Online Payment Systems 11 Online Payment Systems Online


















- Slides: 31

Online Payment Systems 11. Online Payment Systems

Online Payment Basics • Online payment systems – Evolving- Competition for dominance – Faster, Cheaper, Convenient – Environmental friendly • Ways to make payment (consumer) – Q cash, smart cards, credit cards, debit cards – Electronic transfer: Digital, automated • Credit cards~ Worldwide: 90% of online payments • Online business payment requirements – Safe, convenient, widely accepted 2

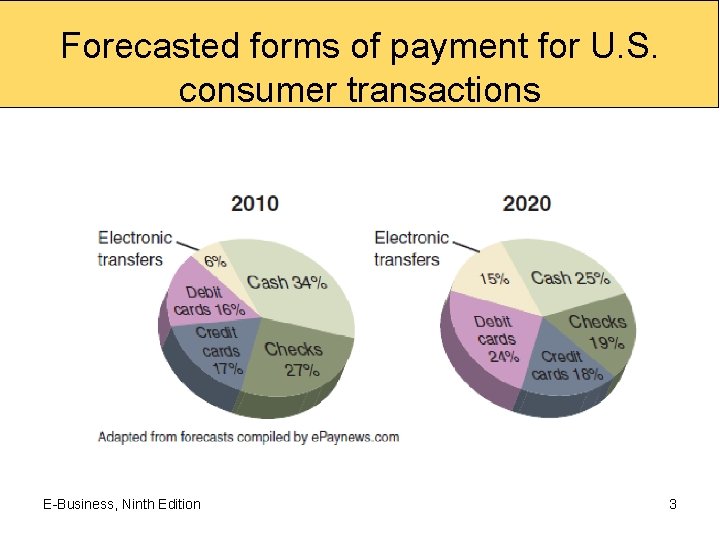
Forecasted forms of payment for U. S. consumer transactions E-Business, Ninth Edition 3

Scrip • Minted by a company. . . – Cannot be exchanged for cash – Exchanged for goods or services • Like a gift certificate: good at every store – Focus: not-for-profit fundraising market Online Payment Basics (cont’d. ) 4

Payment Cards • Credit cards, debit cards, charge cards • Credit card (Visa, Master. Card) – – Balance usually incur interest fees Widely accepted Consumer protection: 30 -day dispute period Occur as Monthly bill • Debit card – Using cardholder’s bank account • Tied to bank account from which funds are withdrawn for each purpose 5

Payment Cards (cont’d. ) • Charge card (American Express, HSBC Amanah mastercard – Used with an account which must be paid in full when a statement is issued – Entire amount due at end of billing period – No line of credit or interest charges – Examples: department store, Gas Station • Retailers may offer their own charge cards • Single-use cards- disposable numbers – Virtual credit card provide various alias credit card number for the same account. – Valid for one transaction only – Designed to prevent unscrupulous vendor fraud 6

Payment Cards. . . • Advantage – Worldwide acceptance, Easy Currency conversion – Fraud protection, Assurance of payments for merchants – Banks make money by charging merchants a credit card processing fee on each transaction • Disadvantage – Per-transaction fees, monthly processing fees – Goods and services prices slightly higher – Annual fee for consumers 7

Payment Acceptance and Processing • EMV standard (Europay, Mastercard and Visa) – Single standard handling payment card transactions • Online stores, mail order stores – Must ship merchandise within 30 days of charging payment Global Standard for inter operation of integrated circuit card and IC card capable point of sale terminal and ATM for authenticating and credit and debit card transaction. 8

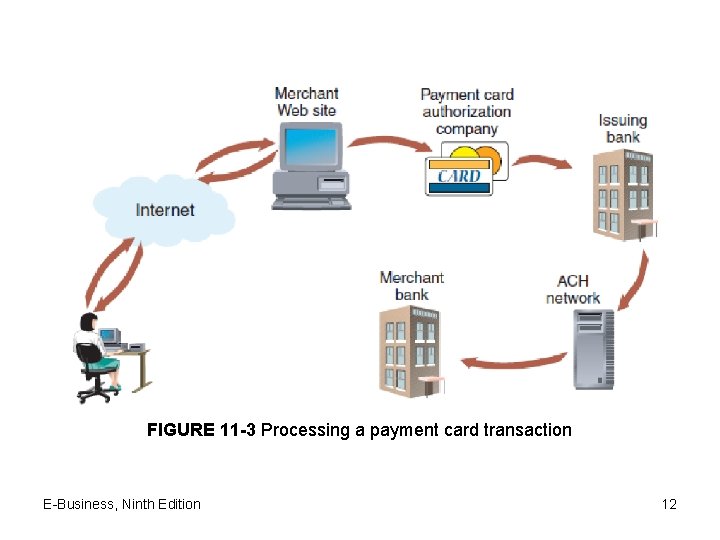
Open and closed loop systems • Closed loop systems – Card issuer pays merchant directly – Does not use intermediary – American Express, Discover Card • Open loop systems (three or more parties) – Third party (intermediary bank) processes transaction – EX: Visa, Master. Card: not issued directly to consumers – Credit card associations: operated by association member banks Payment Acceptance and Processing (cont’d. ) 9

