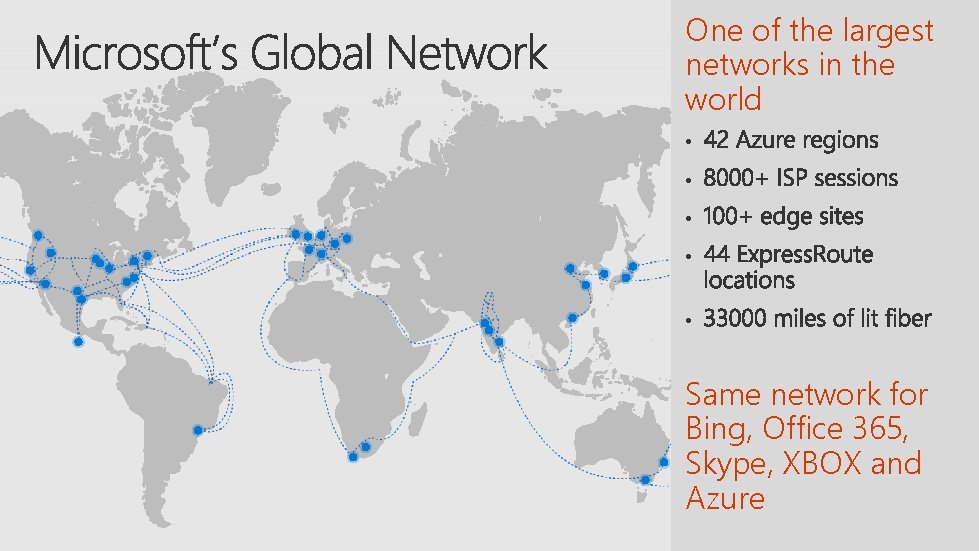
One of the largest networks in the world

















- Slides: 61



One of the largest networks in the world • • • Same network for Bing, Office 365, Skype, XBOX and Azure

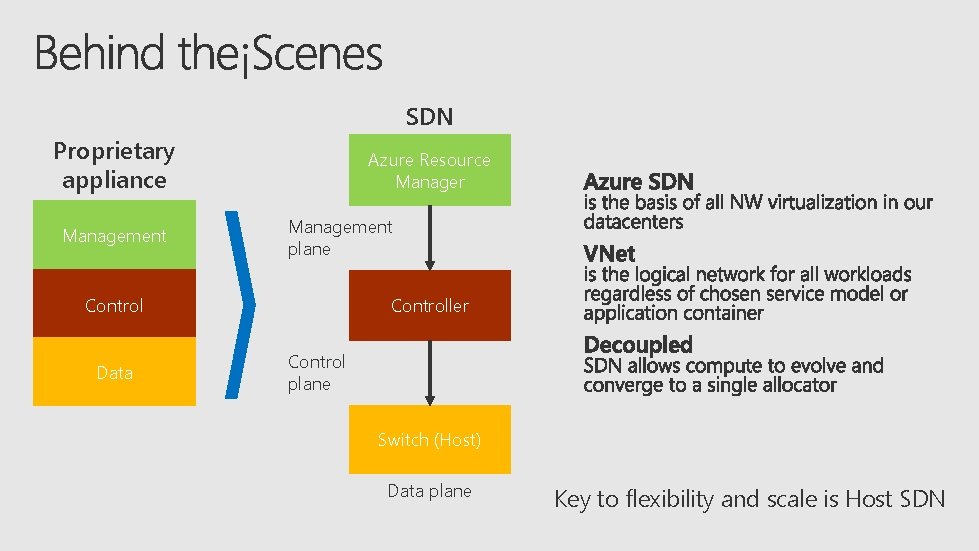
SDN Proprietary appliance Management Azure Resource Manager Management plane Control Data Controller Control plane Switch (Host) Data plane Key to flexibility and scale is Host SDN


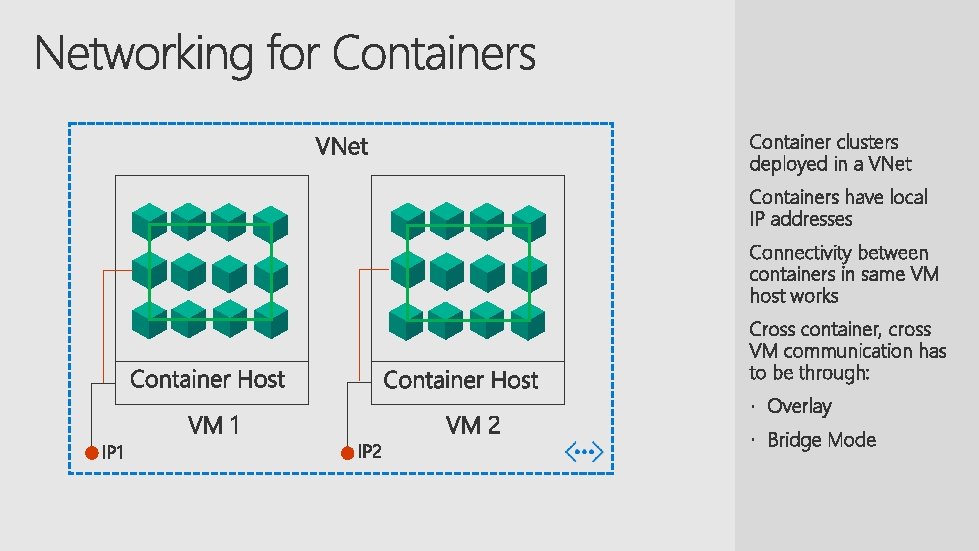
Container clusters deployed in a VNet Containers have local IP addresses Connectivity between containers in same VM host works Cross container, cross VM communication has to be through: Overlay Bridge Mode

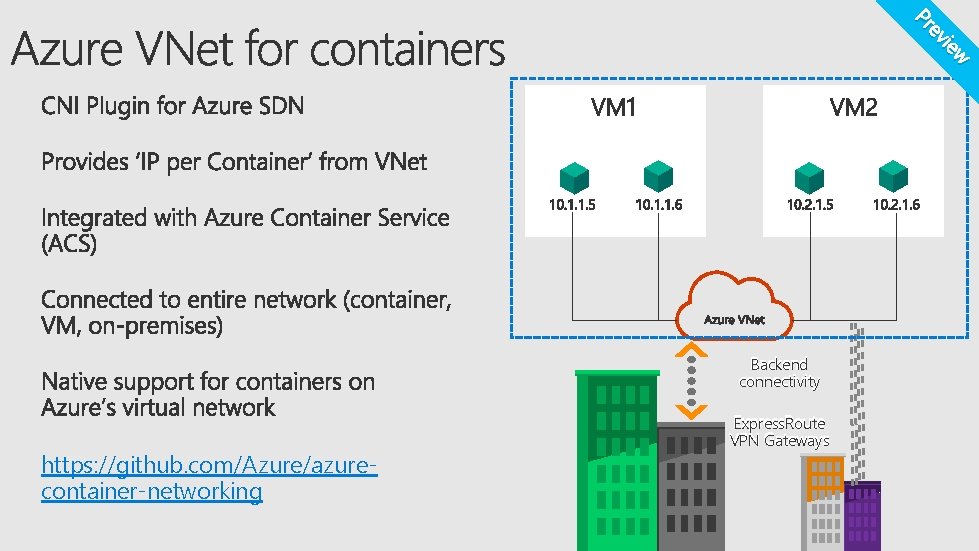
w vie e Pr Backend connectivity https: //github. com/Azure/azurecontainer-networking Express. Route VPN Gateways

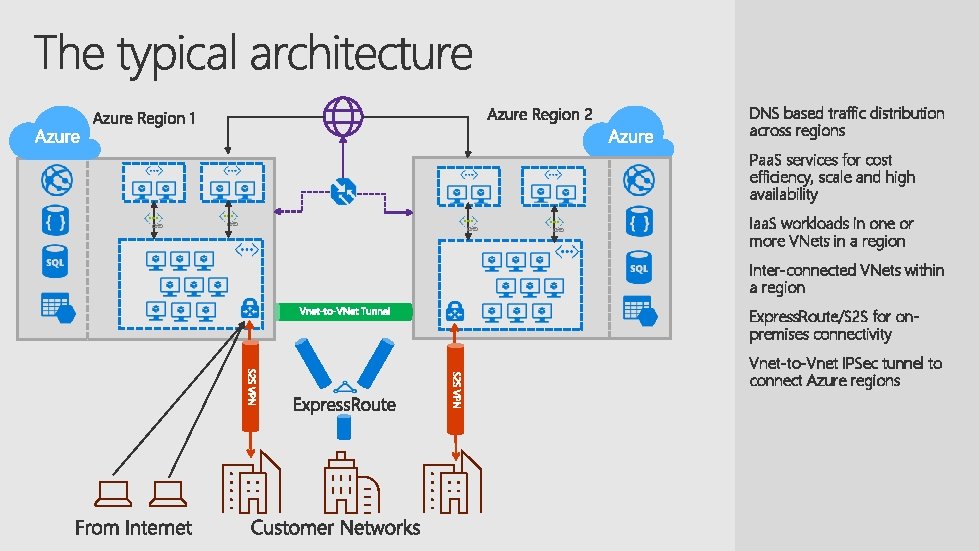
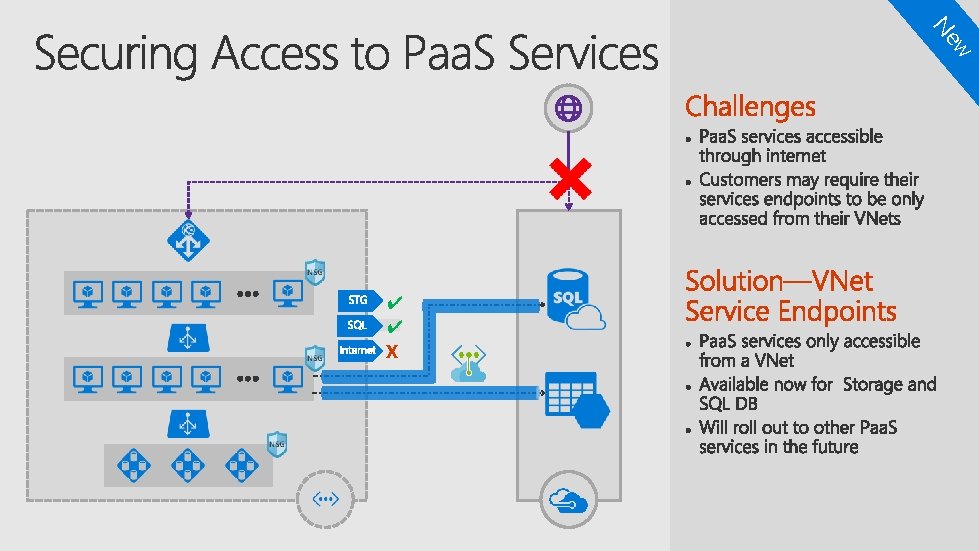
DNS based traffic distribution across regions Paa. S services for cost efficiency, scale and high availability Iaa. S workloads in one or more VNets in a region Inter-connected VNets within a region Express. Route/S 2 S for onpremises connectivity Vnet-to-Vnet IPSec tunnel to connect Azure regions


