Openflow Protocol Software Defined Network SDN Field No






- Slides: 39

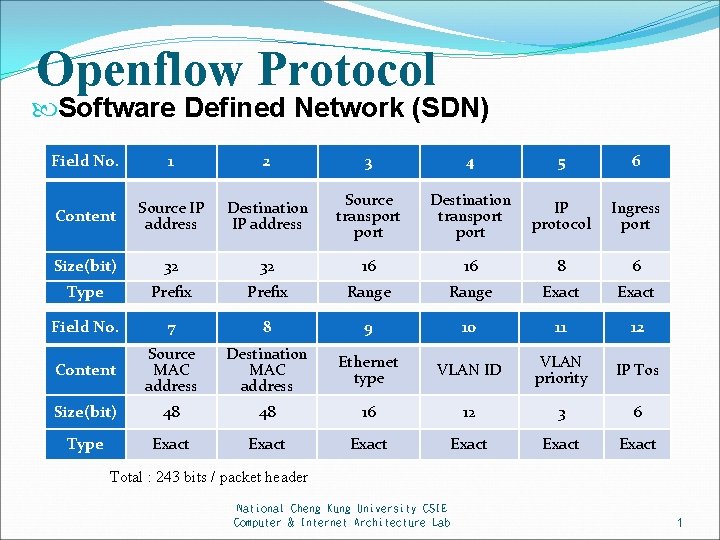
Openflow Protocol Software Defined Network (SDN) Field No. 1 2 3 4 5 6 Content Source IP address Destination IP address Source transport Destination transport IP protocol Ingress port Size(bit) 32 32 16 16 8 6 Type Prefix Range Exact Field No. 7 8 9 10 11 12 Content Source MAC address Destination MAC address Ethernet type VLAN ID VLAN priority IP Tos Size(bit) 48 48 16 12 3 6 Type Exact Exact Total : 243 bits / packet header National Cheng Kung University CSIE Computer & Internet Architecture Lab 1

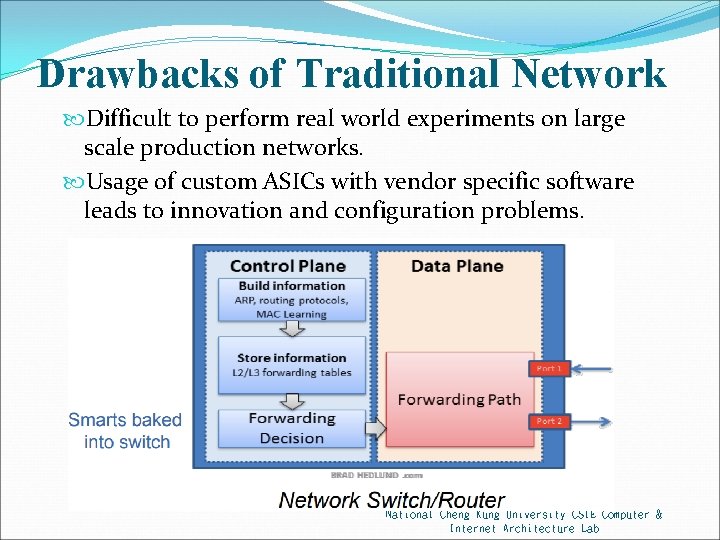
Drawbacks of Traditional Network Difficult to perform real world experiments on large scale production networks. Usage of custom ASICs with vendor specific software leads to innovation and configuration problems. National Cheng Kung University CSIE Computer & Internet Architecture Lab

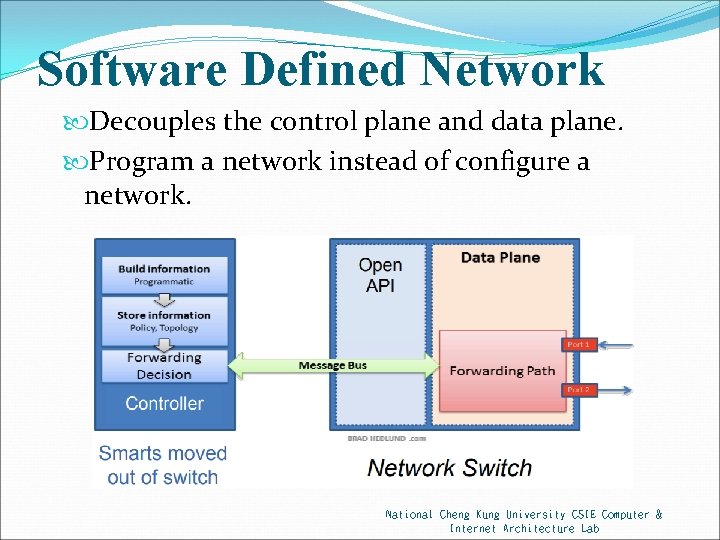
Software Defined Network Decouples the control plane and data plane. Program a network instead of configure a network. National Cheng Kung University CSIE Computer & Internet Architecture Lab

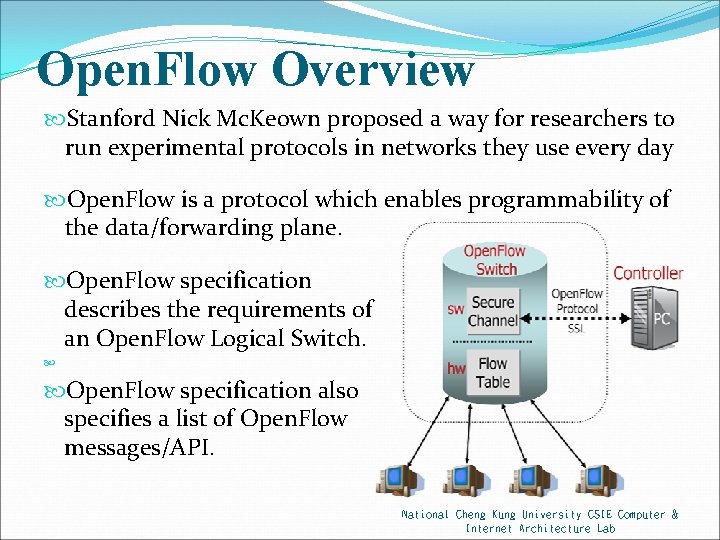
Open. Flow Overview Stanford Nick Mc. Keown proposed a way for researchers to run experimental protocols in networks they use every day Open. Flow is a protocol which enables programmability of the data/forwarding plane. Open. Flow specification describes the requirements of an Open. Flow Logical Switch. Open. Flow specification also specifies a list of Open. Flow messages/API. National Cheng Kung University CSIE Computer & Internet Architecture Lab

