Number Theory and Advanced Cryptography 3 Quadratic Residues

Number Theory and Advanced Cryptography 3. Quadratic Residues and Rabin Public key Cryptosystem Part I: Introduction to Number Theory Part II: Advanced Cryptography Chih-Hung Wang Sept. 2011 1

Quadratic Residues 2

Quadratic Residues 3

Quadratic Residuosity Problem (1) Proof: see page 188 4

Quadratic Residuosity Problem (2) Important! 5
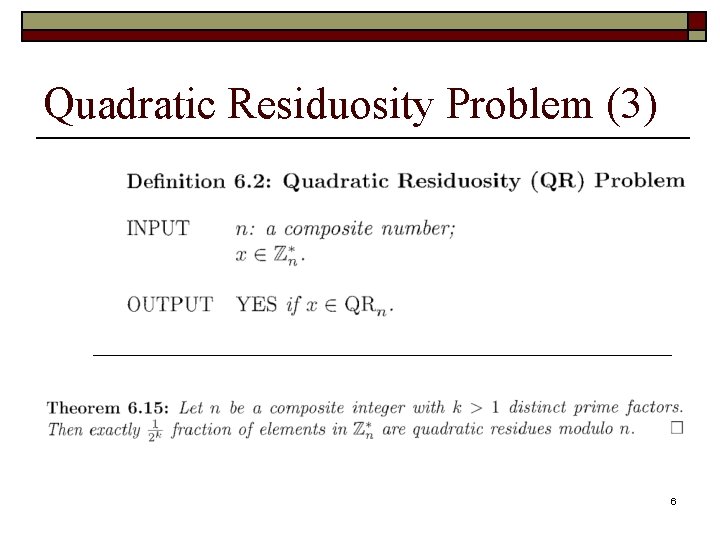
Quadratic Residuosity Problem (3) 6
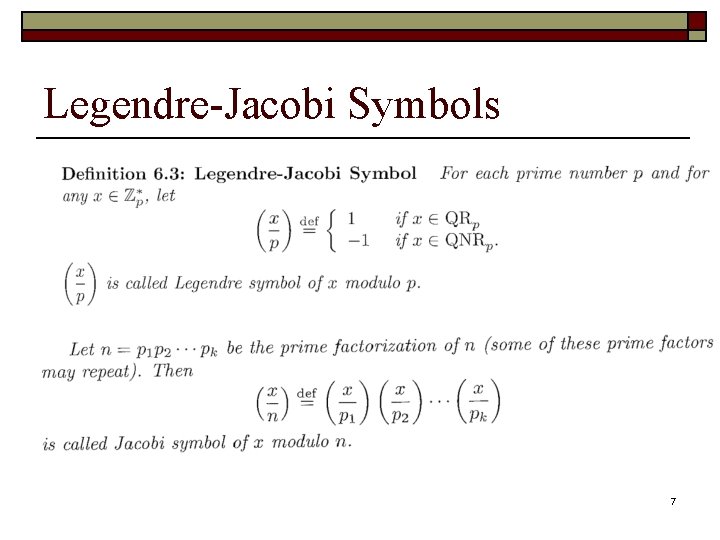
Legendre-Jacobi Symbols 7
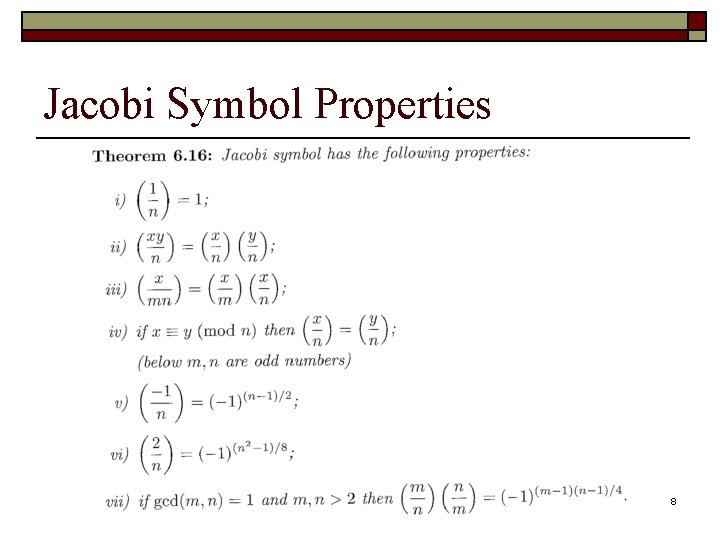
Jacobi Symbol Properties 8
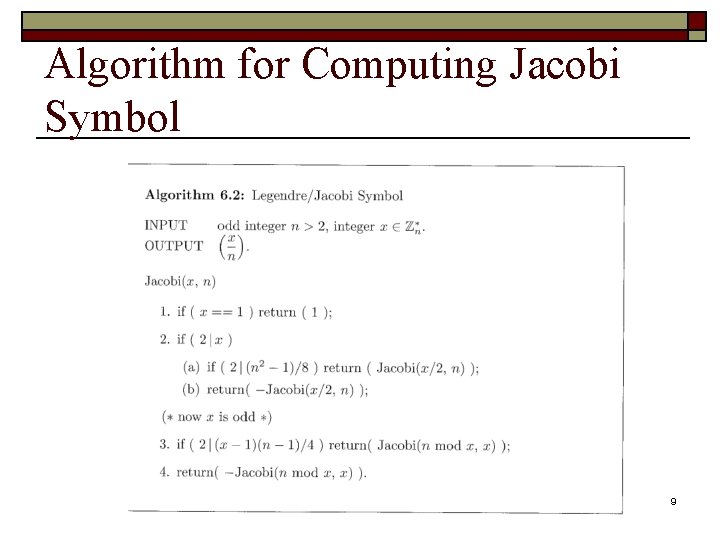
Algorithm for Computing Jacobi Symbol 9
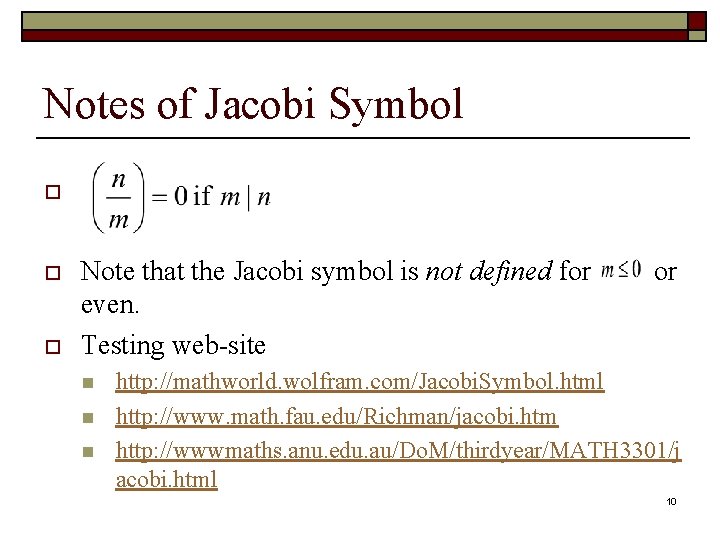
Notes of Jacobi Symbol o o o Note that the Jacobi symbol is not defined for even. Testing web-site