Operating Systems ECE 344 OS Hardware Trap Instruction






- Slides: 13

Operating Systems ECE 344 OS Hardware: Trap Instruction Ashvin Goel ECE University of Toronto

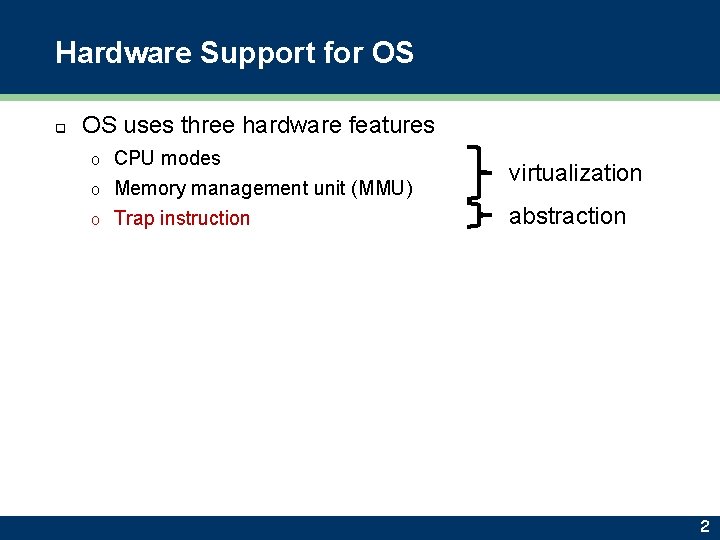
Hardware Support for OS q OS uses three hardware features CPU modes o Memory management unit (MMU) o Trap instruction o virtualization abstraction 2

Trap q q Review: why can’t programs access devices directly, e. g. , read data from disk? So how can a program access a device? o q It needs to run OS code Can a program invoke OS code directly? No: OS code is isolated from user code using MMU o No: OS code needs to run in kernel mode o q q User code needs some way to switch to kernel mode H/W provides trap instruction for switching to kernel mode and running OS code 3

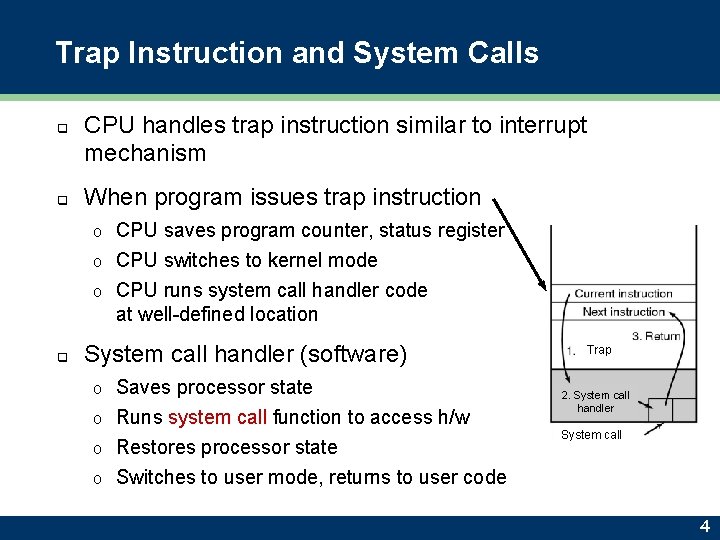
Trap Instruction and System Calls q q CPU handles trap instruction similar to interrupt mechanism When program issues trap instruction o CPU saves program counter, status register CPU switches to kernel mode o CPU runs system call handler code at well-defined location o q System call handler (software) Saves processor state o Runs system call function to access h/w o Restores processor state o Switches to user mode, returns to user code o Trap 2. System call handler System call 4

System Calls q OS functions that provide an abstraction of h/w q Programs use trap instruction to invoke system calls q Set of system calls is OS API q Examples: Create/destroy thread or process o Allocate/deallocate memory from system o Read/write a file o 5