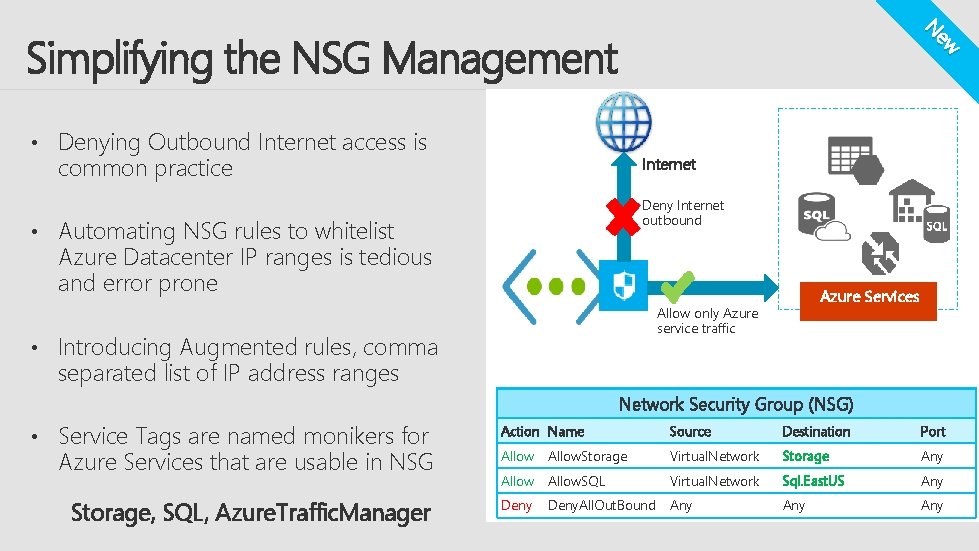
ew N Simplifying the NSG Management • Denying Outbound Internet access is common practice Internet Deny Internet outbound • Automating NSG rules to whitelist Azure Datacenter IP ranges is tedious and error prone Allow only Azure service traffic • Introducing Augmented rules, comma Azure Services separated list of IP address ranges Network Security Group (NSG) • Service Tags are named monikers for Azure Services that are usable in NSG Storage, SQL, Azure. Traffic. Manager Action Name Source Destination Port Allow. Storage Virtual. Network IP 1, IP 2 … IP 100 Storage Any Allow. SQL Virtual. Network IP 101, IP 102. . Sql. East. US Any Internet Any Deny. All. Out. Bound Any

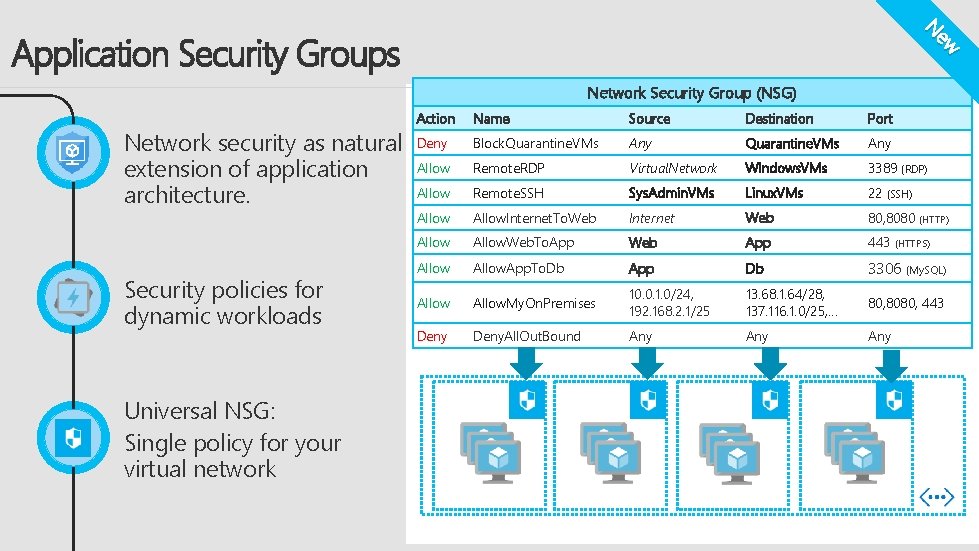
ew N Application Security Groups Network Security Group (NSG) Network security as natural extension of application architecture. Security policies for dynamic workloads Universal NSG: Single policy for your virtual network Action Name Source Destination Port Deny Block. Quarantine. VMs Any Allow Remote. RDP Virtual. Network Windows. VMs 3389 (RDP) Allow Remote. SSH Sys. Admin. VMs Linux. VMs 22 (SSH) Allow. Internet. To. Web Internet Web 80, 8080 (HTTP) Allow. Web. To. App Web App 443 (HTTPS) Allow. App. To. Db App Db 3306 (My. SQL) Allow. My. On. Premises 10. 0. 1. 0/24, 192. 168. 2. 1/25 13. 68. 1. 64/28, 137. 116. 1. 0/25, … 80, 8080, 443 Deny. All. Out. Bound Any Any

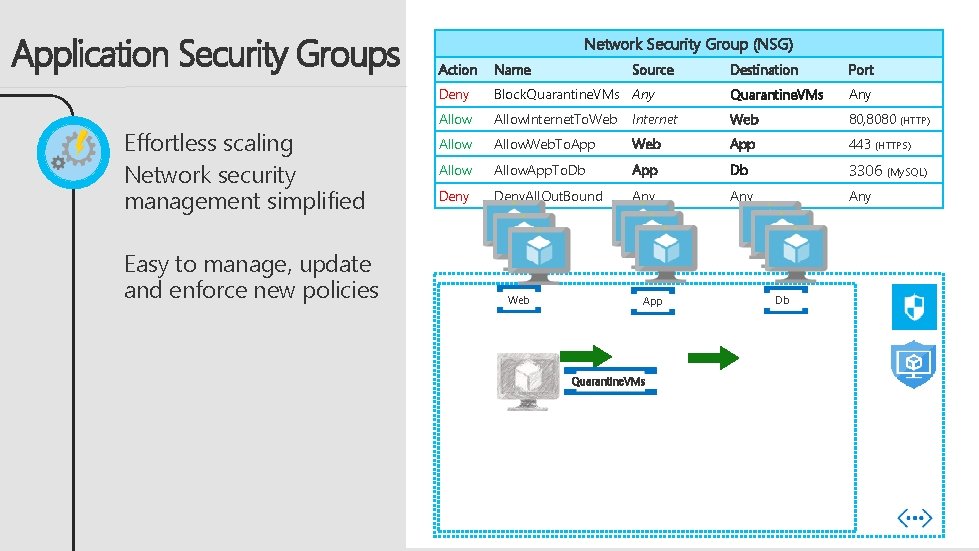
Application Security Groups Effortless scaling Network security management simplified Easy to manage, update and enforce new policies Network Security Group (NSG) Action Name Deny Destination Port Block. Quarantine. VMs Any Allow. Internet. To. Web Internet Web 80, 8080 (HTTP) Allow. Web. To. App Web App 443 (HTTPS) Allow. App. To. Db App Db 3306 (My. SQL) Deny. All. Out. Bound Any Any Web Source App Quarantine. VMs Db




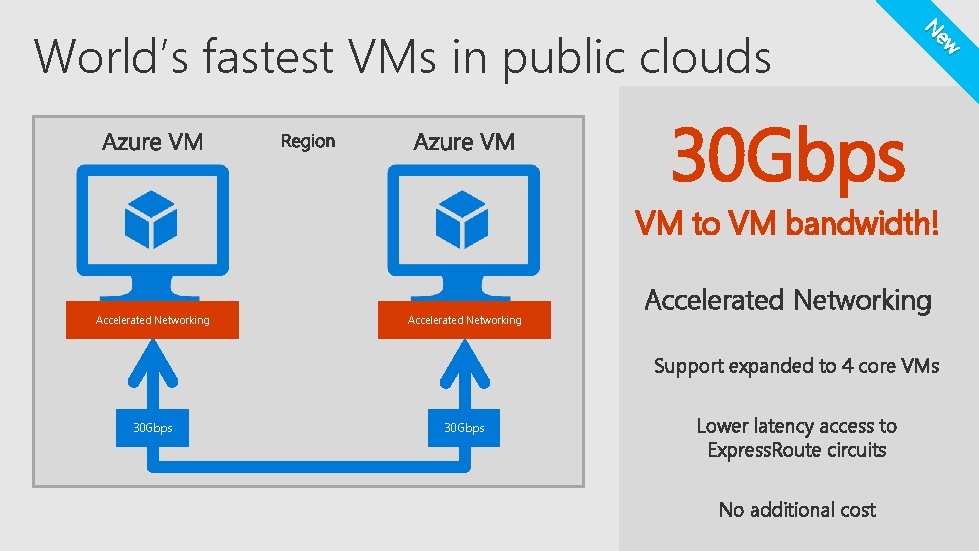
ew N World’s fastest VMs in public clouds 30 Gbps VM to VM bandwidth! Accelerated Networking Support expanded to 4 core VMs 30 Gbps Lower latency access to Express. Route circuits No additional cost

