Network Security Management Tools Objectives Upon completion of

Network Security Management Tools

Objectives Upon completion of this chapter, you will be able to: • Describe security vulnerability testing, detection, and auditing tools useful in the Cisco network security environment Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -2

Integrity Testing Tools Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -3
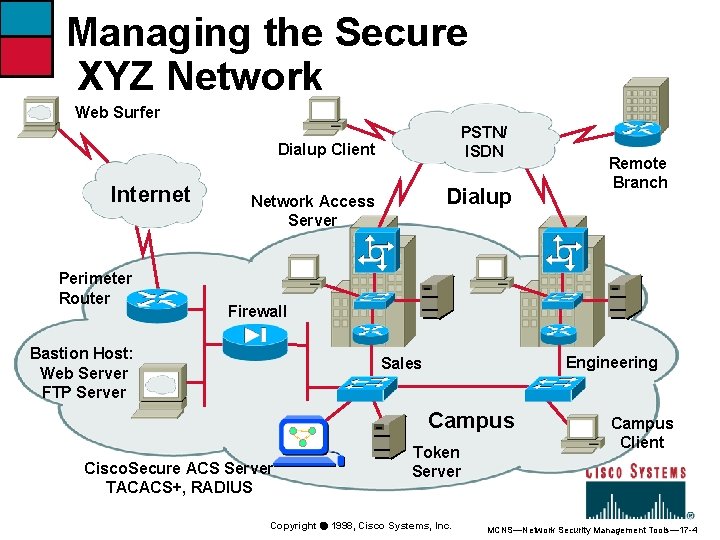
Managing the Secure XYZ Network Web Surfer PSTN/ ISDN Dialup Client Internet Perimeter Router Dialup Network Access Server Remote Branch Firewall Bastion Host: Web Server FTP Server Engineering Sales Campus Cisco. Secure ACS Server TACACS+, RADIUS Token Server Copyright ã 1998, Cisco Systems, Inc. Campus Client MCNS—Network Security Management Tools— 17 -4
Scanners • ISS Safe. Suite (UNIX and NT) Top commercial scanner Suite of several scanners with GUI • SATAN (UNIX) Security Administrator’s Tool for Analyzing Networks Scans remote hosts for most known security holes Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -5
Scanners (cont. ) • NSS (UNIX) • Strobe (UNIX) • Jackal (UNIX) • Ident. TCPScan (UNIX) • CONNECT (UNIX) • FSPScan (Windows, OS/2) • XSCAN (UNIX) Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -6
Sniffers • Network General Sniffer • Network General XRay • Gobbler (DOS/Windows) • ETHLOAD • Netman suite (Etherman) • Esniff. c • Network Monitor (Microsoft) Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -7
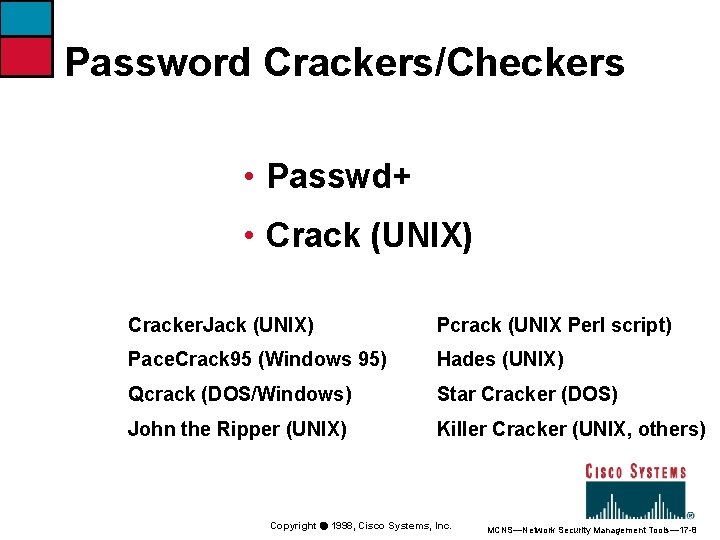
Password Crackers/Checkers • Passwd+ • Crack (UNIX) Cracker. Jack (UNIX) Pcrack (UNIX Perl script) Pace. Crack 95 (Windows 95) Hades (UNIX) Qcrack (DOS/Windows) Star Cracker (DOS) John the Ripper (UNIX) Killer Cracker (UNIX, others) Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -8
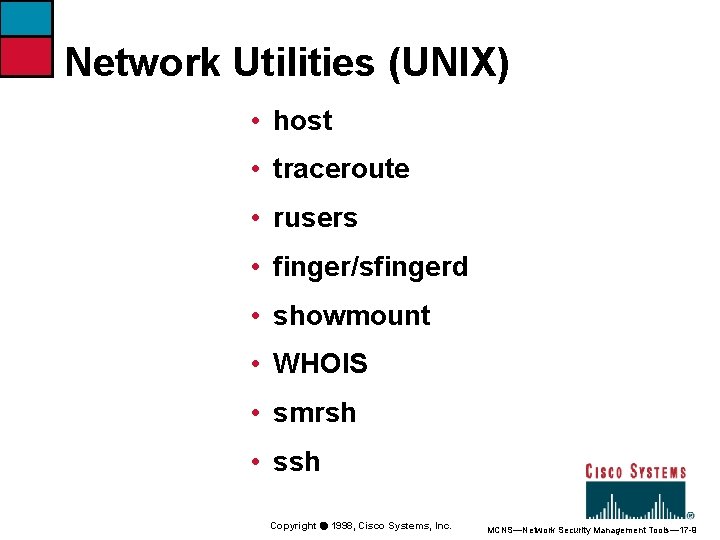
Network Utilities (UNIX) • host • traceroute • rusers • finger/sfingerd • showmount • WHOIS • smrsh • ssh Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -9

