Network Security Professor Dr Adeel Akram Firewalls SSL




































- Slides: 54

Network Security Professor Dr. Adeel Akram

Firewalls, SSL, VPN and IPSec

Outline ► Types of firewalls § Static Packet Filter § Dynamic (Stateful) Packet Filters § Circuit Level Gateway § Application Level Gateway ► Transport ► VPN ► IPSec Layer Security / SSL

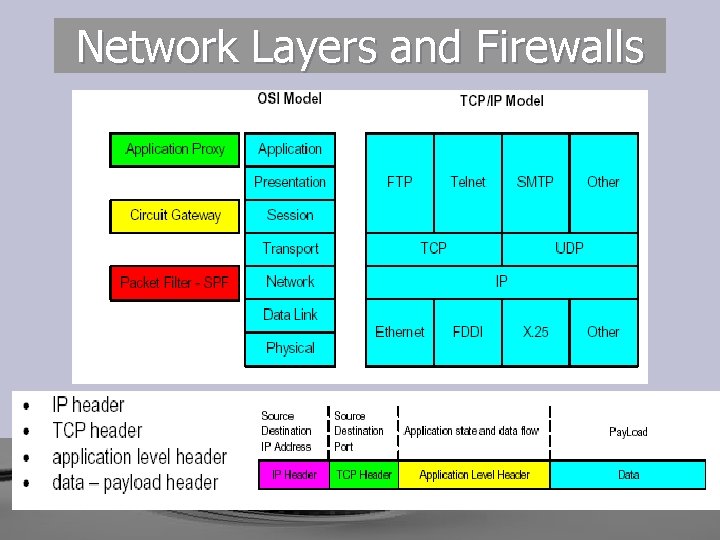
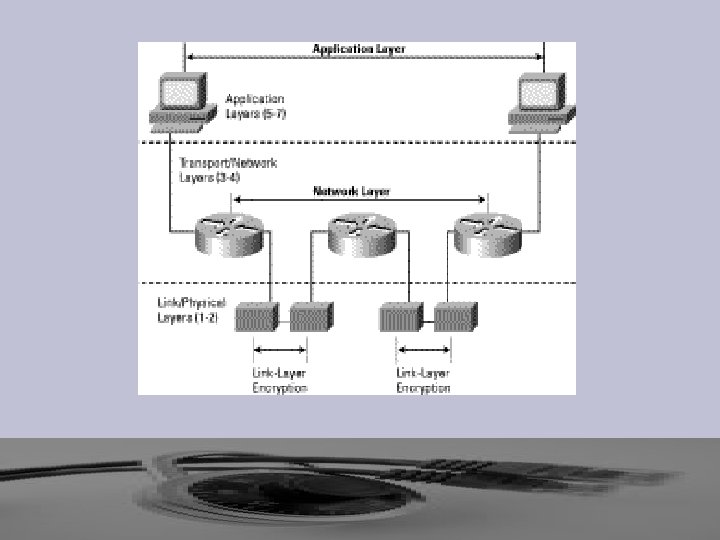
Network Layers and Firewalls

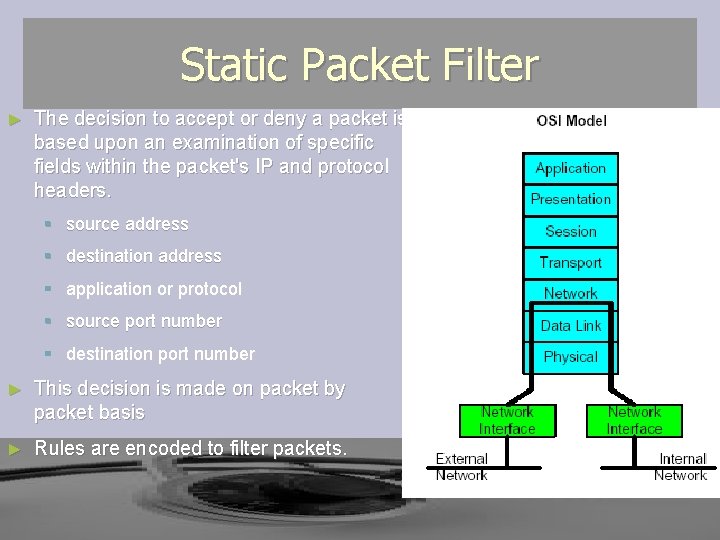
Static Packet Filter ► The decision to accept or deny a packet is based upon an examination of specific fields within the packet's IP and protocol headers. § source address § destination address § application or protocol § source port number § destination port number ► This decision is made on packet by packet basis ► Rules are encoded to filter packets.

