Operating System Structure A key concept of operating

















- Slides: 26


Operating System Structure • A key concept of operating systems is multiprogramming. – Goal of multiprogramming is to efficiently utilize all of the computing resources. – When a job issues an I/O request (e. g. , open a file, read data from a file), it cannot continue until the request is fulfilled. – The CPU then becomes idle (the job is blocked on the request).

Operating System Structure • Basic idea of multiprogramming: – Keep multiple jobs in memory. – When one job blocks on I/O (or other events), the operating system: • Starts the I/O operation. • Switches to another job that is ready to execute. • Now the CPU and I/O device are executing in parallel. – When the I/O device has completed request, it generates an interrupt to inform the CPU. – Virtually all general purpose computers support multiprogramming.

• First developed for batch systems in the 60 s. – Go to the computer center and give them your program (stored on punch cards). – The computer operator “batched” several jobs together and loaded them into the computer. – Come back at 5: 00 to get the results of your program. • Batch systems are non-interactive.

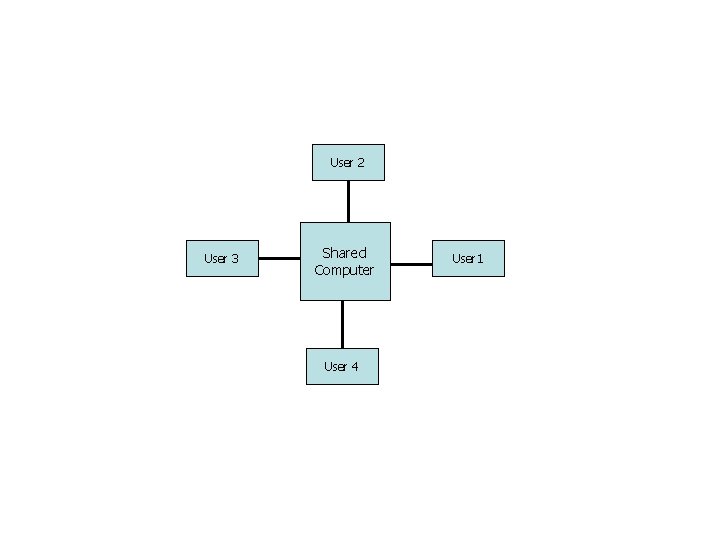
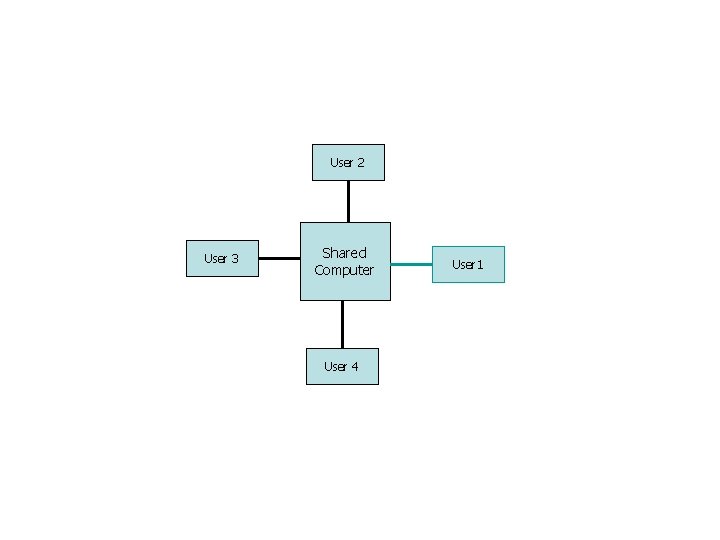
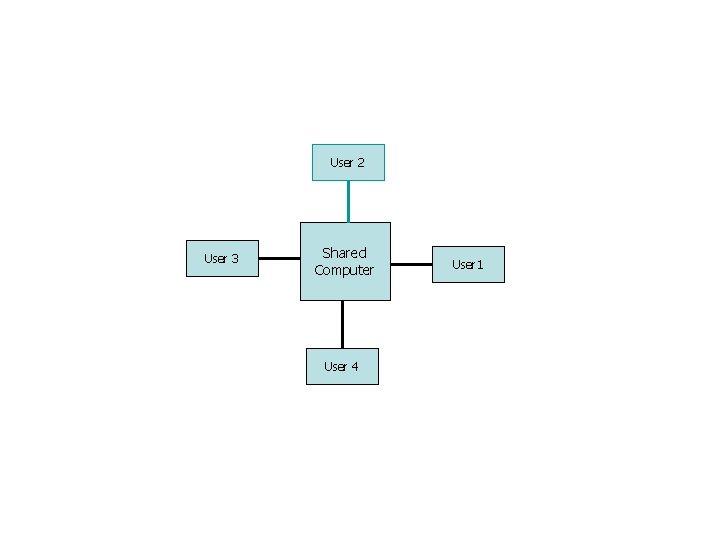
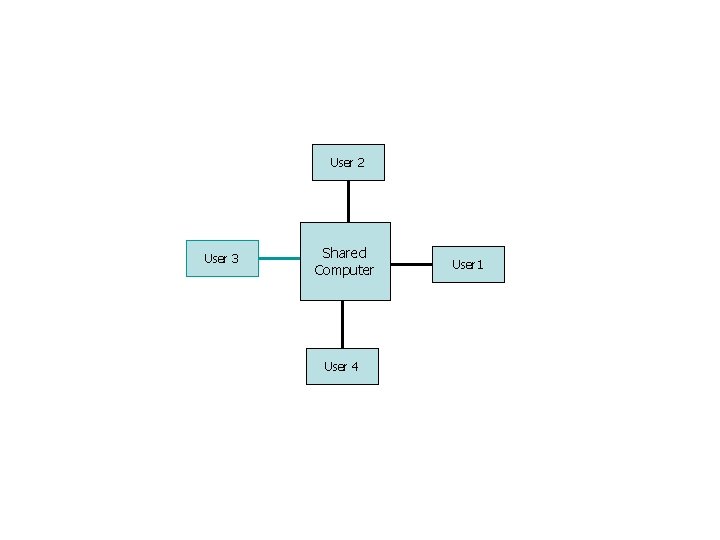
Time-Sharing Systems (Multitasking) n n n Logical extension of multiprogramming termed multitasking. Quite often sitting at terminal using a “command line” interface to interact with computer. n Types in commands from keyboard. n A system program called a shell reads command from the command line and makes OS system calls to carry out commands. OS switches between user’s programs very quickly, generally in round-robin fashion.

