Nexthink V 5 Demo Security Malicious Anomaly Situation




- Slides: 33

Nexthink V 5 Demo Security – Malicious Anomaly

Situation › › Avoid damage resulting from the incident itself and the cost of the unplanned response Protection is not enough anymore to deal with advanced targeted malware detection and prevention • By 2018, 80% of endpoint protection platforms will include user activity monitoring, analytics and forensic capabilities, up from less than 5% in 2013 (Source: Prevention Is Futile in 2020: Protect Information Via Pervasive Monitoring and Collective Intelligence, 30 May 2013, ID G 00252476, by Neil Mac. Donald)

Solution › › Add behavior and anomaly detection to uncover risky activity and compromised devices Need to deal with a mix of malware, negligence and technology glitches. It’s all about 360 degrees insight all the time to: • Quickly mitigates the risks of employees' malware infected PCs. Nexthink automatically analyzes the local and network activity to find PCs that connect to rogue destinations that aren't typical • Become aware early enough about suspicious activity, misused systems, privileges abuse or careless behaviors before it turns into damaging attacks or activities • Validate if appropriate configurations and policies remain enforced overtime

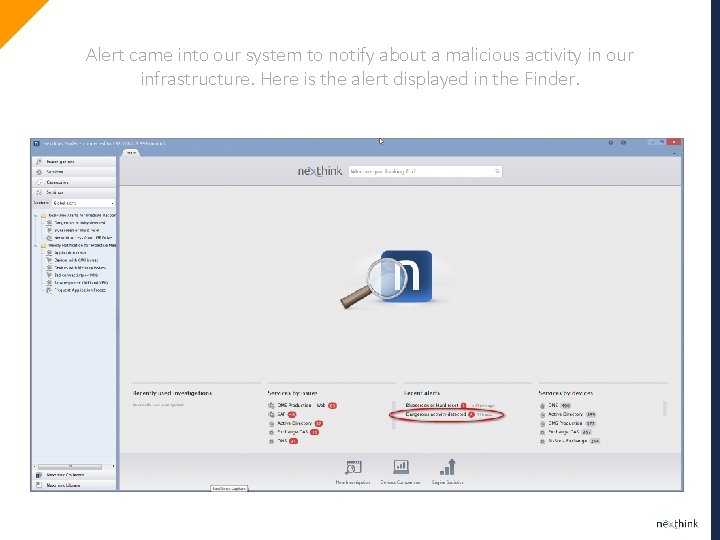
Alert came into our system to notify about a malicious activity in our infrastructure. Here is the alert displayed in the Finder.

