Next Generation IC Card System Yukako Yagi University





- Slides: 24

Next Generation IC Card System Yukako Yagi University of Pittsburgh Medical Center, Pittsburgh, PA, USA Nagaaki OHYAMA Prof. of Frontier collaborative research center, Tokyo Institute of Technology, Tokyo, Japan C Copyright 次世代ICカードシステム研究会 1

Back ground in Japan • “e-Japan strategy” was issued on March, 2001 – Private sector’s initiative – Government provided groundwork – International harmonization • e-Japan strategy ; e-government by 2003 leading country by 2005 • These 3 principles were established in 1998. In reality, however, more depressed economy supplementary budget public sector e-government ( EC again ) EC: all economical activities in the cyberspace C Copyright 次世代ICカードシステム研究会 2

Back ground (2) • “e-Japan strategy II” was issued in June, 2003, because main objectives are almost accomplished; 1. Broadband for 30 M families, 2. Optical fibers for 10 M families, 3. Government provided ground-works for a realization of egovernment such as personal authentication law • “e-Japan strategy II” focuses on 7 practical applications such as e-government and healthcare C Copyright 次世代ICカードシステム研究会 3

Back Ground (3) • For secure e-government services through internet, smart card is officially defined as an interface between private and public sectors – The primary card (Res. Reg. card) is being financially supported by the government (1000 JPY for all) • Primary applications under plan are – Resident registration card e. ID – Personal authentication card digital signature – Health insurance card Health card Note: these applications would be merged into one card, if the card holder agrees. If not, they may use an additional card at their own cost. C Copyright 次世代ICカードシステム研究会 4

System Security • Conventional technology; ex. Financial system – Dedicated information system – Using dedicated communication line, dedicated terminals and encryption algorithm, etc. – System specifications are classified • New technology for Ubiquitous age Open & P 2 P – End to end mutual authentication and encrypted communication – Encryption algorithms are open objective assessment – Encryption keys shall be securely managed and used just like metal keys of home, office, etc. smart card C Copyright 次世代ICカードシステム研究会 5

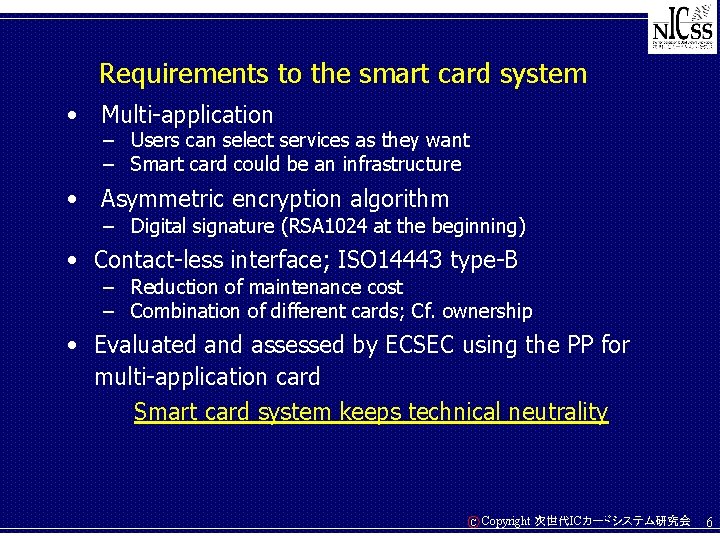
Requirements to the smart card system • Multi-application – Users can select services as they want – Smart card could be an infrastructure • Asymmetric encryption algorithm – Digital signature (RSA 1024 at the beginning) • Contact-less interface; ISO 14443 type-B – Reduction of maintenance cost – Combination of different cards; Cf. ownership • Evaluated and assessed by ECSEC using the PP for multi-application card Smart card system keeps technical neutrality C Copyright 次世代ICカードシステム研究会 6