Static Packet Filter ►A packet filter only examines data in the IP header and TCP header; it cannot know the difference between a real and a forged address. ► If an address meets the packet filter rules along with the other rule criteria, the packet will be allowed to pass.

IP Address Spoofing ► Suppose all packets from unknown IP addresses are filtered out. ► If a Hacker can find the IP address of one trusted client then the hacker can change the source address on the malicious IP packet and use the address of the trusted client.

Static Packet Filter Considerations Pros Cons Low impact on network performance. Operates only at network layer therefore it only examines IP and TCP headers. Low cost – now included Unaware of packet payload – offers low with many OSs level of security. Lacks state awareness – may require numerous ports be left open to facilitate services which use dynamically allocated ports. Susceptible to IP spoofing Difficult to create rules Only provides a low level of protection

Packet Filtering Firewall: Terminology ► Static (Stateless) Firewall: The firewall makes a decision on a packet by packet basis. ► Dynamic (Stateful) Firewall : The firewall keeps state information about transactions (connections).

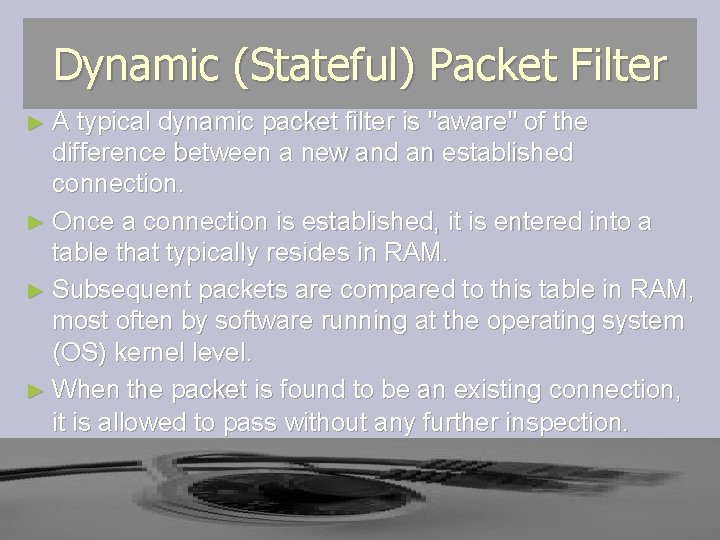
Dynamic (Stateful) Packet Filter ► A typical dynamic packet filter is "aware" of the difference between a new and an established connection. ► Once a connection is established, it is entered into a table that typically resides in RAM. ► Subsequent packets are compared to this table in RAM, most often by software running at the operating system (OS) kernel level. ► When the packet is found to be an existing connection, it is allowed to pass without any further inspection.

Dynamic (Stateful) Packet Filter ► By avoiding having to parse the packet filter rule base for each and every packet that enters the firewall ► and by performing this already established connection table test at the kernel level in RAM, ► the dynamic packet filter enables a measurable performance increase over a static packet filter.

Dynamic (Stateful) Packet Filter ► State creation must follow the handshake needed for connection creation.

