Office 365 and Azure Data Governance ABOUT BEN

Office 365 and Azure Data Governance


ABOUT BEN CURRY Principal Architect • • Summit 7 Systems Lead Architect Ten time Microsoft MVP CISSP, MCT Author of several Share. Point books by Microsoft PRESS Master SCUBA Diver Trainer Ben. Curry@summit 7 systems. com Twitter @curryben • Q&A #O 365 Security

Agenda • Overview of governance features • Is there label equality? • Legacy SPSite-centric controls • DLP • RMS • AIP • ODB

Overview • Office 365 Data Governance is multi-layered • It’s is built by multiple products and features • Understand what your requirements are • Don’t waste $$ on unneeded licensing

Data Security • Office 365 Data Loss Prevention (DLP) provides real-time protection of sensitive content. • Office 365 Labels provide a way to tag document within Office 365 for the purpose of retention, identification, search, and e. Discovery. • Azure Information Protection (AIP) adds additional security to documents in addition to the container they are already secured within. • Azure Intune controls how information is consumed, copied, saved, and forwarded on mobile devices and laptops.
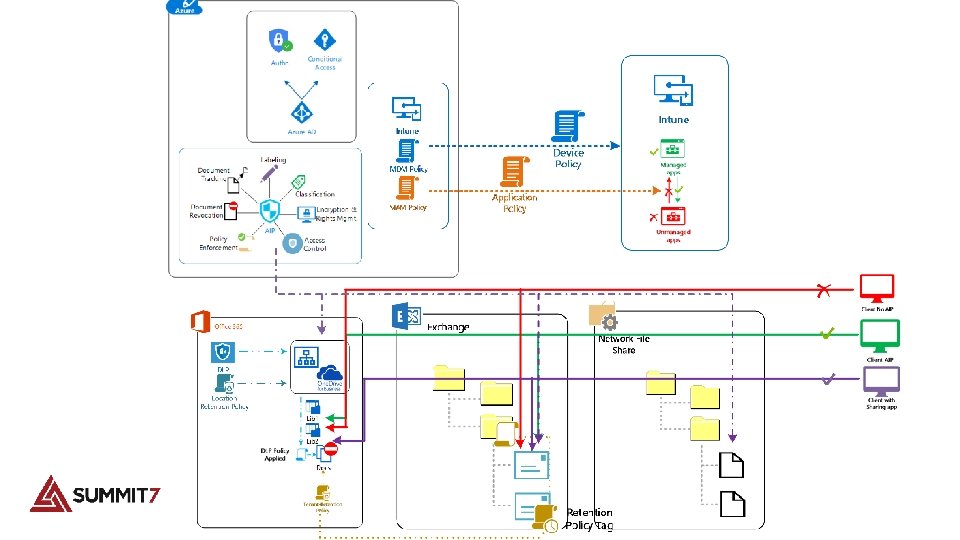

Where do I start? !? • Know what you are governing • Differentiate between mandatory and optional requirements • Assess your current state • Create a security communication plan that’s clear and simple • Find and protect sensitive data • Protect High Value Assets

Do you want a label, or label?

Office 365 Labels • Retention Policy for retaining files based on business requirements • Deletion Policy for automatically deleting files after a determined amount of time since last created or modified • Search and e. Discovery based on the tag • Data Loss Prevention information type based on the Label • For example, a DLP policy could prohibit emailing documents that are labeled PII • This should not be confused with classification labeling within Azure Information Protection • These are on the roadmap to be merged into a single solution
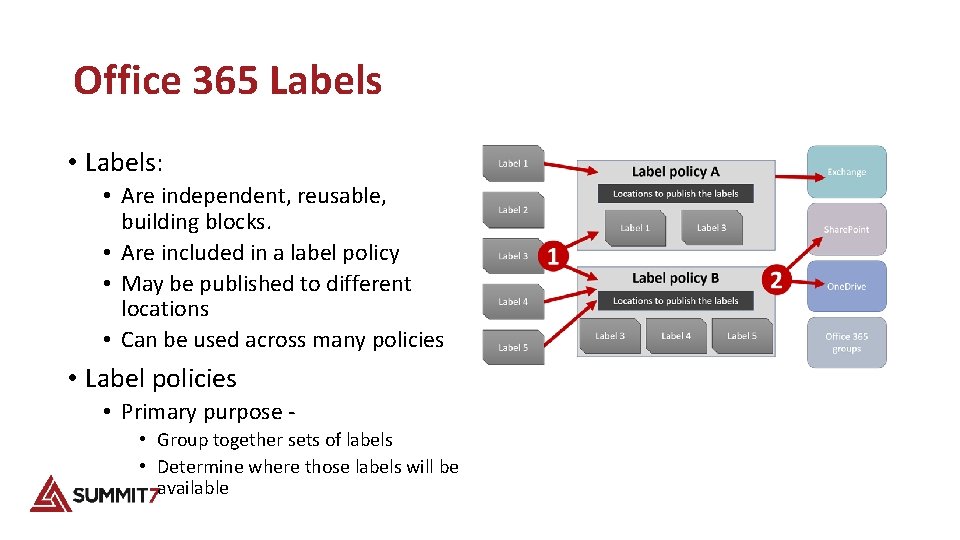
Office 365 Labels • Labels: • Are independent, reusable, building blocks. • Are included in a label policy • May be published to different locations • Can be used across many policies • Label policies • Primary purpose - • Group together sets of labels • Determine where those labels will be available