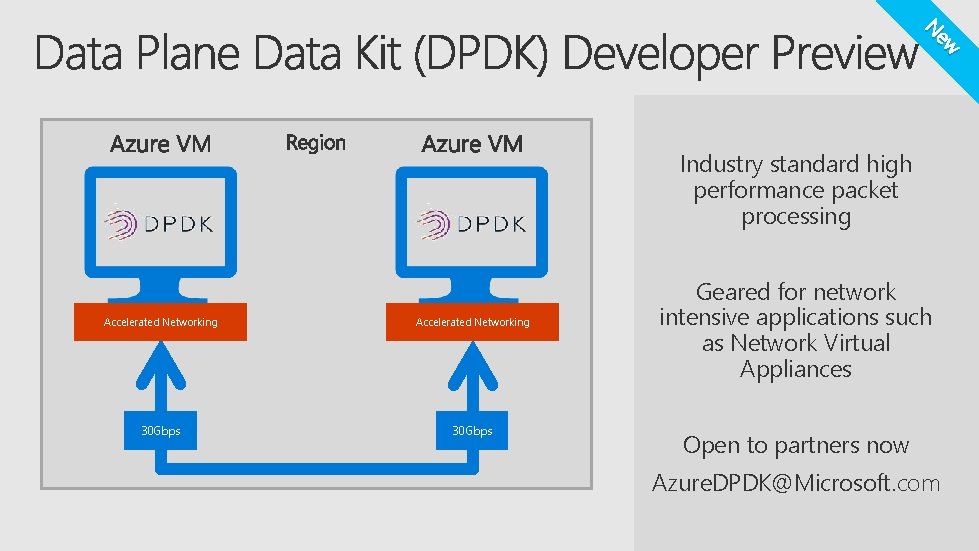
ew N Industry standard high performance packet processing Accelerated Networking 30 Gbps Geared for network intensive applications such as Network Virtual Appliances Open to partners now Azure. DPDK@Microsoft. com

A High Performance Virtual Appliance (v. Thunder) in Azure Saurabh Sureka, Sr. Product Manager Kalpesh Jasapara, Platform Architect Your Secure Application Services Company

A 10 Networks 2016 REVENUE $230 M 5700+ CUSTOMERS IN 72 COUNTRIES + APPLICATION DELIVERY SECURITY + + CLOUD SECURE APPLICATION SERVICES FOUNDED IN 2004 NYSE (ATEN)

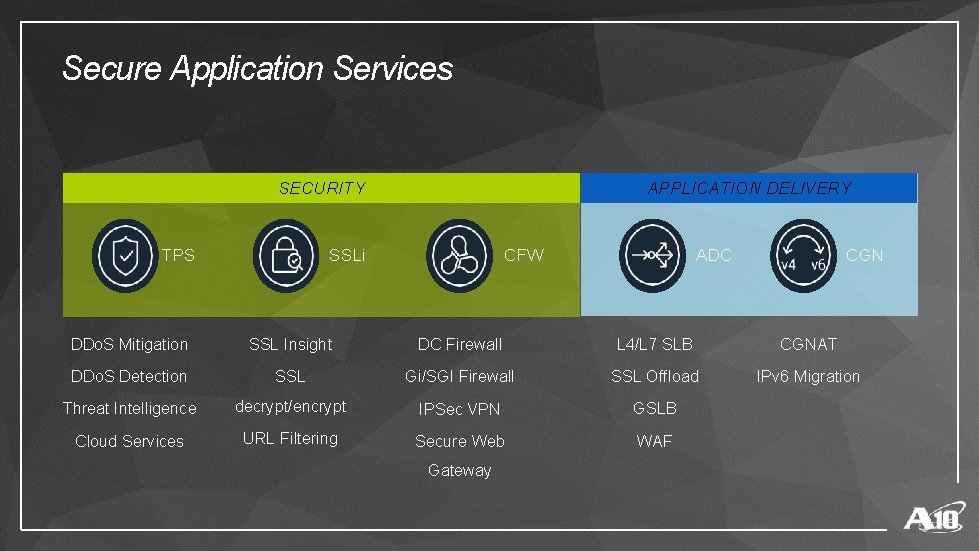
Secure Application Services APPLICATION DELIVERY SECURITY TPS SSLi ADC CFW CGN DDo. S Mitigation SSL Insight DC Firewall L 4/L 7 SLB CGNAT DDo. S Detection SSL Gi/SGI Firewall SSL Offload IPv 6 Migration Threat Intelligence decrypt/encrypt IPSec VPN GSLB Cloud Services URL Filtering Secure Web WAF Gateway

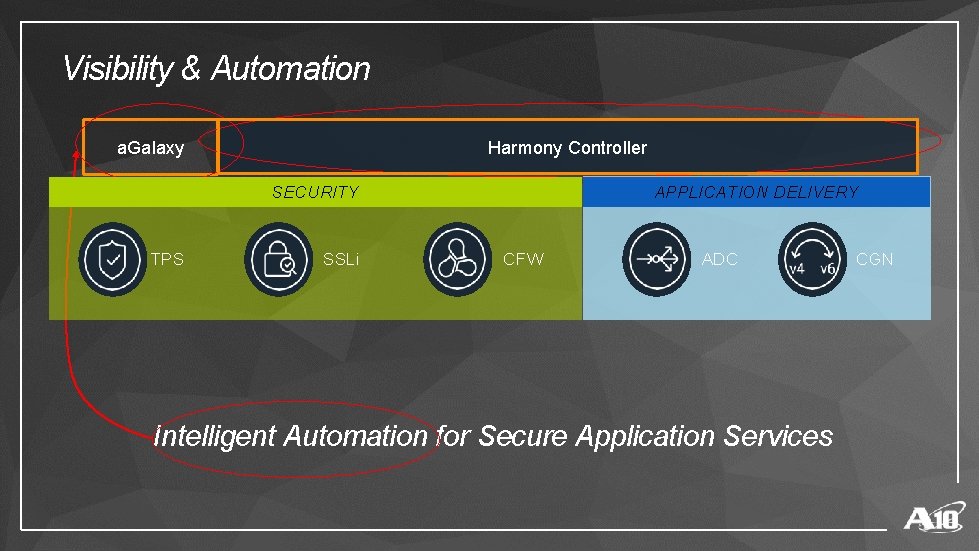
Visibility & Automation Harmony Controller a. Galaxy APPLICATION DELIVERY SECURITY TPS SSLi CFW ADC Intelligent Automation for Secure Application Services CGN

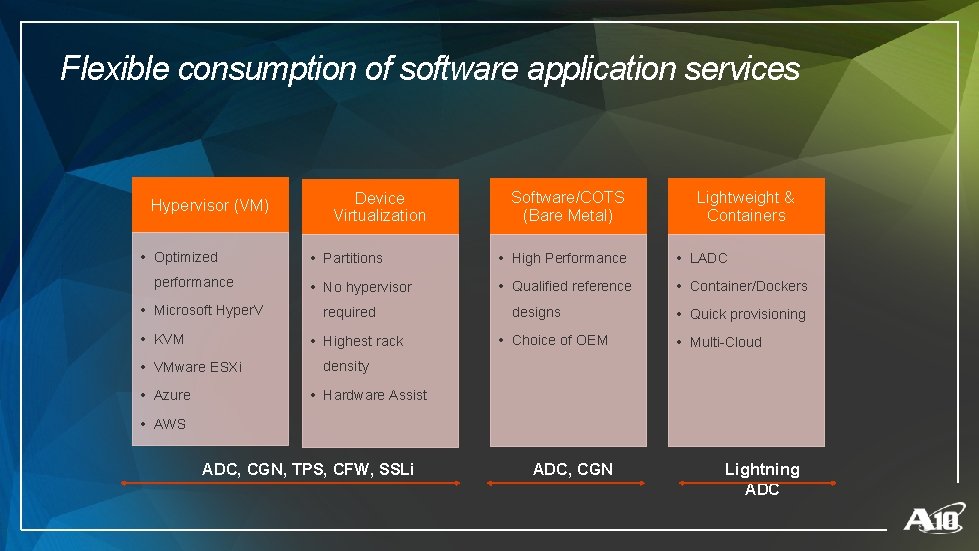
Flexible consumption of software application services Hypervisor (VM) • Optimized performance • Microsoft Hyper. V • KVM Software/COTS (Bare Metal) Lightweight & Containers • Partitions • High Performance • LADC • No hypervisor • Qualified reference • Container/Dockers required • Highest rack • VMware ESXi • Azure Device Virtualization designs • Choice of OEM • Quick provisioning • Multi-Cloud density • Hardware Assist • AWS ADC, CGN, TPS, CFW, SSLi ADC, CGN Lightning ADC

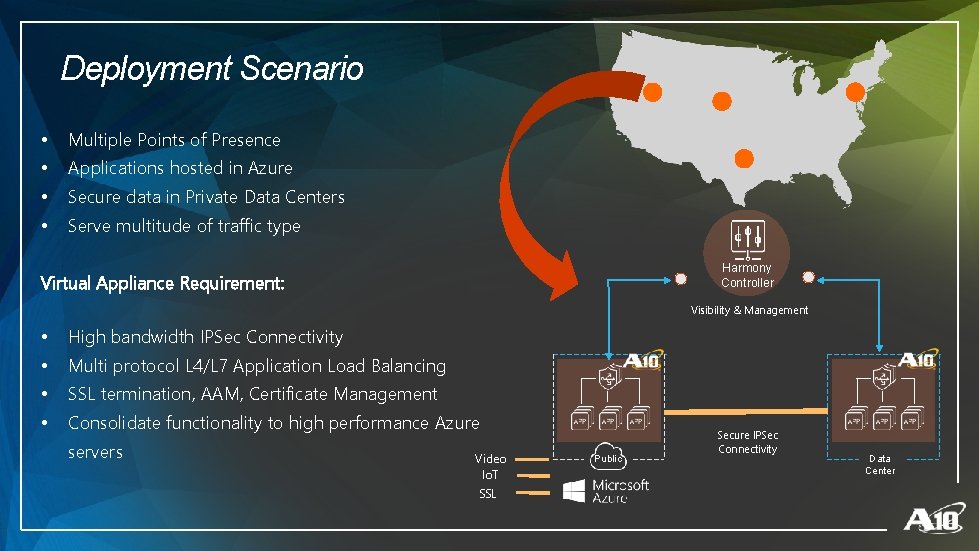
Deployment Scenario • Multiple Points of Presence • Applications hosted in Azure • Secure data in Private Data Centers • Serve multitude of traffic type Harmony Controller Virtual Appliance Requirement: Visibility & Management • High bandwidth IPSec Connectivity • Multi protocol L 4/L 7 Application Load Balancing • SSL termination, AAM, Certificate Management • Consolidate functionality to high performance Azure servers Video Io. T SSL Public Secure IPSec Connectivity Data Center

