Operating Systems Chapter 1 Introduction Instr Yusuf Altunel
























- Slides: 53

Operating Systems Chapter 1: Introduction Instr: Yusuf Altunel IKU Department of Computer Engineering (212) 498 42 10 y. altunel@iku. edu. tr 1

CONTENT 1. 1 What is an operating system 1. 5 Operating system concepts 1. 6 System calls 1. 7 Operating system structure 2

Operating System (OS) • Definition: A software to – provide simpler hardware interfaces • for the user programs – manage and keep track of all devices • • processors, main memory, disks, printers, keyboard, data display (monitor), network interfaces, other input/output devices – use devices correctly and optimally 3

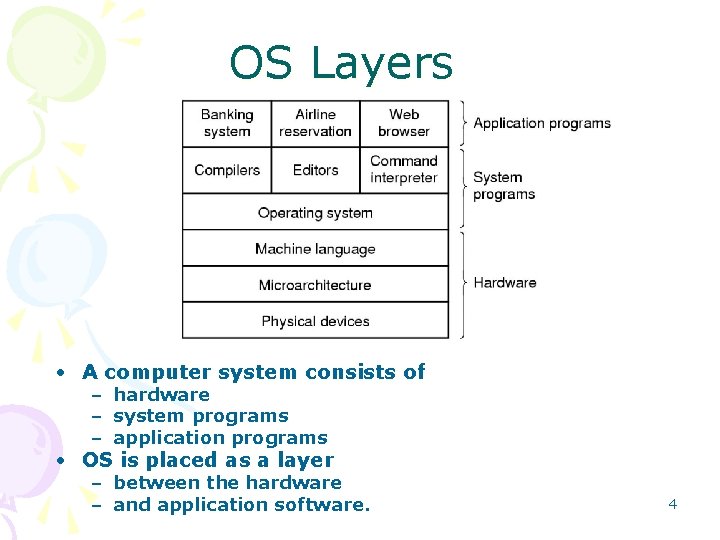
OS Layers • A computer system consists of – hardware – system programs – application programs • OS is placed as a layer – between the hardware – and application software. 4

Hardware Layers • Physical layer: – The actual hardware – physical devices consisting of • • • integrated circuit chips, wires, power supplies, cathode ray tubes, and similar physical devices. 5

Hardware Layers • Microarchitecture level: – The physical devices are grouped • to form functional units. – This layer contains • some registers – internal to CPU (Central Processing Unit) • and a data path – containing an arithmetic logic unit. 6

Hardware Layers • ISA (Instruction Set Architecture) level: – the hardware and instructions • visible to an assembly language program – This level is often called machine language. – to execute some set of instructions. • can be carried out in – one data path cycle; – or multiple data path cycles. • These instructions may use – registers or other hardware facilities. 7

Hardware Layers: ISA Cont. • The machine language – – between 50 and 300 instructions, for moving data around the machine, performing arithmetic operations, and comparing values. • The input/output devices – controlled by loading values – into special device registers. • For example, – command a disk by loading values into its registers • • the disk address, main memory address, byte count, and direction (read or write). 8

System Layers: OS • Consists of a layer of software – (Partially) hides the hardware complexity – to provide the programmer • a more convenient set of instructions • Example – read block from file • is conceptually simple operation – otherwise you have to worry about details • moving disk heads, • waiting for them to settle down, • . . . 9

System Layers: The Rest • the rest of the system software – command interpreter (shell), – window systems, – compilers, – editors, –. . . • These programs are – supplied by the computer manufacturer – not part of the operating system 10

OS Software • is the portion of the software – runs in kernel or supervisor mode. – protected from user. • User mode applications – Compilers and editors run in user mode. • If a user does not like a particular compiler, • he is free to write his own if he so chooses; • Kernel mode applications – protected by hardware • against modification attempts – user is not free to write • his own clock interrupt handler! 11

OS Software • user programs run in kernel mode – help the operating system – perform privileged functions. • Example – program to change password – is not part of the operating system • and does not run in kernel mode, – carries out a sensitive function: • change into kernel mode 12