Logging Tools • TCP_Wrapper • swatch • trimlog • logdaemon (UNIX) Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -10
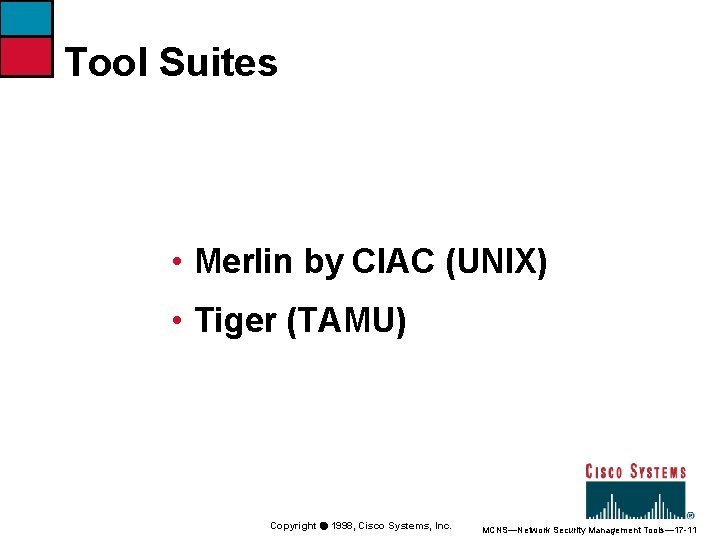
Tool Suites • Merlin by CIAC (UNIX) • Tiger (TAMU) Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -11
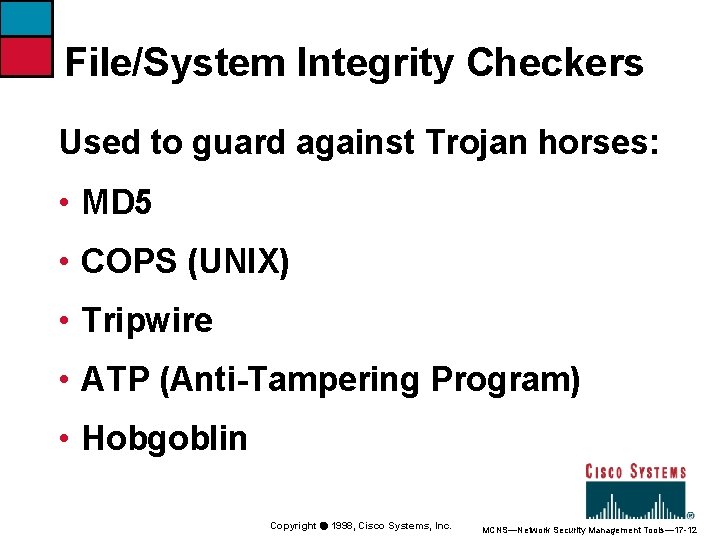
File/System Integrity Checkers Used to guard against Trojan horses: • MD 5 • COPS (UNIX) • Tripwire • ATP (Anti-Tampering Program) • Hobgoblin Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -12
System Monitors • Windows/NT • Cinco Ne. TXray for Win 95 and NT • Ultra. Scan v 1. 2 Port Scanner for NT • Kane Security Analyst for NT • Microsoft EP Dump for NT • Microsoft. C 2 CERT Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -13
Windows 95 Tools • Net. Scan Tools • Network Toolbox • TCP/IP Surveyor Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -14
Macintosh Tools • Mac. TCP Watcher • Query It! • What. Route Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -15

Cisco IOS Software Commands • traceroute • show ip route • debug ip packet • rmon • show ip ? Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -16

Chapter References The following sites contain security tools: • ftp: //ciac. llnl. gov/pub/ciac/sectools/unix/ • ftp: //coast. cs. purdue. edu/pub/tools/ • ftp: //ftp. cert. org/pub/tools/ • ftp: //ftp. win. tue. nl/pub/security/ • ftp: //ftp. funet. fi/pub/unix/security/ • http: //www. rootshell. com/ • http: //filepile. com/ • http: //www. iss. net/ Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -17
Summary • Scanners automatically detect security weaknesses • ISS and SATAN are two of the most popular scanners • Sniffers capture packet traffic for later analysis • Password crackers and checkers can be used to detect weak passwords, improving password security • UNIX is the most powerful operating system for network security, because it has many network utilities • Network logging tools are useful for detecting intrusions • Network security tools are also available for Windows NT and 95, DOS, Macintosh, and OS/2 • Cisco IOS software has commands useful for security Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -18

Review Questions Q 1. Which network security tool for the Windows NT platform would be useful for automatically detecting security weaknesses as part of managing network security? A) ISS Safesuite Q 2. What is the Cisco IOS software command that can substitute for a packet sniffer? A) debug ip packet Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -19

Review Questions (Cont’d) Q 3. How can password crackers and checkers be used in managing network security? A) Password crackers and checkers can be used to detect weak passwords, improving password security Q 4. Which operating system has the largest selection of network security utilities? A) UNIX is the most powerful operating system for network security, because it has many network utilities Copyright ã 1998, Cisco Systems, Inc. MCNS—Network Security Management Tools— 17 -20
- Slides: 20