NETWORK THREAT REVIEW Agenda In this section Network









- Slides: 23

NETWORK THREAT REVIEW

Agenda In this section • Network threats • Worms • Hackers • Security holes • Social engineering Page 2

NETWORK THREATS

Threats • Network worms • Hackers, crackers • Security holes and vulnerabilities • User-installed uncontrolled programs Threats can be divided to external and internal ones based on where they originate from Page 4

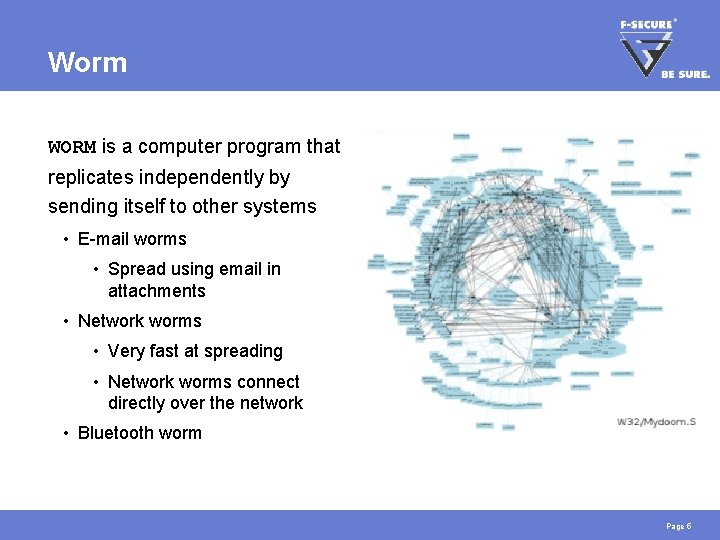
Worm WORM is a computer program that replicates independently by sending itself to other systems • E-mail worms • Spread using email in attachments • Network worms • Very fast at spreading • Network worms connect directly over the network • Bluetooth worm Page 5

Network Worms Network worms use hacker techniques to automatically sneak in from the Internet • For example Nimda, Slammer, Lovsan, Slapper, Sasser • Connect directly over the network (extremely fast spreading) • Traditional antivirus response times are not enough to stop these worms from spreading, personal firewalls are needed • In a way, network worms are automated hacker attacks Page 6

Example: Sasser (2004) Malware type: Network worm Replication mechanism: • Exploits an LSASS security hole in Win 2000 and XP Payload: • Installs a backdoor and launches an DDo. S attack Effect: • Caused unpatched machines to start to reboot • Created problems in at least three large banks; rail traffic was halted in Australia on Saturday, leaving 300, 000 travellers stranded, etc. Writer Sven Jaschen arrested 6 days after seeding Page 7

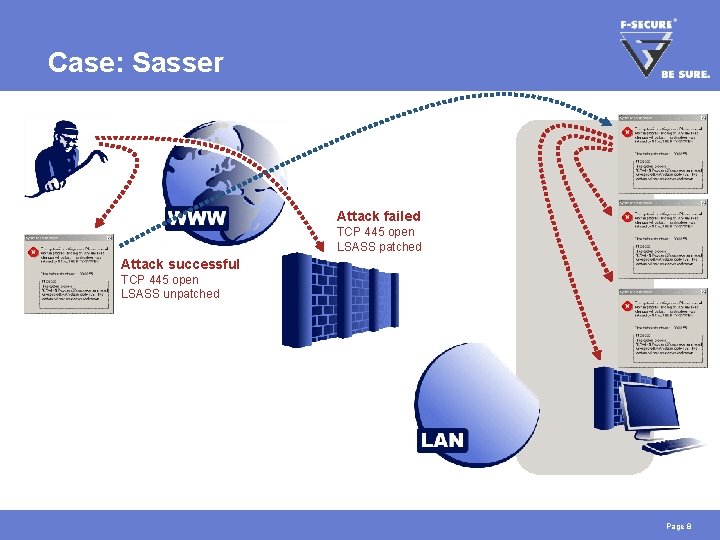
Case: Sasser Attack failed TCP 445 open LSASS patched Attack successful TCP 445 open LSASS unpatched Page 8

Virulence vs. Payload Damage caused by worms can be measured by two key components • VIRULENCE measures how fast a worm spreads, how well the replication mechanism works • Aggressive spreading typically affects resources such as network bandwidth • Extremely virulent worms can cause system overload or failure • PAYLOAD measures what the worm does • May be carried by the worm or distributed later • Doesn’t have to be harmful • Not all worms have payloads, some only exist to propagate Page 9