Application Layer • Above the system programs – all of the application programs. • purchased or written by the users – to solve their particular problems • word processing, • spreadsheets, • engineering calculations, • storing information in a database. 13

What is an Operating System? • It is an extended machine – Hides the messy details of HW operations – Presents user with a virtual machine • easier to use • It is a resource manager – Each program gets – resource time and space 14

OS as an Extended Machine • Hiding hardware details: – hides the truth about the HW • from the programmer – presents a nice, simple view of HW. – Example: Files • shields the programmer form the disk access • presents a simple file-oriented interface • Concealing unpleasant business – interrupts, – timers, – memory management, – other low-level features. . . 15

OS as a Resource Manager • sharing resources in two ways – Time multiplexing • Share the time of the resource – Space multiplexing • Share the space of the resource 16

Time Multiplexing • Resources are used interchangeably – by different programs or users • Example: CPU – User 1: • Allocate the resource, • use it, • leave it – User 2: • Allocate the resource, • use it, • leave it –. . . 17

Space multiplexing • Each user (program) gets – a part of the resource. • Example 1: main memory – divided up among several running programs – each one can be resident at the same time – keep track of • who is using which memory block • Example 2: hard disc – a single disk can hold files • from many users at the same time. – allocate disk space for each file – keep track of • who is using which disk blocks 18

The Operating System Zoo • Mainframe operating systems • Server operating systems • Multiprocessor operating systems • Personal computer operating systems • Real-time operating systems • Embedded operating systems • Smart card operating systems 19

OS CONCEPTS • Processes • Deadlocks • Memory Management • Input/Output • Files • Security • The Shell 20

Processes • Process: A program in execution. • Address space: – The memory portion reserved for the process – The process makes read or write operations. – Contains • the executable program, • the program’s data, • and its stack. • Register assignment : – Program counter, – stack pointer, – other hardware registers. 21

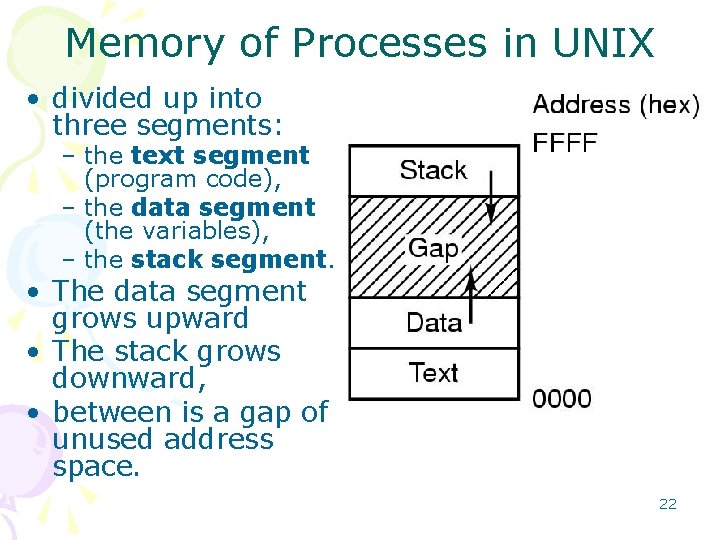
Memory of Processes in UNIX • divided up into three segments: – the text segment (program code), – the data segment (the variables), – the stack segment. • The data segment grows upward • The stack grows downward, • between is a gap of unused address space. 22

Processes in Timesharing OSs • To share the system time – between the processes • the jobs are divided into processes • OS assigns – a priority level – a time quota • OS periodically checks – the time used by each process. • OS decides to suspend the active process – When the process time ends – If a new process higher in privilege arrives • OS must later restart the process – in exactly the same state when it was stopped. – OS must save the process information • open file pointers, • register status, . . . 23

