Operating System Security CSH 6 Chapter 24 Operating





















![Windows 7 Security References: [1] Bradley, T. (2009). “Pros and Cons of Windows 7 Windows 7 Security References: [1] Bradley, T. (2009). “Pros and Cons of Windows 7](https://slidetodoc.com/presentation_image_h/241909042f5a6e80b7963e689b4150a9/image-39.jpg)

- Slides: 40

Operating System Security CSH 6 Chapter 24 “Operating System Security” William Stallings 1 Copyright © 2020 M. E. Kabay. All rights reserved.

Topics ØInformation Protection and Security ØRequirements for Operating System Security ØProtection Mechanisms ØFile Sharing ØTrusted Systems ØWindows 2000 Security ØWindows 7 Security* 2 * Not in chapter: added by M. E. Kabay Copyright © 2020 M. E. Kabay. All rights reserved.

Information Protection & Security (1) Overall protection policies Ø No sharing q Every process completely isolated q Virtualization illustrates this approach Ø Sharing originals of program or data files q Read-only access to program q Sharing data requires locking mechanisms Ø Confined, or memoryless, subsystems q No transfer of protected information across boundaries q E. g. , server and client are partitioned from each other Ø Controlled information dissemination q Security classes for data and users determine access q Widely used 3 Copyright © 2020 M. E. Kabay. All rights reserved.

Information Protection & Security (2) Ø Operating security concerns grouped Ø Access controls q Regulating user access to total system, subsystems, data q Regulating process access to resources & objects in system Ø Information-flow control q Within system & q To users Ø Certification q Proving that access & flow control perform to specification q Demonstrating that measures actually enforce data protection and security policies 4 Copyright © 2020 M. E. Kabay. All rights reserved.

Requirements for Operating System Security ØRequirements ØComputer System Assets ØDesign Principles 5 Copyright © 2020 M. E. Kabay. All rights reserved.

Requirements Ø Confidentiality q. Restrict access to authorized parties q. Prevent disclosure even of existence of data Ø Integrity q. Control over who can make which changes to what system assets q. RWALX (read, write, append, lock, execute) including save, delete, changing Ø Availability q. Timely access to resources with authorization Ø Authenticity C P q. Verify identity of user I Au 6 Av Copyright © 2020 M. E. Kabay. All rights reserved. U

Computer System Assets Ø Hardware q Accidental & deliberate damage or alteration (e. g. , switches, hardware settings) q Theft Ø Software q Availability – deletion, disabling q Corruption – changing functionality (malware, accidental write) q Control – preventing unauthorized copying Ø Data q Unauthorized access for reading or writing (especially personally identifiable information) q Data integrity & data destruction q Inference (data mining and data correlation) 7 Copyright © 2020 M. E. Kabay. All rights reserved.

Design Principles Ø Least privilege q Default no access; explicit granting of permissions Ø Economy of mechanisms q Small, simple security tools q Include in initial design, not as add-ons Ø Acceptability q Meet functional requirements AND keep overhead to minimum q Do not interfere unreasonably with operations Ø Complete mediation q All access must be checked by security processes Ø Open design q Do not depend on secrecy of the design or implementation (Kerkhoffs’ Principle) q Allow for expert review, open discussion 8 Copyright © 2020 M. E. Kabay. All rights reserved.

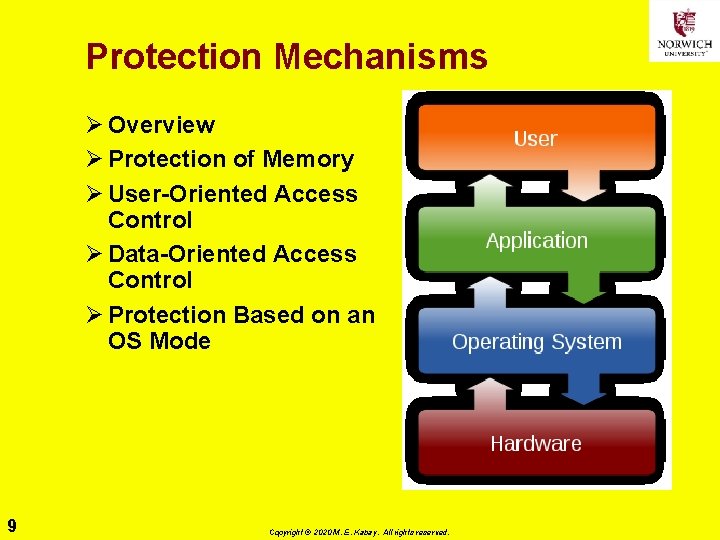
Protection Mechanisms Ø Overview Ø Protection of Memory Ø User-Oriented Access Control Ø Data-Oriented Access Control Ø Protection Based on an OS Mode 9 Copyright © 2020 M. E. Kabay. All rights reserved.