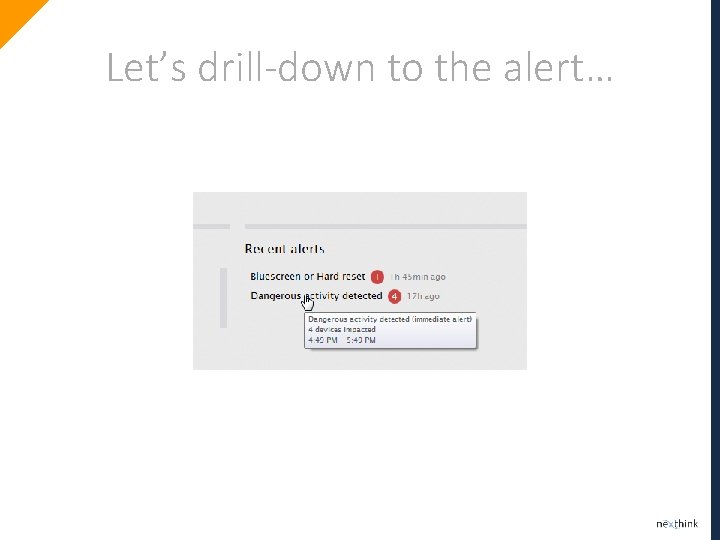
Let’s drill-down to the alert…

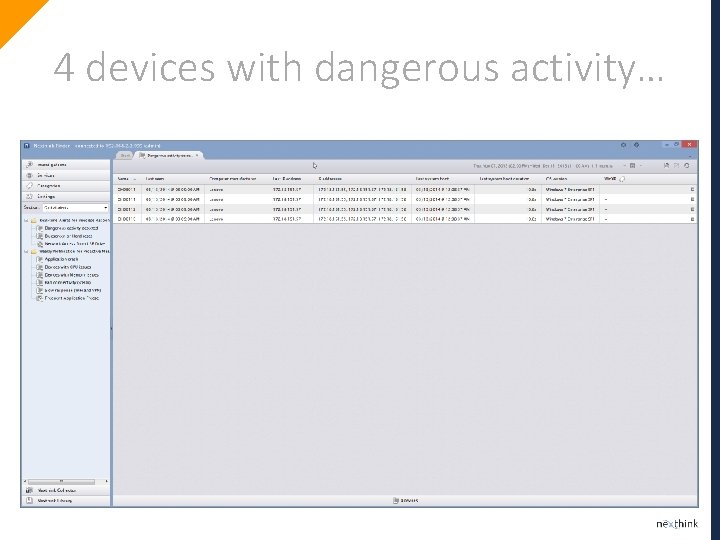
4 devices with dangerous activity…

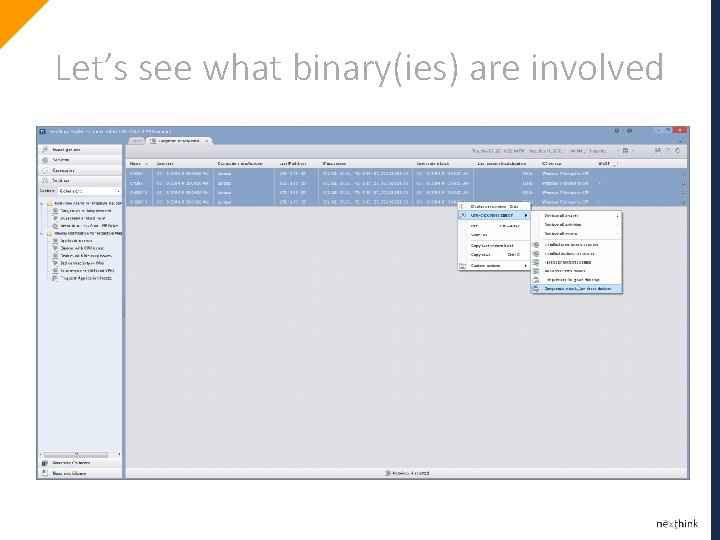
Let’s see what binary(ies) are involved

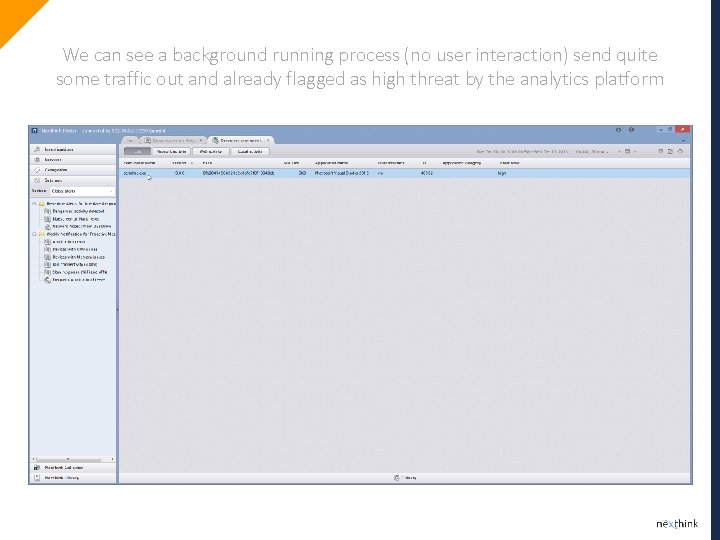
We can see a background running process (no user interaction) send quite some traffic out and already flagged as high threat by the analytics platform

