Network Standards Layered Architectures Chapter 2 Updated January




![Figure 2 -3: Syntax of HTTP Request and Response Messages • [CRLF] – Carriage Figure 2 -3: Syntax of HTTP Request and Response Messages • [CRLF] – Carriage](https://slidetodoc.com/presentation_image/51a0dd940861cb08a15612973e61c65d/image-6.jpg)





















































- Slides: 103

Network Standards Layered Architectures Chapter 2 Updated January 2009 XU Zhengchuan Fudan University

1. Message Standards (Protocols)

Figure 2 -1: Standards Govern the Exchange of Messages • Standards – Rules of operation that allow two hardware or software processes to work together – Even if they are from different vendors • Standards Govern the Exchange of Messages – Messages must be governed by strict rules – Because computers are not intelligent Message 3

Figure 2 -1: Standards Govern the Exchange of Messages (Continued) • Standards Govern Syntax – Syntax: the organization of the message – Human example: “Susan thanked Tom” – This sentence has a subject-verb-object syntax • Standards Govern Semantics – Semantics: The meaning of the message – Human example: “Susan thanked Tom” – Humans understand the meaning of this easily 4

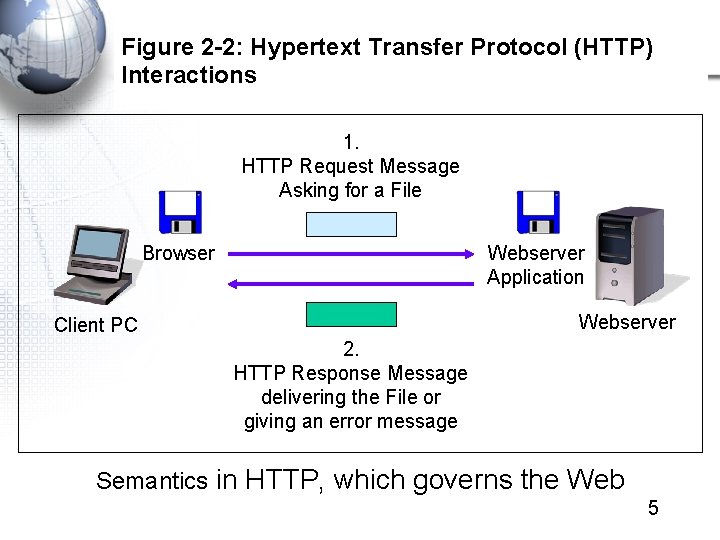
Figure 2 -2: Hypertext Transfer Protocol (HTTP) Interactions 1. HTTP Request Message Asking for a File Browser Webserver Application Webserver Client PC 2. HTTP Response Message delivering the File or giving an error message Semantics in HTTP, which governs the Web 5
![Figure 2 3 Syntax of HTTP Request and Response Messages CRLF Carriage Figure 2 -3: Syntax of HTTP Request and Response Messages • [CRLF] – Carriage](https://slidetodoc.com/presentation_image/51a0dd940861cb08a15612973e61c65d/image-6.jpg)
Figure 2 -3: Syntax of HTTP Request and Response Messages • [CRLF] – Carriage return and line feed (starts a new line) • HTTP Request Message – GET /reports/project 1/final. htm HTTP/1. 1[CRLF] • GET is the method (others exist) • Next comes the path to the file to be retrieved • Last comes the version of the HTTP standard – Host: voyager. cba. Hawaii. edu[CRLF] • The host to be sent the request message 6

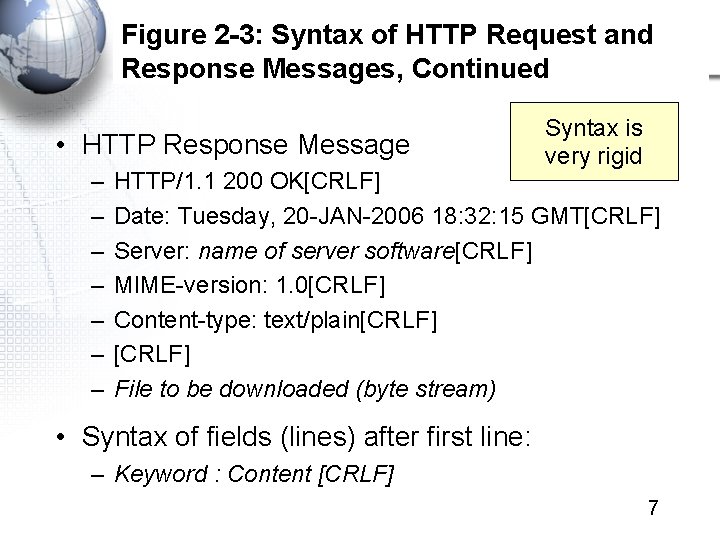
Figure 2 -3: Syntax of HTTP Request and Response Messages, Continued • HTTP Response Message – – – – Syntax is very rigid HTTP/1. 1 200 OK[CRLF] Date: Tuesday, 20 -JAN-2006 18: 32: 15 GMT[CRLF] Server: name of server software[CRLF] MIME-version: 1. 0[CRLF] Content-type: text/plain[CRLF] File to be downloaded (byte stream) • Syntax of fields (lines) after first line: – Keyword : Content [CRLF] 7

• Test Your Understanding • P 100 8

Figure 2 -1: Standards Govern the Exchange of Messages, Continued • General Message Syntax (Organization) – General Message Organization (Figure 2 -4) – Primary parts of messages • Data Field (content to be delivered) • Header (everything before the data field) • Trailer (everything after the data field) – The header and trailer act like a delivery envelope for the data field. Trailer Data Field Header 9

Figure 2 -1: Standards Govern the Exchange of Messages, Continued • General Message Syntax (Organization) – Header and trailer are further divided into fields Trailer Message with all three parts Data Field Header Other Header Field Destination Address Field is Used by Switches and Routers Like the Address on an Envelope 10

Figure 2 -4: General Message Organization, Continued Data Field Message without a trailer Header Other Header Field Destination Address Field Usually only data link layer messages have trailers 11

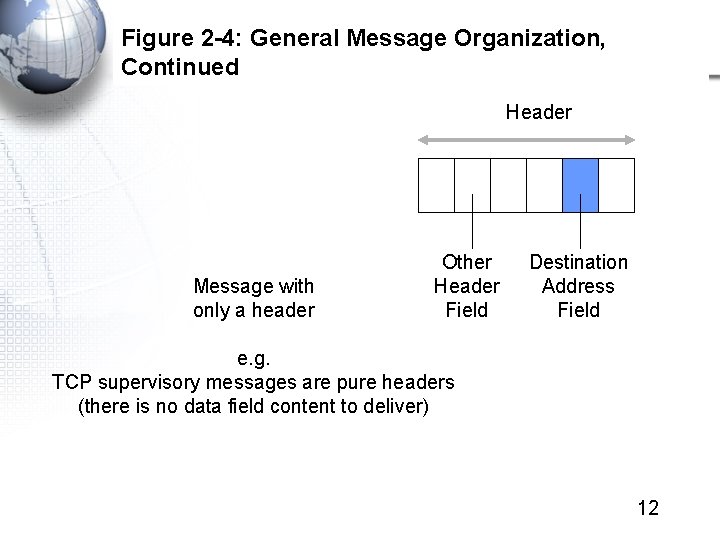
Figure 2 -4: General Message Organization, Continued Header Message with only a header Other Header Field Destination Address Field e. g. TCP supervisory messages are pure headers (there is no data field content to deliver) 12

• Test Your Understanding • P 100 13

2. Reliability

Figure 2 -5: Reliable Transmission Control Protocol (TCP) Session • The Transmission Control Protocol (TCP) is an important standard in Internet transmission • TCP – Receiver acknowledges each correctly-received TCP segment. – If an acknowledgments is not received by the sender, the sender retransmits the TCP message (called a TCP segment) – This gives reliability: error detection and error correction 15