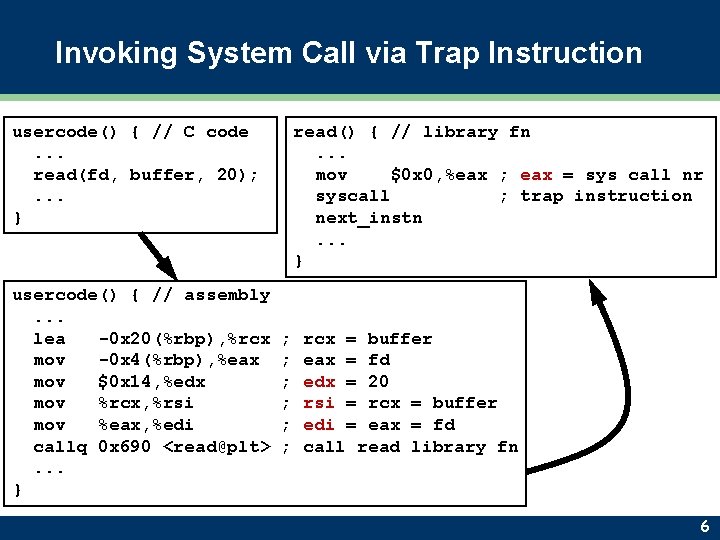
Invoking System Call via Trap Instruction usercode() { // C code. . . read(fd, buffer, 20); . . . } usercode() { // assembly. . . lea -0 x 20(%rbp), %rcx mov -0 x 4(%rbp), %eax mov $0 x 14, %edx mov %rcx, %rsi mov %eax, %edi callq 0 x 690 <read@plt>. . . } read() { // library fn. . . mov $0 x 0, %eax ; eax = sys call nr syscall ; trap instruction next_instn. . . } ; ; ; rcx = buffer eax = fd edx = 20 rsi = rcx = buffer edi = eax = fd call read library fn 6

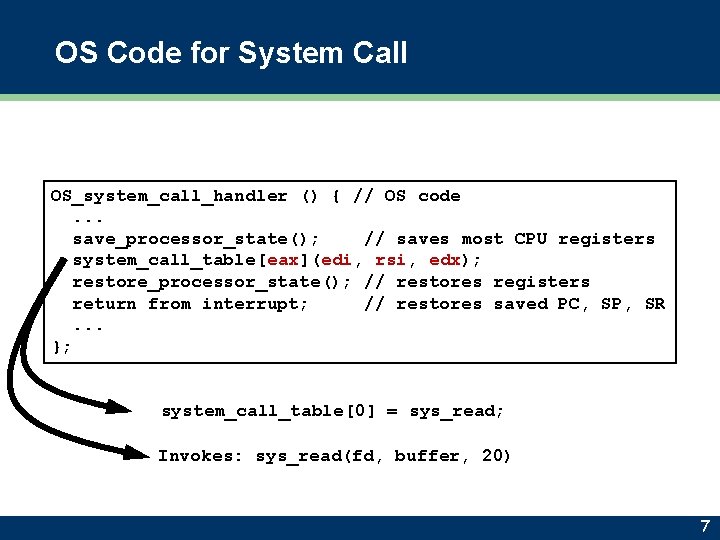
OS Code for System Call OS_system_call_handler () { // OS code. . . save_processor_state(); // saves most CPU registers system_call_table[eax](edi, rsi, edx); restore_processor_state(); // restores registers return from interrupt; // restores saved PC, SP, SR. . . }; system_call_table[0] = sys_read; Invokes: sys_read(fd, buffer, 20) 7

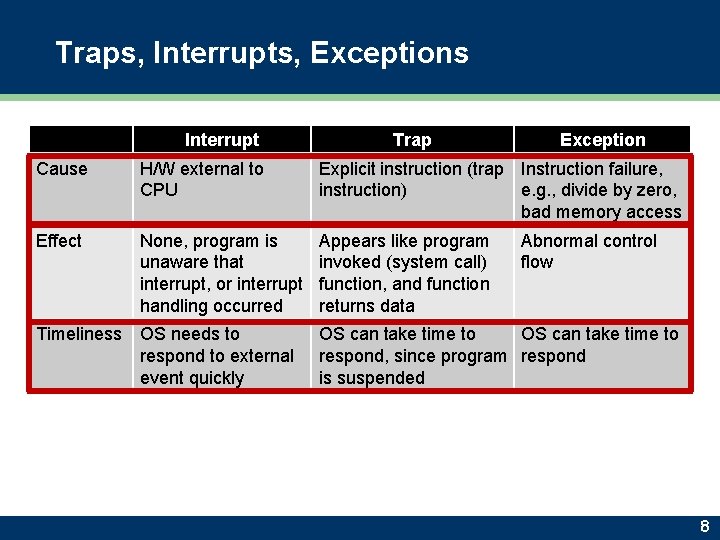
Traps, Interrupts, Exceptions Interrupt Trap Exception Cause H/W external to CPU Explicit instruction (trap Instruction failure, instruction) e. g. , divide by zero, bad memory access Effect None, program is unaware that interrupt, or interrupt handling occurred Appears like program invoked (system call) function, and function returns data Timeliness OS needs to respond to external event quickly OS can take time to respond, since program respond is suspended Abnormal control flow 8

