Networking 101 OSI Reference Model Data Header OSI







![Logic ● You might take vacation time if you [need a break from work] Logic ● You might take vacation time if you [need a break from work]](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-14.jpg)

![Logic [1101 ● [ 1 1 0 1 ● 1 0 0 1 ] Logic [1101 ● [ 1 1 0 1 ● 1 0 0 1 ]](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-17.jpg)









![Addressing ● [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0000] Addressing ● [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0000]](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-27.jpg)

![Addressing ● AC: 01: 44: 6 B = [0111 1111]: [ 1111 0000 0001]: Addressing ● AC: 01: 44: 6 B = [0111 1111]: [ 1111 0000 0001]:](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-29.jpg)

























- Slides: 60

Networking 101

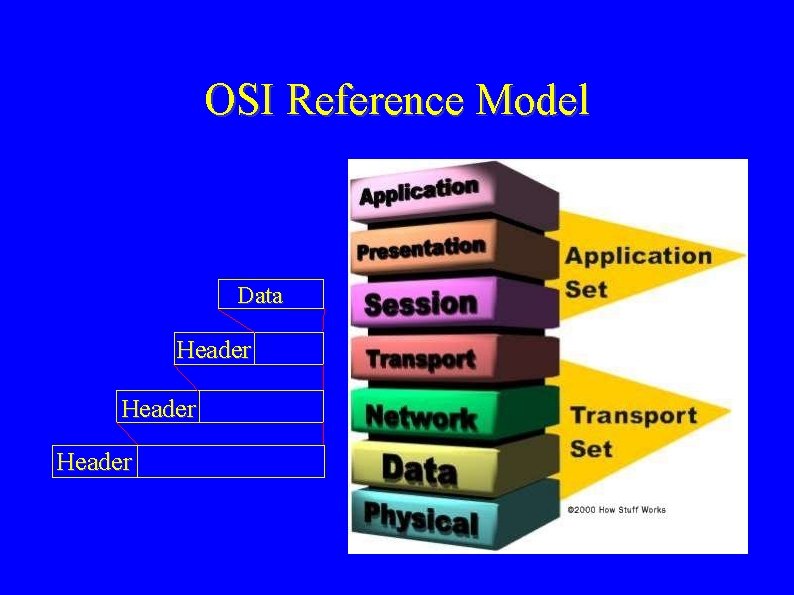
OSI Reference Model Data Header

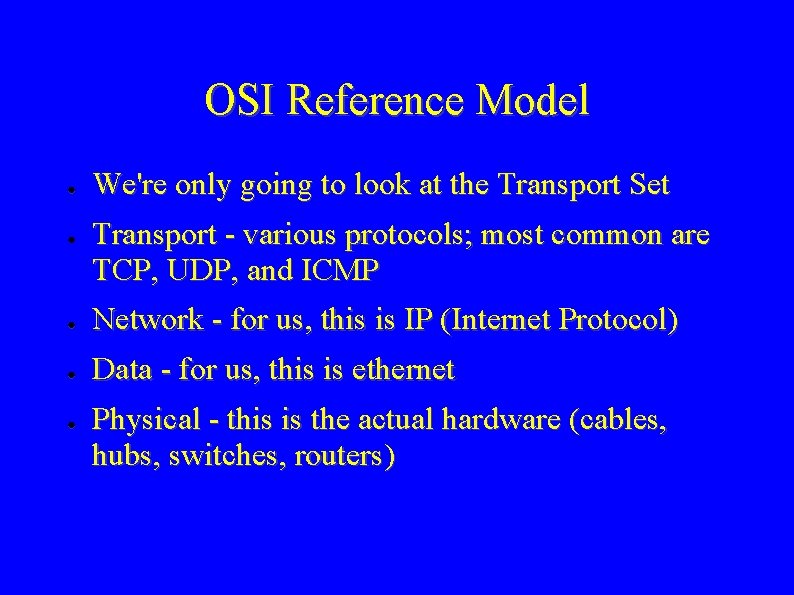
OSI Reference Model ● ● We're only going to look at the Transport Set Transport - various protocols; most common are TCP, UDP, and ICMP ● Network - for us, this is IP (Internet Protocol) ● Data - for us, this is ethernet ● Physical - this is the actual hardware (cables, hubs, switches, routers)