O 365 Labels & Retention • Only pushed to Mailboxes 10 MB or greater • Select where to push them to • Need screens for this section • Takes up to 24 hours for them to publish • All about retention

O 365 Content Classification • Labels are used to associated specific retention policies with documents and locations within Share. Point Online, Exchange Online and One. Drive for Business. • With labels you can create data classifications based off of Microsoft supported "Sensitive Information Types". These information types are based off of 82 common compliance regulations from around the world.
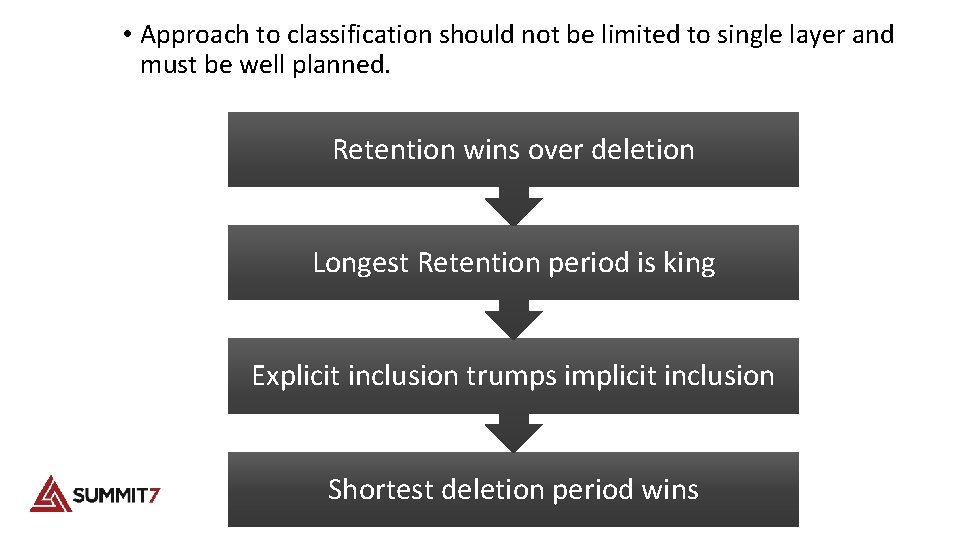
• Approach to classification should not be limited to single layer and must be well planned. Retention wins over deletion Longest Retention period is king Explicit inclusion trumps implicit inclusion Shortest deletion period wins
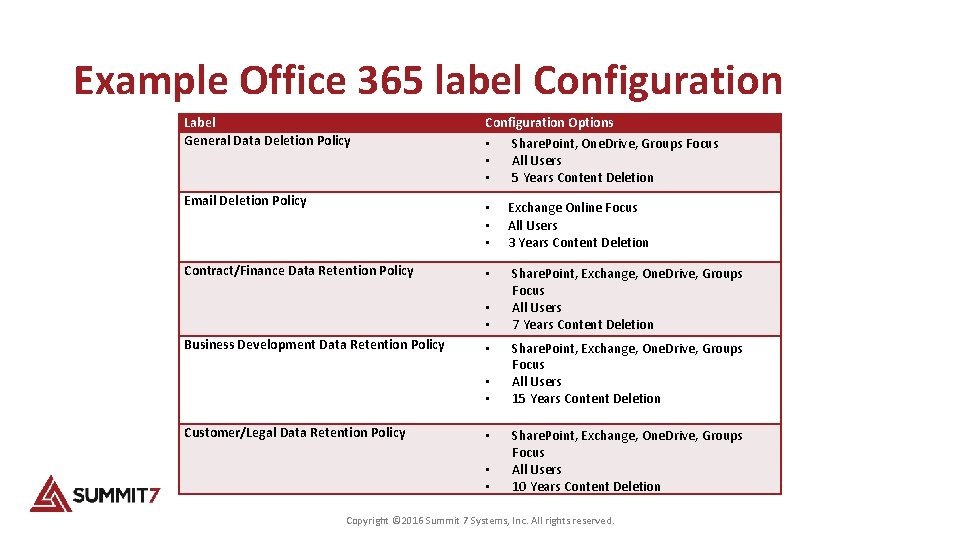
Example Office 365 label Configuration Label General Data Deletion Policy Configuration Options Email Deletion Policy • • • Contract/Finance Data Retention Policy • • • Business Development Data Retention Policy • • • Customer/Legal Data Retention Policy • • • Share. Point, One. Drive, Groups Focus All Users 5 Years Content Deletion Exchange Online Focus All Users 3 Years Content Deletion Share. Point, Exchange, One. Drive, Groups Focus All Users 7 Years Content Deletion Share. Point, Exchange, One. Drive, Groups Focus All Users 15 Years Content Deletion Share. Point, Exchange, One. Drive, Groups Focus All Users 10 Years Content Deletion Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.
