OPERATING SYSTEMS 14 THREATS PIETER HARTEL 1 Security


![Privilege escalation: int main(int argc, char * argv[]) { course submission systemchar fn[N], buf[N]; Privilege escalation: int main(int argc, char * argv[]) { course submission systemchar fn[N], buf[N];](https://slidetodoc.com/presentation_image_h/95238769c132f34ae20e6796c1f390f1/image-8.jpg)

- Slides: 11

OPERATING SYSTEMS 14 - THREATS PIETER HARTEL 1

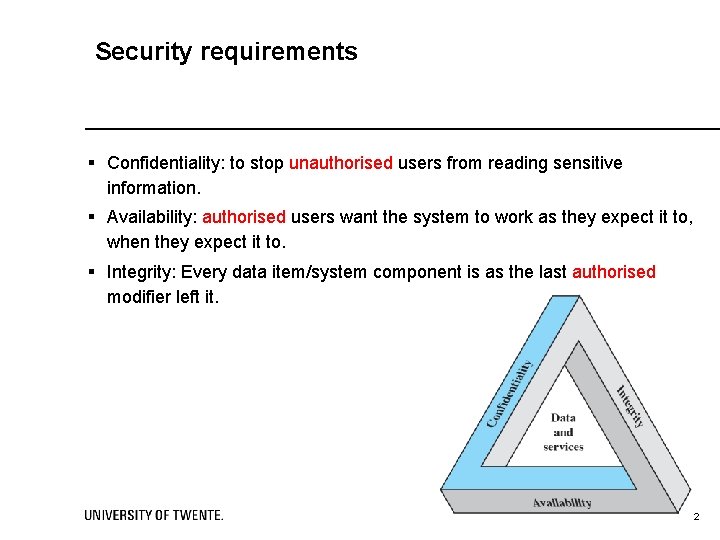
Security requirements § Confidentiality: to stop unauthorised users from reading sensitive information. § Availability: authorised users want the system to work as they expect it to, when they expect it to. § Integrity: Every data item/system component is as the last authorised modifier left it. 2 2

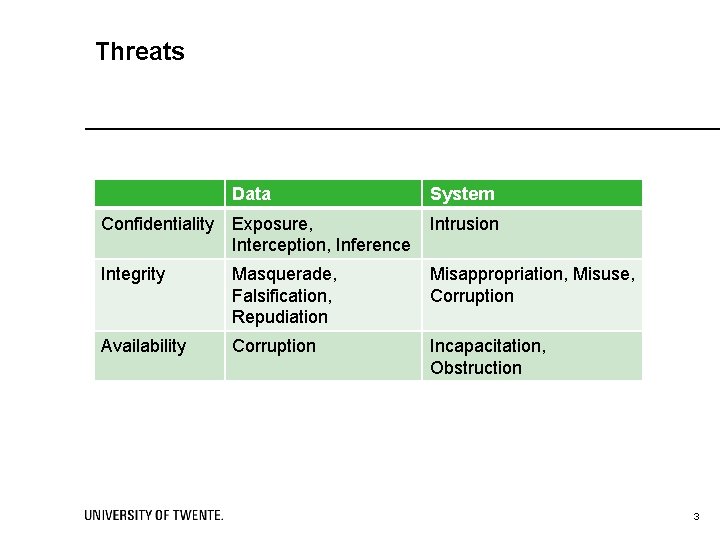
Threats Data System Confidentiality Exposure, Interception, Inference Intrusion Integrity Masquerade, Falsification, Repudiation Misappropriation, Misuse, Corruption Availability Corruption Incapacitation, Obstruction 3

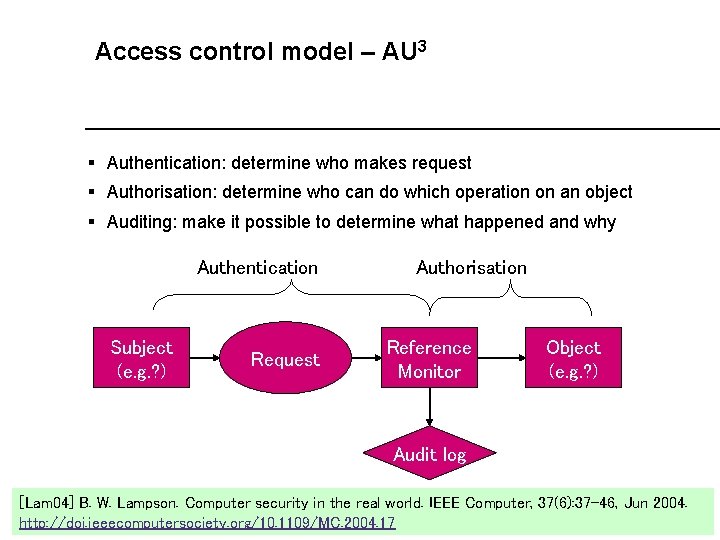
Access control model – AU 3 § Authentication: determine who makes request § Authorisation: determine who can do which operation on an object § Auditing: make it possible to determine what happened and why Authentication Subject (e. g. ? ) Request Authorisation Reference Monitor Object (e. g. ? ) Audit log [Lam 04] B. W. Lampson. Computer security in the real world. IEEE Computer, 37(6): 37 -46, Jun 2004. IIS http: //doi. ieeecomputersociety. org/10. 1109/MC. 2004. 17 Intro. Sec 4 4