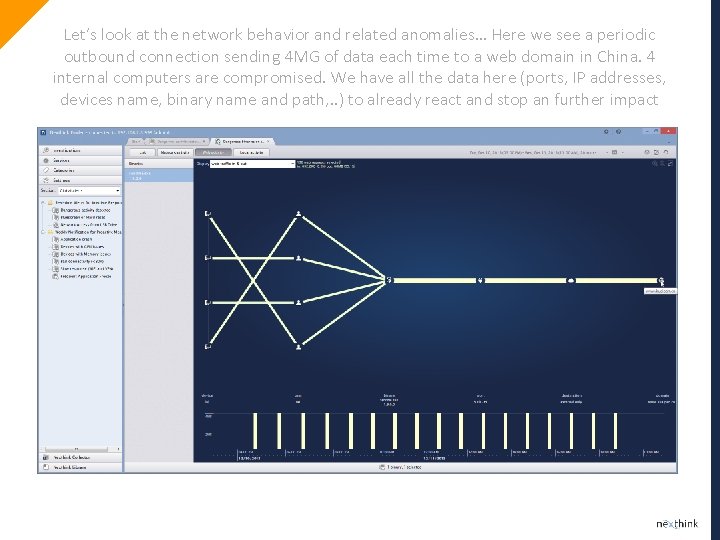
Let’s look at the network behavior and related anomalies… Here we see a periodic outbound connection sending 4 MG of data each time to a web domain in China. 4 internal computers are compromised. We have all the data here (ports, IP addresses, devices name, binary name and path, . . ) to already react and stop an further impact

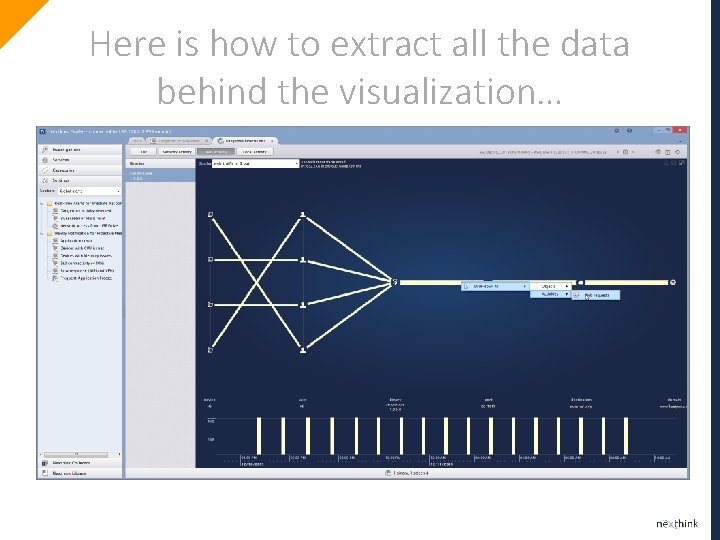
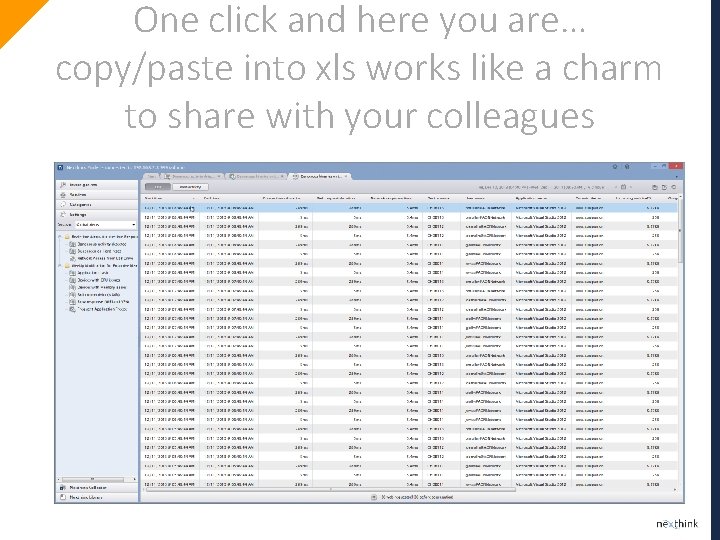
Here is how to extract all the data behind the visualization…

One click and here you are… copy/paste into xls works like a charm to share with your colleagues

