Objectives To understand the criminal use of computer


Objectives • To understand the criminal use of computer systems including: • Unauthorised access and modification of materials • Creation and spreading of malware

Criminal use Learning Aim C The wider implications of digital systems Starter • Which do you think are the top three countries for cyber attacks?
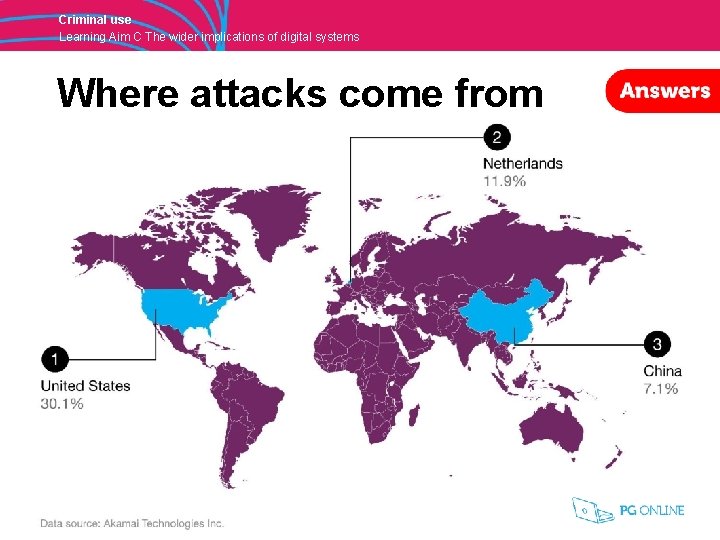
Criminal use Learning Aim C The wider implications of digital systems Where attacks come from

Criminal use Learning Aim C The wider implications of digital systems Unauthorised access • Unauthorised access is where a person gains access to a computer system without permission • This could be a hacker who gains permission to a system they shouldn’t be using • It may also be an employee who has permission to use some of a system, but gains access to another part • Hackers try to find weaknesses in a computer system • They will often gain access with one user account and then try to alter the permissions to get root or admin access

Criminal use Learning Aim C The wider implications of digital systems Unauthorised modification • Unauthorised modification includes: • Deleting other user’s files • Changing the content of documents • Altering the content of web pages or databases • Rewriting computer programs to remove activation keys • What is one other unauthorised modification that can be made?

Criminal use Learning Aim C The wider implications of digital systems Case study: Kevin Mitnick • In 1992, Kevin Mitnick was the most wanted hacker in the USA • He used many hacking techniques to gain unauthorised access to computers, systems and files • He spent five years in prison for his crimes • Kevin now works as a computer security consultant

Criminal use Learning Aim C The wider implications of digital systems Worksheet 6 • Now complete Task 1 and Task 2 on Worksheet 4

Criminal use Learning Aim C The wider implications of digital systems What is malware? • Malware is malicious software • It will do something harmful such as: • Deleting files • Slowing the computer • Sending spam • Malware includes: • Viruses and worms • Botnets and rootkits • What are two other types of malware?
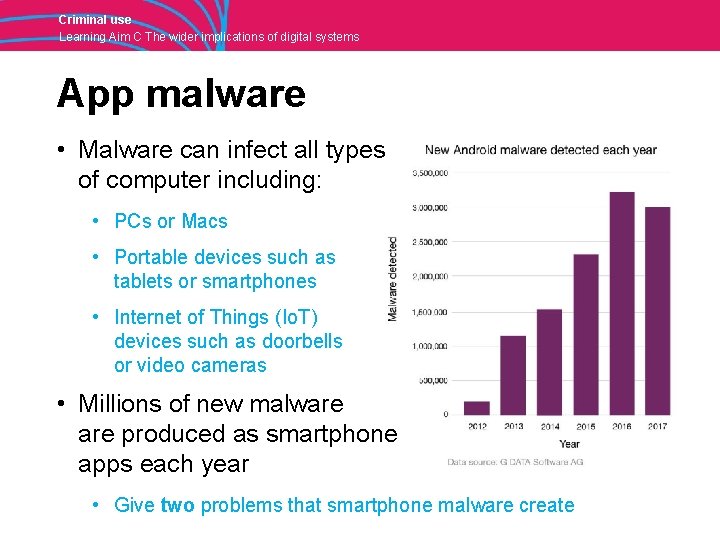
Criminal use Learning Aim C The wider implications of digital systems App malware • Malware can infect all types of computer including: • PCs or Macs • Portable devices such as tablets or smartphones • Internet of Things (Io. T) devices such as doorbells or video cameras • Millions of new malware produced as smartphone apps each year • Give two problems that smartphone malware create