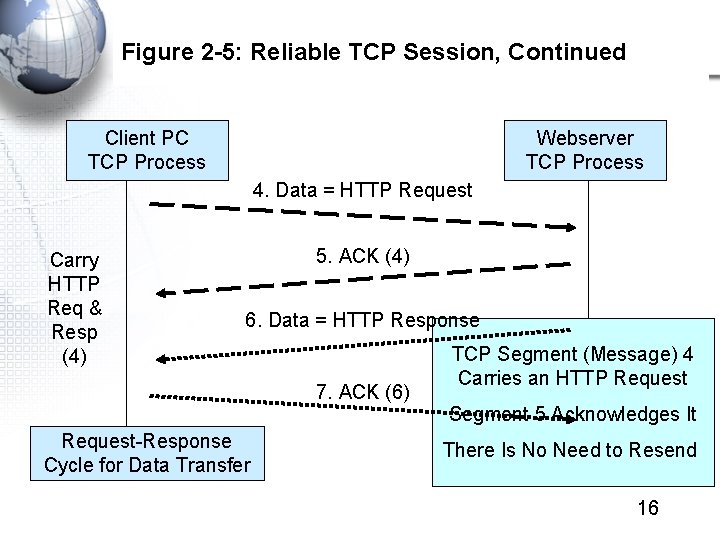
Figure 2 -5: Reliable TCP Session, Continued Client PC TCP Process Webserver TCP Process 4. Data = HTTP Request Carry HTTP Req & Resp (4) 5. ACK (4) 6. Data = HTTP Response 7. ACK (6) TCP Segment (Message) 4 Carries an HTTP Request Segment 5 Acknowledges It Request-Response Cycle for Data Transfer There Is No Need to Resend 16

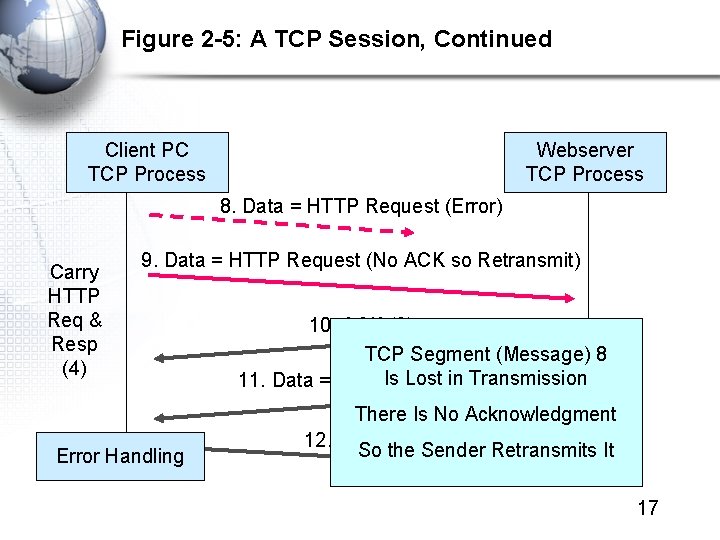
Figure 2 -5: A TCP Session, Continued Client PC TCP Process Webserver TCP Process 8. Data = HTTP Request (Error) Carry HTTP Req & Resp (4) 9. Data = HTTP Request (No ACK so Retransmit) Error Handling 10. ACK (9) TCP Segment (Message) 8 Lost in Transmission 11. Data = HTTPIs. Response There Is No Acknowledgment 12. ACK (11) So the Sender Retransmits It 17

• Test Your Understanding • P 102 18

3. Connection-Oriented and Connectionless Protocols

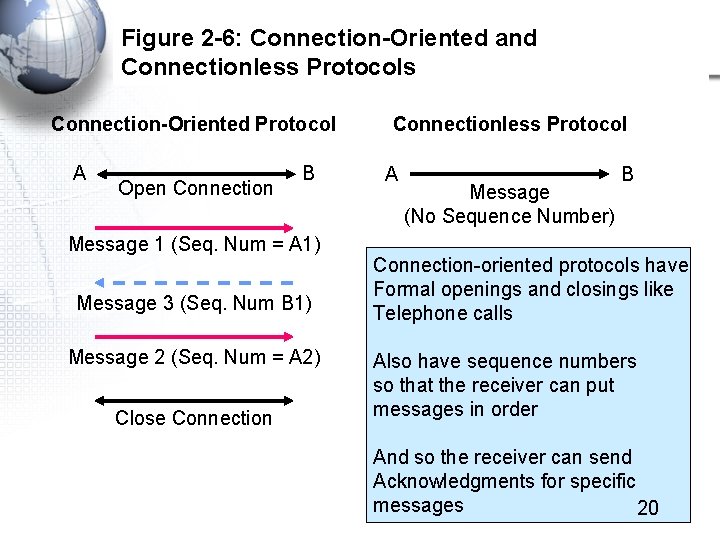
Figure 2 -6: Connection-Oriented and Connectionless Protocols Connection-Oriented Protocol A Open Connection B Message 1 (Seq. Num = A 1) Message 3 (Seq. Num B 1) Message 2 (Seq. Num = A 2) Close Connectionless Protocol A Message (No Sequence Number) B Connection-oriented protocols have Formal openings and closings like Telephone calls Also have sequence numbers so that the receiver can put messages in order And so the receiver can send Acknowledgments for specific messages 20

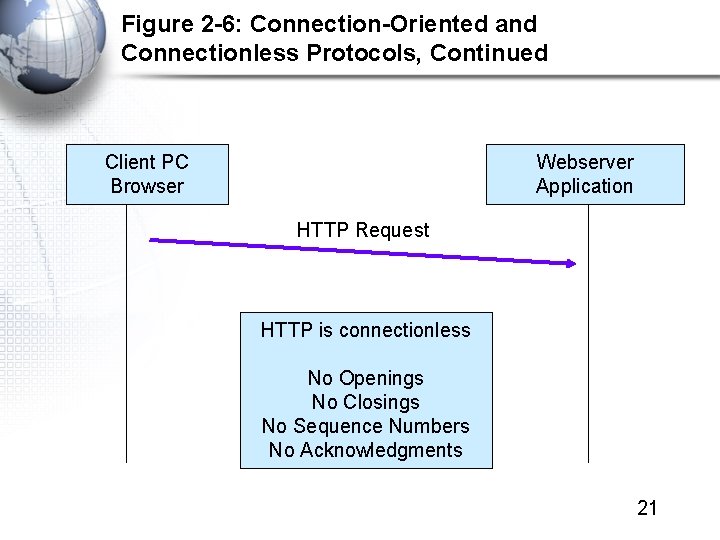
Figure 2 -6: Connection-Oriented and Connectionless Protocols, Continued Client PC Browser Webserver Application HTTP Request HTTP is connectionless No Openings No Closings No Sequence Numbers No Acknowledgments 21

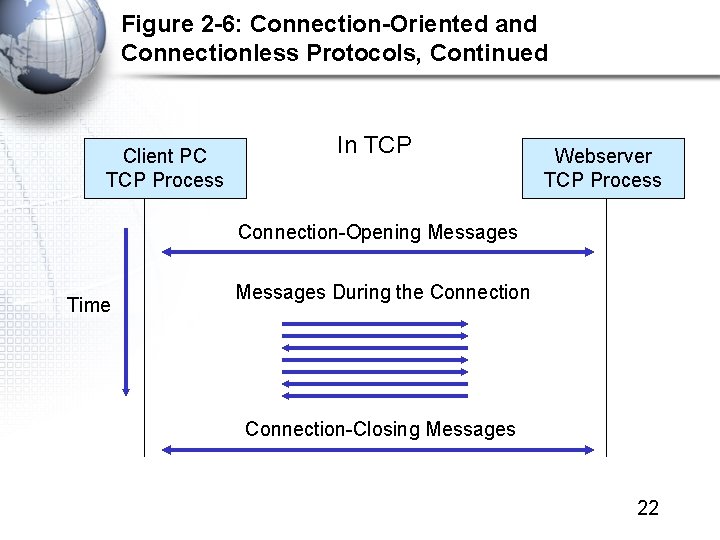
Figure 2 -6: Connection-Oriented and Connectionless Protocols, Continued Client PC TCP Process In TCP Webserver TCP Process Connection-Opening Messages Time Messages During the Connection-Closing Messages 22

Figure 2 -7: Advantages and Disadvantages or Connection-Oriented Protocols • Advantages – Thanks to sequence numbers, the parties can tell if a message is lost. – Error messages, such as ACKs can refer to specific messages. – Long messages can be fragmented into many smaller messages that can fit inside packets. • Fragmentation followed by reassembly on the destination host is an important concept in networking. 23

Figure 2 -7: Advantages and Disadvantages or Connection-Oriented Protocols, Cont. • Disadvantages – The presence of many supervisory messages consumes existing bandwidth – The processing of connection information places a heavy processing load on computers connected to the network 24

• Test Your Understanding • P 105 25

4. The Hybrid TCP/IP-OSI Standards Architecture

Standards Architecture • A Standards Architecture is a Broad Plan for Creating Standards – Break the problem of effective communication into smaller pieces for ease of development – Develop standards for the individual pieces – Just as a building architect creating a general plan for a house before designing the individual rooms in detail – The dominant architecture today is the hybrid TCP/IPOSI standards architecture shown in the next slide 27

