Networking Overview Introduction 1 Introduction 2 Whats a













- Slides: 64

Networking Overview Introduction 1

Introduction 2

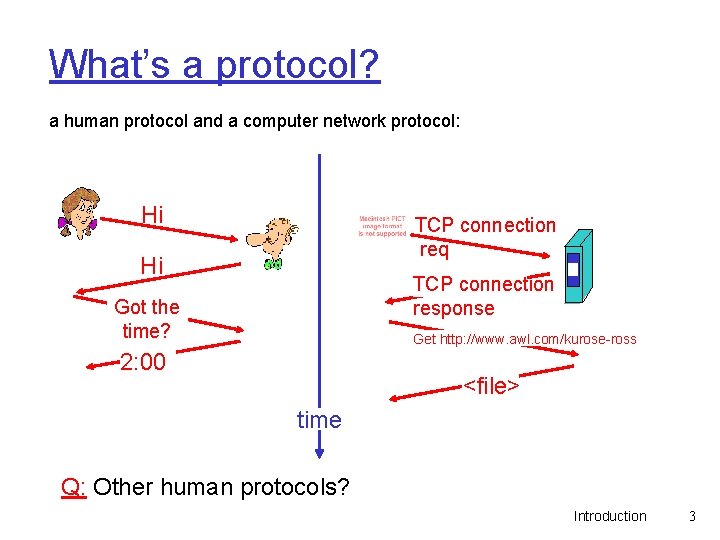
What’s a protocol? a human protocol and a computer network protocol: Hi TCP connection req Hi TCP connection response Got the time? Get http: //www. awl. com/kurose-ross 2: 00 <file> time Q: Other human protocols? Introduction 3

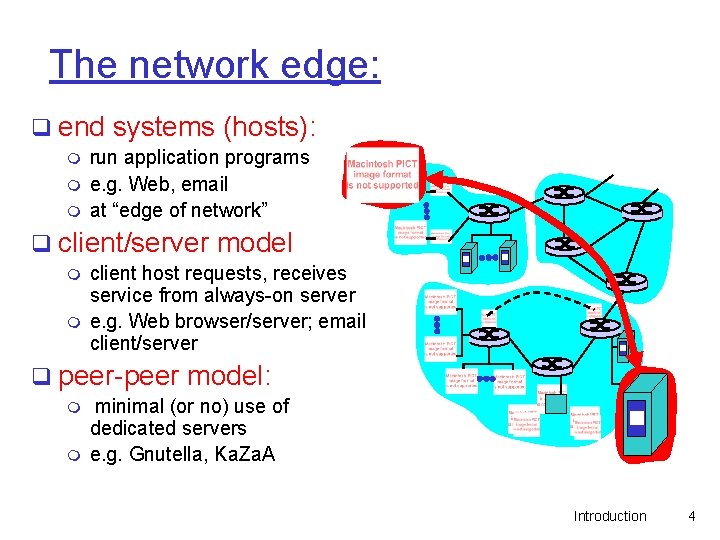
The network edge: q end systems (hosts): m m m run application programs e. g. Web, email at “edge of network” q client/server model m m client host requests, receives service from always-on server e. g. Web browser/server; email client/server q peer-peer model: m m minimal (or no) use of dedicated servers e. g. Gnutella, Ka. Za. A Introduction 4

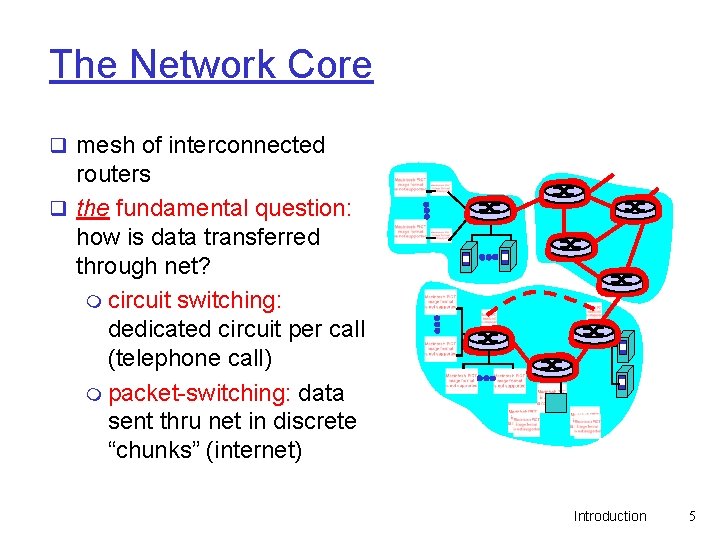
The Network Core q mesh of interconnected routers q the fundamental question: how is data transferred through net? m circuit switching: dedicated circuit per call (telephone call) m packet-switching: data sent thru net in discrete “chunks” (internet) Introduction 5

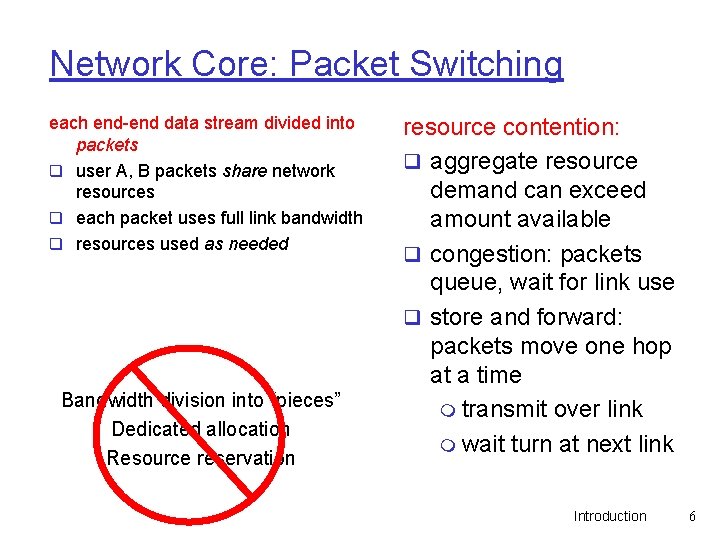
Network Core: Packet Switching each end-end data stream divided into packets q user A, B packets share network resources q each packet uses full link bandwidth q resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation resource contention: q aggregate resource demand can exceed amount available q congestion: packets queue, wait for link use q store and forward: packets move one hop at a time m transmit over link m wait turn at next link Introduction 6

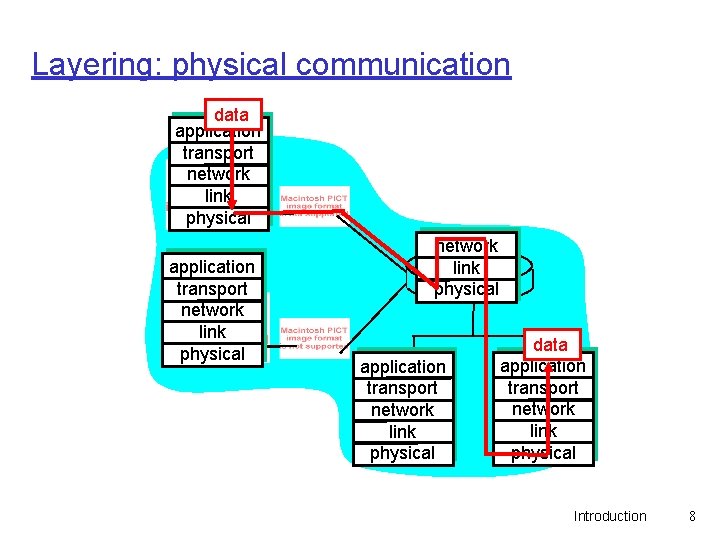
Internet protocol stack q application: supporting network applications m FTP, SMTP, HTTP q transport: host-host data transfer m TCP, UDP q network: routing of datagrams from source to destination m IP, routing protocols q link: data transfer between neighboring network application transport network elements m PPP, Ethernet q physical: bits “on the wire” link physical Introduction 7

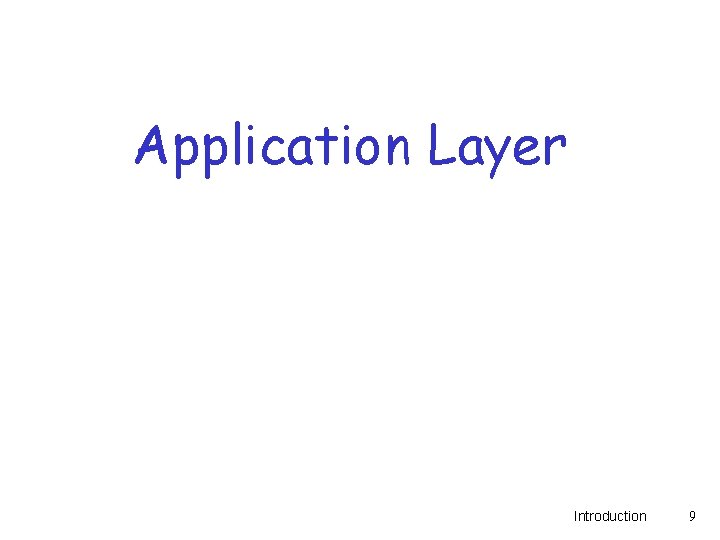
Layering: physical communication data application transport network link physical application transport network link physical data application transport network link physical Introduction 8