Criminal use Learning Aim C The wider implications of digital systems Case study: Skygofree • Malware details: • Created in 2015, but discovered in 2018 • Downloaded from malicious websites • Targets Android devices • Skygofree contains spyware that: • Captures photos and video • Records audio • Reads Whats. App messages • Reads geolocation data
Criminal use Learning Aim C The wider implications of digital systems Creation of malware • Malware is created in the same way as normal computer programs • A hacker will write programming code which exploits weaknesses in computer systems, networks or software • They will then use a number of methods to get users or their computers to run the code • There are tools that allow hackers to create malware without knowing how to program • What are the dangers of using these?

Criminal use Learning Aim C The wider implications of digital systems Spreading of malware • Human viruses are spread by: • Coughing and sneezing • Touching or shaking hands • Touching food with dirty hands • How are computer viruses and malware spread?
Criminal use Learning Aim C The wider implications of digital systems Spreading of malware • How do computer viruses and malware spread? • A number of methods can be used • Email attachments containing malware • Clicking on web page links that download malicious software • Removable media which auto-runs or the user runs the malware • Trojans – a useful item of software which is run also contains malware
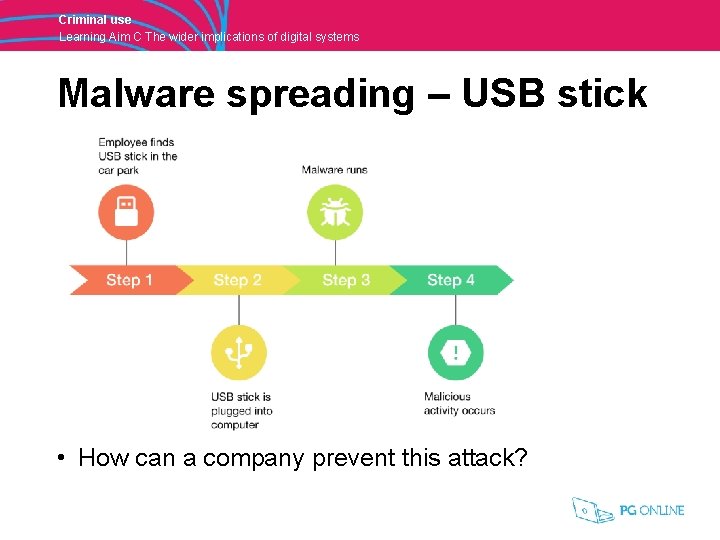
Criminal use Learning Aim C The wider implications of digital systems Malware spreading – USB stick • How can a company prevent this attack?
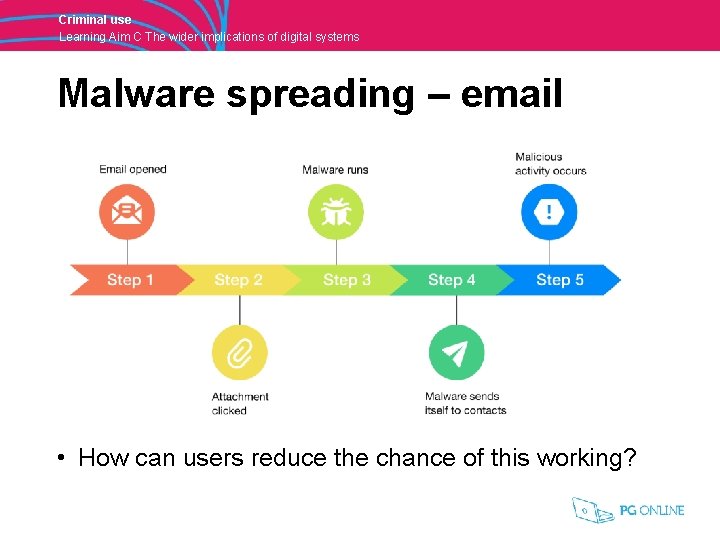
Criminal use Learning Aim C The wider implications of digital systems Malware spreading – email • How can users reduce the chance of this working?
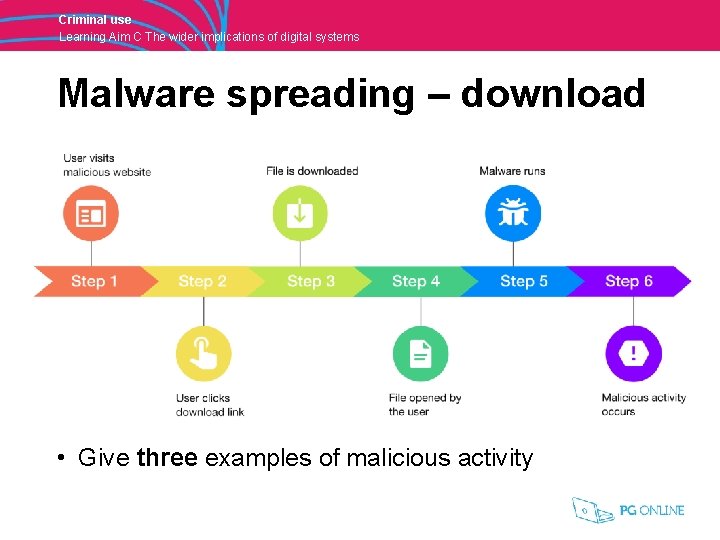
Criminal use Learning Aim C The wider implications of digital systems Malware spreading – download • Give three examples of malicious activity
Criminal use Learning Aim C The wider implications of digital systems Worksheet 6 • Now complete Task 3 on Worksheet 4

