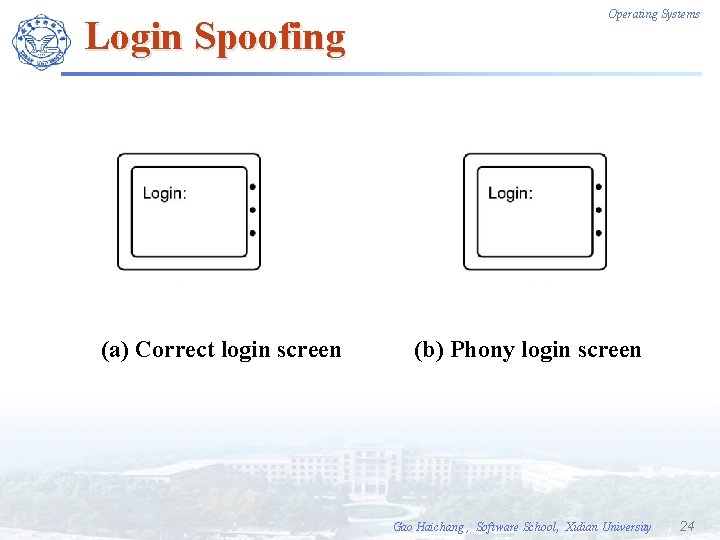
Login Spoofing (a) Correct login screen Operating Systems (b) Phony login screen Gao Haichang , Software School, Xidian University 24

Operating Systems Logic Bombs F Company programmer writes program ³ potential ³ OK ³ if to do harm as long as he/she enters password daily programmer fired, no password and bomb explodes Gao Haichang , Software School, Xidian University 25

Operating Systems Trap Doors (a) Normal code. (b) Code with a trapdoor inserted Gao Haichang , Software School, Xidian University 26

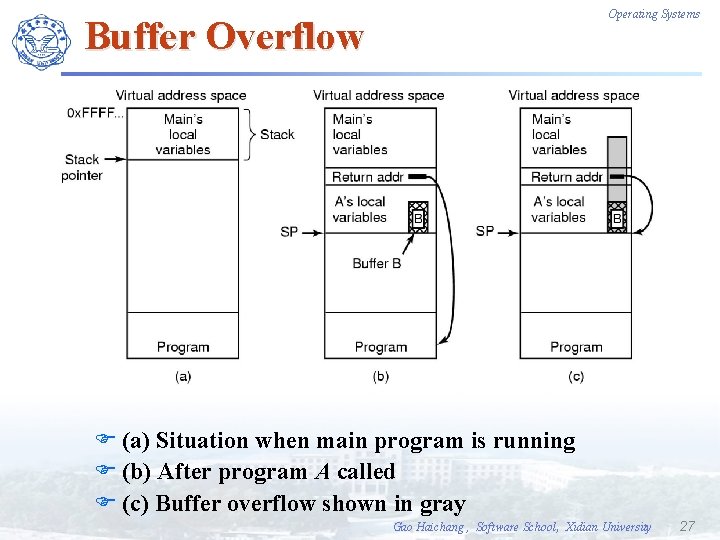
Operating Systems Buffer Overflow F (a) Situation when main program is running F (b) After program A called F (c) Buffer overflow shown in gray Gao Haichang , Software School, Xidian University 27

Generic Security Attacks Operating Systems Typical attacks F Request memory, disk space, tapes and just read F Try illegal system calls F Start a login and hit DEL, RUBOUT, or BREAK F Try modifying complex OS structures F Try to do specified DO NOTs F Convince a system programmer to add a trap door F Beg admin's sec’y to help a poor user who forgot password Gao Haichang , Software School, Xidian University 28

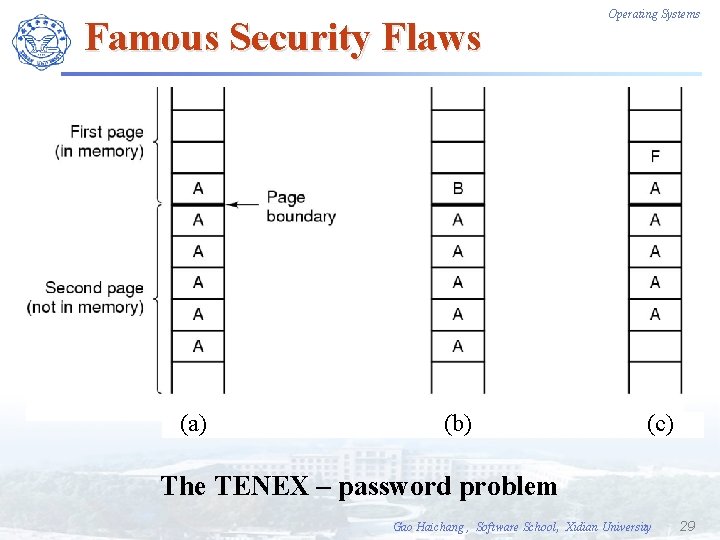
Famous Security Flaws (a) (b) Operating Systems (c) The TENEX – password problem Gao Haichang , Software School, Xidian University 29