Application Layer Introduction 9

Network applications: some jargon Process: program running user agent: interfaces within a host. user “above” and network “below”. q within same host, two processes communicate q implements user using interprocess interface & applicationcommunication (defined level protocol by OS) m Web: browser m E-mail: mail reader q processes running in m streaming audio/video: different hosts media player communicate with an application-layer protocol Introduction 10

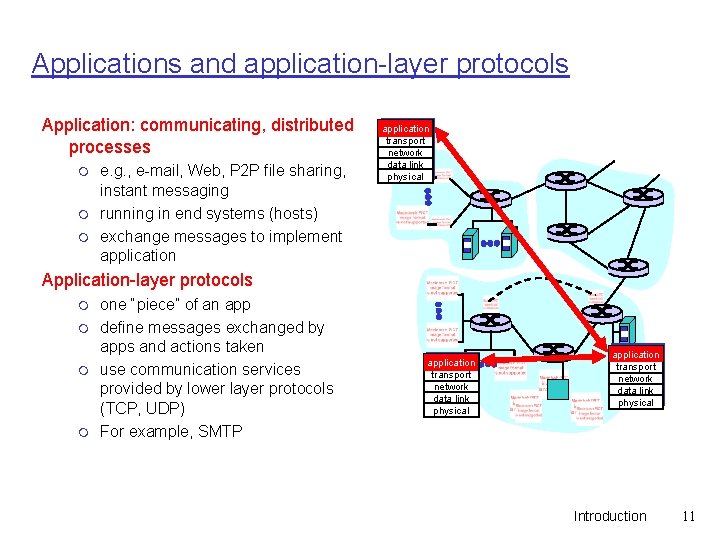
Applications and application-layer protocols Application: communicating, distributed processes m m m e. g. , e-mail, Web, P 2 P file sharing, instant messaging running in end systems (hosts) exchange messages to implement application transport network data link physical Application-layer protocols m m one “piece” of an app define messages exchanged by apps and actions taken use communication services provided by lower layer protocols (TCP, UDP) For example, SMTP application transport network data link physical Introduction 11

Client-server paradigm (“usual” approach) Typical network app has two pieces: client and server Client: application transport network data link physical request q initiates contact with server (“speaks first”) q typically requests service from server, q Web: client implemented in browser; e-mail: in mail reader Server: q provides requested service to client reply application transport network data link physical q e. g. , Web server sends requested Web page, mail server delivers e-mail Hosts: both clients and servers Introduction 12

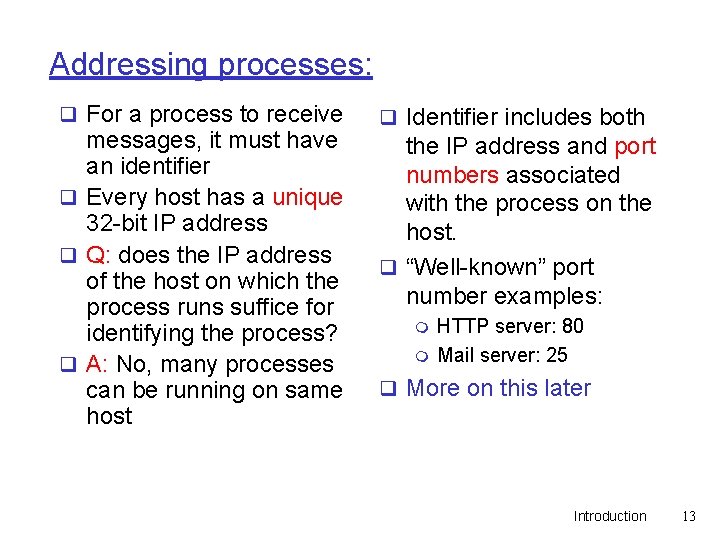
Addressing processes: q For a process to receive messages, it must have an identifier q Every host has a unique 32 -bit IP address q Q: does the IP address of the host on which the process runs suffice for identifying the process? q A: No, many processes can be running on same host q Identifier includes both the IP address and port numbers associated with the process on the host. q “Well-known” port number examples: m m HTTP server: 80 Mail server: 25 q More on this later Introduction 13

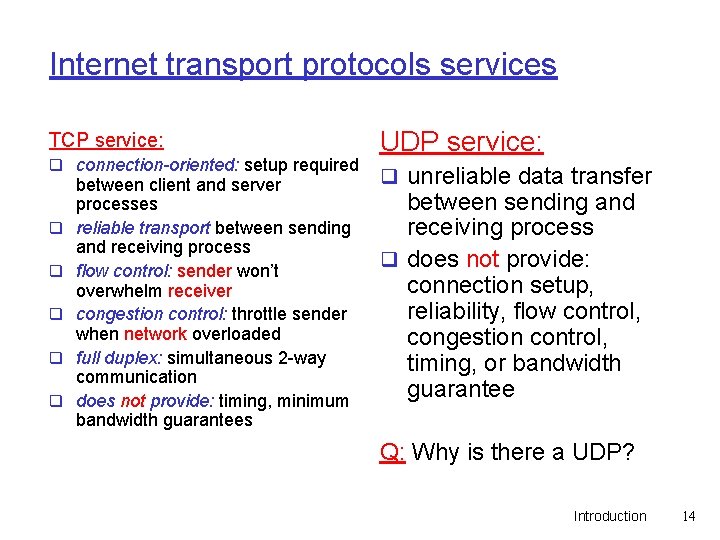
Internet transport protocols services TCP service: q connection-oriented: setup required q q q between client and server processes reliable transport between sending and receiving process flow control: sender won’t overwhelm receiver congestion control: throttle sender when network overloaded full duplex: simultaneous 2 -way communication does not provide: timing, minimum bandwidth guarantees UDP service: q unreliable data transfer between sending and receiving process q does not provide: connection setup, reliability, flow control, congestion control, timing, or bandwidth guarantee Q: Why is there a UDP? Introduction 14

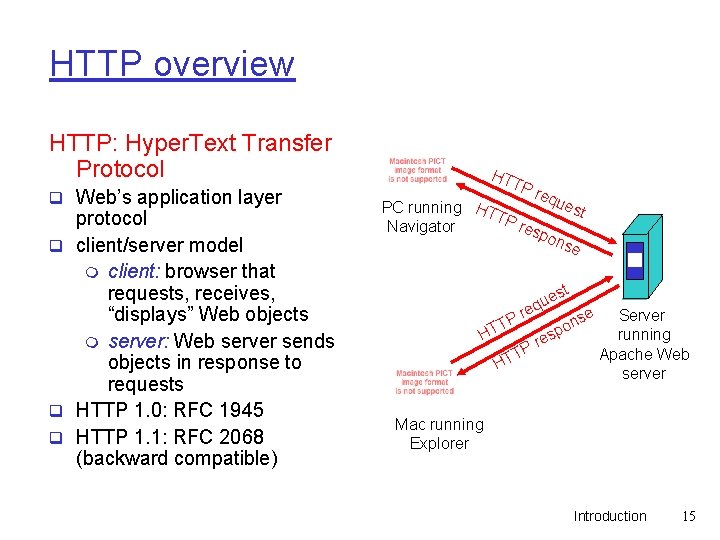
HTTP overview HTTP: Hyper. Text Transfer Protocol q Web’s application layer protocol q client/server model m client: browser that requests, receives, “displays” Web objects m server: Web server sends objects in response to requests q HTTP 1. 0: RFC 1945 q HTTP 1. 1: RFC 2068 (backward compatible) HT TP req ues PC running HT t TP res Navigator pon se e r TP HT st e qu es H Pr T T se n po Server running Apache Web server Mac running Explorer Introduction 15

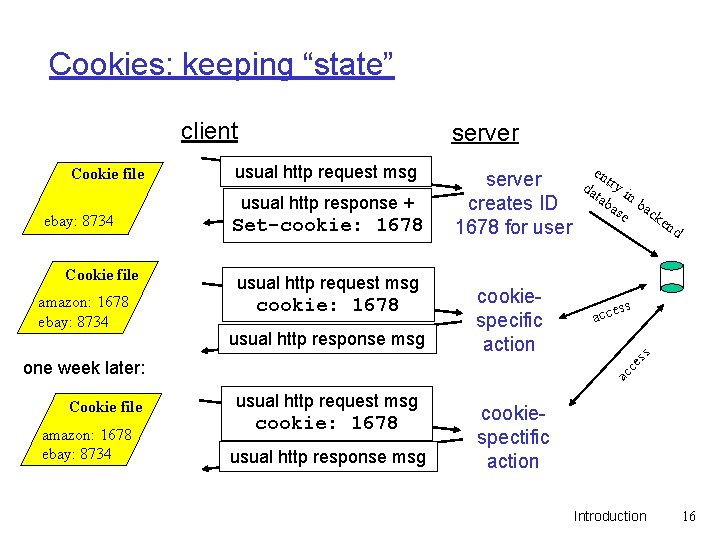
Cookies: keeping “state” client ebay: 8734 Cookie file amazon: 1678 ebay: 8734 usual http request msg usual http response + Set-cookie: 1678 usual http request msg cookie: 1678 usual http response msg server creates ID 1678 for user cookiespecific action Cookie file amazon: 1678 ebay: 8734 en d ss acce ac ce one week later: en da try i tab n b as ac e k ss Cookie file server usual http request msg cookie: 1678 usual http response msg cookiespectific action Introduction 16