n n n or http: //mathworld. wolfram. com/Jacobi. Symbol. html http: //www. math. fau. edu/Richman/jacobi. htm http: //wwwmaths. anu. edu. au/Do. M/thirdyear/MATH 3301/j acobi. html 10
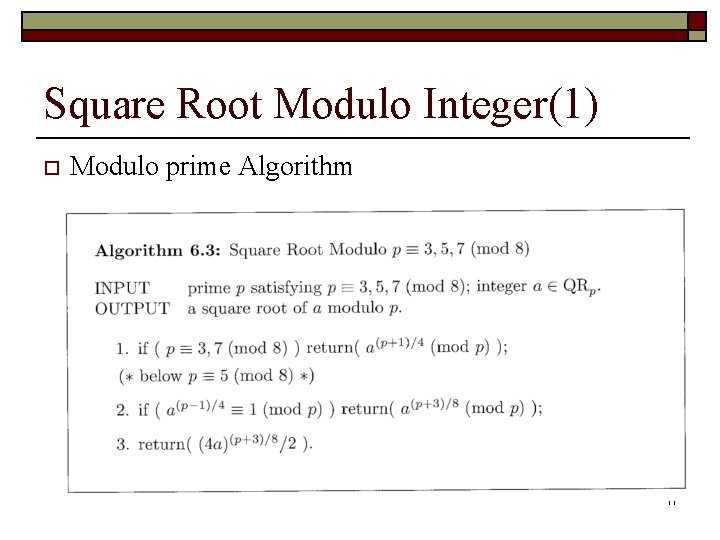
Square Root Modulo Integer(1) o Modulo prime Algorithm 11
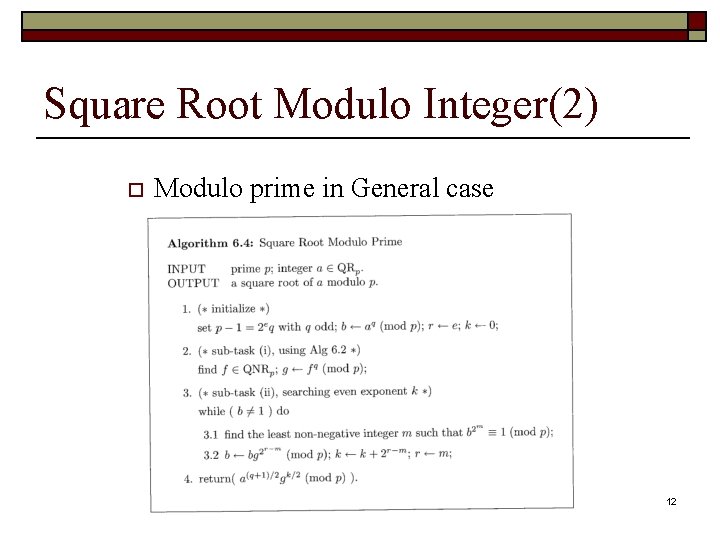
Square Root Modulo Integer(2) o Modulo prime in General case 12
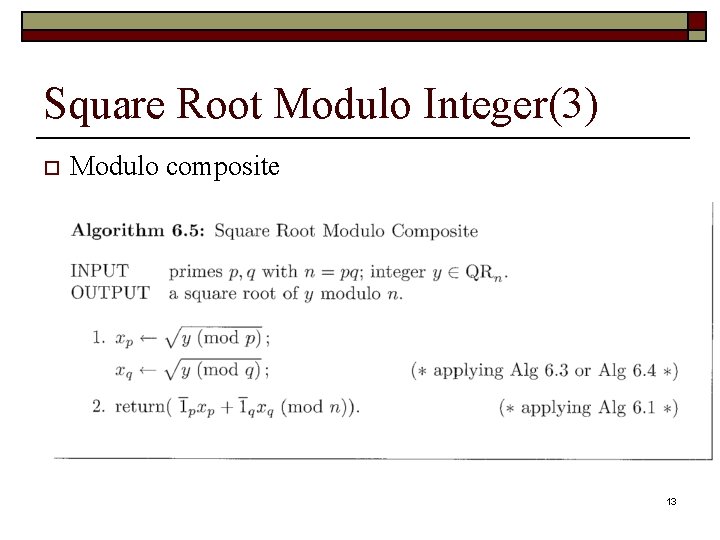