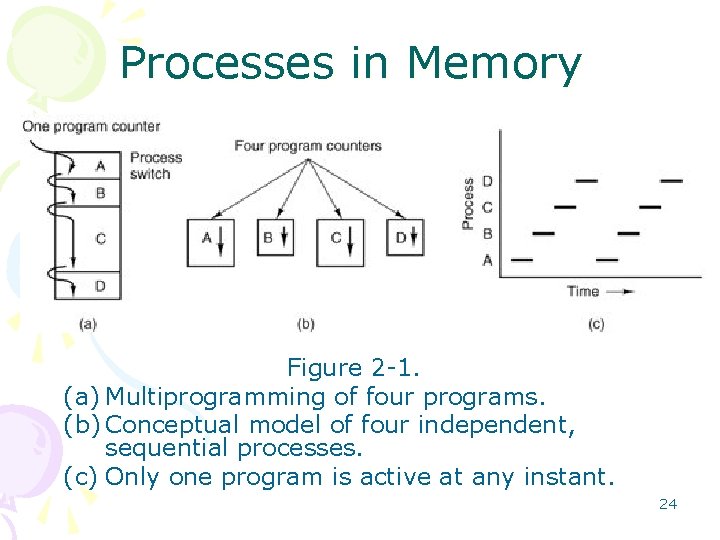
Processes in Memory Figure 2 -1. (a) Multiprogramming of four programs. (b) Conceptual model of four independent, sequential processes. (c) Only one program is active at any instant. 24

Process Table • to keep the information – about the existing (running) processes • maintained by the OS • How to create processes – OS creates a new process – when a user starts the execution of a program. • Process structure (Tree) – A process may create • a child process (fork) – child processes may further create • new child processes and so on. – a tree structure appears 25

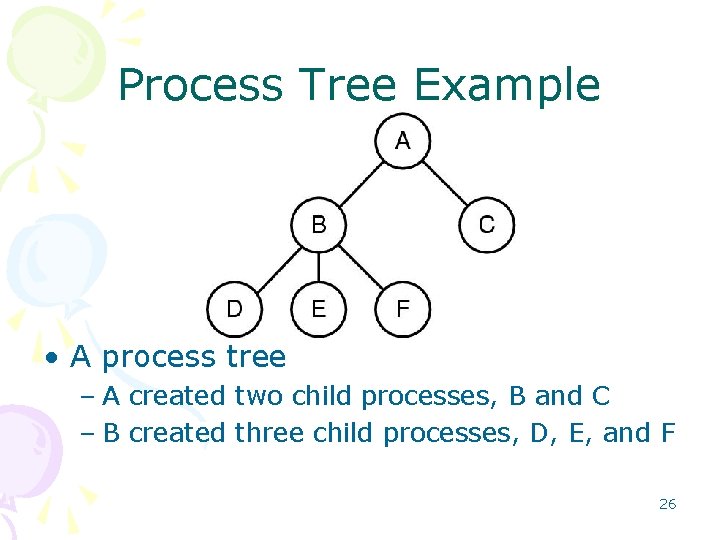
Process Tree Example • A process tree – A created two child processes, B and C – B created three child processes, D, E, and F 26

Interprocess Communication • Related processes can cooperate – to get some job is done. • Processes can send and receive messages • Responsibility of the Operating System – manages the messages – signal alarm • to receive a message • to retransmit a lost message • Responsibility of the processes – Requesting received notification – Retransmission of messages • If the message is lost 27

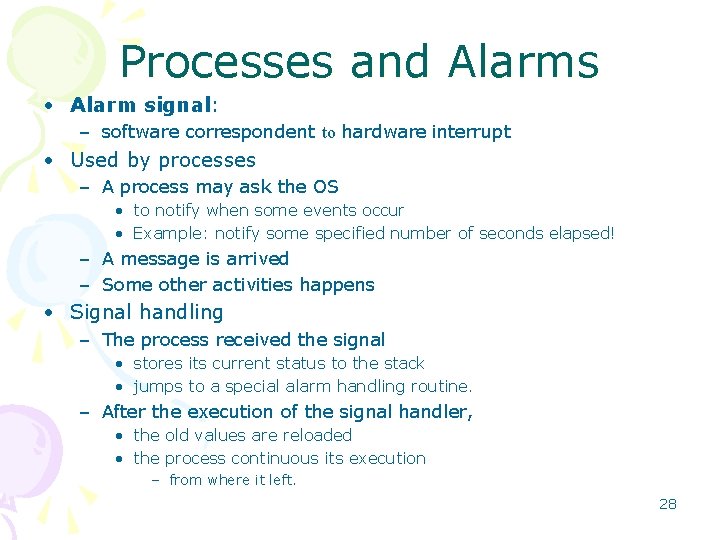
Processes and Alarms • Alarm signal: – software correspondent to hardware interrupt • Used by processes – A process may ask the OS • to notify when some events occur • Example: notify some specified number of seconds elapsed! – A message is arrived – Some other activities happens • Signal handling – The process received the signal • stores its current status to the stack • jumps to a special alarm handling routine. – After the execution of the signal handler, • the old values are reloaded • the process continuous its execution – from where it left. 28