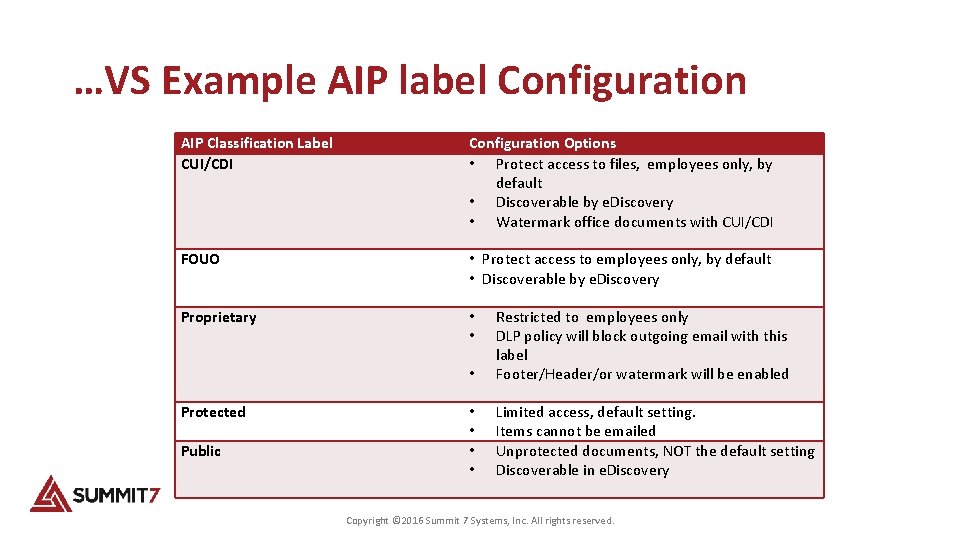
…VS Example AIP label Configuration AIP Classification Label CUI/CDI Configuration Options • Protect access to files, employees only, by default • Discoverable by e. Discovery • Watermark office documents with CUI/CDI FOUO • Protect access to employees only, by default • Discoverable by e. Discovery Proprietary • • Protected Public • Restricted to employees only DLP policy will block outgoing email with this label Footer/Header/or watermark will be enabled • • Limited access, default setting. Items cannot be emailed Unprotected documents, NOT the default setting Discoverable in e. Discovery Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.
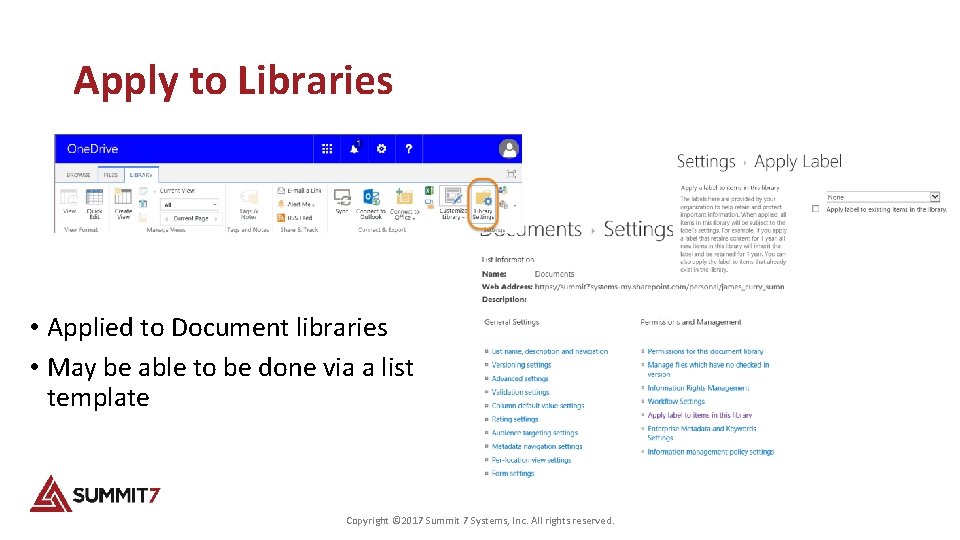
Apply to Libraries • Applied to Document libraries • May be able to be done via a list template Copyright © 2017 Summit 7 Systems, Inc. All rights reserved.
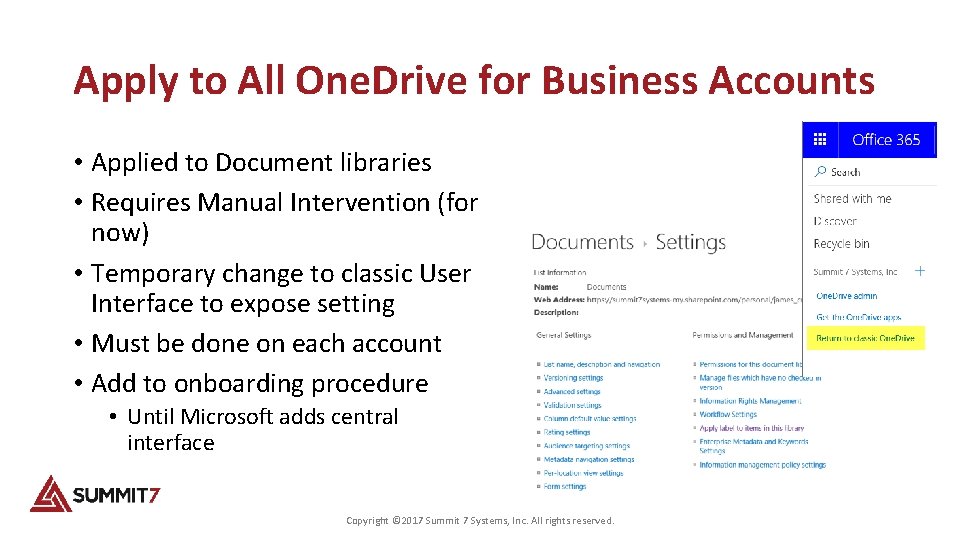
Apply to All One. Drive for Business Accounts • Applied to Document libraries • Requires Manual Intervention (for now) • Temporary change to classic User Interface to expose setting • Must be done on each account • Add to onboarding procedure • Until Microsoft adds central interface Copyright © 2017 Summit 7 Systems, Inc. All rights reserved.