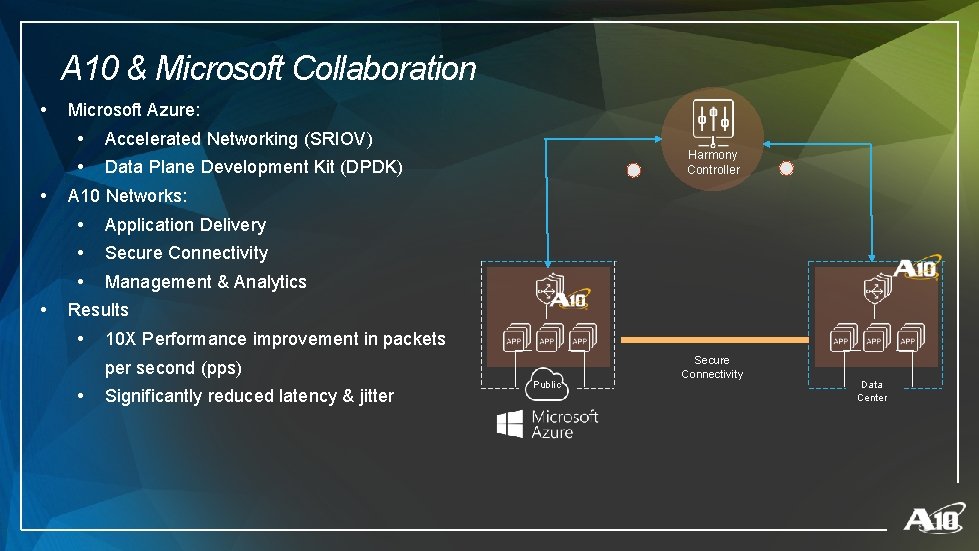
A 10 & Microsoft Collaboration • • • Microsoft Azure: • Accelerated Networking (SRIOV) • Data Plane Development Kit (DPDK) Harmony Controller A 10 Networks: • Application Delivery • Secure Connectivity • Management & Analytics Results • 10 X Performance improvement in packets per second (pps) • Significantly reduced latency & jitter Public Secure Connectivity Data Center

30 G Throughput A 10 v. Thunder Appliance in Azure Accel Net

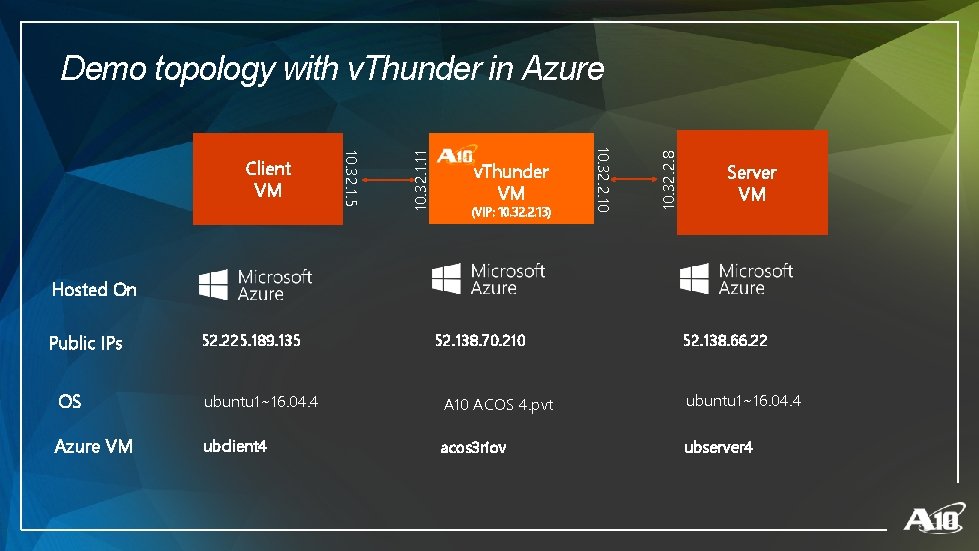
(VIP: 10. 32. 2. 13) 10. 32. 2. 8 v. Thunder VM 10. 32. 2. 10 10. 32. 1. 5 Client VM 10. 32. 1. 11 Demo topology with v. Thunder in Azure Server VM Hosted On Public IPs 52. 225. 189. 135 52. 138. 70. 210 52. 138. 66. 22 OS ubuntu 1~16. 04. 4 A 10 ACOS 4. pvt ubuntu 1~16. 04. 4 Azure VM ubclient 4 acos 3 riov ubserver 4


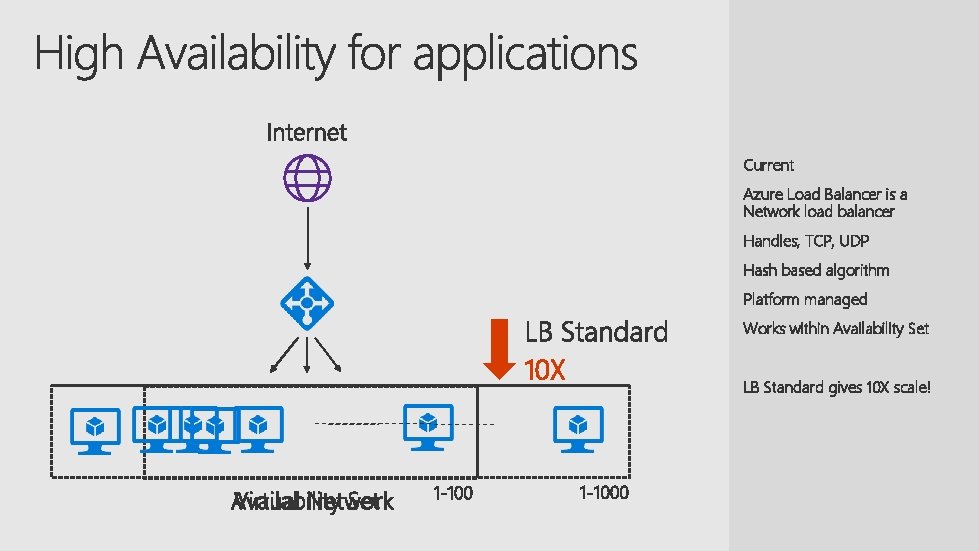
Current Azure Load Balancer is a Network load balancer Handles, TCP, UDP Hash based algorithm Platform managed Works within Availability Set 10 X LB Standard gives 10 X scale!

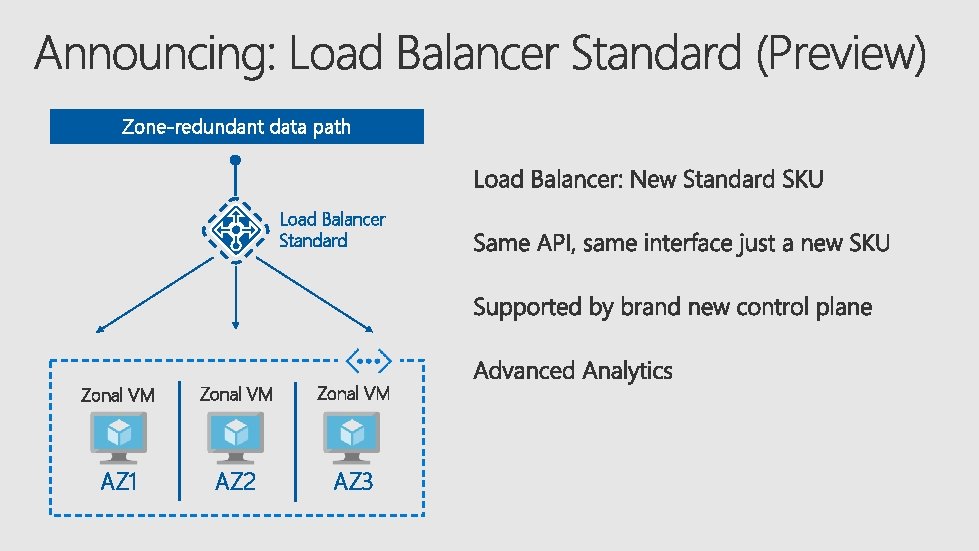
Zone-redundant data path Load Balancer Standard Zonal VM AZ 1 AZ 2 AZ 3

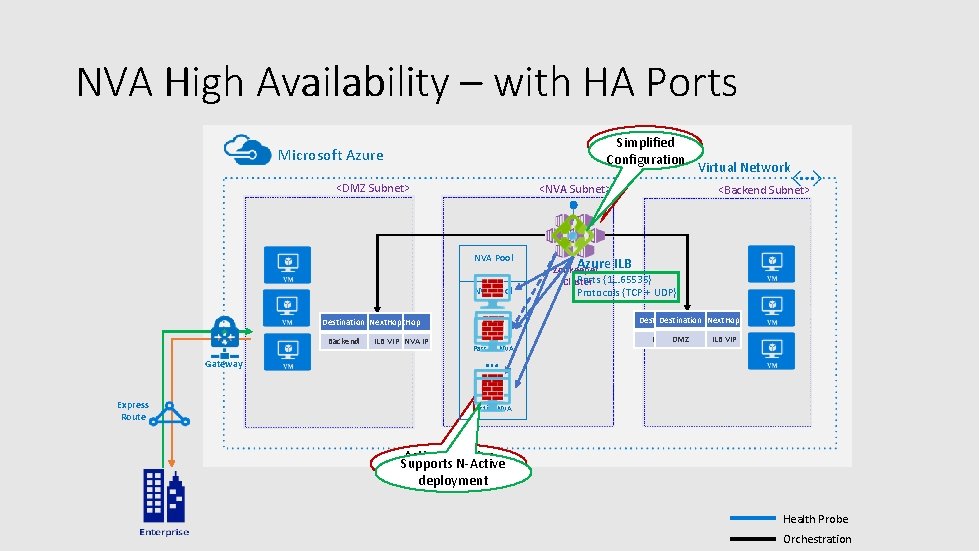
NVA High Availability – with HA Ports Complex Simplified Configuration Microsoft Azure <DMZ Subnet> <NVA Subnet> NVA Pool Gateway Express Route <Backend Subnet> Azure ILB Zookeeper Ports {1… 65535} Cluster Protocols {TCP + UDP} Destination. Next. Hop Destination. Next. Hop Backend ILB Active VIP NVA IP Virtual Network Passive NVA VIP DMZActive. ILB NVA IP … Active NVA Active / Passive Supports N-Active Only deployment Health Probe Orchestration

