Network Standards Chapter 3 Updated January 2009 Raymond














- Slides: 81

Network Standards Chapter 3 Updated January 2009 Raymond Panko’s Business Data Networks and Telecommunications, 7 th edition May only be used by adopters of the book © 2009 Pearson Education, Inc. Publishing as Prentice Hall

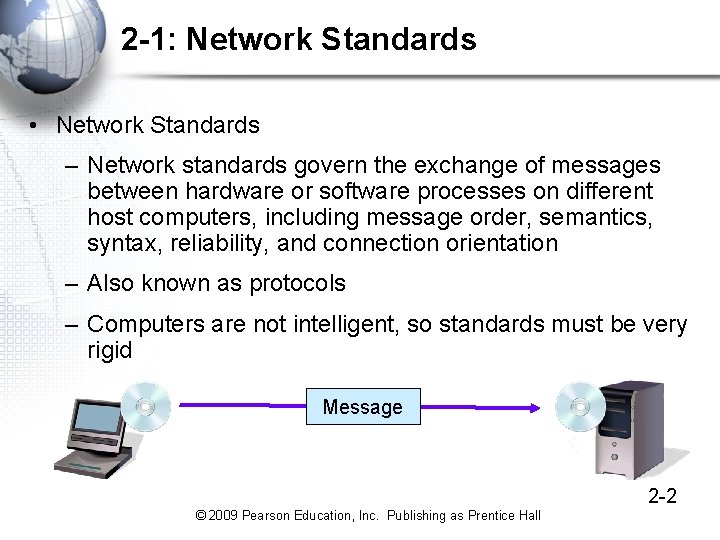
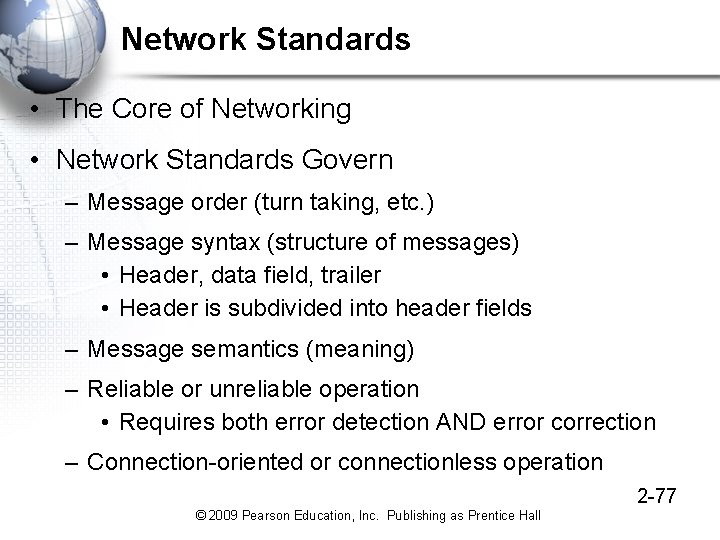
2 -1: Network Standards • Network Standards – Network standards govern the exchange of messages between hardware or software processes on different host computers, including message order, semantics, syntax, reliability, and connection orientation – Also known as protocols – Computers are not intelligent, so standards must be very rigid Message 2 -2 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

1. Message Standards (Protocols) Message syntax Message semantics Message order © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -1: Network Standards • Network Standards Govern – Message Syntax (organization) • Like human grammar, but more rigid • Header, data field, and trailer (Figure 2 -2) – Message order • Turn taking, order of messages in a complex transaction, who must initiate communication, etc. – Message semantics (meaning) • HTTP request message: “Please give me this file” • HTTP response message: Here is the file. (Or, I could not comply for the following reason) 2 -4 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

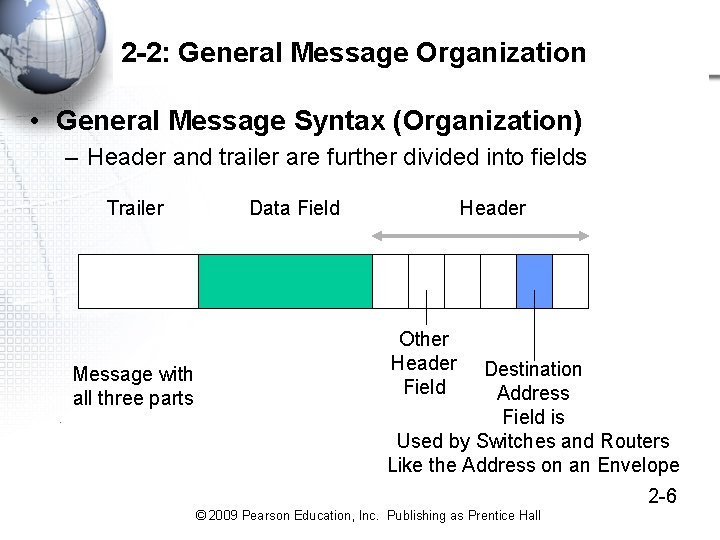
2 -2: General Message Organization • General Message Syntax (Organization) – General Message Organization (Figure 2 -4) – Primary parts of messages • Data Field (content to be delivered) • Header (everything before the data field) • Trailer (everything after the data field) – The header and trailer act like a delivery envelope for the data field Trailer Data Field Header 2 -5 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -2: General Message Organization • General Message Syntax (Organization) – Header and trailer are further divided into fields Trailer Message with all three parts Data Field Header Other Header Field Destination Address Field is Used by Switches and Routers Like the Address on an Envelope 2 -6 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

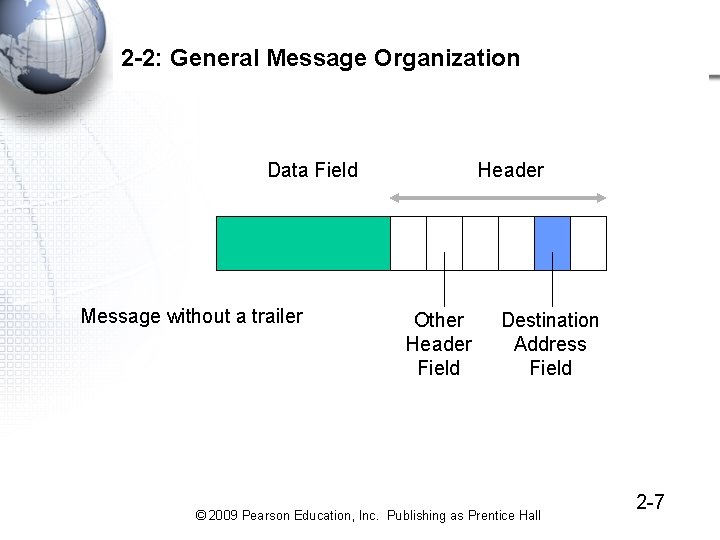
2 -2: General Message Organization Data Field Message without a trailer Header Other Header Field Destination Address Field © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -7

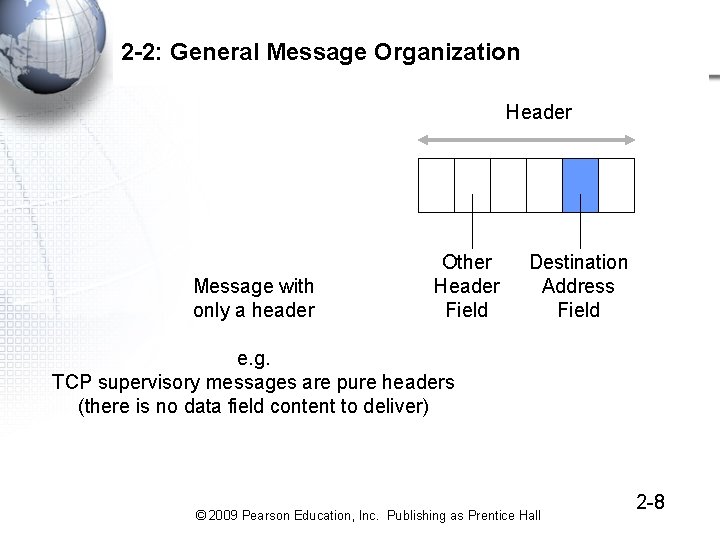
2 -2: General Message Organization Header Message with only a header Other Header Field Destination Address Field e. g. TCP supervisory messages are pure headers (there is no data field content to deliver) © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -8

2. Reliability Error Detection and Correction © 2009 Pearson Education, Inc. Publishing as Prentice Hall

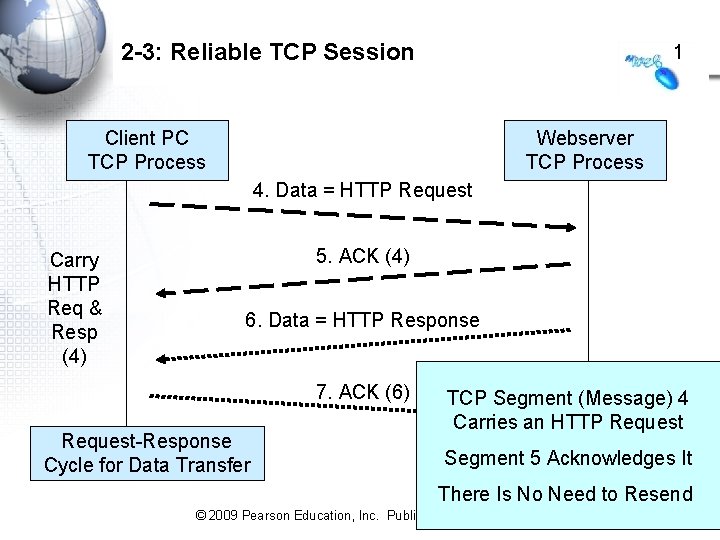
2 -3: Reliable Transmission Control Protocol (TCP) Session 2 • The Transmission Control Protocol (TCP) is an important standard in Internet transmission • TCP – Receiver acknowledges each correctly-received TCP message (called a TCP segment) – If an acknowledgments is not received by the sender, the sender retransmits the TCP segment – This gives reliability: error detection AND error correction 2 -10 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -3: Reliable TCP Session 1 Client PC TCP Process Webserver TCP Process 4. Data = HTTP Request Carry HTTP Req & Resp (4) 5. ACK (4) 6. Data = HTTP Response 7. ACK (6) Request-Response Cycle for Data Transfer TCP Segment (Message) 4 Carries an HTTP Request Segment 5 Acknowledges It There Is No Need to Resend 2 -11 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

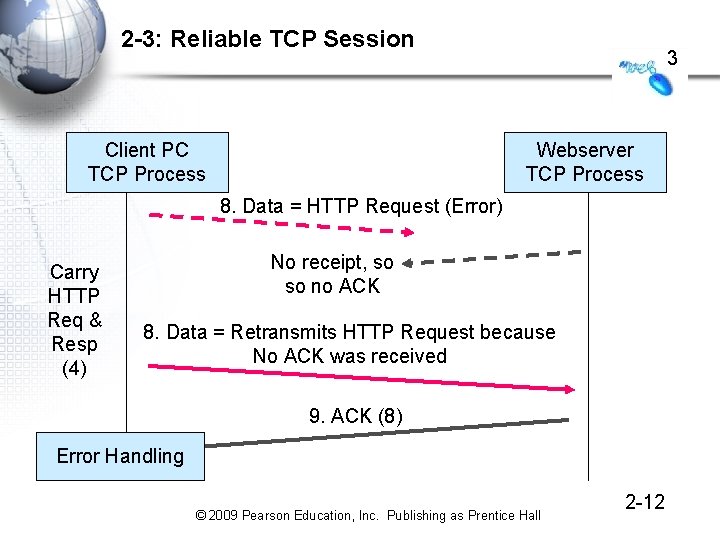
2 -3: Reliable TCP Session Client PC TCP Process 3 Webserver TCP Process 8. Data = HTTP Request (Error) Carry HTTP Req & Resp (4) No receipt, so so no ACK 8. Data = Retransmits HTTP Request because No ACK was received 9. ACK (8) Error Handling © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -12

