Network Security Effective Practices NACP TNC A Survey















![NAC/P Higher Ed Effective Practices Survey Which NAC/P Security mechanisms do[n’t] you use? Use NAC/P Higher Ed Effective Practices Survey Which NAC/P Security mechanisms do[n’t] you use? Use](https://slidetodoc.com/presentation_image_h/9b7d40a0728b7e6f535ce6a4bbe8c0cd/image-22.jpg)










- Slides: 61

Network Security Effective Practices - NAC/P, TNC A Survey of Network Access/Admissions Control Security Practices in Higher Education H. Morrow Long Director, Information Security Yale University Educause 2007 Annual Conference Session Wednesday, October 24, 2007 11: 30 a. m. - 12: 45 p. m.

Introductions 2

Overview This presentation will discuss a survey and informal poll of the current campus network access and admissions security practices and products in higher education on both wired and wireless networks. 3

Agenda Introduction What is NAC, NAP and TNC? NAC/P Concepts and Terminology NAC/P Feature Checklists NAC/P Effective Practices in Higher Ed Survey of NAC/P Practices in Academia Discussion and Questions 4

NAC, NAP, TNC timeline In 2003, RPC/DCOM worms (Blaster, NACHI) caused widespread problems on campus networks. Net. Reg, Bradford Campus Networks and other reg/quarantine systems were used as effective solutions. Cisco (bought Perfigo) and many vendors (particularly wireless) entered this market. Microsoft and the TCG alliance have been promising standars (w/Cisco) for a time (2008? ). 5

NAC/P Open Source Efforts Uconn/Umass/etc (Rodrigue, et al) “Net. Reg” mods (RPC/Dcom NASL scanning ala Nessus) Packet. Fence No. CAT - Captive Web Portal 6

NAC/P Goes Mainstream Standards: Cisco / Microsoft agreement 802. 1 X and EAPs WPA 2 7

What is NAC/NAP/TNC? NAC - Network Access (or Admission) Control § Generic § Cisco NAP - Network Access (or Admission) Protection § Microsoft Vista and Longhorn Server (2008) TNC - Trusted Network Computing (form Trusted Computing Group - TCG) § Anti-Virus / Anti-Malware vendors 8

Why NAC? IS NAT RELEVANT AND STILL NEEDED? New Paradigms may obviate NAC: § Enterrpise wide A/V / Anti-Malware § XP XP 2 Firewall & Vista Security • renders scanners obsolete? § Managed Workstations, “lockdown” GPO policies Arguments for NAC/P going forward: § § Un-managed & guest personal computers & devices End-point protection and assessment IDP/DLP/C<F (Leakage Protection, Content Filtering) Legal Liability, CALEA, etc. 9

NAC/P Issues to deal with NAC/P Phones Printers User hubs, switchs, Wi. Fi Aps and SOHO routers XBOX™, Sony Play. Station™, Nintendo™ PDAs, Smart. Phones, etc. Other unique IP devices and non-std Oses “Guest/Visitor” and conference attendees 10

NAC/P vs. No NAC/P You can actually have even better security using NAC/P IF you use strong encryption (and a good implementation) -- even over wired networks. Inline is more secure, reliable(? ) than noninline… Complex solutions may cause problems (run amuck). You will need to provide overrides and exceptions -- but SOP & Policy should discourage this as much as possible. 11

Threats to NAC/P (in order of sophistication) Scalability - worst case scenario : several thousand PCs seeking network admission simultaneously overwhelming scanner / NAC / Network. Single Point of Failure - only 1 scanner / gate / remediation website, etc Self-Assigning IPs. Spoofing Ips Spoofing EHAs (MACs) ARP spoofing/poisoning (Dsniff, Ettercap, etc. ) Router EHA Cloning Do. S Attack 802. 1 X / EAP Do. S Attacks VLAN “jumping” 12

NAC System Components Database (User, Computer, MAC, etc) Registration System DHCP and/or Authentication (Ra. DIUS/802. 1 X) Server Scanning engine and Policy Server Quarantine LAN/VLAN/Subnet ACL (switch/router), Firewall, Filter/Blocking device Captive Portal Remediation Site Proxy Agent (one time/registration, temporary, permanent) 13 Management Interface and/or Station/App.