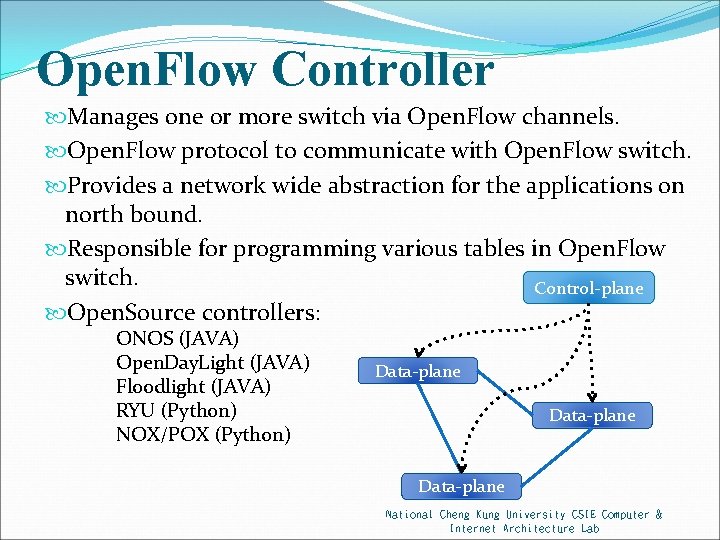
Open. Flow Controller Manages one or more switch via Open. Flow channels. Open. Flow protocol to communicate with Open. Flow switch. Provides a network wide abstraction for the applications on north bound. Responsible for programming various tables in Open. Flow switch. Control-plane Open. Source controllers: ONOS (JAVA) Open. Day. Light (JAVA) Floodlight (JAVA) RYU (Python) NOX/POX (Python) Data-plane National Cheng Kung University CSIE Computer & Internet Architecture Lab

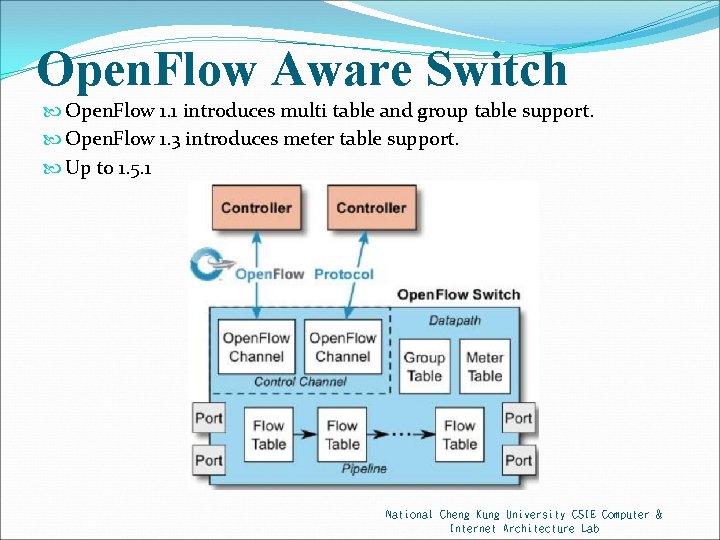
Open. Flow Aware Switch Open. Flow 1. 1 introduces multi table and group table support. Open. Flow 1. 3 introduces meter table support. Up to 1. 5. 1 National Cheng Kung University CSIE Computer & Internet Architecture Lab

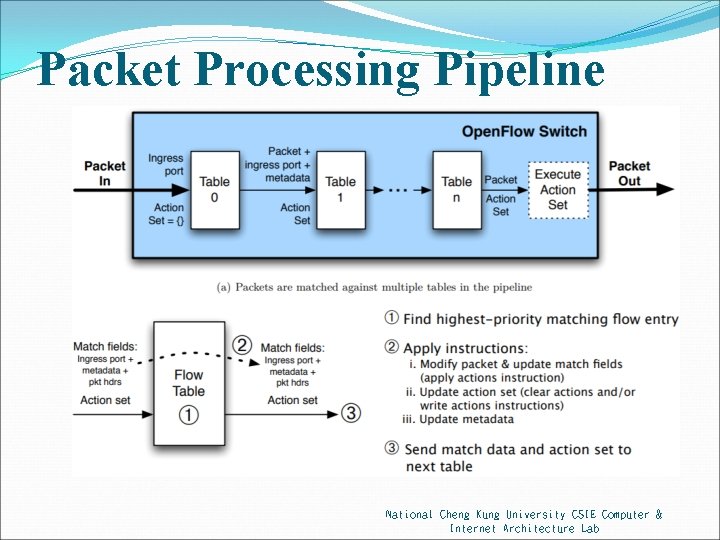
Packet Processing Pipeline National Cheng Kung University CSIE Computer & Internet Architecture Lab

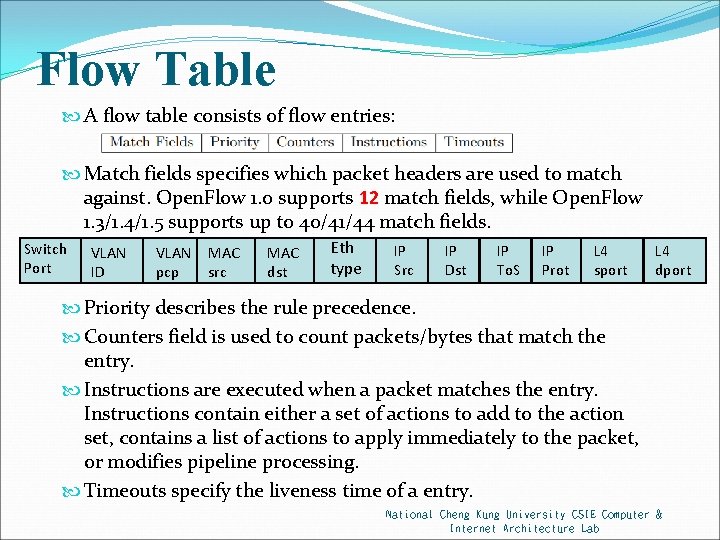
Flow Table A flow table consists of flow entries: Match fields specifies which packet headers are used to match against. Open. Flow 1. 0 supports 12 match fields, while Open. Flow 1. 3/1. 4/1. 5 supports up to 40/41/44 match fields. Switch Port VLAN ID VLAN pcp MAC src MAC dst Eth type IP Src IP Dst IP To. S IP Prot L 4 sport L 4 dport Priority describes the rule precedence. Counters field is used to count packets/bytes that match the entry. Instructions are executed when a packet matches the entry. Instructions contain either a set of actions to add to the action set, contains a list of actions to apply immediately to the packet, or modifies pipeline processing. Timeouts specify the liveness time of a entry. National Cheng Kung University CSIE Computer & Internet Architecture Lab

