Network Security Lab Jelena Mirkovic sunshinecis udel edu

Network Security Lab Jelena Mirkovic sunshine@cis. udel. edu Sig New. Grad presentantion

Main Research Areas n Distributed Denial of Service n n Distributed defense: Def. COM Internet Worms Worm simulation: PAWS n Cooperative defense: WIN n Detecting new malicious executables n n Application-level Honeynets, summarizing firewall logs, predicting routing changes …
Distributed Denial of Service
Distributed Denial of Service
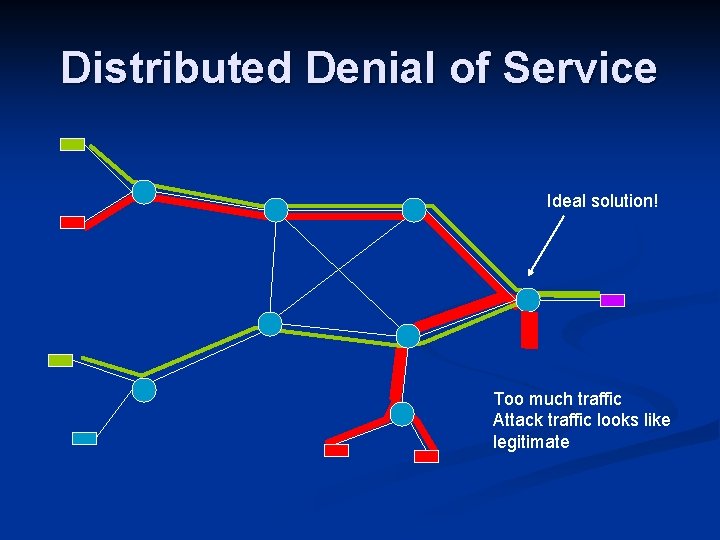
Distributed Denial of Service Ideal solution! Too much traffic Attack traffic looks like legitimate
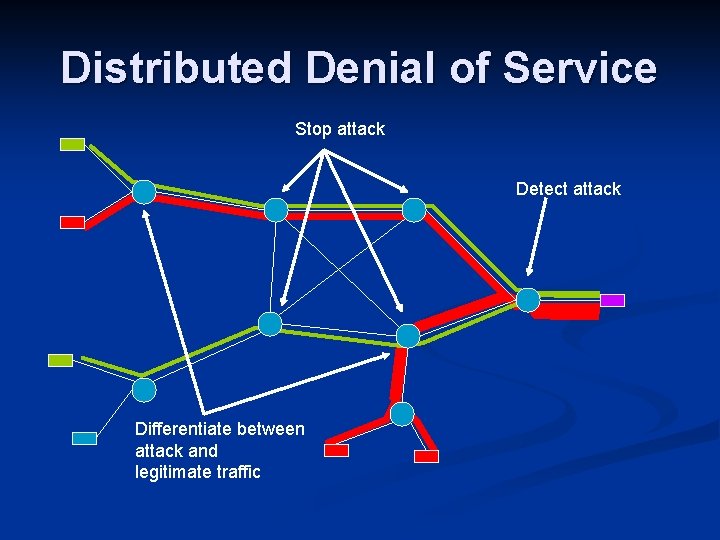
Distributed Denial of Service Stop attack Detect attack Differentiate between attack and legitimate traffic

