Network Security Hacking Defense 2 From Computer Security


























- Slides: 42

Network Security Hacking & Defense 2 From Computer Security: Principles & Practice Chapter 3 Authentication

Objectives The student shall be able to: Ø Define these types of attacks: dictionary, rainbow table, eavesdrop, replay, brute force Ø Define purpose of salt and how it works Ø Describe features of password complexity and advantages of each Ø Show three ways of generating a secure password from a phrase Ø Calculate the number of possible combinations when lower case versus lower & upper case versus alphanumeric plus symbols are used. Ø Describe how remote user authentication works – packet sequence. Not in 2012: Class Time: The class shall be conducted as follows: Ø Lecture 1. 5 hour Ø Lab 1. 5 hour Ø Total 3 hours

Authenticated Attacks Once an attacker gains access: Escalating privilege: After obtaining a user account, next goal -> obtain Administrator status Ø Installing backdoors: To ensure future access Ø Covering tracks: Modifying logs, hiding existence Ø Making vulnerability secure, so system isn’t lost to other hackers. Ø

Privilege Escalation Hacker methods include: Ø Grabbing password hashes Ø DLL injection: Modify or replace the DLL with a Trojan (allowing back door entry) Ø Spoofing LPC Port Requests: Using Local Procedure Call (LPC) to impersonate a client and access a server Ø Install rootkit: includes installing backdoor, replacing existing utilities: ps, telnet

Many slides by William Stallings and Lawrie Brown: Computer Security COMPUTER SECURITY CHAPTER 3 – USER AUTHENTICATION FROM

User Authentication Ø fundamental security building block l basis of access control & user accountability Ø is the process of verifying an identity claimed by or for a system entity Ø has two steps: l l identification - specify identifier verification - bind entity (person) and identifier

Means of User Authentication Ø four means of authenticating user's identity Ø based on something the individual l l knows - e. g. password, PIN possesses - e. g. key, token, smartcard is (static biometrics) - e. g. fingerprint, retina does (dynamic biometrics) - e. g. voice, sign Ø can use alone or combined l ‘two-factor’ or ‘three-factor’ authentication Ø all can provide user authentication Ø all have issues

Password Authentication Ø widely used user authentication method l l user provides name/login and password system compares password with that saved for specified login Ø authenticates ID of user logging and l l l that the user is authorized to access system determines the user’s privileges is used in discretionary access control

Authentication Security Issues client attacks: keystroke monitoring host attacks: capture authentication file eavesdropping: observe or sniff password, keystroke monitor replay: play same password back trojan horse: captures authentication file denial-of-service: prevents access via flooding

Password Choices Ø users may pick short passwords l l e. g. 3% were 3 chars or less, easily guessed system can reject choices that are too short Ø users may pick guessable passwords l l l so crackers use lists of likely passwords e. g. one study of 14000 encrypted passwords guessed nearly 1/4 of them would take about 1 hour on fastest systems to compute all variants, and only need 1 break!

Password Cracking Ø dictionary attacks l try each word then obvious variants in large dictionary against hash in password file Ø rainbow table attacks l l precompute tables of hash values for all salts a mammoth table of hash values e. g. 1. 4 GB table cracks 99. 9% of alphanumeric Windows passwords in 13. 8 secs not feasible if larger salt values used

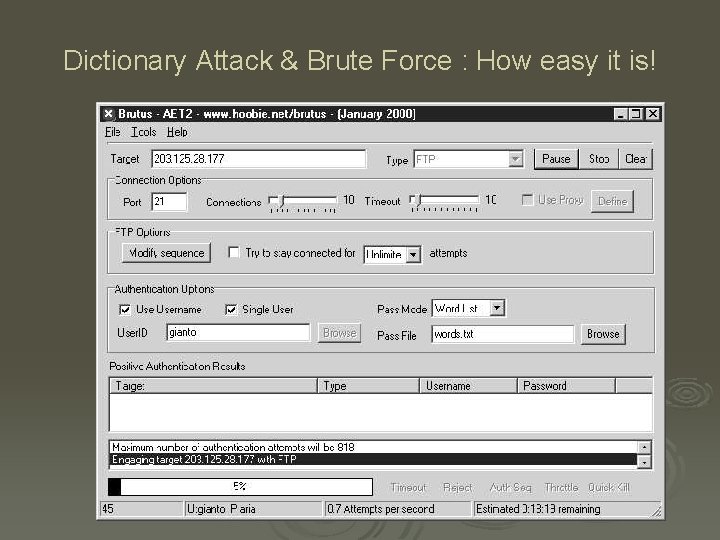
Dictionary Attack & Brute Force : How easy it is!