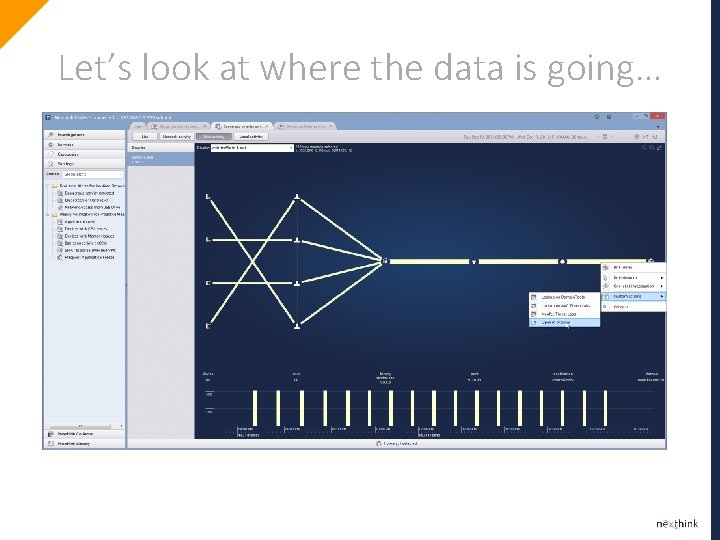
Let’s look at where the data is going…

Oh the Chineese dropbox-like service…

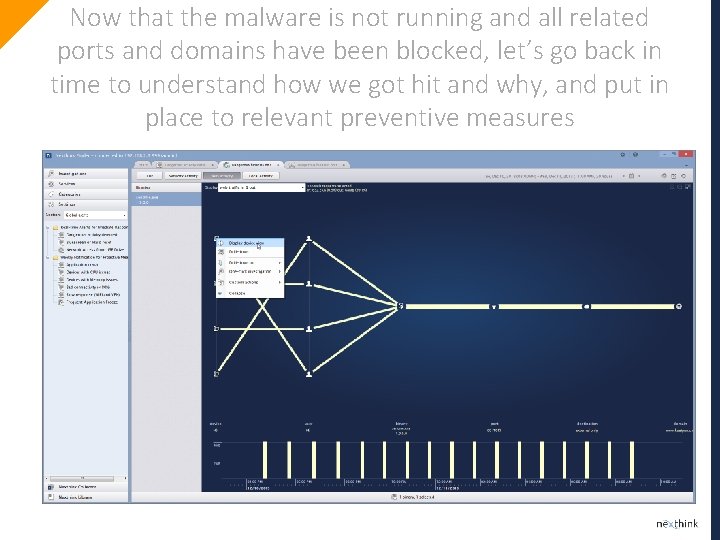
Now that the malware is not running and all related ports and domains have been blocked, let’s go back in time to understand how we got hit and why, and put in place to relevant preventive measures

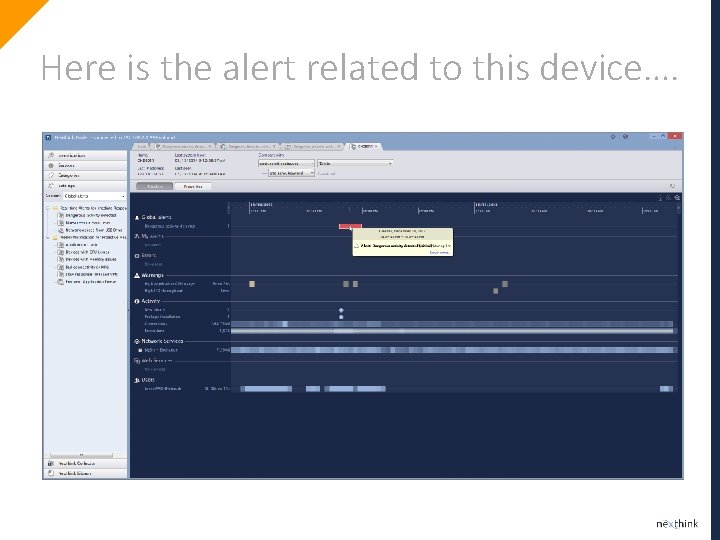
Here is the alert related to this device….

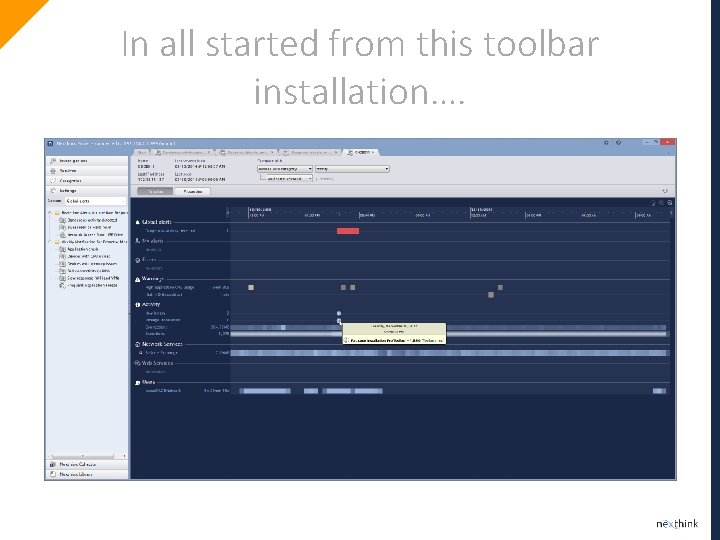
In all started from this toolbar installation….