Def. COM Distributed defense against DDo. S n Combines nodes at: n Victim – Alert generators: detect attack and alert other nodes n Core – Rate limiters: stop attack by dropping traffic n Source – Classifiers: differentiate between legitimate and attack traffic n n Nodes cooperate through an overlay
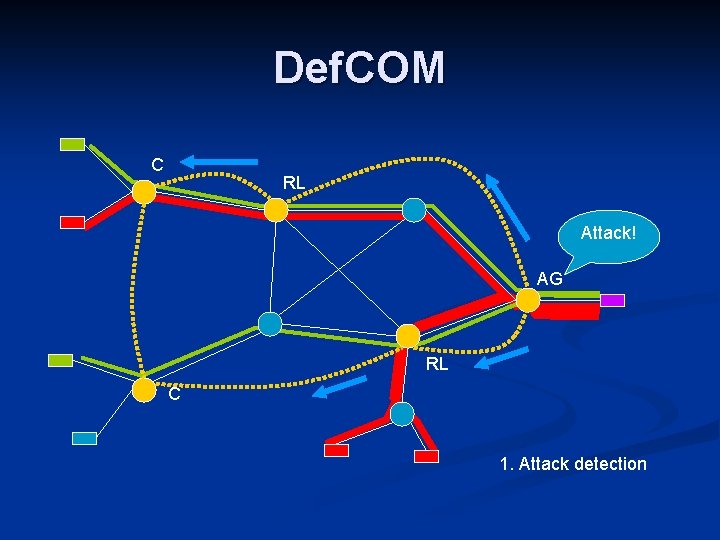
Def. COM C RL Attack! AG RL C 1. Attack detection
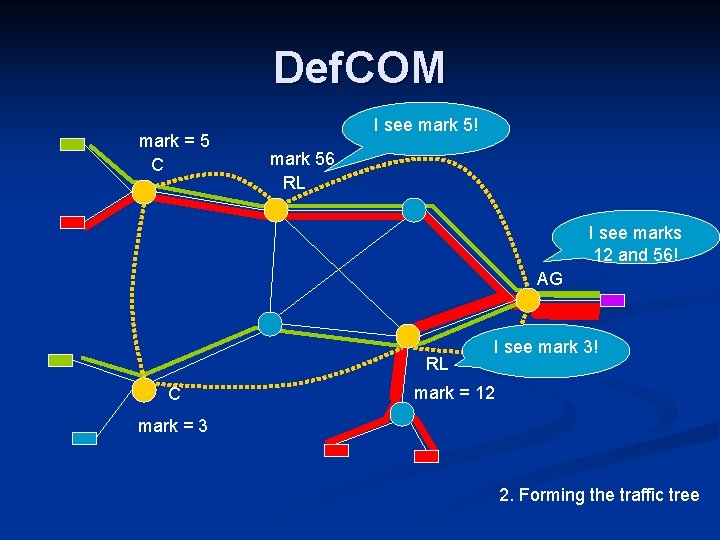
Def. COM mark = 5 C I see mark 5! mark 56 RL I see marks 12 and 56! AG RL C I see mark 3! mark = 12 mark = 3 2. Forming the traffic tree
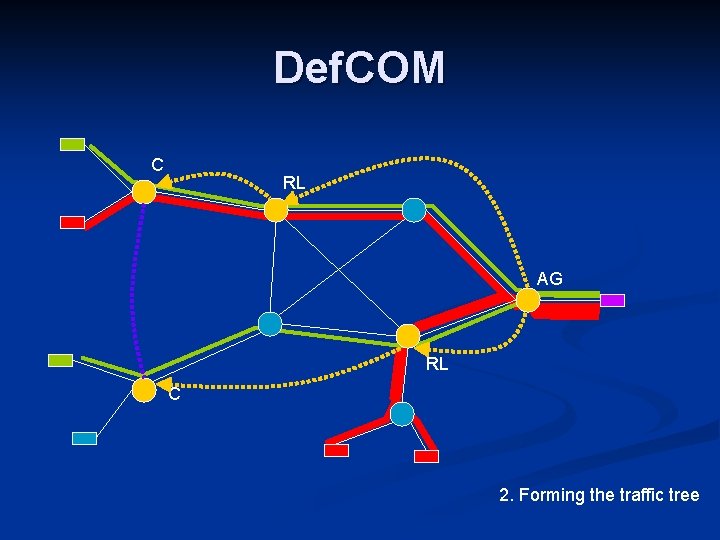
Def. COM C RL AG RL C 2. Forming the traffic tree
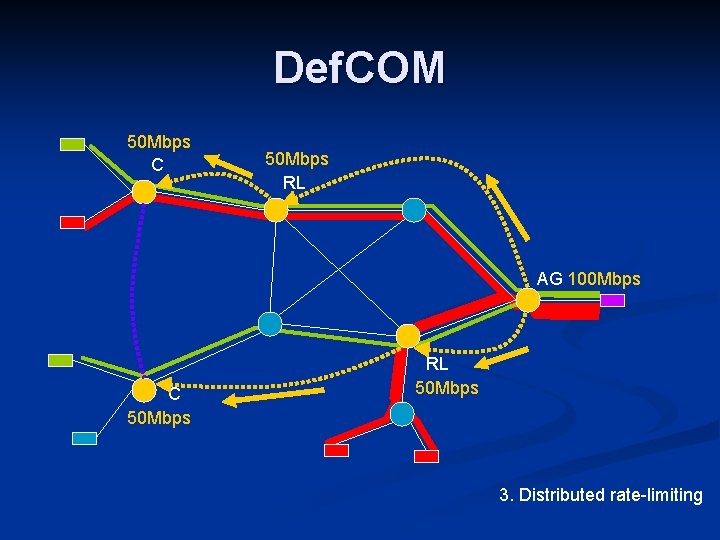
Def. COM 50 Mbps C 50 Mbps RL AG 100 Mbps C 50 Mbps RL 50 Mbps 3. Distributed rate-limiting
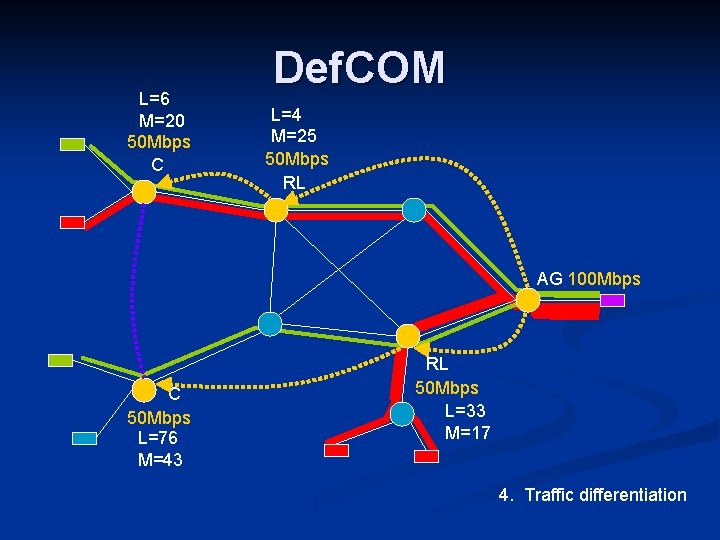
L=6 M=20 50 Mbps C Def. COM L=4 M=25 50 Mbps RL AG 100 Mbps C 50 Mbps L=76 M=43 RL 50 Mbps L=33 M=17 4. Traffic differentiation