Cookies (continued) aside What cookies can bring: q authorization q shopping carts q recommendations q user session state (Web e-mail) Cookies and privacy: q cookies permit sites to learn a lot about you q you may supply name and e-mail to sites q search engines use redirection & cookies to learn yet more q advertising companies obtain info across sites Introduction 17

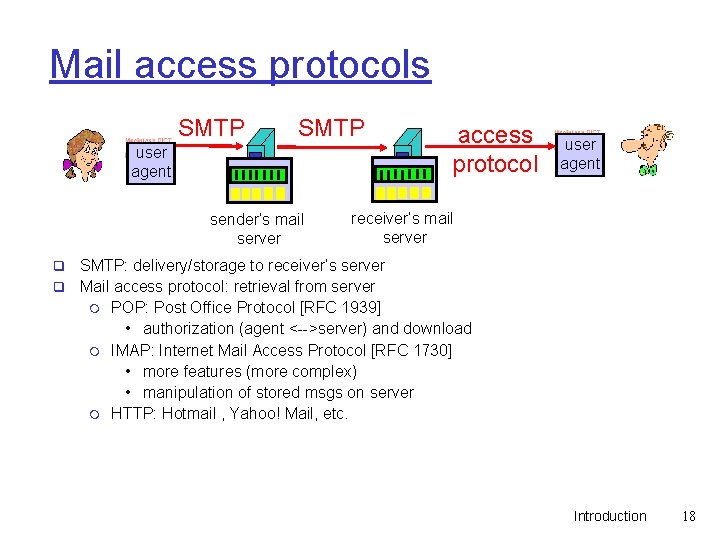
Mail access protocols SMTP user agent sender’s mail server q q access protocol user agent receiver’s mail server SMTP: delivery/storage to receiver’s server Mail access protocol: retrieval from server m POP: Post Office Protocol [RFC 1939] • authorization (agent <-->server) and download m IMAP: Internet Mail Access Protocol [RFC 1730] • more features (more complex) • manipulation of stored msgs on server m HTTP: Hotmail , Yahoo! Mail, etc. Introduction 18

Sample SMTP interaction S: C: S: C: C: C: S: 220 hamburger. edu HELO ca. gov 250 Hello ca. gov, pleased to meet you MAIL FROM: <arnold@ca. gov> 250 arnold@ca. gov. . . Sender ok RCPT TO: <mstamp 1@earthlink. net> 250 mstamp 1@earthlink. net. . . Recipient ok DATA 354 Enter mail, end with ". " on a line by itself It is my pleasure to inform you that you are terminated. 250 Message accepted for delivery QUIT 221 hamburger. edu closing connection Introduction 19

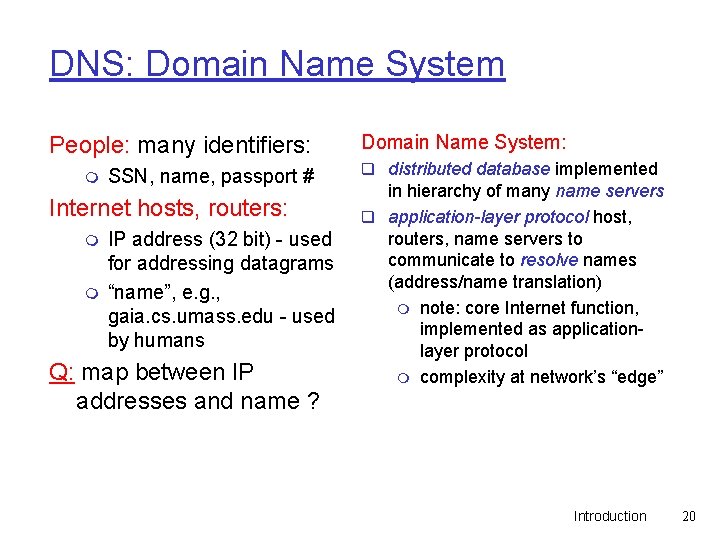
DNS: Domain Name System People: many identifiers: m SSN, name, passport # Internet hosts, routers: m m IP address (32 bit) - used for addressing datagrams “name”, e. g. , gaia. cs. umass. edu - used by humans Q: map between IP addresses and name ? Domain Name System: q distributed database implemented in hierarchy of many name servers q application-layer protocol host, routers, name servers to communicate to resolve names (address/name translation) m note: core Internet function, implemented as applicationlayer protocol m complexity at network’s “edge” Introduction 20

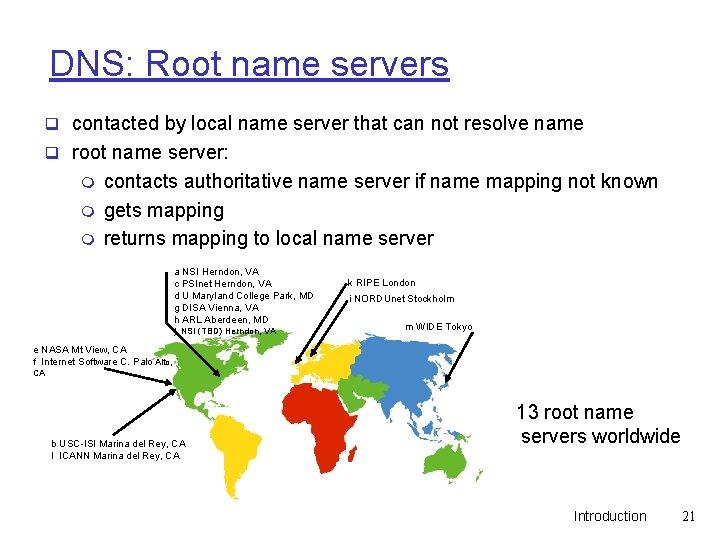
DNS: Root name servers q contacted by local name server that can not resolve name q root name server: m m m contacts authoritative name server if name mapping not known gets mapping returns mapping to local name server a NSI Herndon, VA c PSInet Herndon, VA d U Maryland College Park, MD g DISA Vienna, VA h ARL Aberdeen, MD j NSI (TBD) Herndon, VA k RIPE London i NORDUnet Stockholm m WIDE Tokyo e NASA Mt View, CA f Internet Software C. Palo Alto, CA b USC-ISI Marina del Rey, CA l ICANN Marina del Rey, CA 13 root name servers worldwide Introduction 21

P 2 P file sharing q Alice chooses one of the Example q Alice runs P 2 P client application on her notebook computer q Intermittently connects to Internet; gets new IP address for each connection q Asks for “Hey Jude” q Application displays other peers that have copy of Hey Jude. peers, Bob. q File is copied from Bob’s PC to Alice’s notebook: HTTP q While Alice downloads, other users uploading from Alice. q Alice’s peer is both a Web client and a transient Web server. All peers are servers = highly scalable! Introduction 22

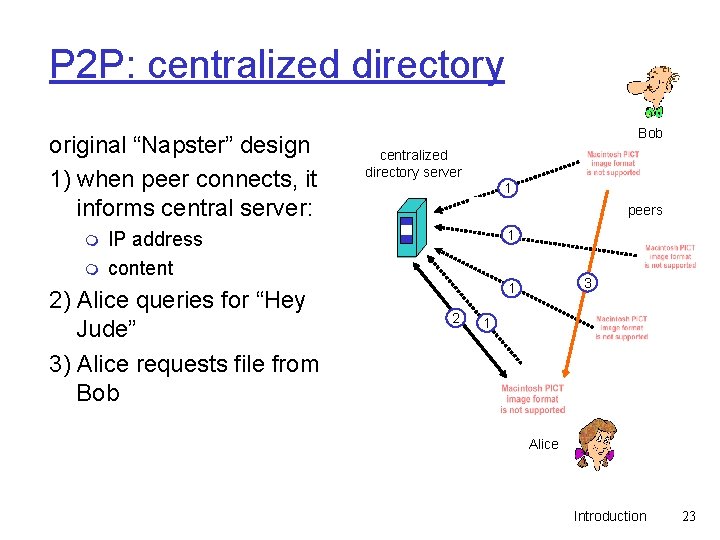
P 2 P: centralized directory original “Napster” design 1) when peer connects, it informs central server: m m Bob centralized directory server 1 peers 1 IP address content 2) Alice queries for “Hey Jude” 3) Alice requests file from Bob 3 1 2 1 Alice Introduction 23

P 2 P: decentralized directory Each peer is either a group leader or assigned to a group leader. q Group leader tracks the content in all its children. q Peer queries group leader; group leader may query other group leaders. q Ka. Za. A uses this idea Introduction 24