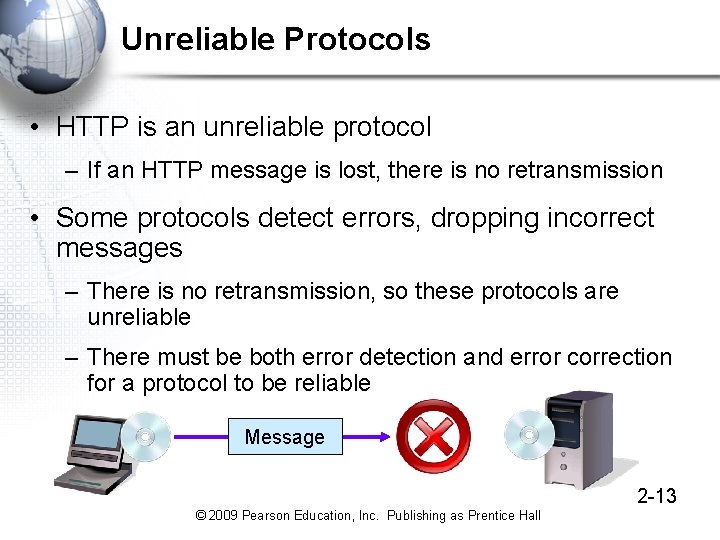
Unreliable Protocols • HTTP is an unreliable protocol – If an HTTP message is lost, there is no retransmission • Some protocols detect errors, dropping incorrect messages – There is no retransmission, so these protocols are unreliable – There must be both error detection and error correction for a protocol to be reliable Message 2 -13 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

3. Connection-Oriented and Connectionless Protocols © 2009 Pearson Education, Inc. Publishing as Prentice Hall

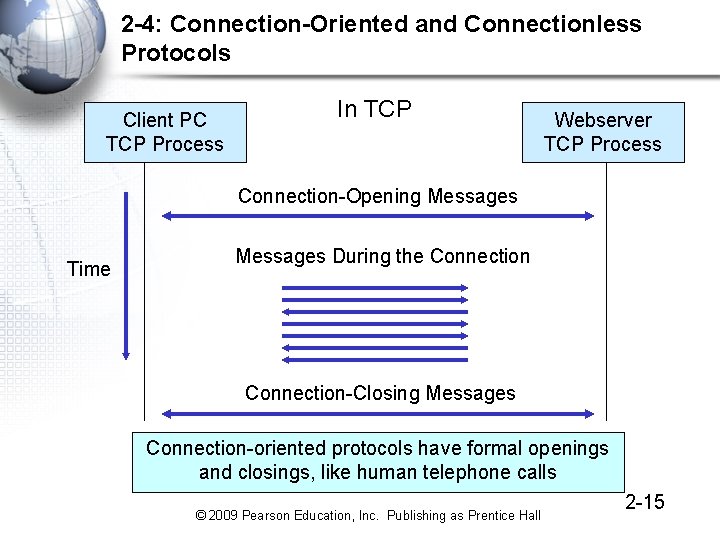
2 -4: Connection-Oriented and Connectionless Protocols Client PC TCP Process In TCP Webserver TCP Process Connection-Opening Messages Time Messages During the Connection-Closing Messages Connection-oriented protocols have formal openings and closings, like human telephone calls © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -15

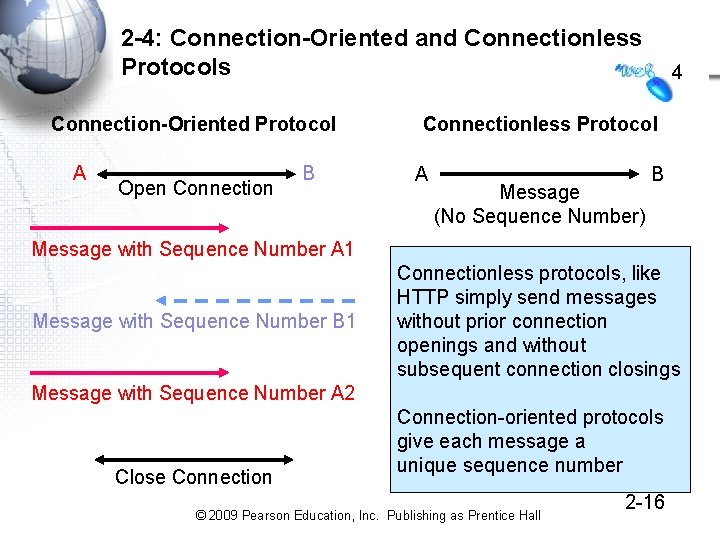
2 -4: Connection-Oriented and Connectionless Protocols Connection-Oriented Protocol A Open Connection B 4 Connectionless Protocol A Message (No Sequence Number) B Message with Sequence Number A 1 Message with Sequence Number B 1 Connectionless protocols, like HTTP simply send messages without prior connection openings and without subsequent connection closings Message with Sequence Number A 2 Close Connection-oriented protocols give each message a unique sequence number © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -16

2 -5: Advantages and Disadvantages of Connection-Oriented Protocols • Advantages – Connection-oriented protocols give each message a sequence number • Thanks to sequence numbers, the parties can tell when a message is lost (There will be a gap in the sequence numbers) • Error messages, such as ACKs, can refer to specific messages according to the sequence numbers of these messages – Long messages can be fragmented into many smaller messages that can fit inside of packets • The fragments will be given sequence numbers so that they can be assembled at the other end • Fragmentation followed by reassembly is an important concept in networking 2 -17 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

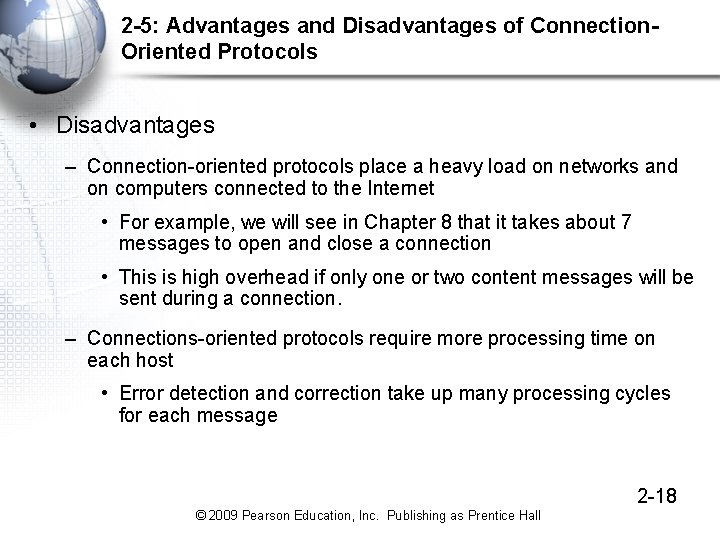
2 -5: Advantages and Disadvantages of Connection. Oriented Protocols • Disadvantages – Connection-oriented protocols place a heavy load on networks and on computers connected to the Internet • For example, we will see in Chapter 8 that it takes about 7 messages to open and close a connection • This is high overhead if only one or two content messages will be sent during a connection. – Connections-oriented protocols require more processing time on each host • Error detection and correction take up many processing cycles for each message 2 -18 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

4. The Hybrid TCP/IP-OSI Standards Architecture © 2009 Pearson Education, Inc. Publishing as Prentice Hall

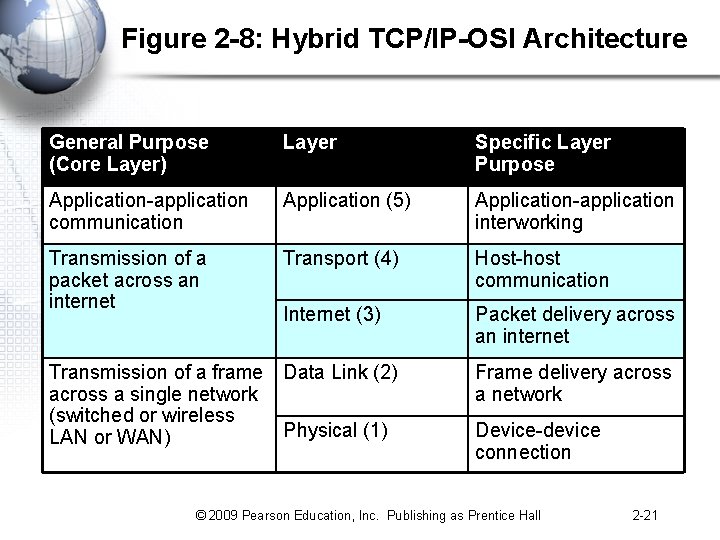
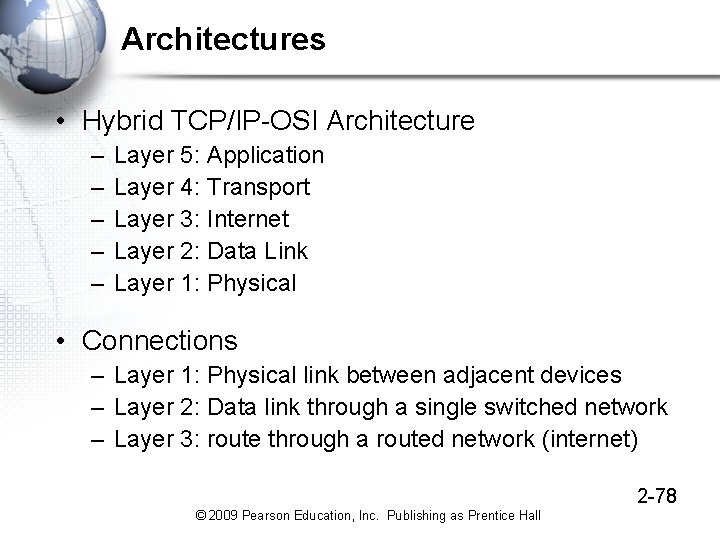
Standards Architecture • A Standards Architecture Is a Broad Plan for Creating Standards – Break the problem into smaller pieces for ease of development – Develop standards for the individual pieces • Assign individual standards to specialists in each area – The dominant architecture today is the hybrid TCP/IPOSI standards architecture shown in the next slide 2 -20 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Figure 2 -8: Hybrid TCP/IP-OSI Architecture General Purpose (Core Layer) Layer Specific Layer Purpose Application-application communication Application (5) Application-application interworking Transmission of a packet across an internet Transport (4) Host-host communication Internet (3) Packet delivery across an internet Transmission of a frame Data Link (2) across a single network (switched or wireless Physical (1) LAN or WAN) Frame delivery across a network Device-device connection © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -21

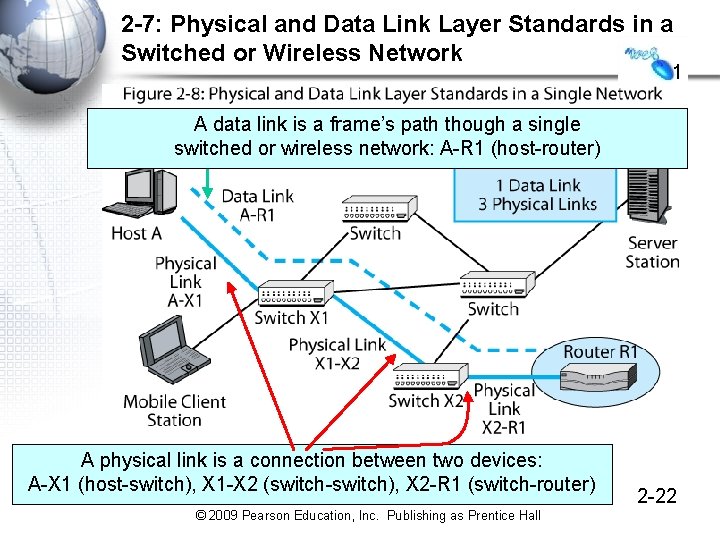
2 -7: Physical and Data Link Layer Standards in a Switched or Wireless Network 1 A data link is a frame’s path though a single switched or wireless network: A-R 1 (host-router) A physical link is a connection between two devices: A-X 1 (host-switch), X 1 -X 2 (switch-switch), X 2 -R 1 (switch-router) © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -22