Common Payloads E-Mail proxies • Installed in stealth • Used as relays for spam distribution Trojan backdoors • Used by the attacker to control the infected computers Distributed Denial of Service (D-Do. S) Page 10

D-Do. S Distributed Denial of Service • Overloading a service by misusing its resources • Very effective way to take someone down, not much one can do about it Most famous incidents • February 2000: Yahoo, Amazon, CNN, e. Bay • Attacks done by a teenager “Mafiaboy” • January 2001: Microsoft • March 2003: www. aljazeera. net • August 2004: Gambling sites blackmail during Olympics Page 11

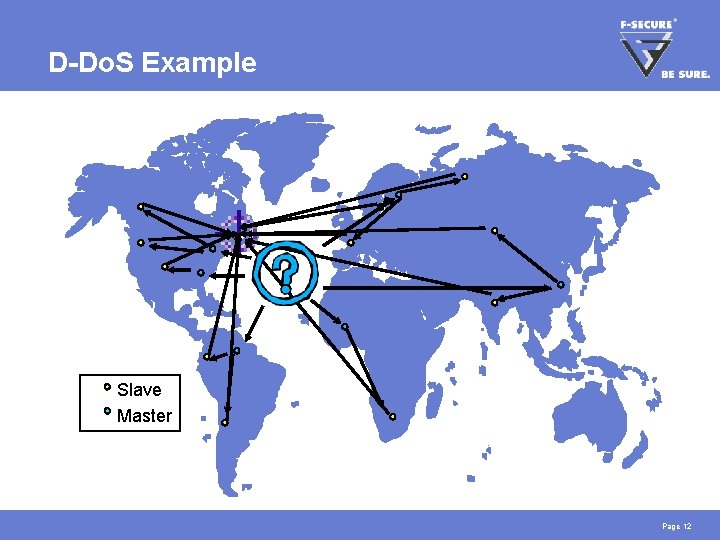
D-Do. S Example Slave Master Page 12

Hacking CRACKING (also HACKING) is gaining direct access to a target system • Wide range of methods available (stolen access information, finding open ports, known security holes, etc. ) • Attacks can be divided to external attacks and internal attacks EXPLOIT is a common term for software that takes advantage of a bug, glitch, security hole or vulnerability • Vulnerability types include buffer overflow, format string attacks, race condition, cross-site scripting, and cross-site request forgery Page 13

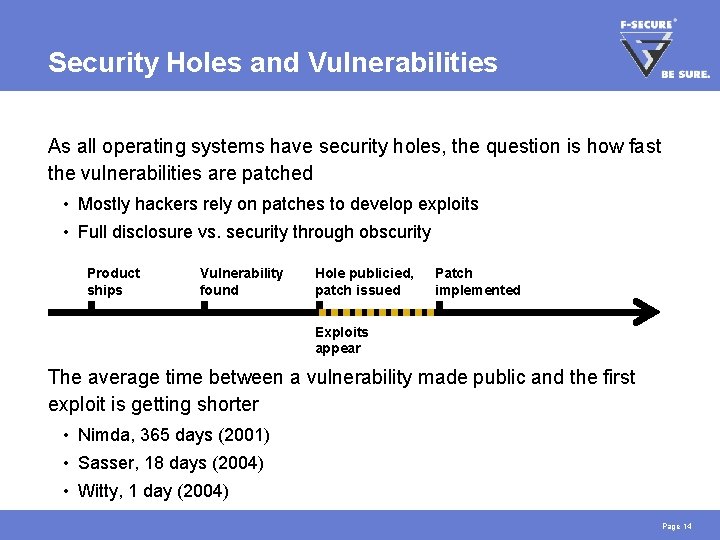
Security Holes and Vulnerabilities As all operating systems have security holes, the question is how fast the vulnerabilities are patched • Mostly hackers rely on patches to develop exploits • Full disclosure vs. security through obscurity Product ships Vulnerability found Hole publicied, patch issued Patch implemented Exploits appear The average time between a vulnerability made public and the first exploit is getting shorter • Nimda, 365 days (2001) • Sasser, 18 days (2004) • Witty, 1 day (2004) Page 14