Design Principles for Security 1. System design should be public 2. Default should be no access 3. Check for current authority 4. Give each process least privilege possible 5. Protection mechanism should be 6. - simple - uniform - in lowest layers of system Operating Systems Scheme should be psychologically acceptable And … keep it simple Gao Haichang , Software School, Xidian University 30

Operating Systems Lesson 2

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 32

Operating Systems Network Security F External threat ³ code transmitted to target machine ³ code executed there, doing damage F Goals of virus writer ³ quickly spreading virus ³ difficult to detect ³ hard to get rid of F Virus = program can reproduce itself ³ attach its code to another program ³ additionally, do harm Gao Haichang , Software School, Xidian University 33

Virus Damage Scenarios Operating Systems F Blackmail F Denial of service as long as virus runs F Permanently damage hardware F Target a competitor's computer ³ do harm ³ espionage 间谍活动 F Intra-corporate dirty tricks ³ sabotage (阴谋破坏) another corporate officer's files Gao Haichang , Software School, Xidian University 34

How Viruses Work Operating Systems F Virus written in assembly language F Inserted into another program ³ use tool called a “dropper” F Virus dormant (潜伏) until program executed ³ then infects other programs ³ eventually executes its “payload” Gao Haichang , Software School, Xidian University 35

How Viruses Work (1) Operating Systems F Several kinds of Viruses based on what is infected ³ companion ³ executable program ³ memory ³ boot sector ³ device driver ³ macro ³ source code viruses Gao Haichang , Software School, Xidian University 36

How Viruses Work (2) Operating Systems Recursive procedure that finds executable files on a UNIX system Virus could infect them all Gao Haichang , Software School, Xidian University 37

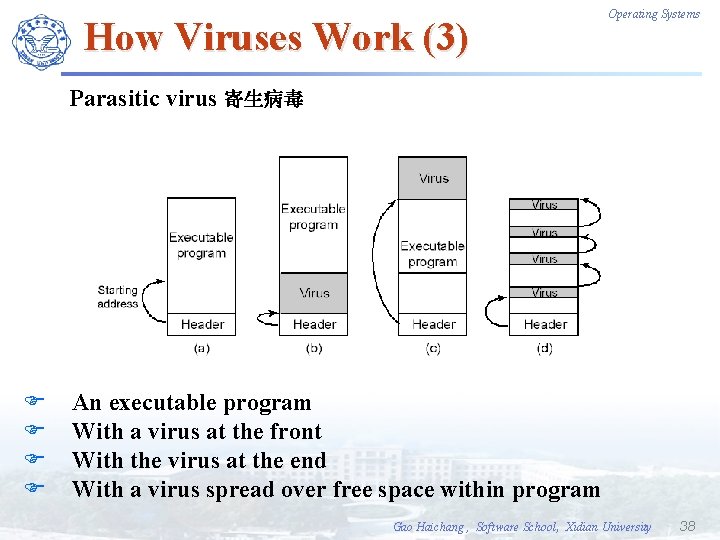
How Viruses Work (3) Operating Systems Parasitic virus 寄生病毒 F F An executable program With a virus at the front With the virus at the end With a virus spread over free space within program Gao Haichang , Software School, Xidian University 38

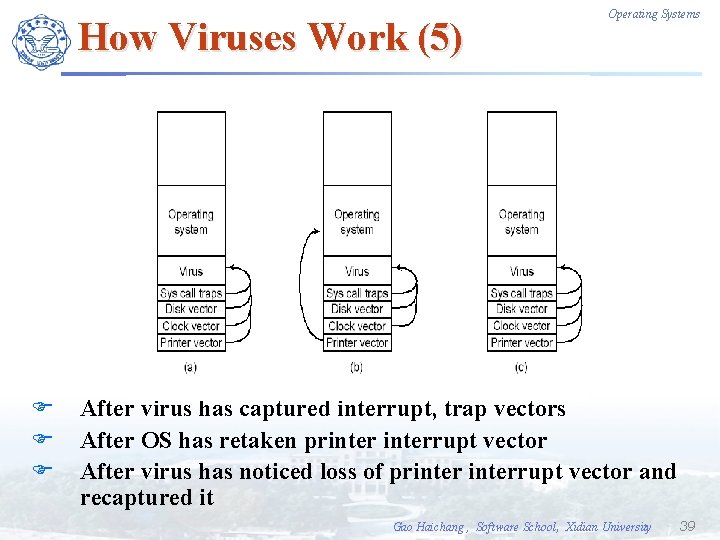
How Viruses Work (5) F F F Operating Systems After virus has captured interrupt, trap vectors After OS has retaken printerrupt vector After virus has noticed loss of printerrupt vector and recaptured it Gao Haichang , Software School, Xidian University 39