Other NAC Architectures § EHA / MAC filtering § NAT Control § Forced VPN option • Wi. Fi • Wired • Remote Access • Guest networks 14

NAC Concepts/Terms In-line Out-of-Band Agent / Agent-less § § Pre-authentication Post-authentication DLP/ILP - Leak Protect One-time Boot/Connect time Dissolvable Continual Policy Server Remediation Server End Point Protection Security via Virtualization Quarantine 15

NAC/P Implementation Checklist Practical NAC/P Planning “high level short list”: Create, publish and enforce security policies. Practice rigorous physical security. Verify user identities. Actively monitor logs, firewalls & IDSes. Logically segregate data & voice traffic. Harden Oses. Encrypt whenever and whatever you can. 16

NAC Implementation Checklist Detailed and Specfic list: Use a separate VLAN with 802. 1 p/q Qo. S w/priority VLAN tagging for the quarantine network. Use a private (RFC 1918) IP network for the quarantine VLAN. Use NAT and/or proxies to hide internal addresses. Use a firewall (packet filtering or ALG) to protect & connect the Quarantine network to the data IP network. Use an IDS or IPS to examine the traffic allowed through the firewall (may be built into the firewall). 17 Use agents, 802. 1 X & RADIUS auth & EAP supplicants.

NAC/P Effective Practices in Higher Ed Some schools: Uses separate VLAN, L 2 switches and RFC 1918 IP addresses for the quarantine network. Many Schools: Using Cisco Secure/Clean Access Rolling their own via Net. Reg, No. Cat & Packet. Fence Looking at appliances 18

NAC/P Effective Practices in Higher Ed Colleges (http: //listserv. educause. edu/cgi-bin/wa. exe? A 2=ind 0701&L=security&P=13595) Date: Fri, 19 Jan 2007 15: 58: 22 -0500 Reply-To: The EDUCAUSE Security Discussion Group Listserv From: "Charles L. Bombard" Subject: Re: Network access control In-Reply-To: <[log in to unmask]> Content-Type: text/plain; charset="us-ascii" Still looking. I am on the fence (excuse the pun) and can go with either one at the moment. Packetfence seems to have acquired a large following, and netreg seems to not be in active development any longer. www. netreg. org www. packetfence. org - Charlie ===================== Charles Bombard, GSEC LAN/Systems Administrator Community College of Vermont 119 Pearl Street Burlington, VT 05401 802. 657. 4234 19

NAC/P Effective Practices in Higher Ed Small Colleges (http: //listserv. educause. edu/cgi-bin/wa. exe? A 2=ind 07&L=smallcol&P=20469) Date: Wed, 18 Apr 2007 11: 00: 47 -0400 Reply-To: The EDUCAUSE Small College Constituent Group Listserv From: "Beyer, Bill (William)" <[log in to unmask]> Subject: Network Access Control and Vista Content-Type: multipart/alternative; Hartwick College has been an early adopter of Network Access Control using Sygate Secure Enterprise in conjunction with using 802. 1 x protocols on our HP network data switches. While Sygate has worked well it does have its limitations mainly that it does not yet have a Vista client (our fingers are crossed that it will be released in May 2007) or a workable Mac client or Linux client. Our plans also include rolling out Vista Business on the student laptops we will issue to all freshmen this fall. 20

