Network Security Routing security Aapo Kalliola T110 5241






























- Slides: 48

Network Security: Routing security Aapo Kalliola T-110. 5241 Network security Aalto University, Nov-Dec 2012

Outline 1. 2. 3. 4. 5. 6. 7. Structure of internet Routing basics Security issues Attack Solutions (? ) Censorship and avoidance Case studies 2

Couldn’t routing be trivial? ”Explosive growth is taxing current Internet routing mechanisms. New sites continue to join the Internet… In some sense, the Internet is a victim of its own success; many routing protocols are being used in environments for which they had not been designed. ” - Thomas Narten, ”Internet routing”, 1989 3

Routing basics 4

Internet (? ) 5

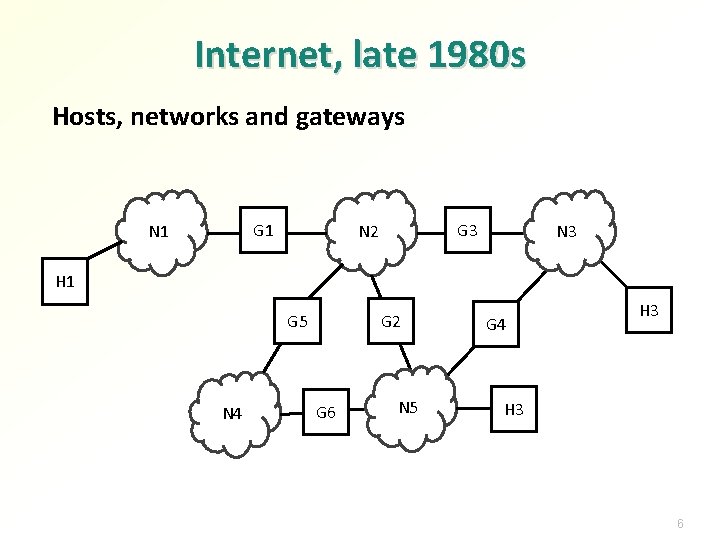
Internet, late 1980 s Hosts, networks and gateways G 1 N 1 G 3 N 2 N 3 H 1 G 5 N 4 G 2 G 6 N 5 G 4 H 3 6

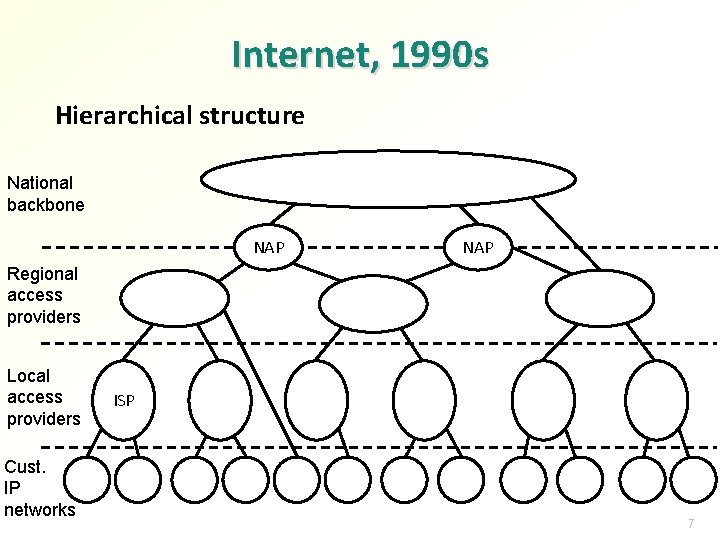
Internet, 1990 s Hierarchical structure National backbone NAP Regional access providers Local access providers Cust. IP networks ISP 7

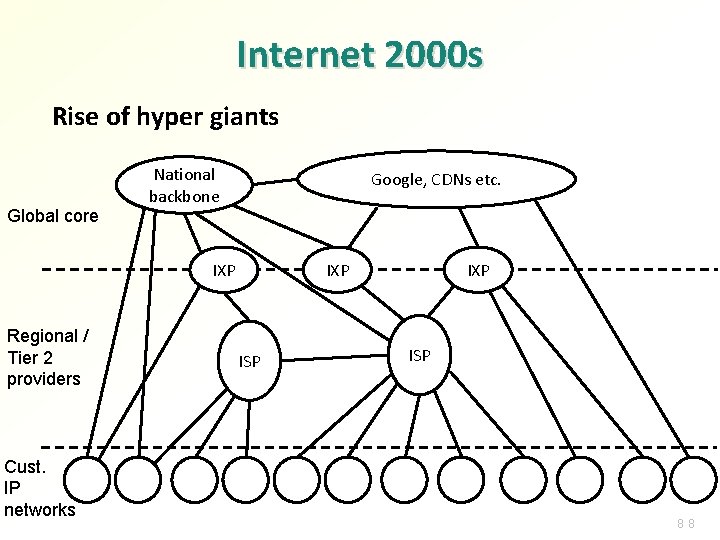
Internet 2000 s Rise of hyper giants Global core National backbone Google, CDNs etc. IXP Regional / Tier 2 providers Cust. IP networks IXP ISP 88