How Viruses Spread Operating Systems F Virus placed where likely to be copied F When copied ³ infects ³ may programs on hard drive, floppy try to spread over LAN F Attach to innocent (无辜) looking email ³ when it runs, use mailing list to replicate Gao Haichang , Software School, Xidian University 40

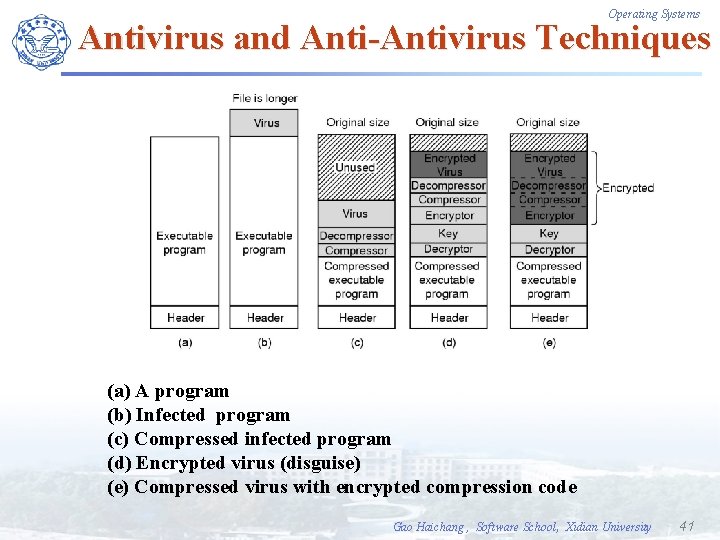
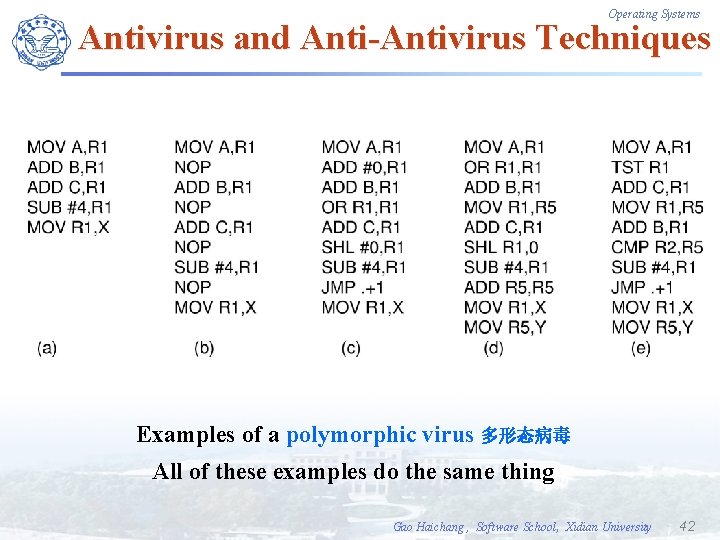
Operating Systems Antivirus and Anti-Antivirus Techniques (a) A program (b) Infected program (c) Compressed infected program (d) Encrypted virus (disguise) (e) Compressed virus with encrypted compression code Gao Haichang , Software School, Xidian University 41

Operating Systems Antivirus and Anti-Antivirus Techniques Examples of a polymorphic virus 多形态病毒 All of these examples do the same thing Gao Haichang , Software School, Xidian University 42

Operating Systems Antivirus and Anti-Antivirus Techniques F Integrity checkers F Behavioral checkers F Virus avoidance ³ good OS ³ install only shrink-wrapped software ³ use antivirus software ³ do not click on attachments to email ³ frequent backups F Recovery from virus attack ³ halt computer, reboot from safe disk, run antivirus Gao Haichang , Software School, Xidian University 43

The Internet Worm (Morris) Operating Systems F Consisted of two programs ³ bootstrap ³ the to upload worm itself F Worm first hid its existence F Next replicated itself on new machines Gao Haichang , Software School, Xidian University 44