Overview of Protection Mechanisms Ø Resources being shared in multiprogramming environments q CPU, Memory, I/O devices, Programs, Data Ø Spectrum of OS protections q No protection – run sensitive procedures at different times q Isolation – all processes completely separate, with no shared resources q Share all or share nothing – public or private q Share via access limitation – every access verified for specific user & specific object q Share via dynamic capabilities – allow dynamic creation of sharing rights for objects q Limit use of an object – functional limitations (read, write, print, statistical measures vs individual data) 10 Copyright © 2020 M. E. Kabay. All rights reserved.

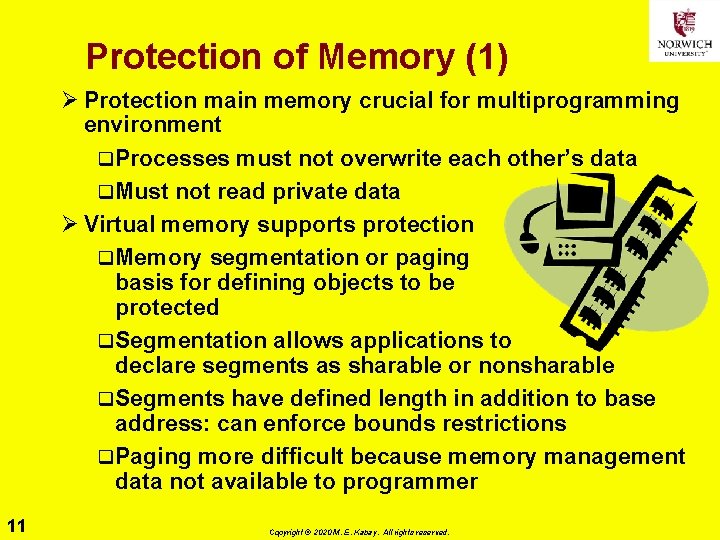
Protection of Memory (1) Ø Protection main memory crucial for multiprogramming environment q. Processes must not overwrite each other’s data q. Must not read private data Ø Virtual memory supports protection q. Memory segmentation or paging basis for defining objects to be protected q. Segmentation allows applications to declare segments as sharable or nonsharable q. Segments have defined length in addition to base address: can enforce bounds restrictions q. Paging more difficult because memory management data not available to programmer 11 Copyright © 2020 M. E. Kabay. All rights reserved.

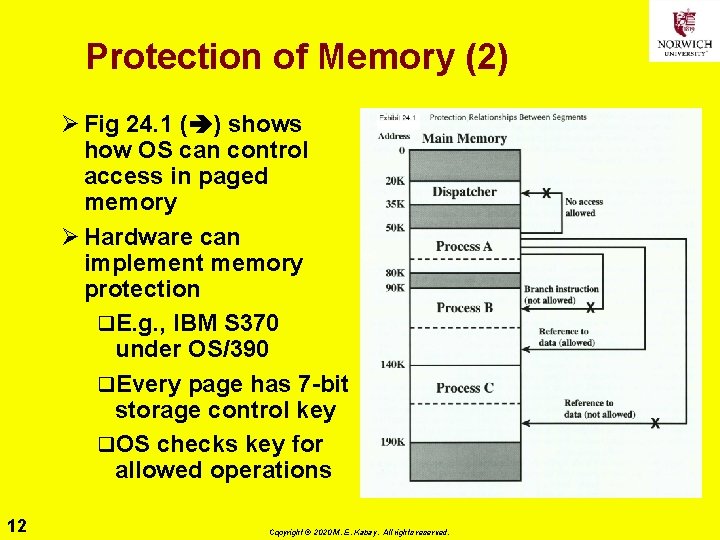
Protection of Memory (2) Ø Fig 24. 1 ( ) shows how OS can control access in paged memory Ø Hardware can implement memory protection q. E. g. , IBM S 370 under OS/390 q. Every page has 7 -bit storage control key q. OS checks key for allowed operations 12 Copyright © 2020 M. E. Kabay. All rights reserved.