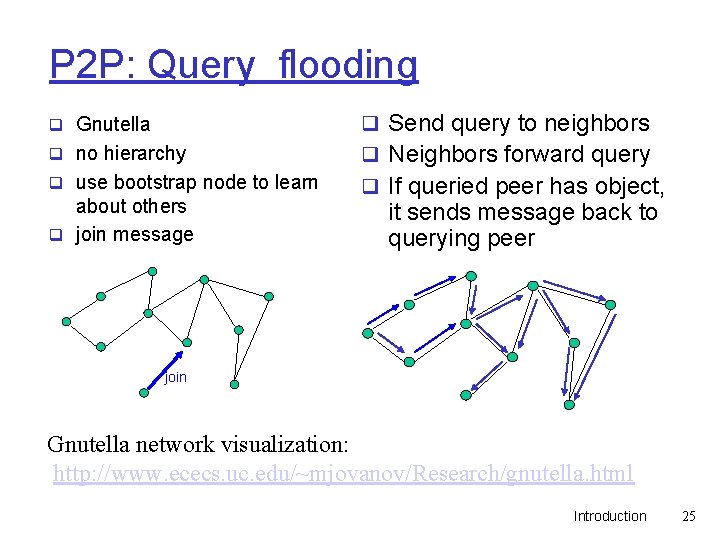
P 2 P: Query flooding q Gnutella q Send query to neighbors q no hierarchy q Neighbors forward query q use bootstrap node to learn q If queried peer has object, about others q join message it sends message back to querying peer join Gnutella network visualization: http: //www. ececs. uc. edu/~mjovanov/Research/gnutella. html Introduction 25

Transport Layer Introduction 26

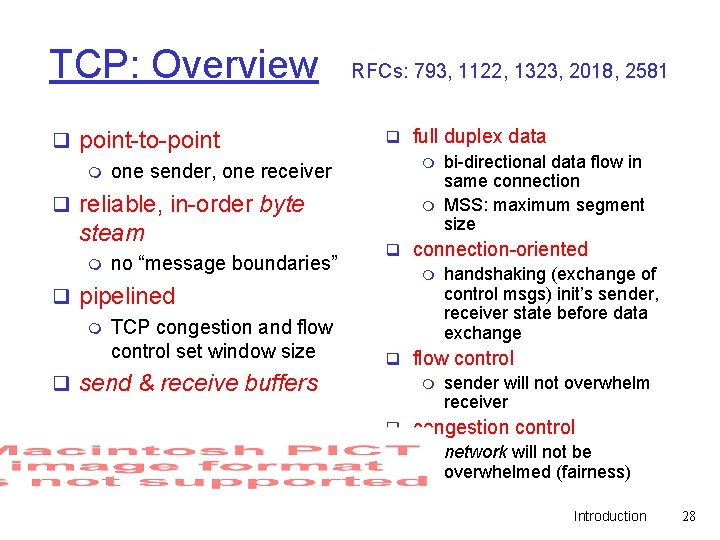
Internet transport-layer protocols q reliable, in-order delivery (TCP) network data link physical rt po q services not available: m delay guarantees m bandwidth guarantees ns tra no-frills extension of “besteffort” IP nd m -e delivery: UDP network data link physical nd q unreliable, unordered le ca m network data link physical gi m congestion control flow control connection setup network data link physical lo m application transport network data link physical Introduction 27

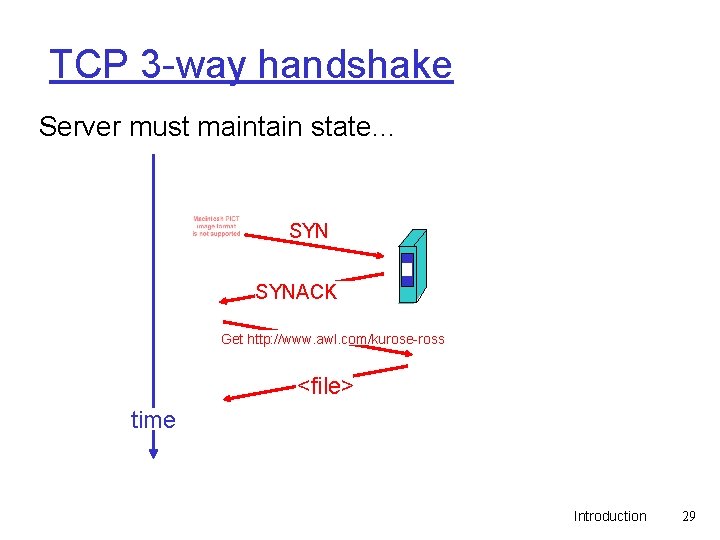
TCP: Overview q point-to-point m one sender, one receiver q reliable, in-order byte steam m no “message boundaries” q pipelined m TCP congestion and flow control set window size q send & receive buffers RFCs: 793, 1122, 1323, 2018, 2581 q full duplex data m bi-directional data flow in same connection m MSS: maximum segment size q connection-oriented m handshaking (exchange of control msgs) init’s sender, receiver state before data exchange q flow control m sender will not overwhelm receiver q congestion control m network will not be overwhelmed (fairness) Introduction 28

TCP 3 -way handshake Server must maintain state… SYNACK Get http: //www. awl. com/kurose-ross <file> time Introduction 29

Network Layer Introduction 30

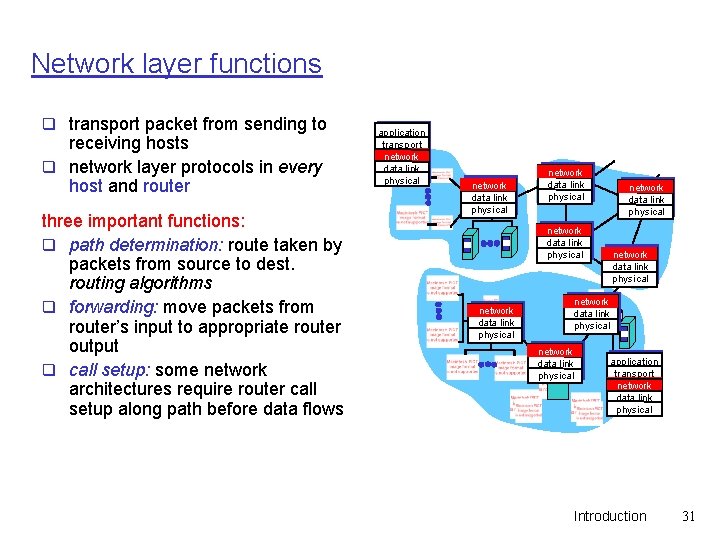
Network layer functions q transport packet from sending to receiving hosts q network layer protocols in every host and router three important functions: q path determination: route taken by packets from source to dest. routing algorithms q forwarding: move packets from router’s input to appropriate router output q call setup: some network architectures require router call setup along path before data flows application transport network data link physical network data link physical network data link physical application transport network data link physical Introduction 31

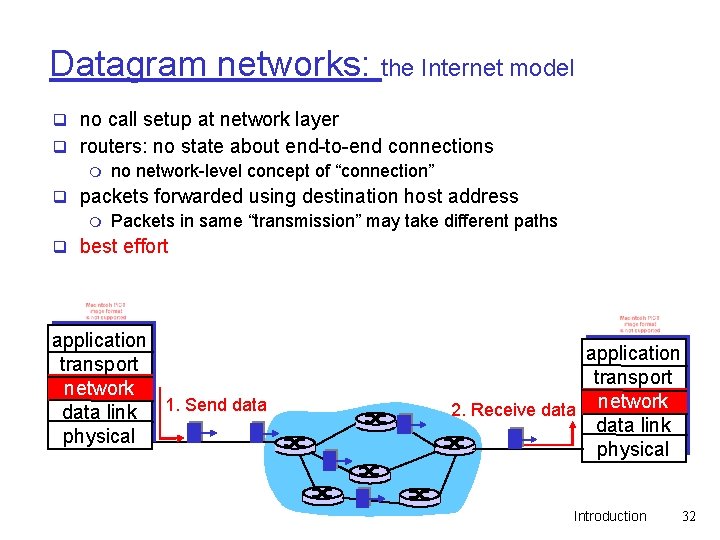
Datagram networks: the Internet model q no call setup at network layer q routers: no state about end-to-end connections m no network-level concept of “connection” q packets forwarded using destination host address m Packets in same “transmission” may take different paths q best effort application transport network data link 1. Send data physical application transport 2. Receive data network data link physical Introduction 32