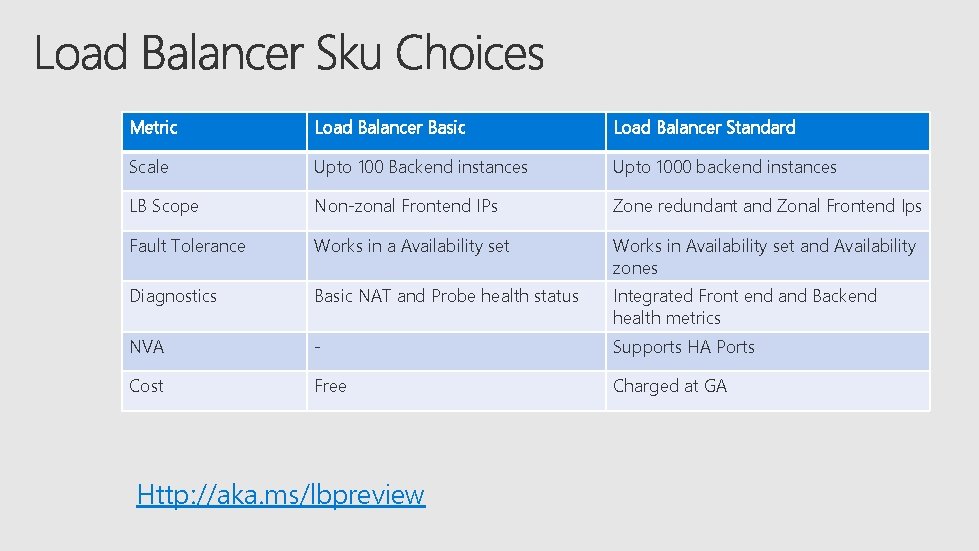
Metric Load Balancer Basic Load Balancer Standard Scale Upto 100 Backend instances Upto 1000 backend instances LB Scope Non-zonal Frontend IPs Zone redundant and Zonal Frontend Ips Fault Tolerance Works in a Availability set Works in Availability set and Availability zones Diagnostics Basic NAT and Probe health status Integrated Front end and Backend health metrics NVA - Supports HA Ports Cost Free Charged at GA Http: //aka. ms/lbpreview


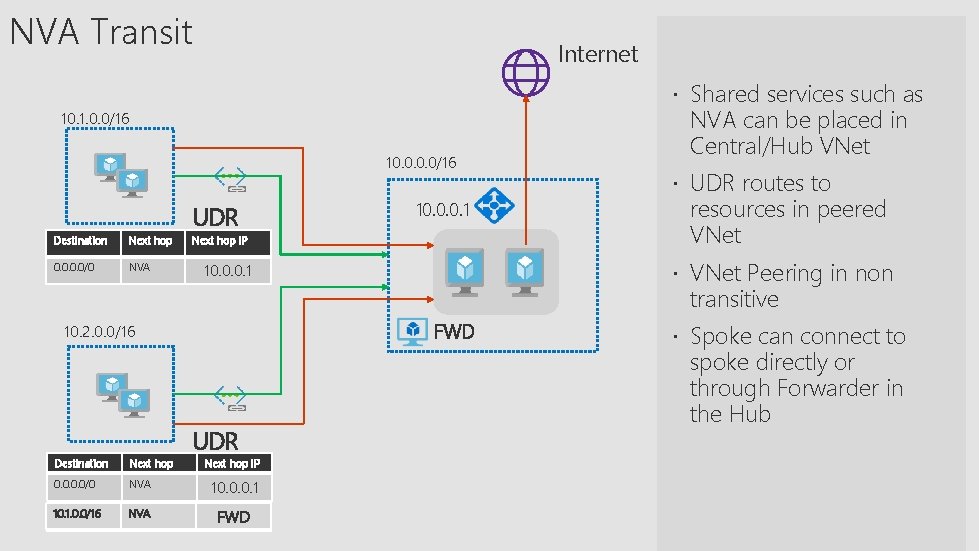
NVA Transit Internet Shared services such as 10. 1. 0. 0/16 10. 0/16 UDR Destination Next hop 0. 0/0 NVA 10. 0. 0. 1 Next hop IP NVA can be placed in Central/Hub VNet UDR routes to resources in peered VNet Peering in non 10. 0. 0. 1 transitive FWD 10. 2. 0. 0/16 UDR Destination Next hop IP 0. 0/0 NVA 10. 0. 0. 1 10. 1. 0. 0/16 NVA FWD Spoke can connect to spoke directly or through Forwarder in the Hub

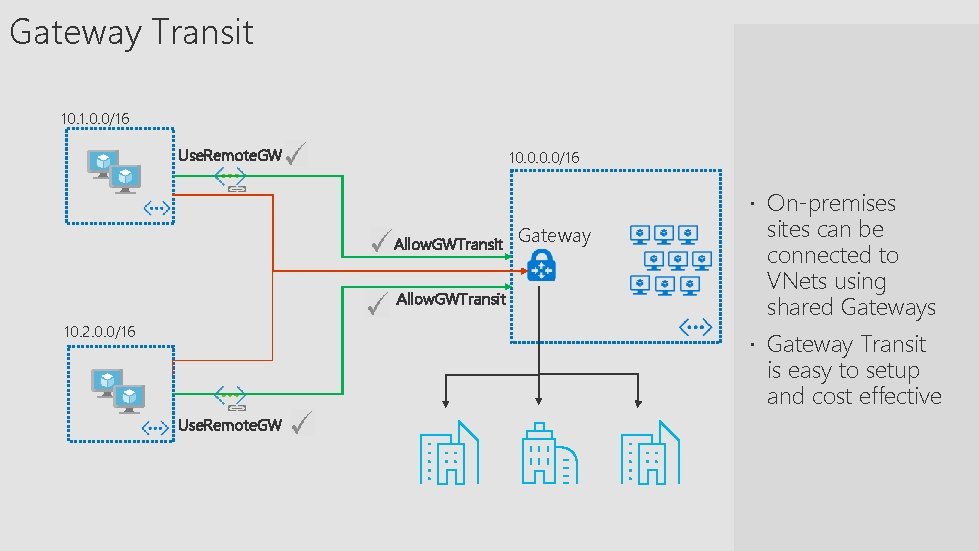
Gateway Transit 10. 1. 0. 0/16 Use. Remote. GW 10. 0/16 On-premises Allow. GWTransit 10. 2. 0. 0/16 Gateway sites can be connected to VNets using shared Gateways Gateway Transit is easy to setup and cost effective Use. Remote. GW

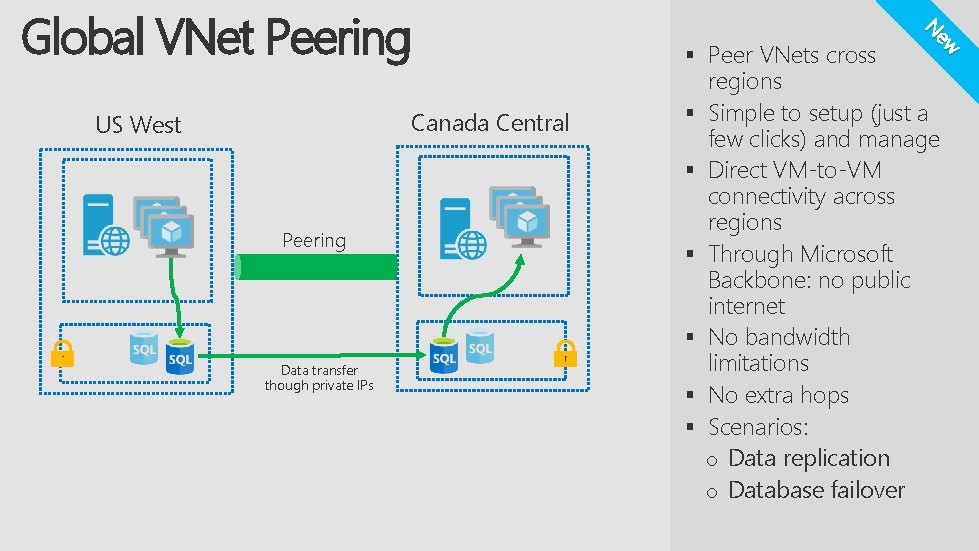
§ § Peering § § Data transfer though private IPs § § ew Canada Central US West § Peer VNets cross N Global VNet Peering regions Simple to setup (just a few clicks) and manage Direct VM-to-VM connectivity across regions Through Microsoft Backbone: no public internet No bandwidth limitations No extra hops Scenarios: o Data replication o Database failover