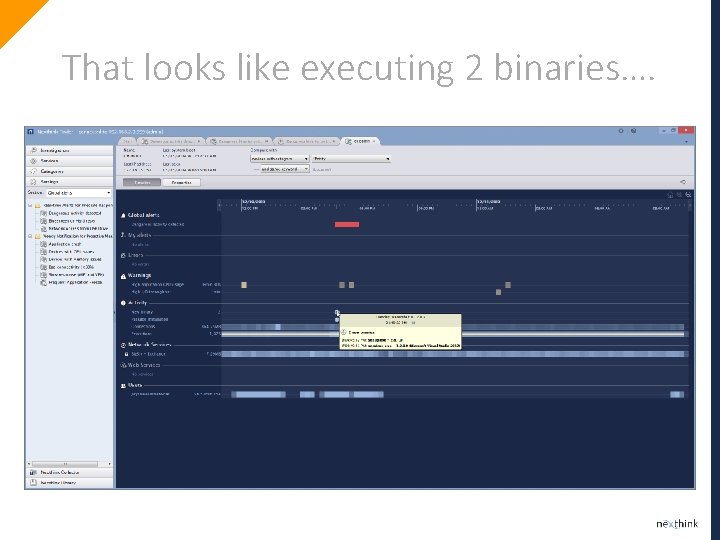
That looks like executing 2 binaries….

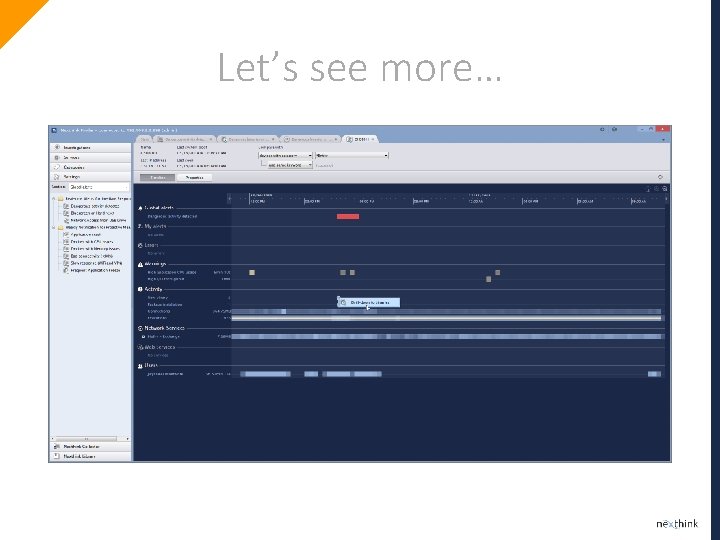
Let’s see more…

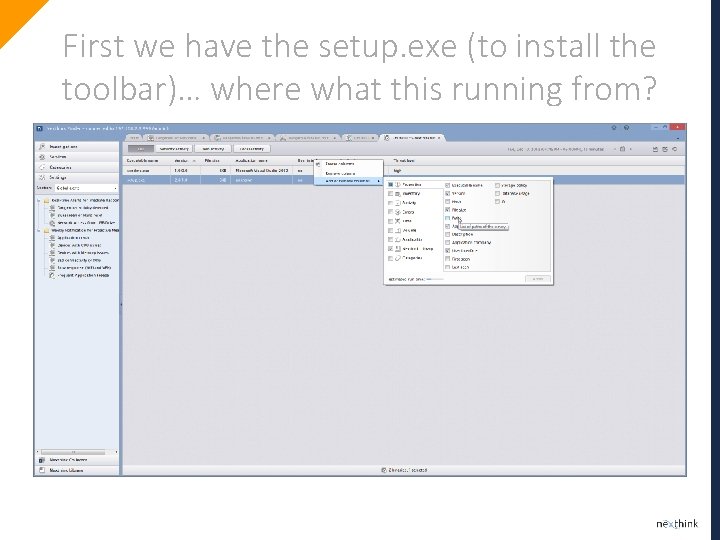
First we have the setup. exe (to install the toolbar)… where what this running from?