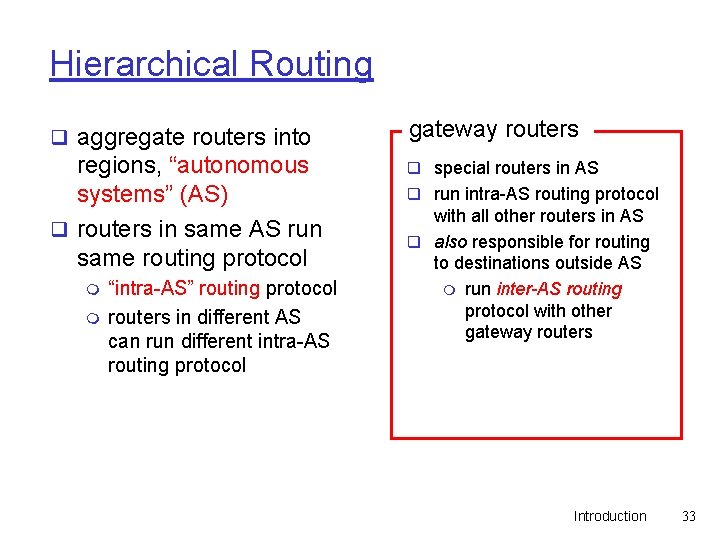
Hierarchical Routing q aggregate routers into gateway routers regions, “autonomous systems” (AS) q routers in same AS run same routing protocol q special routers in AS m m “intra-AS” routing protocol routers in different AS can run different intra-AS routing protocol q run intra-AS routing protocol with all other routers in AS q also responsible for routing to destinations outside AS m run inter-AS routing protocol with other gateway routers Introduction 33

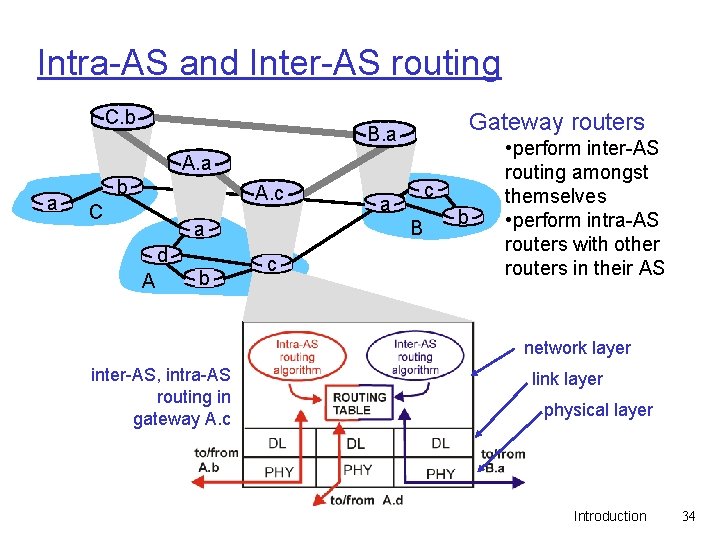
Intra-AS and Inter-AS routing C. b Gateway routers B. a A. a a b A. c C B a d A b c a c b • perform inter-AS routing amongst themselves • perform intra-AS routers with other routers in their AS network layer inter-AS, intra-AS routing in gateway A. c link layer physical layer Introduction 34

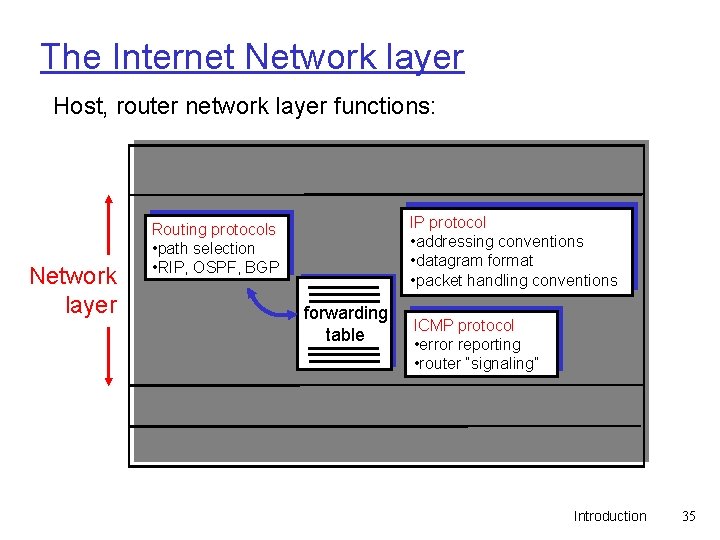
The Internet Network layer Host, router network layer functions: Transport layer: TCP, UDP Network layer IP protocol • addressing conventions • datagram format • packet handling conventions Routing protocols • path selection • RIP, OSPF, BGP forwarding table ICMP protocol • error reporting • router “signaling” Link layer physical layer Introduction 35

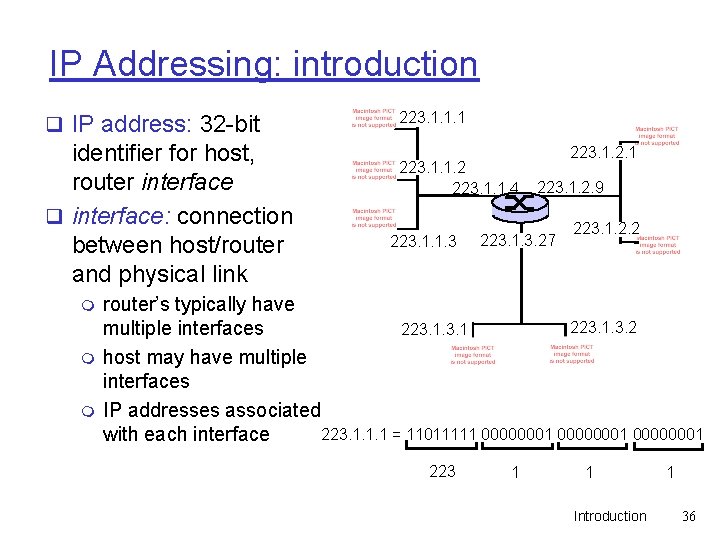
IP Addressing: introduction q IP address: 32 -bit identifier for host, router interface q interface: connection between host/router and physical link m m m 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 1. 3 223. 1. 2. 1 223. 1. 2. 9 223. 1. 3. 27 223. 1. 2. 2 router’s typically have 223. 1. 3. 2 223. 1 multiple interfaces host may have multiple interfaces IP addresses associated 223. 1. 1. 1 = 11011111 00000001 with each interface 223 1 1 Introduction 1 36

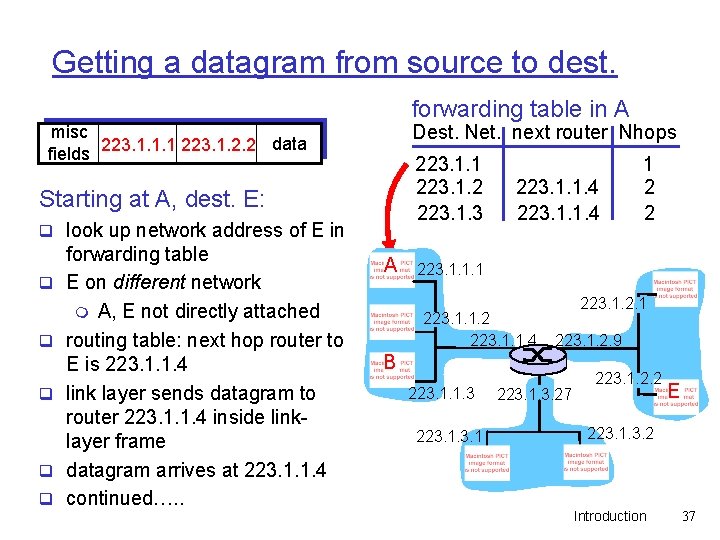
Getting a datagram from source to dest. forwarding table in A Dest. Net. next router Nhops misc data fields 223. 1. 1. 1 223. 1. 2. 2 223. 1. 1 223. 1. 2 223. 1. 3 Starting at A, dest. E: q look up network address of E in q q q forwarding table E on different network m A, E not directly attached routing table: next hop router to E is 223. 1. 1. 4 link layer sends datagram to router 223. 1. 1. 4 inside linklayer frame datagram arrives at 223. 1. 1. 4 continued…. . A 223. 1. 1. 4 1 2 2 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 2. 1 223. 1. 2. 9 B 223. 1. 1. 3 223. 1. 3. 27 223. 1. 2. 2 E 223. 1. 3. 2 Introduction 37