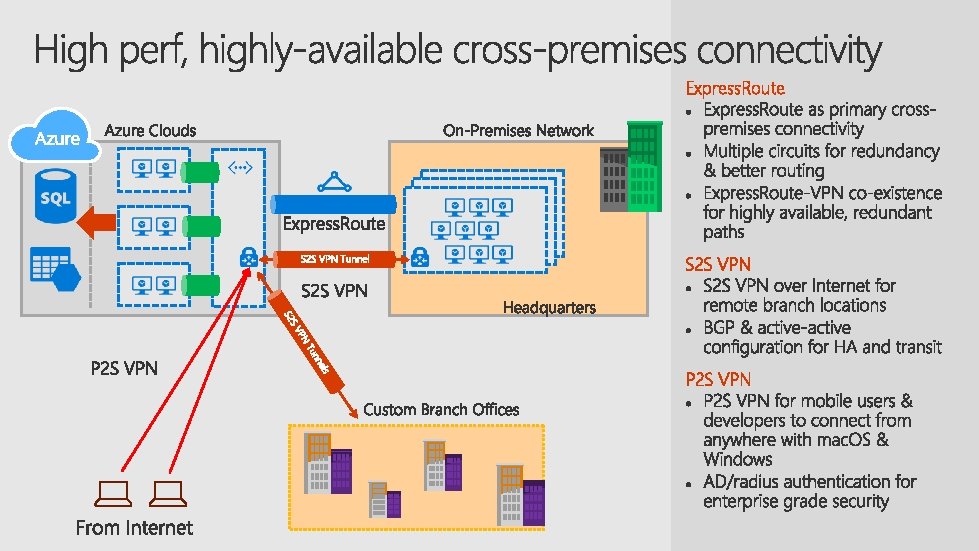
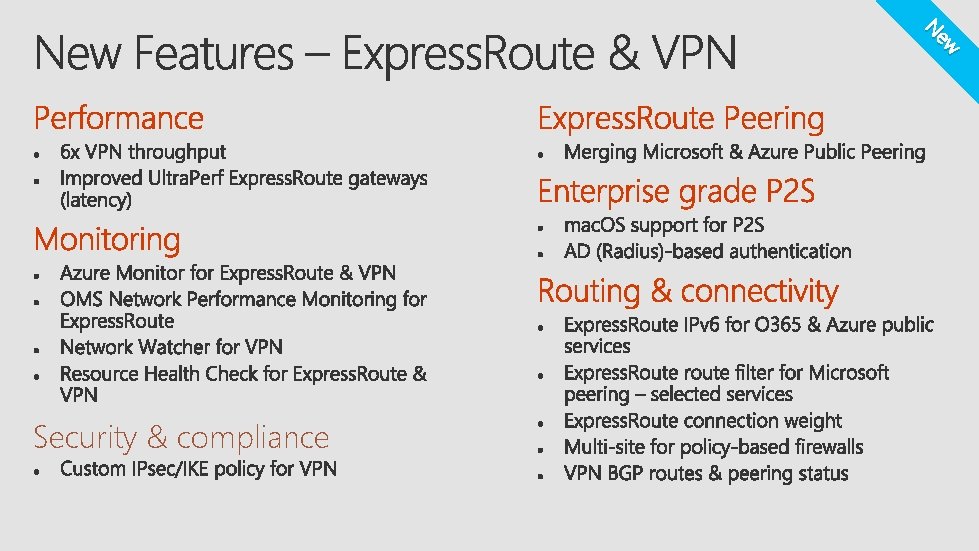
Express. Route S 2 S VPN P 2 S VPN

ew N Security & compliance

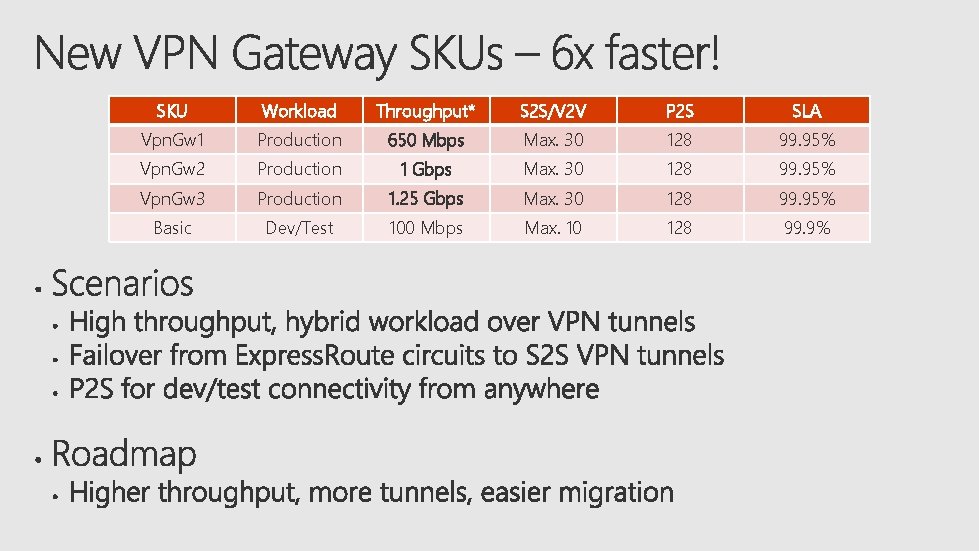
SKU Workload Throughput* S 2 S/V 2 V P 2 S SLA Vpn. Gw 1 Production 650 Mbps Max. 30 128 99. 95% Vpn. Gw 2 Production 1 Gbps Max. 30 128 99. 95% Vpn. Gw 3 Production 1. 25 Gbps Max. 30 128 99. 95% Basic Dev/Test 100 Mbps Max. 10 128 99. 9%

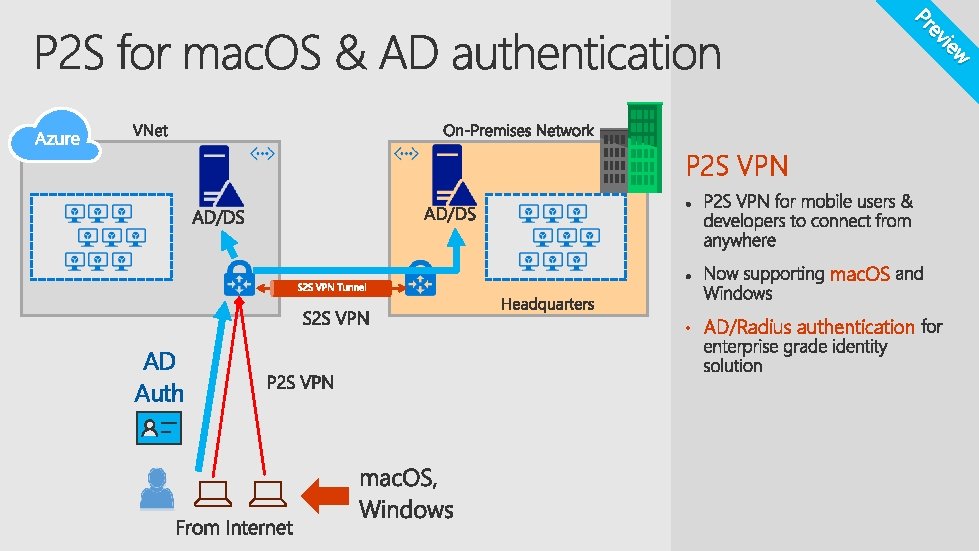
w vie e Pr P 2 S VPN mac. OS • AD/Radius authentication AD Auth

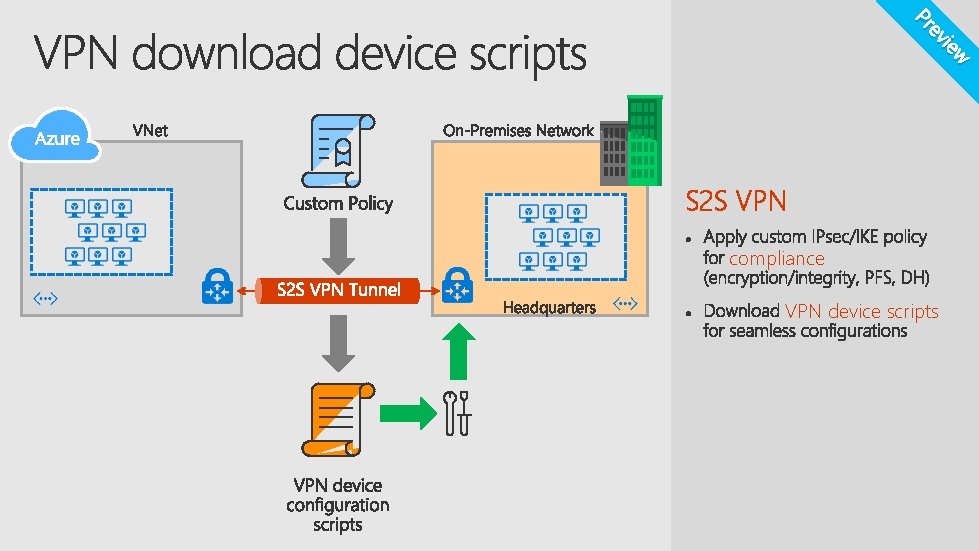
w vie e Pr S 2 S VPN compliance VPN device scripts

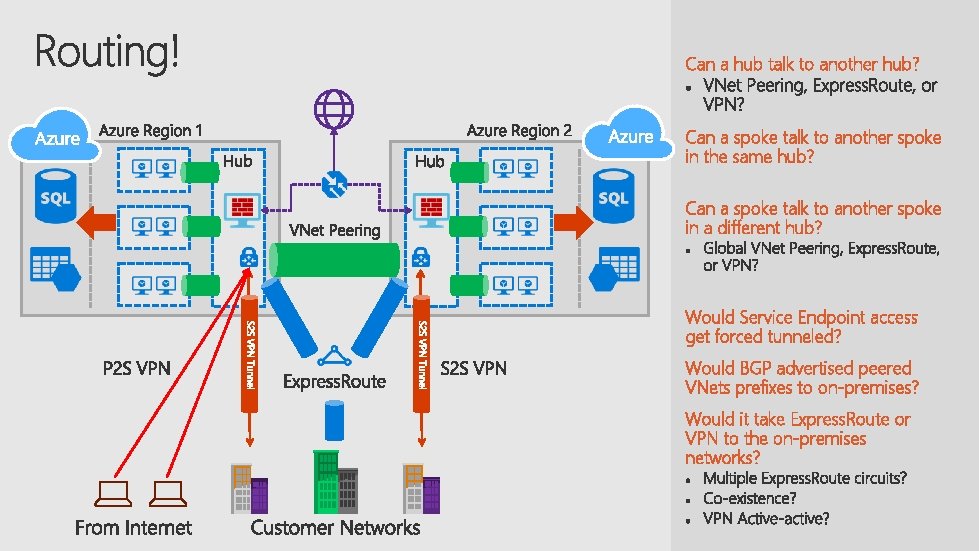
Can a hub talk to another hub? Can a spoke talk to another spoke in the same hub? Can a spoke talk to another spoke in a different hub? Would Service Endpoint access get forced tunneled? Would BGP advertised peered VNets prefixes to on-premises? Would it take Express. Route or VPN to the on-premises networks?