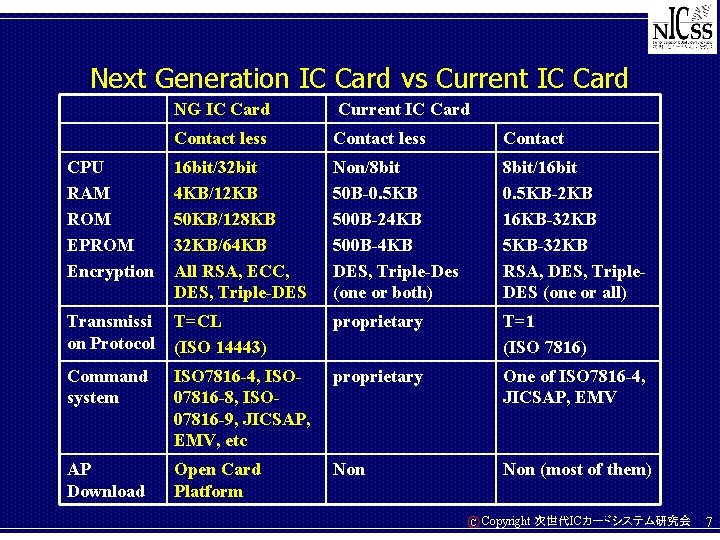
Next Generation IC Card vs Current IC Card NG IC Card Current IC Card Contact less Contact CPU RAM ROM EPROM Encryption 16 bit/32 bit 4 KB/12 KB 50 KB/128 KB 32 KB/64 KB All RSA, ECC, DES, Triple-DES Non/8 bit 50 B-0. 5 KB 500 B-24 KB 500 B-4 KB DES, Triple-Des (one or both) 8 bit/16 bit 0. 5 KB-2 KB 16 KB-32 KB 5 KB-32 KB RSA, DES, Triple. DES (one or all) Transmissi on Protocol T=CL (ISO 14443) proprietary T=1 (ISO 7816) Command system ISO 7816 -4, ISO 07816 -8, ISO 07816 -9, JICSAP, EMV, etc proprietary One of ISO 7816 -4, JICSAP, EMV AP Download Open Card Platform Non (most of them) C Copyright 次世代ICカードシステム研究会 7

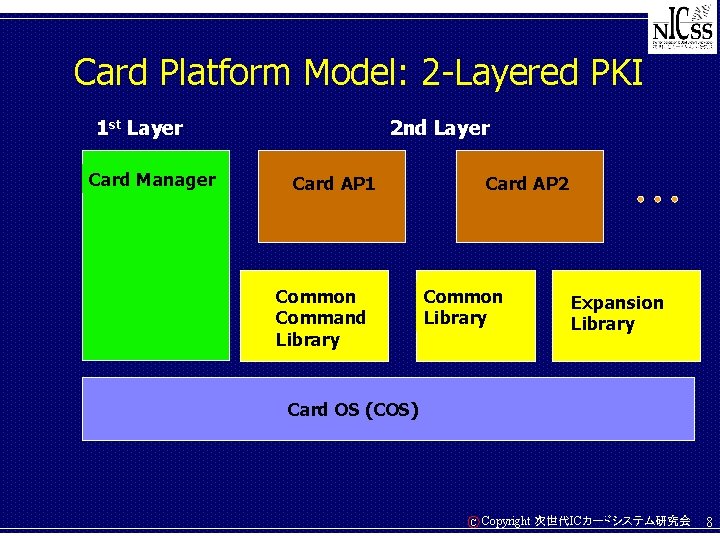
Card Platform Model: 2 -Layered PKI 1 st Layer Card Manager 2 nd Layer Card AP 1 Common Command Library Card AP 2 Common Library Expansion Library Card OS (COS) C Copyright 次世代ICカードシステム研究会 8