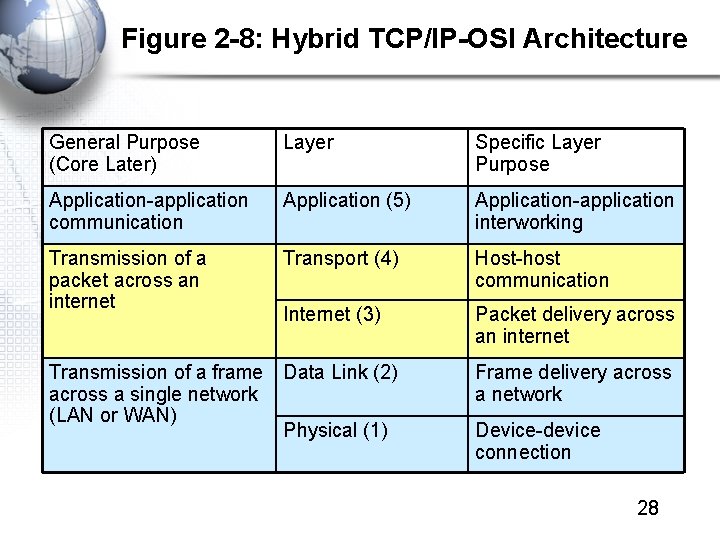
Figure 2 -8: Hybrid TCP/IP-OSI Architecture General Purpose (Core Later) Layer Specific Layer Purpose Application-application communication Application (5) Application-application interworking Transmission of a packet across an internet Transport (4) Host-host communication Internet (3) Packet delivery across an internet Transmission of a frame Data Link (2) across a single network (LAN or WAN) Physical (1) Frame delivery across a network Device-device connection 28

Figure 2 -8: Hybrid TCP/IP-OSI Architecture, Continued • Physical and Data Link Layer Standards – Govern Communication Through a Single Network – LAN or WAN 29

Figure 2 -9: Physical and Data Link Layer Standards in a Single Network • Physical Layer – Physical layer standards govern transmission between adjacent devices connected by a transmission medium Physical Link A-X 1 Host A Switch X 1 Physical Link X 1 -X 2 Switch X 2 30

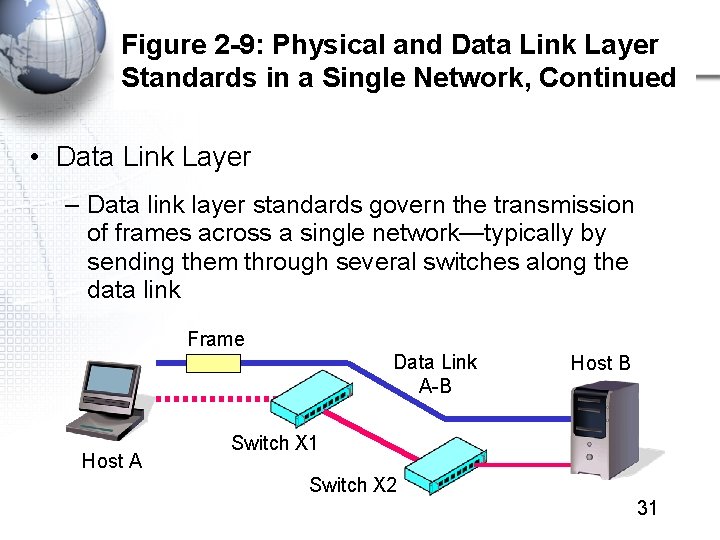
Figure 2 -9: Physical and Data Link Layer Standards in a Single Network, Continued • Data Link Layer – Data link layer standards govern the transmission of frames across a single network—typically by sending them through several switches along the data link Frame Data Link A-B Host A Host B Switch X 1 Switch X 2 31

Figure 2 -9: Physical and Data Link Layer Standards in a Single Network, Continued • Data Link Layer – Data link layer standards also govern • Frame organization • Switch operation 32

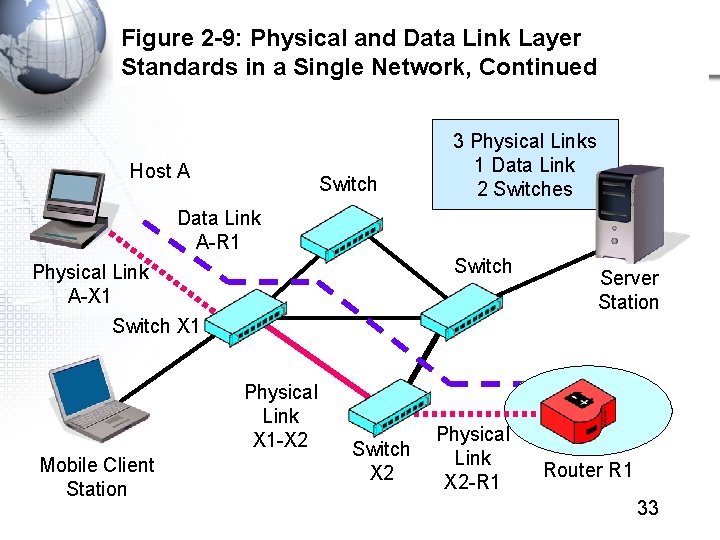
Figure 2 -9: Physical and Data Link Layer Standards in a Single Network, Continued Host A Switch 3 Physical Links 1 Data Link 2 Switches Data Link A-R 1 Switch Physical Link A-X 1 Switch X 1 Physical Link X 1 -X 2 Mobile Client Station Switch X 2 Physical Link X 2 -R 1 Server Station Router R 1 33

• Test Your Understanding • P 107 34

Figure 2 -10: Internet and Data Link Layers in an Internet • Internet and Transport Layers – An internet is a group of networks connected by routers so that any application on any host on any network can communicate with any application on any other host on any other network – Internet and transport layer standards govern communication across an internet composed of two or more single networks 35

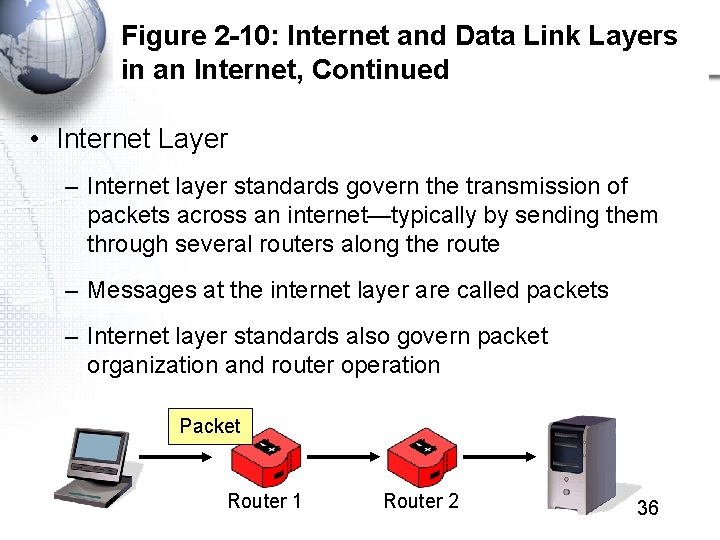
Figure 2 -10: Internet and Data Link Layers in an Internet, Continued • Internet Layer – Internet layer standards govern the transmission of packets across an internet—typically by sending them through several routers along the route – Messages at the internet layer are called packets – Internet layer standards also govern packet organization and router operation Packet Router 1 Router 2 36

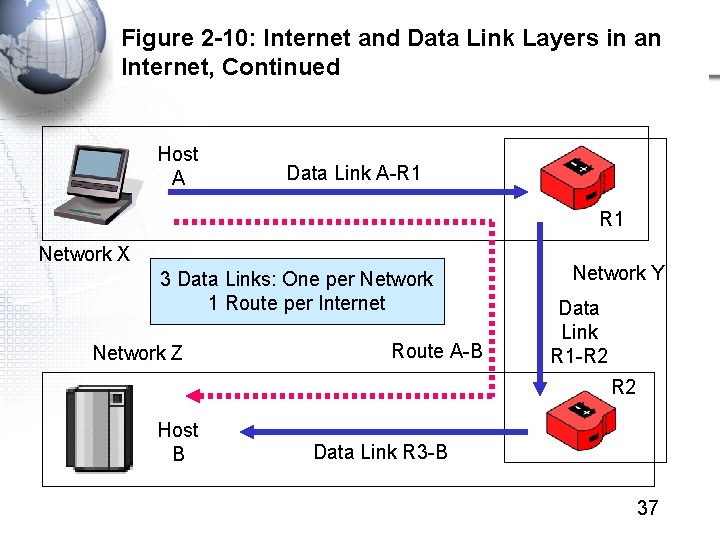
Figure 2 -10: Internet and Data Link Layers in an Internet, Continued Host A Data Link A-R 1 Network X 3 Data Links: One per Network 1 Route per Internet Network Z Route A-B Network Y Data Link R 1 -R 2 Host B Data Link R 3 -B 37