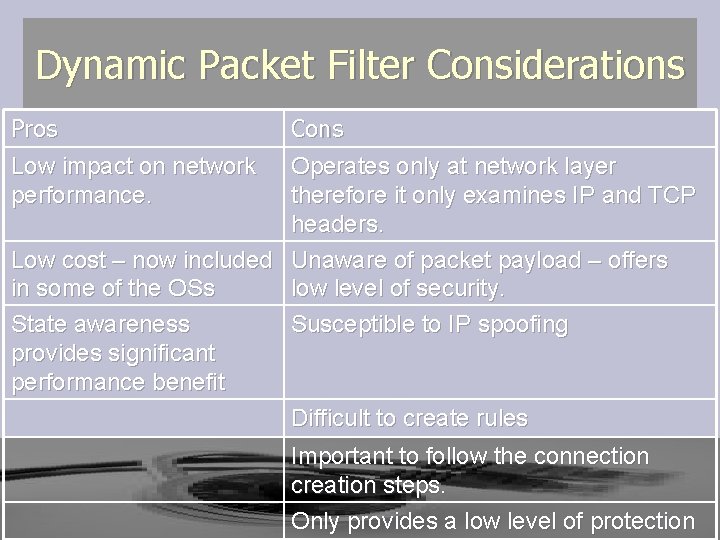
Dynamic Packet Filter Considerations Pros Cons Low impact on network performance. Operates only at network layer therefore it only examines IP and TCP headers. Low cost – now included Unaware of packet payload – offers in some of the OSs low level of security. State awareness Susceptible to IP spoofing provides significant performance benefit Difficult to create rules Important to follow the connection creation steps. Only provides a low level of protection

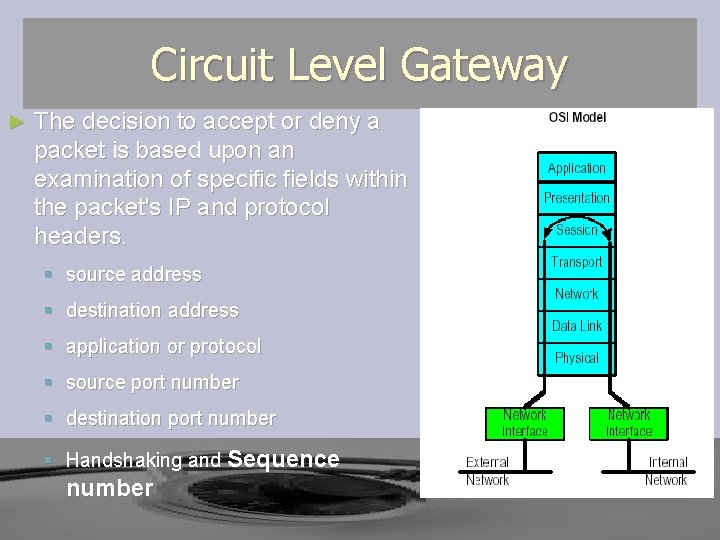
Circuit Level Gateway ► The decision to accept or deny a packet is based upon an examination of specific fields within the packet's IP and protocol headers. § source address § destination address § application or protocol § source port number § destination port number § Handshaking and Sequence number