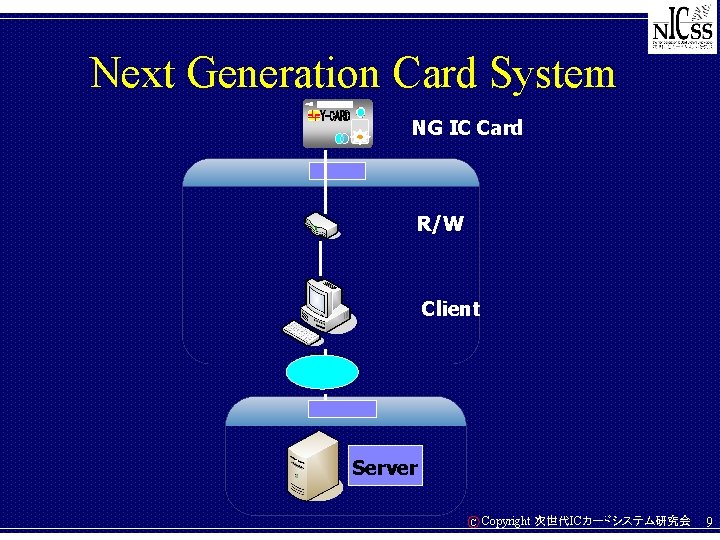
Next Generation Card System NG IC Card R/W Client Server C Copyright 次世代ICカードシステム研究会 9

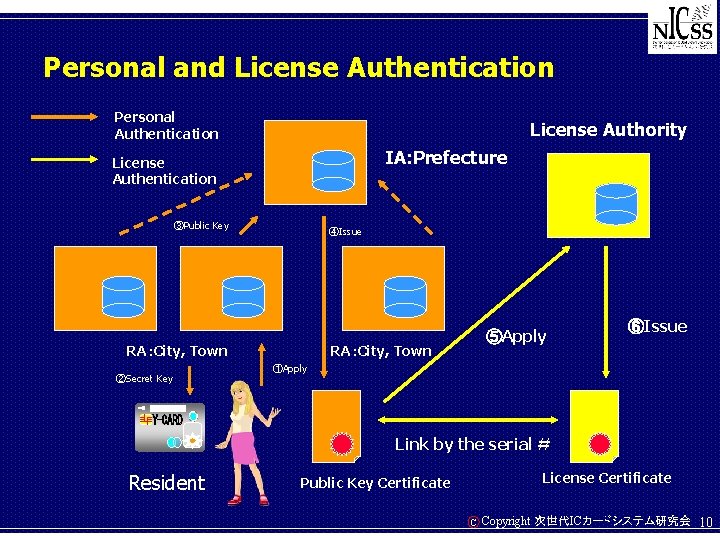
Personal and License Authentication Personal Authentication License Authority IA: Prefecture License Authentication ③Public Key ④Issue RA:City, Town ②Secret Key ⑤Apply RA:City, Town ⑥Issue ①Apply Link by the serial # Resident License Certificate Public Key Certificate C Copyright 次世代ICカードシステム研究会 10

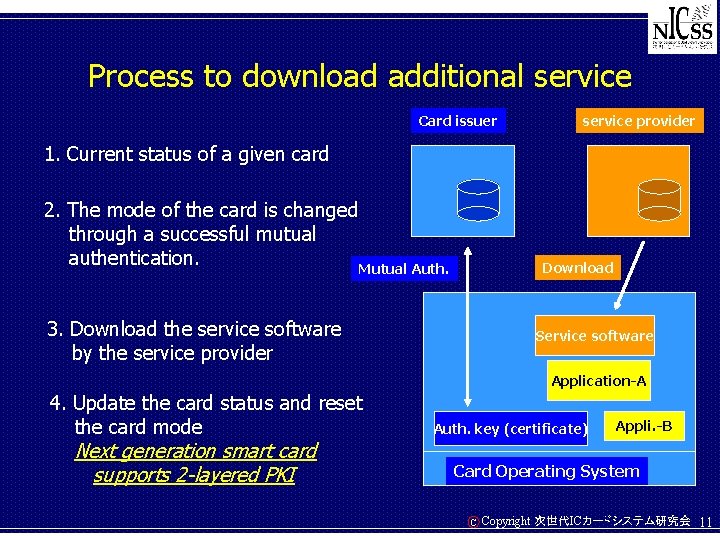
Process to download additional service Card issuer service provider 1. Current status of a given card 2. The mode of the card is changed through a successful mutual authentication. Mutual Auth. Download 3. Download the service software by the service provider Service software Application-A 4. Update the card status and reset the card mode Next generation smart card supports 2 -layered PKI Auth. key (certificate) Appli. -B Card Operating System C Copyright 次世代ICカードシステム研究会 11

