New Protocols for Asymmetric Communication Channels Presented by

New Protocols for Asymmetric Communication Channels Presented by Nick Farnan 11 -11 -08

Asymmetric Communications Setup: Client needs to send server an n-length bit string x The communication channel to send from server to client has much greater bandwidth than the one from client to server The server knows D, the distribution of probabilities of receiving any give n-length bit string from the client (Note that the client has no knowledge of D)

Asymmetric Communications In his “A Mathematical Theory of Communication”, Shannon provided a limit to the amount of lossless compression of any communication with Shannon entropy Entropy is defined to be a measure of uncertainty in a random variable (in this case a bit string) A repeating string (i. e. “ 00000. . . ”) has minimal entropy as it is completely predictable, while a random bit string (could be any bit string of length n with equal probability) has maximum entropy

Asymmetric Communications From this, we can draw the conclusion that the absolute minimum expected number of bits that the client will have to send to the server to describe x to the server is the entropy of x, H(x)

Asymmetric Communications Consider a list of all n length bit string ordered from least to greatest Let F(x) be the sum of D(y) for all y < x Let F'(x) = F(x) + 1/2(D(x)) Given a real number v in the range (0, 1], a bit string y is considered to be a v-split string if it is the largest n bit string such that F'(y) <= v
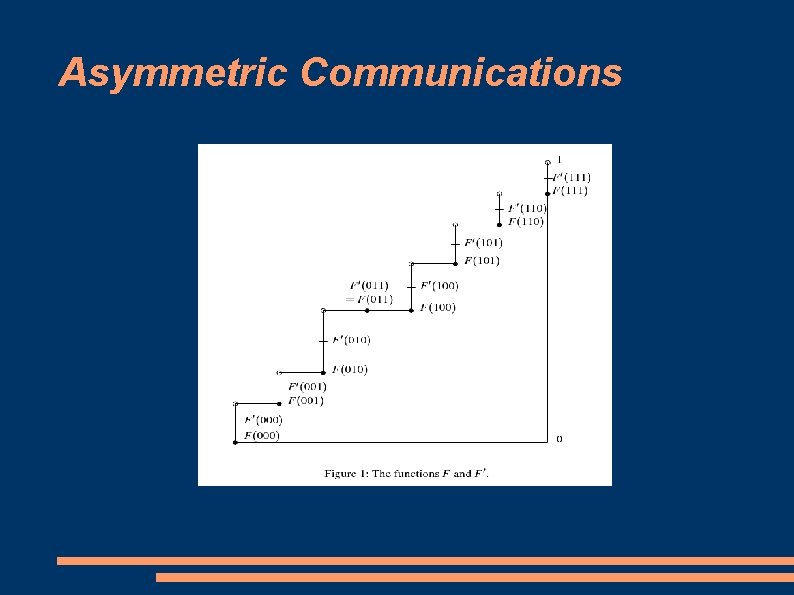
Asymmetric Communications

Split-String Algorithm
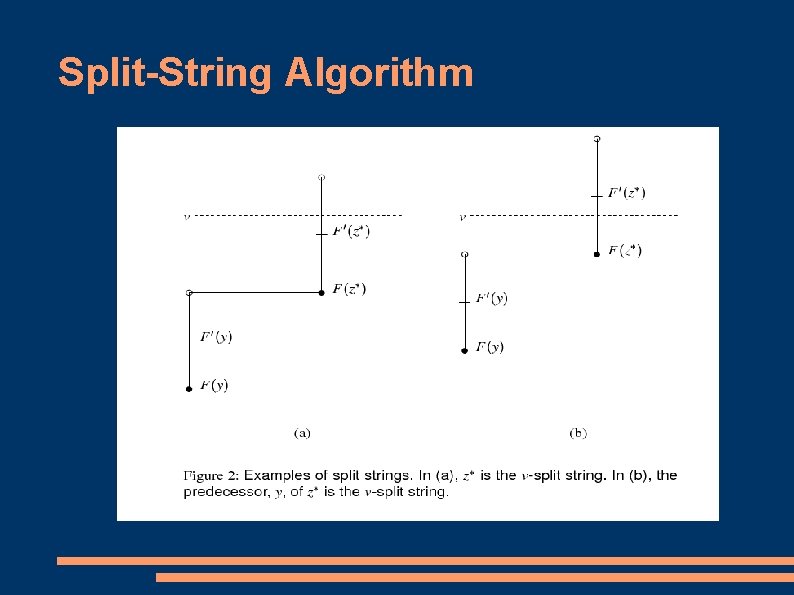
Split-String Algorithm

Bit-Efficient-Split By using split strings, the server can do a sort of binary search through the space of n bit strings to determine the string x that the client wishes to send.