User 2 User 3 Shared Computer User 4 User 1

User 2 User 3 Shared Computer User 4 User 1

User 2 User 3 Shared Computer User 4 User 1

User 2 User 3 Shared Computer User 4 User 1

User 2 User 3 Shared Computer User 4 User 1

Time-Sharing Systems (Multitasking) n n n Switching between users is very fast. Goal is to give the illusion that each user has own machine. n Think about using a text editor, or getting a directory listing. Response time is a priority.

Protection of System Resources • • • I/O Devices Memory CPU Files Operating System

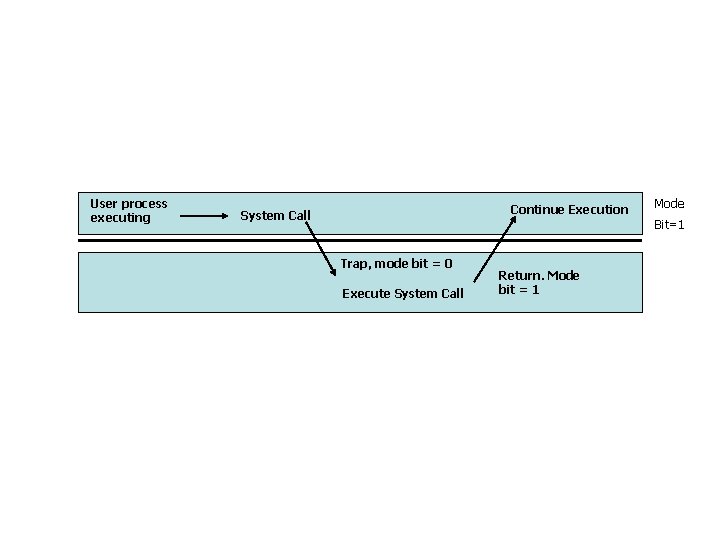
Protection of System Resources • Based on dual-mode execution: – kernel mode and user mode. – Privileged instructions can be issued only in kernel mode. – Mode bit in Process Status Word (PSW), checked on every instruction.