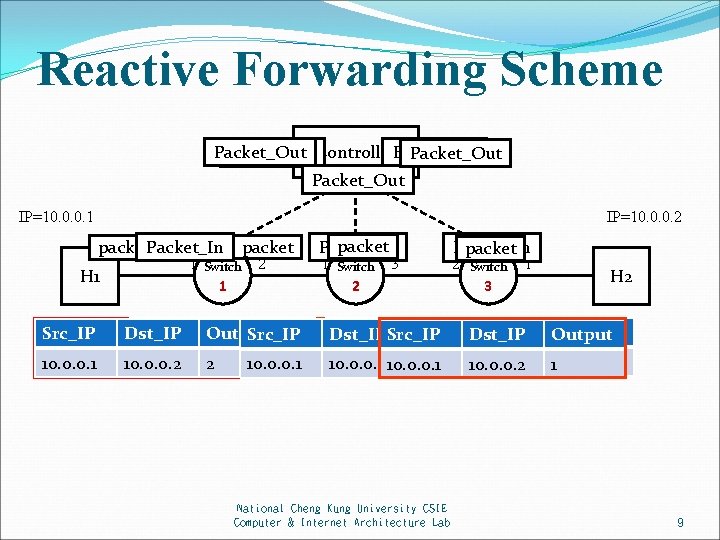
Reactive Forwarding Scheme Packet_Out Flow_Mod Controller. Flow_Mod Packet_Out IP=10. 0. 0. 2 IP=10. 0. 0. 1 packet. Packet_In packet 1 Switch 1 H 1 2 Src_IP Buffer ID Value Dst_IP Output Src_IP 10. 0. 0. 1 123 10. 0. 0. 2 2 Packet 10. 0. 0. 1 packet Packet_In 1 Switch 2 3 Packet_In packet 2 Switch 3 1 Buffer ID Value Buffer ID Dst_IP Output Src_IP Dst_IP 123 10. 0. 0. 2 3 Packet 10. 0. 0. 1 10. 0. 0. 2 National Cheng Kung University CSIE Computer & Internet Architecture Lab H 2 Value Output Packet 1 9

Hash-based Open. Flow Packet Classification on Heterogeneous System Architecture (在異質性系統架構上之以Hash為基礎的 Open. Flow封包分類) Single hash table can not process the macroflow rules. Linear Search in the macroflow tables is very slow. Binary Range Tree and Binary Trie are not efficient for the fields eith only exact values. National Cheng Kung University CSIE Computer & Internet Architecture Lab 10

Proposed scheme We proposed a hash-based and decision-tree based scheme to process the fields those contain exact value This scheme can be used as an accelerator for traditional packet classification method. National Cheng Kung University CSIE Computer & Internet Architecture Lab 11

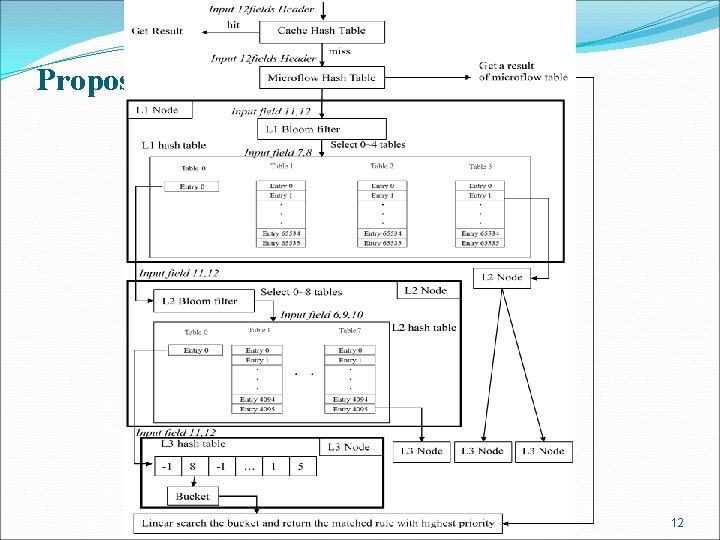
Proposed scheme – Overview National Cheng Kung University CSIE Computer & Internet Architecture Lab 12

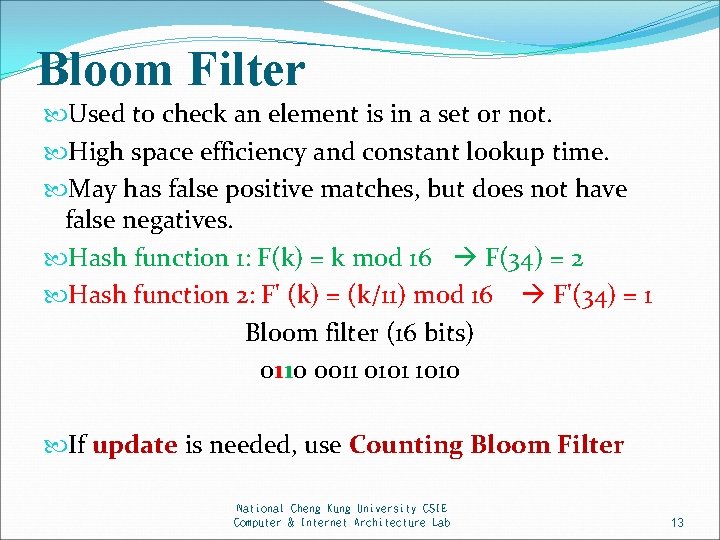
Bloom Filter Used to check an element is in a set or not. High space efficiency and constant lookup time. May has false positive matches, but does not have false negatives. Hash function 1: F(k) = k mod 16 F(34) = 2 Hash function 2: F' (k) = (k/11) mod 16 F'(34) = 1 Bloom filter (16 bits) 0110 0011 0101 1010 If update is needed, use Counting Bloom Filter National Cheng Kung University CSIE Computer & Internet Architecture Lab 13

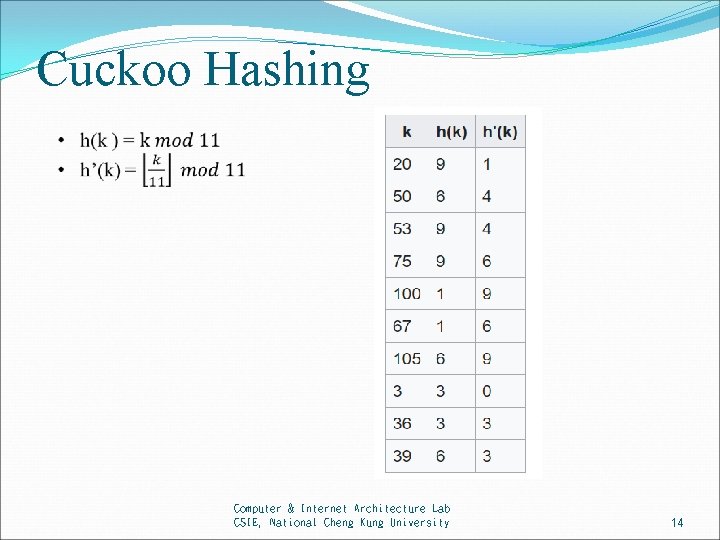
Cuckoo Hashing Computer & Internet Architecture Lab CSIE, National Cheng Kung University 14