User-Oriented Access Control Karlheinz Ø Distinguish between q. Identification: provision I&A of an identifier (e. g. , user. ID) q. Authentication: ascertaining binding between identifier & user of identifier Ø User logon is I&A q. Identification (provide user. ID) & q. Authentication (provide some other bound information – see later chapters on I&A) Ø Once process(es) established for user, can use data-oriented access control 13 Copyright © 2020 M. E. Kabay. All rights reserved. Stockhausen (identifier) Karlheinz Stockhausen’s passport (authentifier)

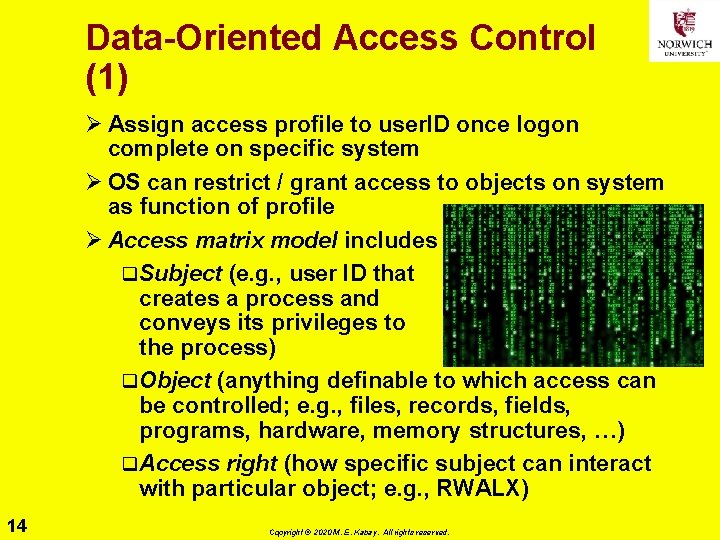
Data-Oriented Access Control (1) Ø Assign access profile to user. ID once logon complete on specific system Ø OS can restrict / grant access to objects on system as function of profile Ø Access matrix model includes q. Subject (e. g. , user ID that creates a process and conveys its privileges to the process) q. Object (anything definable to which access can be controlled; e. g. , files, records, fields, programs, hardware, memory structures, …) q. Access right (how specific subject can interact with particular object; e. g. , RWALX) 14 Copyright © 2020 M. E. Kabay. All rights reserved.

Data-Oriented Access Control (2) Ø Most frequent implementation of data-oriented access control uses access control lists (ACLs) q For each object, list users & allowed access modes q Can specify groups of users q Usually includes default mode for unlisted users Ø Capability tickets apply to users q For each user, list authorized objects & access modes q Users may lend or give them to other users (delegation) q But dispersal increases need for authenticity of the tickets q Therefore OS often holds ticket in central store 15 Copyright © 2020 M. E. Kabay. All rights reserved.

Protection Based on an OS Mode (1) Ø Processors support multiple (at least 2) modes of operation *Kernel is part of OS w/ critical functions q. More privileged mode üSystem, control, or kernel* mode üPermits R/W of control registers, direct I/O, memory management, process control q. Less privileged mode üUser mode üNormal mode for user processes 16 Copyright © 2020 M. E. Kabay. All rights reserved.

Protection Based on an OS Mode (2) 17 Copyright © 2020 M. E. Kabay. All rights reserved.