NAC/P - Other Surveys Network Computing Magazine Rolling Review Kickoff: Out-Of-Band NAC Oct 22, 2007 - By Mike Fratto “Thing is, out-of-band NAC seems to have an image problem: Our own reader research indicates that 65% of organizations deploying NAC prefer in-line appliances versus 50% using out-of-band products. And the outlook doesn't look likely to improve. Nearly 70% of companies in the planning stages are leaning toward in-line systems, versus just 43% favoring out-of-band NAC. A recent survey by Infonetics Research shows that 55% of companies plan on buying in-line NAC products; this syncs with the firm's market forecast, which shows more than half the NAC units shipped are in-line appliances. Is the problem just bad PR, or does the out-of-band approach really carry technical disadvantages compared with going in-band? ” http: //www. networkcomputing. com/channels/security/show. Article. jht ml? article. ID=202403321 21
![NACP Higher Ed Effective Practices Survey Which NACP Security mechanisms dont you use Use NAC/P Higher Ed Effective Practices Survey Which NAC/P Security mechanisms do[n’t] you use? Use](https://slidetodoc.com/presentation_image_h/9b7d40a0728b7e6f535ce6a4bbe8c0cd/image-22.jpg)
NAC/P Higher Ed Effective Practices Survey Which NAC/P Security mechanisms do[n’t] you use? Use of IPS or FW between NAC/P network and production backbone IP network. Use of IDS between NAC/P network and production backbone IP network. Use NAC (network access control) such as 802. 1 X and RADIUS to authenticate. Devices require the use of the separate NAC/P network (physical LAN, VLAN, subnet address, etc. ) from the production backbone data IP network. Vo. IP phones are automatically allowed access to the backbone network? . Computers are allowed with IPSEC or other VPNs. Use NAC (network access control) such as 802. 1 X and RADIUS to authenticate hard phones. Allow quarantine access automatically to the Internet but not campus network? Provide separate dedicated bandwidth for NAC/P quarantine network traffic to the Internet? 22

Survey 47 Responses (as of October 20, 2007) http: //www. surveymonkey. com/s. aspx? sm=w 7 FZIc_2 f. K 4_2 fr. F 3 ic. Ygf. KXig_3 d_3 d 23

NAC/P Higher Ed Effective Practices Survey 24

NAC/P Higher Ed Effective Practices Survey 2. 6% Solutions (1 Response each) IBM (Internet Security Systems) Impulse Point (Safe Connect) Info. Blox (ID Aware) Juniper Networks (Endpoint Assurance (was Funk)) LANDesk Software (Trusted Access) Lockdown Networks (Lockdown Enforcer) Mc. Afee (Mc. Afee Policy Enforcer) Pro. Curve Networking Symantec (Sygate NAC) 25 Veri. Sign Inc

NAC/P Higher Ed Effective Practices Survey Q 1: Other Category Several comments about not having NAC, planning on buying NAC, using oepn source or developing a home grown solution. 26

NAC/P Higher Ed Effective Practices Survey 27

NAC/P Higher Ed Effective Practices Survey Q 2: Other Category 1. RACS - homegrown system 2. We rolled our own (for wireless) 3. none 4. Saint Mary's Net. Reg and in house developed 5. Homebuilt 6. Complete Home Brew 7. home grown 8. nessus 28

NAC/P Higher Ed Effective Practices Survey 29

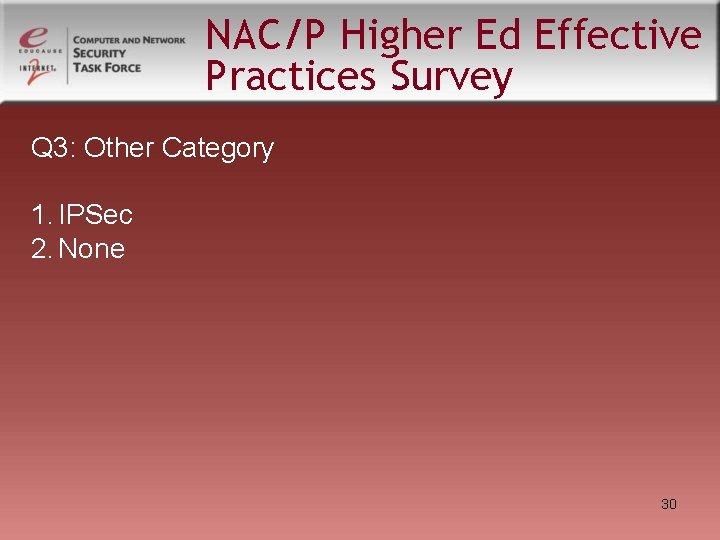
NAC/P Higher Ed Effective Practices Survey Q 3: Other Category 1. IPSec 2. None 30