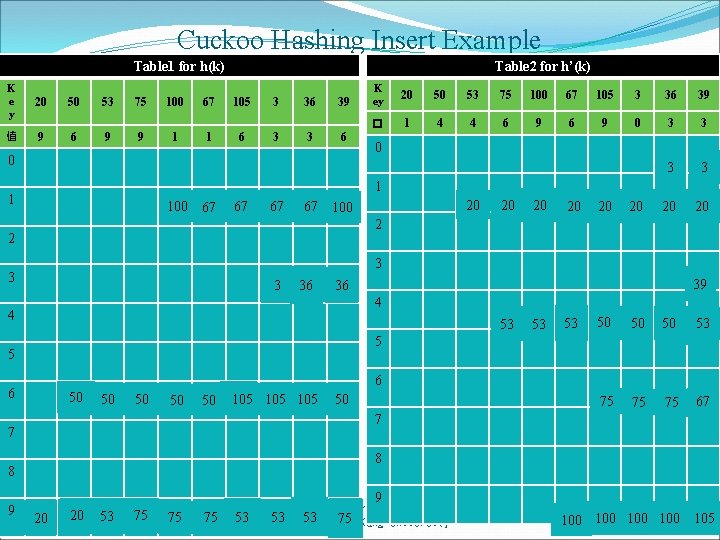
Cuckoo Hashing Insert Example Table 2 for h’(k) Table 1 for h(k) K e y 20 值 9 50 6 53 9 75 9 100 1 67 1 105 6 3 3 36 3 39 6 0 20 50 53 75 100 67 105 3 36 39 � 1 4 4 6 9 0 3 3 20 20 0 1 1 100 67 67 100 67 20 20 2 2 3 36 3 39 36 4 4 53 53 53 50 50 75 75 67 75 75 53 50 5 5 6 6 50 50 50 105 105 50 39 7 7 8 8 9 K ey 9 20 20 53 20 75 53 75 75 Computer & Internet Architecture Lab 53 53 Cheng 53 National 75 53 Kung University 75 CSIE, 105 100 100 100

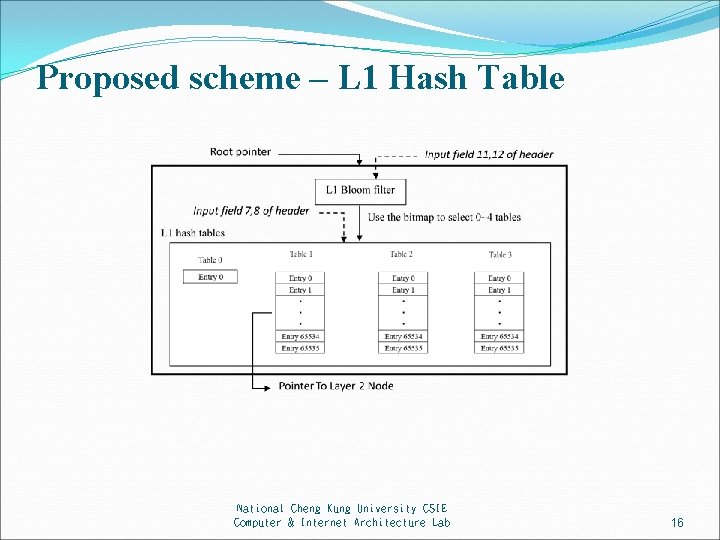
Proposed scheme – L 1 Hash Table National Cheng Kung University CSIE Computer & Internet Architecture Lab 16

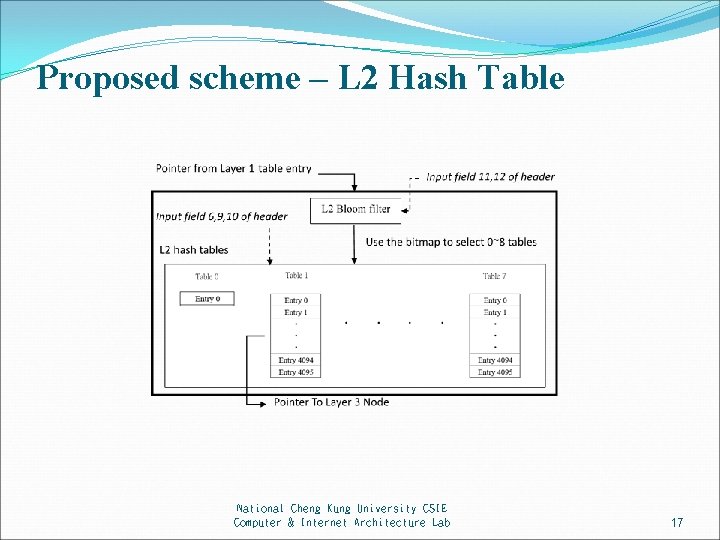
Proposed scheme – L 2 Hash Table National Cheng Kung University CSIE Computer & Internet Architecture Lab 17

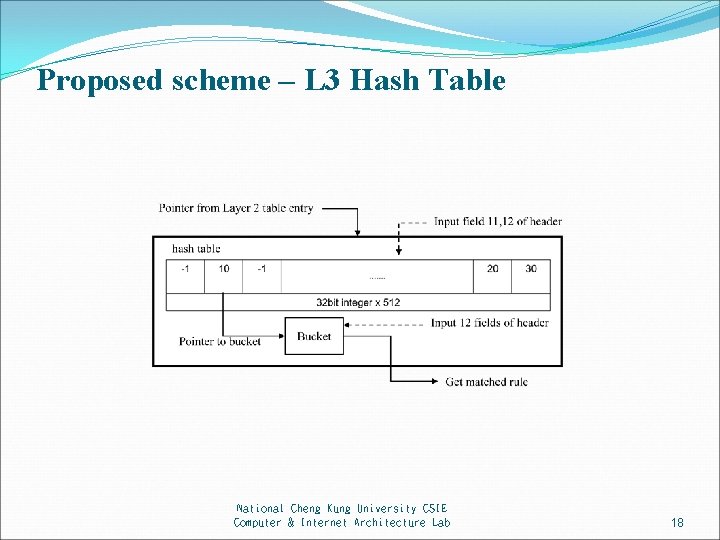
Proposed scheme – L 3 Hash Table National Cheng Kung University CSIE Computer & Internet Architecture Lab 18

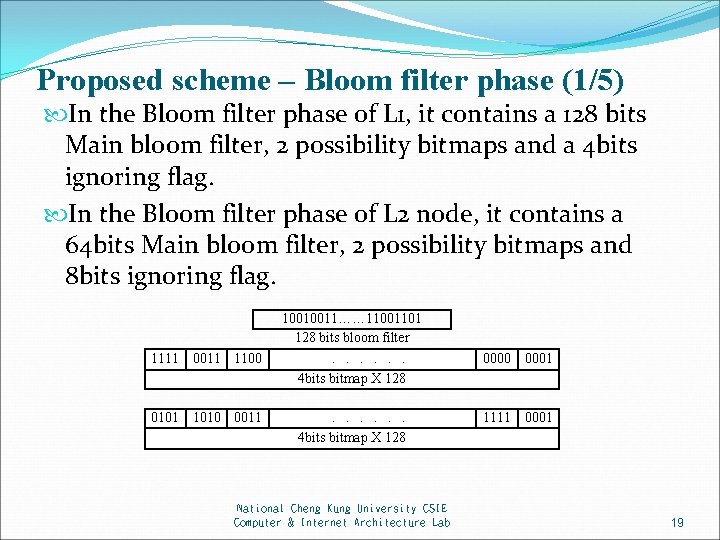
Proposed scheme – Bloom filter phase (1/5) In the Bloom filter phase of L 1, it contains a 128 bits Main bloom filter, 2 possibility bitmaps and a 4 bits ignoring flag. In the Bloom filter phase of L 2 node, it contains a 64 bits Main bloom filter, 2 possibility bitmaps and 8 bits ignoring flag. 1111 0011 1100 0101 1010 0011 10010011…… 11001101 128 bits bloom filter ...... 4 bits bitmap X 128 National Cheng Kung University CSIE Computer & Internet Architecture Lab 0000 0001 1111 0001 19