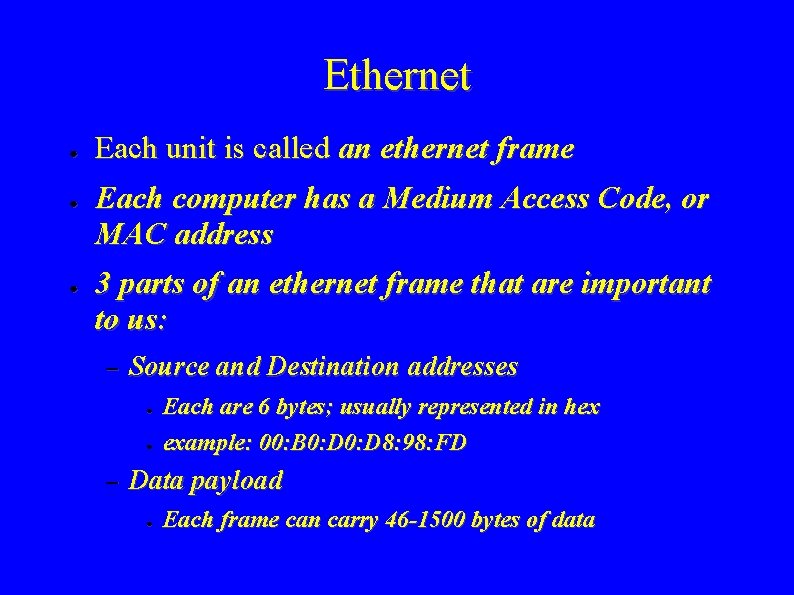
Ethernet ● ● ● Each unit is called an ethernet frame Each computer has a Medium Access Code, or MAC address 3 parts of an ethernet frame that are important to us: – Source and Destination addresses ● ● – Each are 6 bytes; usually represented in hex example: 00: B 0: D 8: 98: FD Data payload ● Each frame can carry 46 -1500 bytes of data

Internet Protocol (IP) ● Each unit is called a packet ● Source and Destination address – – ● 4 byte number, typically represented like 172. 1. 68. 59 Could be represented like ethernet addresses as well (172. 1. 68. 59 would be AC: 01: 44: 3 B) Protocol – A number representing the protocol used by the transport layer (ex. 1=ICMP, 6=TCP, 17=UDP)

Internet Protocol (IP) ● TTL (Time To Live) – – This is the number of routers a packet can pass through before being dropped Each time a packet passes through a router, the router decrements the TTL by 1 ● ● ● Prevents router loops By setting it to 1, you can keep anything from leaving your local network Identification number – 2 byte number used to identify the packet

Internet Protocol (IP) ● Packet length – ● Can be from 20 to 65, 535 bytes (this includes the header length as well) Fragmentation information – – Remember, an ethernet frame can only carry 1500 bytes of data If the IP packet is more than 1500 bytes long, the data layer must chop the packet up in to fragments ● Each fragment has the same identification number

Counting (If you were asleep, you need to wake up now!)

Counting ● ● ● When we use numbers, we use them in a certain base Typically, we use base-10 without even specifying that is the base. It is just assumed. Easiest for us because we have 10 fingers However, computers only have 2 "fingers", so they count much better in base-2 or binary Binary numbers get really long really fast, so we use base-16 or hexadecimal to simplify things

Counting ● ● ● Remember back to when you were a little kid. When someone asked your age, you held up your hand with a few fingers up and said "I'm this many" – we're going to forget the names of numbers for a few minutes If you are counting with your fingers and you need to count to 11, what do you do? You count to 10, then start over, remembering that you have already counted to 10 once.