Attacks § Insider attacks § Trap doors (try the vi command : help 42) § Login spoofing § Exploiting code bugs § Malicious code (more…) § Buffer overrun (more…) § Privilege escalation (more…) § Exploiting the user § Phishing § Sony rootkit (more…) 5

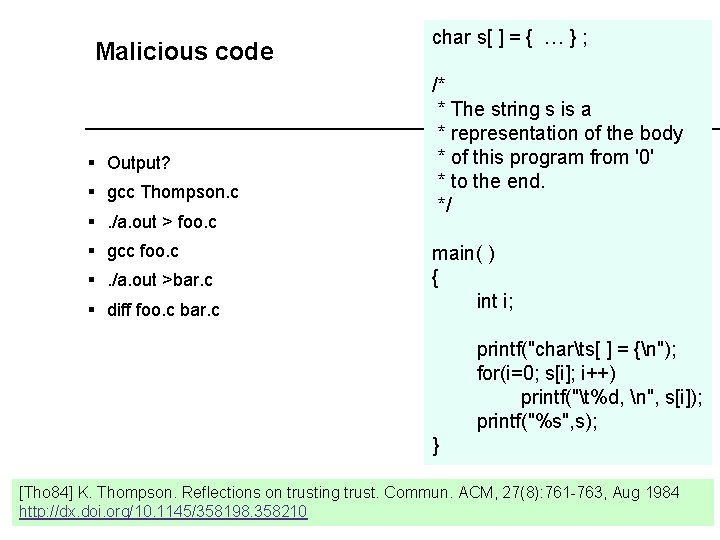
Malicious code § Output? § gcc Thompson. c §. /a. out > foo. c § gcc foo. c §. /a. out >bar. c § diff foo. c bar. c char s[ ] = { … } ; /* * The string s is a * representation of the body * of this program from '0' * to the end. */ main( ) { int i; printf("charts[ ] = {n"); for(i=0; s[i]; i++) printf("t%d, n", s[i]); printf("%s", s); } [Tho 84] K. Thompson. Reflections on trusting trust. Commun. ACM, 27(8): 761 -763, Aug 1984 http: //dx. doi. org/10. 1145/358198. 358210 6

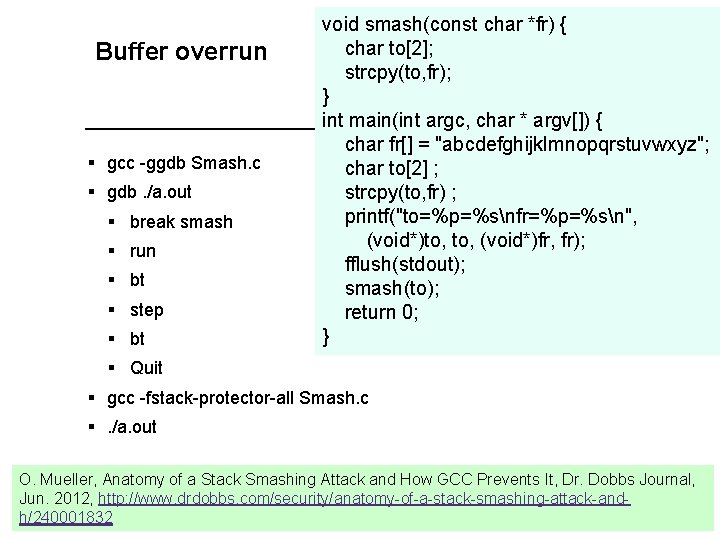
Buffer overrun § gcc -ggdb Smash. c § gdb. /a. out § break smash § run § bt § step § bt void smash(const char *fr) { char to[2]; strcpy(to, fr); } int main(int argc, char * argv[]) { char fr[] = "abcdefghijklmnopqrstuvwxyz"; char to[2] ; strcpy(to, fr) ; printf("to=%p=%snfr=%p=%sn", (void*)to, (void*)fr, fr); fflush(stdout); smash(to); return 0; } § Quit § gcc -fstack-protector-all Smash. c §. /a. out O. Mueller, Anatomy of a Stack Smashing Attack and How GCC Prevents It, Dr. Dobbs Journal, Jun. 2012, http: //www. drdobbs. com/security/anatomy-of-a-stack-smashing-attack-and 7 h/240001832
![Privilege escalation int mainint argc char argv course submission systemchar fnN bufN Privilege escalation: int main(int argc, char * argv[]) { course submission systemchar fn[N], buf[N];](https://slidetodoc.com/presentation_image_h/95238769c132f34ae20e6796c1f390f1/image-8.jpg)
Privilege escalation: int main(int argc, char * argv[]) { course submission systemchar fn[N], buf[N]; uid_t id = getuid(); printf("rid=%d, eid=%dn", id, geteuid()); snprintf(fn, N, "%s/%d", DIR, id); FILE *fp = fopen(fn, "w"); setreuid(id, id); printf("rid=%d, eid=%dn", getuid(), geteuid()); fflush(stdout); while (gets(buf) != NULL) { fputs(buf, fp); fputc('n', fp); } fclose(fp); return 0; § lecturer: § mkdir /tmp/db § chmod 700 /tmp/db § gcc '-DDIR="/tmp/db/"' Setuid. c § mv a. out /tmp/submit § chmod +s /tmp/submit § echo test | /tmp/submit § ls -l. R /tmp/db /tmp/submit § id § student: § echo bbb | /tmp/submit } find / -perm -4000 >junk 2>/dev/null& 8