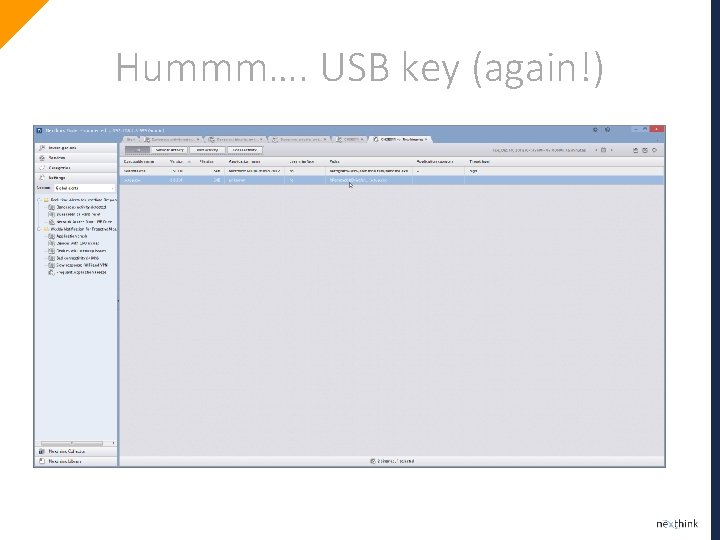
Hummm…. USB key (again!)

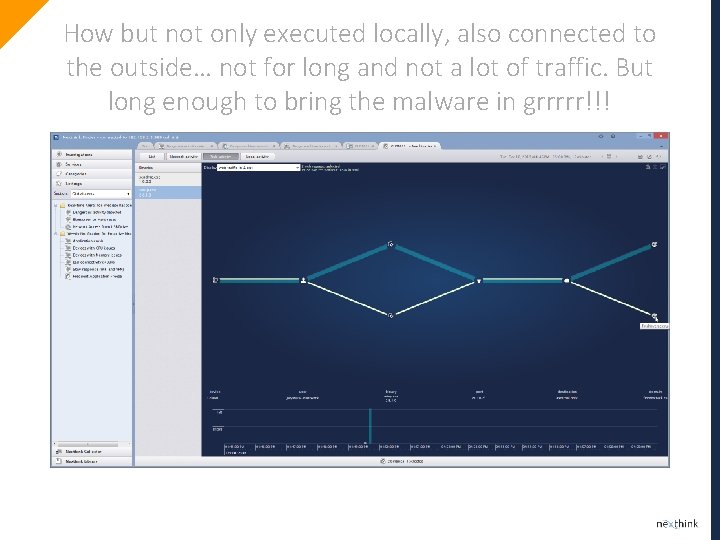
How but not only executed locally, also connected to the outside… not for long and not a lot of traffic. But long enough to bring the malware in grrrrr!!!

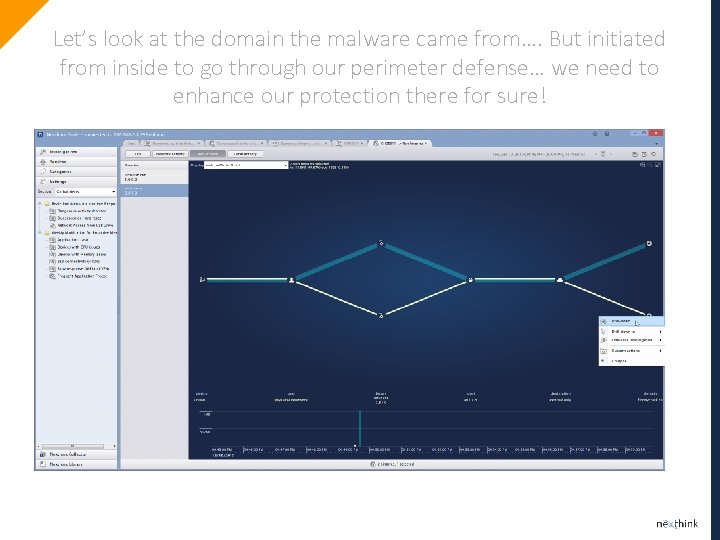
Let’s look at the domain the malware came from…. But initiated from inside to go through our perimeter defense… we need to enhance our protection there for sure!