Criminal use Learning Aim C The wider implications of digital systems Law • The Computer Misuse Act (1990) makes it illegal to: • Gain unauthorised access to a computer system • Make unauthorised modifications to software or data • Spread malware • The Police and Justice Act (2006) makes it illegal to: • Create malware or items that may be used in computer misuse • Committing these crimes can result in up to 10 years in prison and a fine
Criminal use Learning Aim C The wider implications of digital systems Worksheet 6 • Now complete Task 4 on Worksheet 4

Criminal use Learning Aim C The wider implications of digital systems Plenary • Lucy and Abdi are shopping online for birthday presents • They are looking at websites which offer gifts from overseas • One of these sites offers a link to an app which will allow them to see their gift’s journey from the USA to the UK • Lucy wants to download the app, but Abdi thinks it is a bad idea • Why does Abdi have concerns?
Criminal use Learning Aim C The wider implications of digital systems Copyright © 2019 PG Online Limited The contents of this unit are protected by copyright. This unit and all the worksheets, Power. Point presentations, teaching guides and other associated files distributed with it are supplied to you by PG Online Limited under licence and may be used and copied by you only in accordance with the terms of the licence. Except as expressly permitted by the licence, no part of the materials distributed with this unit may be used, reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic or otherwise, without the prior written permission of PG Online Limited. Licence agreement This is a legal agreement between you, the end user, and PG Online Limited. This unit and all the worksheets, Power. Point presentations, teaching guides and other associated files distributed with it is licensed, not sold, to you by PG Online Limited for use under the terms of the licence. The materials distributed with this unit may be freely copied and used by members of a single institution on a single site only. You are not permitted to share in any way any of the materials or part of the materials with any third party, including users on another site or individuals who are members of a separate institution. You acknowledge that the materials must remain with you, the licencing institution, and no part of the materials may be transferred to another institution. You also agree not to procure, authorise, encourage, facilitate or enable any third party to reproduce these materials in whole or in part without the prior permission of PG Online Limited.
- Slides: 22