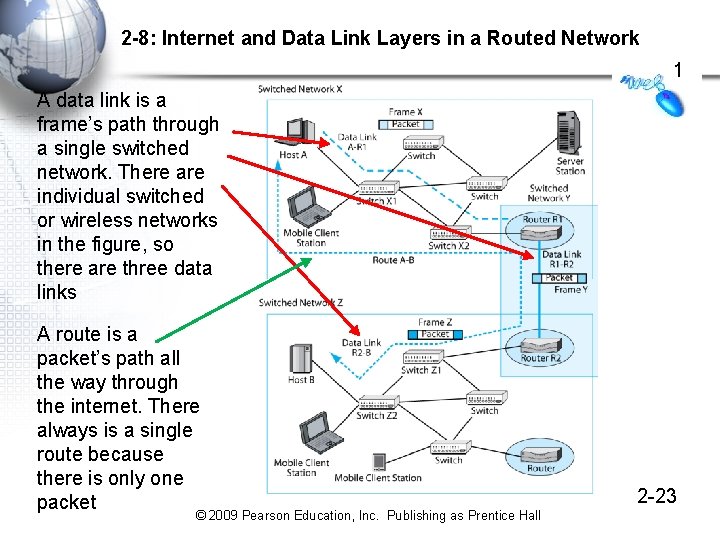
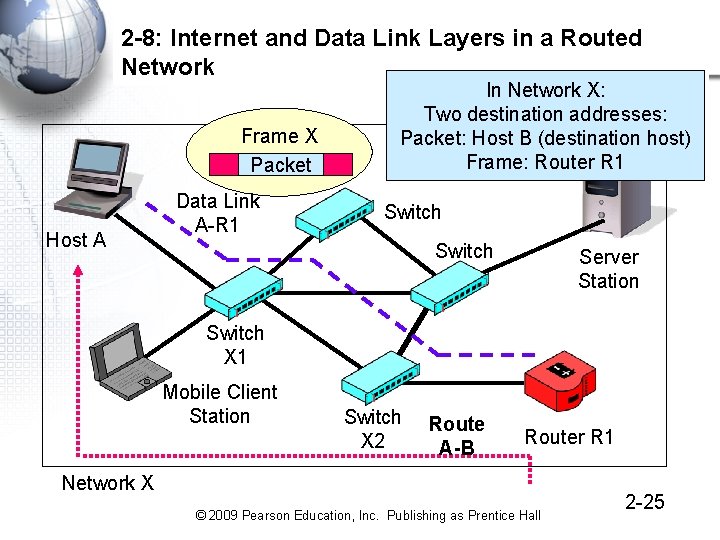
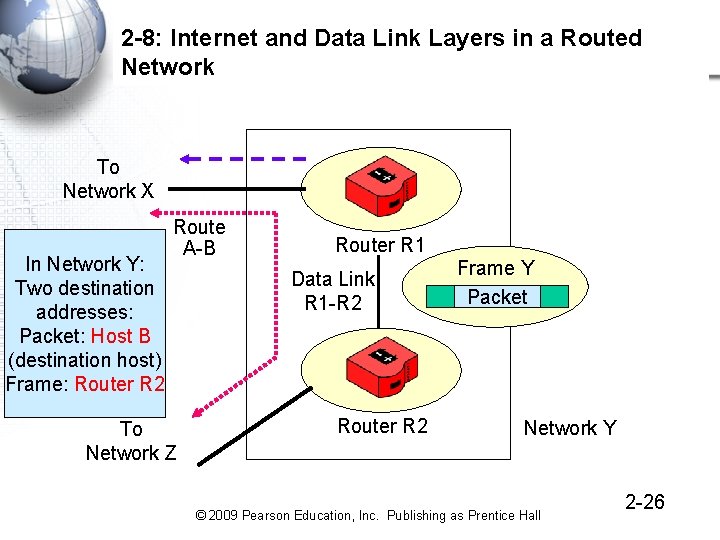
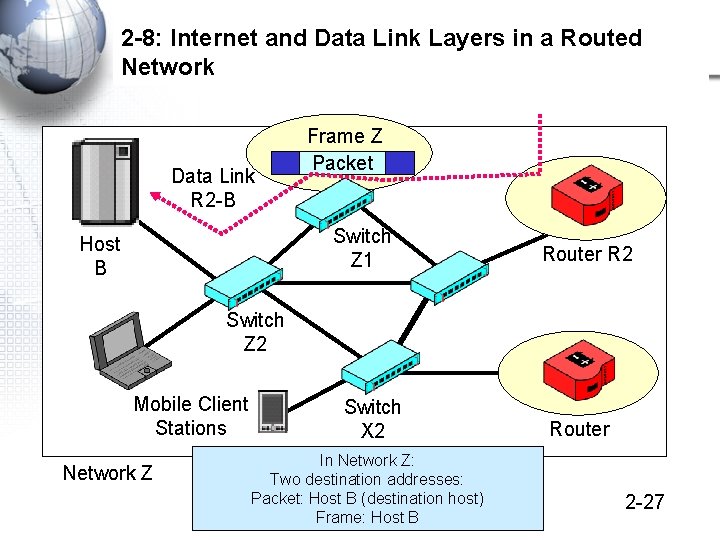
2 -8: Internet and Data Link Layers in a Routed Network 1 A data link is a frame’s path through a single switched network. There are individual switched or wireless networks in the figure, so there are three data links A route is a packet’s path all the way through the internet. There always is a single route because there is only one packet © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -23

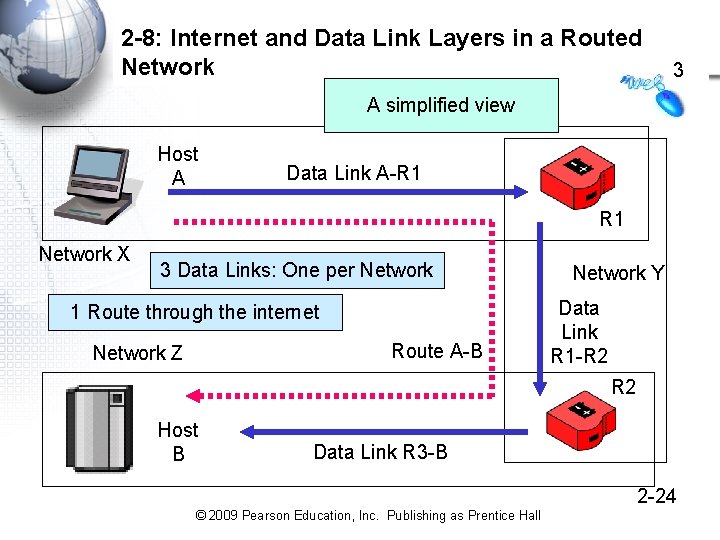
2 -8: Internet and Data Link Layers in a Routed Network 3 A simplified view Host A Data Link A-R 1 Network X 3 Data Links: One per Network 1 Route through the internet Route A-B Network Z Network Y Data Link R 1 -R 2 Host B Data Link R 3 -B 2 -24 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -8: Internet and Data Link Layers in a Routed Network Frame X Packet Host A Data Link A-R 1 In Network X: Two destination addresses: Packet: Host B (destination host) Frame: Router R 1 Switch Server Station Switch X 1 Mobile Client Station Switch X 2 Route A-B Router R 1 Network X © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -25

2 -8: Internet and Data Link Layers in a Routed Network To Network X In Network Y: Two destination addresses: Packet: Host B (destination host) Frame: Router R 2 Route A-B To Network Z Router R 1 Data Link R 1 -R 2 Router R 2 Frame Y Packet Network Y © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -26

2 -8: Internet and Data Link Layers in a Routed Network Data Link R 2 -B Frame Z Packet Switch Z 1 Host B Router R 2 Switch Z 2 Mobile Client Stations Network Z Switch X 2 In Network Z: Two destination addresses: Packet: Host B (destination host) © 2009 Pearson Education, Inc. Publishing as Prentice Hall Frame: Host B Router 2 -27

Figure 2 -10: Internet and Data Link Layers in an Internet • Internet and Transport Layers – An internet is a group of switched or wireless networks connected by routers so that any application on any host on any network can communicate with any application on any other host on any other network – Internet and transport layer standards govern communication across an internet composed of two or more switched or wireless networks 2 -28 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

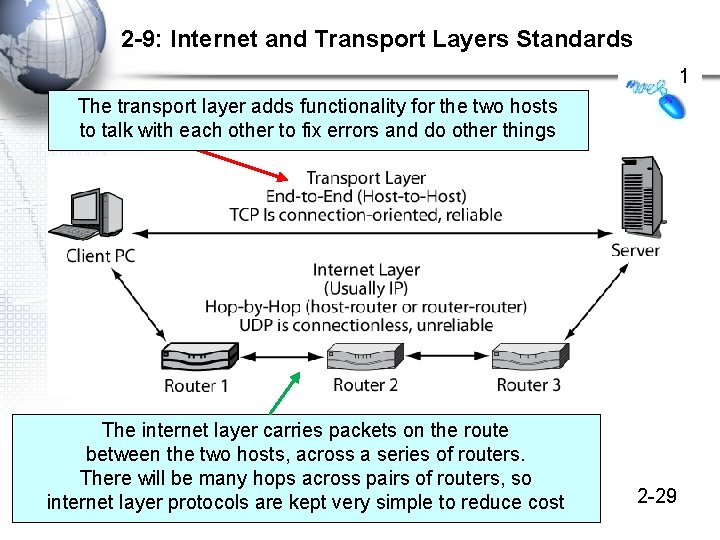
2 -9: Internet and Transport Layers Standards 1 The transport layer adds functionality for the two hosts to talk with each other to fix errors and do other things The internet layer carries packets on the route between the two hosts, across a series of routers. There will be many hops across pairs of routers, so internet layer protocols are kept very simple to reduce cost © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -29

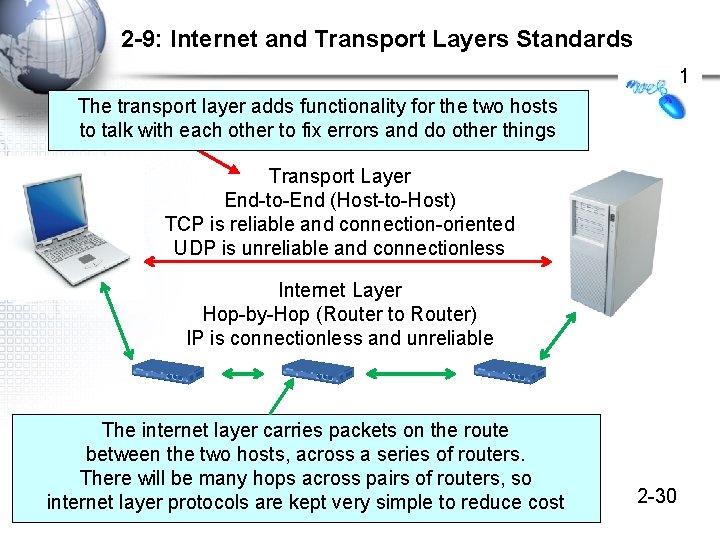
2 -9: Internet and Transport Layers Standards 1 The transport layer adds functionality for the two hosts to talk with each other to fix errors and do other things Transport Layer End-to-End (Host-to-Host) TCP is reliable and connection-oriented UDP is unreliable and connectionless Internet Layer Hop-by-Hop (Router to Router) IP is connectionless and unreliable The internet layer carries packets on the route between the two hosts, across a series of routers. There will be many hops across pairs of routers, so internet layer protocols are kept very simple to reduce cost © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -30

2 -10: Application Layer Standards • Application Layer Standards – Govern how two applications work with each other, even if they are from different vendors • There are many application layer standards because there are many applications – – – World Wide Web (HTTP) E-Mail (SMTP, POP, etc. ) FTP (FTP) Database (ODBC) Etc. There are more application layer standards than any other type of standards 2 -31 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Standards Layers: Recap • Application (5) Be able to repeat this in your sleep! • Transport (4) • Internet (3) • Data Link (2) • Physical (1) 2 -32 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

