Old Dominion University College of Science Department of









- Slides: 24

Old Dominion University College of Science Department of Computer Science System. Security. Permission s namespace Presented By: Ahmed ALSUM Ph. D Student CS 895: . Net Security

Outline Introduction Types of Permissions Basic Permission classes Classes under Permission namespace Classes out Permission namespace

What’s a Permission �Permissions limit what an assembly can do ◦ –run if code not verifiable? ◦ –access file system? ◦ –access the network? ◦ –access certain environment variables? ◦ –call native code (COM objects, DLLs)? ◦ –access files or printers without asking user?

Security Code Access Security �Code may require permissions to run �Security policy determines what code is allowed to run ◦ By machine �Where did this code come from? �Who authored it? ◦ By user �If no permission then a Security. Exception is thrown

Security Code Access Security �Can specify the permissions needed by code ◦ Declarative, with attributes ◦ Imperative �Create a permission object, then call Demand() �By default, the CLR will ensure that all code in call chain has the necessary permissions

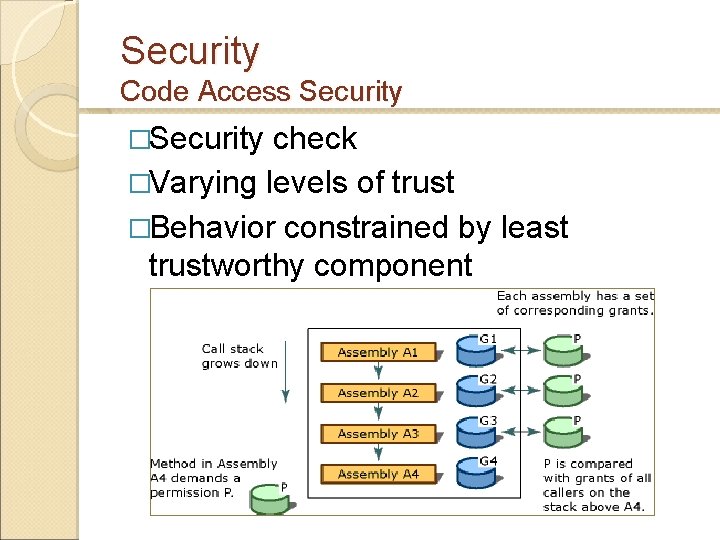
Security Code Access Security �Security check �Varying levels of trust �Behavior constrained by least trustworthy component Call Chain Assembly A 1 G 1 P Assembly A 2 G 2 P Assembly A 3 G 3 P Assembly A 4 G 4

Security Code Access Security �Can override security checks ◦ Assert() lets you and the code you call perform actions that you have permission to do, but your callers may not. ◦ Deny() lets you prevent downstream code from performing certain actions ◦ Permit. Only() is like Deny(), but you specify the only permissions the downstream code will have.

Security Permissions �Code access permissions ◦ Protect resources and operations ◦ Ex. Dns. Permission, Environment. Permission, Web. Permission �Identity permissions ◦ Characteristics of an assembly‘s identity ◦ Ex. URLIdentity. Permission, Zone. Identity. Permission �Role-based permissions ◦ Discover a user‘s role or identity ◦ Ex. Principal. Permission �Custom permissions ◦ Design and implement your own classes