Additional items to be standardized 1. Download process ⇒ NP to SC 17 • Mutual authentication process to change the card mode; to accept and reject enhanced system commands such as creating/deleting file, checking the free memory size, getting a list of application IDs on the card • Exchange scheme of session keys to establish a secure communication with card 2. Compact certificate other than X. 50 x ⇒ not yet • Mutual authentication between card and terminals • Limited use of card and terminal certificates C Copyright 次世代ICカードシステム研究会 12

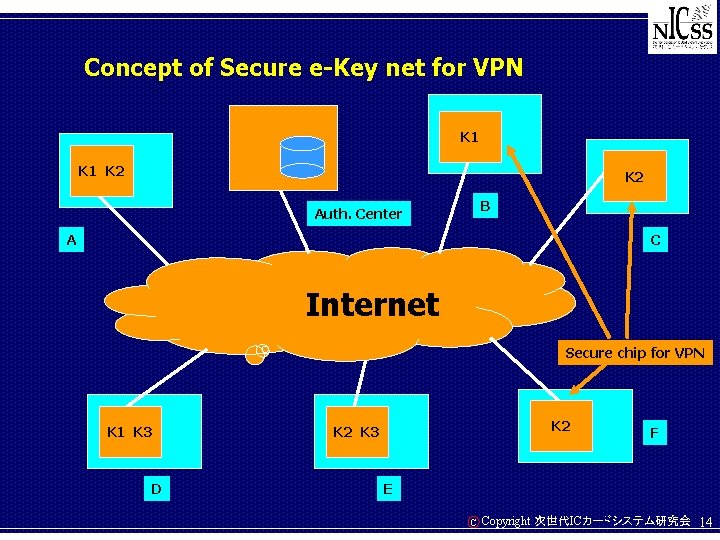
Next action using secure IC chip – About VPN • VPN is widely used for so called intranet • VPN usually requires a key setup procedure in a manual way – About secure IC chip • The price of the next generation secure chip is reduced down to 3 US$ • This chip is compliant to international standards • This chip supports mutual authentication through 2 -layered PKI • The e-key delivery could be securely managed by the NICSS frame work using 2 -layered PKI scheme – Combination • VPN with secure IC chip does not need manual key setup • R and D project started this year and it is named “Secure e-Key net” C Copyright 次世代ICカードシステム研究会 13

Concept of Secure e-Key net for VPN K 1 K 2 B Auth. Center A C Internet Secure chip for VPN K 1 K 3 D K 2 K 3 F E C Copyright 次世代ICカードシステム研究会 14

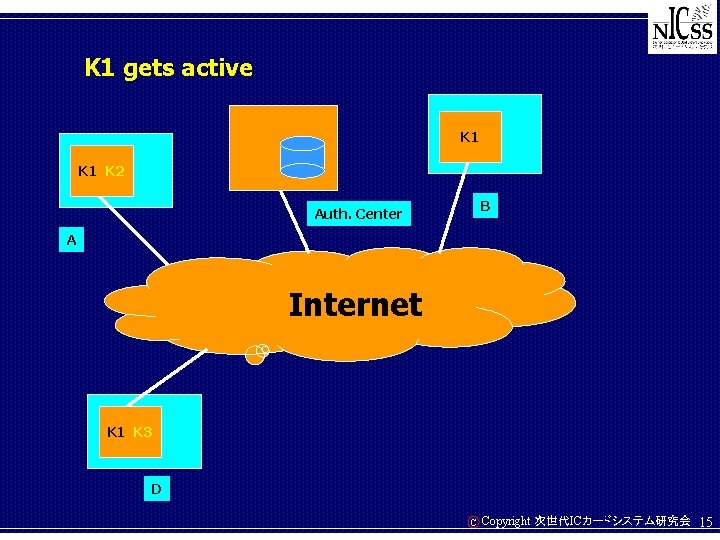
K 1 gets active K 1 K 2 B Auth. Center A Internet K 1 K 3 D C Copyright 次世代ICカードシステム研究会 15