5. Syntax Examples: Ethernet and IP © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Syntax • How Messages are Organized – Usually organized as a succession of parts called fields – Fields are a few or many bits long Field 1 Field 2 Field 3 Field 4 Field 5 Field 6 2 -34 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

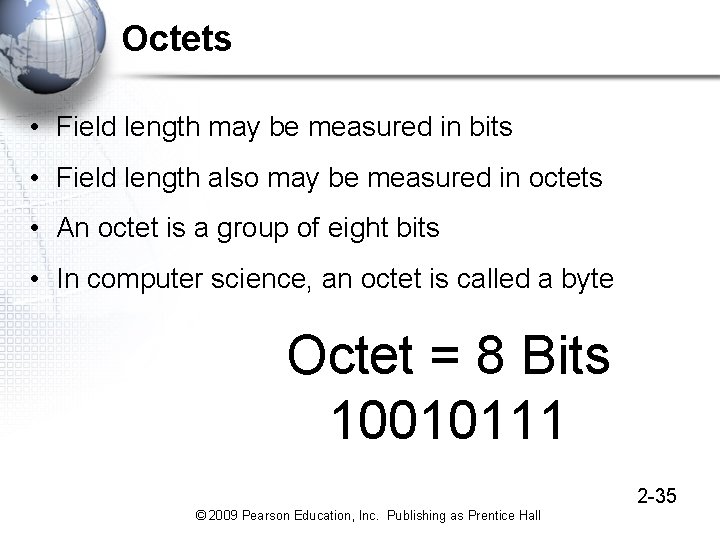
Octets • Field length may be measured in bits • Field length also may be measured in octets • An octet is a group of eight bits • In computer science, an octet is called a byte Octet = 8 Bits 10010111 2 -35 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

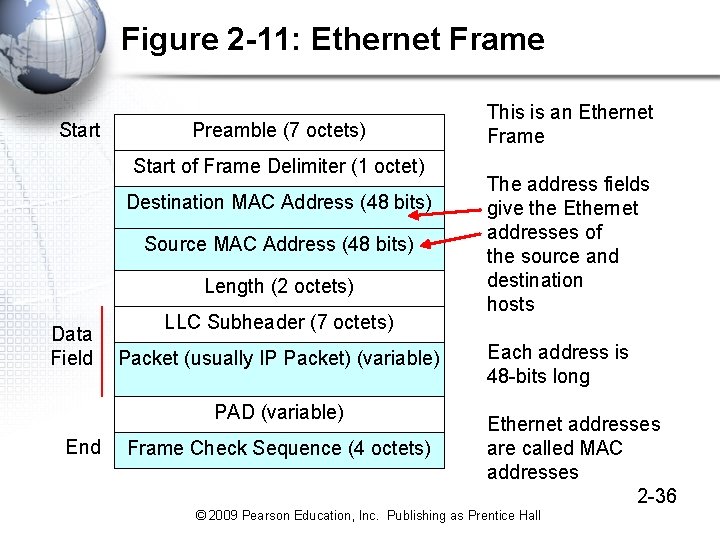
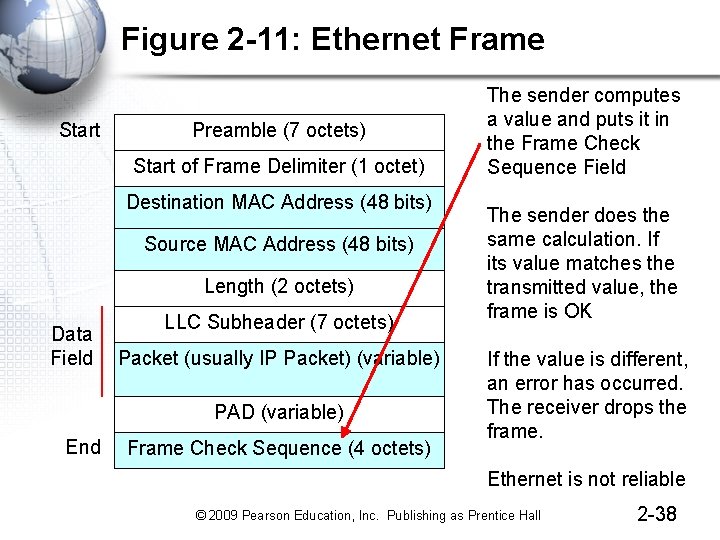
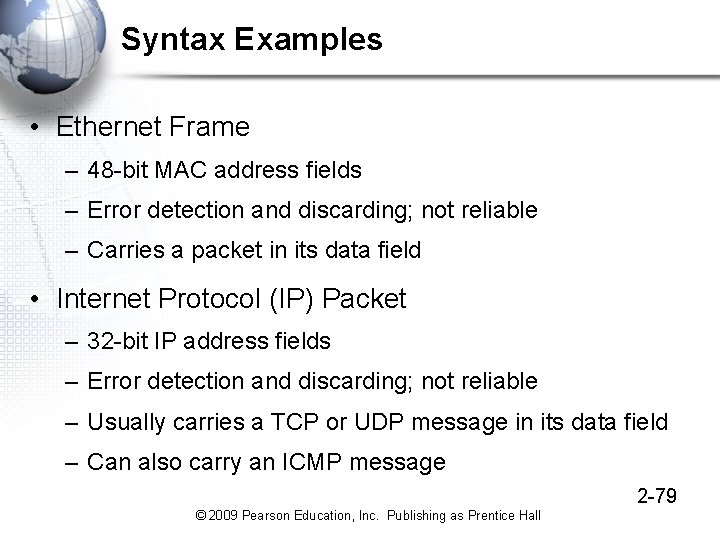
Figure 2 -11: Ethernet Frame Start Preamble (7 octets) Start of Frame Delimiter (1 octet) Destination MAC Address (48 bits) Source MAC Address (48 bits) Length (2 octets) Data Field LLC Subheader (7 octets) Packet (usually IP Packet) (variable) PAD (variable) End Frame Check Sequence (4 octets) This is an Ethernet Frame The address fields give the Ethernet addresses of the source and destination hosts Each address is 48 -bits long Ethernet addresses are called MAC addresses 2 -36 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

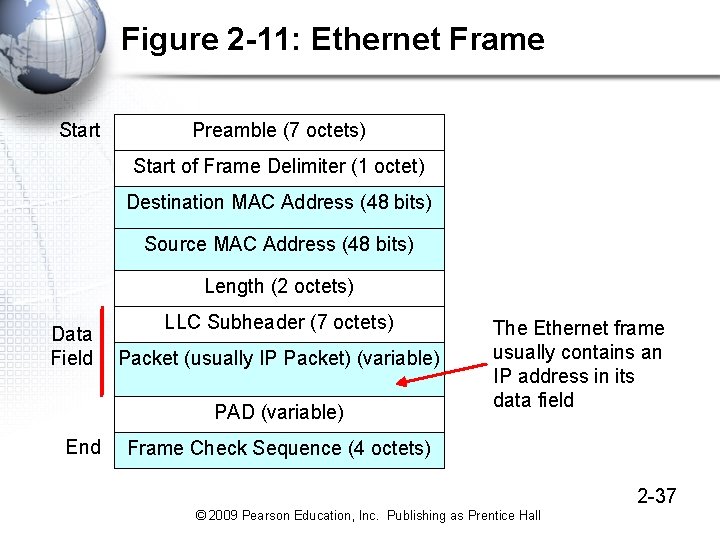
Figure 2 -11: Ethernet Frame Start Preamble (7 octets) Start of Frame Delimiter (1 octet) Destination MAC Address (48 bits) Source MAC Address (48 bits) Length (2 octets) Data Field LLC Subheader (7 octets) Packet (usually IP Packet) (variable) PAD (variable) End The Ethernet frame usually contains an IP address in its data field Frame Check Sequence (4 octets) 2 -37 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Figure 2 -11: Ethernet Frame Start Preamble (7 octets) Start of Frame Delimiter (1 octet) Destination MAC Address (48 bits) Source MAC Address (48 bits) Length (2 octets) Data Field LLC Subheader (7 octets) Packet (usually IP Packet) (variable) PAD (variable) End Frame Check Sequence (4 octets) The sender computes a value and puts it in the Frame Check Sequence Field The sender does the same calculation. If its value matches the transmitted value, the frame is OK If the value is different, an error has occurred. The receiver drops the frame. Ethernet is not reliable © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -38

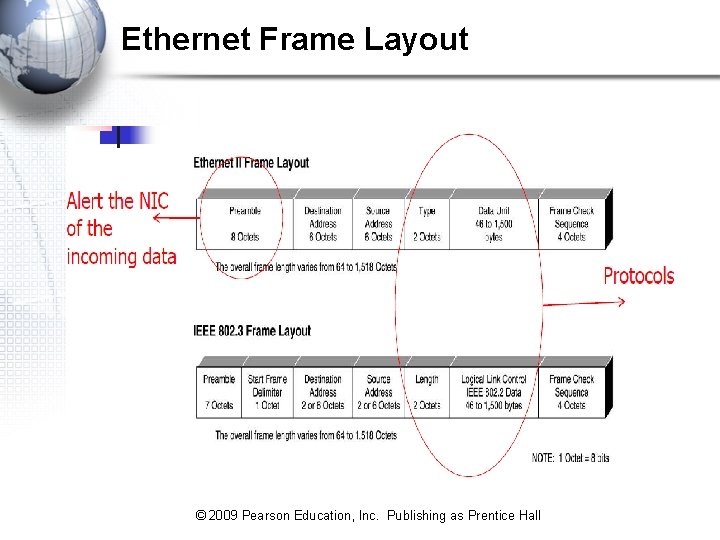
Ethernet Frame Layout © 2009 Pearson Education, Inc. Publishing as Prentice Hall

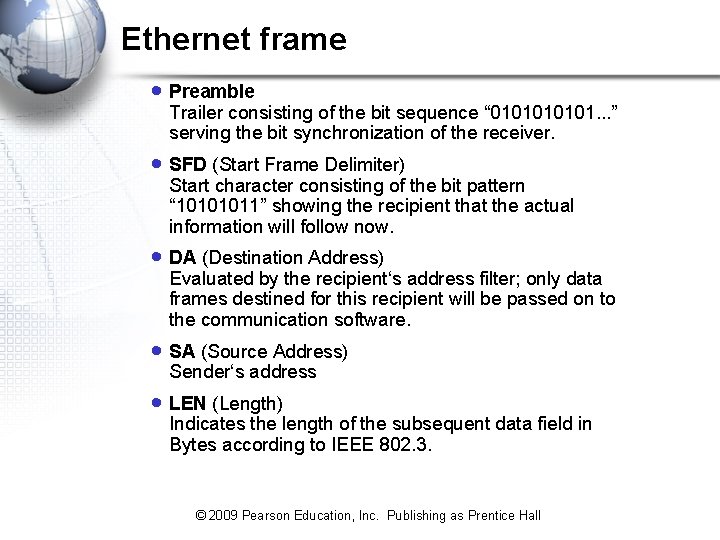
Ethernet frame · Preamble Trailer consisting of the bit sequence “ 010101. . . ” serving the bit synchronization of the receiver. · SFD (Start Frame Delimiter) Start character consisting of the bit pattern “ 10101011” showing the recipient that the actual information will follow now. · DA (Destination Address) Evaluated by the recipient‘s address filter; only data frames destined for this recipient will be passed on to the communication software. · SA (Source Address) Sender‘s address · LEN (Length) Indicates the length of the subsequent data field in Bytes according to IEEE 802. 3. © 2009 Pearson Education, Inc. Publishing as Prentice Hall

