Network Security Chapter 1 Background Information Security requirements

Network Security Chapter 1
Background Information Security requirements have changed in recent times Ø traditionally provided by physical and administrative mechanisms Ø computer use requires automated tools to protect files and other stored information Ø use of networks and communications links requires measures to protect data during transmission Ø

Definitions Computer Security - generic name for the collection of tools designed to protect data and Computer systems Ø Network Security - measures to protect data during their transmission Ø Internet Security - measures to protect data during their transmission over a collection of interconnected networks Ø

Aim of Course Ø our focus is on Internet Security Ø which consists of measures to deter, prevent, detect, and correct security violations that involve the transmission & storage of information
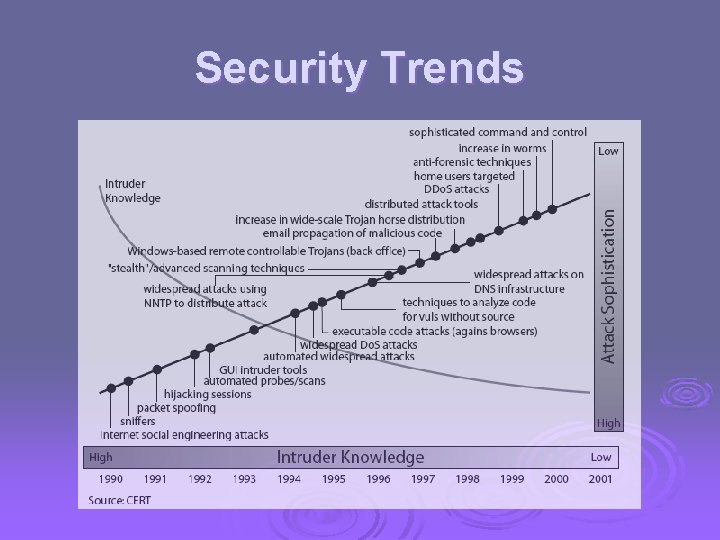
Security Trends

OSI Security Architecture Ø ITU-T X. 800 “Security Architecture for OSI” Ø defines a systematic way of defining and providing security requirements Ø for us it provides a useful, if abstract, overview of concepts we will study

What is security Architecture x. 800 Ø An international and systematic standard of defining and providing security requirements. Ø Useful to managers as a way of organizing the task of providing security. Ø Proposed by ITU-T in recommendations X. 800 as “Security Architecture for OSI” Ø Computer and communications vendors have developed security features for their products and services under the definition
Definations Ø 1. Security attack Ø Any action that compromises the security of information owned by an organization. Ø 2. Security mechanism (control) Ø A process (or a device incorporating sucha a process) that is designed to detect, prevent, or recover from a security attack. Ø 3. Security service Ø The service are intended to counter

Principles of Security Ø 1. Confidentially Ø 2. Authentication Ø 3. Integrity Ø 4. Availability

Confidentially Ø It states that only the sender and the receiver should have an access to the information. Also known as privacy or secrecy of information
Attack on confidentiality Ø Snooping refers to unauthorized access to or interception of data. Ø Traffic analysis monitoring online traffic and collecting sensitive data.

Authentication Ø The assurance that the communicating entity is the one that it claims to be. It identifies who is sender and who is receiver

Data Integrity Ø The assurance that data received are exactly as sent by an authorized entity (i. e. , contain no modification, insertion, deletion or replay) Ø Any changes done to the message must either be prevented or detected.

Attack on Data integrity Ø Modification : altering of messages Ø Masquerading / spoofing: attacker impersonates somebody else. Ø Replaying: replaying the old captured messages Ø Repudiation means that sender of the message might later deny that she has send the message; the receiver of the message might later deny that he has received the message.