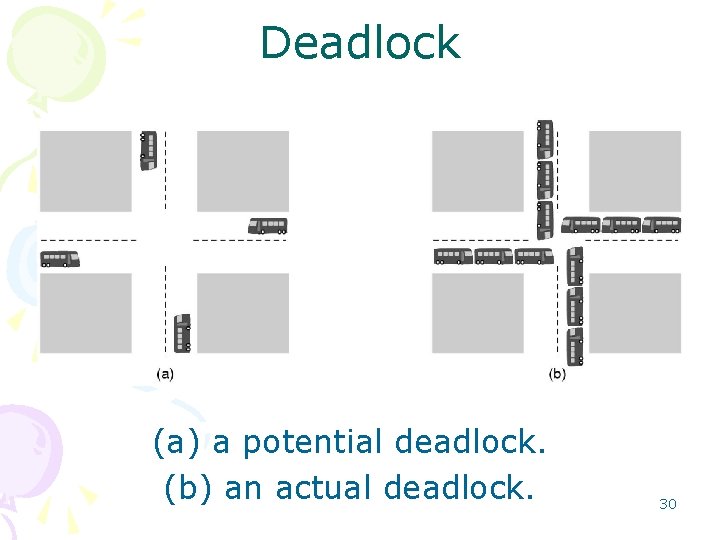
Deadlocks • When two or more processes – need to access a restricted resource, – can get into a stalemate situation • Such situations are called deadlock. • Deadlocks – waste the system power • they are not deserved, – catching prevention algorithms available – but this is sometimes more costly 29

Deadlock (a) a potential deadlock. (b) an actual deadlock. 30

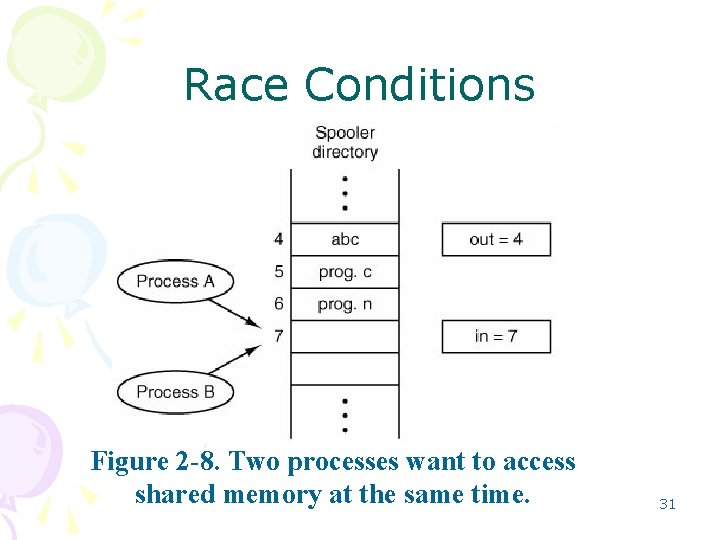
Race Conditions Figure 2 -8. Two processes want to access shared memory at the same time. 31

Memory Management • Simple OSs: one program – allows only one program • to execute in memory at a time. – A second can only be executed, • when the first program is removed • and the second one placed in memory. • Sophisticated OSs: multiple programs – – Memory is partitioned Each program holds its own partition Programs are executed interchangeably. Attention! • protect memory against other programs 32