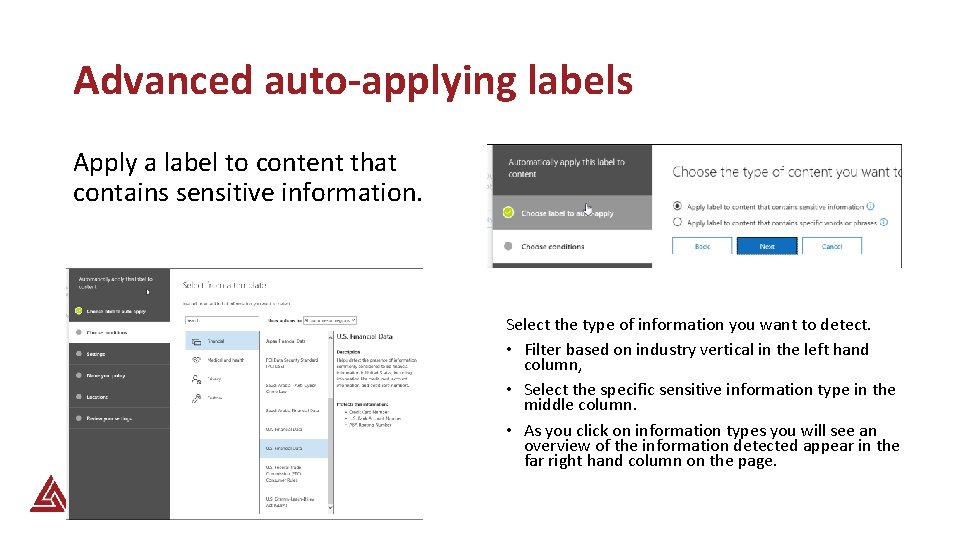
Advanced auto-applying labels Apply a label to content that contains sensitive information. Select the type of information you want to detect. • Filter based on industry vertical in the left hand column, • Select the specific sensitive information type in the middle column. • As you click on information types you will see an overview of the information detected appear in the far right hand column on the page.
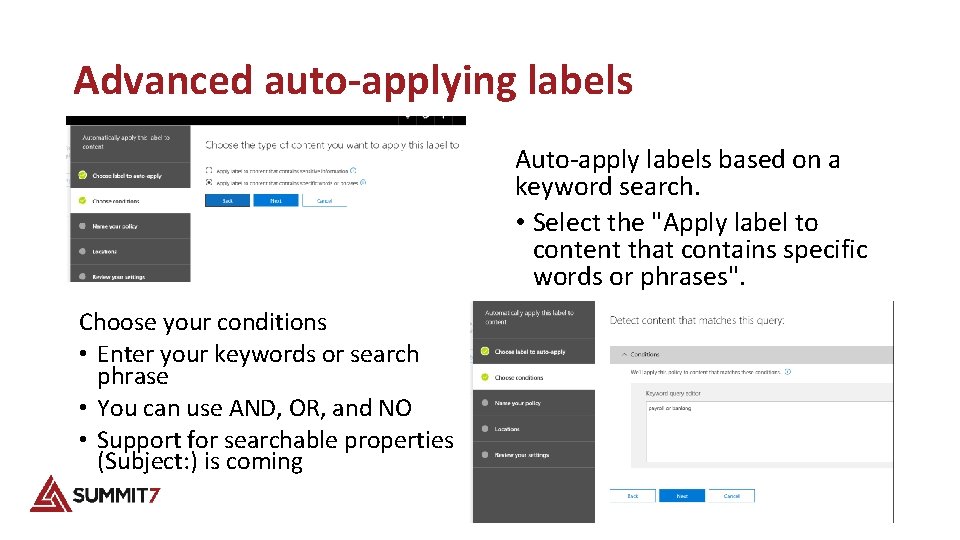
Advanced auto-applying labels Auto-apply labels based on a keyword search. • Select the "Apply label to content that contains specific words or phrases". Choose your conditions • Enter your keywords or search phrase • You can use AND, OR, and NO • Support for searchable properties (Subject: ) is coming
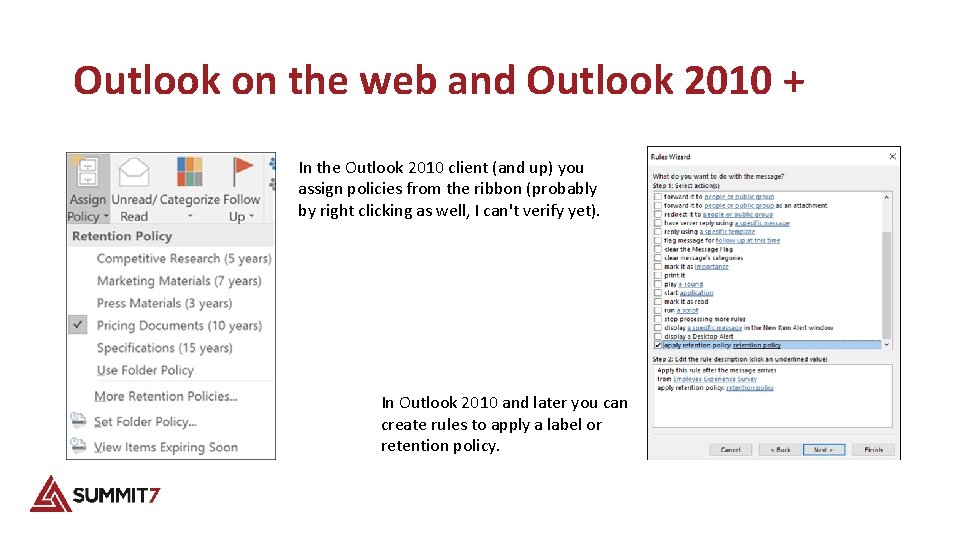
Outlook on the web and Outlook 2010 + In the Outlook 2010 client (and up) you assign policies from the ribbon (probably by right clicking as well, I can't verify yet). In Outlook 2010 and later you can create rules to apply a label or retention policy.
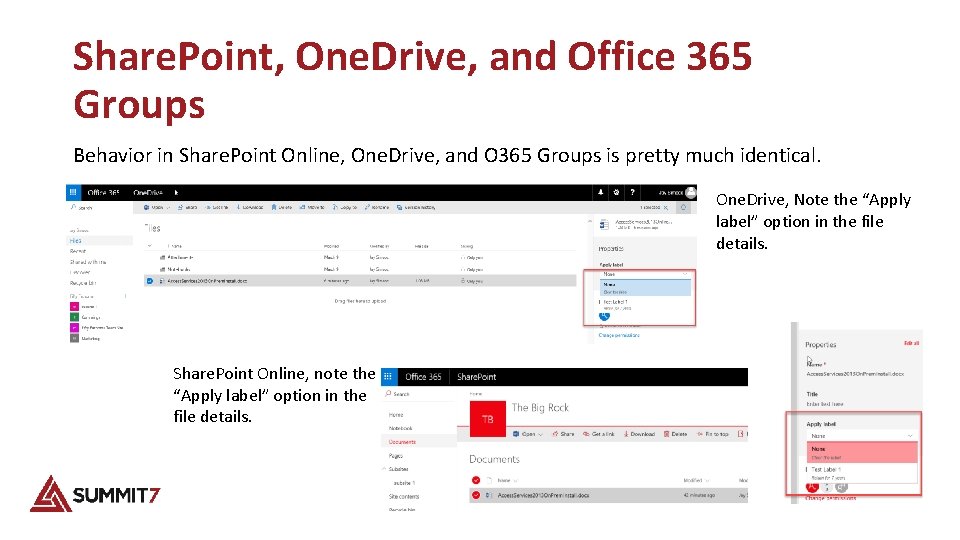
Share. Point, One. Drive, and Office 365 Groups Behavior in Share. Point Online, One. Drive, and O 365 Groups is pretty much identical. One. Drive, Note the “Apply label” option in the file details. Share. Point Online, note the “Apply label” option in the file details.

