Operating System Protection Through Program Evolution By Dr

Operating System Protection Through Program Evolution By Dr. Frederick B. Cohen Presented by William Lu

The Ultimate Attack n How to defeat defensive measures of a system? n. Gain physical access to the system n. Reverse n. Find engineer defenses weak link and exploit

The Ultimate Defense n How to defend against attackers n n Make attacks extremely complex Make costs too high to be worth attacking n i. e. passwords n n n Large space Spread out probability density (diffusion) Obscuring stored information (confusion)

The Ultimate Defense n Current operating systems n n n Space is enormous (all programs that fit in memory) High probability subspace (very small number of versions) No confusion

The Ultimate Defense n How to increase operating system defenses? n Reducing coherence n How? n n Feasibility? n n Unique defense for each system Too many unique defenses to design Compromise? n Implement a fixed number of defenses

The Ultimate Defense n More practical solution? n n Evolutionary defenses Goal? n n n Produce a large search space Provide confusion Provide diffusion

(some) Techniques for Program Evolution n Equivalent instruction sequences Instruction reordering Variable substitution

Equivalent Instruction Sequences n What does it do? n Replaces instruction sequences with equivalent sequences n n i. e. add 17 is equivalent to add 20 and subtract 3 How does it help defend against attacks? n n Potentially infinite evolutions Creates enormous possible executions

Instruction Reordering n What does it do? n n n Reorders instructions without altering program execution Order does not matter How does it help defend against attacks? n Increases complexity of attacks to n! different orderings (n = # of different instructions)
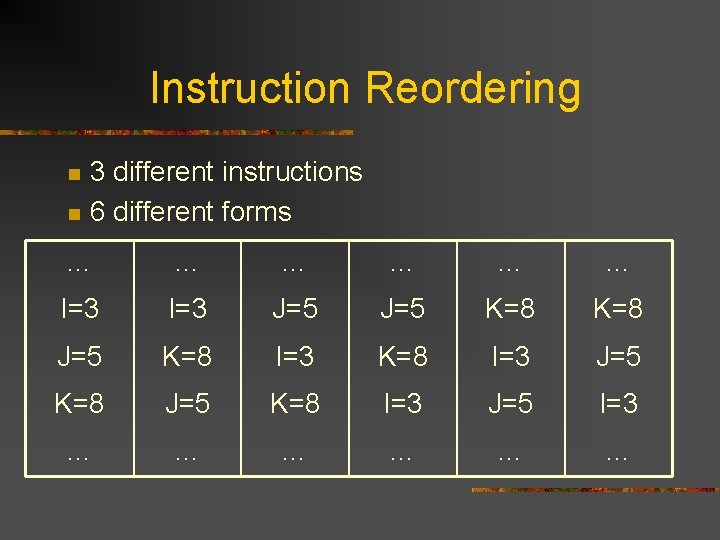
Instruction Reordering n n 3 different instructions 6 different forms … … … I=3 J=5 K=8 I=3 J=5 K=8 I=3 J=5 I=3 … … …

Variable Substitution n What does it do? n n Alters the location of memory storage areas How does it help defend against attacks? n Prevents static examination and analysis of parameters

What to do with these (and other) techniques?

Providing Evolution in Defenses n How to evolve? n n Select a mix of evolution techniques Increase complexity while minimizing impact on end users

Providing Evolution in Defenses n When to evolve? n At the factory? Uniquely identify each disk sent out n Reduced efficiency n n At installation? Crucial to have unique and confidential evolution n Takes time at end user level n

Providing Evolution in Defenses n When to evolve? n After installation? Cannot assure against corruption n Cannot trust internal checking n Attack that succeeds on one day may fail the next n

Attacks on Program Evolution n n Points of Attack Tracing Attack

Point of Attack n How? n n n Find original entry point and exploit it Gain direct access to hardware or operating system internals How to defend against it? n n Evolve the core of the operating system Evolving the calling mechanism n Calls that bypass protection may be of the wrong form

Tracing Attacks n How? n n Trace programs at execution or simulation How to defend against it? n Use redundancy n Force attacker to use tracing on each attack

Conclusion n Program evolution can increase the complexity for an attacker Create a large search space to make attacks infeasible Need more study to reach maturity
- Slides: 19