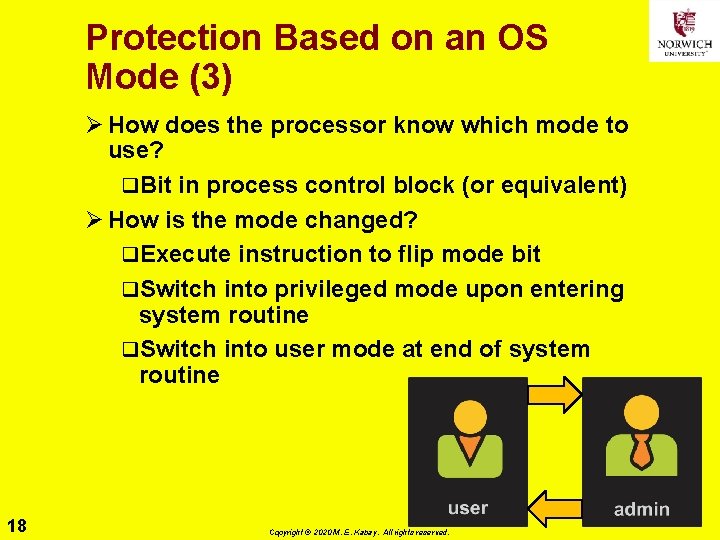
Protection Based on an OS Mode (3) Ø How does the processor know which mode to use? q. Bit in process control block (or equivalent) Ø How is the mode changed? q. Execute instruction to flip mode bit q. Switch into privileged mode upon entering system routine q. Switch into user mode at end of system routine 18 Copyright © 2020 M. E. Kabay. All rights reserved.

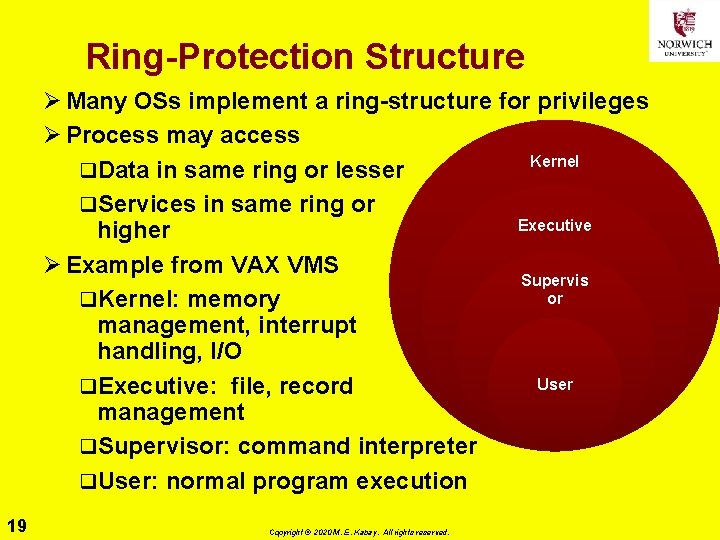
Ring-Protection Structure Ø Many OSs implement a ring-structure for privileges Ø Process may access Kernel q. Data in same ring or lesser q. Services in same ring or Executive higher Ø Example from VAX VMS Supervis or q. Kernel: memory management, interrupt handling, I/O User q. Executive: file, record management q. Supervisor: command interpreter q. User: normal program execution 19 Copyright © 2020 M. E. Kabay. All rights reserved.

File Sharing: Access Rights Ø Can control access to range of file information and functions; e. g. , q None: not even knowledge of existence NOTES: q Knowledge: file exists, owner *In text, author does not q Execution: run program limit “update” to this function only. q Read: input from file ** Author refers to write function as part of q Append: output to end of file “update” q Update: modify existing records ***Not mentioned in text only* q Write: add, change, delete records** q Change protection: usually owner only q Delete: destroy file q Lock: flag for concurrency control*** 20 Copyright © 2020 M. E. Kabay. All rights reserved.

Trusted Systems: Multilevel Security Ø Categories of security requirements; e. g. , q. Top Secret, Confidential, Unclassified q. Corporate-officers-only, Companyconfidential, General-release Ø Fundamental: higher-classification data must not be released to lower-classification group without reclassification Ø Rules q. No read up (simple security property): read only at equal or lower level q. No write down (*-property): write only at equal or higher level See CSH 5 Chapter 9 for more details on security models 21 Copyright © 2020 M. E. Kabay. All rights reserved.