Linux vs. Windows Average expectancy to compromise for an unpatched Linux system has increased from 72 hours to 3 months in two years • Windows has an average life expectancy of a few minutes • Still, Microsoft usually is faster at releasing fixes to security holes • Also, Microsoft is becoming more security-conscious (SP 2 for XP centres around security features only, anti-spyware tool) Most direct intrusions are performed against Windows hosts • Lower level of basic protection, especially if not updated regularly • Windows dominates the market, which makes it an attractive target • Monoculture, homogenous environments Page 15

Linux and OSX is 2004 There were no major incidents in Linux operating system • Linux users were targeted with a spam message that claimed a security vulnerability has been found in Fedora and the fix is available at fedora-redhat. com. The fake update file turned out to be a rootkit. • Some bugs were found and Su. SE dispatched three local security holes to prevent a local user from hacking the computer Opener, the first real malware for Apple Macintosh OS X was found • Bash script containing a keylogger, a backdoor etc. Security holes were found (and patched in silence) in Samba, Squid, PHP and others Page 16

Social Engineering and Users have the possibility to install software which can leak out information – either by themselves or because they have been fooled in doing so • The line between ’good’ and ’bad’ programs is blurry (spyware, peer-topeer software, etc. ) • Worms and viruses are looking for non-protected entry points, such as Instant Messaging, peer-to-peer networks, Internet Relay Chat (IRC) • Companies typically do not have any means to prevent employees from using software that is not allowed PHISHING means luring sensitive information (like passwords) from a victim by masquerading as someone trustworthy with a real need for such information Page 17

Company Visitors Unsafe devices (laptops, PDAs, mobile phones) that visitors connect to the corporate network are a big threat • These devices might be infected with a fast spreading network worm • These may then try to infect not just internal but also external targets • Damage to the company reputation! Page 18

Other Attack Types A wealth of other methods are available as well • Hacking • Exploiting a known weakness (vulnerabilities) of the operating system or application • Spoofing • IP spoofing: Changing the packet source address to falsify the actual source • DNS spoofing (poisoning): Changing DNS records • E-Mail spoofing: Changing the source e-mail address (e. g used in spam or phishing attacks) • URL / Web spoofing: Sites that look the same as the real ones, but are in fact plagiates (for example using extended domain names) • Scanning • Systematic scanning to find open ports or operating system Page 19

Uninvited Guests Why? Who? • National interest (spies) • Personal gain (thiefs) • Personal fame (trespassers) • Curiosity (vandals, script kiddies) Page 20

Other Malware MALWARE is a common name for all kinds of unwanted software such as viruses, worms, spyware and trojans TROJAN HORSE (or trojan) is a program with hidden destructive functionality SPAM means unsolicited bulk email, something the recipient did not ask for it and that is sent in large volumes Page 21

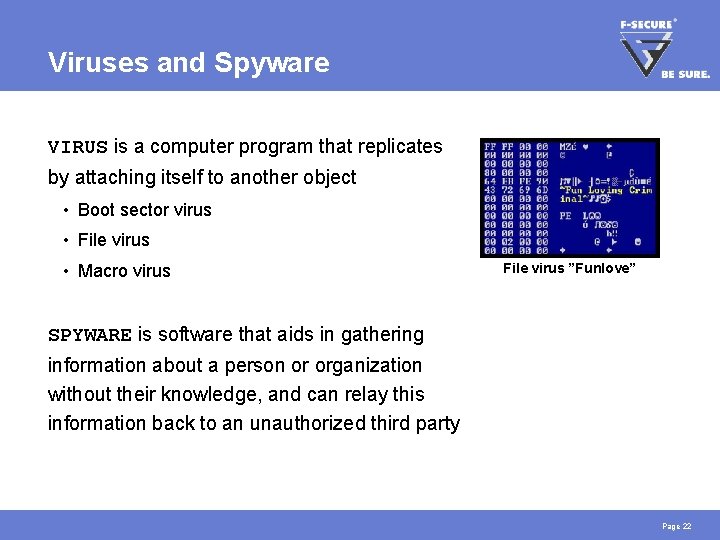
Viruses and Spyware VIRUS is a computer program that replicates by attaching itself to another object • Boot sector virus • File virus • Macro virus File virus ”Funlove” SPYWARE is software that aids in gathering information about a person or organization without their knowledge, and can relay this information back to an unauthorized third party Page 22

Summary In this section • Network threats • Worms • Hackers • Security holes • Social engineering Page 23