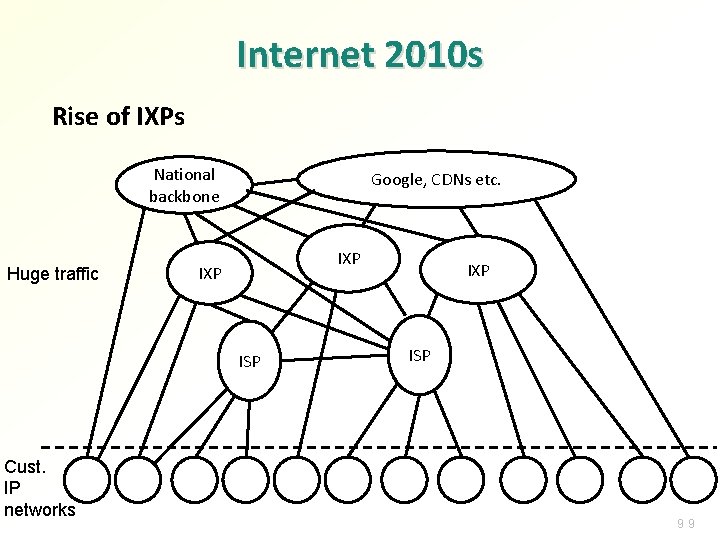
Internet 2010 s Rise of IXPs National backbone Huge traffic Google, CDNs etc. IXP ISP Cust. IP networks IXP ISP 99

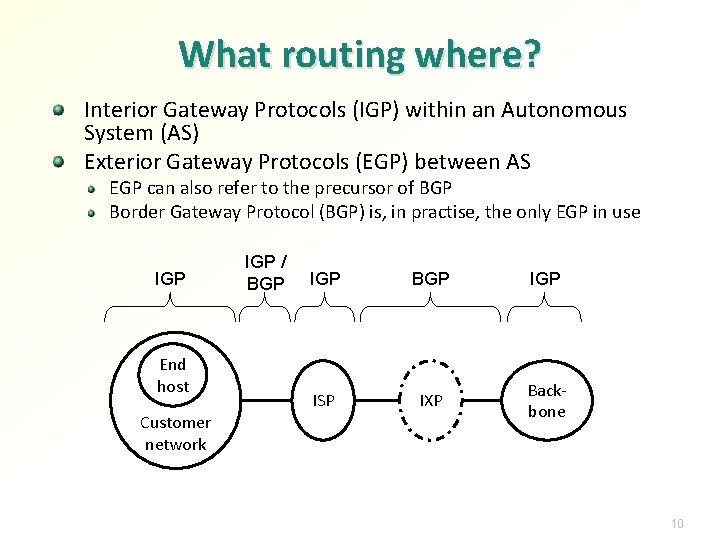
What routing where? Interior Gateway Protocols (IGP) within an Autonomous System (AS) Exterior Gateway Protocols (EGP) between AS EGP can also refer to the precursor of BGP Border Gateway Protocol (BGP) is, in practise, the only EGP in use IGP End host Customer network IGP / BGP IGP ISP IXP Backbone 10

Routing in and between Autonomous Systems (Ases) Tens of thousands of ASes Internally motivated by efficiency Externally motivated by Link costs Transmission capacity Load Policy decisions 11

Interior gateway protocols IGPs exchange routing information within an AS Link-state protocols maintain information about the whole network topology Open Shortest Path First (OSPF) Intermediate System to Intermediate System (IS-IS) Distance-vector protocols converge over time to common understanding of paths RIP / RIPv 2 IGRP Hybrid protocols have features from both E-IGRP 12

Border gateway protocol BGP is the procol for making routing decisions between ASes Routing decisions are not made by automation but rather by commercial interests Two main types of relations: Peering – exchanging traffic freely between peers Transit – smaller AS buying data transit from larger AS 13

BGP Design goals Scalability for connecting AS on internet scale Enabling policy decisions such as filtering route announcements Must work in a distributed competitive environment (vs. early centralized internet) Two types of BGP sessions e. BGP for routers from different ASes • Route information exchange between ASes i. BGP for routers within AS • Disseminating information about learned external routes within AS 14

How routes are distributed AS may be in three relations to another AS: Peer Customer Provider Typical model, not always so: Routes from customers are re-distributed to customers, peers and providers Peer-learned routes are re-distributed to customers but not to other peers nor to providers Provider-learned routes are re-distributed to customers, but not to other providers, nor to any peers 15