Data Loss Prevention • Near real-time protection of sensitive content • Can prevent accidental sharing of specified content • Provides for reporting • Help identify where protected information is located • DLP can span many locations such as One. Drive for Business, Share. Point Online, and Exchange

Data Loss Prevention • Includes Office 365 MDM (free stack) • Policy Driven • It has merged with Ex. O and is NOT the same UI as On-Premises Share. Point 2016 • It is now an active service • It can block files on upload • Options on how to handle violations • Apply policies in “read only” mode first! • You WILL get false positives, there’s no way around it • Minimize with good testing, get executive buy-in and support
Data Loss Prevention (DLP) • DLP allows us to control access to content based on many configurable options using policies. • Policies can be created 4 ways: • With the built-in sensitive information types found in Azure. • Programmed via XML and uploaded to the tenant. • Based on managed search properties and document tagging. • Based on Office 365 labels • Day 1 vs Day 180 planning Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.

O 365 Sensitive Information Types * AB Canada Bank Account Number Canada Driver's License Number Canada Health Service Number Canada Passport Number Canada Personal Health Identification Number (PHIN) • Canada Social Insurance Number • Credit Card Number • A Routing Number • • U. K. Driver's License Number • U. K. Electoral Roll Number • U. K. National Health Service Number • U. K. National Insurance Number (NINO) • U. S. / U. K. Passport Number • U. S. Bank Account Number • U. S. Driver's License Number • U. S. Individual Taxpayer Identification Number (ITIN) • U. S. Social Security Number (SSN)
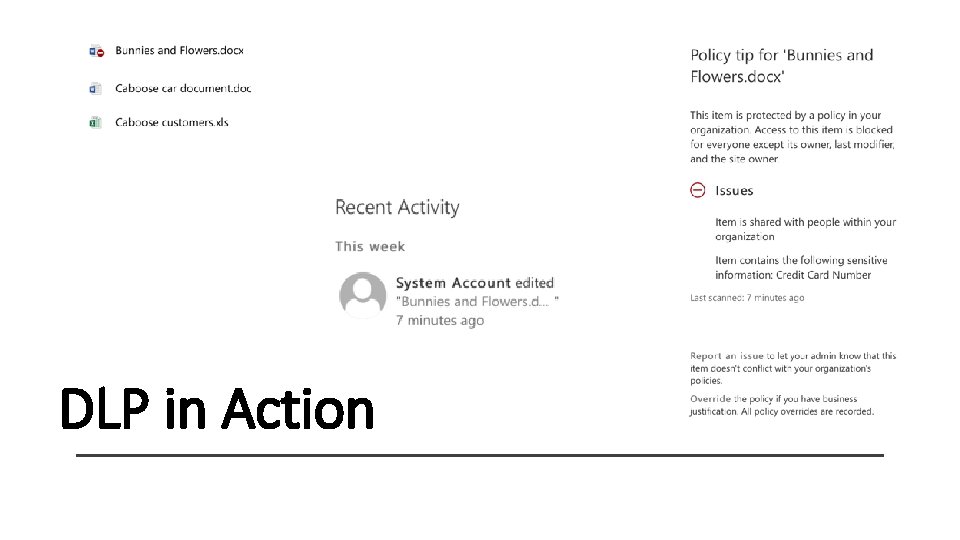
DLP in Action