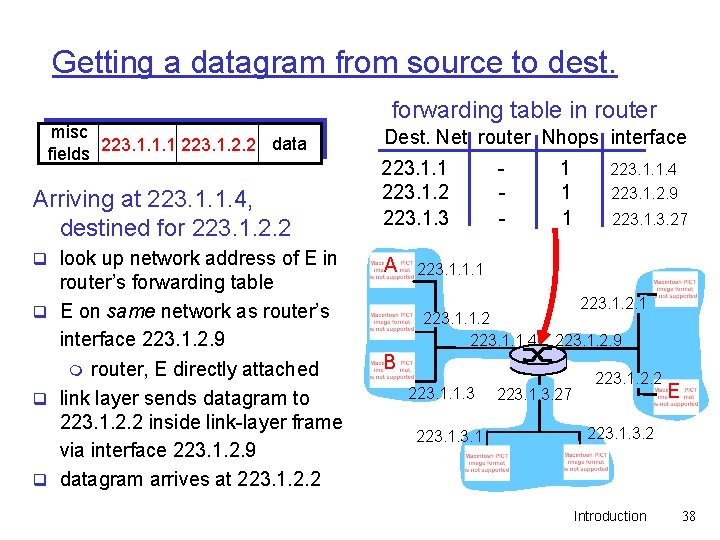
Getting a datagram from source to dest. misc data fields 223. 1. 1. 1 223. 1. 2. 2 Arriving at 223. 1. 1. 4, destined for 223. 1. 2. 2 q look up network address of E in router’s forwarding table q E on same network as router’s interface 223. 1. 2. 9 m router, E directly attached q link layer sends datagram to 223. 1. 2. 2 inside link-layer frame via interface 223. 1. 2. 9 q datagram arrives at 223. 1. 2. 2 forwarding table in router Dest. Net router Nhops interface 223. 1. 1 223. 1. 2 223. 1. 3 A - 1 1 1 223. 1. 1. 4 223. 1. 2. 9 223. 1. 3. 27 223. 1. 1. 1 223. 1. 1. 2 223. 1. 1. 4 223. 1. 2. 1 223. 1. 2. 9 B 223. 1. 1. 3 223. 1. 3. 27 223. 1. 2. 2 E 223. 1. 3. 2 Introduction 38

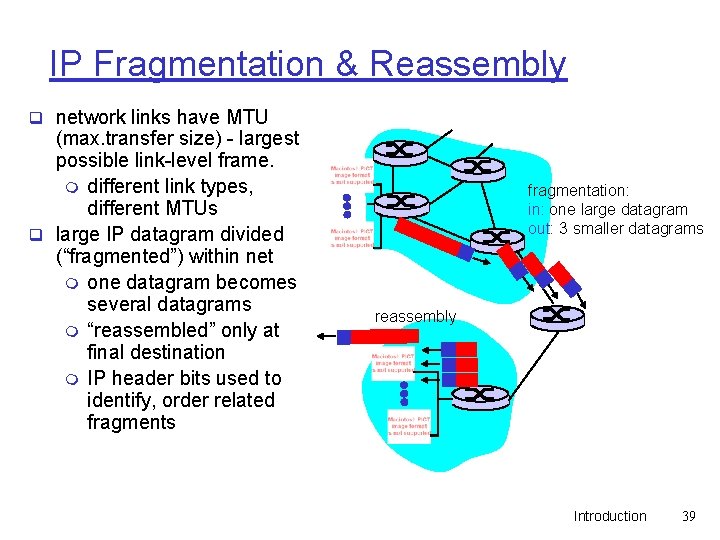
IP Fragmentation & Reassembly q network links have MTU (max. transfer size) - largest possible link-level frame. m different link types, different MTUs q large IP datagram divided (“fragmented”) within net m one datagram becomes several datagrams m “reassembled” only at final destination m IP header bits used to identify, order related fragments fragmentation: in: one large datagram out: 3 smaller datagrams reassembly Introduction 39

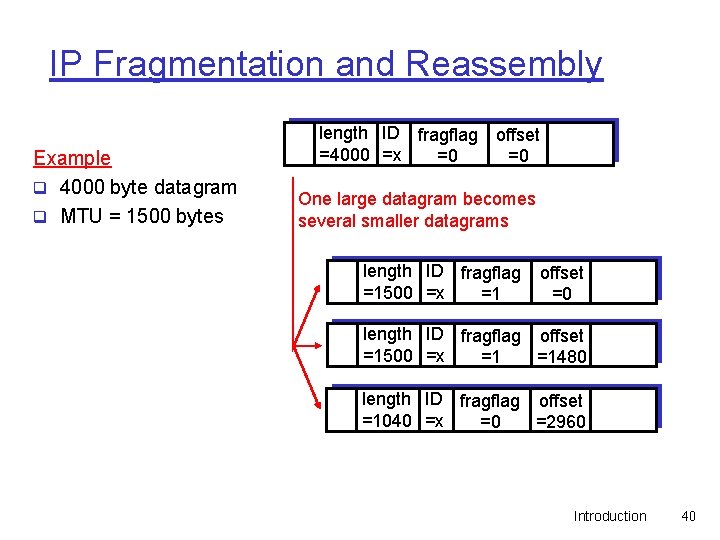
IP Fragmentation and Reassembly Example q 4000 byte datagram q MTU = 1500 bytes length ID fragflag =4000 =x =0 offset =0 One large datagram becomes several smaller datagrams length ID fragflag =1500 =x =1 offset =0 length ID fragflag offset =1500 =x =1 =1480 length ID fragflag offset =1040 =x =0 =2960 Introduction 40

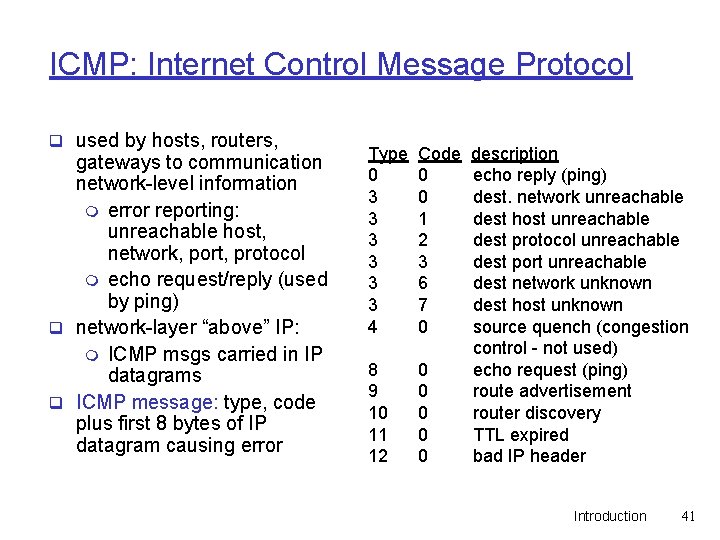
ICMP: Internet Control Message Protocol q used by hosts, routers, gateways to communication network-level information m error reporting: unreachable host, network, port, protocol m echo request/reply (used by ping) q network-layer “above” IP: m ICMP msgs carried in IP datagrams q ICMP message: type, code plus first 8 bytes of IP datagram causing error Type 0 3 3 3 4 Code 0 0 1 2 3 6 7 0 8 9 10 11 12 0 0 0 description echo reply (ping) dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) echo request (ping) route advertisement router discovery TTL expired bad IP header Introduction 41

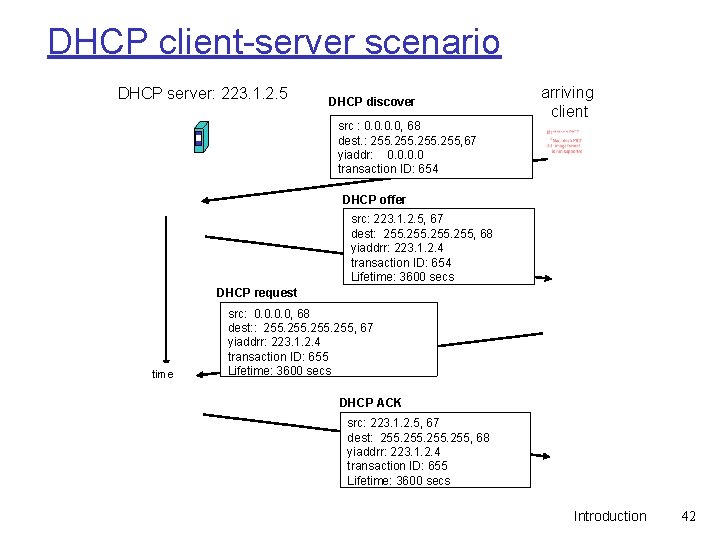
DHCP client-server scenario DHCP server: 223. 1. 2. 5 DHCP discover src : 0. 0, 68 dest. : 255, 67 yiaddr: 0. 0 transaction ID: 654 arriving client DHCP offer src: 223. 1. 2. 5, 67 dest: 255, 68 yiaddrr: 223. 1. 2. 4 transaction ID: 654 Lifetime: 3600 secs DHCP request time src: 0. 0, 68 dest: : 255, 67 yiaddrr: 223. 1. 2. 4 transaction ID: 655 Lifetime: 3600 secs DHCP ACK src: 223. 1. 2. 5, 67 dest: 255, 68 yiaddrr: 223. 1. 2. 4 transaction ID: 655 Lifetime: 3600 secs Introduction 42