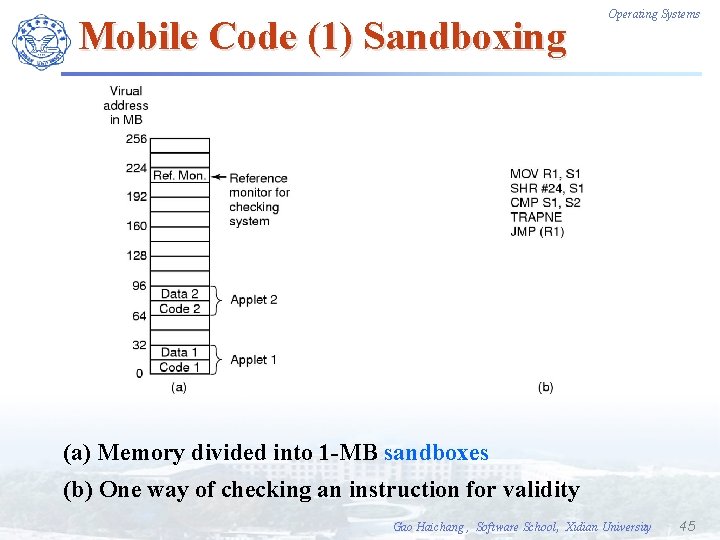
Mobile Code (1) Sandboxing Operating Systems (a) Memory divided into 1 -MB sandboxes (b) One way of checking an instruction for validity Gao Haichang , Software School, Xidian University 45

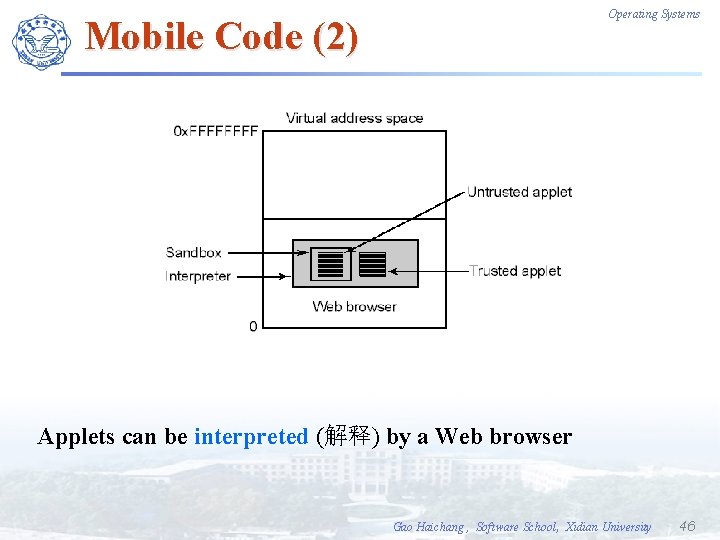
Operating Systems Mobile Code (2) Applets can be interpreted (解释) by a Web browser Gao Haichang , Software School, Xidian University 46

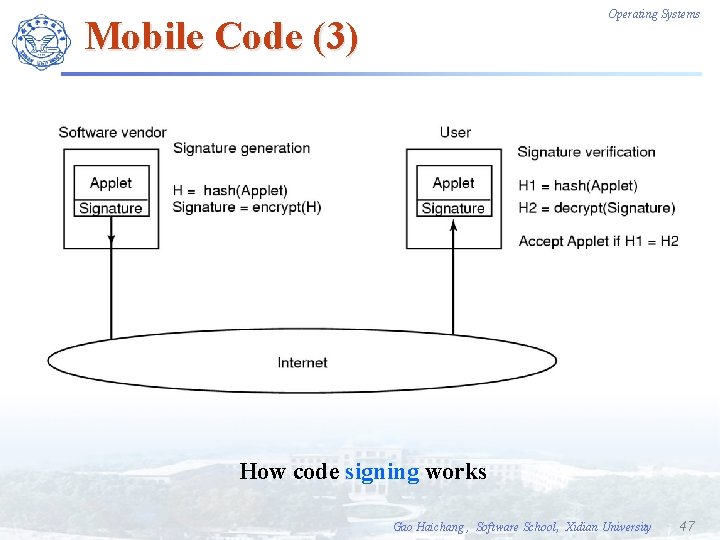
Operating Systems Mobile Code (3) How code signing works Gao Haichang , Software School, Xidian University 47

Operating Systems Java Security F A type safe language ³ compiler rejects attempts to misuse variable F Checks include … 1. Attempts to forge 伪造 pointers 2. Violation of access restrictions on private class members 3. Misuse of variables by type 4. Generation of stack over/underflows 5. Illegal conversion of variables to another type Gao Haichang , Software School, Xidian University 48