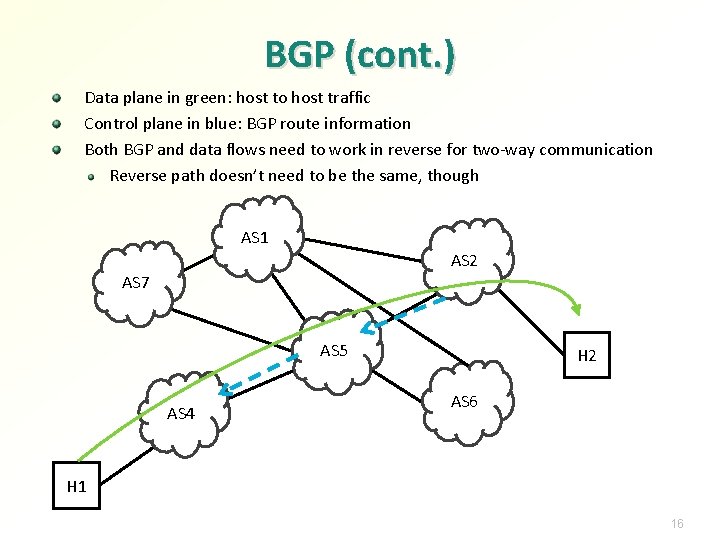
BGP (cont. ) Data plane in green: host to host traffic Control plane in blue: BGP route information Both BGP and data flows need to work in reverse for two-way communication Reverse path doesn’t need to be the same, though AS 1 AS 2 AS 7 AS 5 AS 4 H 2 AS 6 H 1 16

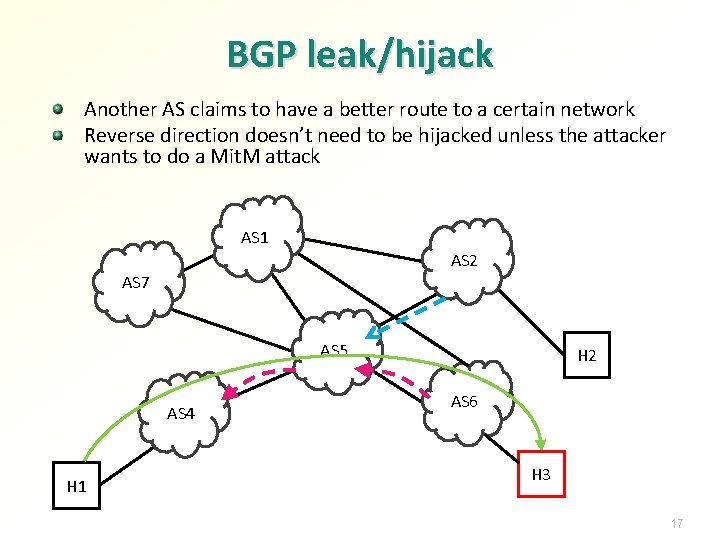
BGP leak/hijack Another AS claims to have a better route to a certain network Reverse direction doesn’t need to be hijacked unless the attacker wants to do a Mit. M attack AS 1 AS 2 AS 7 AS 5 AS 4 H 1 H 2 AS 6 H 3 17

How an AS is created Apply for an AS number from local Regional Internet Registry Get a connection to an IXP Could also just use a normal ISP -> waste of AS numbers Get transit or peering from another AS -> you’re on! 18

Security issues in routing 19

Attacks on BGP – outside Link cutting Physical Logical Do. S Attacks using data plane Clever use of data plane DDo. S to cut BGP connections 20

CXPST is an extension of previous low-rate TCP attack work on DDo. Sing big routers Ingredients: medium botnet (250000 bots) Internet structure recoinnassance Good timing Overwhelm one router at a time Router drops its BGP connections When the router is re-establishing BGP connections, target the neighbours Could theoretically take down large parts of internet 21

Attacks on BGP – inside Attacks on control plane Route leaks Route hijacks Man-in-the-Middle • Tricky but possible Possible to find attacker AS, though not trivial 22

How to get inside? Set up a throw-away AS Use false information and stolen credit cards Establish transit/peering No need to have many connections Advertise malicious routes Profit!! (or whatever you want to do with the traffic you get) Leave the AS untended 23

Route leaking / hijacking Route leaking Accidental by definition AS_x has multiple links to other Ases AS_x gets complete internet route announcement set from its provider AS_x accidentally announces the set through another AS link This wrong annoucement gets propagated -> all traffic from affected ASes goes to AS_x Route hijacking Malicious by definition AS_x announces a very good path to the target network ASes receiving the annoucement prefer this path and route directed to target to AS_x -> traffic directed to attack target from affected ASes gets intercepted by AS_x Could be indistinguishable from each other 24