Square Root Modulo Integer(3) o Modulo composite 13
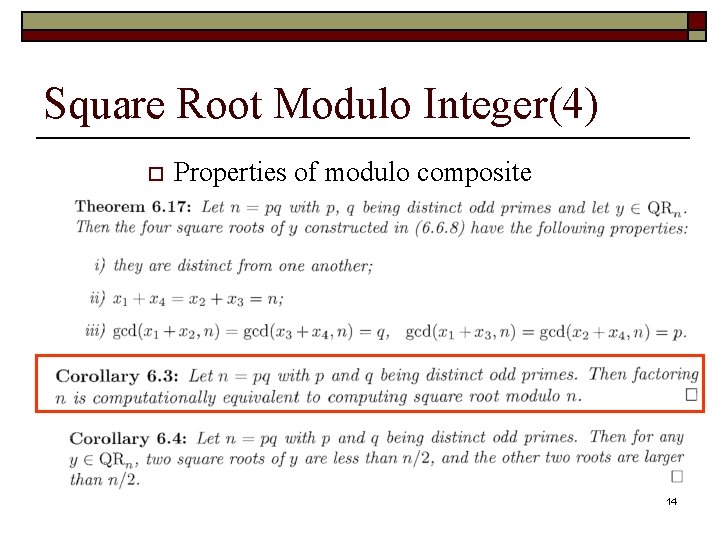
Square Root Modulo Integer(4) o Properties of modulo composite 14
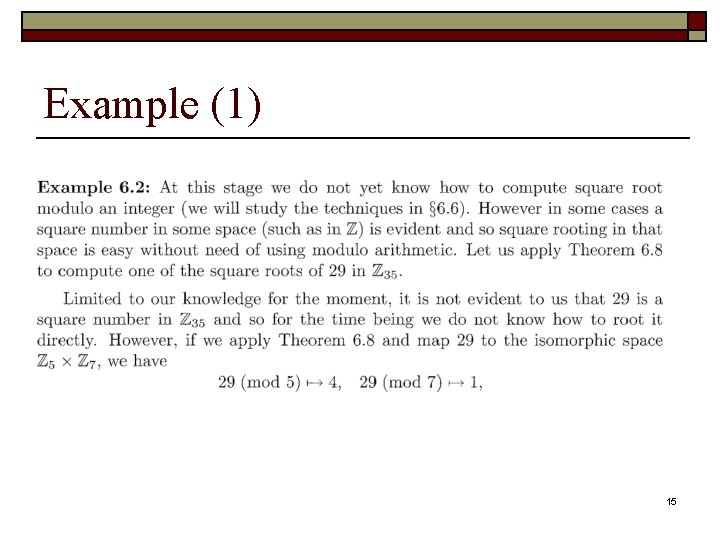
Example (1) 15
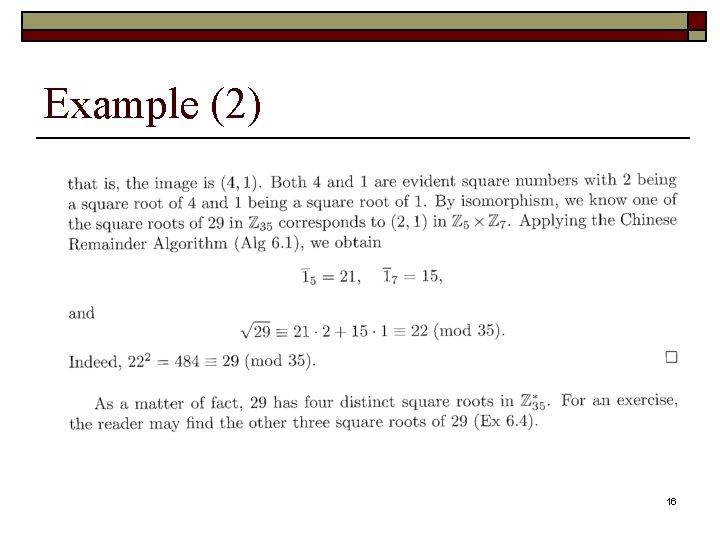
Example (2) 16

Factoring Problem o For a large n with large prime factors, factoring is a hard problem, but not as hard as it used to be. n