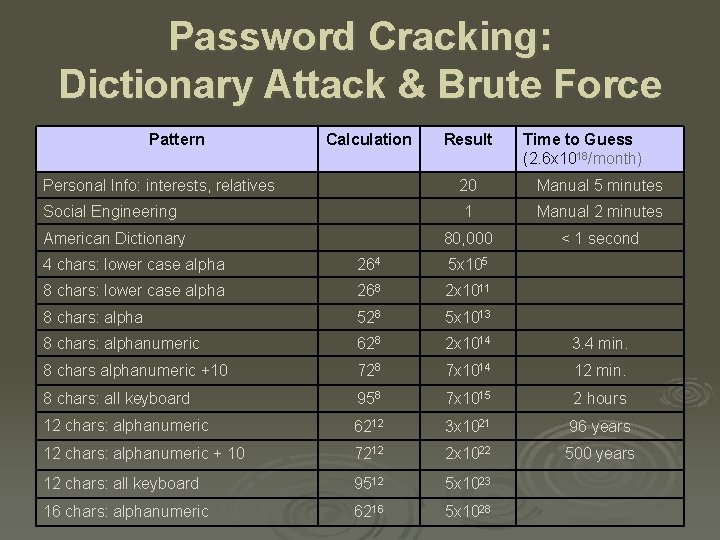
Password Cracking: Dictionary Attack & Brute Force Pattern Calculation Result Time to Guess (2. 6 x 1018/month) Personal Info: interests, relatives 20 Manual 5 minutes Social Engineering 1 Manual 2 minutes 80, 000 < 1 second American Dictionary 4 chars: lower case alpha 264 5 x 105 8 chars: lower case alpha 268 2 x 1011 8 chars: alpha 528 5 x 1013 8 chars: alphanumeric 628 2 x 1014 3. 4 min. 8 chars alphanumeric +10 728 7 x 1014 12 min. 8 chars: all keyboard 958 7 x 1015 2 hours 12 chars: alphanumeric 6212 3 x 1021 96 years 12 chars: alphanumeric + 10 7212 2 x 1022 500 years 12 chars: all keyboard 9512 5 x 1023 16 chars: alphanumeric 6216 5 x 1028

Password Vulnerabilities Single user focus Ø specific account attack Ø password guessing against known user Ø workstation hijacking: unattended console Ø exploiting user mistakes: write down passwd Ø exploiting same password: different machines Multi-user Ø electronic eavesdropping Ø offline dictionary attack Ø popular password attack

Password Complexity CIS Recommendations: Ø At least 8 (CIS: preferably 14) chars. Ø Password expires in 90 Days Ø Lockout after 5 bad login attempts Ø Reset count after 15 minutes Ø Lockout duration 15 minutes Ø Enforce password history (24 -count memory of passwords)

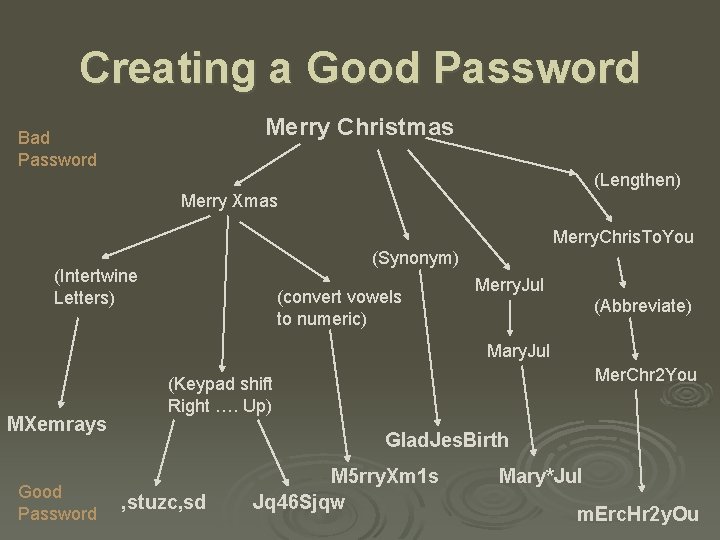
Creating a Good Password Merry Christmas Bad Password (Lengthen) Merry Xmas Merry. Chris. To. You (Synonym) (Intertwine Letters) (convert vowels to numeric) Merry. Jul (Abbreviate) Mary. Jul MXemrays Good Password Mer. Chr 2 You (Keypad shift Right …. Up) Glad. Jes. Birth , stuzc, sd M 5 rry. Xm 1 s Jq 46 Sjqw Mary*Jul m. Erc. Hr 2 y. Ou