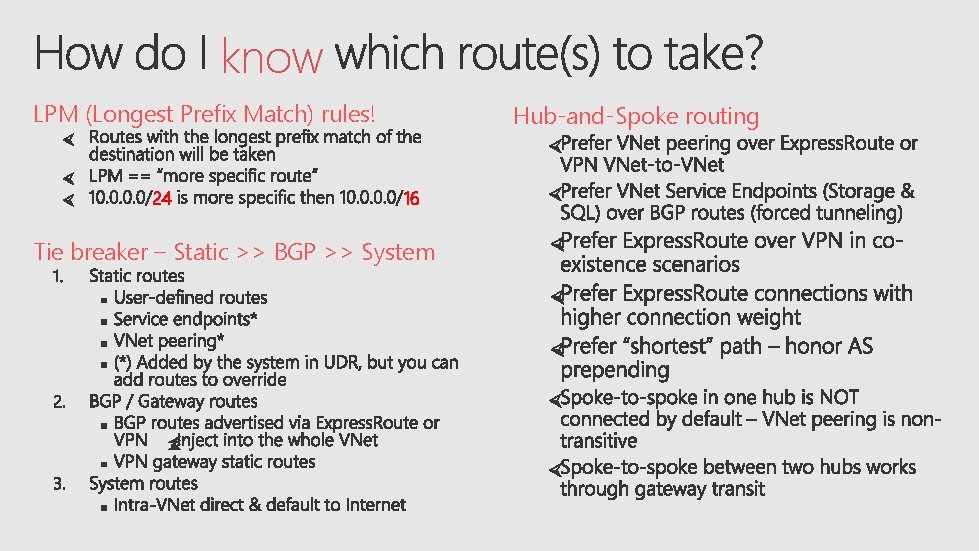
know LPM (Longest Prefix Match) rules! 24 Hub-and-Spoke routing 16 Tie breaker – Static >> BGP >> System

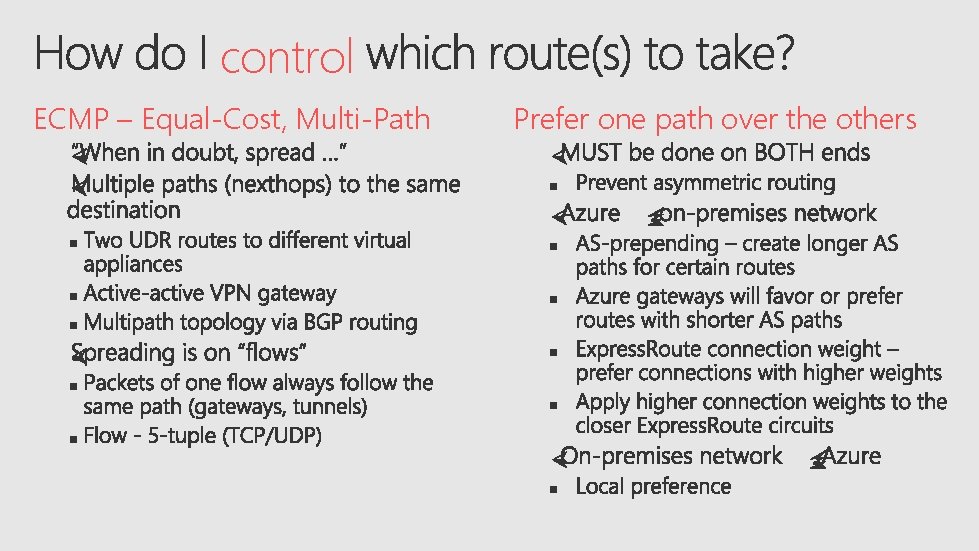
control ECMP – Equal-Cost, Multi-Path Prefer one path over the others

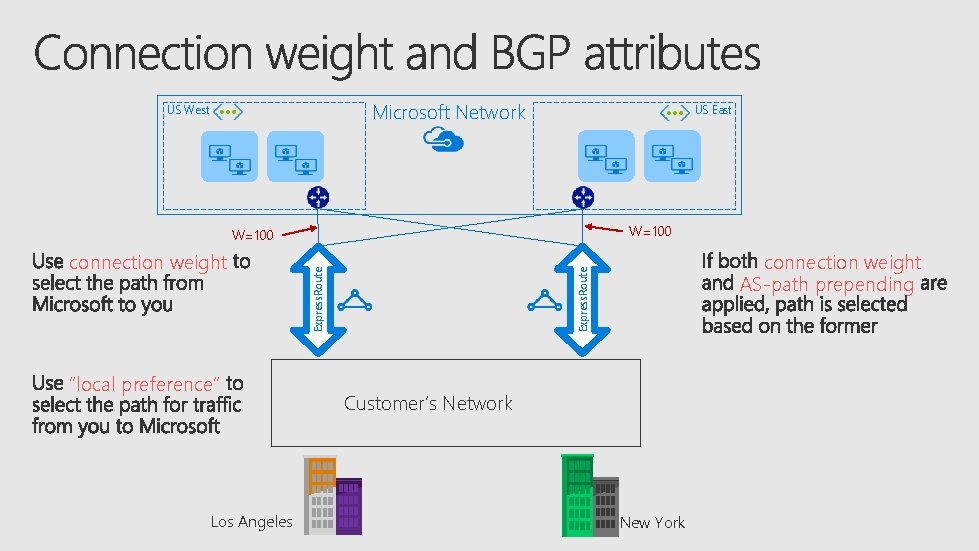
Microsoft Network US West US East W=100 “local preference” Los Angeles Express. Route connection weight AS-path prepending Express. Route W=100 Customer’s Network New York



Josh Hetland Technical Architect | Cloud Engineering Member of Walgreens Boots Alliance

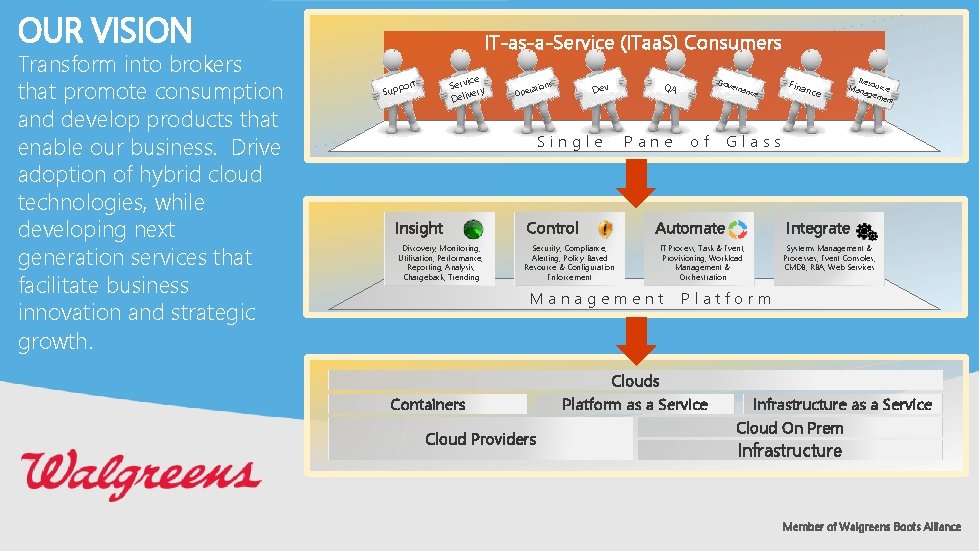
OUR VISION Transform into brokers that promote consumption and develop products that enable our business. Drive adoption of hybrid cloud technologies, while developing next generation services that facilitate business innovation and strategic growth. IT-as-a-Service (ITaa. S) Consumers ice Serv ry e Deliv ort Supp ons Dev rati Ope Single Insight Discovery, Monitoring, Utilisation, Performance, Reporting, Analysis, Chargeback, Trending Control Security, Compliance, Alerting, Policy-Based Resource & Configuration Enforcement Pane Cloud Providers erna of nce Fina nce Res Man ource agem ent Glass Automate Integrate IT Process, Task & Event, Provisioning, Workload Management & Orchestration Management Containers Gov QA Systems Management & Processes, Event Consoles, CMDB, RBA, Web Services Platform Clouds Platform as a Service Infrastructure as a Service Cloud On Prem Infrastructure Member of Walgreens Boots Alliance

Horizontal Scalability – The system can scale horizontally by adding/removing servers as business demands dictate. Even across regions to deliver more fault tolerance. Virtual Compute Resources - Application workload should be suitable for virtual compute resources. Variable Capacity Requirements – Applications with predictable variable resource requirements (ie. predictable seasonal peaks and quiet periods) can take advantage of elastic consumption services offered by public cloud providers. Limited-Term Environments – Environments that need to be provisioned, used for a period of time, and can then be removed from use. This allows expenditures to match demand avoid the cost of dedicated infrastructure. Secure and Compliant – Cloud offering must provide the ability to meet any required governance or compliance needs.

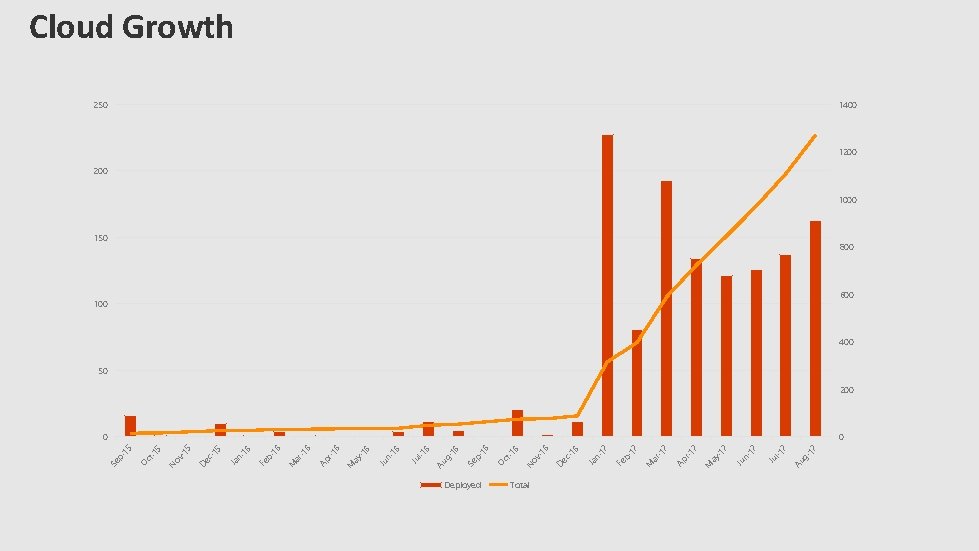
Deployed Total 7 17 g- Au l-1 Ju 17 n- Ju 7 M ay -1 17 r- Ap 7 -1 ar M 17 b- Fe 17 n- Ja 6 c 1 De 6 -1 ov N 16 ct - O 16 p- Se 16 g- Au 6 -1 Ju l 6 -1 Ju n 6 -1 ay M 16 r- Ap 6 M ar -1 16 b- Fe 16 n- Ja 5 5 c 1 De -1 ov N 15 ct - O 15 p- Se Cloud Growth 250 1400 1200 1000 150 800 100 600 400 50 200 0 0