User process executing Continue Execution System Call Mode Bit=1 Trap, mode bit = 0 Execute System Call Return. Mode bit = 1

Protection of I/O Devices • All I/O instructions are privileged instructions. • Only accessed through system calls.

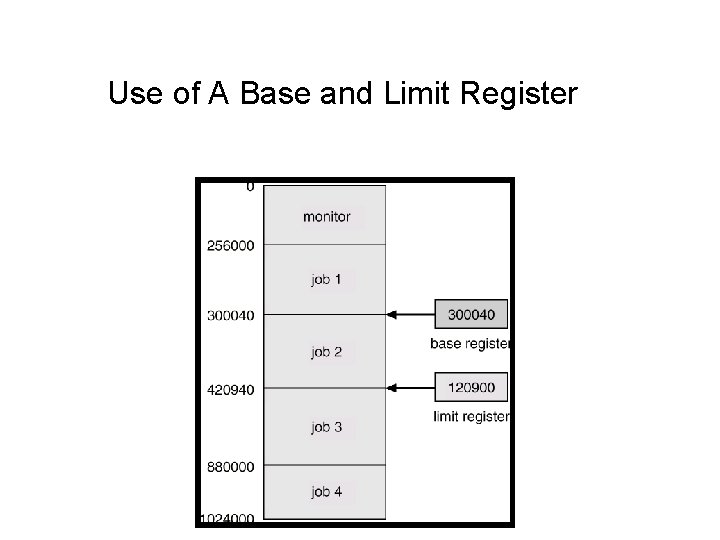
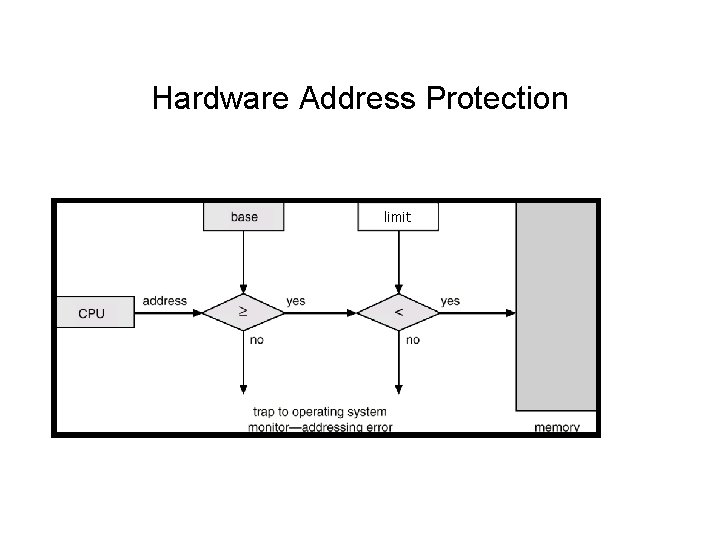
Memory Protection • Must provide memory protection for the interrupt vector, interrupt service routines, and other applications address space. • Two registers that determine the range of legal addresses a program may access: – Base register – holds the smallest legal physical memory address. – Limit register – contains the size of the range • Memory outside the defined range is protected.

Use of A Base and Limit Register

Hardware Address Protection limit

CPU (and OS) Protection • Keep user from monopolizing CPU. • Ensure OS regains control of CPU.

CPU Protection • Timer – interrupts computer after specified period to ensure operating system maintains control. – Timer is decremented every clock tick. – When timer reaches the value 0, an interrupt occurs. • Timer commonly used to implement time sharing.

Privileged Instructions • Load base and limit registers?

Privileged Instructions • Load base and limit registers? • Set the system timer?

Privileged Instructions • Load base and limit registers? • Set the system timer? • Read the system clock?

Privileged Instructions • • Set the system timer? Read the system clock? Load base and limit registers? Open a file?

Privileged Instructions • • • Load base and limit registers? Set the system timer? Read the system clock? Open a file? Compile a program and create executable?

Privileged Instructions • • • Load base and limit registers? Set the system timer? Read the system clock? Open a file? Compile a program and create executable? Enable/disable interrupts?