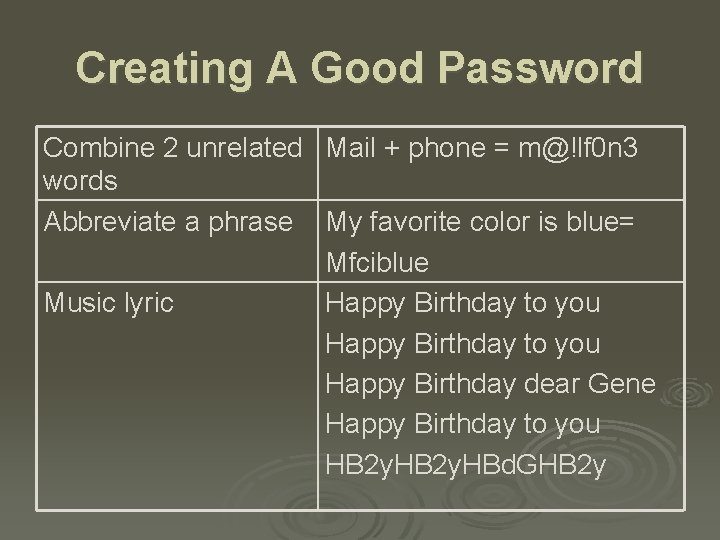
Creating A Good Password Combine 2 unrelated Mail + phone = m@!lf 0 n 3 words Abbreviate a phrase My favorite color is blue= Mfciblue Music lyric Happy Birthday to you Happy Birthday dear Gene Happy Birthday to you HB 2 y. HBd. GHB 2 y

Password Recommendations Change the default passwords on firewalls, services, servers, etc. Ø Never use ‘admin’ or ‘root’ or ‘administrator’ as a login for the admin l Use a software firewall on each computer system, with antivirus & antispyware. Ø A good password is: Ø l l l l Ø private: it is used and known by one person only secret: it does not appear in clear text in any file or program or on a piece of paper pinned to the terminal changed regularly: periodically change your password. easily remembered: so there is no need to write it down at least 8 characters but preferably 12 -14 a mixture of at least 3 of the following: upper case letters, lower case letters, digits and punctuation not guessable by any program in a reasonable time, for instance less than one week. Why you must change passwords Even if you choose a good password, it can still be discovered: l l someone may see you typing it or snoop network. If you accidentally type your password instead of your login name, it can be in system log files

Using Better Passwords Ø clearly there are problems with passwords Ø goal is to eliminate guessable passwords Ø while still easy for user to remember Ø techniques: l l user education computer-generated passwords reactive password checking proactive password checking

Proactive Password Checking Ø rule enforcement plus user advice, e. g. l l 8+ chars, upper/lower/numeric/punctuation may not suffice Ø password cracker l time and space issues Ø Bloom Filter l l use to build table based on dictionary using hashes check proposed password against this table

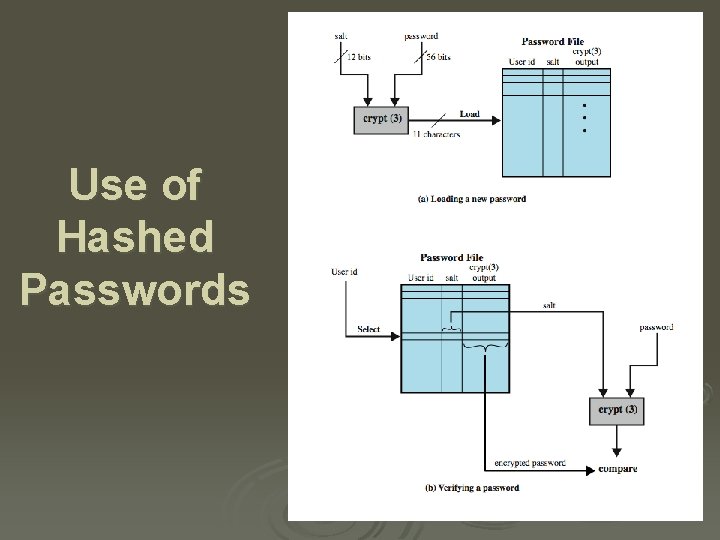
Use of Hashed Passwords

Salt + Password Salt : Ø prevents identical passwords from giving the same encrypted value. Ø increases length of password without requiring user to remember additional characters