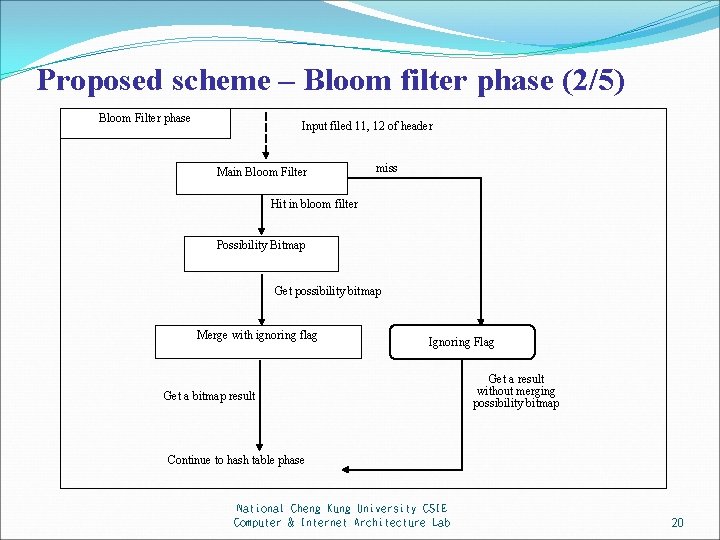
Proposed scheme – Bloom filter phase (2/5) Bloom Filter phase Input filed 11, 12 of header Main Bloom Filter miss Hit in bloom filter Possibility Bitmap Get possibility bitmap Merge with ignoring flag Ignoring Flag Get a bitmap result Get a result without merging possibility bitmap Continue to hash table phase National Cheng Kung University CSIE Computer & Internet Architecture Lab 20

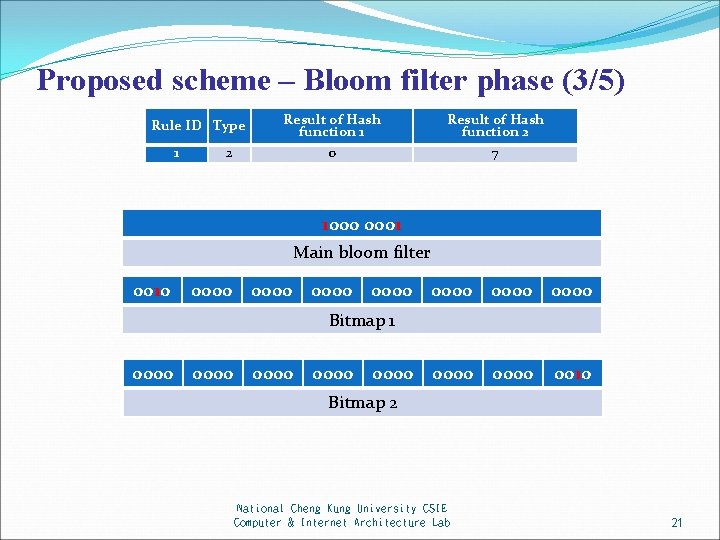
Proposed scheme – Bloom filter phase (3/5) Rule ID Type 1 02 Result of Hash function 1 Result of Hash function 2 0 7 0000 1000 0001 Main bloom filter 0000 0010 0000 0000 Bitmap 1 0000 0000 0000 0000 0010 Bitmap 2 National Cheng Kung University CSIE Computer & Internet Architecture Lab 21

Proposed scheme – Bloom filter phase (4/5) Main Bloom filter 0011 0101 8 bits bloom filter • Use 2 hash functions • Result of hash function 1 = 2 • Result of hash function 2 = 7 National Cheng Kung University CSIE Computer & Internet Architecture Lab 22

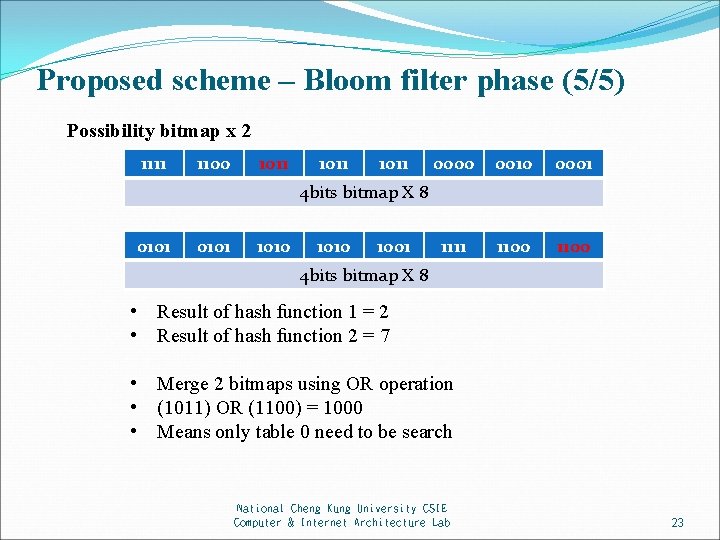
Proposed scheme – Bloom filter phase (5/5) Possibility bitmap x 2 1111 1100 1011 0000 0010 0001 1111 1100 4 bits bitmap X 8 0101 1010 1001 4 bits bitmap X 8 • Result of hash function 1 = 2 • Result of hash function 2 = 7 • Merge 2 bitmaps using OR operation • (1011) OR (1100) = 1000 • Means only table 0 need to be search National Cheng Kung University CSIE Computer & Internet Architecture Lab 23

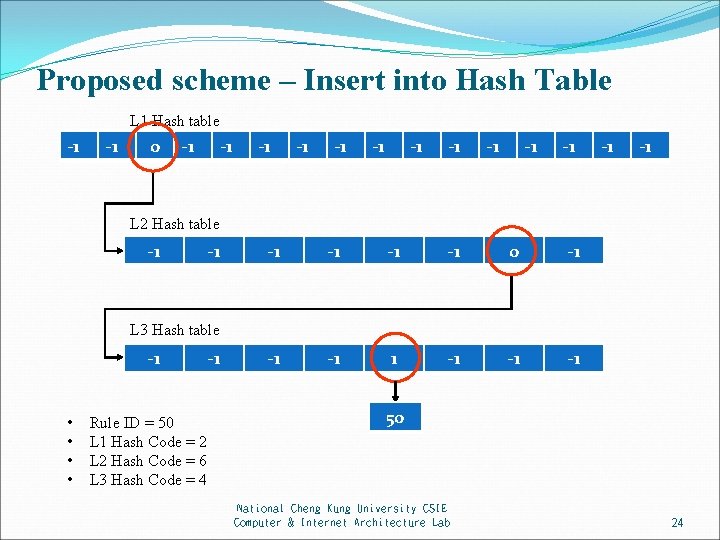
Proposed scheme – Insert into Hash Table L 1 Hash table -1 -1 -10 -1 -1 -1 -1 L 2 Hash table -1 -1 -1 0 -1 -1 -11 -1 -1 -1 L 3 Hash table -1 • • -1 Rule ID = 50 L 1 Hash Code = 2 L 2 Hash Code = 6 L 3 Hash Code = 4 50 -1 National Cheng Kung University CSIE Computer & Internet Architecture Lab 24