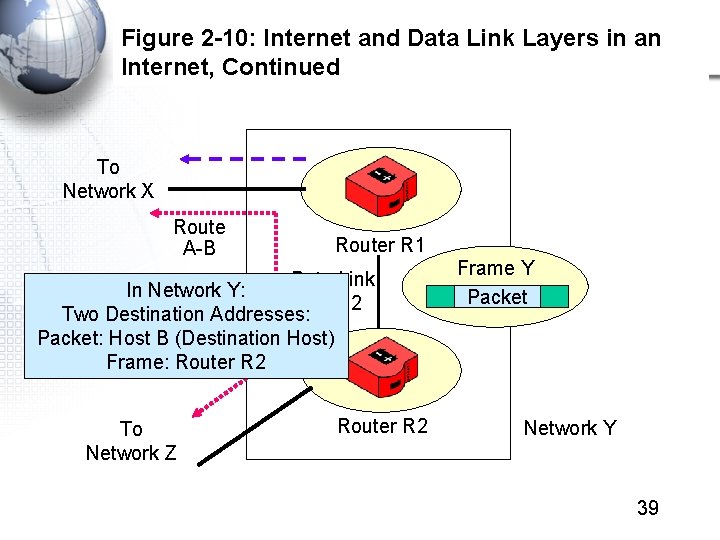
Figure 2 -10: Internet and Data Link Layers in an Internet, Continued Frame X Packet Host A Data Link A-R 1 In Network X: Switch Two Destination Addresses: Packet: Switch Host B (Destination Host) Server Frame: Router Station R 1 Switch X 1 Mobile Client Station Switch X 2 Route A-B Router R 1 Network X 38

Figure 2 -10: Internet and Data Link Layers in an Internet, Continued To Network X Route A-B Router R 1 Data Link In Network Y: R 1 -R 2 Two Destination Addresses: Packet: Host B (Destination Host) Frame: Router R 2 To Network Z Router R 2 Frame Y Packet Network Y 39

Figure 2 -10: Internet and Data Link Layers in an Internet, Continued Data Link R 2 -B Frame Z Packet Switch Z 1 Host B Router R 2 In Network Z: Two Destination. Switch Addresses: Packet: Host B (Destination Host) Z 2 Frame: Host B Mobile Client Stations Switch X 2 Router Network Z 40

Frames and Packets • In an internet with hosts separated by N networks, there will be: – 2 hosts – One packet (going all the way between hosts) – One route (between the two hosts) – N frames (one in each network) – There usually are many switches within single networks – There usually are many physical links within networks 41

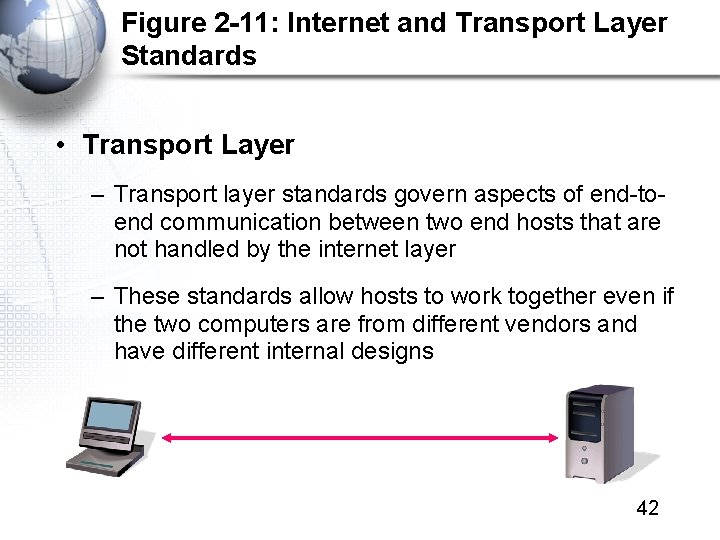
Figure 2 -11: Internet and Transport Layer Standards • Transport Layer – Transport layer standards govern aspects of end-toend communication between two end hosts that are not handled by the internet layer – These standards allow hosts to work together even if the two computers are from different vendors and have different internal designs 42

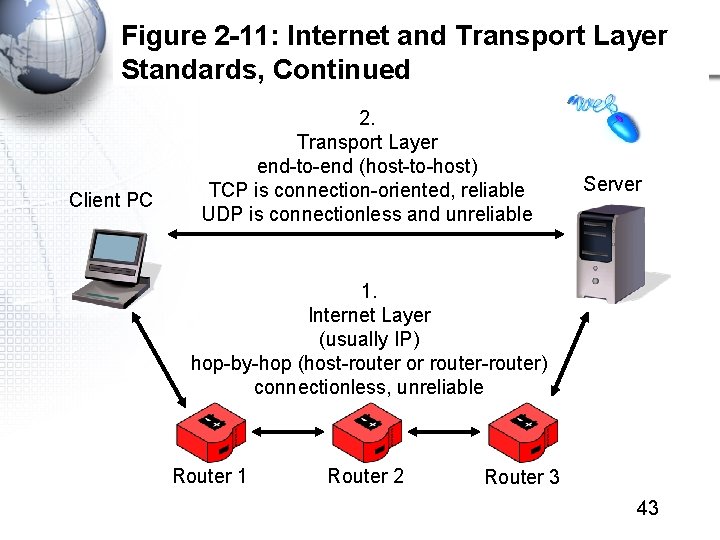
Figure 2 -11: Internet and Transport Layer Standards, Continued Client PC 2. Transport Layer end-to-end (host-to-host) TCP is connection-oriented, reliable UDP is connectionless and unreliable Server 1. Internet Layer (usually IP) hop-by-hop (host-router or router-router) connectionless, unreliable Router 1 Router 2 Router 3 43

• Test Your Understanding • P 110 44

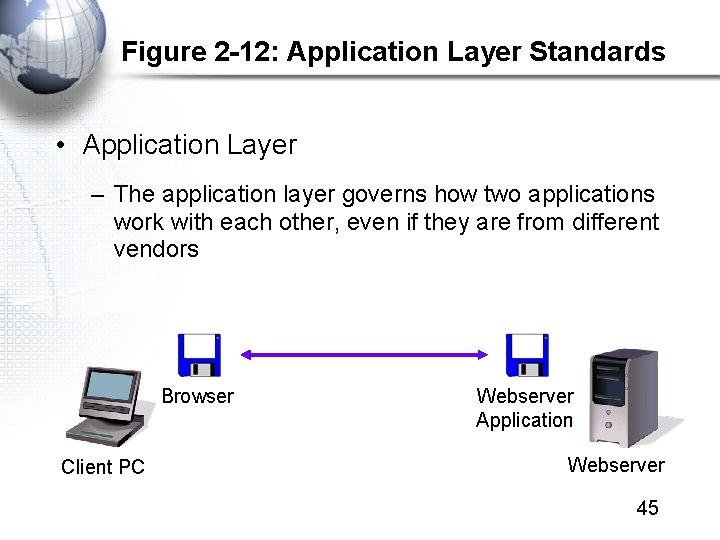
Figure 2 -12: Application Layer Standards • Application Layer – The application layer governs how two applications work with each other, even if they are from different vendors Browser Client PC Webserver Application Webserver 45

Figure 2 -12: Application Layer Standards • There are more application layer standards than any other type of standard because there are many applications – HTTP – E-Mail – Database – Instant Messaging – FTP – Etc. 46

• Test Your Understanding • P 111 47

Standards Layers: Recap • Application (5) Be able to repeat this in your sleep! • Transport (4) • Internet (3) • Data Link (2) • Physical (1) 48

• Why Layered Architectures? • Page 111 49

5. Syntax Examples for Some Layer Messages

Octets • Field length may be measured in octets • An octet is a group of eight bits • In computer science, an octet is called a byte Octet = 8 Bits 10010111 51