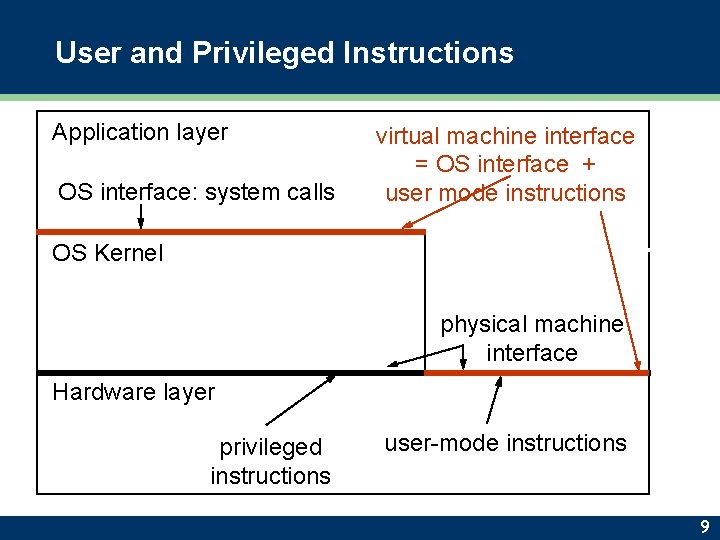
User and Privileged Instructions Application layer OS interface: system calls virtual machine interface = OS interface + user mode instructions OS Kernel physical machine interface Hardware layer privileged instructions user-mode instructions 9

Summary q OS manages h/w by virtualizing and abstracting h/w q Virtualization CPU modes: enable running programs with limited privileges, so that they do not have full access to h/w o MMU: helps provide memory isolation o q Abstraction o Trap: provides a secure way to enter the kernel, enables programs to access devices and OS services via system calls (OS API) 10

Think Time: Program Operation q What if a program tries to cheat? 1. 2. 3. 4. What happens if it invokes a privileged instruction directly? What if a running program doesn’t make a system call to the OS and hence hogs the CPU? What stops the running program from disabling an interrupt? What happens if a program sends a bogus or malicious argument to a system call? 11

Think Time: OS Operation q How does the trap instruction provide a “secure” way to enter the kernel? q Why is the OS not a normal program? q How does the OS solve these problems: Time sharing the CPU among programs? o Space sharing memory among programs? o 12

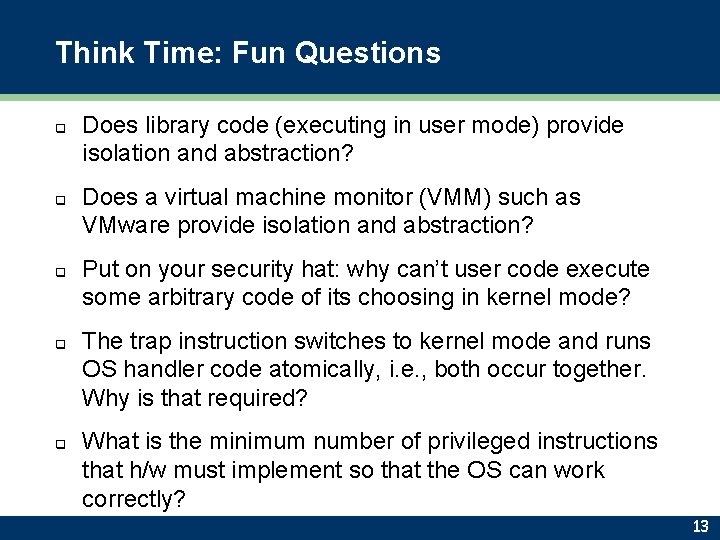
Think Time: Fun Questions q q q Does library code (executing in user mode) provide isolation and abstraction? Does a virtual machine monitor (VMM) such as VMware provide isolation and abstraction? Put on your security hat: why can’t user code execute some arbitrary code of its choosing in kernel mode? The trap instruction switches to kernel mode and runs OS handler code atomically, i. e. , both occur together. Why is that required? What is the minimum number of privileged instructions that h/w must implement so that the OS can work correctly? 13