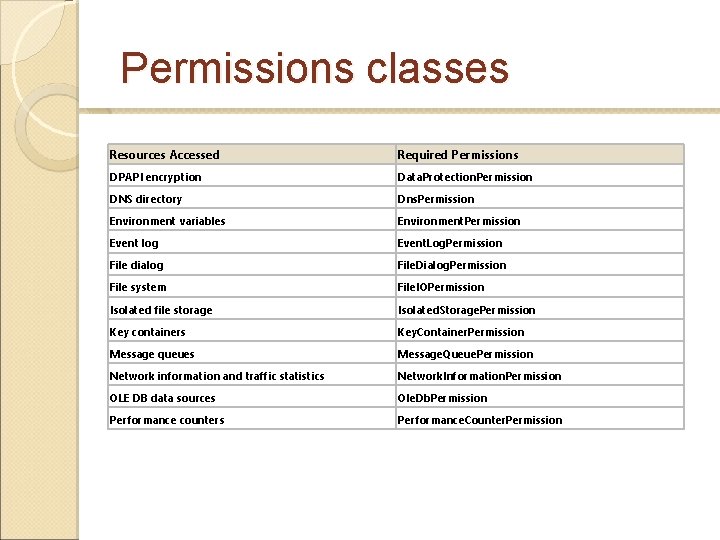
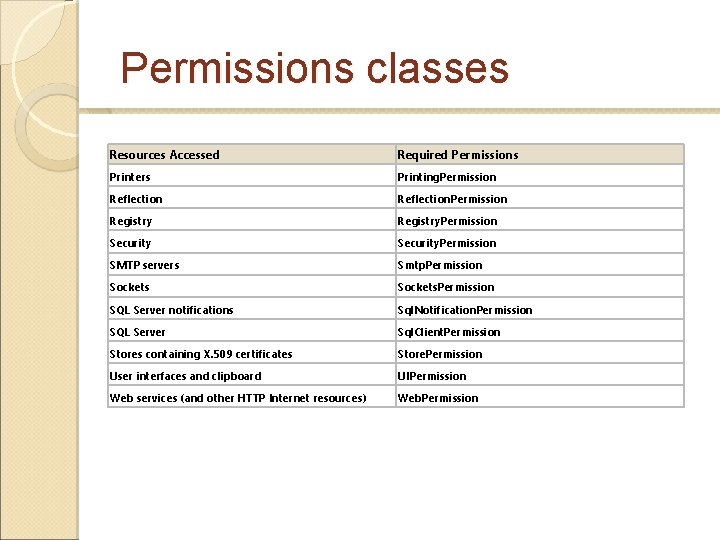
Permissions classes Resources Accessed Required Permissions DPAPI encryption Data. Protection. Permission DNS directory Dns. Permission Environment variables Environment. Permission Event log Event. Log. Permission File dialog File. Dialog. Permission File system File. IOPermission Isolated file storage Isolated. Storage. Permission Key containers Key. Container. Permission Message queues Message. Queue. Permission Network information and traffic statistics Network. Information. Permission OLE DB data sources Ole. Db. Permission Performance counters Performance. Counter. Permission

Permissions classes Resources Accessed Required Permissions Printers Printing. Permission Reflection. Permission Registry. Permission Security. Permission SMTP servers Smtp. Permission Sockets. Permission SQL Server notifications Sql. Notification. Permission SQL Server Sql. Client. Permission Stores containing X. 509 certificates Store. Permission User interfaces and clipboard UIPermission Web services (and other HTTP Internet resources) Web. Permission

Namespace: System. Security Code. Access. Permission �Defines the underlying structure of all code access permissions �When you inherit from Code. Access. Permission, you must also implement the IUnrestricted. Permission interface. �The following Code. Access. Permission members must be overridden: Copy, Intersect, Is. Subset. Of, To. Xml, From. Xml, and Union. �You must also define a constructor that takes a Permission. State as its only parameter. �You must apply the Serializable. Attribute attribute to a class that inherits from Code. Access. Permission. � Custom Permission Example

Namespace: System. Security. Permissions Code. Access. Security. Attribute �The security information declared by a security attribute is stored in the metadata of the attribute target and is accessed by the system at run time. Security attributes are used only for declarative security. �All permission attributes derived from this class must have only a single constructor that takes a Security. Action as its only parameter. � Custom Attribute Example