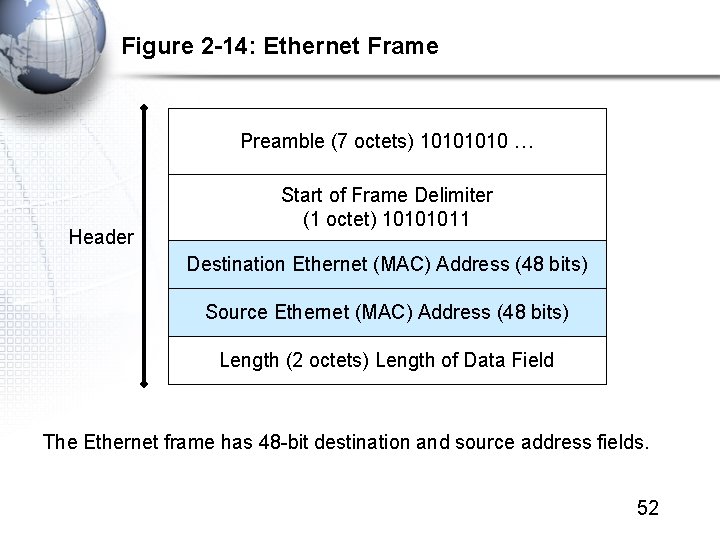
Figure 2 -14: Ethernet Frame Preamble (7 octets) 1010 … Header Start of Frame Delimiter (1 octet) 10101011 Destination Ethernet (MAC) Address (48 bits) Source Ethernet (MAC) Address (48 bits) Length (2 octets) Length of Data Field The Ethernet frame has 48 -bit destination and source address fields. 52

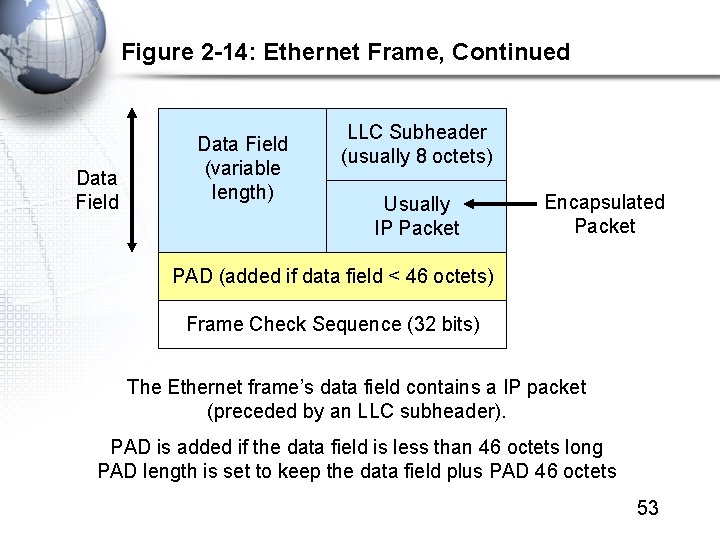
Figure 2 -14: Ethernet Frame, Continued Data Field (variable length) LLC Subheader (usually 8 octets) Usually IP Packet Encapsulated Packet PAD (added if data field < 46 octets) Frame Check Sequence (32 bits) The Ethernet frame’s data field contains a IP packet (preceded by an LLC subheader). PAD is added if the data field is less than 46 octets long PAD length is set to keep the data field plus PAD 46 octets 53

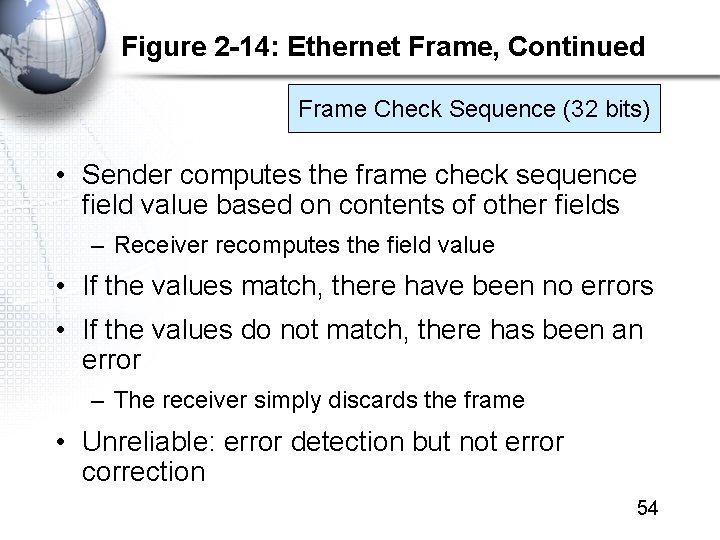
Figure 2 -14: Ethernet Frame, Continued Frame Check Sequence (32 bits) • Sender computes the frame check sequence field value based on contents of other fields – Receiver recomputes the field value • If the values match, there have been no errors • If the values do not match, there has been an error – The receiver simply discards the frame • Unreliable: error detection but not error correction 54

• Test Your Understanding • P 115 12 -15 55

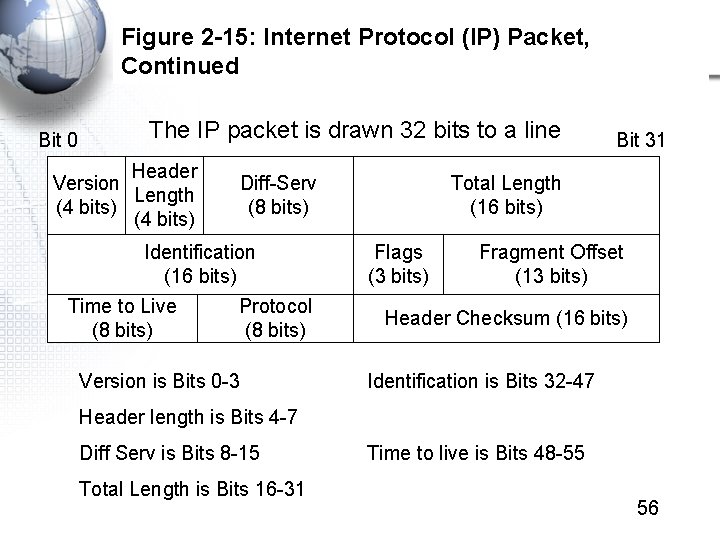
Figure 2 -15: Internet Protocol (IP) Packet, Continued Bit 0 The IP packet is drawn 32 bits to a line Header Version Length (4 bits) Diff-Serv (8 bits) Identification (16 bits) Time to Live (8 bits) Protocol (8 bits) Version is Bits 0 -3 Bit 31 Total Length (16 bits) Flags (3 bits) Fragment Offset (13 bits) Header Checksum (16 bits) Identification is Bits 32 -47 Header length is Bits 4 -7 Diff Serv is Bits 8 -15 Total Length is Bits 16 -31 Time to live is Bits 48 -55 56

Figure 2 -15: Internet Protocol (IP) Packet Bit 0 Version Bit 31 Header Length Diff-Serv Identification Time to Live Protocol Total Length Flags Fragment Offset Header Checksum Source IP Address (32 bits) Destination IP Address (32 bits) Options (if any) Padding (to 32 -bit boundary) Data Field (dozens, hundreds, or thousands of bits) Often contains a TCP segment 57

• Test Your Understanding • P 116 -117, 16 -18 58

Figure 2 -16: TCP and UDP at the Transport Layer • TCP is reliable • Not all applications need reliability – Voice over IP cannot wait for lost or damaged packets to be transmitted – Network management protocols need to place as low a burden on the network as possible – Both types of applications use the simpler User Datagram Protocol (UDP) instead of TCP 59

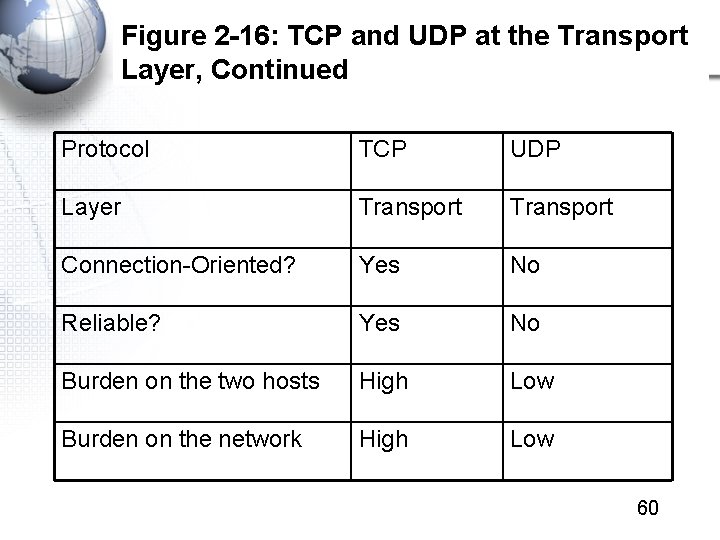
Figure 2 -16: TCP and UDP at the Transport Layer, Continued Protocol TCP UDP Layer Transport Connection-Oriented? Yes No Reliable? Yes No Burden on the two hosts High Low Burden on the network High Low 60