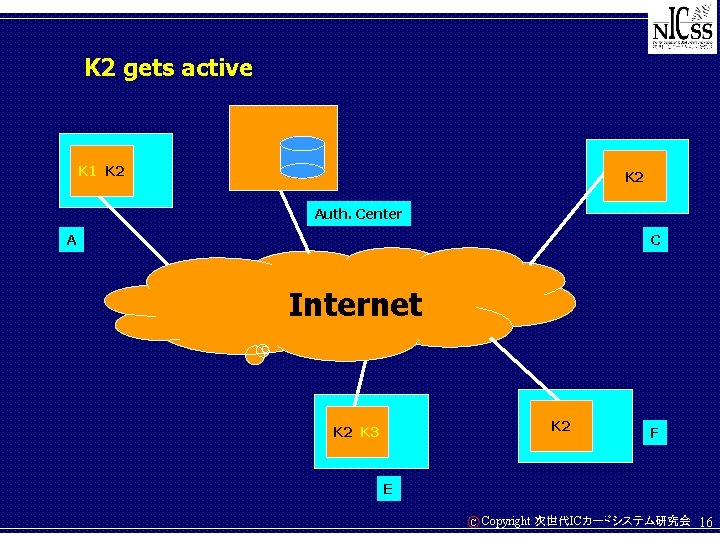
K 2 gets active K 1 K 2 Auth. Center A C Internet K 2 K 3 F E C Copyright 次世代ICカードシステム研究会 16

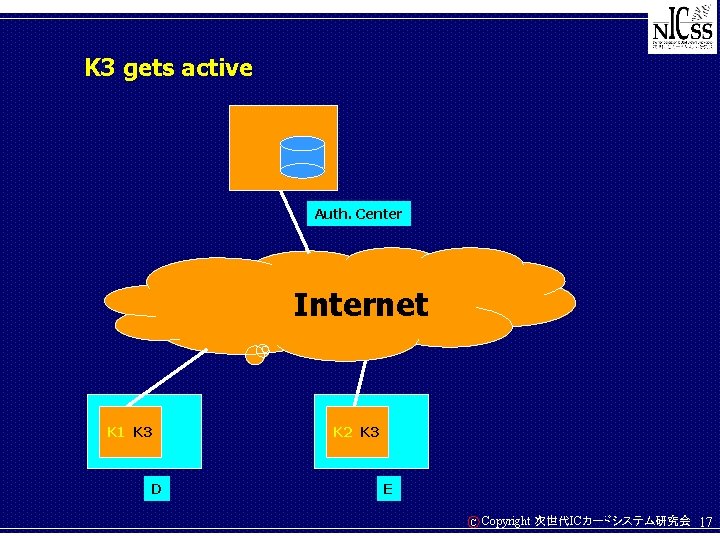
K 3 gets active Auth. Center Internet K 1 K 3 D K 2 K 3 E C Copyright 次世代ICカードシステム研究会 17

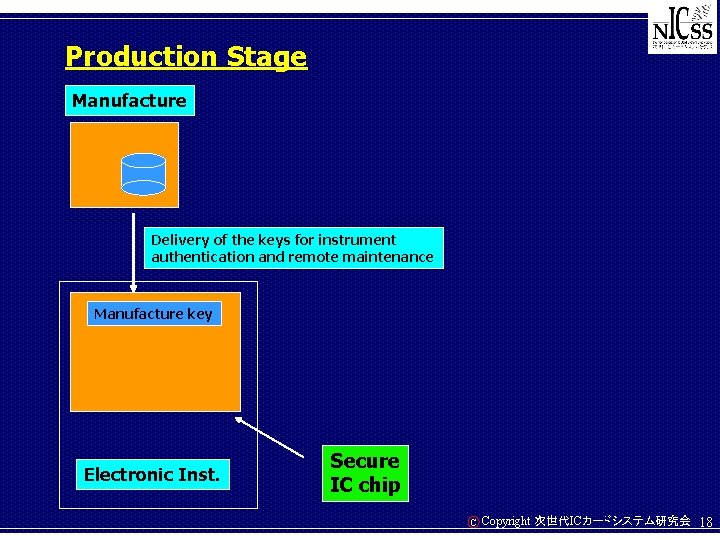
Production Stage Manufacture Delivery of the keys for instrument authentication and remote maintenance Manufacture key Electronic Inst. Secure IC chip C Copyright 次世代ICカードシステム研究会 18