UNIX Implementation Ø original scheme l l 8 character password form 56 -bit key 12 -bit salt used to modify DES encryption into a one-way hash function 0 value repeatedly encrypted 25 times output translated to 11 character sequence Ø now regarded as woefully insecure l e. g. supercomputer, 50 million tests, 80 min Ø sometimes still used for compatibility

Improved Implementations Ø have other, stronger, hash/salt variants Ø many systems now use MD 5 l l with 48 -bit salt password length is unlimited is hashed with 1000 times inner loop produces 128 -bit hash Ø Open. BSD uses Blowfish block cipher based hash algorithm called Bcrypt l uses 128 -bit salt to create 192 -bit hash value

Password File Access Control Ø can block offline guessing attacks by denying access to encrypted passwords l l Ø make available only to privileged users often using a separate shadow password file still have vulnerabilities l l l exploit O/S bug keystroke logger accident with permissions making it readable users with same password on other systems access from unprotected backup media sniff passwords in unprotected network traffic

Token Authentication Ø object user possesses to authenticate, e. g. l l embossed card magnetic stripe card memory card smartcard

Memory Card Ø store but do not process data Ø magnetic stripe card, e. g. bank card Ø electronic memory card Ø used alone for physical access Ø with password/PIN for computer use Ø drawbacks of memory cards include: l l l need special reader loss of token issues user dissatisfaction

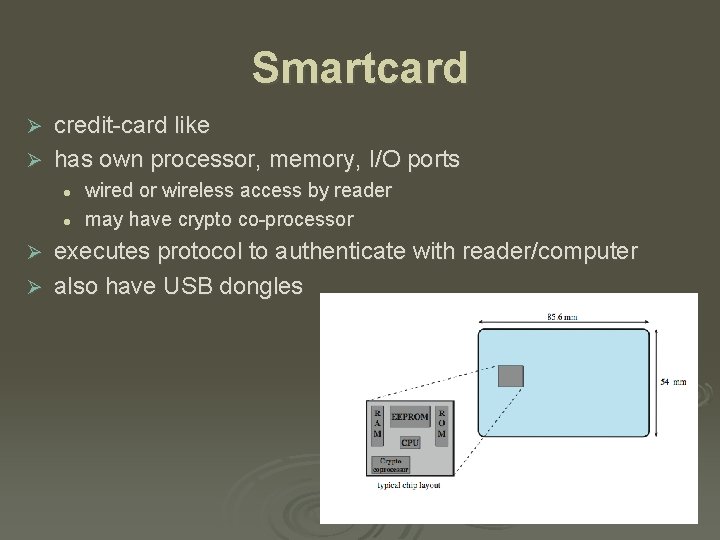
Smartcard credit-card like Ø has own processor, memory, I/O ports Ø l l wired or wireless access by reader may have crypto co-processor executes protocol to authenticate with reader/computer Ø also have USB dongles Ø

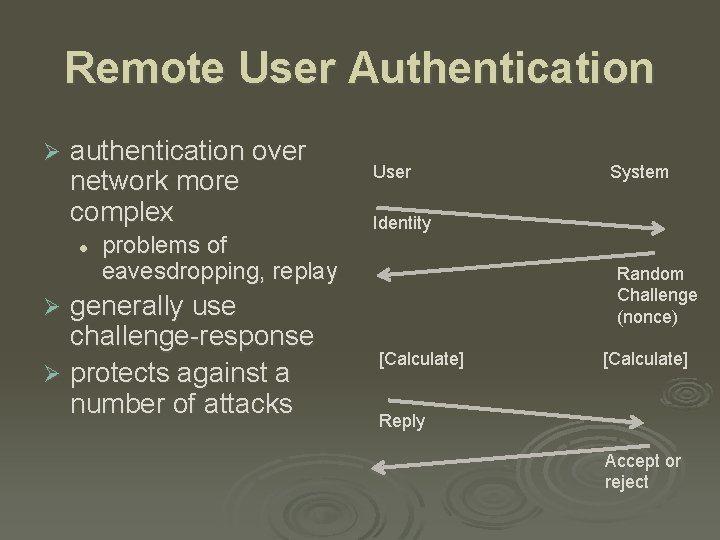
Remote User Authentication Ø authentication over network more complex l problems of eavesdropping, replay generally use challenge-response Ø protects against a number of attacks User System Identity Random Challenge (nonce) Ø [Calculate] Reply Accept or reject