BGP Man-in-the-Middle Traceroute & plan reply path to target Note the ASN’s seen towards target from traceroute & bgp table on your router Apply as-path prepends naming each of the ASN’s intended for reply path Set up static routes towards the next hop of the first AS in reply path -> done 25

Attacks

Traffic snooping Comprehensive traffic recording? This might already be going on without need for BGP attacks Popularization of IXPs? ”A few people operate the SIX with a few Cisco switches in a rack. Essentially every major carrier and service provider now connects to the SIX. . ” Not really indicative of any real problem with IXPs, just that there are many different parties involved in getting a data packet from source to destination 27

Traffic spoofing MITM for all traffic Can also modify, possibly without detection Total interception Faked replies Censorship purposes Dropping / reseting / redirecting replies 28

Other Spamming (fly-by) Capture a network that hasn’t been used for malicious activity Send spam from the network Network gets blocked Repeat Do. S Capture the target network Drop the incoming traffic Target impersonation Capture the target network Reply to incoming traffic with valid responses of your own Attacking the routers themselves Default passwords 29

How to react? Analysis of what is happening Where the attack originates Malicious vs. Accidental Malicious attacks difficult to stop • Must get several ASes to cooperate in filtering out the offending route announcements Accidents fixed by informing the origin of the erronous traffic -> fixes in minutes, usually After origin is fixed the global routing state corrects itself Complete correction might take a long time: hours/days 30

Solutions (? ) 31

Sanity checks Maximum number of routes accepted from a neighbouring AS Helps against accidental ”all-of-internet here” route leaks Not accepting too specific routes /22 probably ok, /32 suspicious Cutting BGP sessions that clearly advertise erronous routes Might cause even worse problems 32

Origin authentication An AS gets a crypto certificate from its RIR containing its network and AS number It’s possibly to verify AS identity using Resource Public Key Infrastructure (RPKI) Additional overhead Many routers don’t support RPKI 33

Secure Origin BGP Certificate-based system, backed by Cisco Options for transporting certificates by various means Even on data plane Tweaking routes by accepting some and denying some possible 34

Secure BGP Certificate-based system, pretty much similar to so. BGP Requires PKI 35

Data-plane verification Requires functionality on both control and data plane In addition to doing normal BGP operation check for data plane reachability problems Works for blackholing, accidents and stale routes Does not require PKI infrastructure Overhead! 36

Censorship and avoidance 37

Great firewall of China Does snooping filtering DNS injection Also tries to prevent accessing foreign proxies for free internet access Unwittingly also affects also traffic transiting through China For instance German subnets have received censored DNS replies Hopefully fixed since published fall 2012 38

Decoy Routing Setup routers with special functionality randomly around the internet Censored end host apparently try to access allowed content A special router is on path to allowed content The special router recognizes the end host are routes request to censored content Censored content origin is faked to look like allowed content origin Censored end host receives the censored content 39

Problems in previous proposal The special routers need to be on the traffic path Number of routers required already quite high. . especially if the censor has lots of connections If the censor is capable of modifying routing Interconnectivity way too high to deploy enough routers Nation-wide censorship usually is routing-capable 40

More case studies 41

AS 7007 incident, 1997. . where the BGP worries started AS 7007 started leaking a large part of complete route table -> Much of traffic in internet blackholed Took priority in BGP due to chopping announced networks to /24 blocks BGP cleanup took quite a while 42

ICANN DNS root server L, 2008 ICANN moved root server L to a new IP address Regardless, the old IP kept responding to DNS requests 43

Pakistan blocking Youtube, 2008 Country-internal blocking by leaked to the whole internet 44

China Telecom 2010 China “leaked”routes and captures a significant portion of internet traffic for some minutes 45

Australia outage, 2012 30 mins Filtering failure leading to route leakage leading to BGP session kill due to maximum prefix limiting 46

Summary Logical structure of internet is a function of commercial interests and geography Internet routing is largely based on trust and correct operation Don’t blindly trust internet routing Good practises help! http: //tools. ietf. org/html/draft-jdurand-bgp-security-00 47

Further reading BGP Man-in-the-Middle http: //www. defcon. org/images/defcon-16/dc 16 presentations/defcon-16 -pilosov-kapela. pdf China's 18 -Minute Mystery http: //www. renesys. com/blog/2010/11/chinas-18 -minutemystery. shtml How the Internet in Australia went down under http: //www. bgpmon. net/how-the-internet-in-australia-wentdown-under/ How Secure are Secure Interdomain Routing Protocols? http: //research. microsoft. com/pubs/120428/bgpattack-full. pdf 48