Why Make TCP Reliable? • Two reasons: • 1. The transport layer only involves processing on the two hosts. – Reliability is a heavy process. – It would be far more expensive to make the internet or data link layer reliable because this would require complex processing on many routers or switches, respectively. • 2. TCP’s reliability fixes errors at the transport layer and all lower layers in the process. This allows the transport layer to give the application clean data. 61

Figure 2 -17: A Complex Application Protocol: The Simple Mail Transfer Protocol (SMTP) • Some application protocols are simple – HTTP: Simple request-response message cycle shown in Figure 2 -2 • Some application protocols are complex (Figure 217) – Simple Mail Transfer Protocol (SMTP) for e-mail – More than a dozen messages must be exchanged to send an e-mail message 62

• Test Your Understanding • P 119 -121, 19 -22 63

6. Vertical Communication Between Layer Processes on the Same Host

Figure 2 -18: Layered Communication on the Source Host The process begins when a browser creates an HTTP request message Application Process HTTP Message Passes Message Down to Transport Process HTTP TCP Message Hdr Encapsulation of HTTP Message in Data Field of TCP Segment 65

Figure 2 -18: Layered Communication on the Source Host, Continued • When a layer process (N) creates a message, it passes it down to the nextlower-layer process (N-1) immediately • The receiving process (N-1) will encapsulate the Layer N message, that is, place it in the data field of its own (N-1) message 66

Figure 2 -18: Layered Communication on the Source Host, Continued Transport Process Internet Process HTTP TCP Message Hdr HTTP TCP IP Message Hdr Encapsulation of TCP Segment in Data Field of IP Packet 67

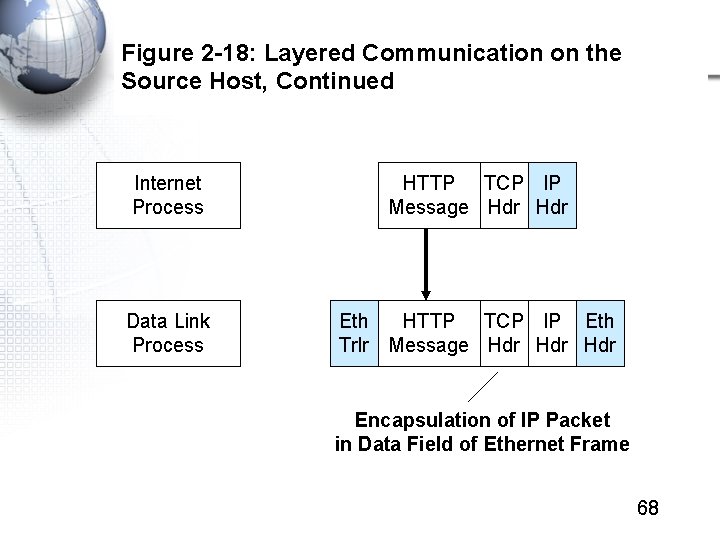
Figure 2 -18: Layered Communication on the Source Host, Continued Internet Process HTTP TCP IP Message Hdr Data Link Process Eth HTTP TCP IP Eth Trlr Message Hdr Hdr Encapsulation of IP Packet in Data Field of Ethernet Frame 68

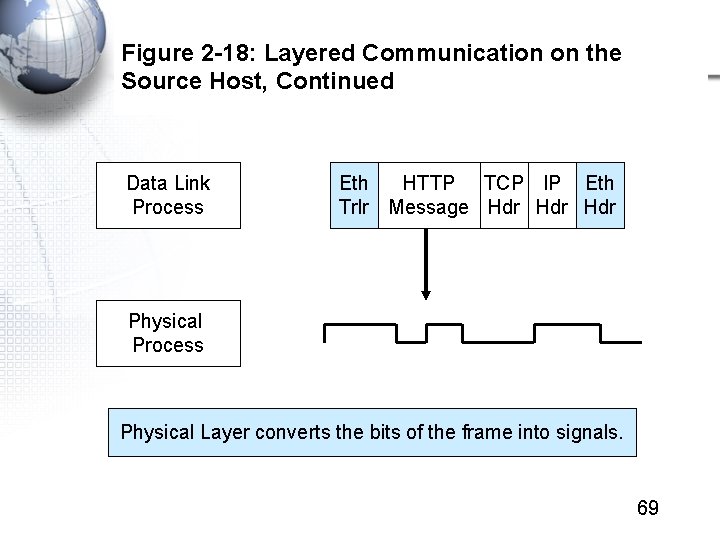
Figure 2 -18: Layered Communication on the Source Host, Continued Data Link Process Eth HTTP TCP IP Eth Trlr Message Hdr Hdr Physical Process Physical Layer converts the bits of the frame into signals. 69

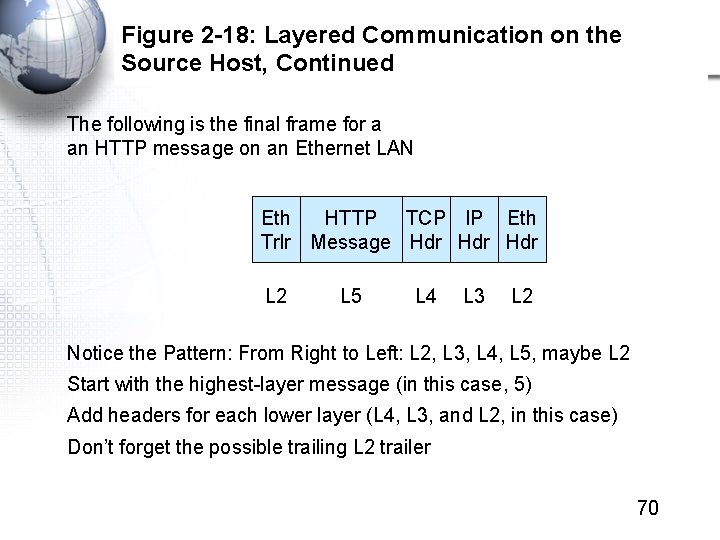
Figure 2 -18: Layered Communication on the Source Host, Continued The following is the final frame for a an HTTP message on an Ethernet LAN Eth HTTP TCP IP Eth Trlr Message Hdr Hdr L 2 L 5 L 4 L 3 L 2 Notice the Pattern: From Right to Left: L 2, L 3, L 4, L 5, maybe L 2 Start with the highest-layer message (in this case, 5) Add headers for each lower layer (L 4, L 3, and L 2, in this case) Don’t forget the possible trailing L 2 trailer 70

• Test Your Understanding • P 124 23 71

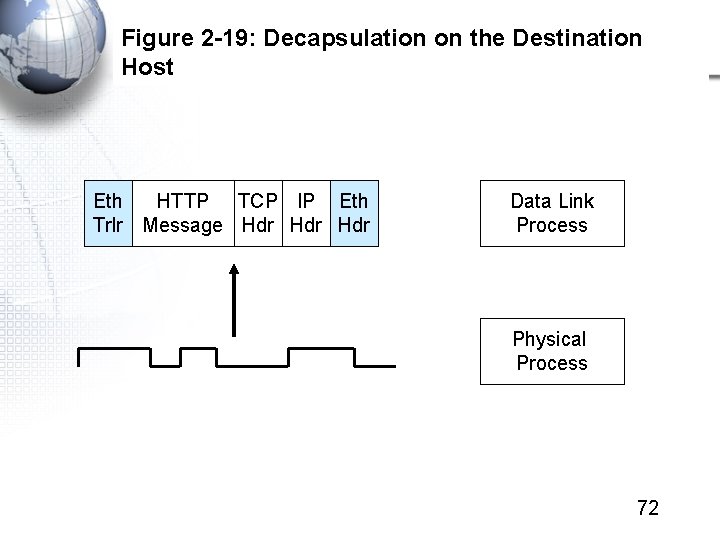
Figure 2 -19: Decapsulation on the Destination Host Eth HTTP TCP IP Eth Trlr Message Hdr Hdr Data Link Process Physical Process 72

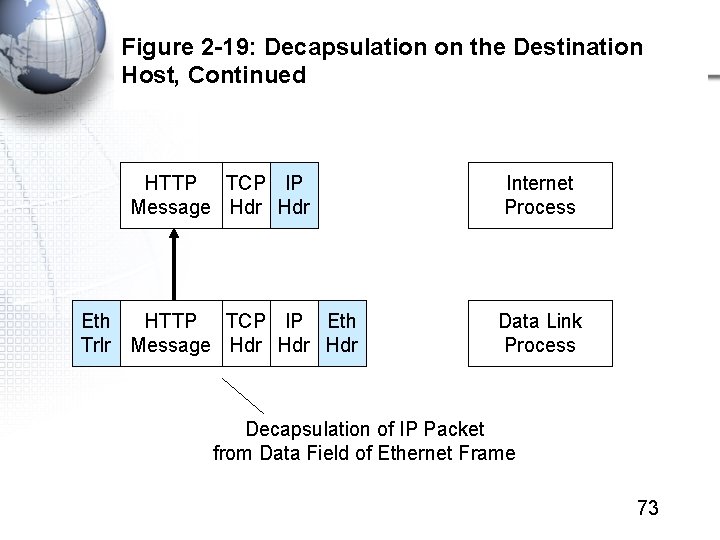
Figure 2 -19: Decapsulation on the Destination Host, Continued HTTP TCP IP Message Hdr Internet Process Eth HTTP TCP IP Eth Trlr Message Hdr Hdr Data Link Process Decapsulation of IP Packet from Data Field of Ethernet Frame 73

