Operating System Features 1 Operating System Features Memory





- Slides: 18

Operating System Features 1

Operating System Features • • • Memory protection Temporary file issues Dead space issues Sandboxing Object Request Brokers 2

Separation • Physical – processes use different physical objects • Temporal – processes use same objects at different times • Logical – processes use objects in constrained space • Cryptographic – processes use only intelligible objects 3

Levels of Protection • • • None Isolation Share all/Share none Share via access limitation Share by capabilities Limited use 4

Granularity • • Volume (physical storage structure) Data collection (file, database, memory) Data element (entry, memory structure) Field (value within data element) Word (addressable memory unit) Byte (character) Bit (1/0) Detail vs. Efficiency 5

Mechanisms • • Fence Register Relocation Base/Bounds Register Tagged Architecture Segmentation Paging Paged Segmentation Capability 6

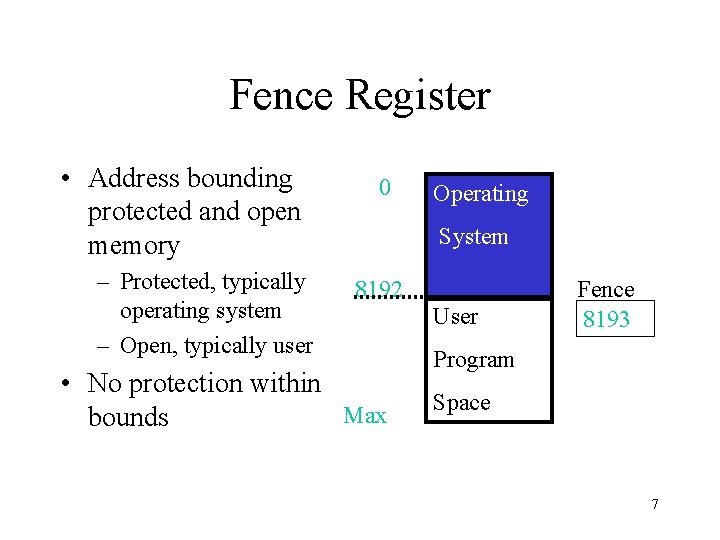
Fence Register • Address bounding protected and open memory – Protected, typically operating system – Open, typically user 0 Operating System 8192 • No protection within Max bounds User Fence 8193 Program Space 7

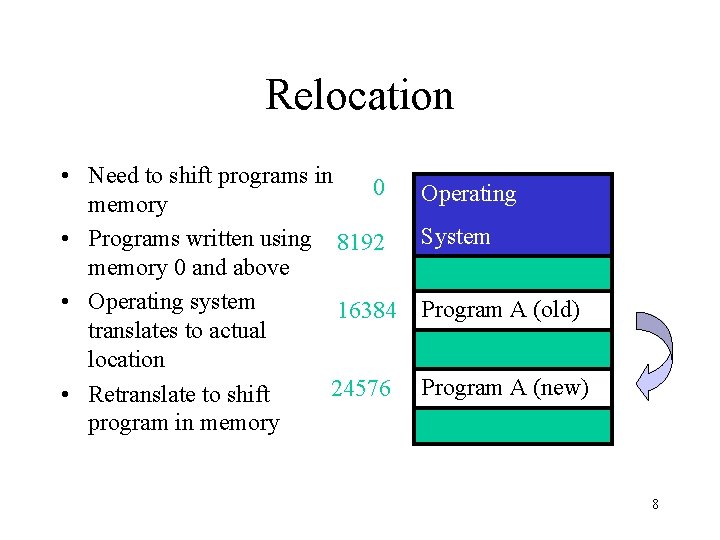
Relocation • Need to shift programs in 0 memory • Programs written using 8192 memory 0 and above • Operating system 16384 translates to actual location 24576 • Retranslate to shift program in memory Operating System Program A (old) Program A (new) 8

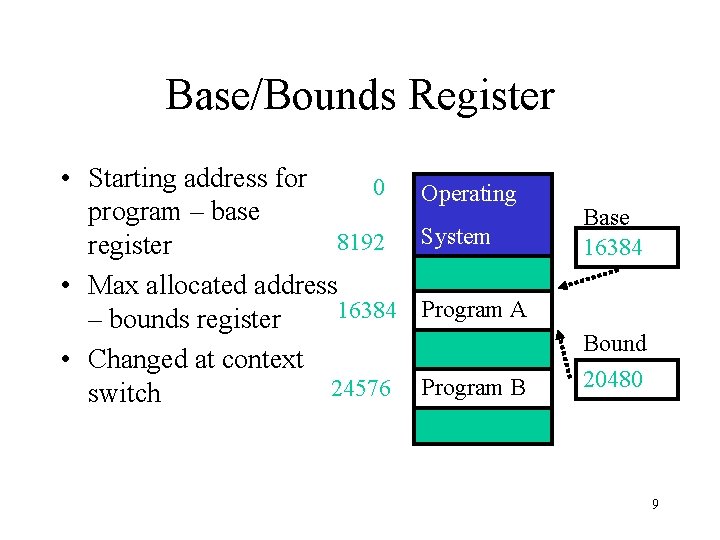
Base/Bounds Register • Starting address for 0 program – base 8192 register • Max allocated address 16384 – bounds register • Changed at context 24576 switch Operating System Base 16384 Program A Program B Bound 20480 9