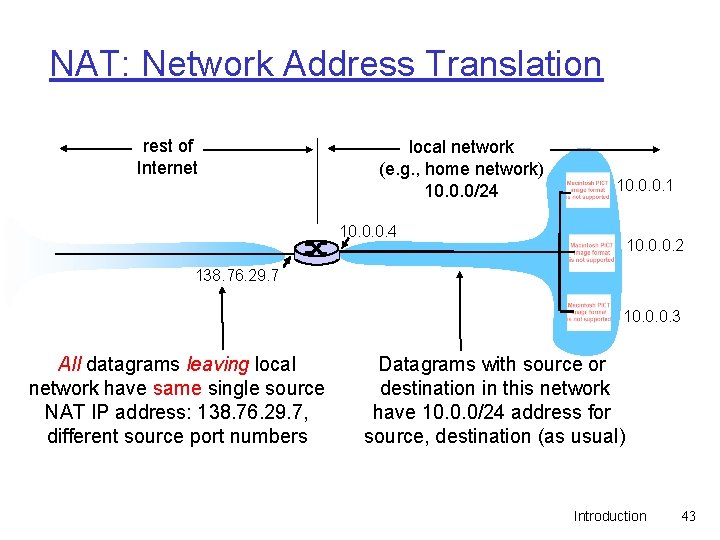
NAT: Network Address Translation rest of Internet local network (e. g. , home network) 10. 0. 0/24 10. 0. 0. 1 10. 0. 0. 4 10. 0. 0. 2 138. 76. 29. 7 10. 0. 0. 3 All datagrams leaving local network have same single source NAT IP address: 138. 76. 29. 7, different source port numbers Datagrams with source or destination in this network have 10. 0. 0/24 address for source, destination (as usual) Introduction 43

Intra-AS Routing q Also known as Interior Gateway Protocols (IGP) q Most common Intra-AS routing protocols: m RIP: Routing Information Protocol m OSPF: Open Shortest Path First m IGRP: Interior Gateway Routing Protocol (Cisco proprietary) Introduction 44

Inter-AS routing in the Internet: BGP Introduction 45

Why different Intra- and Inter-AS routing ? Policy: q Inter-AS: admin wants control over how its traffic routed, who routes through its net. q Intra-AS: single admin, so no policy decisions needed Scale: q Hierarchical routing saves table size, reduced update traffic Performance: q Intra-AS: can focus on performance q Inter-AS: policy may dominate over performance Introduction 46

Link Layer Introduction 47

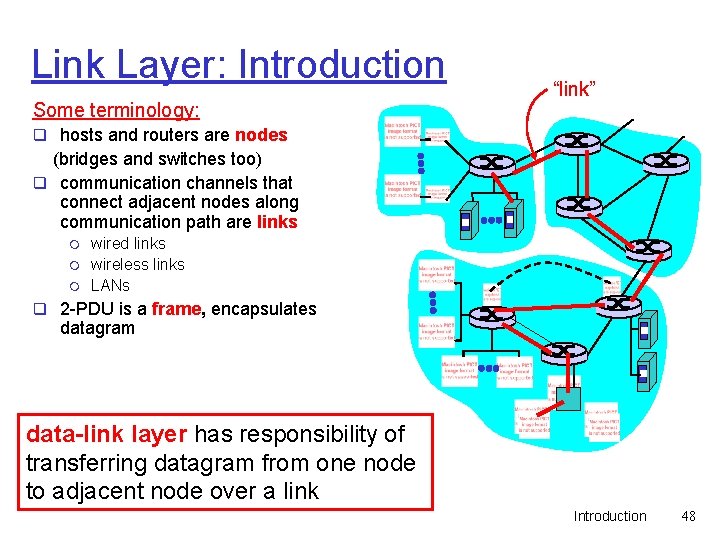
Link Layer: Introduction Some terminology: “link” q hosts and routers are nodes (bridges and switches too) q communication channels that connect adjacent nodes along communication path are links m m m wired links wireless links LANs q 2 -PDU is a frame, encapsulates datagram data-link layer has responsibility of transferring datagram from one node to adjacent node over a link Introduction 48

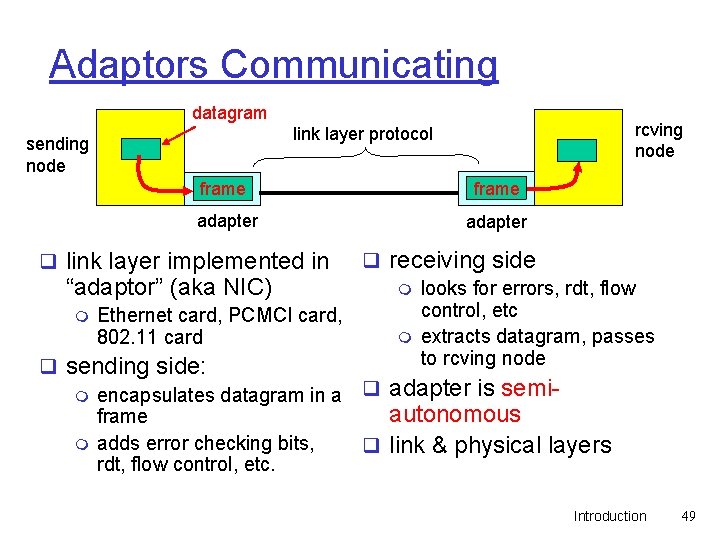
Adaptors Communicating datagram rcving node link layer protocol sending node frame adapter q receiving side “adaptor” (aka NIC) m looks for errors, rdt, flow control, etc m Ethernet card, PCMCI card, m extracts datagram, passes 802. 11 card to rcving node q sending side: m encapsulates datagram in a q adapter is semiautonomous frame m adds error checking bits, q link & physical layers rdt, flow control, etc. q link layer implemented in Introduction 49

Multiple Access protocols q single shared broadcast channel q two or more simultaneous transmissions by nodes: interference m only one node can send successfully at a time multiple access protocol q distributed algorithm that determines how nodes share channel, i. e. , determine when node can transmit q communication about channel sharing must use channel itself (in-band signalling) Introduction 50

MAC Protocols: a taxonomy Three broad classes: q Channel Partitioning m m divide channel into smaller “pieces” (time slots, frequency, code) allocate piece to node for exclusive use q Random Access m channel not divided, allow collisions (data ruined) m “recover” from collisions q Taking turns m tightly coordinate shared access to avoid collisions Introduction 51

Random Access Protocols q When node has packet to send m m transmit at full channel data rate R. no a priori coordination among nodes q two or more transmitting nodes -> collision (data lost) q Random multiple access protocol specifies m m how to detect collisions how to recover from collisions (e. g. , via delayed retransmissions) q Examples of random multiple access protocols m m m slotted ALOHA CSMA, CSMA/CD, CSMA/CA (used in Ethernet) Introduction 52

CSMA Carrier Sense Mulitple Access (CSMA): listen before transmitting q If channel is idle, transmit entire frame q If channel is busy, wait q Human analogy: don’t interrupt others! Introduction 53

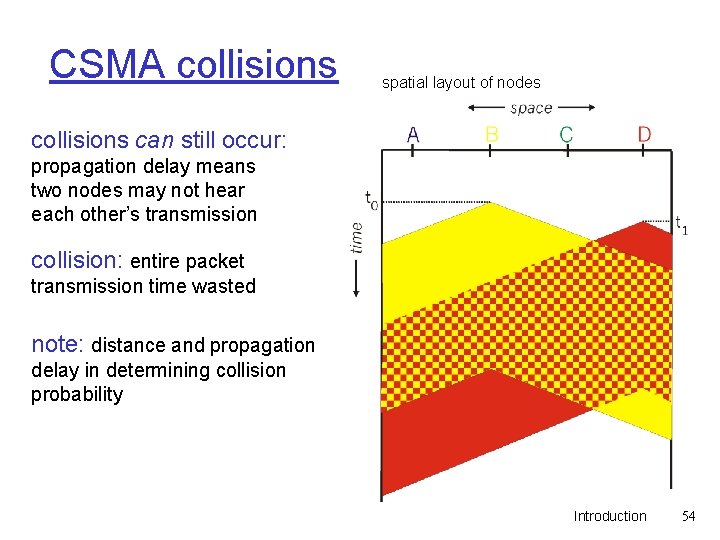
CSMA collisions spatial layout of nodes collisions can still occur: propagation delay means two nodes may not hear each other’s transmission collision: entire packet transmission time wasted note: distance and propagation delay in determining collision probability Introduction 54

CSMA/CD (Collision Detection) CSMA/CD: carrier sensing, deferral as in CSMA m collisions detected within short time m colliding transmissions aborted, reducing channel wastage q collision detection m easy in wired LANs: measure signal strengths, compare transmitted, received signals m difficult in wireless LANs: receiver shut off while transmitting q human analogy: the polite conversationalist Introduction 55

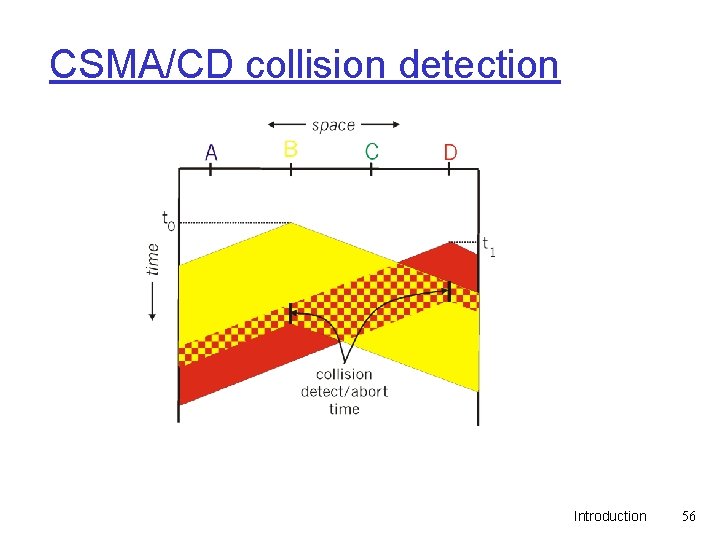
CSMA/CD collision detection Introduction 56