Merchant accounts • Merchant bank (acquiring bank) – Bank wanting to accept payment cards – Dealing in commercial loans and investment – Combination of Banking and consultancy services( financial, marketing, managerial and legal matter) • Merchant account – Business needs to process payment cards – Issued by Merchant bank – Bank account that allow business to accept debit or credit cards. • Chargeback: when customer disputes the transaction or return the purchased item 10

Processing payment cards online • Payment processing service providers – Companies offering payment card processing • Example: Internet. Secure – – Supports Canadian and U. S. Visa and Master. Card Provides risk management and fraud detection Bank-approved payment card processing infrastructure Notification of approved orders • Automated Clearing House (ACH): Financial network used for Electronic payment • No paper checks, wire transfer or cash • Merchant: owns a retail business and sell goods. (wholesaler, Retailer) 11

FIGURE 11 -3 Processing a payment card transaction E-Business, Ninth Edition 12

Micropayments and Small Payments – Not implemented very well on the Web yet – Human psychology about this payment is not good • Companies that developed micropayment systems – All failed in the US- Millicent, Digi. Cash – No company gained broad acceptance of its system E-Business, Ninth Edition 13

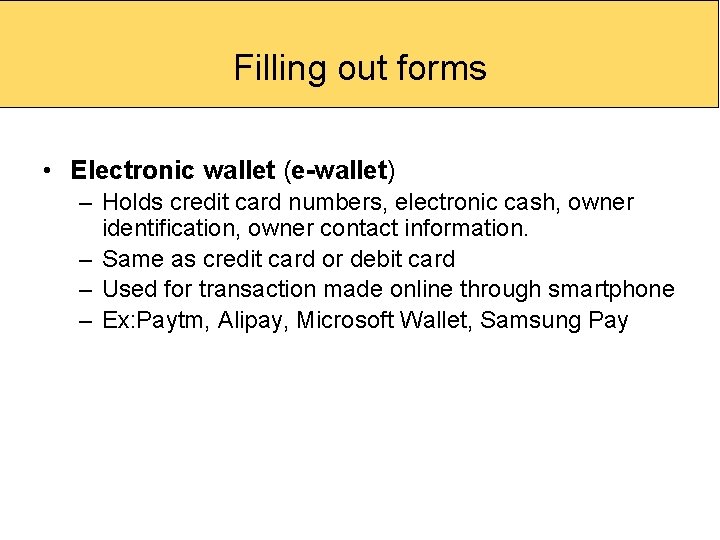
Filling out forms • Electronic wallet (e-wallet) – Holds credit card numbers, electronic cash, owner identification, owner contact information. – Same as credit card or debit card – Used for transaction made online through smartphone – Ex: Paytm, Alipay, Microsoft Wallet, Samsung Pay

Stored-Value Cards • Microchip smart card or magnetic strip plastic card – Electronic bank debit card – Examples: phone, subway, bus and rail Service for consumers who can’t open checking Or other deposit accounts. Ex: ACH fund transfer, credit or debit card, Magnetic strip cards, smart cards store e-cash – Smart card better suited for Internet transactions 15

Smart Cards • Stored-value card – Plastic card with embedded microchip • 100 x More information than magnetic strip – Provide: Personal Information, authentication, SIM Financial facts, security and health insurance information. . . • Encrypted- Safer than conventional credit cards • Popular in Europe, Asia – Public telephone calls, cable television programs E-Business, Ninth Edition 16

Criminal Activity and Payment Systems: Phishing and Identity Theft • Attractive for criminal – Large amounts of money provide tempting targets • Phishing expedition – Attacker sends e-mail message – Email message tells recipient: account compromised • Recipient must log on to account to correct problem – E-mail message includes different links E-Business, Ninth Edition 17

Internet Technologies and the Banking Industry (cont’d) 2. Mobile Banking ü Banks exploring mobile commerce potential ü 2009: banks launched sites allowing customers using smart phones to: v Obtain bank balance, view account statement, find a nearby ATM ü Future plans v Offering downloadable applications smart phone users can install v Use to transact all types of banking business E-Business, Ninth Edition 18