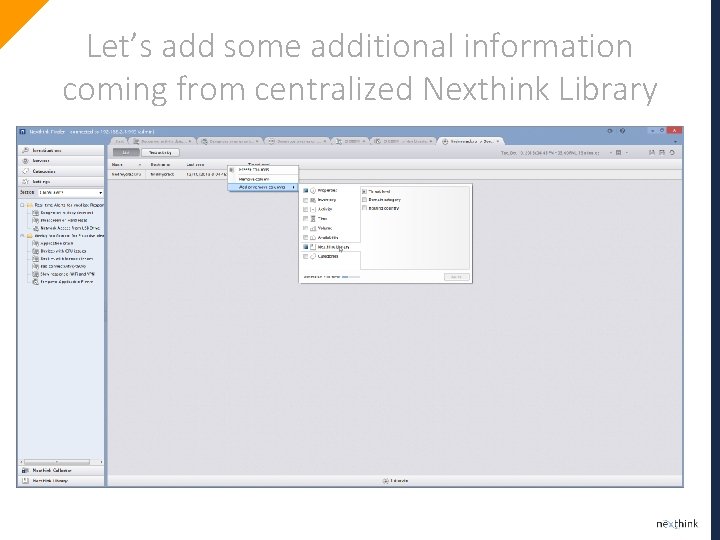
Let’s add some additional information coming from centralized Nexthink Library

That’s a web site you don’t want to connect Let’s also block it!

Curious why our endpoint security did not detect and block this activity and malware code…. Let’s see how the AV, Anti-Spyware configured and up to date… We might have a hole there….

Let’s select the security compliance checks I want to make…

Here are the 4 infected machines… with all protection in place and well running….

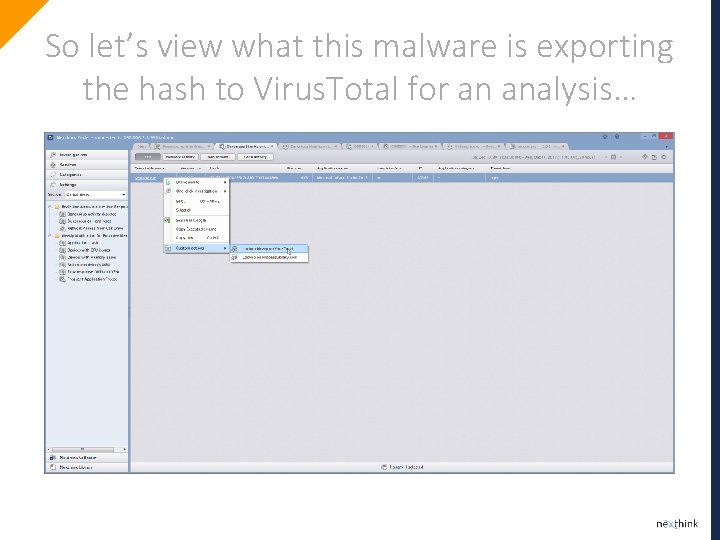
So let’s view what this malware is exporting the hash to Virus. Total for an analysis…

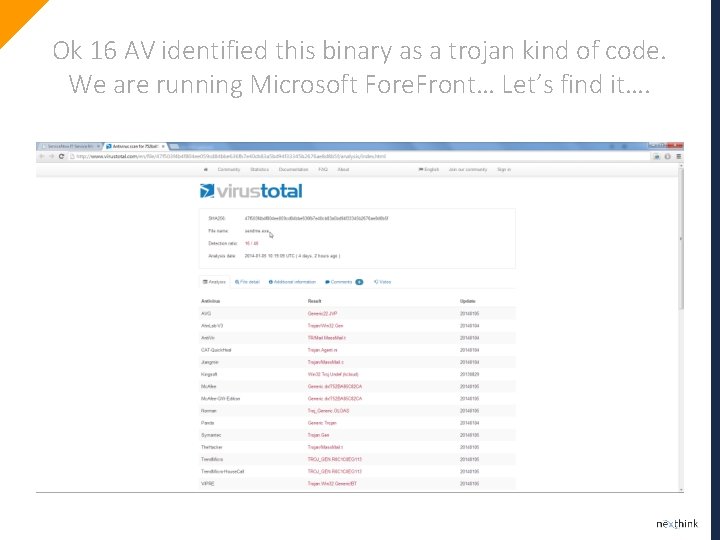
Ok 16 AV identified this binary as a trojan kind of code. We are running Microsoft Fore. Front… Let’s find it….