Example: factorize 48770428682337401 => hard problem o n 1977: three inventors of RSA issue “Mathematical Games” o n Easy problem: Is 223092871 a factor of 48770428682337401? $100 reward 1994: RSA-129 (428 bits) breaking 17
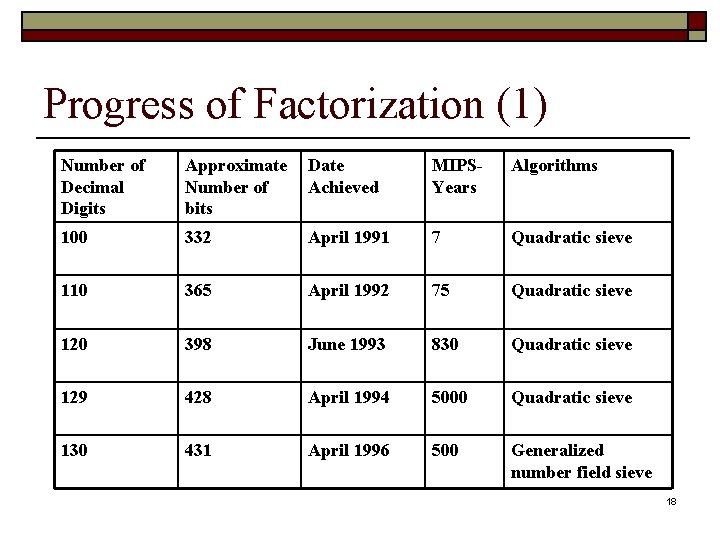
Progress of Factorization (1) Number of Decimal Digits Approximate Number of bits Date Achieved MIPSYears Algorithms 100 332 April 1991 7 Quadratic sieve 