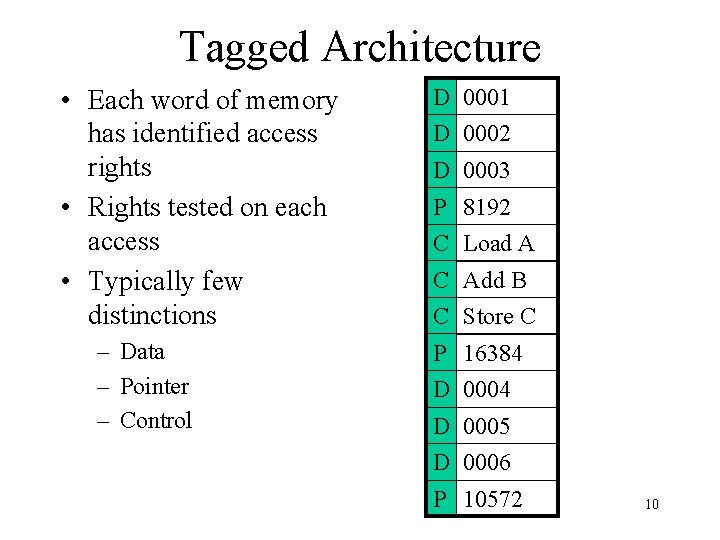
Tagged Architecture • Each word of memory has identified access rights • Rights tested on each access • Typically few distinctions – Data – Pointer – Control D 0001 D 0002 D 0003 P 8192 C Load A C Add B C Store C P 16384 D 0005 D 0006 P 10572 10

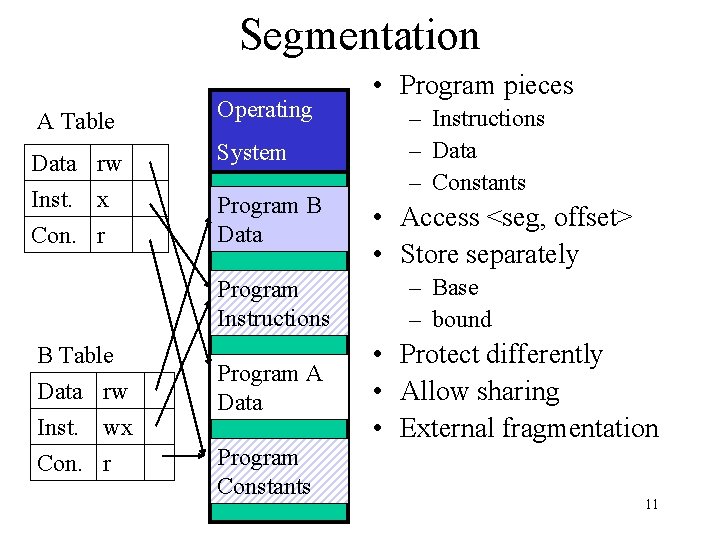
Segmentation A Table Operating Data rw Inst. x Con. r System Program B Data Program Instructions B Table Data rw Inst. wx Con. r Program A Data Program Constants • Program pieces – Instructions – Data – Constants • Access <seg, offset> • Store separately – Base – bound • Protect differently • Allow sharing • External fragmentation 11

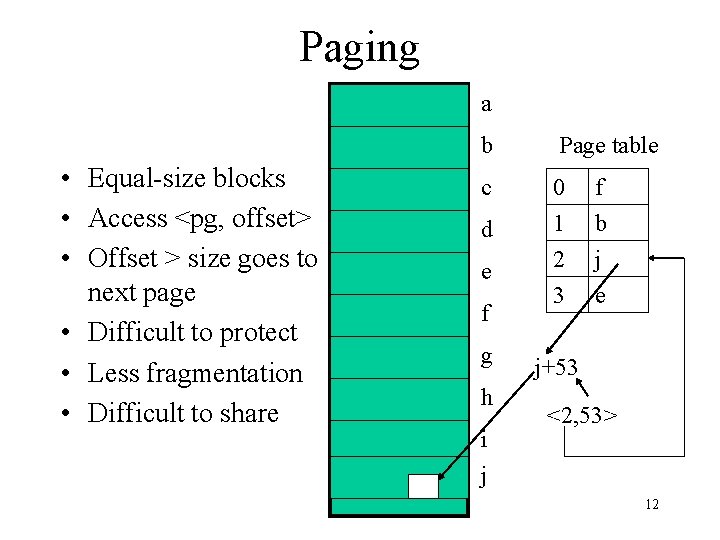
Paging a • Equal-size blocks • Access <pg, offset> • Offset > size goes to next page • Difficult to protect • Less fragmentation • Difficult to share b Page table c 0 1 2 3 d e f g h i j f b j e j+53 <2, 53> 12

Paged Segmentation • Segment references translate to page references – <seg, offset> – <<page of seg>, <page offset>> • Segmentation for sharing/protection • Paging for ease of handling 13

Capabilities • Unforgeable token – Identity of object requested – Rights to object – Signature of broker • Control of rights transfer • Control of rights propagation • Done at structure level 14

Temporary File Issues • Temporary file – duration for life of process only • Intended private and non-invasive • Threats – Disclosure – Modification – Misdirection • Protection via atomic transactions 15

Dead Space Issues • What are default values? – Random – Zero – Whatever was there before • What are cleared values? – Random – Zero – Pattern – No clearing 16

Sandboxing • Restricted environment for untrusted code – Web code – Email code – Issues of completeness, operations available • Alternative: trust vendor signature(Active. X) • Alternative: carry proof (lab systems) • Alternative: cryptography (Microsoft) 17

Object Request Brokers • Object – code and data bundle, limited access methods • Broker – mediate communication between objects • CORBA – industry standard • Still a lot of discussion about protection 18