Power. Shell 101 for Security Admins $User. Credential = Get-Credential $Session = New-PSSession -Configuration. Name Microsoft. Exchange Connection. Uri https: //ps. compliance. protection. outlook. com/powershell-liveid/ Credential $User. Credential -Authentication Basic -Allow. Redirection Import-PSSession $Session
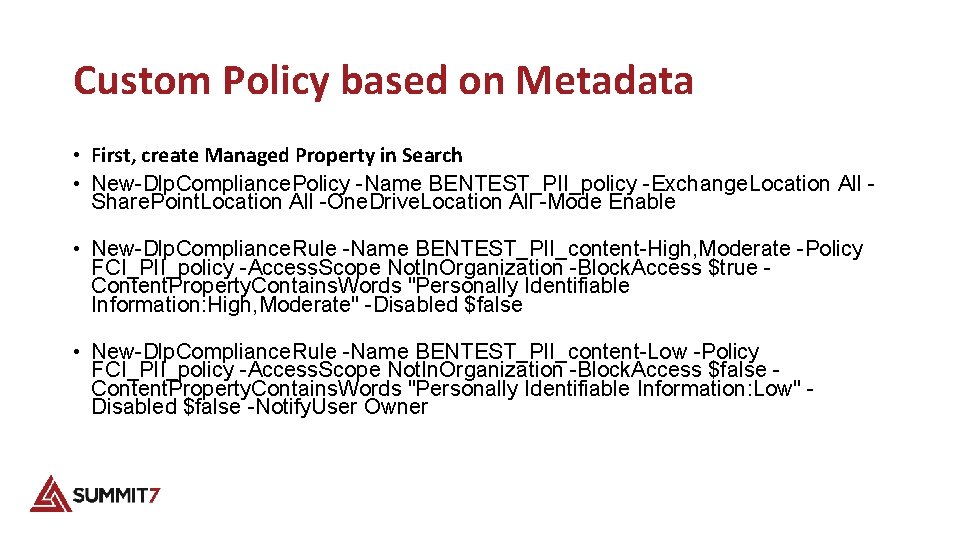
Custom Policy based on Metadata • First, create Managed Property in Search • New-Dlp. Compliance. Policy -Name BENTEST_PII_policy -Exchange. Location All Share. Point. Location All -One. Drive. Location All -Mode Enable • New-Dlp. Compliance. Rule -Name BENTEST_PII_content-High, Moderate -Policy FCI_PII_policy -Access. Scope Not. In. Organization -Block. Access $true Content. Property. Contains. Words "Personally Identifiable Information: High, Moderate" -Disabled $false • New-Dlp. Compliance. Rule -Name BENTEST_PII_content-Low -Policy FCI_PII_policy -Access. Scope Not. In. Organization -Block. Access $false Content. Property. Contains. Words "Personally Identifiable Information: Low" Disabled $false -Notify. User Owner

Custom Sensitive Information Type • https: //support. office. com/en-us/article/Create-a-custom-sensitiveinformation-type-82 c 382 a 5 -b 6 db-44 fd-995 d-b 333 b 3 c 7 fc 30? ui=en. US&rs=en-US&ad=US • If policies hang, use Power. Shell to force remove
Legacy Azure Rights Management • Configure from Settings -> Services and Add-ins & Share. Point Online Tenant Settings!! • Library and Document scoped • It’s now “Azure Information Protection” • This is a bit confusing • Other features still branded ”Azure Information Protection”