110 365 April 1992 75 Quadratic sieve 120 398 June 1993 830 Quadratic sieve 129 428 April 1994 5000 Quadratic sieve 130 431 April 1996 500 Generalized number field sieve 18
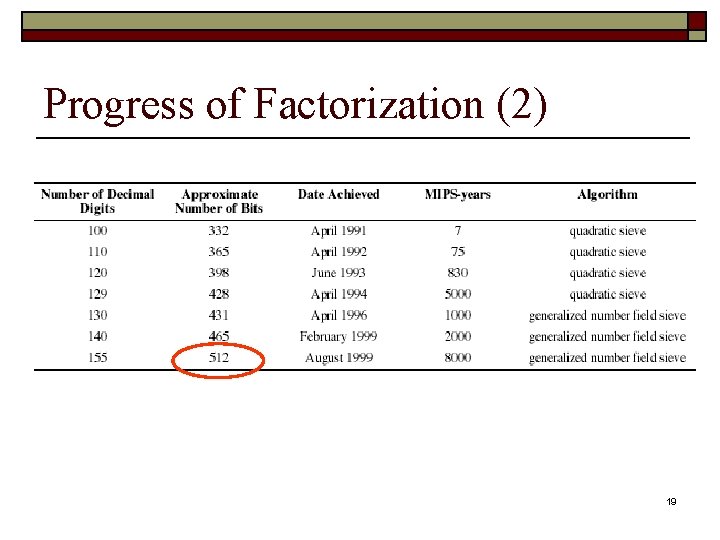
Progress of Factorization (2) 19
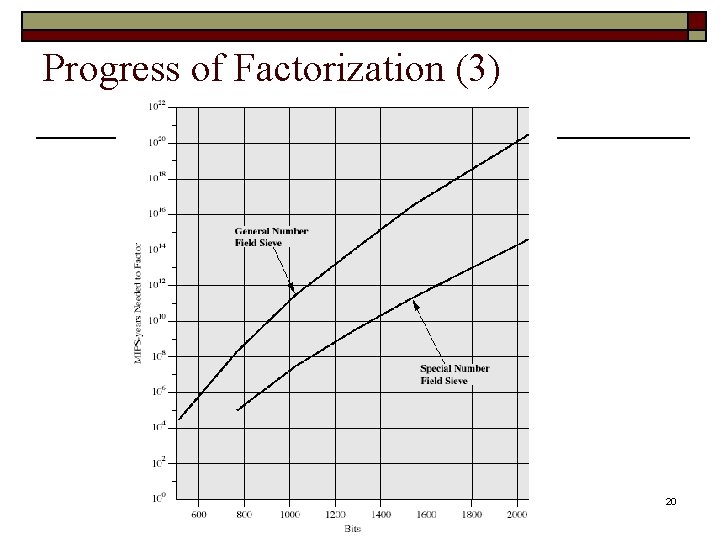
Progress of Factorization (3) 20
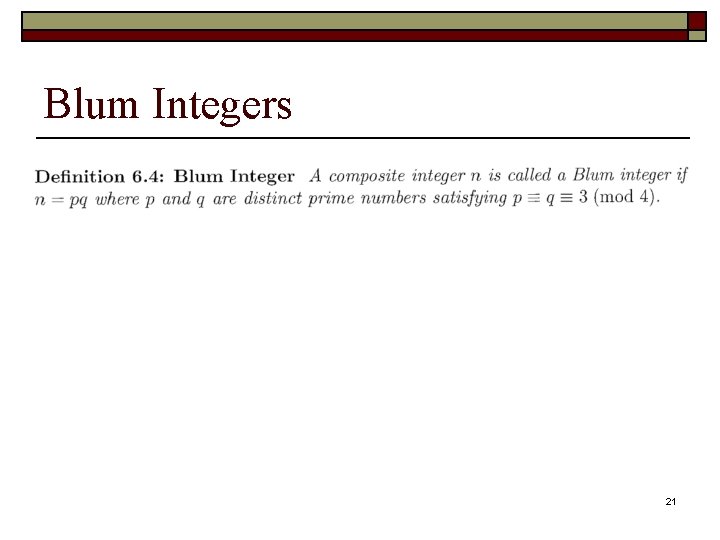
Blum Integers 21
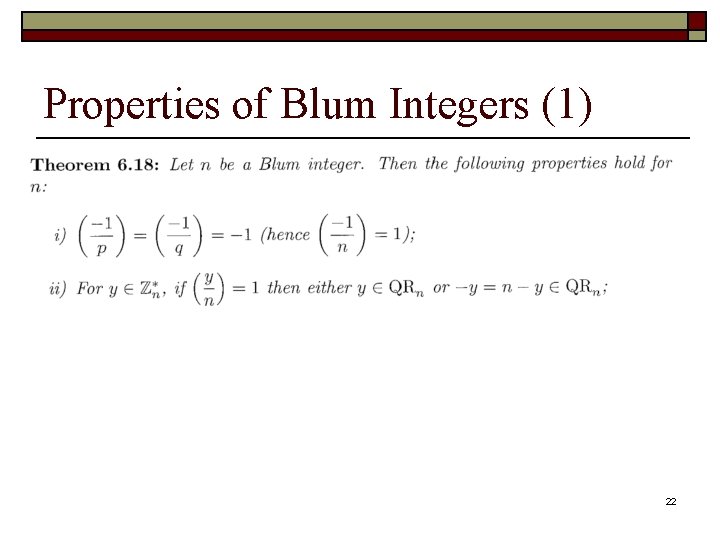