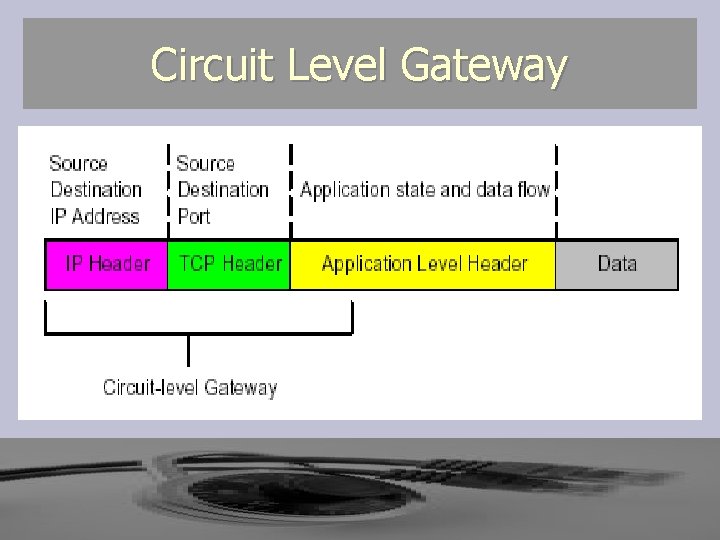
Circuit Level Gateway

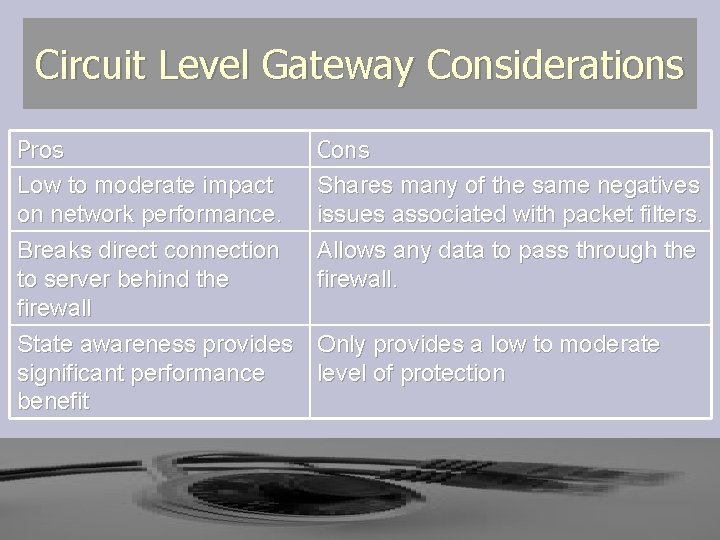
Circuit Level Gateway Considerations Pros Low to moderate impact on network performance. Breaks direct connection to server behind the firewall State awareness provides significant performance benefit Cons Shares many of the same negatives issues associated with packet filters. Allows any data to pass through the firewall. Only provides a low to moderate level of protection

Application Level Proxy ► An application level gateway intercepts the incoming and outgoing packets ► Run proxies that prevent direct connection between a trusted server or client and an untrusted host. ► Proxies examine the entire packet and can filter packets at the application layer. ► Proxies are application specific.

Application Level Gateway ► ► ► Current technology application level gateways are often referred to as strong application proxies. A strong application proxy extends the level of security afforded by the application level gateway. Instead of copying the entire datagram on behalf of the user, a strong application proxy actually creates a brand new empty datagram inside the firewall. Only those commands and data found acceptable to the strong application proxy are copied from the original datagram outside the firewall to the new datagram inside the firewall. By employing this methodology the strong application proxy can mitigate the risk of an entire class of covert channel attacks.

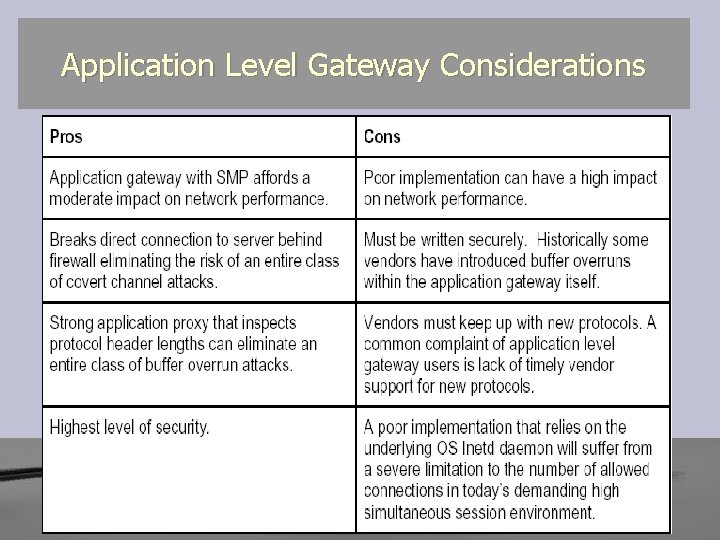
Application Level Gateway Considerations

Covert Channel Attacks ► ICMP_ECHO traffic can be used to construct covert communications channels through networks. ► The normal "ping" protocol states that one site (the pinger) sends an ICMP_ECHO packet to the target (the pingee). The pingee then sends an ICMP_ECHOREPLY back. ► ICMP_ECHO packets have an option to include a data section that usually stores timing information to determine round-trip packet times.