Counting ● Count to 21 in base-10 ● Count to 21 in base-8 ● Count to 21 in base-16 ● Count to 1111 in base-2

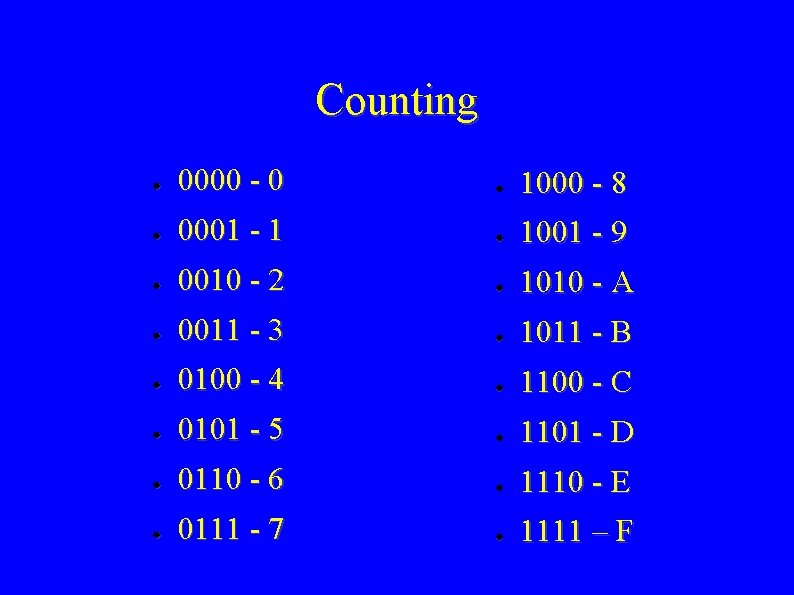
Counting ● 0000 - 0 ● 1000 - 8 ● 0001 - 1 ● 1001 - 9 ● 0010 - 2 ● 1010 - A ● 0011 - 3 ● 1011 - B ● 0100 - 4 ● 1100 - C ● 0101 - 5 ● 1101 - D ● 0110 - 6 ● 1110 - E ● 0111 - 7 ● 1111 – F

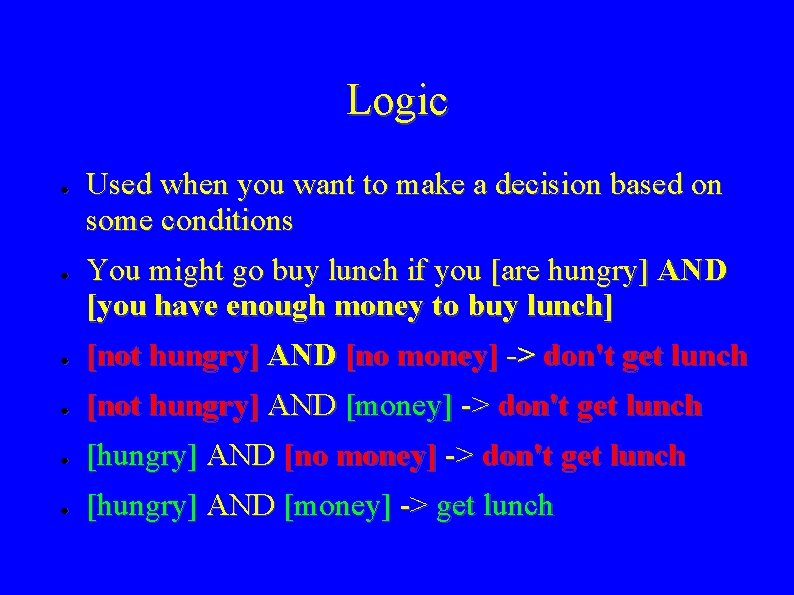
Logic ● ● Used when you want to make a decision based on some conditions You might go buy lunch if you [are hungry] AND [you have enough money to buy lunch] ● [not hungry] AND [no money] -> don't get lunch ● [not hungry] AND [money] -> don't get lunch ● [hungry] AND [no money] -> don't get lunch ● [hungry] AND [money] -> get lunch
![Logic You might take vacation time if you need a break from work Logic ● You might take vacation time if you [need a break from work]](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-14.jpg)
Logic ● You might take vacation time if you [need a break from work] OR [for a special event] OR both ● [no break] OR [no event] -> no vacation ● [no break] OR [event] -> vacation ● [break] OR [no event] -> vacation ● [break] OR [event] -> vacation ● Now, let's change the red items to 0's and the green items to 1's. . .