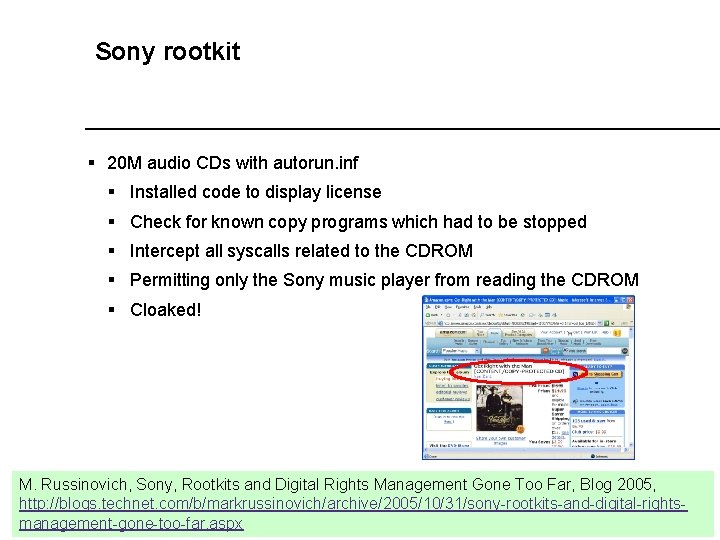
Sony rootkit § 20 M audio CDs with autorun. inf § Installed code to display license § Check for known copy programs which had to be stopped § Intercept all syscalls related to the CDROM § Permitting only the Sony music player from reading the CDROM § Cloaked! M. Russinovich, Sony, Rootkits and Digital Rights Management Gone Too Far, Blog 2005, http: //blogs. technet. com/b/markrussinovich/archive/2005/10/31/sony-rootkits-and-digital-rightsmanagement-gone-too-far. aspx 9

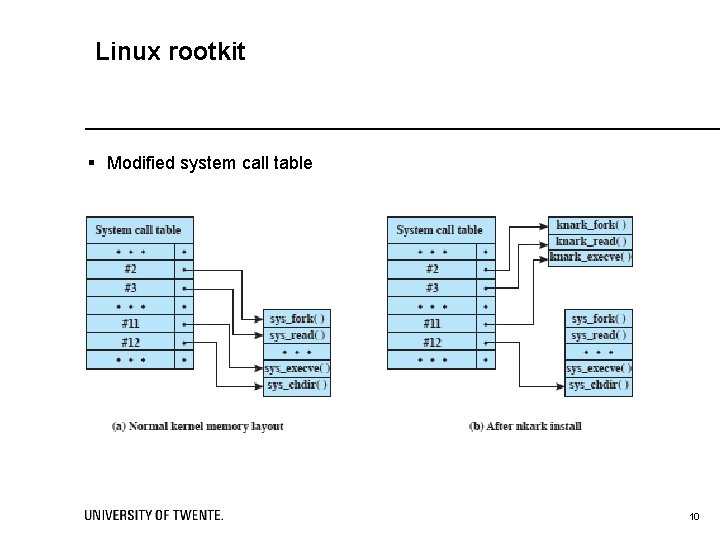
Linux rootkit § Modified system call table 10

Summary § Standard security requirements CIA § Code bugs and human behaviour facilitate attacks § The operating system is popular target of attacks § The operating system can do a lot to prevent, avoid or detect attacks § The reference monitor is the gold standard 11