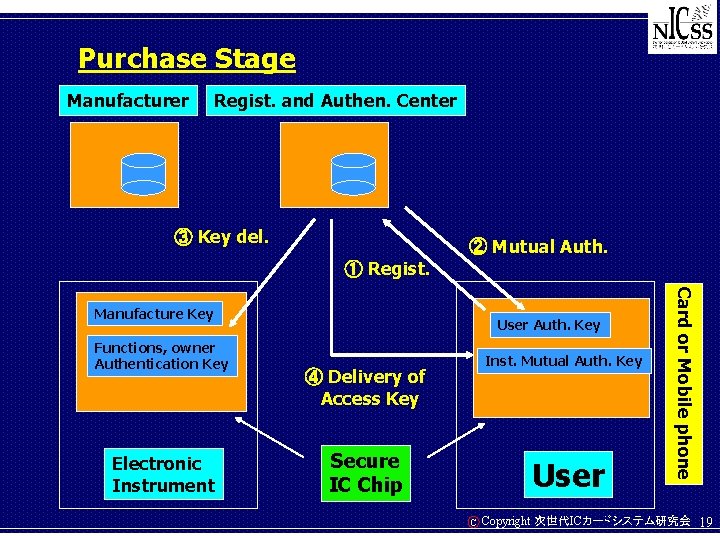
Purchase Stage Manufacturer Regist. and Authen. Center ③ Key del. ② Mutual Auth. ① Regist. Functions, owner Authentication Key Electronic Instrument User Auth. Key Inst. Mutual Auth. Key ④ Delivery of Access Key Secure IC Chip User C Card or Mobile phone Manufacture Key Copyright 次世代ICカードシステム研究会 19

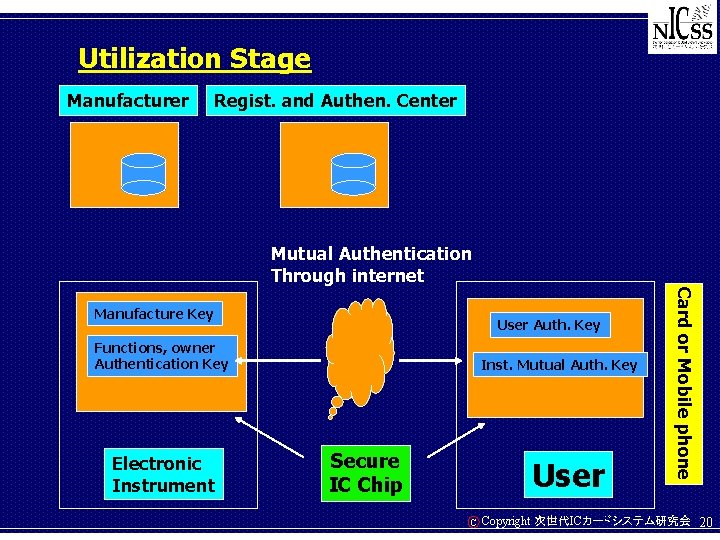
Utilization Stage Manufacturer Regist. and Authen. Center Mutual Authentication Through internet User Auth. Key Functions, owner Authentication Key Electronic Instrument Inst. Mutual Auth. Key Secure IC Chip User C Card or Mobile phone Manufacture Key Copyright 次世代ICカードシステム研究会 20