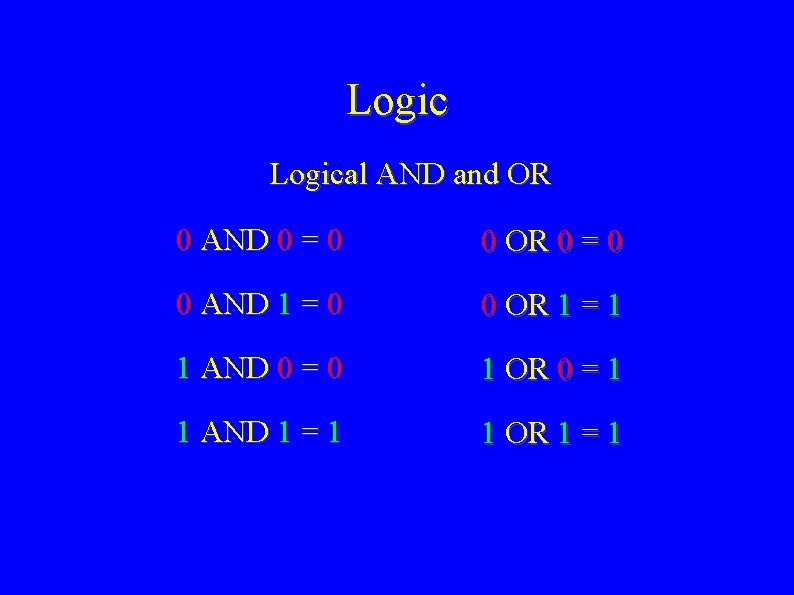
Logical AND and OR 0 AND 0 = 0 0 OR 0 = 0 0 AND 1 = 0 0 OR 1 = 1 1 AND 0 = 0 1 OR 0 = 1 1 AND 1 = 1 1 OR 1 = 1

Logic ● ● ● We just applied the AND and OR operators to a single bit, but they can also be applied to a whole byte, or even multiple bytes. This is called a bitwise AND or bitwise OR [1101 1001] AND [1111 1100] = ? ? ? ? You simply apply the operator to each column seperately. . .
![Logic 1101 1 1 0 1 1 0 0 1 Logic [1101 ● [ 1 1 0 1 ● 1 0 0 1 ]](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-17.jpg)
Logic [1101 ● [ 1 1 0 1 ● 1 0 0 1 ] AND 1100] = 1000] 0 AND 0 = 0 0 AND 1 = 0 1 AND 0 = 0

Counting and Logic Any questions on counting or logic?

Addressing ● What is an IP address? ● Let's look at 172. 1. 68. 107 as an example ● ● Part of this is the network address and part of it is the host address First, we'll say – – The network address is "172. 1. 68. 0" The host address is "107"

Masking ● Have you ever used masking tape while painting? ● Used as a cover to keep from seeing something ● There is such a thing as masking with bits as well ● ● In some situations, you may need to look at certain bits in a binary number To look at only those bits, you create another binary number, called a mask and you perform a bitwise AND of the number and the mask

Masking ● ● Think back to our previous example of the bitwise AND Our first binary number was 1101 1001 Let's say that the first 6 digits are important to us and we don't care about the last 2 If a digit is important, it means we want to know if that digit is a 1 or 0. If we don't care about it, it means it doesn't matter whether it is a 1 or 0 (we end up using a 0 as a placeholder for these digits)

Masking ● ● ● I realize it may seem silly to say we have to use a mask to determine if a digit is a 1 or 0 since we can simply tell by looking at it. But remember, computers don't have eyes. To create a mask, use a 1 for the digits that are important, and use a 0 for the digits that are not So, since we consider the first 6 digits to be important and don't care about the last 2, we would use 1111 1100

Masking ● Reviewing our example of the bitwise AND, we have ● Our binary number: [1101 1001] AND ● Our bitwise mask [1111 1100] = ● The answer! [1101 1000] ● This leads us to the subnet mask or netmask ● A subnet mask is used to separate the network address from the host address

Some Review ● ● ● An IP address can also be represented like a MAC address -- 172. 1. 68. 107 would be AC: 01: 44: 6 B 172. 1. 68. 0 (or AC: 01: 44: 00) is the network address 107 (or 6 B) is the host address We use hexadecimal numbers to represent binary numbers Let's review that representation