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 49

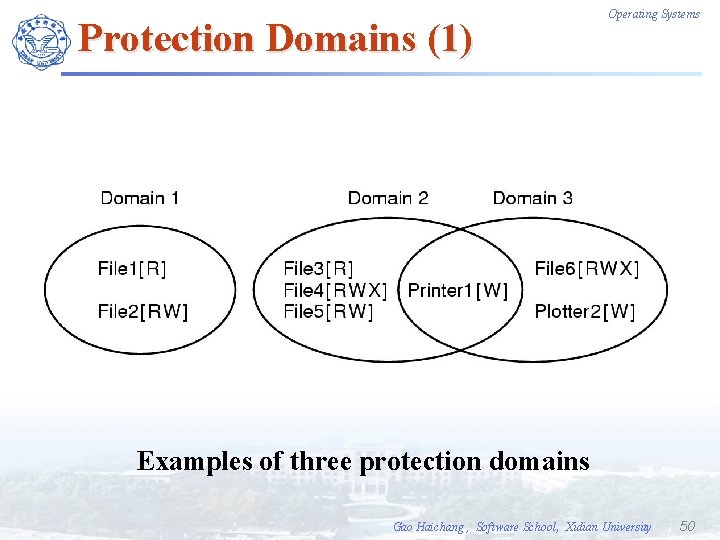
Protection Domains (1) Operating Systems Examples of three protection domains Gao Haichang , Software School, Xidian University 50

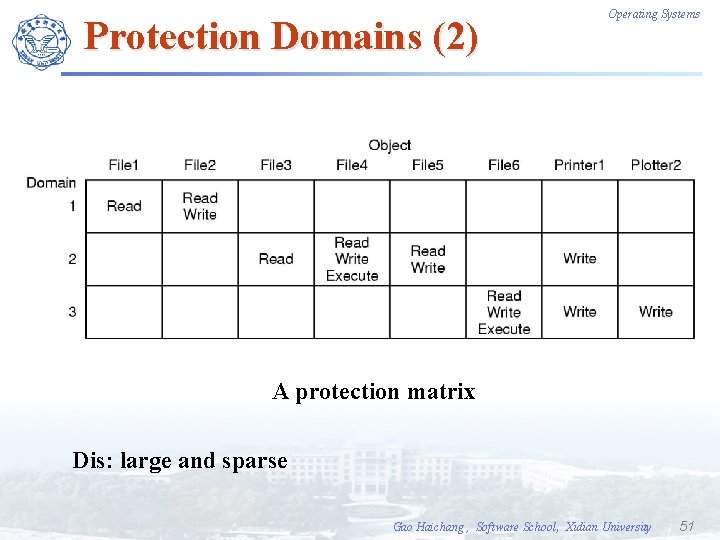
Protection Domains (2) Operating Systems A protection matrix Dis: large and sparse Gao Haichang , Software School, Xidian University 51

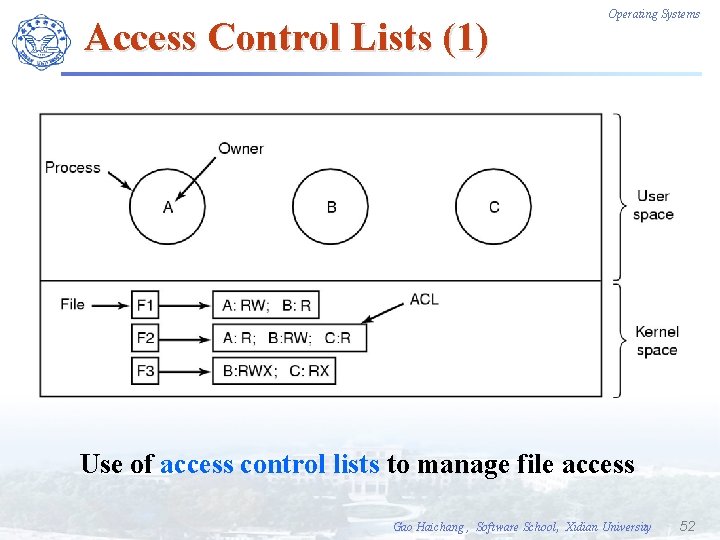
Access Control Lists (1) Operating Systems Use of access control lists to manage file access Gao Haichang , Software School, Xidian University 52

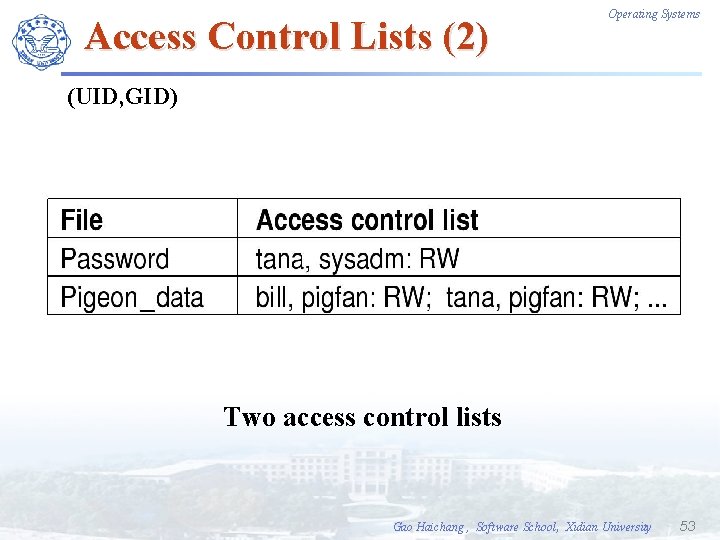
Access Control Lists (2) Operating Systems (UID, GID) Two access control lists Gao Haichang , Software School, Xidian University 53