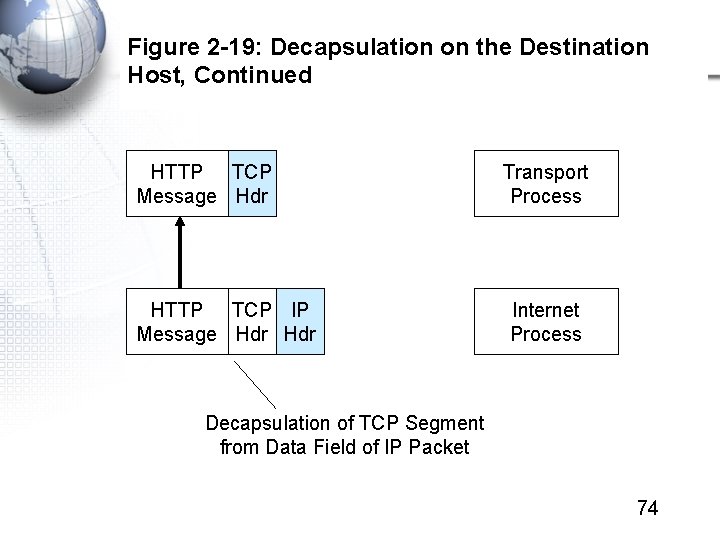
Figure 2 -19: Decapsulation on the Destination Host, Continued HTTP TCP Message Hdr HTTP TCP IP Message Hdr Transport Process Internet Process Decapsulation of TCP Segment from Data Field of IP Packet 74

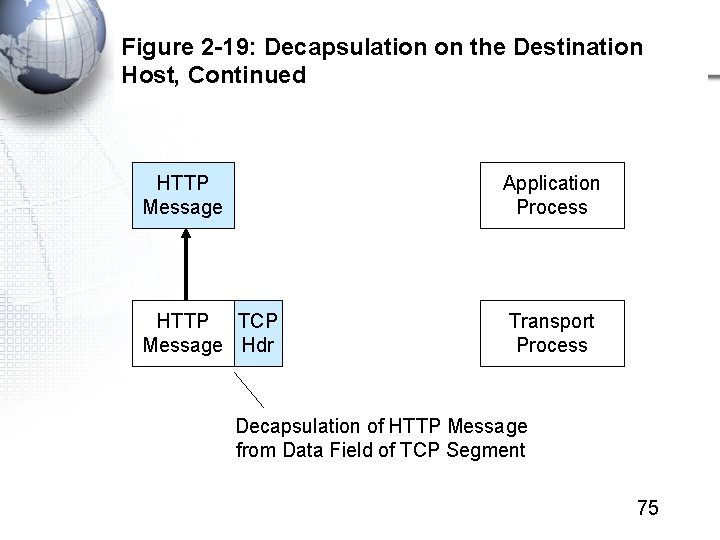
Figure 2 -19: Decapsulation on the Destination Host, Continued HTTP Message Application Process HTTP TCP Message Hdr Transport Process Decapsulation of HTTP Message from Data Field of TCP Segment 75

• Test Your Understanding • P 126 24 76

Figure 2 -20: Layered End-to-End Communication Source and Destination Hosts Have 5 Layers App Trans Int DL Phy Source Host Switches Have Two Layers --Each Switch Port Has One Layer (1) Switch 1 Switch 2 Routers Have Three Layers --Each Router Port Has Two Layers (1&2) Router 1 Switch 3 Router Destination 2 Host 77

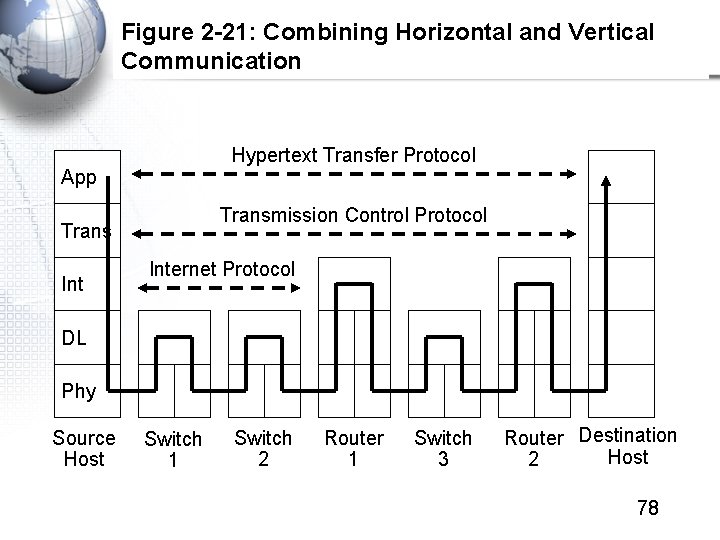
Figure 2 -21: Combining Horizontal and Vertical Communication Hypertext Transfer Protocol App Transmission Control Protocol Trans Internet Protocol DL Phy Source Host Switch 1 Switch 2 Router 1 Switch 3 Router Destination Host 2 78

• Test Your Understanding • P 127 25 -26 79

7. OSI, TCP/IP, and Other Standards Architectures

Figure 2 -22: The Hybrid TCP/IP-OSI Architecture Broad Purpose Hybrid TCP/IP-OSI Communication between applications Internetworking Transmission within a single LAN or WAN TCP/IP Application (Layer 5) Presentation Application Session Transport (Layer 4) Transport Internet (Layer 3) Network Internet Data Link (Layer 2) Data Link Physical (Layer 1) Physical Use OSI Standards Here 81

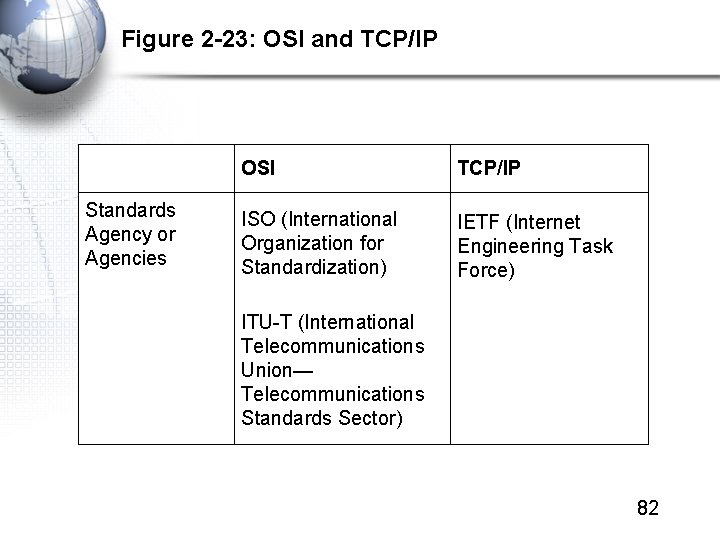
Figure 2 -23: OSI and TCP/IP Standards Agency or Agencies OSI TCP/IP ISO (International Organization for Standardization) IETF (Internet Engineering Task Force) ITU-T (International Telecommunications Union— Telecommunications Standards Sector) 82

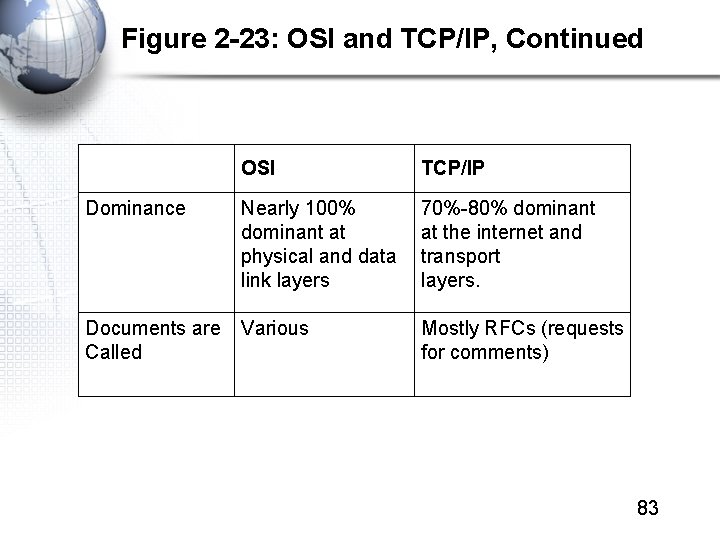
Figure 2 -23: OSI and TCP/IP, Continued OSI TCP/IP Dominance Nearly 100% dominant at physical and data link layers 70%-80% dominant at the internet and transport layers. Documents are Called Various Mostly RFCs (requests for comments) 83