Counting ● 0 - 0000 ● 8 - 1000 ● 1 - 0001 ● 9 - 1001 ● 2 - 0010 ● A - 1010 ● 3 - 0011 ● B - 1011 ● 4 - 0100 ● C - 1100 ● 5 - 0101 ● D - 1101 ● 6 - 0110 ● E - 1110 ● 7 - 0111 ● F - 1111

Addressing ● ● ● So, translating our hexadecimal IP address, AC: 01: 44: 6 B, to binary form, we get [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0110 1011] 1011 So, if we are only interested in the network address, what would our subnet mask be? ● [1111 1111]: [ 1111 0000] 0000 ● Performing a bitwise AND, we get ● [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0000] 0000
![Addressing 0111 1111 1111 0000 0001 0001 0100 0100 0000 Addressing ● [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0000]](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-27.jpg)
Addressing ● [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0000] 0000 ● Translating this to hexadecimal, we get ● AC: 01: 44: 00 or in dotted decimal, 172. 1. 68. 0 ● If our subnet mask was [1111 1111]: [ 1111 0000] 0000 in binary, what would it be in hexadecimal? ● FF: FF: 00 or, in dotted decimal, 255. 0

Addressing ● However, what if we use 255. 192 as the subnet mask. What does that mean? ● First, convert it to hexadecimal: FF: FF: C 0 ● Then, to binary: [1111 1111]: [ 1111 1100 0000] 0000 ● If we use this as a subnet mask for our example IP address, 172. 1. 68. 107 (or AC: 01: 44: 6 B), we have
![Addressing AC 01 44 6 B 0111 1111 1111 0000 0001 Addressing ● AC: 01: 44: 6 B = [0111 1111]: [ 1111 0000 0001]:](https://slidetodoc.com/presentation_image_h2/88cfd046b64e8ce4ac87cdc97f0ab005/image-29.jpg)
Addressing ● AC: 01: 44: 6 B = [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0110 1011] 1011 ● Subnet mask: FF: FF: C 0 = [1111 1111]: [ 1111 1100 0000] 0000 ● Performing a bitwise AND gives us [0111 1111]: [ 1111 0000 0001]: [ 0001 0100]: [ 0100 0000] 0000 ● Converting this to hexadecimal: AC: 01: 44: 40 ● Now, in dotted decimal: 172. 1. 68. 64

Addressing ● ● Now, we have the network address for 172. 1. 68. 107 when the subnet mask is 255. 192 -> 172. 1. 68. 64 So, what is a network address anyway? All computers that have the same network address are considered local to each other Computers that are local to each other can send data to each other directly. If they are not local, they must "talk" through a router

Addressing Any questions on addressing?

Hubs, Switches, and Routers ● ● These are the main devices we hear about that connect computers together Each uses one more layer from the OSI reference model than the previous one Hubs and switches perform a similar function; switches are just more intelligent Routers perform a different function than hubs and switches

Hubs ● Function at the physical layer (layer 1) of the OSI model ● No intelligence - doesn't look at any data ● All traffic is sent to every port

Hubs ● ● The medium is shared by all the connected computers Kind of like an intercom system – – Only one person can talk at a time Everyone else hears what the person said If the person speaking is not talking to you, you just ignore them (unless you want to eavesdrop on what is said) When two people talk at the same time, the message is garbled and each of you has to try again ● This is called a collision

Hubs - Pros ● Good for troubleshooting – – Remember the part about eavesdropping with an intercom system? You can use a network traffic "sniffer" to "hear" what the other computers on the hub are saying even if they are not talking specifically to you ● tcpdump, ethereal

Hubs - Cons ● Don't scale well – Remember only 1 computer can talk at a time ● ● ● If 100 computers are connected together, each one will have to wait a lot longer to talk than if only 10 computers were connected together Therefore, more computers mean more collisions No computer can talk and listen at the same time – – This is called half duplex Duplex - the ability to communicate simultaneously in 2 directions

Switches ● ● Function at the data layer (layer 2) of the OSI model More like a telephone system than an intercom system – – ● Telephones allow you to talk directly to another person without anyone else listening Allows you to talk and listen at the same time Full Duplex