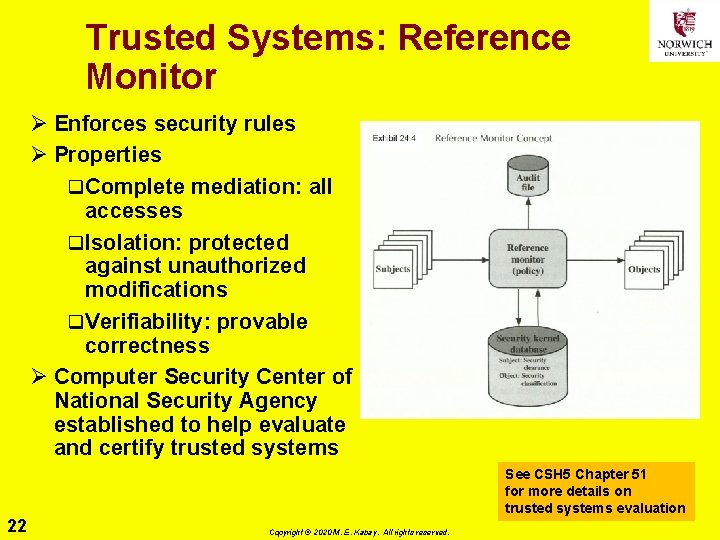
Trusted Systems: Reference Monitor Ø Enforces security rules Ø Properties q Complete mediation: all accesses q Isolation: protected against unauthorized modifications q Verifiability: provable correctness Ø Computer Security Center of National Security Agency established to help evaluate and certify trusted systems See CSH 5 Chapter 51 for more details on trusted systems evaluation 22 Copyright © 2020 M. E. Kabay. All rights reserved.

Trusted Systems: Trojan Horse Defense Ø Trojan horse programs attempt to subvert security by tricking higher-privilege user into executing harmful code Ø Some Trojans such as keyloggers attempt to store privileged information in files that can be accessed by unprivileged users Ø But a reference monitor can prevent write-down (*property) and thus stymie the Trojan data collection 23 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows 2000 (& Later) Security ØIntroduction ØAccess-Control Scheme ØAccess Token ØSecurity Descriptors 24 Copyright © 2020 M. E. Kabay. All rights reserved.

Introduction to W 2 K Security Ø Windows 2000 (W 2 K) OS q. Released Feb 2000 q. Successor to NT q. Followed by XP, Server 2003, Vista, 7 Ø Access control uniformly applied q. Processes, files, flags, windows…. Ø Uses 2 entities q. Access token for each process q. Security descriptor for each object 25 Copyright © 2020 M. E. Kabay. All rights reserved.

W 2 K Access-Control Scheme Ø User logs on with user. ID/ password Ø User process has access token created q. Security. ID (SID) q. Child processes inherit SID Ø Functions of access token q. Consolidates all security information for fast validation q. Lets process modify own security parameters without interfering with other processes Ø Security descriptor q. Associated with each object q. Includes ACL 26 Copyright © 2020 M. E. Kabay. All rights reserved.

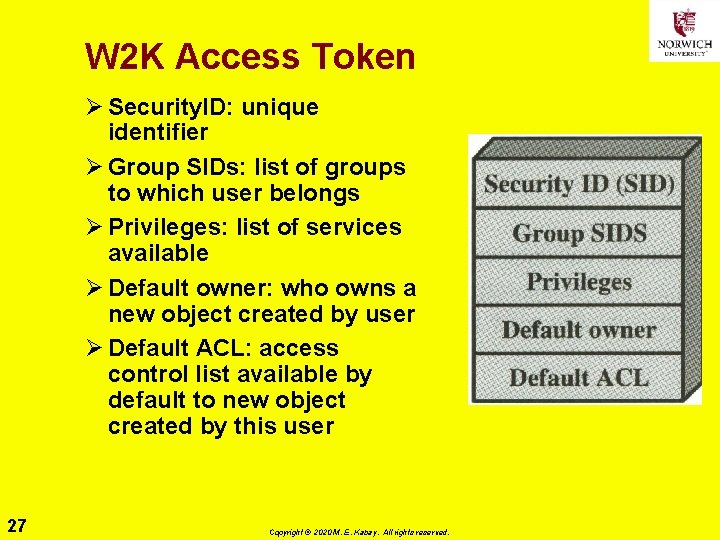
W 2 K Access Token Ø Security. ID: unique identifier Ø Group SIDs: list of groups to which user belongs Ø Privileges: list of services available Ø Default owner: who owns a new object created by user Ø Default ACL: access control list available by default to new object created by this user 27 Copyright © 2020 M. E. Kabay. All rights reserved.