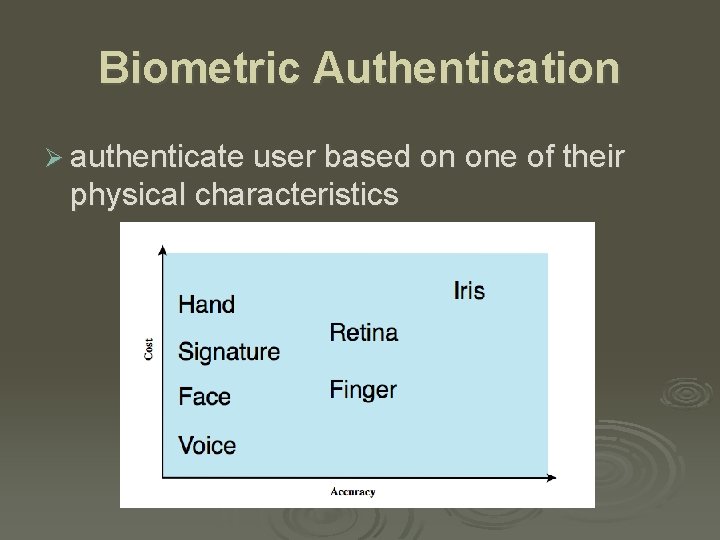
Biometric Authentication Ø authenticate user based on one of their physical characteristics

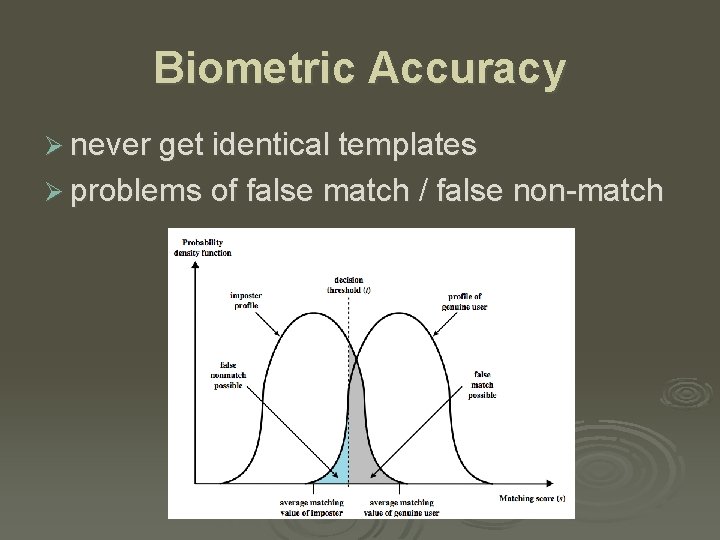
Biometric Accuracy Ø never get identical templates Ø problems of false match / false non-match

Countermeasures - Admin Establish the Administrator account as having no or few privileges Ø Use admin (root) account only when necessary (e. g. , not to read email) Ø Use longer passwords for admin accounts Ø For any system, never retain default passwords! Ø Name Administrator account something else Ø Set an account lockout threshold Ø l ensure it applies to Administrator particularly for remote access

Countermeasures - User Ø Check for and remove invalid accounts (e. g. , accounts not used in 30 days) Ø Enforce strong password policy Ø Enable audit account logon failures and review event logs regularly Ø Implement training & enforcement of policies Ø Enable automatic workstation lockout or logoff

Countermeasures – User Access Apply Principle of Least Privilege: Ø Grant minimum Permissions necessary Ø Provide access to files and database segments only as necessary Ø Specify as limited permissions (rwx) as possible Ø Limit use of admin accounts – no email Ø Separation of Duties in System Administration – the Administrator and separate log reader

Countermeasures - Computer Ø Do not allow boots from floppy or CDs Ø Lock up servers to prevent physical access Ø Do not use the same password from one machine to the next. (Minimally compartmentalize passwords) Ø Stop unauthorized access to password file

Countermeasures - Network Ø Ø Ø Ø Restrict access or disable SMB services on TCP port 139 & 445 at firewalls Monitor with intrusion detection Counter sniffing with encrypted network links: e. g. , IPSec Avoid software which sends passwords or operate in the clear: rlogin, telnet, POP 3, alerter, clipbook, … Limit permission on Windows shares (from Everyone – Full Control or Read) Eliminate or reduce anonymous or guest access Use mail packages that check for viruses.