Switches ● More secure – ● Scale better – ● Only sends data to desired recipient Because the medium is not shared by all computers, more than one can talk at a time Intelligent – Keeps a table of which MAC addresses are connected to which ports (lookup table)

Switches ● How do they keep track of who is on which port? – – Each ethernet frame has a source and destination address When a computer sends some data, the switch looks at the source address and adds it to its list of computers on that port If it doesn't have the destination port in its table anywhere, it sends the packet to all ports (except the one the packet come in on) Entries in the table expire (are erased) after some amount of time (5 to 30 minutes)

Routers ● ● ● A router is simply a computer (or network device) that is part of multiple subnets that knows how to relay data between the different subnets Normally, the router has a separate network interface to each of the networks It uses a routing table to keep track of which subnet each interface is connected to

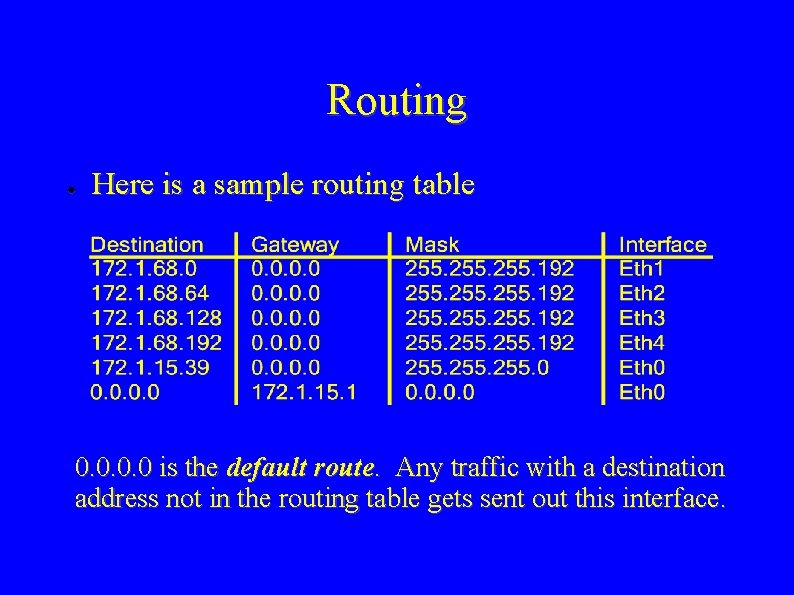
Routing ● Here is a sample routing table 0. 0 is the default route. Any traffic with a destination address not in the routing table gets sent out this interface.

Hubs, Switches, and Routers Any questions on hubs, switches or routers?

Where IP and Ethernet Meet ● ● ● Remember that IP and ethernet are on different layers of the OSI Reference Model Once a computer knows the IP address of another computer with which it wants to communicate, it needs to figure out the other computer's ethernet (or MAC) address (if it is local) It uses the address resolution protocol to do this

Address Resolution Protocol (ARP) ● ● ● Computers use ARP to map MAC addresses to IP addresses If 172. 1. 68. 107 wants to talk to 172. 1. 68. 108, it knows the source and destination IP addresses, but it only knows its own MAC address An ARP Request is sent to MAC address FF: FF: FF: FF, which is known as the broadcast address, asking for the computer having 172. 1. 68. 108 to respond with an ARP reply telling what its MAC address is

Address Resolution Protocol (ARP) ● ● It then adds the other computer's MAC address to its ARP table, which is just a mapping of IP addresses and MAC addresses Each entry in the table expires after some amount of time (4. 5 min. on linux, 20. 5 min. on solaris)

Where IP and Ethernet Meet ● What happens if the other computer is not local? ● We know it must communicate through a router ● ● ● At the IP layer, we send data to the intended IP address (172. 1. 68. 108 from our example) However, at the ethernet layer, we send data to the router The router then sends it to the right network or to another router and, eventually, it will be sent to the other computer