Address Space Management • Process must be able – to think the execution starts – from a memory space starting from 0 • Process needs a sufficiently large memory – to execute smoothly • Swapping: – If the memory is full: – swap between the memory and disk. • Memory space allocation – OS must dynamically • allocates and deallocates • pieces of memory space. 33

Input/Output • Many Input/Output devices • Different types of Input/Output devices • OS must be able – to deal with many devices – to treat differently • to each type of operation. • Example: – disks need block read and write, – the keyboard is character oriented. 34

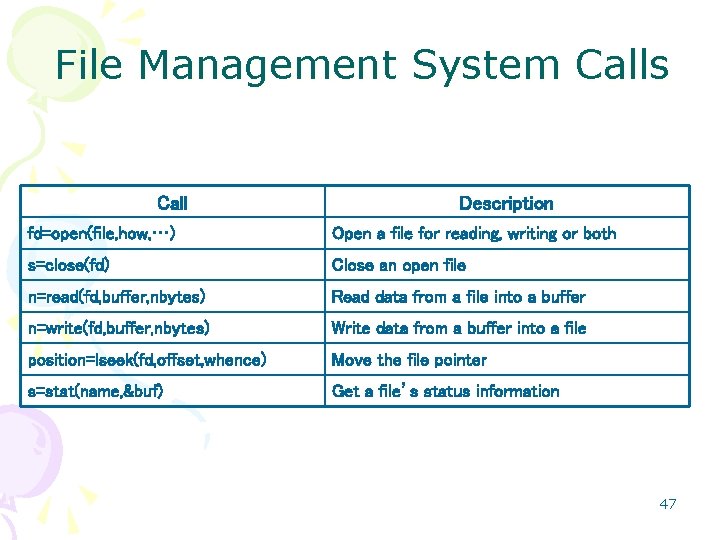
File Management • File system presents the programmer – a nice, clean abstract model of • device-independent files – hide the peculiarities of • the disk and other I/O devices • System calls for file management – – create files, remove files, read files, write files. – – locate on the disk open read close • Using a file: 35

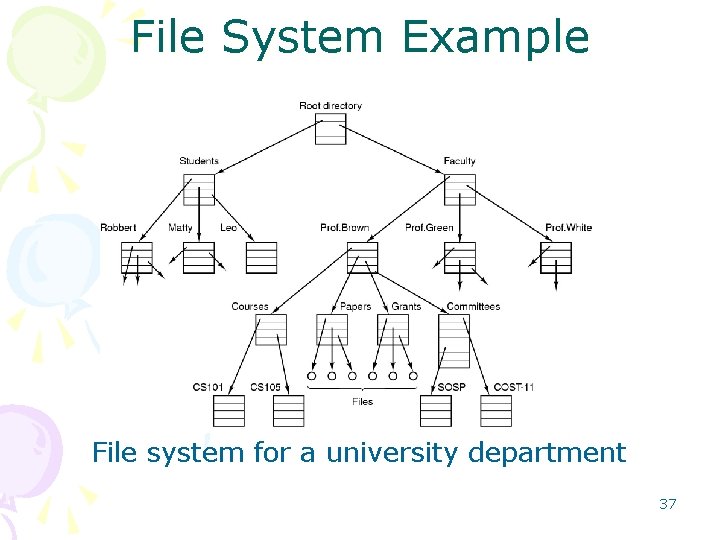
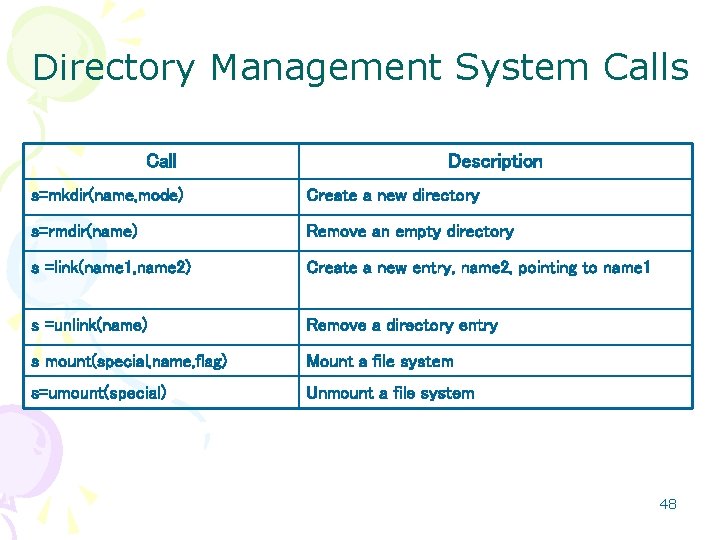
Directories • A concept used to group files together. • System calls are needed – to create and remove directories. – to put an existing file in a directory, – to remove a file from the directory. • Directory Hierarchy – A hierarchy of the directories – some directories contain others • Path: The location of a file in the hierarch – “/” or “” is used – to separate directory and file names in paths – Example: /Faculty/Prof. Brown/Courses/CS 101 • Root directory: – The top-most directory in the hierarchy. – An absolute path always starts with the root directory. • Working directory: – each process has a current directory – used to read and store information. 36