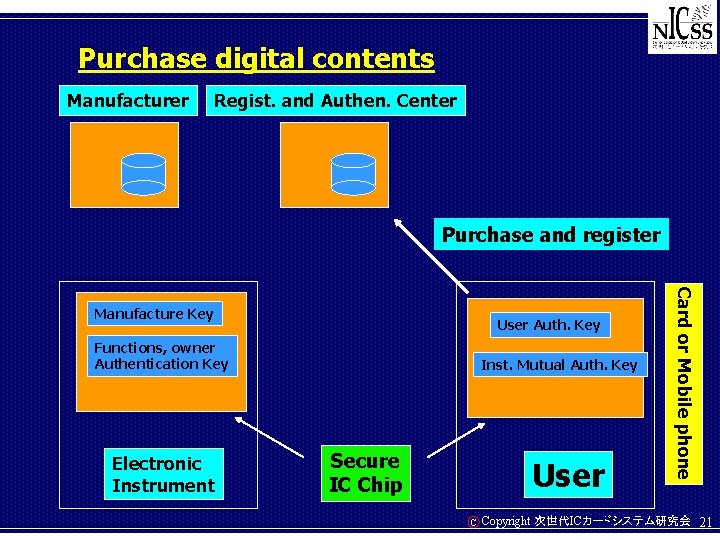
Purchase digital contents Manufacturer Regist. and Authen. Center Purchase and register User Auth. Key Functions, owner Authentication Key Electronic Instrument Inst. Mutual Auth. Key Secure IC Chip User C Card or Mobile phone Manufacture Key Copyright 次世代ICカードシステム研究会 21

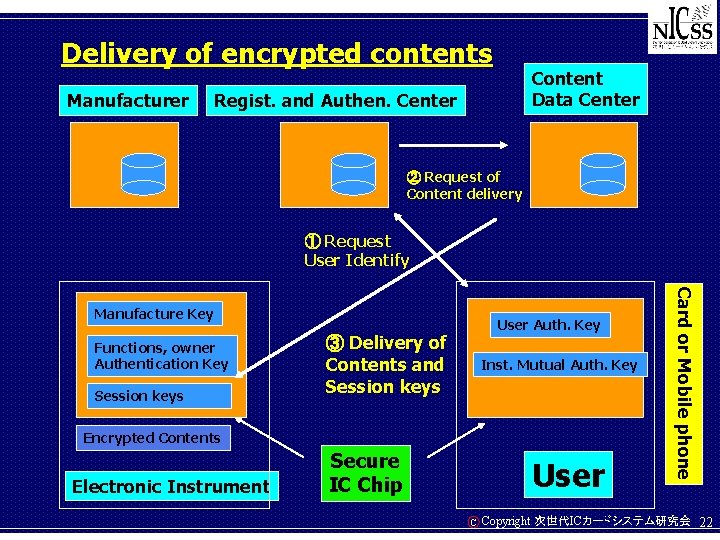
Delivery of encrypted contents Manufacturer Content Data Center Regist. and Authen. Center ② Request of Content delivery ① Request User Identify Functions, owner Authentication Key Session keys User Auth. Key ③ Delivery of Contents and Session keys Inst. Mutual Auth. Key Encrypted Contents Electronic Instrument Secure IC Chip User C Card or Mobile phone Manufacture Key Copyright 次世代ICカードシステム研究会 22

Applications for Telemedicine – Firewall issues – HIPPA issues – Especially, Network Medical Equipments are on the market – Network Medical Equipments are low cost, less maintenance required and easy to control remotely – not allowed to connect current network because of security issue Using the combination of Next Generation IC Card system, we can solve the problem. Trial experiment to proof the security between UPMC and Tokyo Institute of Technology will be started in Nov, 2004 C Copyright 次世代ICカードシステム研究会 23

Summary – Smart Card is the key technology for secure environment in the cyber space – Contact-less Smart card will be the second infrastructure in Japan and new businesses are highly expected to emerge – Japanese government has started to procure 3 M cards this year and more than 10 M a year from next year – All requirements to and specifications of resident registration card are open to public except for secret keys – Res. Reg. card was already under practical use from 25, Aug. 2003. – Access rights to the internet-connected devices as well as digital contents need to be authorized as attributes of each user. C Copyright 次世代ICカードシステム研究会 24