Covert Channel Attacks ► Firewalls and filtering routers do not check the data content, so it is possible to transmit malicious information in this packet. ► This is a covert channel. Most network routers pass, drop or return ICMP traffic. Since they don't filter the data content, it is possible to masquerade Trojan packets as valid ICMP_ECHO packets. ► One example of this type of attack is described in Phrack Magazine and is called Project Loki.

Transport Layer Security

Transport Layer Security ►Lecture prepared using information from ►Chapter 7 of Network Security Essentials Applications and Standards by Stallings ►Section 8. 3. 3 of Computer Networks by Peterson and Davie ►Introduction to SSL. htm ►Analysis of SSL 3. 0 Protocol by Wagner and Schneier

SSL ► The Transport Layer Security protocols started with the Secure Socket Layer (SSL) protocol

SSL § So, what is it? § Secure Sockets Layer (version 3. 0) § According to the specification… “The primary goal of the SSL Protocol is to provide privacy and reliability between two communicating applications. The protocol allows client/server applications to communicate in a way that is designed to prevent eavesdropping, tampering, or message forgery. ”

SSL § Designed with four basic goals § Cryptographic security § Interoperability § Extensibility § Relative efficiency

SSL § SSL has three basic properties: § The connection is private. Encryption is used after an initial handshake to define a secret key. Symmetric cryptography is used for data encryption (e. g. , DES, RC 4, etc. ) § The peer's identity can be authenticated using asymmetric, or public key, cryptography (e. g. , RSA, DSS, etc. ). § The connection is reliable. Message transport includes a message integrity check using a keyed MAC. Secure hash functions (e. g. , SHA, MD 5, etc. ) are used for MAC computations.

SSL/TLS § Well then, what is TLS? § Transport Layer Security (version 1. 0) SSL was developed by Netscape. The standards community wanted their own version free from any patents/restrictions § Thus was born TLS § § IETF changed the name to avoid showing bias § We’ll use the two terms interchangeably

SSL/TLS § Users want to connect to servers without the connection being listened to (securely) § E. g. Electronic commerce § Every server has a certificate § Basically a public key § Signed by a trusted third party

SSL Services ► SSL server authentication allows a user to confirm a server’s identity (SSL Certificates). ► SSL client authentication allows a server to confirm a client’s identity ► An encrypted SSL connection allows confidential information exchange.

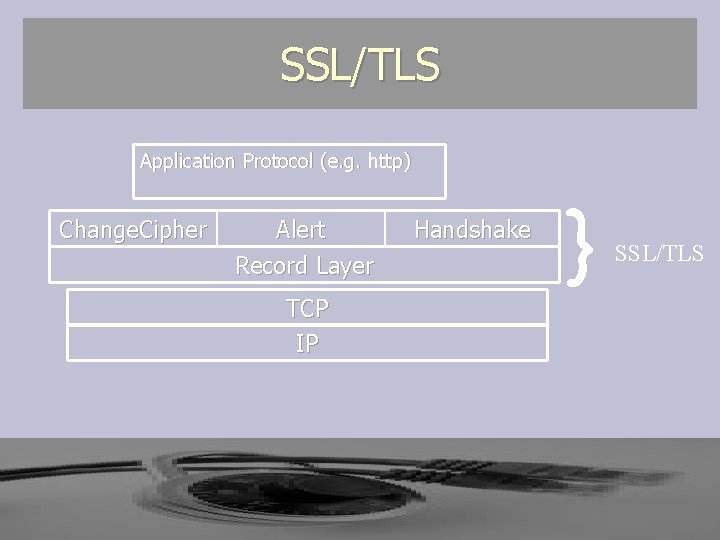
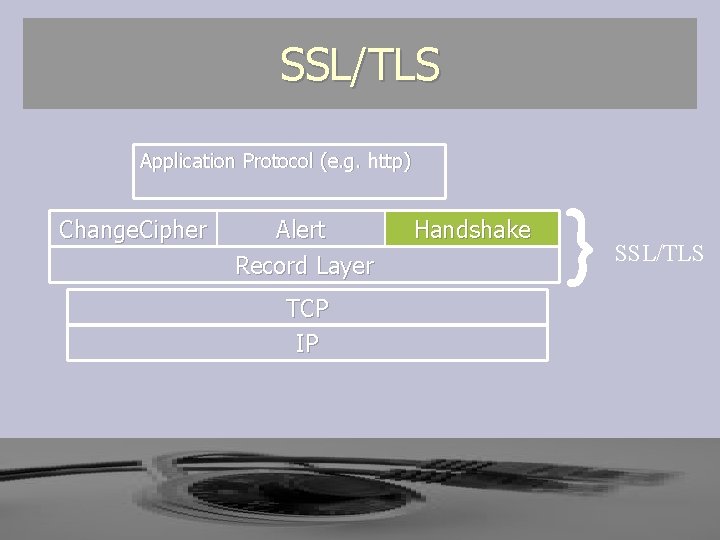
SSL/TLS Application Protocol (e. g. http) Change. Cipher Alert Record Layer TCP IP Handshake } SSL/TLS