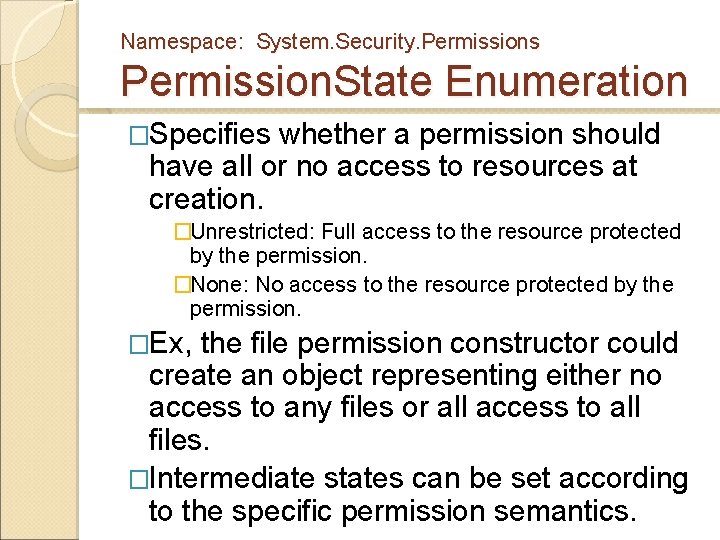
Namespace: System. Security. Permissions Permission. State Enumeration �Specifies whether a permission should have all or no access to resources at creation. �Unrestricted: Full access to the resource protected by the permission. �None: No access to the resource protected by the permission. �Ex, the file permission constructor could create an object representing either no access to any files or all access to all files. �Intermediate states can be set according to the specific permission semantics.

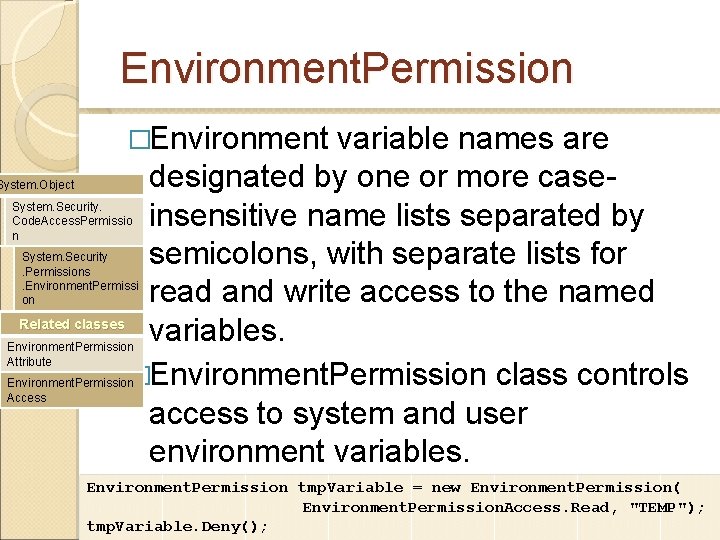
Environment. Permission �Environment variable names are designated by one or more caseinsensitive name lists separated by semicolons, with separate lists for read and write access to the named Related classes variables. �Environment. Permission class controls access to system and user environment variables. System. Object System. Security. Code. Access. Permissio n System. Security. Permissions. Environment. Permissi on Environment. Permission Attribute Environment. Permission Access Environment. Permission tmp. Variable = new Environment. Permission( Environment. Permission. Access. Read, "TEMP"); tmp. Variable. Deny();

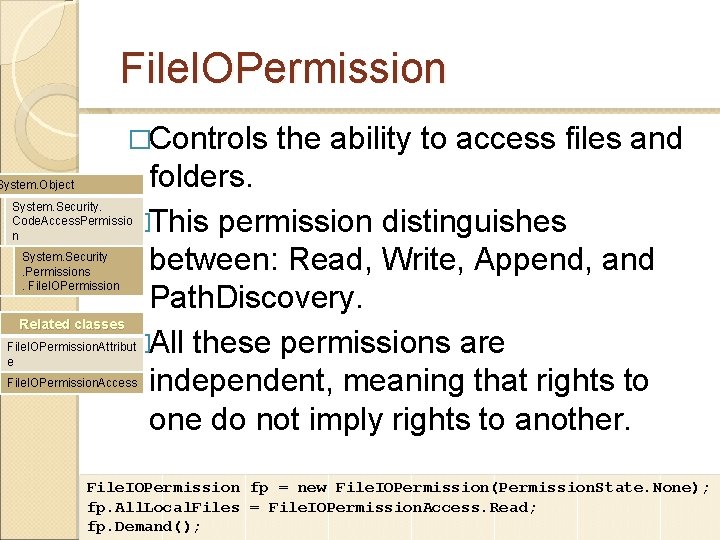
File. IOPermission �Controls the ability to access files and folders. �This permission distinguishes between: Read, Write, Append, and Path. Discovery. Related classes �All these permissions are independent, meaning that rights to one do not imply rights to another. System. Object System. Security. Code. Access. Permissio n System. Security. Permissions. File. IOPermission. Attribut e File. IOPermission. Access File. IOPermission fp = new File. IOPermission(Permission. State. None); fp. All. Local. Files = File. IOPermission. Access. Read; fp. Demand();