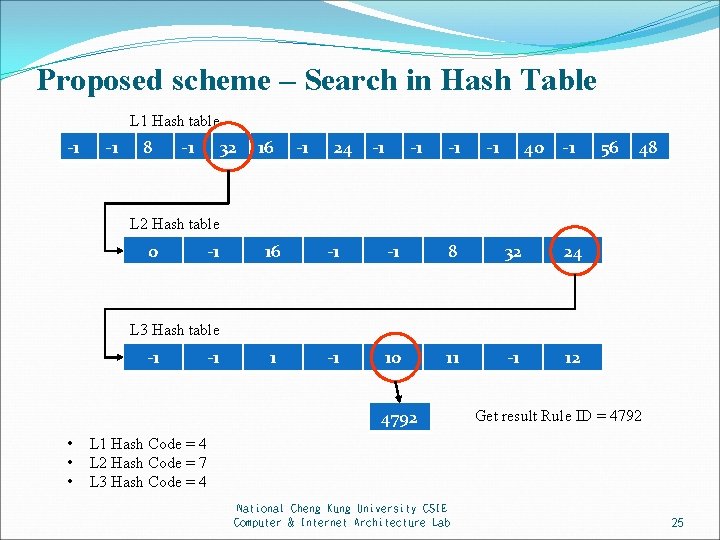
Proposed scheme – Search in Hash Table L 1 Hash table -1 -1 8 -1 32 16 -1 24 -1 -1 40 -1 56 48 L 2 Hash table 0 -1 16 -1 -1 8 32 24 1 -1 10 11 -1 12 L 3 Hash table -1 -1 4792 • • • Get result Rule ID = 4792 L 1 Hash Code = 4 L 2 Hash Code = 7 L 3 Hash Code = 4 National Cheng Kung University CSIE Computer & Internet Architecture Lab 25

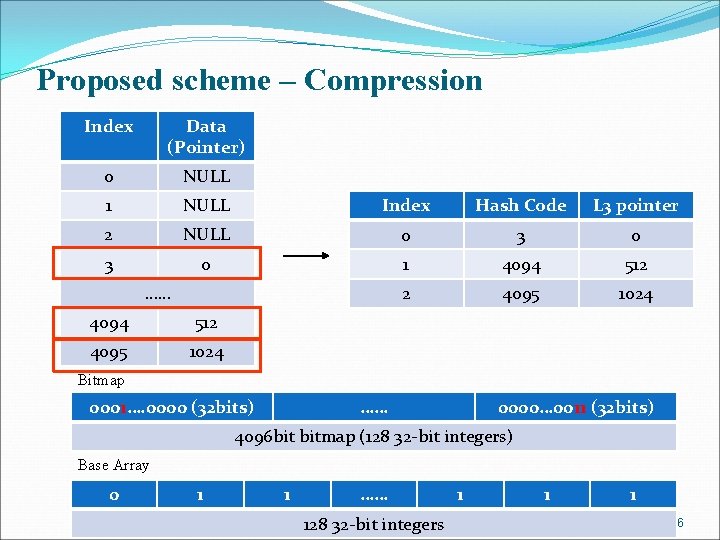
Proposed scheme – Compression Index Data (Pointer) 0 NULL 1 NULL Index Hash Code L 3 pointer 2 NULL 0 3 0 1 4094 512 2 4095 1024 …… 4094 512 4095 1024 Bitmap 0000…. 0000 (32 bits) 0001…. 0000 (32 bits) …… 0000 (32 bits) 0000… 0011 (32 bits) 4096 bit bitmap (32 bit integer x 128) 4096 bit bitmap (128 32 -bit integers) Base Array 0 01 01 …… National Cheng Kung University CSIE Computer & Internet Architecture Lab 128 32 -bit integers 32 bit integer x 128 01 01 01 26

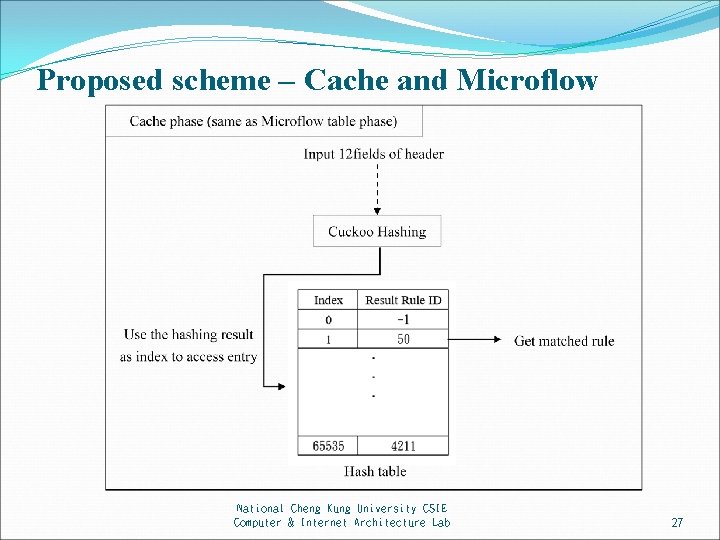
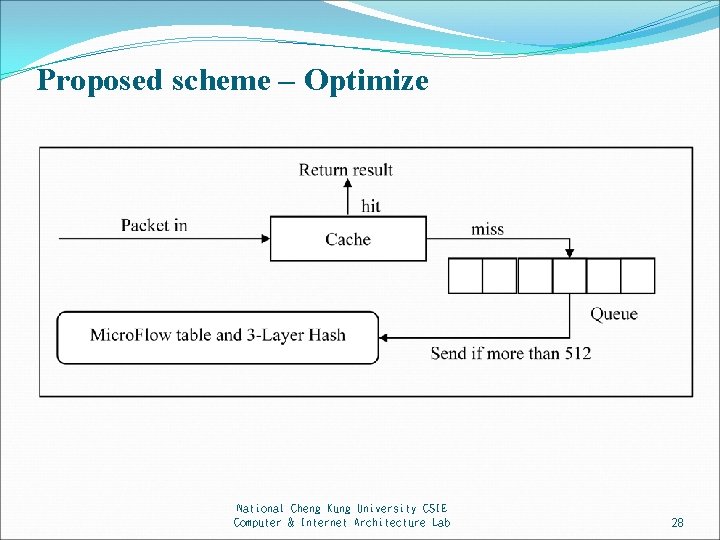
Proposed scheme – Cache and Microflow National Cheng Kung University CSIE Computer & Internet Architecture Lab 27