SSL/TLS ► SSL consists of two protocol layers ► The Record Layer encapsulates all messages § The Handshake protocol negotiates all options of the session § The Alert protocol indicates errors or other caution conditions have occurred in the connection § The Change. Cipher. Spec protocol indicates the channel is ready for secure communications

SSL/TLS Application Protocol (e. g. http) Change. Cipher Alert Record Layer TCP IP Handshake } SSL/TLS

SSL/TLS ► The SSL Record Layer Provides § Confidentiality § Authenticity § Replay Protection ► Over a connection oriented reliable transport protocol like TCP

SSL/TLS Application Protocol (e. g. http) Change. Cipher Alert Record Layer TCP IP Handshake } SSL/TLS

SSL/TLS Application Protocol (e. g. http) Change. Cipher Alert Record Layer TCP IP Handshake } SSL/TLS

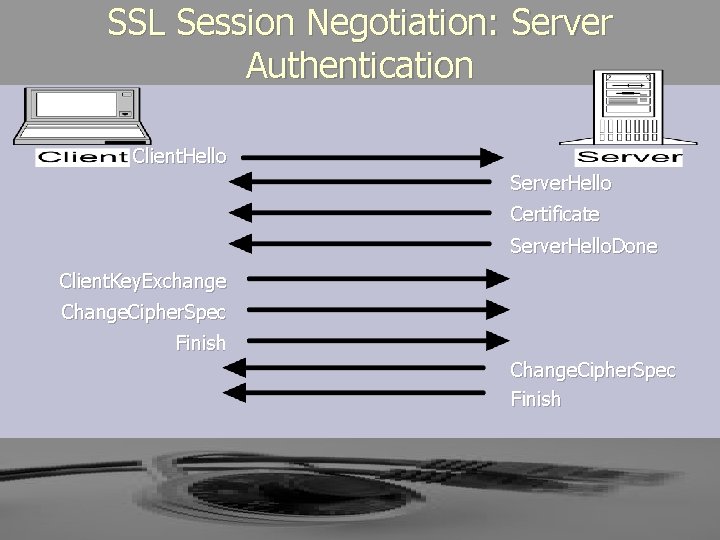
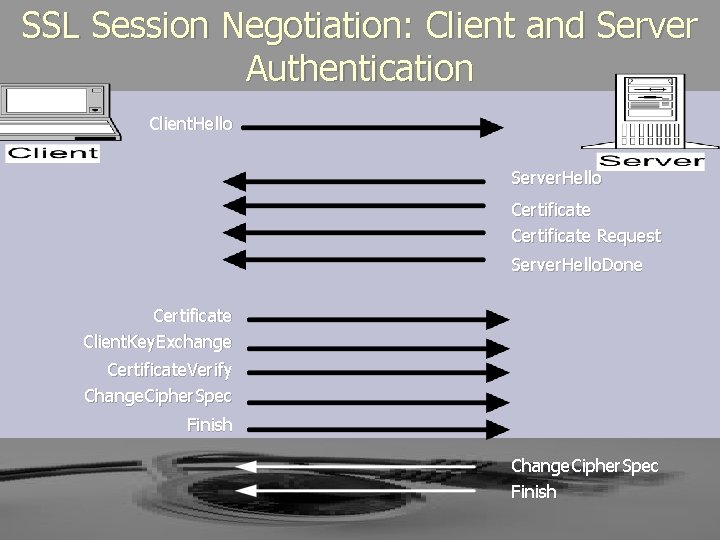
► The SSL protocol uses a combination of public-key and symmetric key encryption. ► An SSL session always begins with an exchange of messages called the SSL handshake. ► The handshake allows § the server to authenticate itself to the client using publickey techniques, § the client to authenticate itself to the server optionally § the client and the server to cooperate in the creation of symmetric keys used for rapid encryption, decryption, and tamper detection during the session that follows.