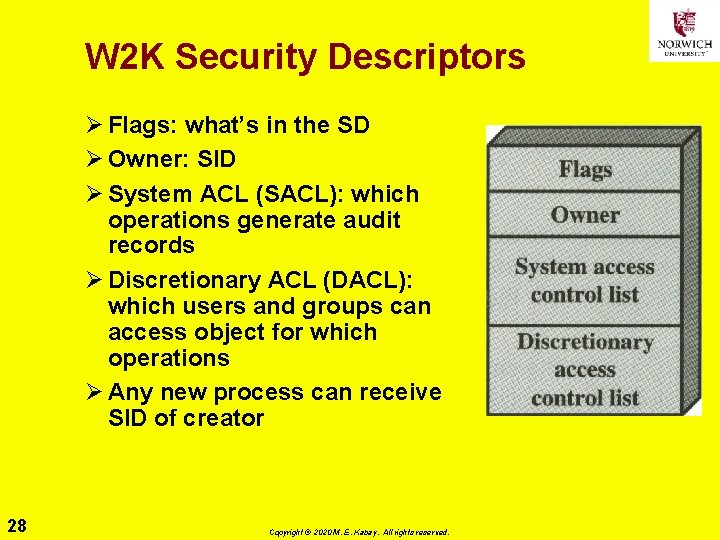
W 2 K Security Descriptors Ø Flags: what’s in the SD Ø Owner: SID Ø System ACL (SACL): which operations generate audit records Ø Discretionary ACL (DACL): which users and groups can access object for which operations Ø Any new process can receive SID of creator 28 Copyright © 2020 M. E. Kabay. All rights reserved.

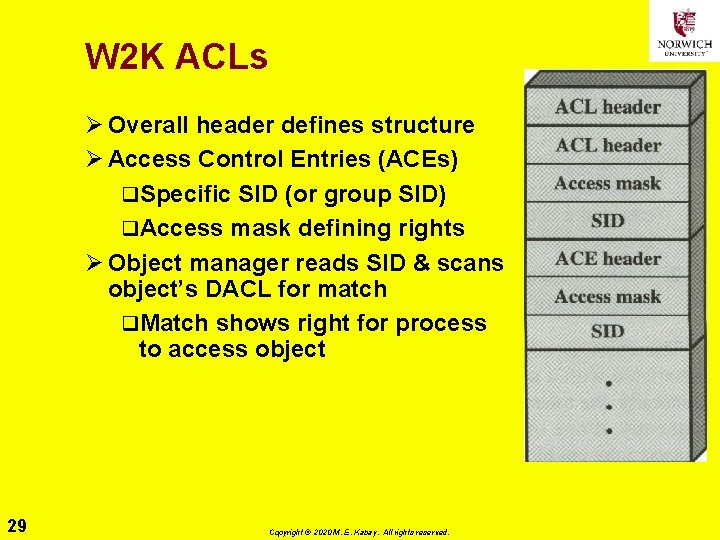
W 2 K ACLs Ø Overall header defines structure Ø Access Control Entries (ACEs) q. Specific SID (or group SID) q. Access mask defining rights Ø Object manager reads SID & scans object’s DACL for match q. Match shows right for process to access object 29 Copyright © 2020 M. E. Kabay. All rights reserved.

