Not so long ago in a galaxy not
















- Slides: 20

Not so long ago, in a galaxy not so far, away. . . It is a period of cyber attack in the universe. Information and Physical Security, striking from a hidden base, has won another victory against the evil Galactic virus. This computer virus is strong and the spaceships cannot fight the battle alone.

During the battle, Security Agents manage to acquire anti-complacency plans to attack the Empire's ultimate weapon: an armored space station with enough viruses to destroy productivity in the Universe. Pursued by the Empire's sinister agents, Security races home aboard their starship, custodian of the acquired plans. They have discovered the one critical element to fight complacency that will save Texaco and it’s employees and restore security to the galaxy. . .

Security sends a message to all employees. “Help us, employees. You are our only hope!”

The key to security awareness is embedded in the word security.

Why are we doing this? Audit Findings: Physical Intrusion • • Two people were able to get in the building. They also were able to obtain contract badges. They obtained access to the Data Center. The intruders used Social Engineering to convince users to reveal passwords and network information.

Why are we doing this? Audit Findings: Cyber Penetration • Able to access servers that had weak security configurations. • Able to access dial in devices with “default” passwords. • Able to steal a list of usernames with passwords and cracked 6, 500 of those passwords in a few days. • Most were cracked in a couple of seconds. • They exploited trust relationships with Joint Ventures (JVs).

Workshop Guidelines It’s O. K. to: • • • Participate actively Ask questions Have fun Learn and teach others Disagree • Be open to others’ ideas • Try, risk and make mistakes • Think unconventionally, creatively • Tell stories that support Security Awareness • Doodle!!

Security Video • Case for Action video

Security Topics We Will Address Personal Physical Information

Integration with Existing Efforts Workplace Violence Six Sigma and Other Quality Efforts New Hire Orientation Safety

Activity - Scenario Exercise

Scenario You receive a phone call from an unknown person. She states that her PC is locked. She would like for you to give her access to the network because she is working on a critical report for the CEO and is in a hurry. She further states that if you don’t assist her, he will certainly hear about it. What should you do?

Scenario You are using a DSL communication line in a hotel. All of a sudden you notice that your personal firewall indicates that someone is probing your PC. What should you do?

Scenario A Senior Executive walks into a meeting and he is not wearing a badge. What should you do?

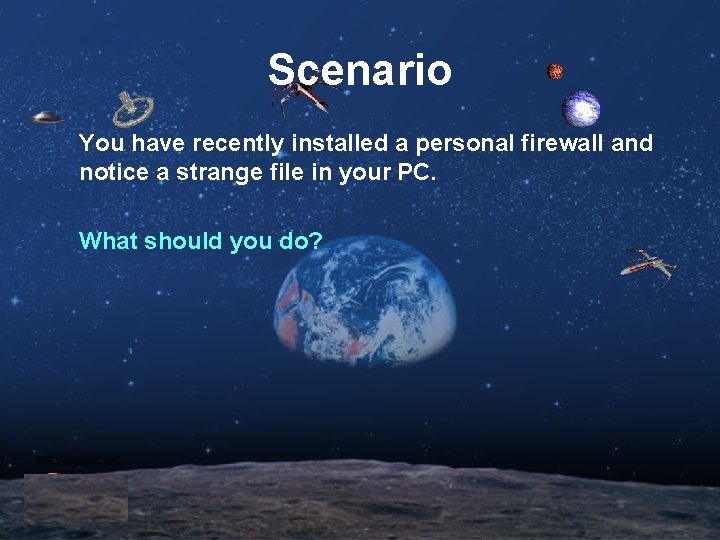
Scenario You have recently installed a personal firewall and notice a strange file in your PC. What should you do?

Scenario Your friend tells you that his password is DILBERT… What should you say?

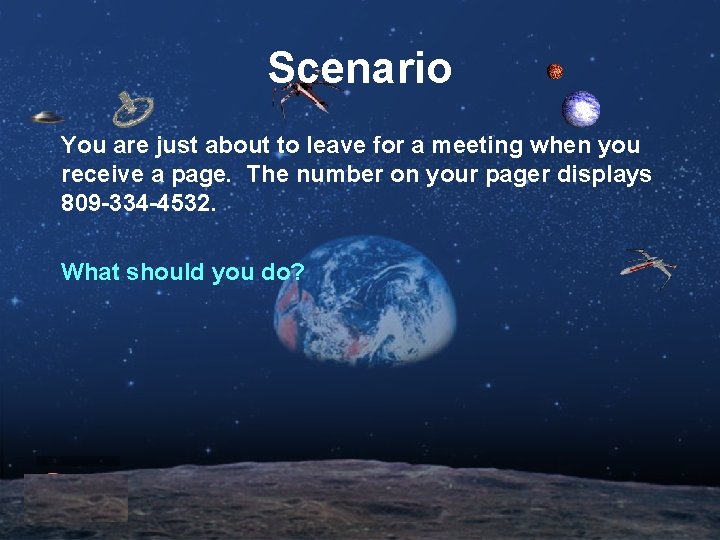
Scenario You are just about to leave for a meeting when you receive a page. The number on your pager displays 809 -334 -4532. What should you do?

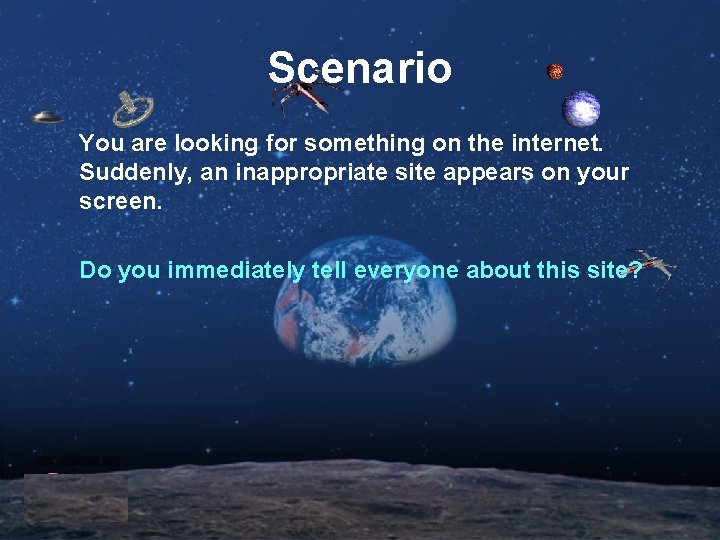
Scenario You are looking for something on the internet. Suddenly, an inappropriate site appears on your screen. Do you immediately tell everyone about this site?

Security Contest

If not you, who? If not now, when? Remember in SEC-U-R-IT-Y