Properties of Blum Integers (1) 22
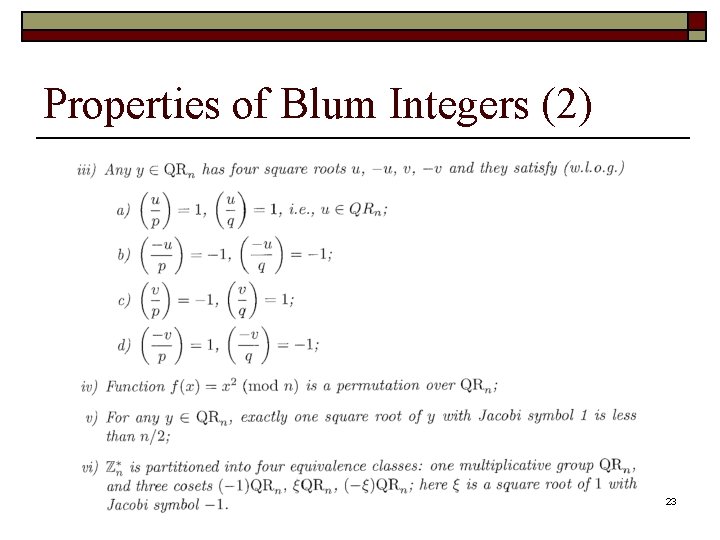
Properties of Blum Integers (2) 23
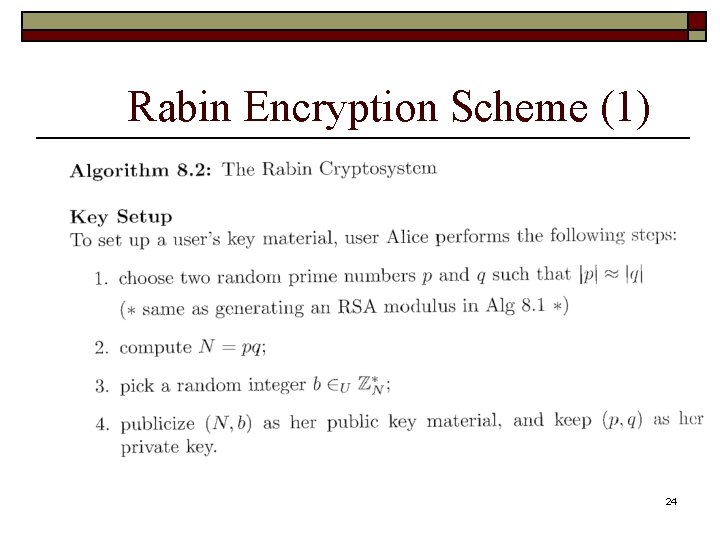
Rabin Encryption Scheme (1) 24
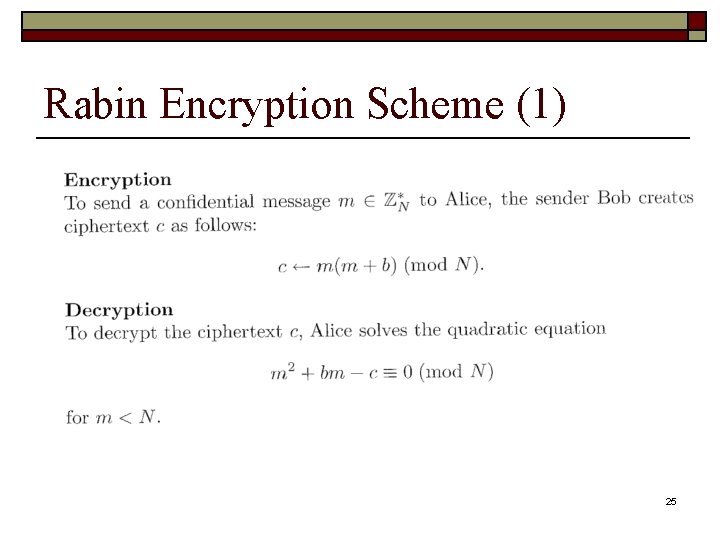
Rabin Encryption Scheme (1) 25
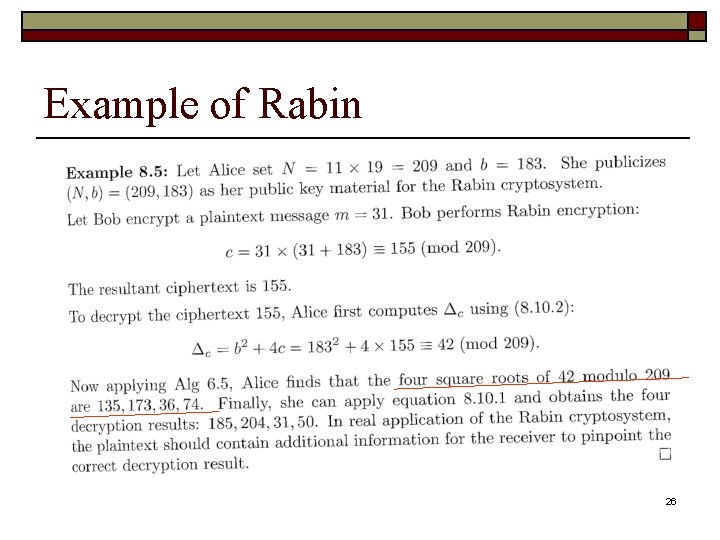
Example of Rabin 26

Insecurity of Rabin CPA (Chosen-plaintext attack) CCA (Chosen-ciphertext attack) 27
- Slides: 27