W 2 K Access Mask Standard Access Types Ø Access mask bits define allowable modes q. Synchronize: can make object part of wait q. Write_owner: modify owner of object q. Write_DAC: modify protection q. Read_control: get the security data for object q. Delete: destroy object See Exhibit 24. 7 for additional bits in Access Mask 30 Copyright © 2020 M. E. Kabay. All rights reserved.

W 2 K Access Mask Generic Access Bits Ø Define general-purpose access modes Ø Can be applied to any object Ø Types are q. Generic_all: allow all access q. Generic_execute: run code q. Generic_write: any form of output to object q. Generic_read: input from object 31 Copyright © 2020 M. E. Kabay. All rights reserved.

W 2 K Access Mask Special. Purpose Bits Ø Access_System_Security q. Allows process to modify audit & alarm control q. Access token must have appropriate privilege enabled Ø Maximum_allowed q. Alters algorithm for granting privilege to user q. If off, security monitor scans entire list to locate privilege requested or end of list q. If on, monitor limits privilege to a defined maximum 32 Copyright © 2020 M. E. Kabay. All rights reserved.

W 2 K Options for Access Ø Attempt to open object for all possible accesses q. But may be denied q. Even though enough access available for needs Ø Open object with specific access every time required q. Reliably get access q. Increase overhead due to extra table entries Ø Open object with maximal access allowed for object q. But may grant more than needed q. Can lead to security issues with bad code 33 Copyright © 2020 M. E. Kabay. All rights reserved.

Application-Level Usage of W 2 K Security Ø Applications can apply W 2 K security to specific objects; e. g. , q. Database server can attach descriptors to elements of DB q. Add special DB-specific functions such as JOIN Ø OS checks access rights as usual 34 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows 7 Security ØASLR ØDEP ØBit. Locker-to-Go ØIE 8 ØUAC ØCrypto improvements 35 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows 7 Security (1) Ø ASLR q. Address Space Layout Randomization q. Unpredictable location of DLLs in RAM q. Much harder for malware to target code Ø DEP q. Data Execution Prevention q. Restrictions on buffer overflow attacks Ø Bit. Locker-to-Go q. Encryption for any kind of data storage q. Includes removable media 36 [ref 1] Copyright © 2020 M. E. Kabay. All rights reserved.

Windows 7 Security (2) Ø Internet Explorer 8 Smart. Screen q. Anti-phishing / anti-malware feature q. Blocks known bad sites q. Highlights actual URL of links in address bar (warning against phishing)[ref 1] Ø UAC q. User Account Control q. Distinguish between admin and normal user q. Set domain environment to “Always notify” so “users will be prompted to input their passwords to perform high-risk administrative actions”[ref 2] 37 Copyright © 2020 M. E. Kabay. All rights reserved.

Windows 7 Security (3) Ø Crypto improvements q. Swap file easily encrypted üXP and earlier allowed swap file erasure üBut could add 10 minutes to shutdown üW 7 allows swap-file encryption q. All modern encryption methods supported üSuite B: AES, ECDSA (Elliptic Curve Digital Signature Algorithm), ECDH (Elliptic Curve Diffie-Hellman, SHA 2) üSee < http: //tinyurl. com/3 xs 28 uz > q. Encrypting File System improved üControl user actions – keylengths, ciphers, force backups of keys 38 [ref 2] Copyright © 2020 M. E. Kabay. All rights reserved.
![Windows 7 Security References 1 Bradley T 2009 Pros and Cons of Windows 7 Windows 7 Security References: [1] Bradley, T. (2009). “Pros and Cons of Windows 7](https://slidetodoc.com/presentation_image_h/241909042f5a6e80b7963e689b4150a9/image-39.jpg)
Windows 7 Security References: [1] Bradley, T. (2009). “Pros and Cons of Windows 7 Security. ” PCWorld (Nov 23, 2009). < http: //tinyurl. com/yfarf 6 z > [2] Grimes, R. A. (2010). “Expert’s Guide to Windows 7 Security. ” Infoworld (Sep 30, 2010). < http: //tinyurl. com/37 zkskp > 39 Copyright © 2020 M. E. Kabay. All rights reserved.

Now go and study 40 Copyright © 2020 M. E. Kabay. All rights reserved.