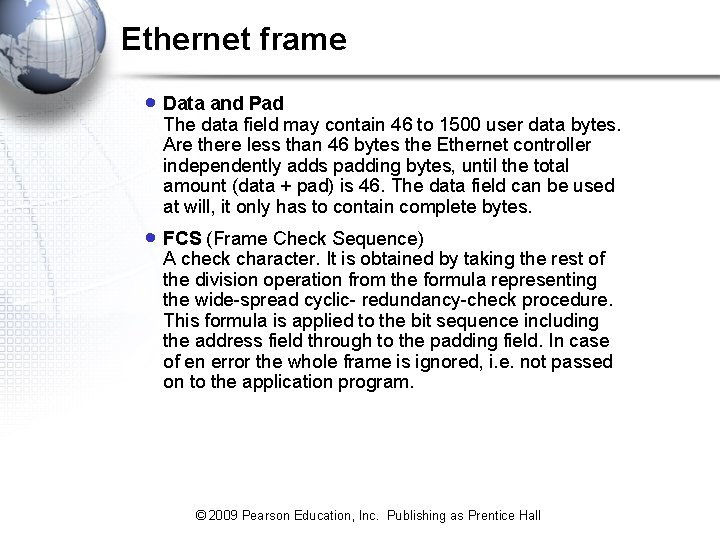
Ethernet frame · Data and Pad The data field may contain 46 to 1500 user data bytes. Are there less than 46 bytes the Ethernet controller independently adds padding bytes, until the total amount (data + pad) is 46. The data field can be used at will, it only has to contain complete bytes. · FCS (Frame Check Sequence) A check character. It is obtained by taking the rest of the division operation from the formula representing the wide-spread cyclic- redundancy-check procedure. This formula is applied to the bit sequence including the address field through to the padding field. In case of en error the whole frame is ignored, i. e. not passed on to the application program. © 2009 Pearson Education, Inc. Publishing as Prentice Hall

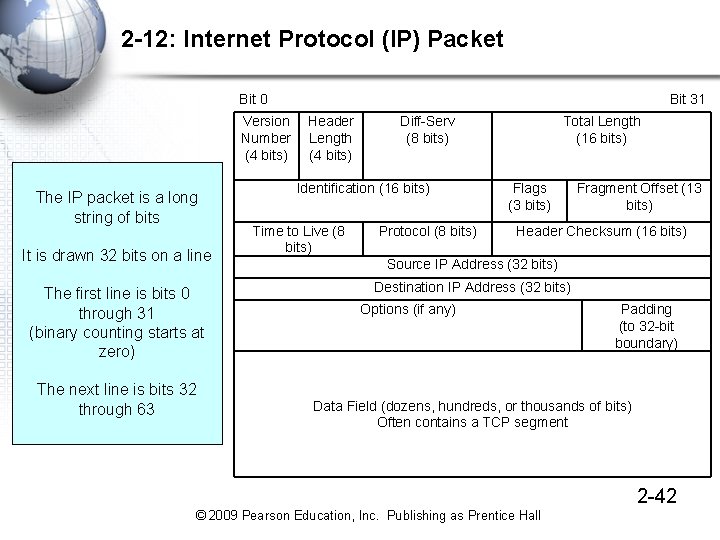
2 -12: Internet Protocol (IP) Packet Bit 0 Version Number (4 bits) The IP packet is a long string of bits It is drawn 32 bits on a line The first line is bits 0 through 31 (binary counting starts at zero) The next line is bits 32 through 63 Bit 31 Header Length (4 bits) Diff-Serv (8 bits) Identification (16 bits) Time to Live (8 bits) Protocol (8 bits) Total Length (16 bits) Flags (3 bits) Fragment Offset (13 bits) Header Checksum (16 bits) Source IP Address (32 bits) Destination IP Address (32 bits) Options (if any) Padding (to 32 -bit boundary) Data Field (dozens, hundreds, or thousands of bits) Often contains a TCP segment 2 -42 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

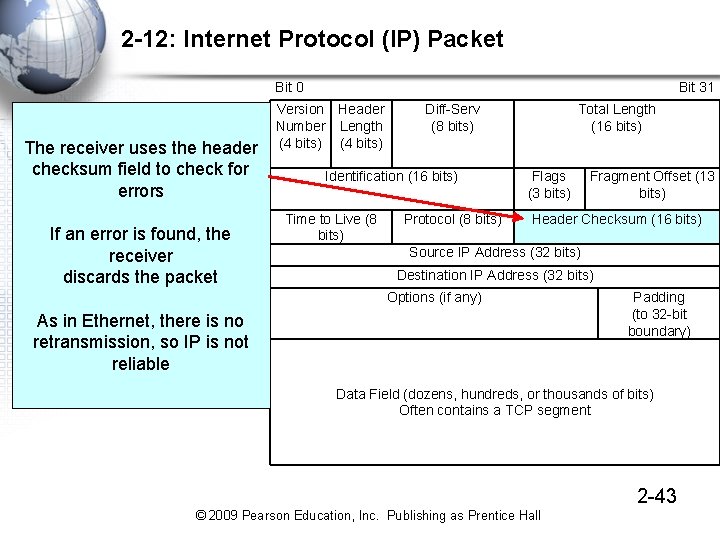
2 -12: Internet Protocol (IP) Packet Bit 0 The receiver uses the header checksum field to check for errors If an error is found, the receiver discards the packet Bit 31 Version Header Number Length (4 bits) Diff-Serv (8 bits) Identification (16 bits) Time to Live (8 bits) Protocol (8 bits) Total Length (16 bits) Flags (3 bits) Fragment Offset (13 bits) Header Checksum (16 bits) Source IP Address (32 bits) Destination IP Address (32 bits) Options (if any) As in Ethernet, there is no retransmission, so IP is not reliable Padding (to 32 -bit boundary) Data Field (dozens, hundreds, or thousands of bits) Often contains a TCP segment 2 -43 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

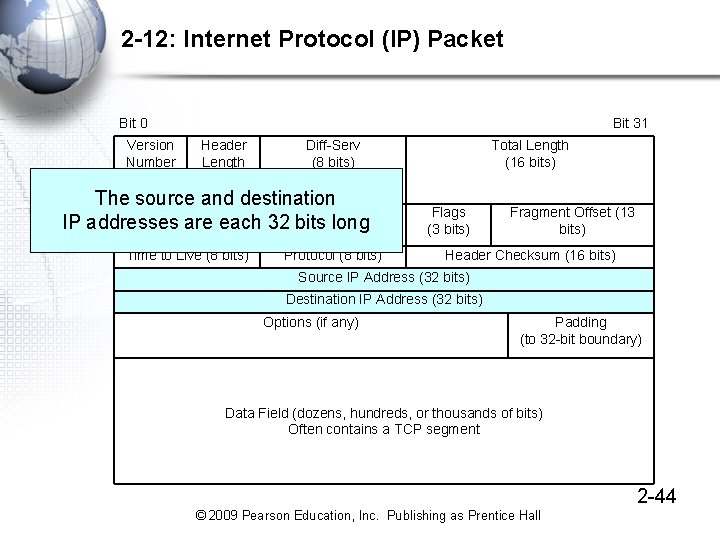
2 -12: Internet Protocol (IP) Packet Bit 0 Version Number (4 bits) Bit 31 Header Length (4 bits) Diff-Serv (8 bits) The source and destination Identification (16 bits) IP addresses are each 32 bits long Time to Live (8 bits) Protocol (8 bits) Total Length (16 bits) Flags (3 bits) Fragment Offset (13 bits) Header Checksum (16 bits) Source IP Address (32 bits) Destination IP Address (32 bits) Options (if any) Padding (to 32 -bit boundary) Data Field (dozens, hundreds, or thousands of bits) Often contains a TCP segment 2 -44 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

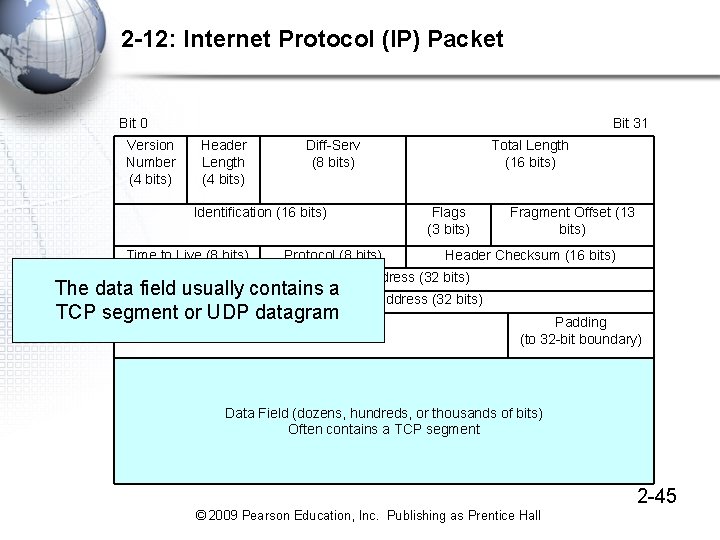
2 -12: Internet Protocol (IP) Packet Bit 0 Version Number (4 bits) Bit 31 Header Length (4 bits) Diff-Serv (8 bits) Identification (16 bits) Time to Live (8 bits) Protocol (8 bits) Total Length (16 bits) Flags (3 bits) Fragment Offset (13 bits) Header Checksum (16 bits) Source IP Address (32 bits) The data field usually contains a Destination IP Address (32 bits) TCP segment or UDP datagram Options (if any) Padding (to 32 -bit boundary) Data Field (dozens, hundreds, or thousands of bits) Often contains a TCP segment 2 -45 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

6. Reliability Options at the Transport Layer TCP versus UDP © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -13: Why Not Make All Layers Reliable? • Reliability Is Expensive – When errors are rare (in hops between routers and switches), the cost is not justified – Switches and routers would be much more expensive if they did hop-by-hop error correction – There are many switch and router hops, so doing error correction between hops would be very expensive – Error correction at the transport layer corrects errors made at lower layers, making correction at lower layer unnecessary as well as expensive 2 -47 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -13: Why Not Make All Layers Reliable? 2 • Why Does Doing Error Correction at the Transport Layer Make Sense? • First, – There are only two transport processes: one on the source host, one on the destination host – So error correction has to be done only once, keeping cost low • Second, – The transport process is just below the application layer – So doing error correction at the transport layer frees the application layer from doing error correction 2 -48 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

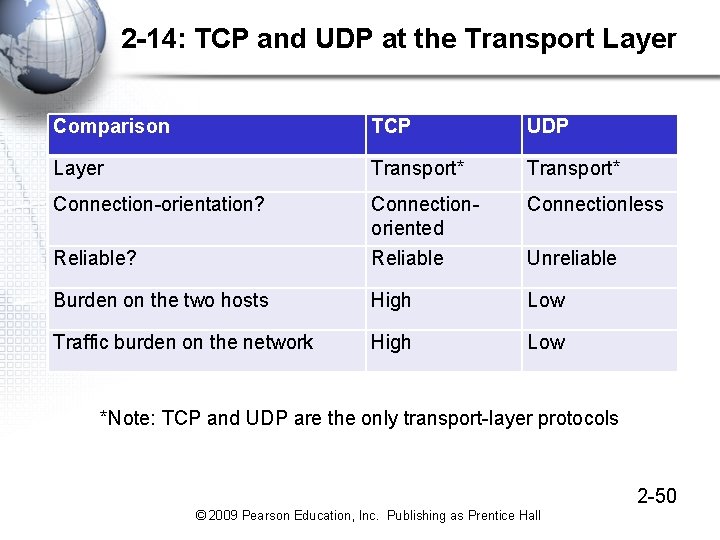
2 -14: TCP and UDP at the Transport Layer • Not all applications need reliability – Voice over IP cannot wait for lost or damaged packets to be retransmitted – Network management protocols need to place as low a burden on the network as possible – Both types of applications use the simpler User Datagram Protocol (UDP) instead of TCP 2 -49 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -14: TCP and UDP at the Transport Layer Comparison TCP UDP Layer Transport* Connection-orientation? Connectionless Reliable? Connectionoriented Reliable Burden on the two hosts High Low Traffic burden on the network High Low Unreliable *Note: TCP and UDP are the only transport-layer protocols 2 -50 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

7. Vertical Communication Between Layer Processes on the Same Host © 2009 Pearson Education, Inc. Publishing as Prentice Hall