Here it is…. Ok got it… No luck this time… Thanks we did not only rely on protection but had real-time activity monitoring and anomaly analytics otherwise I don’t know him much date would have gone out from how many computers

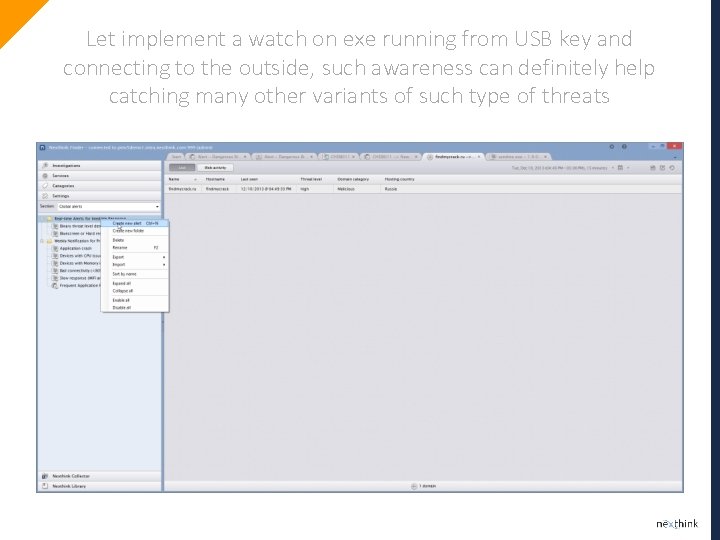
Let implement a watch on exe running from USB key and connecting to the outside, such awareness can definitely help catching many other variants of such type of threats

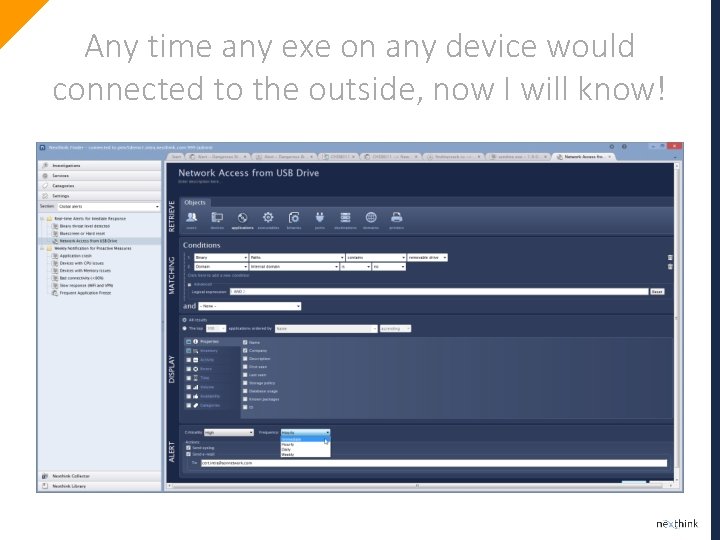
Any time any exe on any device would connected to the outside, now I will know!

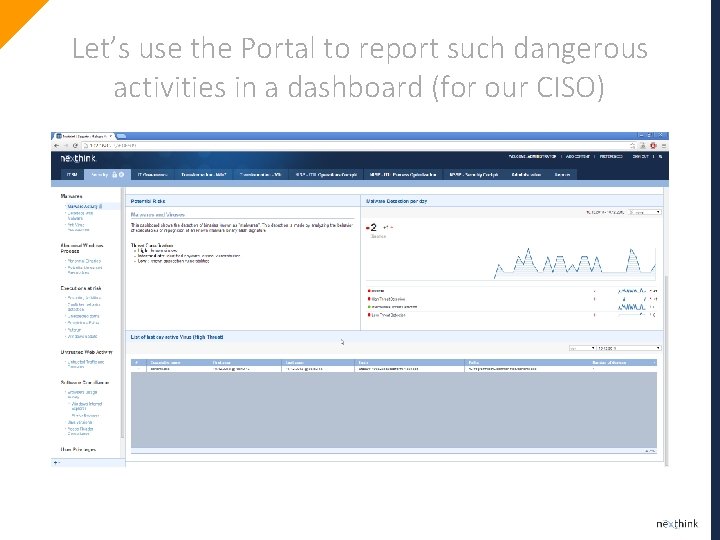
Let’s use the Portal to report such dangerous activities in a dashboard (for our CISO)