File System Example File system for a university department 37

Files • File descriptor: – a number to identify the file – used in subsequent operations • Mounting: – Attaching removable media • CD ROMs, floppies, etc – to the file system. • Special files: – to make I/O devices look like files. – read and write using the file managment system calls • as are used for reading and writing files. – special file types • block special files • character special files • Pipes 38

Special Files • Block special files: – to model the devices • consisting of randomly addressable blocks • Block special device example: Discs – Example • directly access the 4 th block of data. • Character special files: – to model devices • read and write data character by character – Examples: • printers, modems, and other character stream devices – special files in UNIX • are kept in /dev directory. • Pipe: – A sort of pseudo file • to connect two processes. – processes A and B can talk using pipe – to send data to B, • A writes on pipe • Process B reads the data from pipe – Interprocess communication in UNIX • looks very much like ordinary file operations 39

Security • System resources must be protected – against un-authorized users. • UNIX file protection – assigning 9 -bit binary protection code. – three fields of protection code: • the owner (3 - rwx bits) • owner’s group members (3 - rwx bits) • everyone else (3 - rwx bits) • Protection fields: – rwx : represents the right to read – rwx : represents the right to write – rwx : represents the right to execute • Example: rwx r-x --x – the owner (rwx): • can read, write, or execute the file, – owner’s group members (r-x): c • an read or execute but not write the file, – everyone else (--x): can execute but not read or write the file. 40

The Shell • The operating system’s command interpreter, – not part of the operating system, – but used to make certain system calls. • The primary interface – between the user and the operating system. • In UNIX many shells exist. – Examples: sh, csh, ksh, and bash. – sh is the original one • and all others are derived from sh. 41

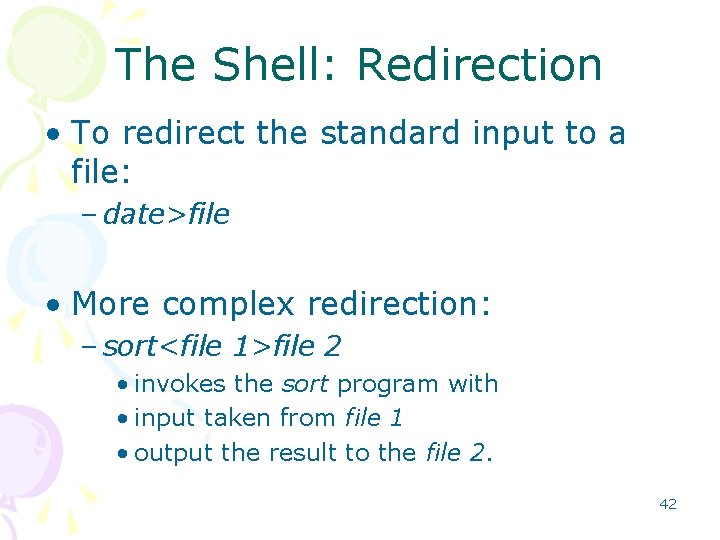
The Shell: Redirection • To redirect the standard input to a file: – date>file • More complex redirection: – sort<file 1>file 2 • invokes the sort program with • input taken from file 1 • output the result to the file 2. 42