Figure 2 -24: OSI Layers • Layer 1: OSI Physical Layer Standards – Nearly always used in the hybrid TCP/IP-OSI architecture • Layer 2: OSI Data Link Layer Standards – Nearly always used in the hybrid TCP/IP-OSI architecture 84

Figure 2 -24: OSI Layers, Continued • Layer 3: OSI Network Layer Standards – Same function as internet layer standards in TCP/IP – But OSI network layer standards are incompatible with TCP/IP internet layer standards – Rarely used • Layer 4: OSI Transport Layer Standards – Same function as transport layer in TCP/IP – But OSI transport layer standards are incompatible with TCP/IP transport layer standards – Rarely used 85

Figure 2 -24: OSI Layers, Continued • Layer 5: OSI Session Layer Standards – Initiate and maintain a connection between application programs on different computers – Nothing like this layer in TCP/IP – Rarely used because OSI is rarely used above the data link layer and below the application layer 86

Figure 2 -24: OSI Layers, Continued • Layer 6: OSI Presentation Layer Standards – Designed to handle data formatting differences between the computers, data compression, and encryption. • Rarely used this way because OSI standards are rarely used above the data link layer and below the application layer – In practice, a category for general OSI file format standards used in multiple applications • JPEG, etc. • These standards are widely used 87

Figure 2 -24: OSI Layers, Continued • Layer 7: OSI Application Layer – For other application-specific matters – Some OSI application layer standards are used • Run over TCP/IP transport/internet layer processes • Almost always without actual session and presentation layer processes 88

Figure 2 -25: Other Major Standards Architectures • IPX/SPX – Used by older Novell Net. Ware file servers – Popular option for newer Novell Net. Ware file servers • SNA (Systems Network Architecture) – Used by IBM mainframe computers • Apple. Talk – Used by Apple Macintoshes 89

Figure 2 -26: Characteristics of Protocols Discussed in the Chapter Layer Protocol Connection. Oriented /Connectionless Reliable/ Unreliable 5 (App) HTTP Connectionless Unreliable 4 (Transport) TCP Connectionoriented Reliable 4 (Transport) UDP Connectionless Unreliable 3 (Internet) IP Connectionless Unreliable 2 (Data Link) Ethernet Connectionless Unreliable Note: Only TCP is connection-oriented and reliable 90

• Case study • Chp 1 a page 42 • Chp 1 c page 77 91

8. Topics Covered

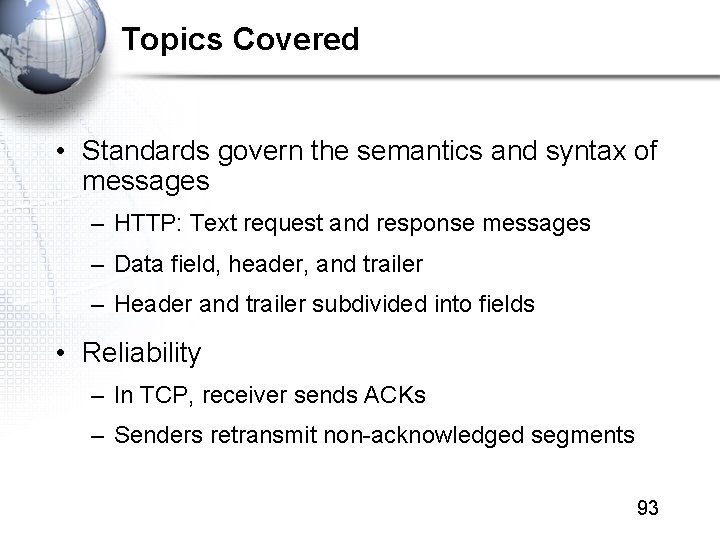
Topics Covered • Standards govern the semantics and syntax of messages – HTTP: Text request and response messages – Data field, header, and trailer – Header and trailer subdivided into fields • Reliability – In TCP, receiver sends ACKs – Senders retransmit non-acknowledged segments 93

Topics Covered • Connection-oriented versus connectionless – TCP is connection-oriented – HTTP is connectionless • Hybrid TCP/IP-OSI Architecture – OSI is nearly 100% dominant at Layers 1 and 2 – TCP/IP is 70% to 80% dominant at Layers 3 and 4 – Situation at Layer 5 is complex 94

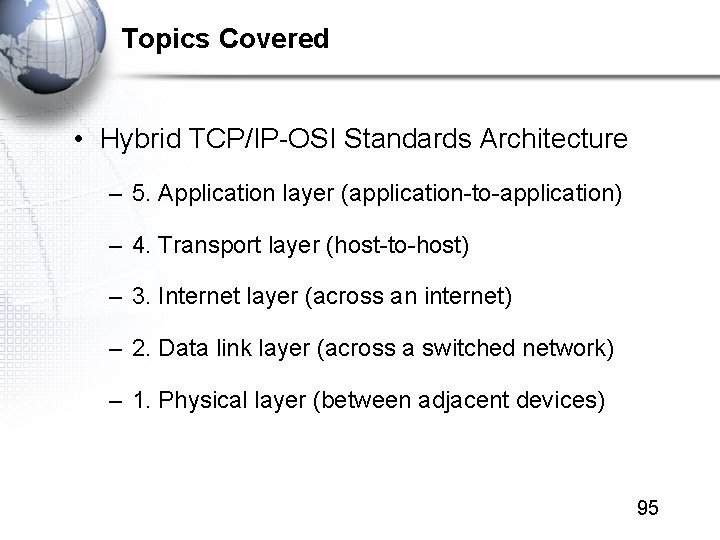
Topics Covered • Hybrid TCP/IP-OSI Standards Architecture – 5. Application layer (application-to-application) – 4. Transport layer (host-to-host) – 3. Internet layer (across an internet) – 2. Data link layer (across a switched network) – 1. Physical layer (between adjacent devices) 95

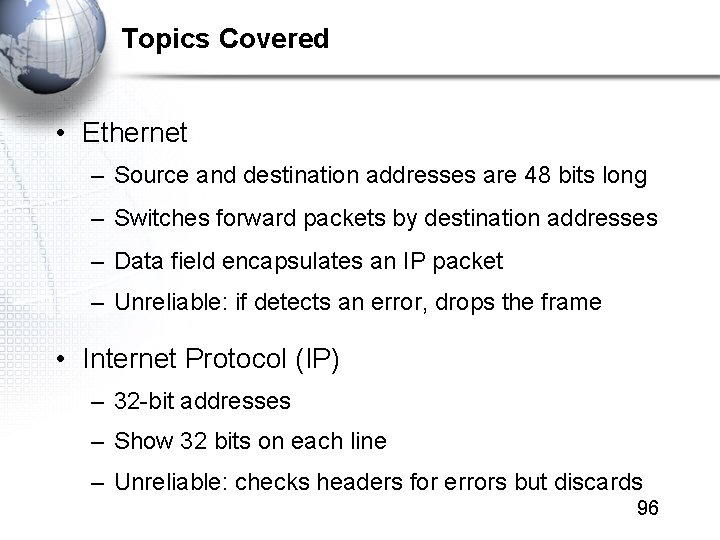
Topics Covered • Ethernet – Source and destination addresses are 48 bits long – Switches forward packets by destination addresses – Data field encapsulates an IP packet – Unreliable: if detects an error, drops the frame • Internet Protocol (IP) – 32 -bit addresses – Show 32 bits on each line – Unreliable: checks headers for errors but discards 96

Topics Covered • Vertical Communication on the Source Host – Layer process creates message and then sends the message to the next-lower layer – Next-lower layer encapsulates the message in its own message – This continues until the final frame at the data link layer • Vertical Communication on the Destination Host – Decapsulation and passing up 97

Topics Covered • Not All Devices Have All Layers – Hosts have all five – Routers have only the lowest three – Switches have only the lowest two 98

Topics Covered • OSI Architecture – Divides application layer into three layers • Session • Presentation • Application • Other Standards Architectures – IPX/SPX – SNA – Apple. Talk 99