SSL Session Negotiation: Server Authentication Client. Hello Server. Hello Certificate Server. Hello. Done Client. Key. Exchange Change. Cipher. Spec Finish

SSL Session Negotiation: Client and Server Authentication Client. Hello Server. Hello Certificate Request Server. Hello. Done Certificate Client. Key. Exchange Certificate. Verify Change. Cipher. Spec Finish

SSL/TLS Application Protocol (e. g. http) Change. Cipher Alert Record Layer TCP IP Handshake } SSL/TLS

Virtual Private Networks (VPN) § What is a VPN? § “…a group of two or more computer systems, typically connected to a private network with limited public-network access, that communicates ‘securely’ over a public network. ” § “A combination of tunneling, encryption, authentication and access control technologies and services used to carry trusted traffic over an Untrusted IP network”

Virtual Private Networks (VPN) § What makes a VPN secure? § Encryption § Strong authentication of remote users and hosts. § Mechanisms for hiding or masking information about the private network topology from potential attackers

VPN ► If we are going to create a VPN using Internet it is tempting to make all IP traffic secure. ► A VPN may support many different applications § § Distributed computing resources Vo. IP SNMP FTP ► These applications have very different requirements.


Outline ► IP Security Overview ► IP Security Architecture ► Authentication Header ► Encapsulating Security Payload ► Combinations of Security Associations ► Key Management

IPSEC in a few words ► IPSec is an IETF standard for real-time communication security. ► In such a protocol, Alice initiates communication with a target, Bob. ► Each side authenticates itself to the other based on some key that the other side associates with it. ► Then they establish secret session keys (4 keys, one for integrity protection, and one for encryption, for each direction).

IP Security Overview ► IPSEC is a framework for security that operates at the Network Layer by extending the IP Packet Header ► This gives the ability to encrypt any higher layer protocol, including arbitrary TCP and UDP sessions. ► This flexibility comes with complexity. ► IPSEC’s complexity has be criticized quite severely in the literature.

IP Security Scenario

IP Security Overview ► IPSEC is highly modular. It allows users to select from § a variety of encryption algorithms § And specialized security protocols ► IPSEC allows users to select from a large menu of security services including § § Access control Authentication Confidentiality Protection against replay attacks

IP Security Architecture ► IPSEC has two major components. § The first component is a pair of protocols that implements security services provided by IPSEC § The second component provides support for key management

IP Security Architecture – Security Services ► In IPSEC security services are provided by a pair of protocols § The Authentication Header (AH) protocol provides ► Access control ► Connectionless message integrity ► Authentication ► Anti-replay protection § The Encapsulating Security Payload (ESP) protocol provides ► All the services provided by AH ► Confidentiality

IP Security Architecture – Key Management ► Key management is done by a protocol known as Internet Security Association and Key Management Protocol (ISAKMP)

IP Security Architecture ► IPSec documents: § RFC 2401: An overview of security architecture § RFC 2402: Description of a packet encryption extension to IPv 4 and IPv 6 § RFC 2406: Description of a packet encryption extension to IPv 4 and IPv 6 § RFC 2408: Specification of key managament capabilities

Questions ? ? ? ? ? ? ? ? ? adeel. akram@gmail. com