Bit-Efficient-Split

Bit-Efficient-Split Fact: F'(x) is the midpoint of the interval (F(x), F(x) + D(x)) After m rounds, given that D(x) >= 2^(1 -m), and that F'(x) is contained within (um, vm), at the end of the current round, y == x == z, and hence the string has been discovered! Hence, if it takes at most m+1 rounds to discover the string being sent, the client m+1 bits indicating which side of the split string the x falls on

Bit-Efficient-Split Now, as: m+1 = ceil(lg(1/D(x)))+1 <= lg(1/D(x))+2 The expected number of rounds can be bounded by the sum over all x of: D(x) * (lg(1/D(x)) + 2 =sum(D(x) * lg(1/D(x))) + 2 =H(D) + 2 A constant factor from optimal!

Asymmetric Communication Protocols via Hotlink Assignments Presented by Nick Farnan 11 -11 -08

The Hotlinking Problem Proposed for the Web to make particular pages on a site more accessible Given a rooted tree where each leaf has a probability attached to it (let D be the distribution of these probabilities), the Hotlinking problem moves subtrees up the tree closer to to the root in order to minimize the cost of the tree as a whole.

The Hotlinking Problem Definitions: c(u) is the sum of all of the probabilities of the leaves of the subtree rooted at node u, this is the cost of u c(u, v) where u is the parent of v, is c(v), this is the cost of edge u-v d(u, T) is the length of the path from the root of T to u c(T) is the sum of the costs of all the edges in tree T L(T) is the set of leaves of T

The Hotlinking Problem Adoption A node u can adopt one of its decedents (w) by removing w from it's parents list of children and adding it instead to u's list of children

The Hotlinking Problem A k-hotlink-assignment of T is obtained by performing up to k adoptions (where k is some integer) at the root of T, creating T 1, and the further find a k-hotlink-assignment for each subtree of T 1 that is a child of the root. This problem has been show to be generalized as: at each node u, adopt a its descendants until all descendants of u are either leaves or have a cost <= (2/(k+2)) * c(u)

The Hotlinking Problem The resulting tree will have a cost of at most: (H/(lg(k + 2) – 1)) + 1, where H is the entropy of D, the distribution of the leaves

Hotlinking in Asymmetric Communications Let T be a complete binary tree with 2 n leaves (where n is the length of the string being sent from client to server) and a label on each edge such that all edges leading to left children have the label 0 and all the right are labeled 1 Each vertex is then labeled with its path from the root (i. e. going left, right then left from the root would lead to a node labelled “ 010”)

Hotlinking in Asymmetric Communications Both client and server maintain r 1 and r 2 where r 1~r 2 is the string r that the client wishes to send. Initially, r 1 is set to empty and the server does not know r 2 Find T', the k-hotlink-assignment of T For each round of the protocol, the server considers all of the children (w) of node u in T whose label is r 1, and send to the client all l where l is label(w) - r 1

Hotlinking in Asymmetric Communications The client then replies with the index in the last server message of the longest l that is a prefix of r 2 The client then removes l from the beginning of r 2, and both client and server add l to r 1 If |r 1| == n, the server outputs r 1 and the communication terminates

Hotlinking in Asymmetric Communications The client can then be expected to send c(T') * ceil(lg(k + 2)) Given that c(T') = (H/(lg(k + 2) – 1)) + 1, the client can then be expected to send H*(ceil(lg(k+2))/(lg(k+2)-1)) + ceil(lg(k+2)) bits setting e = (ceil(lg(k+2))/(lg(k+2)-1)) – 1, and ce = ceil(lg(k+2)), then, a protocol where client is expected to send (1+e)H + ce bits is achieved
- Slides: 22