Azure Information Protection • Adds additional security to documents in addition to the container they are already secured within • AIP allows us to classify documents, such as Public, Proprietary, CDI/CUI and PII • Classify for the purpose of adding technical security and to ensure the visibility of the secure nature of the file • For example, a CUI/CDI file could be controlled access and also contain a watermark, automatically, noting it’s file type. This helps to adhere to compliance regulations and keep the content with the need to know circle it was intended for.
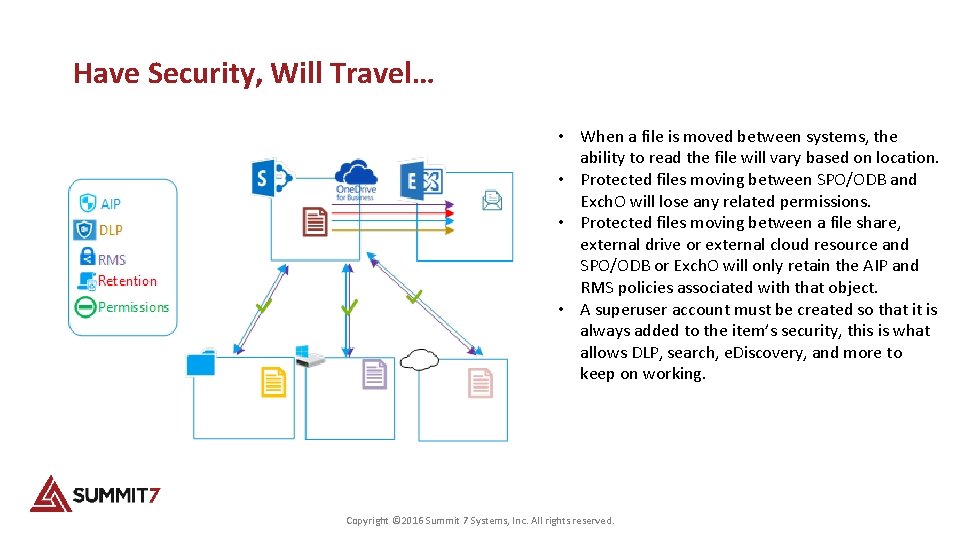
Have Security, Will Travel… • When a file is moved between systems, the ability to read the file will vary based on location. • Protected files moving between SPO/ODB and Exch. O will lose any related permissions. • Protected files moving between a file share, external drive or external cloud resource and SPO/ODB or Exch. O will only retain the AIP and RMS policies associated with that object. • A superuser account must be created so that it is always added to the item’s security, this is what allows DLP, search, e. Discovery, and more to keep on working. Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.
AIP Global Configuration • AIP is primarily used to protect access to files on the client • The following options can be configured on any label: • Restricted Actions • Encryption • Group-scoped Policies (security trimmed labels) • Labels apply metadata that can be seen by other systems, i. e. DLP, e. Discovery, Search. • Force justification when classifying down, such as with CUI/CDI changes seen in the accompanying graphic: • A full version of the AIP client must be installed to author and classify documents. • Office Online allows read-only access to AIP protected files – coauthoring is not allowed. • Only a Windows machine with the full AIP client will be able to edit AIP documents. Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.
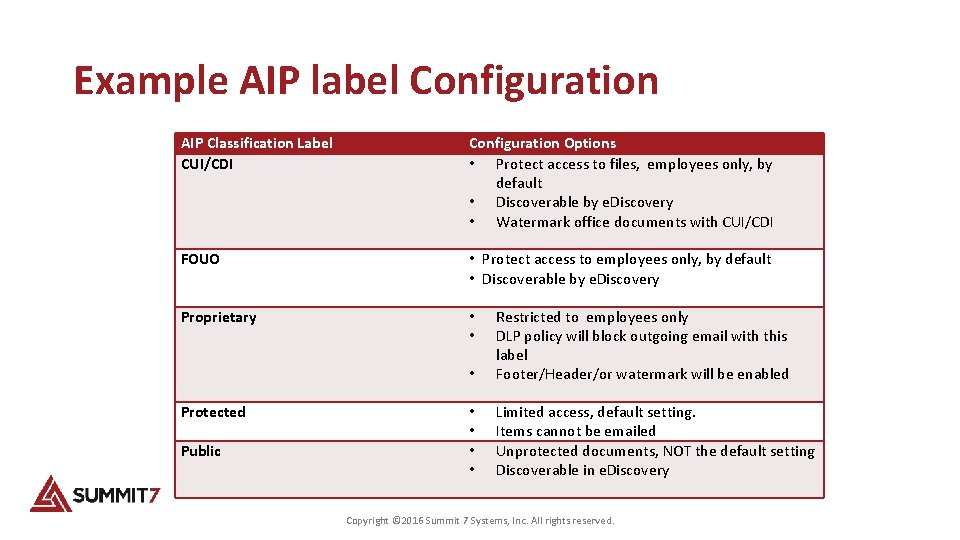
Example AIP label Configuration AIP Classification Label CUI/CDI Configuration Options • Protect access to files, employees only, by default • Discoverable by e. Discovery • Watermark office documents with CUI/CDI FOUO • Protect access to employees only, by default • Discoverable by e. Discovery Proprietary • • Protected Public • Restricted to employees only DLP policy will block outgoing email with this label Footer/Header/or watermark will be enabled • • Limited access, default setting. Items cannot be emailed Unprotected documents, NOT the default setting Discoverable in e. Discovery Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.
One. Drive for Business Governance • I’m just going to demo this…are you tired of PPTx yet?
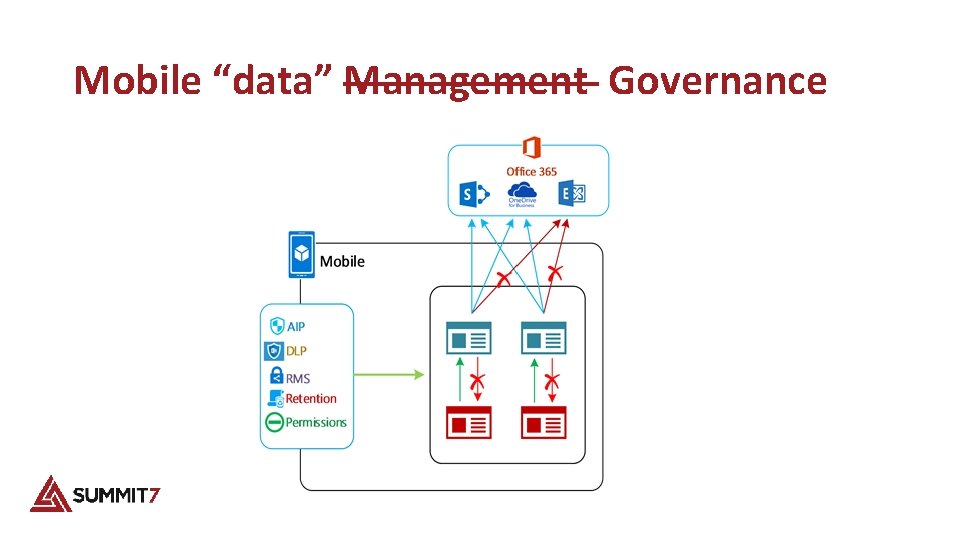
Mobile “data” Management Governance
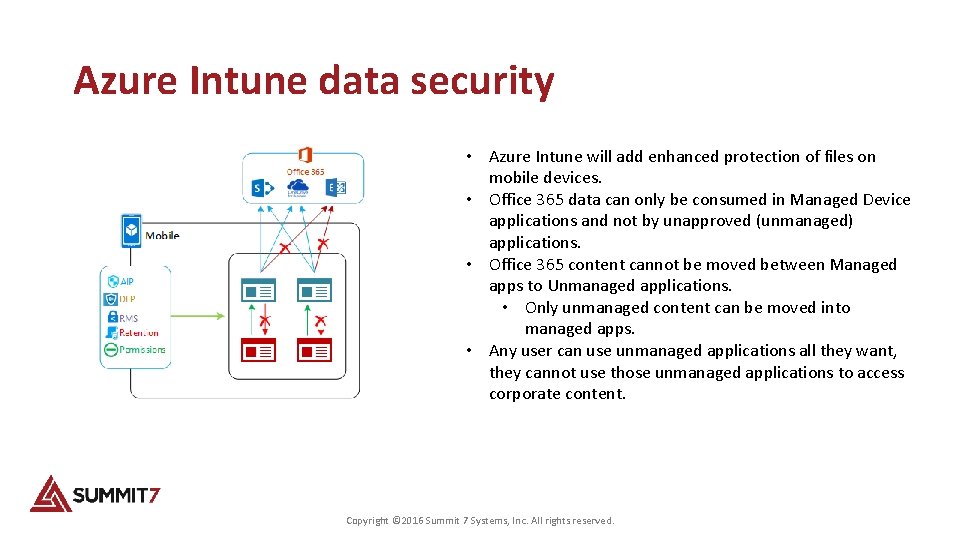
Azure Intune data security • Azure Intune will add enhanced protection of files on mobile devices. • Office 365 data can only be consumed in Managed Device applications and not by unapproved (unmanaged) applications. • Office 365 content cannot be moved between Managed apps to Unmanaged applications. • Only unmanaged content can be moved into managed apps. • Any user can use unmanaged applications all they want, they cannot use those unmanaged applications to access corporate content. Copyright © 2016 Summit 7 Systems, Inc. All rights reserved.