Proposed scheme – Optimize National Cheng Kung University CSIE Computer & Internet Architecture Lab 28

Outline Introduction Related Work Proposed Schemes Experimental Result Conclusion National Cheng Kung University CSIE Computer & Internet Architecture Lab 29

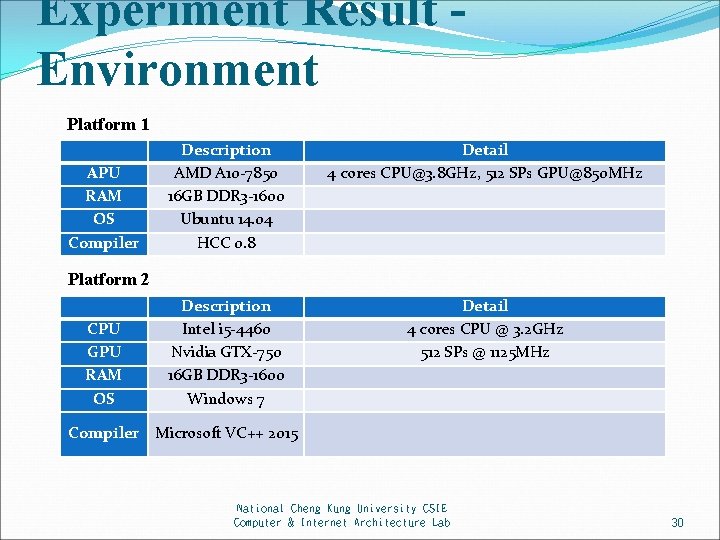
Experiment Result Environment Platform 1 APU RAM OS Compiler Description AMD A 10 -7850 16 GB DDR 3 -1600 Ubuntu 14. 04 HCC 0. 8 Detail 4 cores CPU@3. 8 GHz, 512 SPs GPU@850 MHz Description Intel i 5 -4460 Nvidia GTX-750 16 GB DDR 3 -1600 Windows 7 Detail 4 cores CPU @ 3. 2 GHz 512 SPs @ 1125 MHz Platform 2 CPU GPU RAM OS Compiler Microsoft VC++ 2015 National Cheng Kung University CSIE Computer & Internet Architecture Lab 30

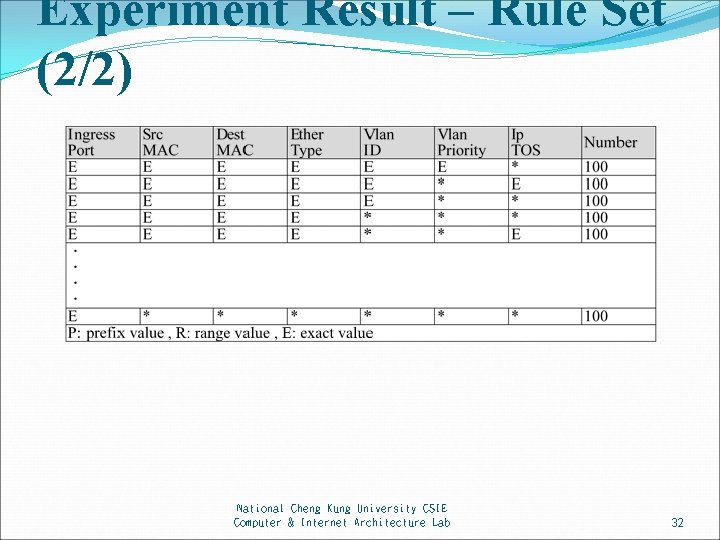
Experiment Result – Rule Set (1/2) We use FRu. G to generate two rule sets. One ruleset contains only one type of rule, contains no wildcard (*), the size is 50 K Another one ruleset contains 127 types of rules, contains wildcards (*), the size is 12 K. All the parameter of generator is set as default. National Cheng Kung University CSIE Computer & Internet Architecture Lab 31

Experiment Result – Rule Set (2/2) National Cheng Kung University CSIE Computer & Internet Architecture Lab 32

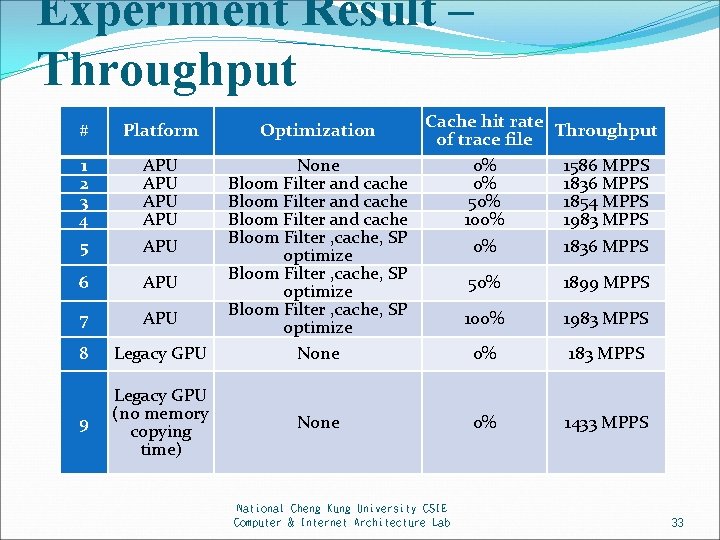
Experiment Result – Throughput # Platform Optimization 1 2 3 4 5 APU APU APU 6 APU 7 APU 8 Legacy GPU None Bloom Filter and cache Bloom Filter , cache, SP optimize None 9 Legacy GPU (no memory copying time) Cache hit rate of trace file 0% 0% 50% 100% 0% Throughput 50% 1899 MPPS 100% 1983 MPPS 0% 1433 MPPS None National Cheng Kung University CSIE Computer & Internet Architecture Lab 1586 MPPS 1836 MPPS 1854 MPPS 1983 MPPS 1836 MPPS 33

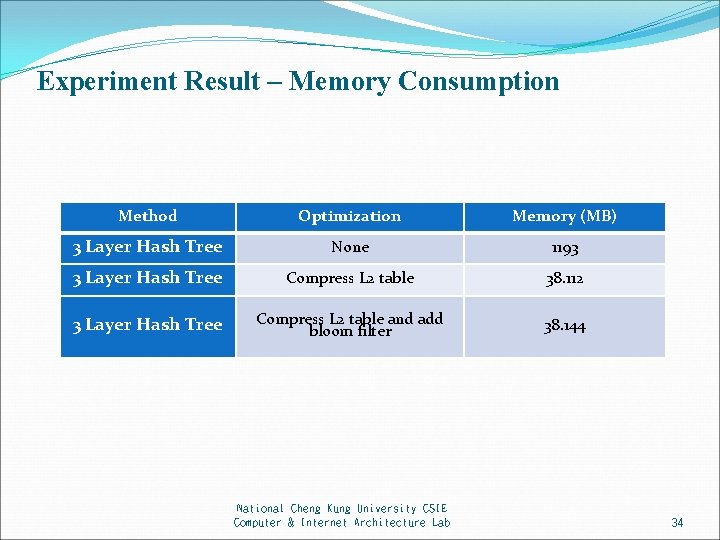
Experiment Result – Memory Consumption Method Optimization Memory (MB) 3 Layer Hash Tree None 1193 3 Layer Hash Tree Compress L 2 table 38. 112 3 Layer Hash Tree Compress L 2 table and add bloom filter 38. 144 National Cheng Kung University CSIE Computer & Internet Architecture Lab 34