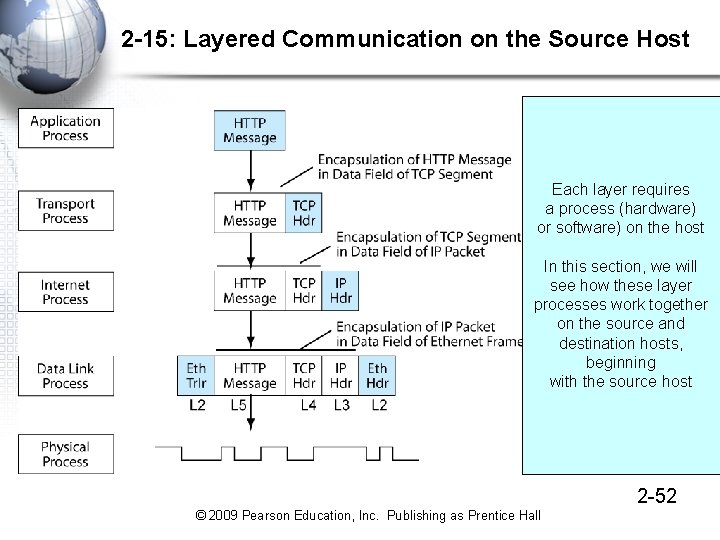
2 -15: Layered Communication on the Source Host Each layer requires a process (hardware) or software) on the host In this section, we will see how these layer processes work together on the source and destination hosts, beginning with the source host 2 -52 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

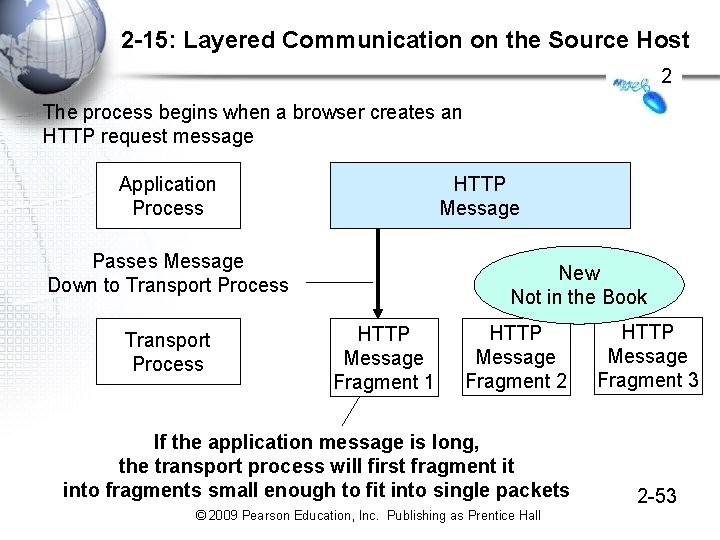
2 -15: Layered Communication on the Source Host 2 The process begins when a browser creates an HTTP request message Application Process HTTP Message Passes Message Down to Transport Process New Not in the Book HTTP Message Fragment 1 HTTP Message Fragment 2 If the application message is long, the transport process will first fragment it into fragments small enough to fit into single packets © 2009 Pearson Education, Inc. Publishing as Prentice Hall HTTP Message Fragment 3 2 -53

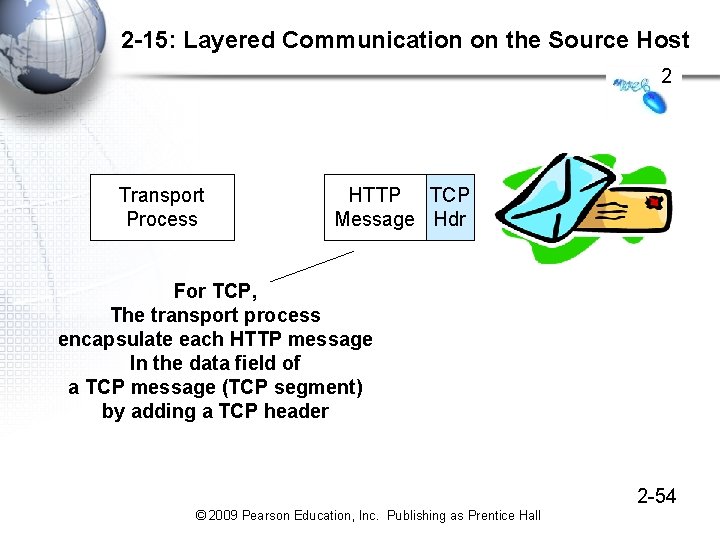
2 -15: Layered Communication on the Source Host 2 Transport Process HTTP TCP Message Hdr For TCP, The transport process encapsulate each HTTP message In the data field of a TCP message (TCP segment) by adding a TCP header 2 -54 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

2 -15: Layered Communication on the Source Host • When a layer process (N) creates a message, it passes it down to the nextlower-layer process (N-1) immediately • The receiving process (N-1) will encapsulate the Layer N message, that is, place it in the data field of its own (N-1) message © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -55

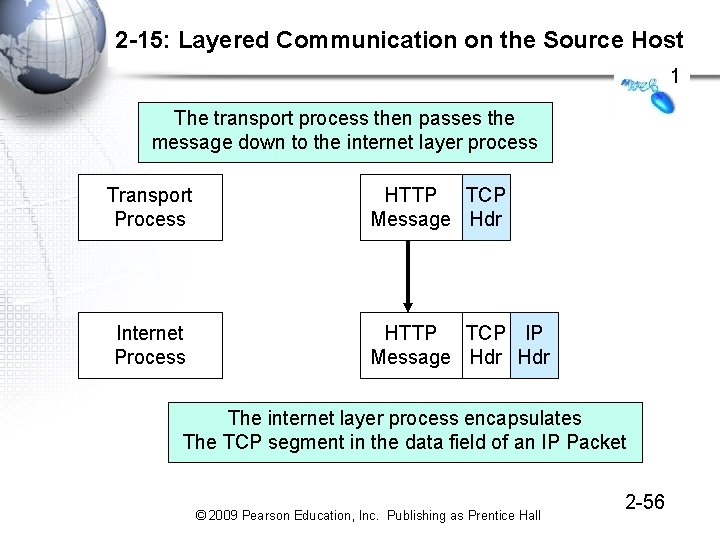
2 -15: Layered Communication on the Source Host 1 The transport process then passes the message down to the internet layer process Transport Process Internet Process HTTP TCP Message Hdr HTTP TCP IP Message Hdr The internet layer process encapsulates The TCP segment in the data field of an IP Packet © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -56

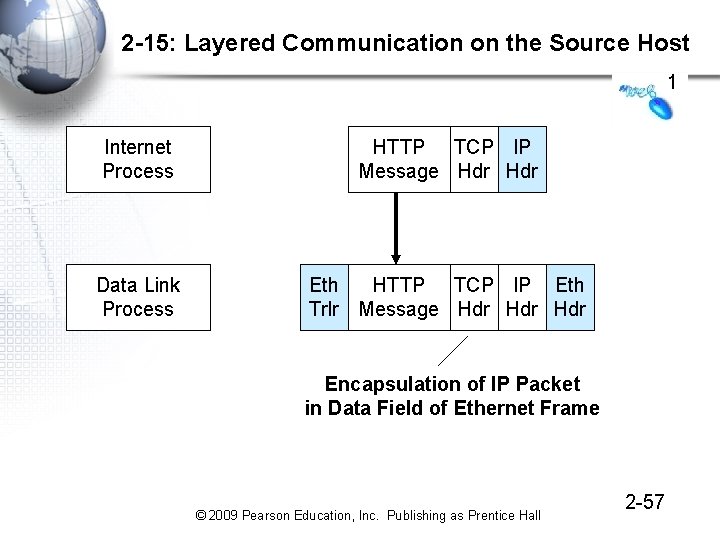
2 -15: Layered Communication on the Source Host 1 Internet Process HTTP TCP IP Message Hdr Data Link Process Eth HTTP TCP IP Eth Trlr Message Hdr Hdr Encapsulation of IP Packet in Data Field of Ethernet Frame © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -57

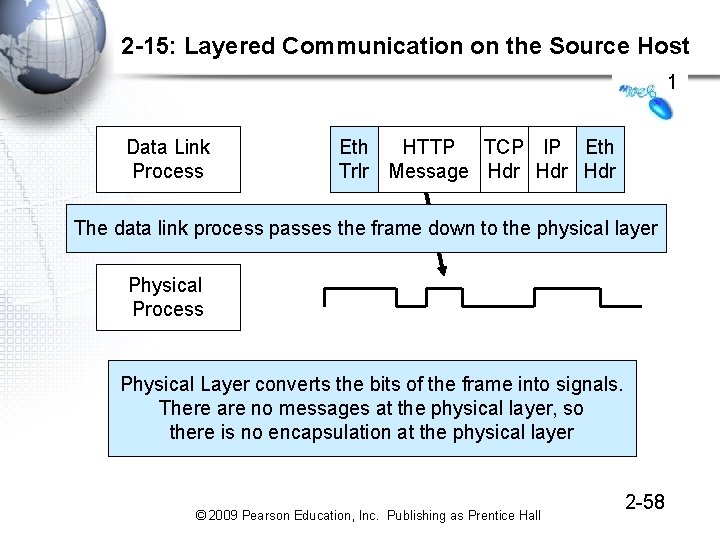
2 -15: Layered Communication on the Source Host 1 Data Link Process Eth HTTP TCP IP Eth Trlr Message Hdr Hdr The data link process passes the frame down to the physical layer Physical Process Physical Layer converts the bits of the frame into signals. There are no messages at the physical layer, so there is no encapsulation at the physical layer © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -58

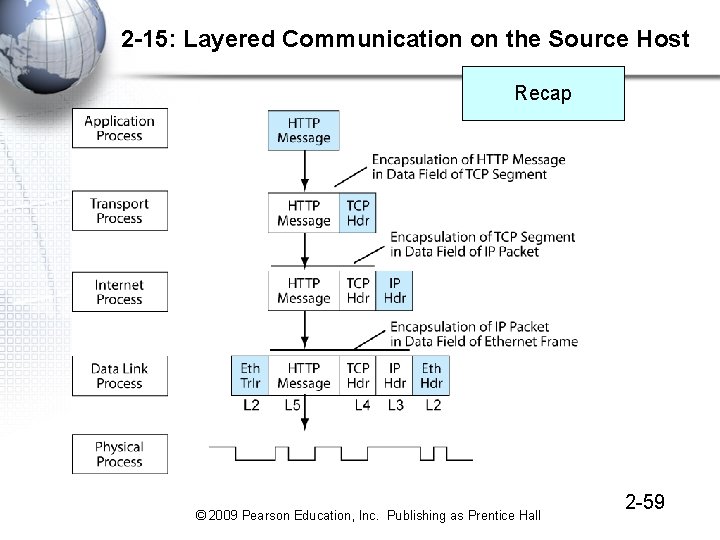
2 -15: Layered Communication on the Source Host Recap © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -59

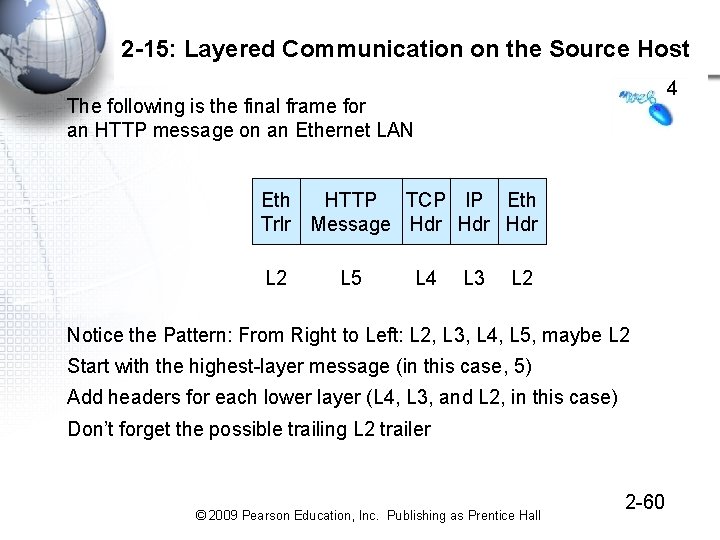
2 -15: Layered Communication on the Source Host 4 The following is the final frame for an HTTP message on an Ethernet LAN Eth HTTP TCP IP Eth Trlr Message Hdr Hdr L 2 L 5 L 4 L 3 L 2 Notice the Pattern: From Right to Left: L 2, L 3, L 4, L 5, maybe L 2 Start with the highest-layer message (in this case, 5) Add headers for each lower layer (L 4, L 3, and L 2, in this case) Don’t forget the possible trailing L 2 trailer © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -60