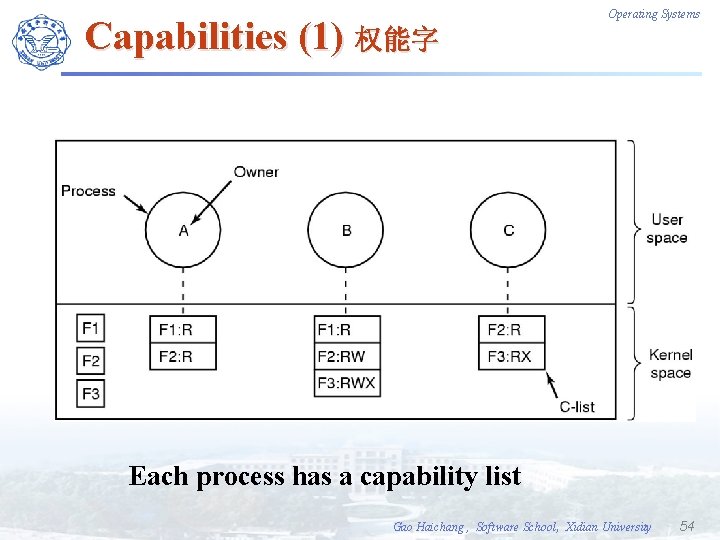
Capabilities (1) 权能字 Operating Systems Each process has a capability list Gao Haichang , Software School, Xidian University 54

Operating Systems Capabilities (2) F Capability list must be protected from user tampering 篡改 1. First way, require a tagged architecture 2. Second way, keep the C-list inside the OS 3. Third way, keep the C-list in user space, but manage the capabilities cryptographically Gao Haichang , Software School, Xidian University 55

Chapter 9: Security ³ 9. 1 The security environment ³ 9. 2 Basics of cryptography ³ 9. 3 User authentication ³ 9. 4 Attacks from inside the system ³ 9. 5 Attacks from outside the system ³ 9. 6 Protection mechanisms ³ 9. 7 Trusted systems Operating Systems Gao Haichang , Software School, Xidian University 56

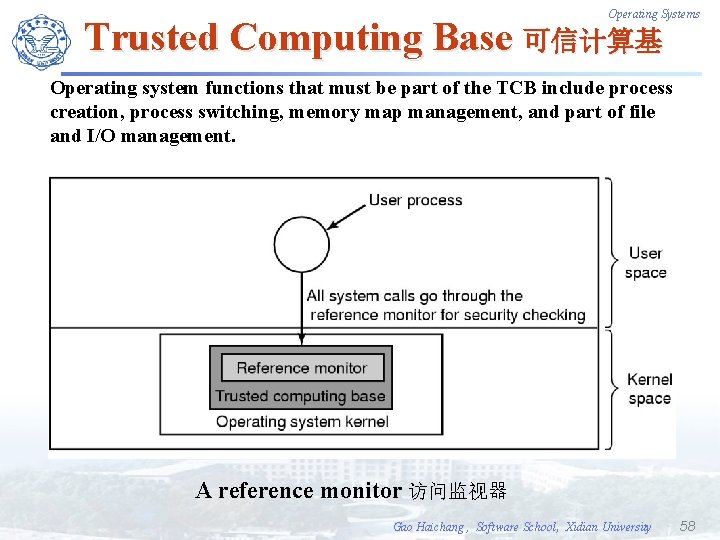
Trusted Computing Base F Is it possible to build a secure computer system? F If so, why is it not done? ³ user habits ³ feature is the enemy of security Operating Systems Gao Haichang , Software School, Xidian University 57

Operating Systems Trusted Computing Base 可信计算基 Operating system functions that must be part of the TCB include process creation, process switching, memory map management, and part of file and I/O management. A reference monitor 访问监视器 Gao Haichang , Software School, Xidian University 58

Operating Systems Formal Models of Secure Systems F Six primitive operations on the protection matrix that can be used as a base to model any protection system. (protection commands) ³ create object, delete object ³ create domain, delete domain ³ insert right, remove right Gao Haichang , Software School, Xidian University 59