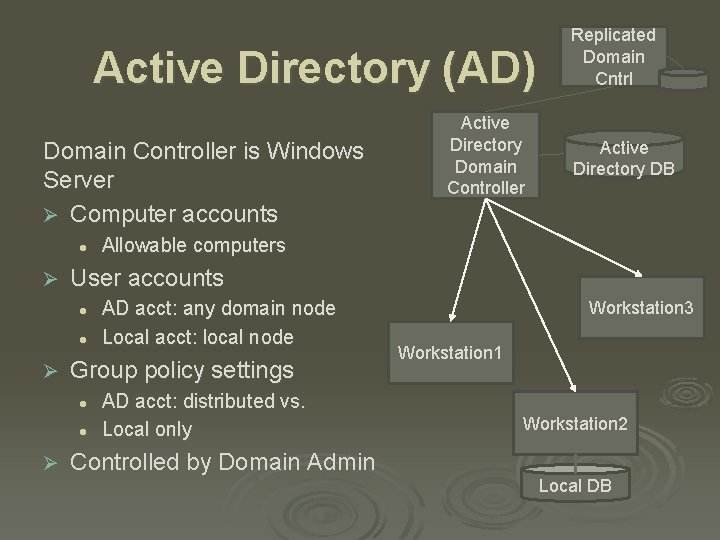
Active Directory (AD) Domain Controller is Windows Server Ø Computer accounts l Ø l Allowable computers AD acct: any domain node Local acct: local node Group policy settings l l Ø Active Directory DB User accounts l Ø Active Directory Domain Controller Replicated Domain Cntrl AD acct: distributed vs. Local only Controlled by Domain Admin Workstation 3 Workstation 1 Workstation 2 Local DB

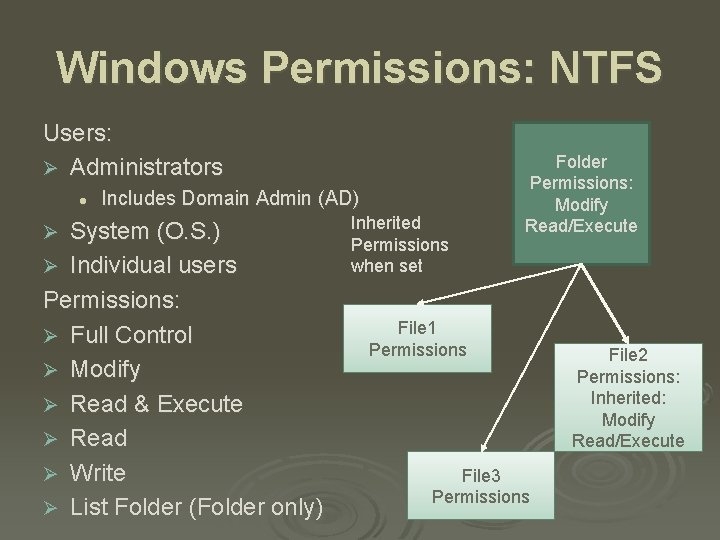
Windows Permissions: NTFS Users: Ø Administrators l Includes Domain Admin (AD) System (O. S. ) Ø Individual users Permissions: Ø Full Control Ø Modify Ø Read & Execute Ø Read Ø Write Ø List Folder (Folder only) Ø Inherited Permissions when set Folder Permissions: Modify Read/Execute File 1 Permissions File 3 Permissions File 2 Permissions: Inherited: Modify Read/Execute