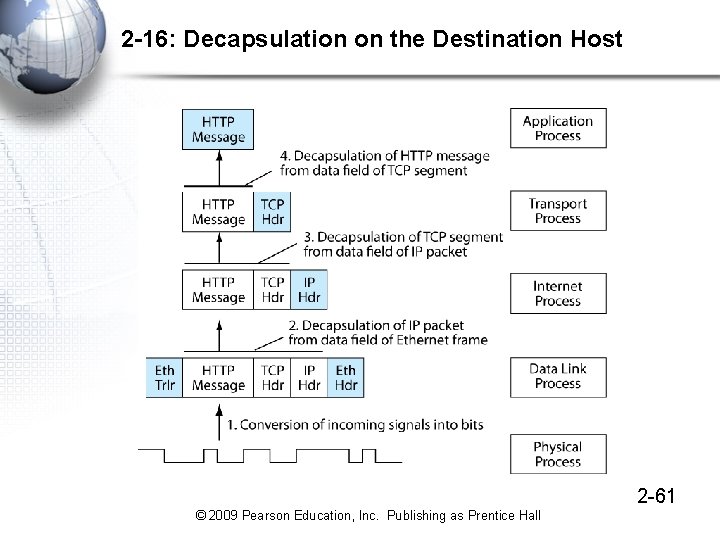
2 -16: Decapsulation on the Destination Host 2 -61 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

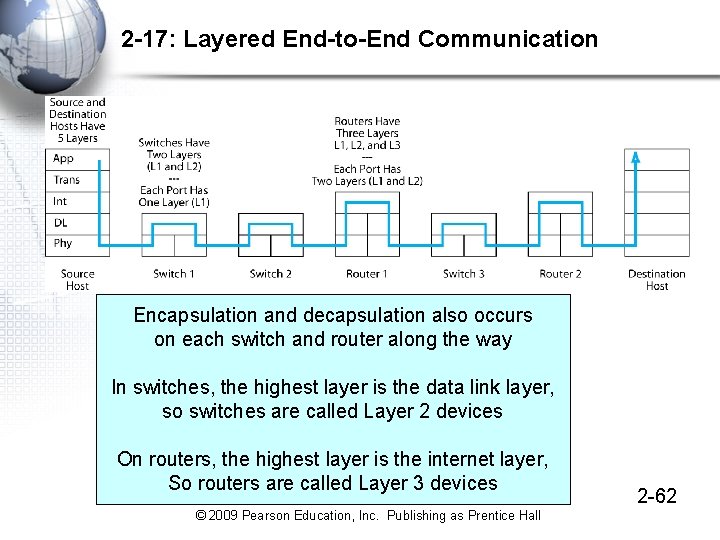
2 -17: Layered End-to-End Communication Encapsulation and decapsulation also occurs on each switch and router along the way In switches, the highest layer is the data link layer, so switches are called Layer 2 devices On routers, the highest layer is the internet layer, So routers are called Layer 3 devices © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -62

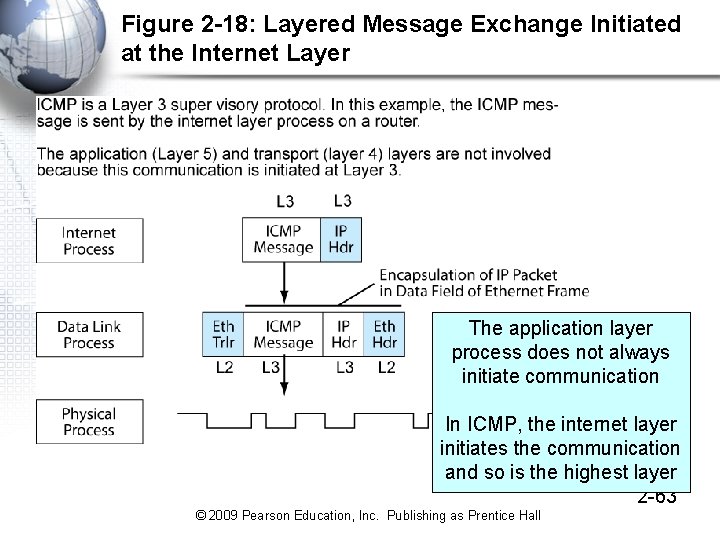
Figure 2 -18: Layered Message Exchange Initiated at the Internet Layer The application layer process does not always initiate communication In ICMP, the internet layer initiates the communication and so is the highest layer 2 -63 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

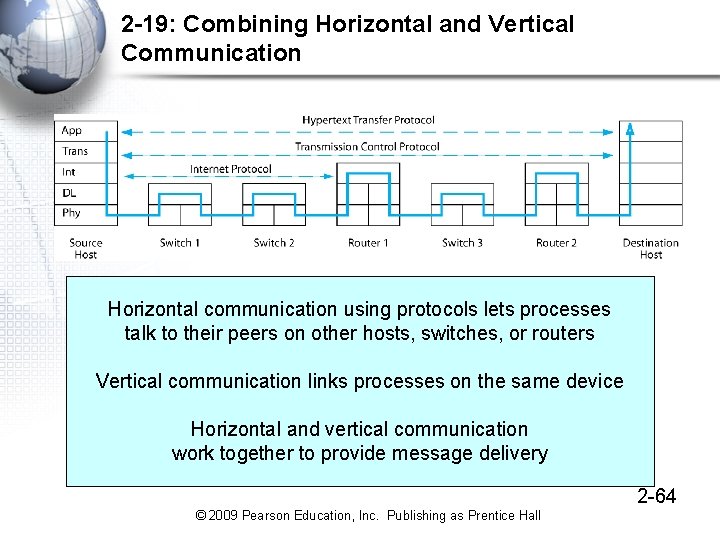
2 -19: Combining Horizontal and Vertical Communication Horizontal communication using protocols lets processes talk to their peers on other hosts, switches, or routers Vertical communication links processes on the same device Horizontal and vertical communication work together to provide message delivery 2 -64 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

8. OSI, TCP/IP, and Other Standards Architectures © 2009 Pearson Education, Inc. Publishing as Prentice Hall

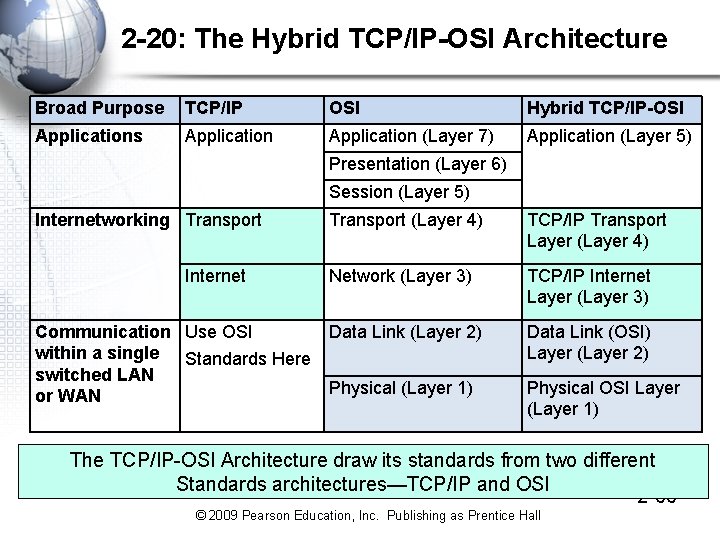
2 -20: The Hybrid TCP/IP-OSI Architecture Broad Purpose TCP/IP OSI Hybrid TCP/IP-OSI Applications Application (Layer 7) Application (Layer 5) Presentation (Layer 6) Session (Layer 5) Internetworking Transport Internet Communication Use OSI within a single Standards Here switched LAN or WAN Transport (Layer 4) TCP/IP Transport Layer (Layer 4) Network (Layer 3) TCP/IP Internet Layer (Layer 3) Data Link (Layer 2) Data Link (OSI) Layer (Layer 2) Physical (Layer 1) Physical OSI Layer (Layer 1) The TCP/IP-OSI Architecture draw its standards from two different Standards architectures—TCP/IP and OSI 2 -66 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

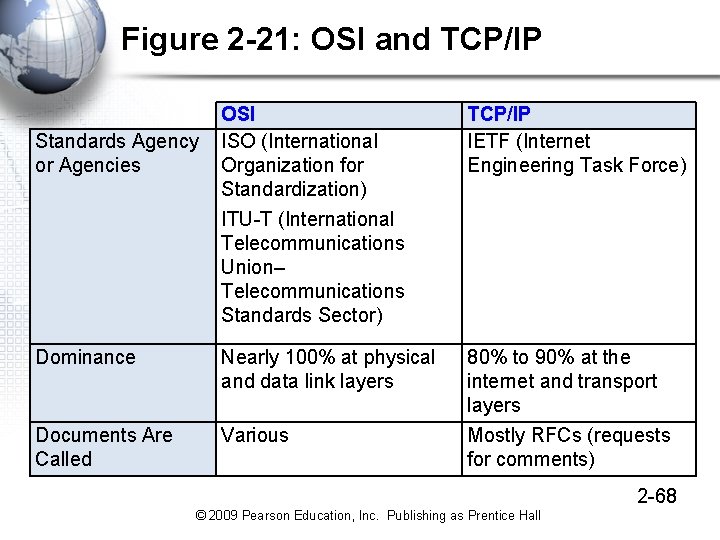
Figure 2 -21: OSI and TCP/IP OSI Standards Agency ISO (International or Agencies Organization for Standardization) ITU-T (International Telecommunications Union– Telecommunications Standards Sector) TCP/IP IETF (Internet Engineering Task Force) Dominance Nearly 100% at physical and data link layers 80% to 90% at the internet and transport layers Documents Are Called Various Mostly RFCs (requests for comments) 2 -68 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

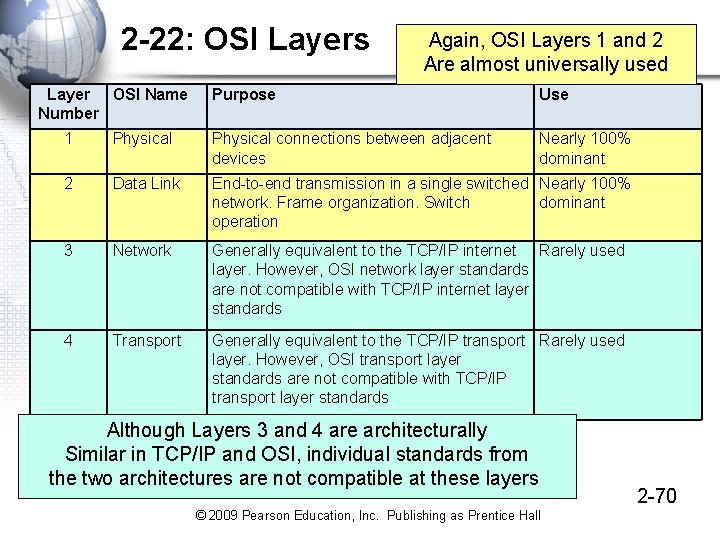
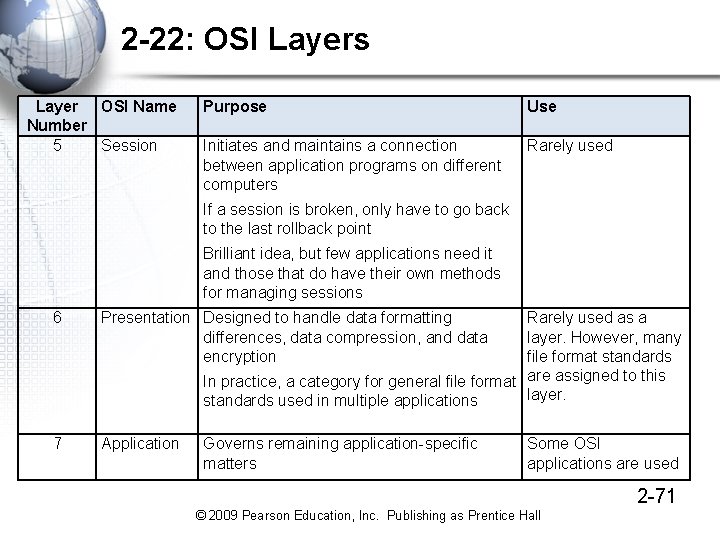
2 -22: OSI Layers Layer OSI Name Number Again, OSI Layers 1 and 2 Are almost universally used Purpose Use Nearly 100% dominant 1 Physical connections between adjacent devices 2 Data Link End-to-end transmission in a single switched Nearly 100% network. Frame organization. Switch dominant operation 3 Network Generally equivalent to the TCP/IP internet Rarely used layer. However, OSI network layer standards are not compatible with TCP/IP internet layer standards 4 Transport Generally equivalent to the TCP/IP transport Rarely used layer. However, OSI transport layer standards are not compatible with TCP/IP transport layer standards Although Layers 3 and 4 are architecturally Similar in TCP/IP and OSI, individual standards from the two architectures are not compatible at these layers © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -70