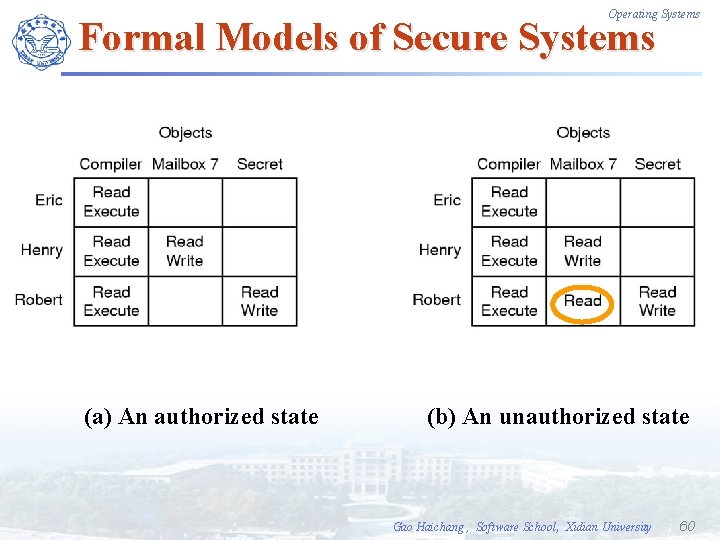
Operating Systems Formal Models of Secure Systems (a) An authorized state (b) An unauthorized state Gao Haichang , Software School, Xidian University 60

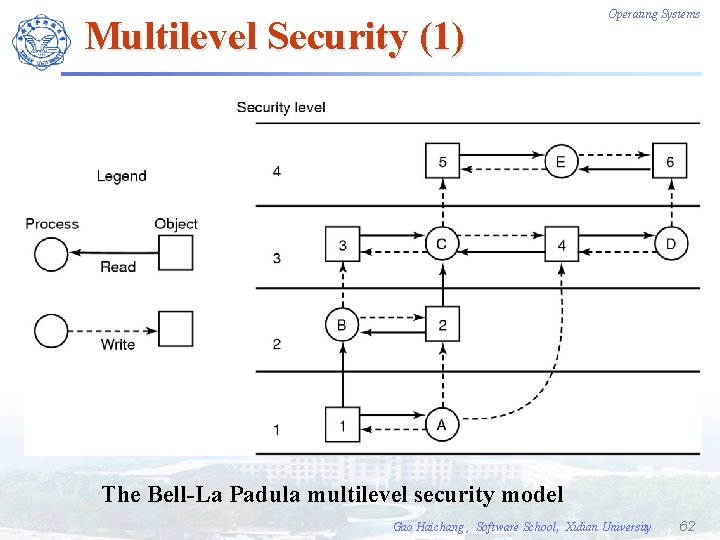
Multilevel Security Operating Systems F Discretionary access control 自主访问控制: allow individual users to determine who may read and write their files and other objects. F Mandatory access control 强制访问控制: the stated security policies are enforced by the system. F Bell-La Padula model (popular multilevel security model) ³ The simple security property. A process running at security level k can read only objects at its level or lower. ³ The * property. A process running at security level k can write only objects at its level or higher. Gao Haichang , Software School, Xidian University 61

Multilevel Security (1) Operating Systems The Bell-La Padula multilevel security model Gao Haichang , Software School, Xidian University 62

Multilevel Security (2) Operating Systems Dis of Bell-La Padula: devise to keep secrets, but not guarantee the integrity of the data. F The Biba Model ³ Simple integrity principle. process can write only objects at its security level or lower. ³ The integrity * property. process can read only objects at its security level or higher. Gao Haichang , Software School, Xidian University 63

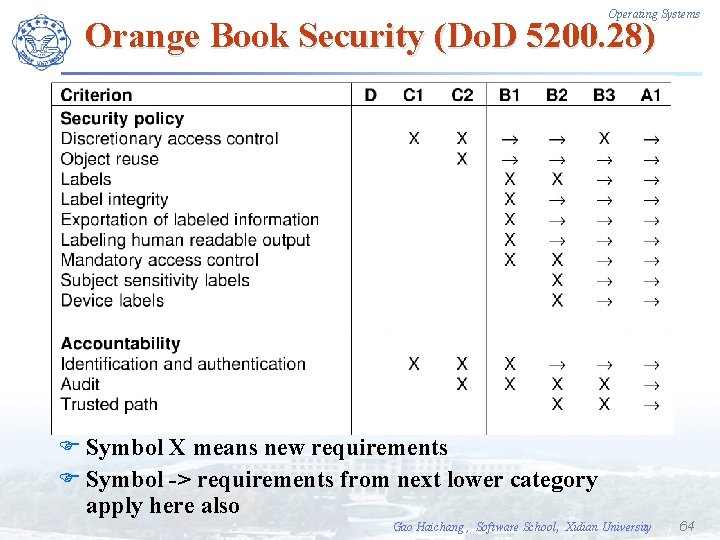
Operating Systems Orange Book Security (Do. D 5200. 28) F Symbol X means new requirements F Symbol -> requirements from next lower category apply here also Gao Haichang , Software School, Xidian University 64