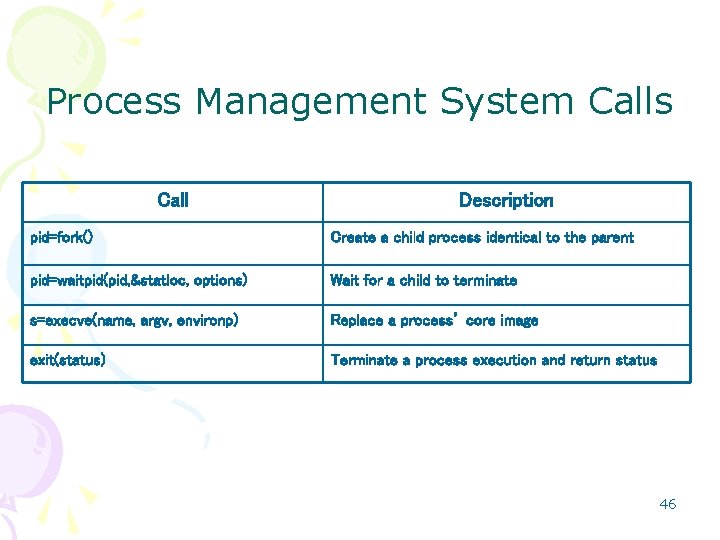
System Calls • The commands – telling the OS what to do • Used when process needs OS service • The interface – between the OS and the user programs • Vary from one OS to another 43

Making System Calls • a process: running user mode • needs system service – Example: reading data from a file • execute a trap or system call instruction • transfers control to the operating system. • OS inspects parameters to figure out – what the calling process wants • Call the OS procedure • Carry out the system call • Return the control to the process – To the next instruction following the system call. 44

System Calls: Example read • It has three parameters: – The file descriptor, – The buffer, – The number of bytes. • it is invoked from C programs (like other system calls) – by calling a library procedure – read. • count=read(fd, buffer, nbytes); • The system call return the number of bytes read in count. – This value is normally the same as nbytes, – but may be smaller, • example, end-of-file is encountered while reading. • If the system call cannot be carried out – count is set to – 1, – and the error number is put in a global variable, errno. – Programs should always check the results of a system call 45

Process Management System Calls Call Description pid=fork() Create a child process identical to the parent pid=waitpid(pid, &statloc, options) Wait for a child to terminate s=execve(name, argv, environp) Replace a process’ core image exit(status) Terminate a process execution and return status 46

File Management System Calls Call Description fd=open(file, how, …) Open a file for reading, writing or both s=close(fd) Close an open file n=read(fd, buffer, nbytes) Read data from a file into a buffer n=write(fd, buffer, nbytes) Write data from a buffer into a file position=lseek(fd, offset, whence) Move the file pointer s=stat(name, &buf) Get a file’s status information 47

Directory Management System Calls Call Description s=mkdir(name, mode) Create a new directory s=rmdir(name) Remove an empty directory s =link(name 1, name 2) Create a new entry, name 2, pointing to name 1 s =unlink(name) Remove a directory entry s mount(special, name, flag) Mount a file system s=umount(special) Unmount a file system 48