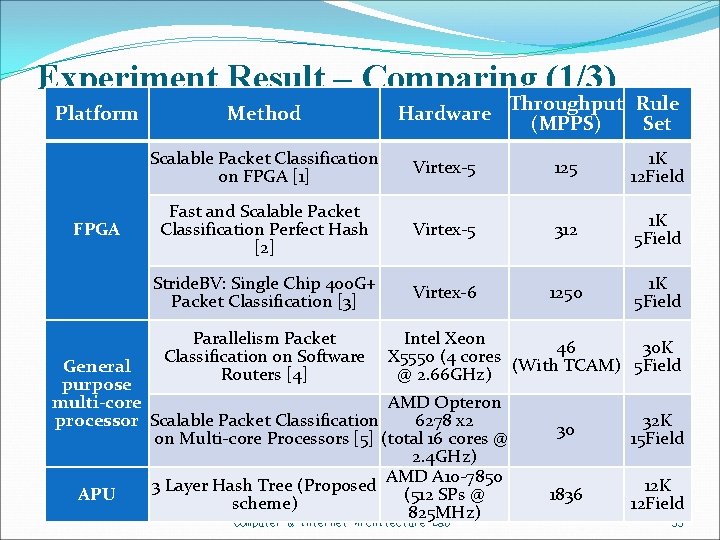
Experiment Result – Comparing (1/3) Platform FPGA Method Rule Hardware Throughput (MPPS) Set Scalable Packet Classification on FPGA [1] Virtex-5 125 1 K 12 Field Fast and Scalable Packet Classification Perfect Hash [2] Virtex-5 312 1 K 5 Field Stride. BV: Single Chip 400 G+ Packet Classification [3] Virtex-6 1250 1 K 5 Field Parallelism Packet Classification on Software Routers [4] Intel Xeon 46 30 K X 5550 (4 cores (With TCAM) 5 Field @ 2. 66 GHz) General purpose multi-core AMD Opteron processor Scalable Packet Classification 6278 x 2 on Multi-core Processors [5] (total 16 cores @ 2. 4 GHz) AMD A 10 -7850 3 Layer Hash Tree (Proposed APU (512 SPs @ scheme) National Cheng Kung University CSIE 825 MHz) Computer & Internet Architecture Lab 30 32 K 15 Field 1836 12 K 12 Field 35

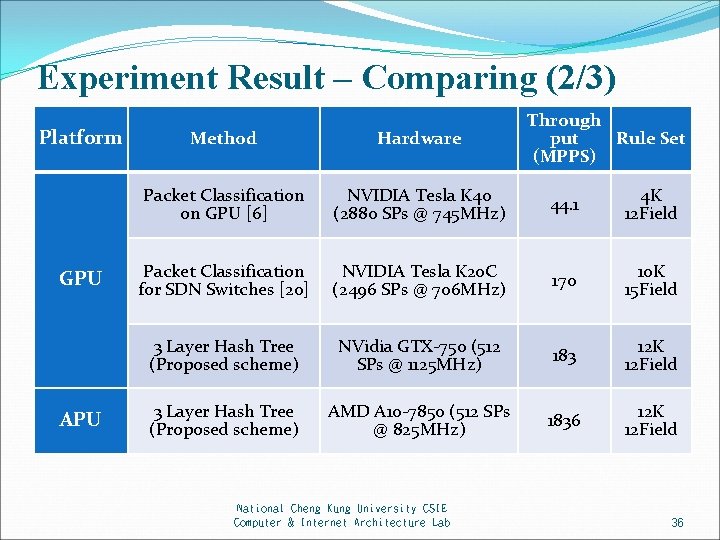
Experiment Result – Comparing (2/3) Platform GPU APU Through Rule Set put (MPPS) Method Hardware Packet Classification on GPU [6] NVIDIA Tesla K 40 (2880 SPs @ 745 MHz) 44. 1 4 K 12 Field Packet Classification for SDN Switches [20] NVIDIA Tesla K 20 C (2496 SPs @ 706 MHz) 170 10 K 15 Field 3 Layer Hash Tree (Proposed scheme) NVidia GTX-750 (512 SPs @ 1125 MHz) 183 12 K 12 Field 3 Layer Hash Tree (Proposed scheme) AMD A 10 -7850 (512 SPs @ 825 MHz) 1836 12 K 12 Field National Cheng Kung University CSIE Computer & Internet Architecture Lab 36

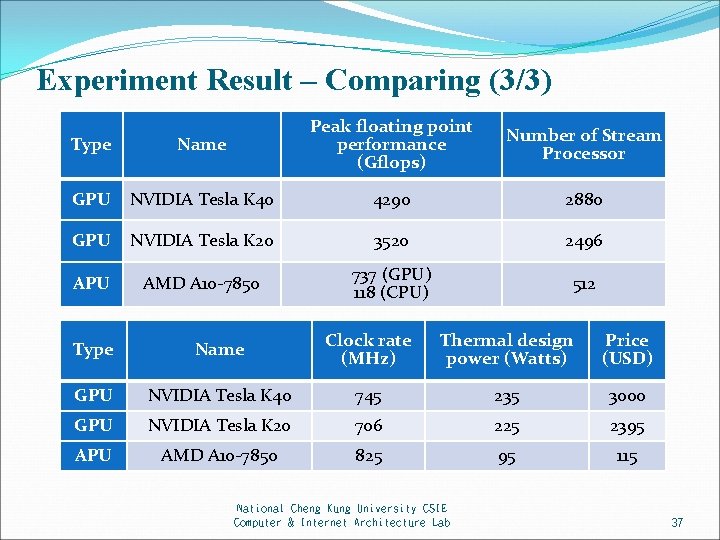
Experiment Result – Comparing (3/3) Type Name Peak floating point performance (Gflops) GPU NVIDIA Tesla K 40 4290 2880 GPU NVIDIA Tesla K 20 3520 2496 APU AMD A 10 -7850 737 (GPU) 118 (CPU) 512 Number of Stream Processor Type Name Clock rate (MHz) Thermal design power (Watts) Price (USD) GPU NVIDIA Tesla K 40 745 235 3000 GPU NVIDIA Tesla K 20 706 225 2395 APU AMD A 10 -7850 825 95 115 National Cheng Kung University CSIE Computer & Internet Architecture Lab 37

Conclusion In this thesis, we proposed a high throughput, low cost and low power consumption scheme, it can achieve high throughput on APU platform. The throughput of our scheme can achieve 1836 MPPS, and achieve 1983 MPPS with cache. The memory consumption is 38 MB. The power consumption of whole platform is about 115 watts. National Cheng Kung University CSIE Computer & Internet Architecture Lab 38

Thanks for Your Attention National Cheng Kung University CSIE Computer & Internet Architecture Lab 39