NAC/P Higher Ed Effective Practices Survey 31

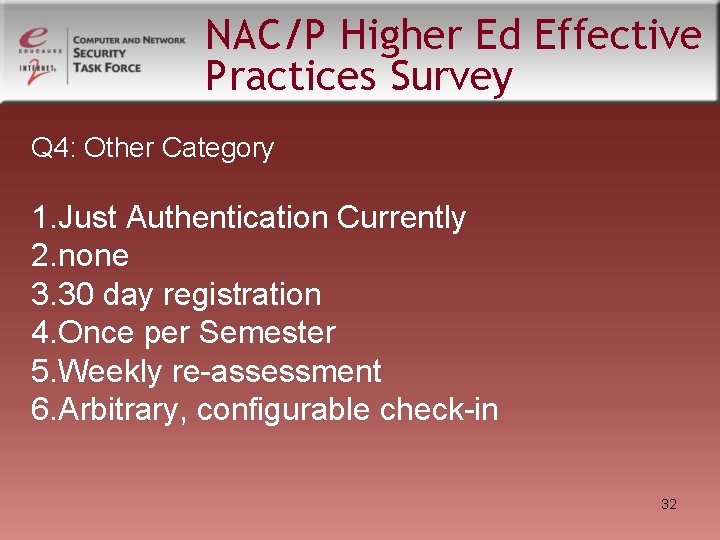
NAC/P Higher Ed Effective Practices Survey Q 4: Other Category 1. Just Authentication Currently 2. none 3. 30 day registration 4. Once per Semester 5. Weekly re-assessment 6. Arbitrary, configurable check-in 32

NAC/P Higher Ed Effective Practices Survey 33

NAC/P Higher Ed Effective Practices Survey Q 5: Other Category 1. staff/student laptops 2. No where 34

NAC/P Higher Ed Effective Practices Survey 35

NAC/P Higher Ed Effective Practices Survey 36

NAC/P Higher Ed Effective Practices Survey 37

NAC/P Higher Ed Effective Practices Survey 38

NAC/P Higher Ed Effective Practices Survey 39

NAC/P Higher Ed Effective Practices Survey 40

NAC/P Higher Ed Effective Practices Survey 41

NAC/P Higher Ed Effective Practices Survey 42

NAC/P Higher Ed Effective Practices Survey 43

NAC/P Higher Ed Effective Practices Survey 44

NAC/P Higher Ed Effective Practices Survey 45

NAC/P Higher Ed Effective Practices Survey 46

NAC/P Higher Ed Effective Practices Survey 47

NAC/P Higher Ed Effective Practices Survey 48

NAC/P Higher Ed Effective Practices Survey 49

NAC/P Higher Ed Effective Practices Survey 50

NAC/P Higher Ed Effective Practices Survey 51

NAC/P Higher Ed Effective Practices Survey 52

NAC/P Higher Ed Effective Practices Survey 53

NAC/P Higher Ed Effective Practices Survey 54

Survey Conclusions Implementers appear : § § Somewhat satisfied. Split between commerical and open source s/w Allow overrides & don’t require agents. Don’t allow private Wi. Fi Access Points. Technology appears to be fairly mature now. http: //www. surveymonkey. com/s. aspx? sm=w 7 FZIc_2 f. K 4_2 fr. F 3 ic. Ygf. KXig_3 d_3 d 55

Listservs & Newsgroups EDUCAUSE Security Discussion Listserv http: //www. educause. edu/Security. Discussion. Group/979 I 2 SALSA Net. Auth Working Group http: //www. internet 2. edu/netauth IETF Working Group Network Endpoint Assessment (nea) http: //tools. ietf. org/wg/nea/ http: //www. ietf. org/html. charters/neacharter. html 56

Q&A Question & Answer 57

Contact Info H. Morrow Long morrow. long@yale. edu Security. yale. edu 58

Credits: Cisco - NAC Overview, http: //www. cisco. com/en/US/netsol/ns 466/networking_solutions_package. html Gartner RAS Core Research Note G 00143551, John Pescatore, Mark Nicolett, Lawrence Orans, 5 October 2006 R 2052 1/25/2007 http: //www. cisco. com/web/ES/publicaciones/06 -10 -Cisco-gartner-NAC. pdf "Network Access Control" Seminar Presentation, Security Professionals Conference 2006, Kevin Amorin (Harvard University), Chris Misra (University of Massachusetts, Amherst) 59

Credits: Wikipedia (Pages on NAC/NAP, etc. ) 60

This has been a chalk outline™ production.