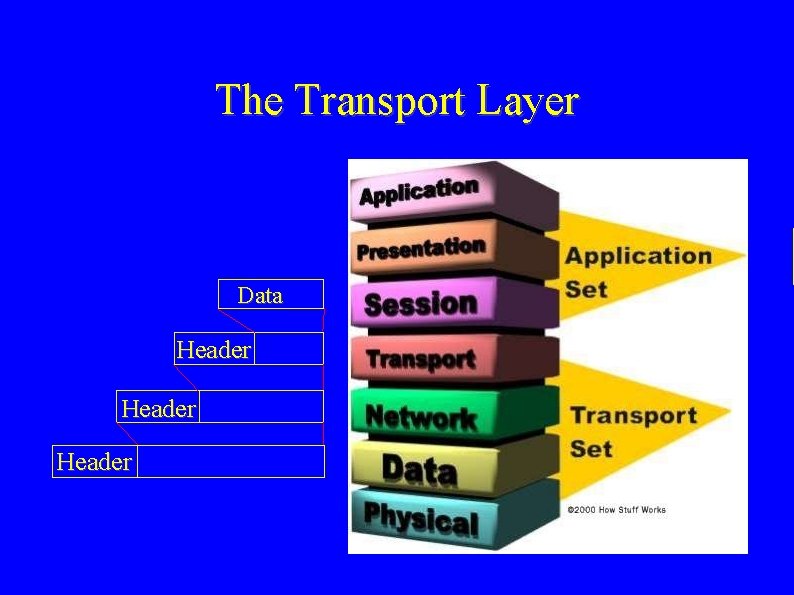
The Transport Layer Data Header

The Transport Layer ● ● There are many protocols at the transport layer Some of the more common ones you may have heard are – TCP - transmission control protocol UDP - user datagram protocol – ICMP - internet control message protocol –

The Transport Layer ● ● ● TCP and UDP have what are called ports To understand ports, lets look at how apartment complexes generally numbered Each building has an address Within the building, each apartment has an address as well My old address was 2921 -33 2921 was the building number, 33 was the apartment number

The Transport Layer ● ● ● Think of the network as an apartment complex Each computer has an address like each building has an address Each program has an address like each apartment has an address

The Transport Layer ● Some of the programs have standard addresses so they can be found more easily – – ● Web server programs use port 80 FTP server programs use port 21 SSH server programs use port 22 Windows networking primarily uses ports 135 -139 and 445 As with IP addresses, there are both a source and destination port used when communicating

The Transport Layer ● ● The source and destination ports do not have to be equal For example, if I am using a web browser, the destination port is going to be 80, but the port my computer uses doesn't have to be 80 (and in fact probably won't be)

The Transport Layer Any questions on the transport layer?

Domain Name Servers ● ● Computers only know how to communicate using IP addresses So, when you type www. ncsu. edu, your computer needs to figure out what IP address is associated with www. ncsu. edu To get this information, it asks a domain name server A domain name server is a program that knows what IP addresses belong to which names and vice versa

Unicast and Broadcast ● Computers can communicate in different ways – – ● ● Unicast - 1 computer to other 1 computer Broadcast - 1 computer to everyone else (that is local) Unicast is how we typically think of computers communicating - it is similar to 2 people having a conversation Broadcast is more like giving a presentation - one person talking to everyone else in the room

Unicast and Broadcast ● ● For unicast, the other computer's IP address is used as the destination address For broadcast, there are specific IP addresses used that all computers know to be broadcast addresses Each subnet has its own broadcast address -- it is the highest address in that subnet Additionally, there is a broadcast address that is not specific to any subnet - 255

Firewalls ● ● ● In construction, a firewall is a structure built to protect against a fire spreading from one location to another A network firewall is a device that keeps network traffic that we consider to be harmful (or that even might be harmful) from coming into our network There are 2 types of network firewalls – – Packet level Application level

Firewalls ● Packet level firewalls filter data based on the information in each packet. – Source and/or destination IP address Transport layer protocols – Source and/or destination port (for TCP and UDP) – ● ● Packet level firewalls can be on a computer or a router It is generally recommended to filter packets with a source or destination port of 135 -139 or 445 to block attacks against Windows

Firewalls ● ● An application level firewall runs on a computer and is more intelligent than a packet level firewall It can tell which packets are related to which programs running on the computer These firewalls block traffic based on which programs the traffic is related to Example: Zone. Alarm

Questions?