2 -22: OSI Layers Layer OSI Name Number 5 Session Purpose Use Initiates and maintains a connection between application programs on different computers Rarely used If a session is broken, only have to go back to the last rollback point Brilliant idea, but few applications need it and those that do have their own methods for managing sessions 6 Presentation Designed to handle data formatting differences, data compression, and data encryption Rarely used as a layer. However, many file format standards In practice, a category for general file format are assigned to this layer. standards used in multiple applications 7 Application Governs remaining application-specific matters Some OSI applications are used 2 -71 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

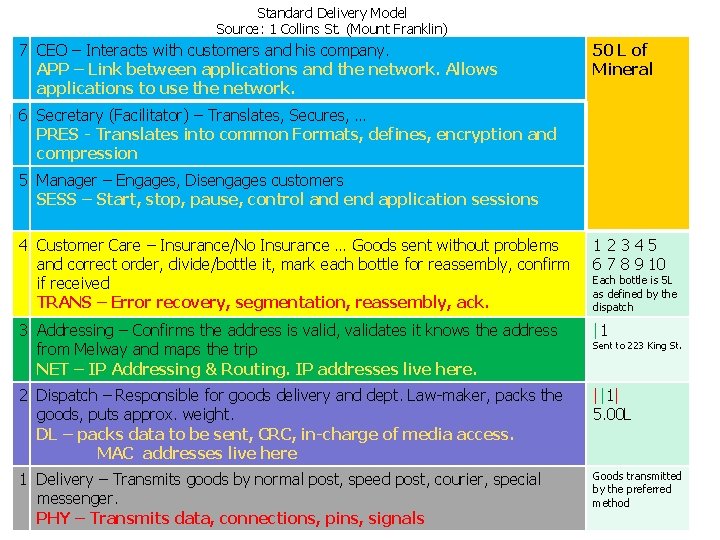
Standard Delivery Model Source: 1 Collins St. (Mount Franklin) 7 CEO – Interacts with customers and his company. APP – Link between applications and the network. Allows applications to use the network. 50 L of Mineral 6 Secretary (Facilitator) – Translates, Secures, … PRES - Translates into common Formats, defines, encryption and compression 5 Manager – Engages, Disengages customers SESS – Start, stop, pause, control and end application sessions 4 Customer Care – Insurance/No Insurance … Goods sent without problems and correct order, divide/bottle it, mark each bottle for reassembly, confirm if received TRANS – Error recovery, segmentation, reassembly, ack. 1 2 3 4 5 6 7 8 9 10 3 Addressing – Confirms the address is valid, validates it knows the address from Melway and maps the trip NET – IP Addressing & Routing. IP addresses live here. |1 2 Dispatch – Responsible for goods delivery and dept. Law-maker, packs the goods, puts approx. weight. DL – packs data to be sent, CRC, in-charge of media access. MAC addresses live here ||1| 5. 00 L 1 Delivery – Transmits goods by normal post, speed post, courier, special messenger. PHY – Transmits data, connections, pins, signals Goods transmitted by the preferred method Each bottle is 5 L as defined by the dispatch Sent to 223 King St.

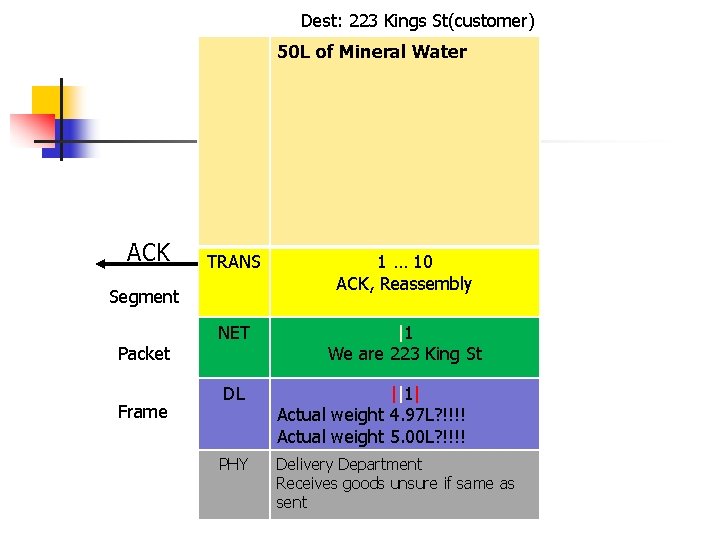
Dest: 223 Kings St(customer) 50 L of Mineral Water ACK TRANS 1 … 10 ACK, Reassembly NET |1 We are 223 King St Segment Packet Frame DL ||1| Actual weight 4. 97 L? !!!! Actual weight 5. 00 L? !!!! PHY Delivery Department Receives goods unsure if same as sent

2 -23: Other Major Standards Architectures • IPX/SPX – Used by older Novell Net. Ware file servers for file and print service – Sometimes used in newer Novell Net. Ware file servers for consistency with older Net. Ware servers • SNA (Systems Network Architecture) – Used by older IBM mainframe computers • Apple. Talk – Used by Apple Macintosh desktops and notebooks to talk to Macintosh servers 2 -74 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

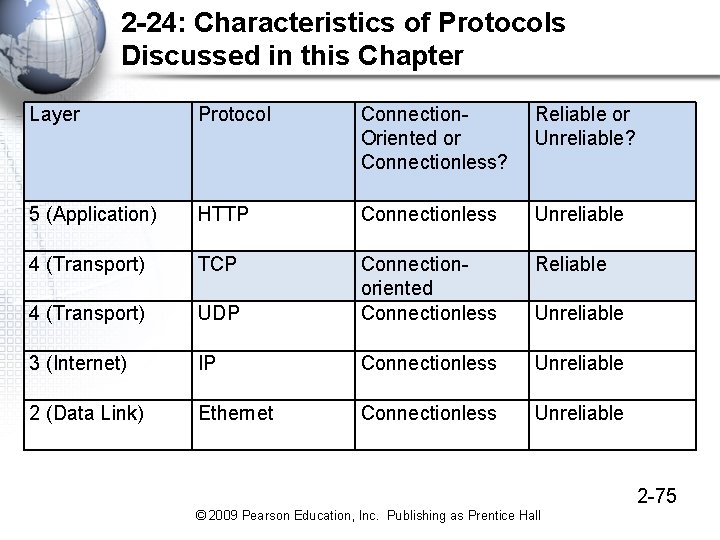
2 -24: Characteristics of Protocols Discussed in this Chapter Layer Protocol Connection. Oriented or Connectionless? Reliable or Unreliable? 5 (Application) HTTP Connectionless Unreliable 4 (Transport) TCP Reliable 4 (Transport) UDP Connectionoriented Connectionless 3 (Internet) IP Connectionless Unreliable 2 (Data Link) Ethernet Connectionless Unreliable 2 -75 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

9. Topics Covered © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Network Standards • The Core of Networking • Network Standards Govern – Message order (turn taking, etc. ) – Message syntax (structure of messages) • Header, data field, trailer • Header is subdivided into header fields – Message semantics (meaning) – Reliable or unreliable operation • Requires both error detection AND error correction – Connection-oriented or connectionless operation 2 -77 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Architectures • Hybrid TCP/IP-OSI Architecture – – – Layer 5: Application Layer 4: Transport Layer 3: Internet Layer 2: Data Link Layer 1: Physical • Connections – Layer 1: Physical link between adjacent devices – Layer 2: Data link through a single switched network – Layer 3: route through a routed network (internet) 2 -78 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

Syntax Examples • Ethernet Frame – 48 -bit MAC address fields – Error detection and discarding; not reliable – Carries a packet in its data field • Internet Protocol (IP) Packet – 32 -bit IP address fields – Error detection and discarding; not reliable – Usually carries a TCP or UDP message in its data field – Can also carry an ICMP message 2 -79 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

TCP and UDP • The Only Protocols at the Transport Layer • TCP is Reliable – Reliability is expensive – TCP fixes errors at all lower layers, giving the application process clean data – Error correction only has to be done once, on the source and destination hosts • UDP is Unreliable – Low burden on the network and hosts – Useful if application cannot use reliability or prefers not to use it 2 -80 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

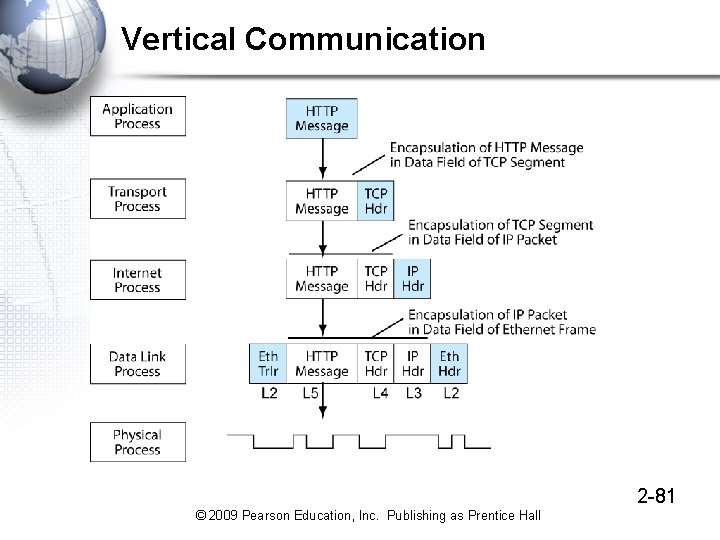
Vertical Communication 2 -81 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

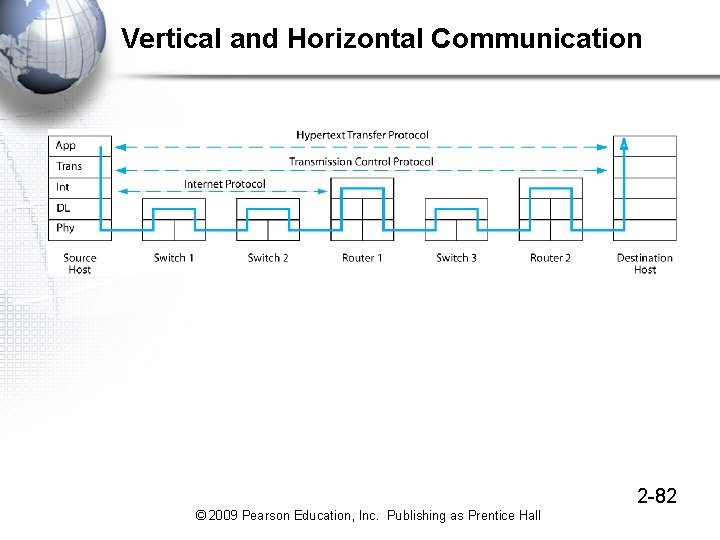
Vertical and Horizontal Communication 2 -82 © 2009 Pearson Education, Inc. Publishing as Prentice Hall

All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. Printed in the United States of America. Copyright © 2009 Pearson Education, Inc. Publishing as Prentice Hall 2 -83