Web. Browser. Permission �It controls the ability to create the Web. Browser control. �In the Windows Presentation Foundation (WPF), the Web browser control enables frames to navigate Related classes HTML. �This permission uses the values of the Web. Browser. Permission enumerations. System. Object System. Security. Code. Access. Permissio n System. Security. Permissions. Web. Browser. Permissio n Web. Browser. Permission Attribute Web. Browser. Permission Level Web. Browser. Permission web. Browser. Permission = new Web. Browser. Permission(Web. Browser. Permission. Level. Unrestricted);

Media. Permission �The System. Object System. Security. Code. Access. Permissio n System. Security. Permissions. Media. Permission Related classes Media. Permission. Attribut e Media. Permission. Audio Media. Permission. Image Media. Permission. Video Media. Permission describes a set of security permissions that controls the ability for audio, image, and video media to work in a partial-trust Windows Presentation Foundation (WPF) application.

Registry. Permission �Registry. Permission System. Object System. Security. Code. Access. Permissio n System. Security. Permissions. Registry. Permission Related classes Registry. Permission. Attri bute Registry. Permission. Acce ss describes protected operations on registry variables. Registry variables should not be stored in memory locations where code without Registry. Permission can access them. If the registry object is passed to an untrusted caller it can be misused. Registry. Permission f = new Registry. Permission( Registry. Permission. Access. Read, "HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\Central. Proces sor\0");

Principal. Permission � By passing identity information (user name and role) to the constructor, Principal. Permission can be System. Object used to demand that the identity of the active System. Security. Permissions principal matches this information. . Principal. Permission � It implements the IPermission interface. This is because Principal. Permission is not a code access permission; that is, it is not granted based on the Related classes Principal. Permission. Attri identity of the executing assembly. Instead, it bute allows code to perform actions (Demand, Union, Intersect, and so on) against the current user identity. App. Domain. Current. Domain. Set. Principal. Policy( Principal. Policy. Windows. Principal); Principal. Permission principal. Perm = new Principal. Permission(null, "Administrators"); principal. Perm. Demand();

Namespace: System. Net Web. Permission �Web. Permission System. Object System. Security. Code. Access. Permissio n System. Net. Web. Permission Related classes Web. Permission. Attribute Network. Access provides a set of methods and properties to control access to Internet resources. You can use a Web. Permission to provide either restricted or unrestricted access to your resource, based on the Permission. State that is set when the Web. Permission is created. Regex my. Regex = new Regex(@"http: //www. microsoft. com/. *"); Web. Permission wp = new Web. Permission(Network. Access. Connect, my. Regex); wp. Add. Permission(Network. Access. Accept, "http: //www. odu. edu/"); wp. Demand();

Namespace: System. Data. Ole. Db. Permission �Enables System. Object System. Security. Code. Access. Permissio n System. Data. Common. DBData. Permission System. Data. Ole. Db. Permission Related classes Ole. Db. Permission. Attribu te the. NET Framework Data Provider for OLE DB to help make sure that a user has a security level sufficient to access an OLE DB data source

Namespace: System. Net Dns. Permission �Controls rights to access Domain Name System (DNS) servers on the network. �The default permissions allow all local and Intranet zone applications to Related classes access DNS services, and no DNS permission for Internet zone applications. System. Object System. Security. Code. Access. Permissio n System. Net. Dns. Permission. Attribute Dns. Permission permission = new Dns. Permission(Permission. State. Unrestricted); permission. Demand();

References �Programming . NET Security, O’Reilly by Adam Freeman, Allen Jones �. NET Framework Class Library System. Security. Permissions Namespace URL: http: //msdn. microsoft. com/enus/library/24 ed 02 w 7. aspx �. NET Framework Developer's Guide Key Security Concepts URL: http: //msdn. microsoft. com/enus/library/z 164 t 8 hs(v=VS. 71). aspx

QUESTIONS?