Ethernet uses CSMA/CD q No slots q adapter doesn’t transmit if it senses that some other adapter is transmitting, that is, carrier sense q transmitting adapter aborts when it senses that another adapter is transmitting, that is, collision detection q Before attempting a retransmission, adapter waits a random time, that is, random access Introduction 57

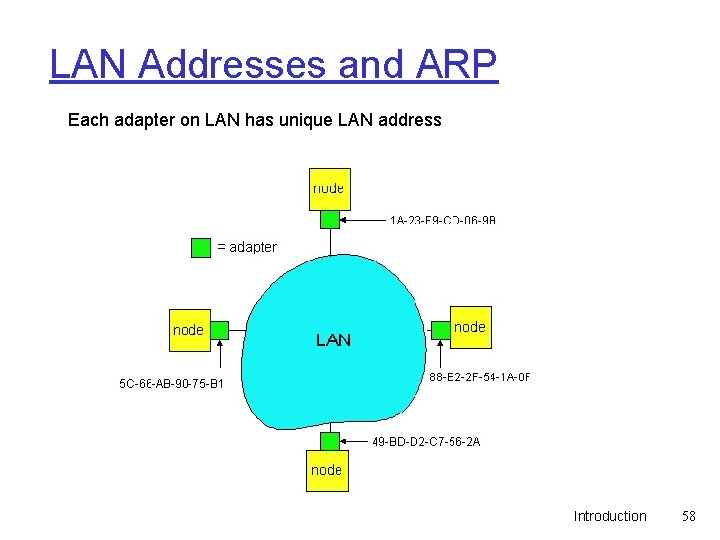
LAN Addresses and ARP Each adapter on LAN has unique LAN address Introduction 58

LAN Address (more) q MAC address allocation administered by IEEE q manufacturer buys portion of MAC address space (to assure uniqueness) q Analogy: (a) MAC address: like Social Security Number (b) IP address: like postal address q MAC flat address => portability m can move LAN card from one LAN to another q IP hierarchical address NOT portable m depends on IP network to which node is attached Introduction 59

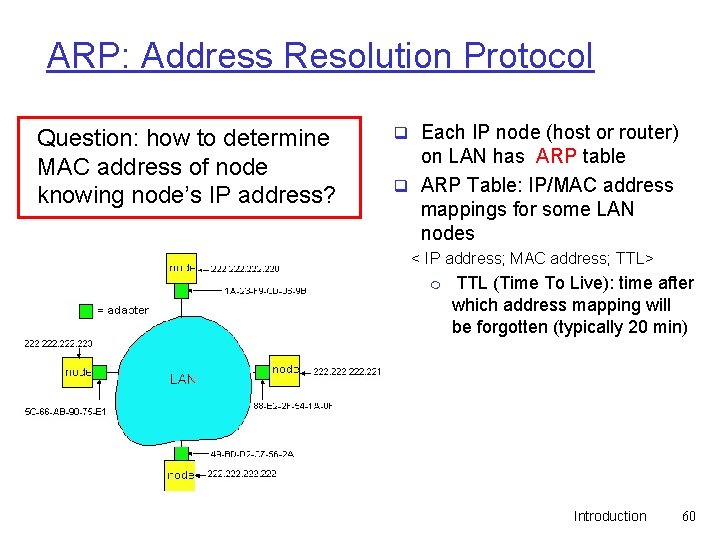
ARP: Address Resolution Protocol Question: how to determine MAC address of node knowing node’s IP address? q Each IP node (host or router) on LAN has ARP table q ARP Table: IP/MAC address mappings for some LAN nodes < IP address; MAC address; TTL> m TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) Introduction 60

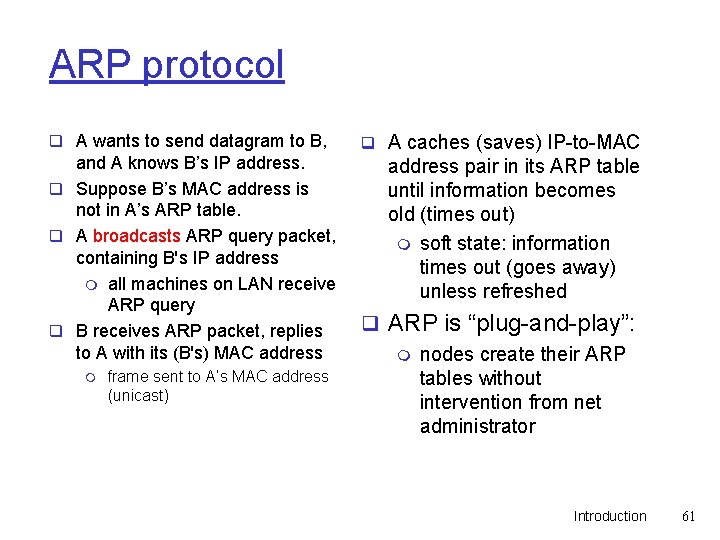
ARP protocol q A wants to send datagram to B, and A knows B’s IP address. q Suppose B’s MAC address is not in A’s ARP table. q A broadcasts ARP query packet, containing B's IP address m all machines on LAN receive ARP query q B receives ARP packet, replies to A with its (B's) MAC address m frame sent to A’s MAC address (unicast) q A caches (saves) IP-to-MAC address pair in its ARP table until information becomes old (times out) m soft state: information times out (goes away) unless refreshed q ARP is “plug-and-play”: m nodes create their ARP tables without intervention from net administrator Introduction 61

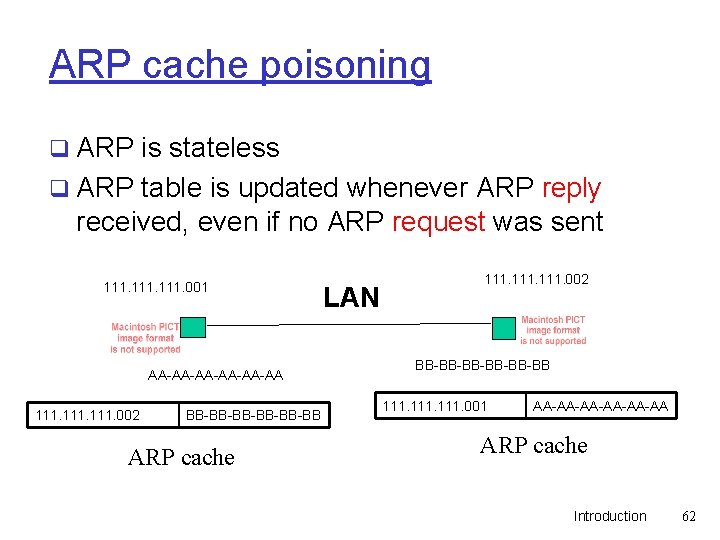
ARP cache poisoning q ARP is stateless q ARP table is updated whenever ARP reply received, even if no ARP request was sent 111. 001 AA-AA-AA-AA 111. 002 BB-BB-BB-BB ARP cache LAN 111. 002 BB-BB-BB-BB 111. 001 AA-AA-AA-AA ARP cache Introduction 62

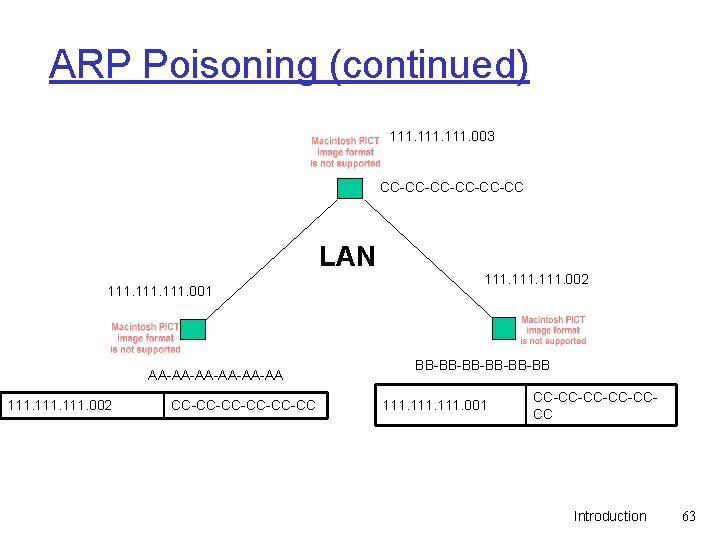
ARP Poisoning (continued) 111. 003 CC-CC-CC-CC LAN 111. 001 AA-AA-AA-AA 111. 002 CC-CC-CC-CC 111. 002 BB-BB-BB-BB 111. 001 CC-CC-CCCC Introduction 63

Summary comparison Introduction 64