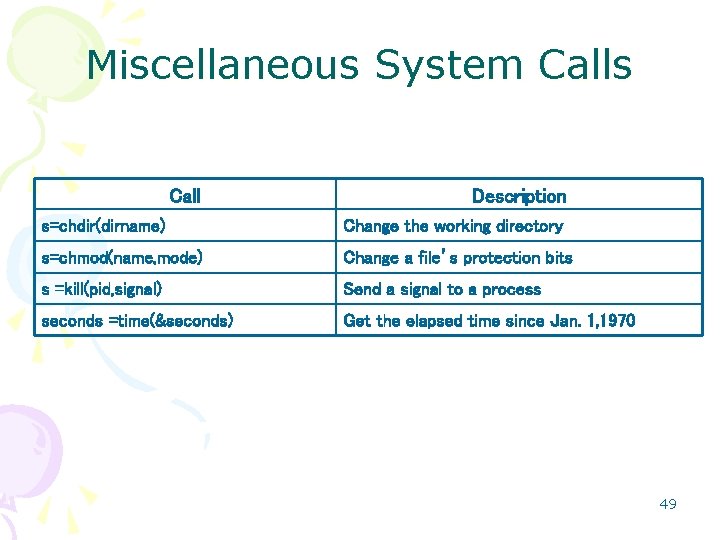
Miscellaneous System Calls Call Description s=chdir(dirname) Change the working directory s=chmod(name, mode) Change a file’s protection bits s =kill(pid, signal) Send a signal to a process seconds =time(&seconds) Get the elapsed time since Jan. 1, 1970 49

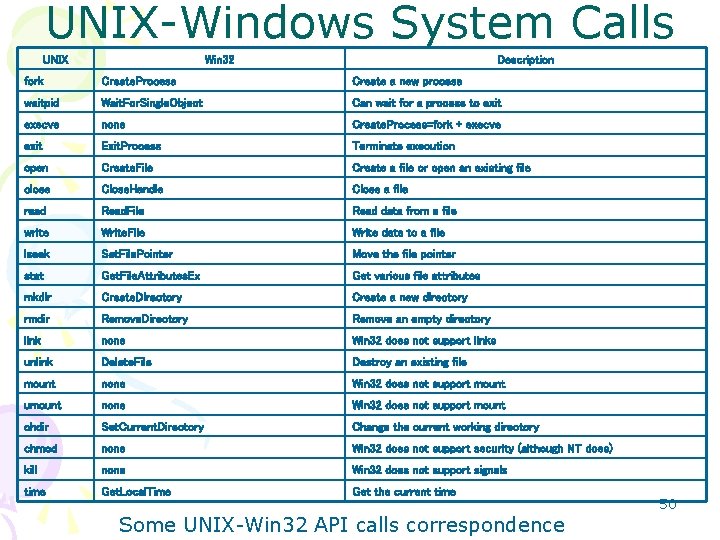
UNIX-Windows System Calls UNIX Win 32 Description fork Create. Process Create a new process waitpid Wait. For. Single. Object Can wait for a process to exit execve none Create. Process=fork + execve exit Exit. Process Terminate execution open Create. File Create a file or open an existing file close Close. Handle Close a file read Read. File Read data from a file write Write. File Write data to a file lseek Set. File. Pointer Move the file pointer stat Get. File. Attributes. Ex Get various file attributes mkdir Create. Directory Create a new directory rmdir Remove. Directory Remove an empty directory link none Win 32 does not support links unlink Delete. File Destroy an existing file mount none Win 32 does not support mount umount none Win 32 does not support mount chdir Set. Current. Directory Change the current working directory chmod none Win 32 does not support security (although NT does) kill none Win 32 does not support signals time Get. Local. Time Get the current time Some UNIX-Win 32 API calls correspondence 50

Comparing UNIX with Windows • Windows and UNIX differ in a fundamental way – in their respective programming models. • A UNIX program consists of code – does something or other, – making system calls to have certain services performed. • a Windows program is normally event driven – The main program waits for some event to happen, – then calls a procedure to handle it. • GUI (e. g. X Windows and Motif) in UNIX – runs entirely in user space • minor system calls runs in Kernel mode. – many of GUI facilities provided by the X Windows • but these are not system calls in any sense. 51

Win 32 API • Win 32 API (Application Programming Interface) – Microsoft has defined a set of procedures, – To be used by the programmers • to get operating system services. • Win 32 API is the interface supported – by all versions of Windows since Windows 95. • the Win 32 API has a huge number of calls – managing windows, geometric figures, text, fonts, scrollbars, dialog boxes, menus, and other features of the GUI. . . 52

End of Chapter 1 INTRODUCTION 53