Group Membership (Azure AD) • Assigned vs. Dynamic • Assigned is old-school groups • Dynamic is new in AAS • Set rules base on user attributes (dept, location, etc) • Members are automagically added or removed from security group(s) • Dynamic Groups are much more powerful than assigned groups • Basic Business Logic • (user. department -eq "Sales") -or (user. department -eq "Marketing") • (user. department -eq "Sales") -and -not (user. job. Title -contains ”Engineer") • (user. location -eq ”NA") -and -not (user. region -contains ”NE")
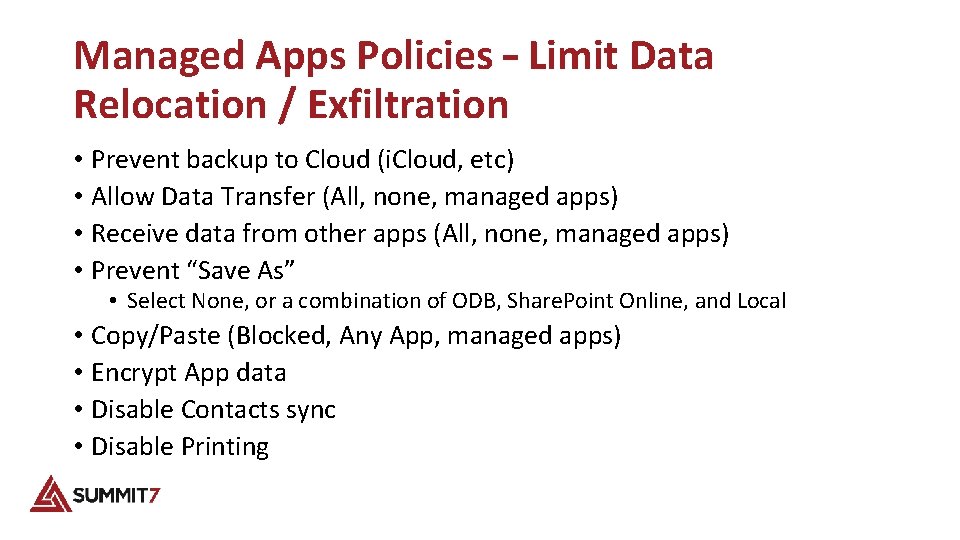
Managed Apps Policies – Limit Data Relocation / Exfiltration • Prevent backup to Cloud (i. Cloud, etc) • Allow Data Transfer (All, none, managed apps) • Receive data from other apps (All, none, managed apps) • Prevent “Save As” • Select None, or a combination of ODB, Share. Point Online, and Local • Copy/Paste (Blocked, Any App, managed apps) • Encrypt App data • Disable Contacts sync • Disable Printing

Summation • Have a roadmap and be realistic • Know what you are protecting • Buy the correct licenses • Apply a layered approach • Borrow our learning curve • Find a partner that will transfer knowledge
- Slides: 42