Criminal Activity and Payment Systems: Phishing and Identity Theft • Online payment systems • Offer criminals and criminal enterprises an attractive arena in which to operate – Average consumers: easy prey – Large amounts of money provide tempting targets – Phishing expedition – Technique for committing fraud against online businesses customers – Particular concern to financial institutions E-Business, Ninth Edition 19

Phishing Attacks • Basic structure q Attacker sends e-mail message To accounts with potential for an account at targeted Web site q E-mail message tells recipient: account compromised ü Recipient must log on to account to correct problem q E-mail message includes link ü Appears to be Web site login page ü Actually leads to perpetrator’s Web site disguised to look like the targeted Web site q Recipient enters login name, password ü Perpetrator captures ü Uses to access recipient’s account ü Perpetrator accesses personal information, makes E-Business, Ninth purchases, withdraws funds ü Edition 20

Phishing e-mail message 21

Phishing e-mail message ( cont’d) 22

Spear phishing • Carefully designed phishing expedition targeting a particular person or organization • Requires considerable research to control target from intruders. • Increases chance of email being opened Phishing Attacks (cont’d. ) 23

Phishing e-mail with graphics 24

Phishing Attacks (cont’d. ) • E-mail link disguise(means of altering one’s appearance to conceal one’s identity) and tricks – Example: Web server ignores all characters preceding “@”: • https: //www. paypal. com@218. 36. 41. 188/fl/login. html • Link appears different in email – Pop-up windows • Look exactly like browser address bar – Including Website graphics of financial institutions • Looks more convincing E-Business, Ninth Edition 25

Using Phishing Attacks for Identity Theft • Organized crime (racketeering) – highly organized, disciplined association for profit – Generates spam, phishing, identity theft • Identity theft – Perpetrator gathers victim’s personal information – Uses information to obtain credit – Perpetrator runs up account charges and disappears E-Business, Ninth Edition 26

Types of personal information most useful to identity thieves Full name Address Social Security number Date of birth Mother’s maiden name Personal Identification Numbers (PINs) used for ATM, debit, and credit cards Passwords or passphrases that access online accounts Bank and credit card account numbers Birth certificate Passport Credit report Financial statements: bank, credit card, investment, life insurance, loan 27

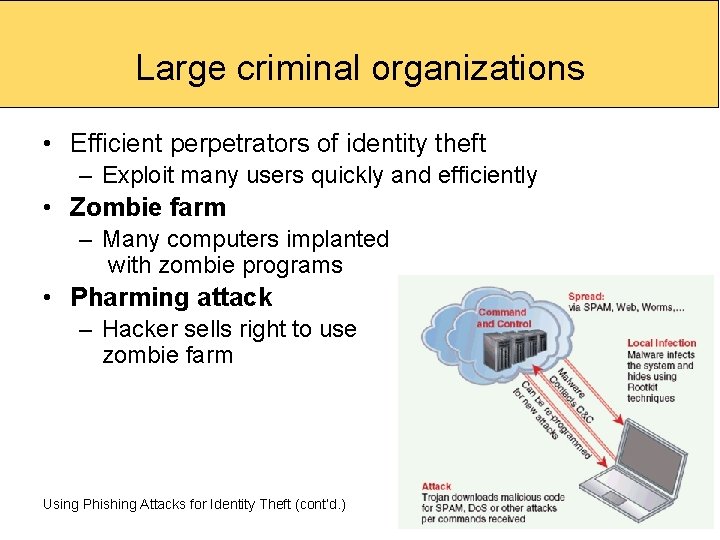
Large criminal organizations • Efficient perpetrators of identity theft – Exploit many users quickly and efficiently • Zombie farm – Many computers implanted with zombie programs • Pharming attack – Hacker sells right to use zombie farm Using Phishing Attacks for Identity Theft (cont’d. ) 28

Phishing Attack Countermeasures • Change protocol – Improve email recipients’ ability to identify message source • Educate Web site users • Contract with consulting firms specializing in antiphishing work • Monitor online chat rooms, newsgroups used by criminals, video conference and other platforms. E-Business, Ninth Edition 29

Summary • Online stores: payment forms – Credit, debit, charge cards (payment cards) • Ubiquitous, convenient, easy to use – Electronic cash advantages and potential uses • Making micropayments, stored online or offline – Electronic wallets provide convenience – Stored-value cards • Smart cards, magnetic strip cards – Banks process most monetary transactions • Use Internet technologies to process checks – Concerns: phishing expeditions, identity theft E-Business, Ninth Edition 30

Learning Objectives In this chapter, you will learn about: • The basic functions of online payment systems • The use of payment cards in electronic commerce • The history and future of electronic cash • How electronic wallets work • The use of stored-value cards in electronic commerce • Internet technologies and the banking industry E-Business, Ninth Edition 31