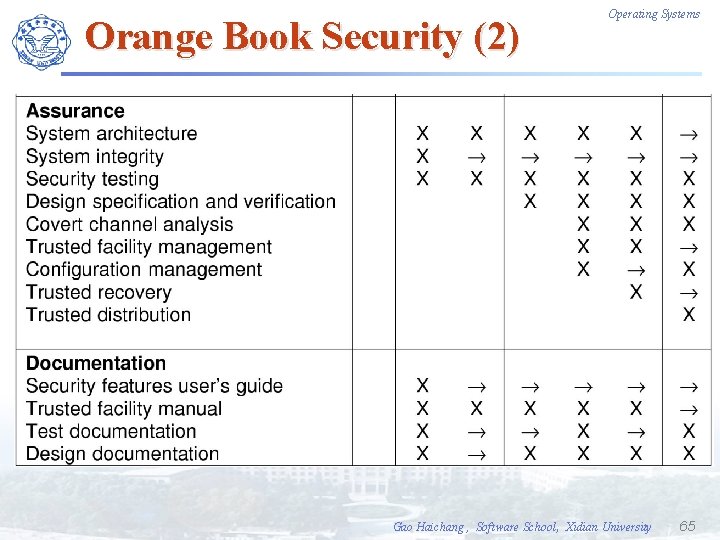
Orange Book Security (2) Operating Systems Gao Haichang , Software School, Xidian University 65

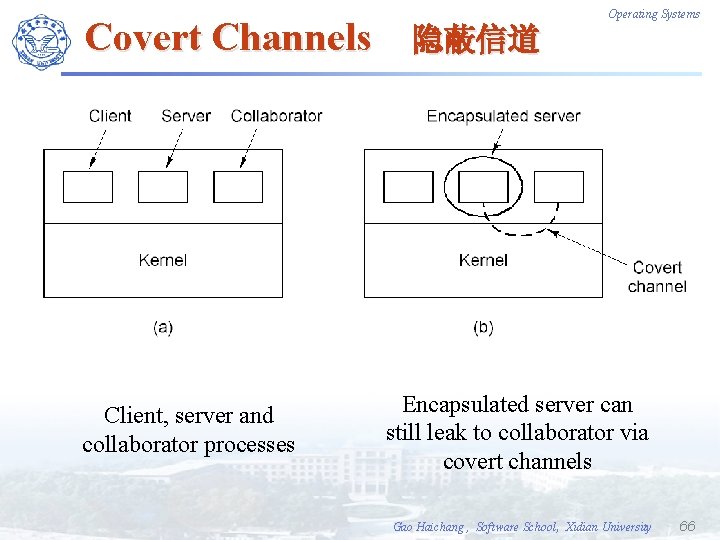
Covert Channels Client, server and collaborator processes Operating Systems 隐蔽信道 Encapsulated server can still leak to collaborator via covert channels Gao Haichang , Software School, Xidian University 66

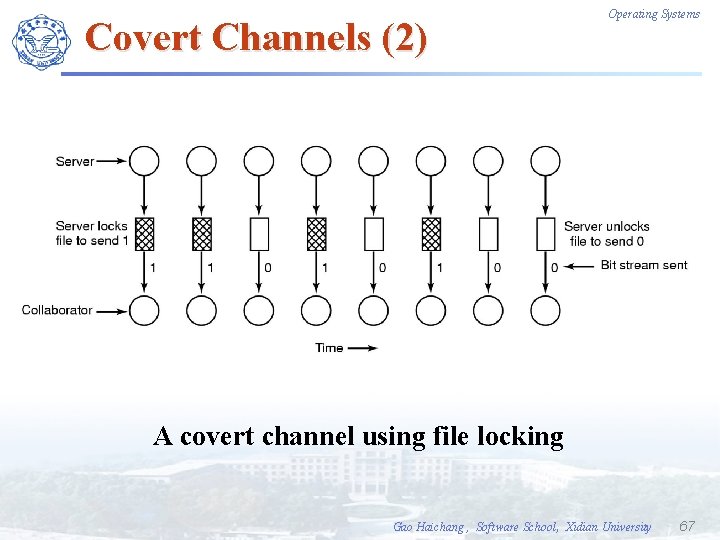
Covert Channels (2) Operating Systems A covert channel using file locking Gao Haichang , Software School, Xidian University 67

Covert Channels (3) Operating Systems F Pictures appear the same F Picture on right has text of 5 Shakespeare plays ³ encrypted, inserted into low order bits of color values Zebras Hamlet , King Lear, Macbeth , Merchant of Venice, Julius Caesar Gao Haichang , Software School, Xidian University 68