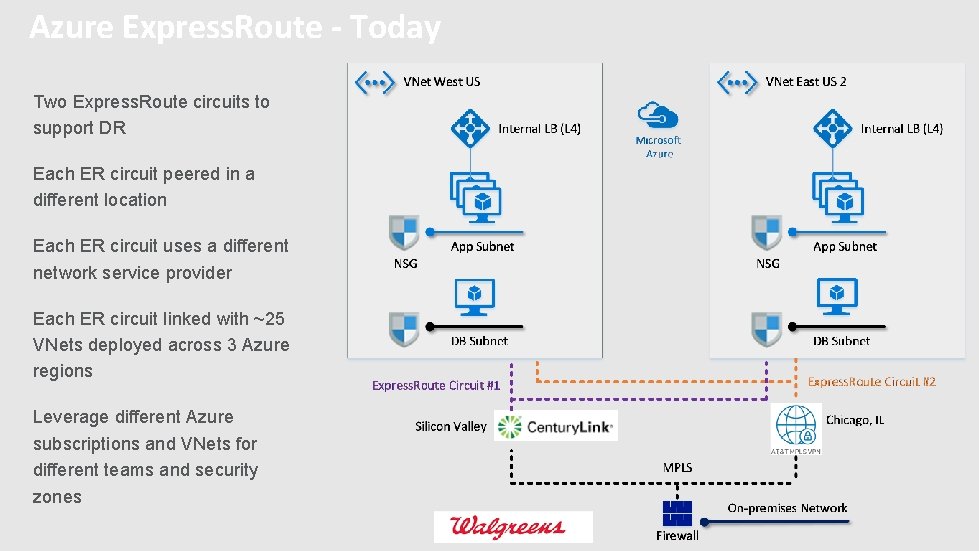
Azure Express. Route - Today Two Express. Route circuits to support DR Each ER circuit peered in a different location Each ER circuit uses a different network service provider Each ER circuit linked with ~25 VNets deployed across 3 Azure regions Leverage different Azure subscriptions and VNets for different teams and security zones

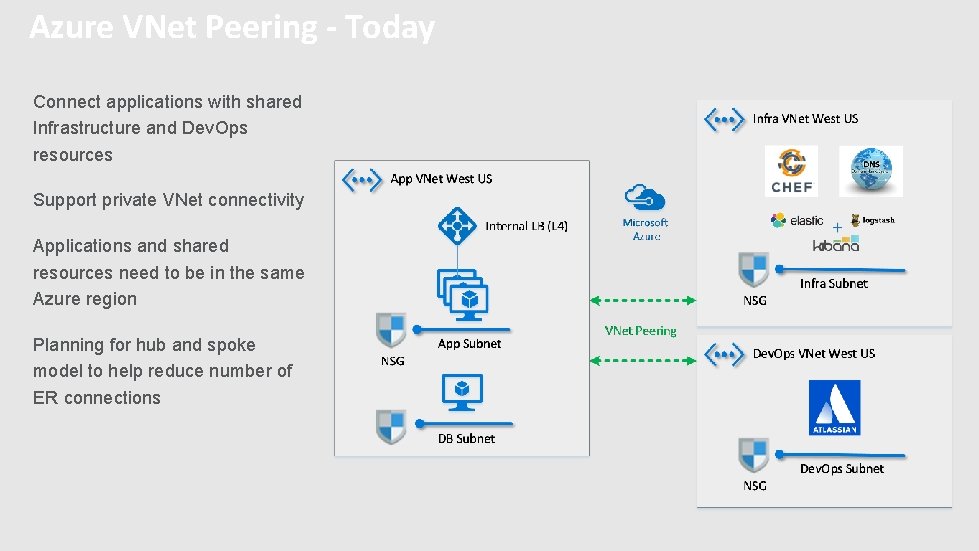
Azure VNet Peering - Today Connect applications with shared Infrastructure and Dev. Ops resources Support private VNet connectivity Applications and shared resources need to be in the same Azure region Planning for hub and spoke model to help reduce number of ER connections

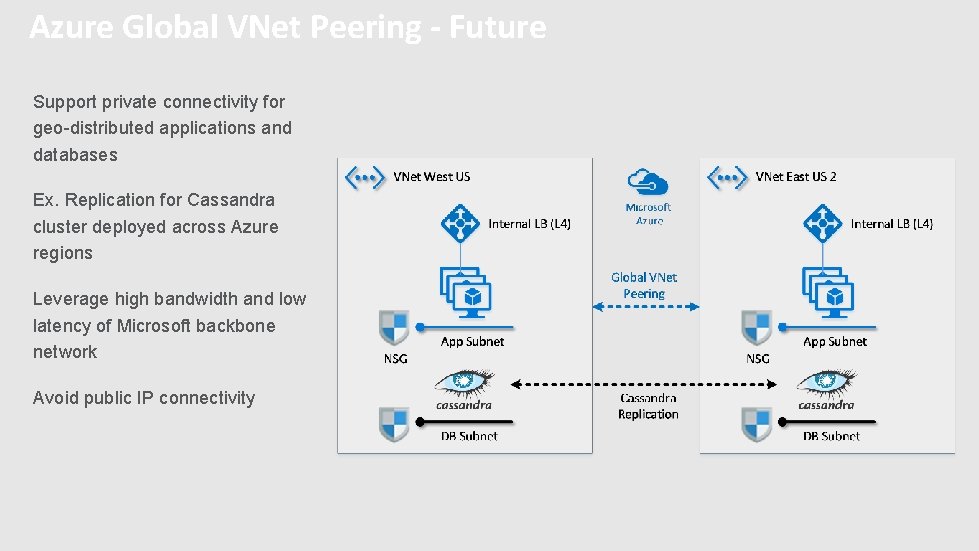
Azure Global VNet Peering - Future Support private connectivity for geo-distributed applications and databases Ex. Replication for Cassandra cluster deployed across Azure regions Leverage high bandwidth and low latency of Microsoft backbone network Avoid public IP connectivity


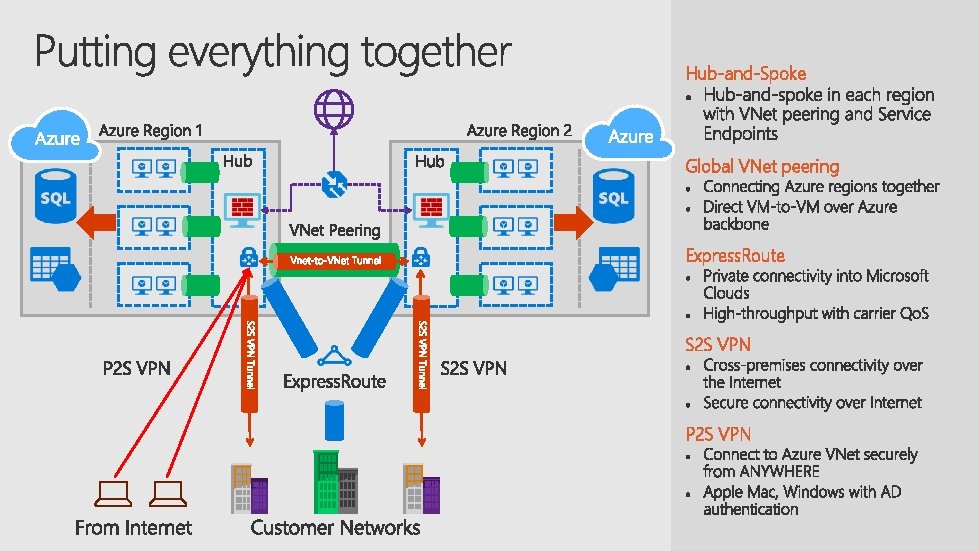
Hub-and-Spoke Global VNet peering Express. Route S 2 S VPN P 2 S VPN

VPN get BGP routes, download device scripts world’s fastest

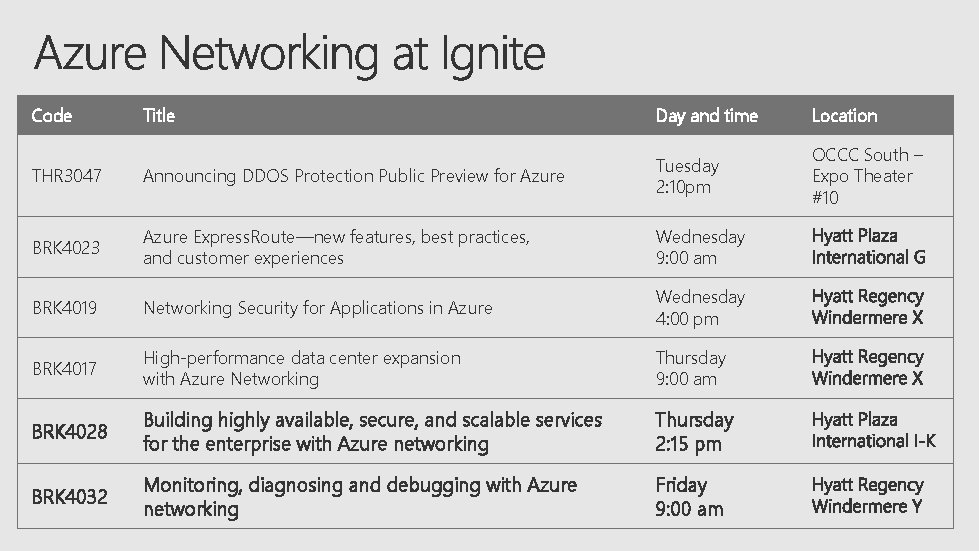
Code Title Day and time Location THR 3047 Announcing DDOS Protection Public Preview for Azure Tuesday 2: 10 pm OCCC South – Expo Theater #10 BRK 4023 Azure Express. Route—new features, best practices, and customer experiences Wednesday 9: 00 am BRK 4019 Networking Security for Applications in Azure Wednesday 4: 00 pm BRK 4017 High-performance data center expansion with Azure Networking Thursday 9: 00 am BRK 4028 Building highly available, secure, and scalable services for the enterprise with Azure networking Thursday 2: 15 pm BRK 4032 Monitoring, diagnosing and debugging with Azure networking Friday 9: 00 am

https: //myignite. microsoft. com/evaluations https: //aka. ms/ignite. mobileapp