Locked Permissions

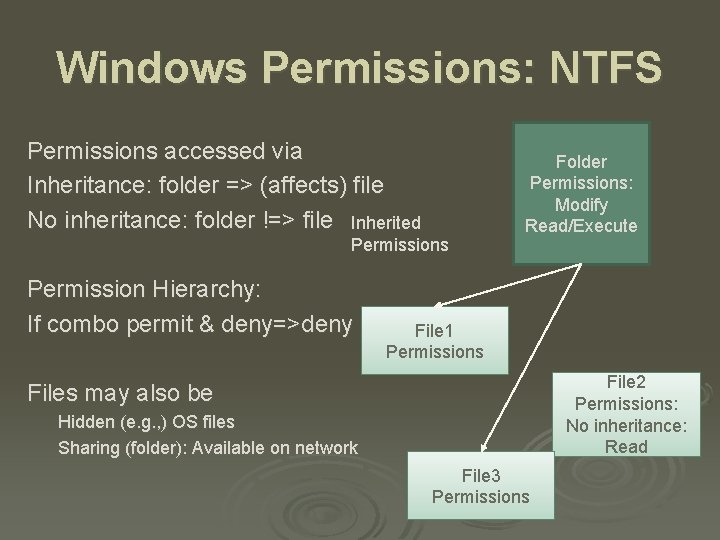
Windows Permissions: NTFS Permissions accessed via Inheritance: folder => (affects) file No inheritance: folder !=> file Inherited Permissions Permission Hierarchy: If combo permit & deny=>deny Folder Permissions: Modify Read/Execute File 1 Permissions File 2 Permissions: No inheritance: Read Files may also be Hidden (e. g. , ) OS files Sharing (folder): Available on network File 3 Permissions

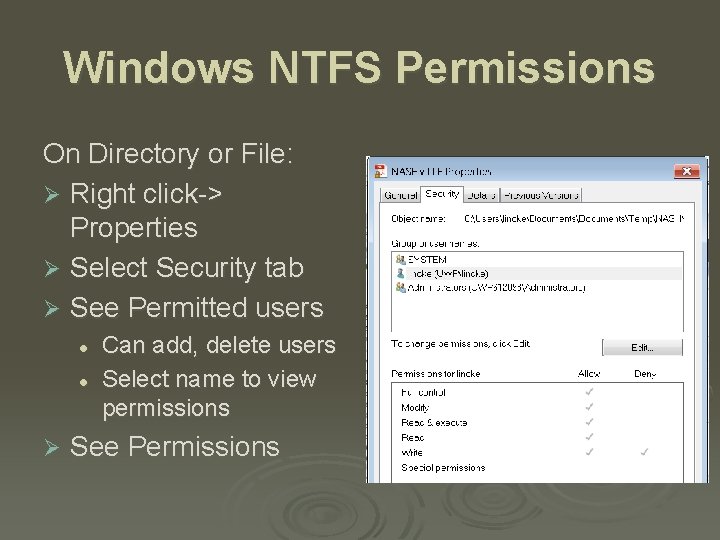
Windows NTFS Permissions On Directory or File: Ø Right click-> Properties Ø Select Security tab Ø See Permitted users l l Ø Can add, delete users Select name to view permissions See Permissions

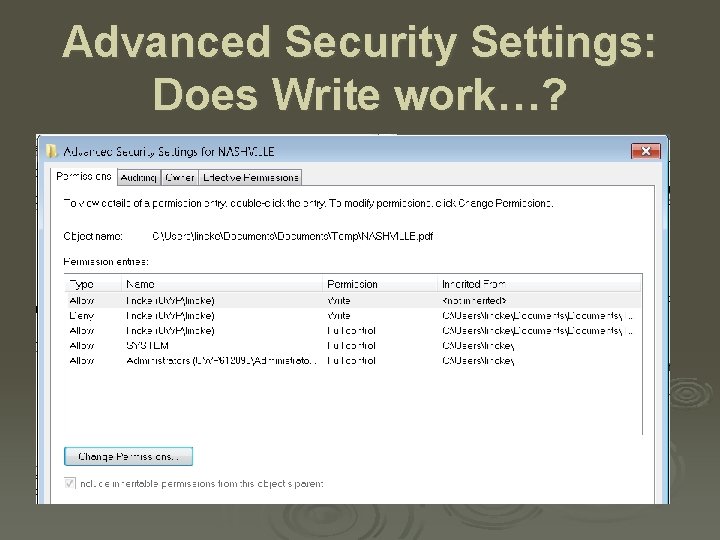
Advanced Security Settings: Does Write work…?