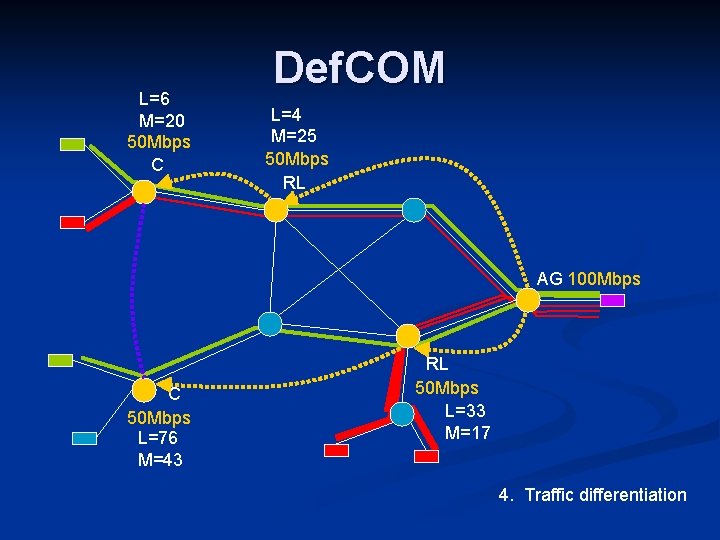
L=6 M=20 50 Mbps C Def. COM L=4 M=25 50 Mbps RL AG 100 Mbps C 50 Mbps L=76 M=43 RL 50 Mbps L=33 M=17 4. Traffic differentiation

Internet Worms Ø A program that: Ø Scans network for vulnerable machines Ø Breaks into machines by exploiting the found vulnerability Ø Installs some piece of malicious code – backdoor, DDo. S tool Ø Moves on Don’t need any user action to spread Ø Spread very fast! Ø

PAWS Ø Parallel worm simulator Ø Runs on multiple machines – gain memory and CPU resources Ø Can simulate greater detail than single-node simulators Ø Can simulate various defenses Ø Machines synchronize with network messages

WIN Worm information network Ø We need fast, automatic response to stop worms Ø Ø How can we detect worms Ø How can we devise signatures quickly and automatically Ø How can we share signatures with other networks Ø How can we accept signatures from others and be sure we won’t filter out legitimate traffic
- Slides: 16