Availability Ø Resources / applications must be available to authentic users all the time. If not available It is also known as Denial of Service attack

Attacks on various principles Ø Normal flow Ø Interruption Ø Interception Ø Modification Ø Fabrication

Threats Ø Confidentially l Interception • Unauthorized access • Wiretapping Ø Integrity l Modification • Change or Delete : Data, Messages, Programs Ø Availability l Interruption • Hardware destruction

Attacks Ø Passive Attacks Ø Active Attacks

Passive Attacks Ø Nature of eavesdropping on, or monitoring of transmissions. The goal of the opponent is to obtain information that is being transmitted. Ø Two types Ø 1. Release of message contents Ø 2. Traffic analysis
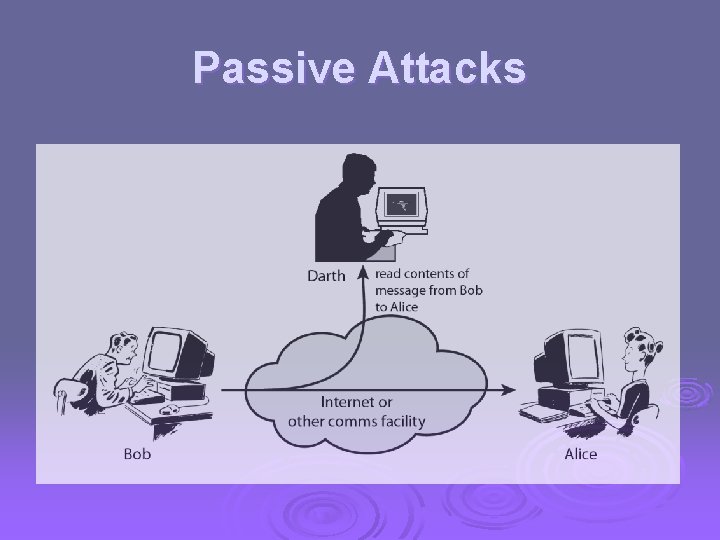
Passive Attacks

Release of Message contents Ø Prevent an opponent from learning the contents of telephone conversation, an electronic mail message, and a transferred file transmissions.

Traffic Analysis Ø Attacker Observe the pattern of the messages. The opponent could determine the location and identity of communicating hosts and could observe the frequency and length of messages being exchanged.

Active Attacks Ø Masquerade Ø Replay Ø Modification of messages Ø Denial of service
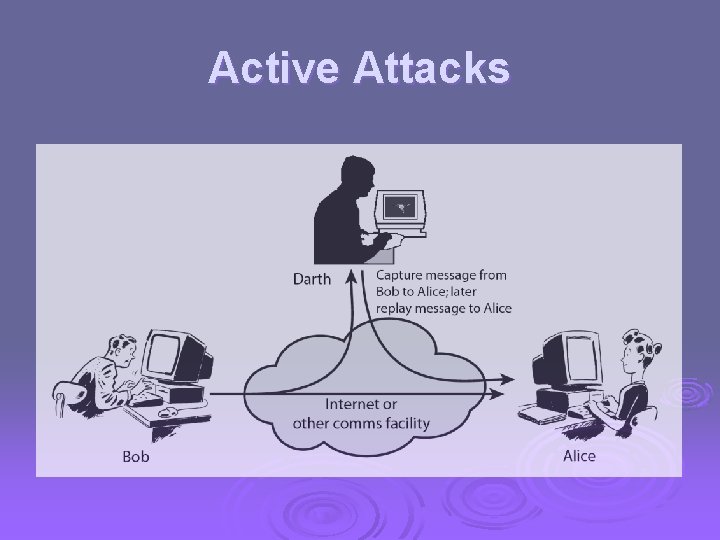
Active Attacks

Masquerade Ø A masquerade takes place when one entity pretends to be a different entity. Ø Example: Authentication sequences can be captured and replayed after a valid authentication sequence has taken place

Replay Ø It involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect

Modification of Messages Ø Modification of messages simply means that some portion of a legitimate message is altered or that messages are delayed or reordered to produce an unauthorized effect.

Denial of Service Ø Prevents or inhibits the normal use or management of communications facilities. Flooding the network or system with bogus messages.

Comparison Ø Passive attacks – focus on Prevention l l Easy to stop Hard to detect Ø Active attacks – focus on Detection and Recovery l l Hard to stop Easy to detect

Security Services Ø Authentication Ø Confidentiality Ø Integrity Ø Availability Ø Access control Ø Non Repudiation

Security Services Ø 1. Access control Ø The Prevention of unauthorized use of a resource Ø A) who can have access to a resource Ø B) under what conditions access can occur Ø C) What those accessing the resource are allowed to do.

Non repodiation Ø Assurance that someone cannot deny the validity of something. Ø Non repudiation prevents either sender or receiver from denying a transmitted message Ø Non repudiation origin Ø No repudiation destination
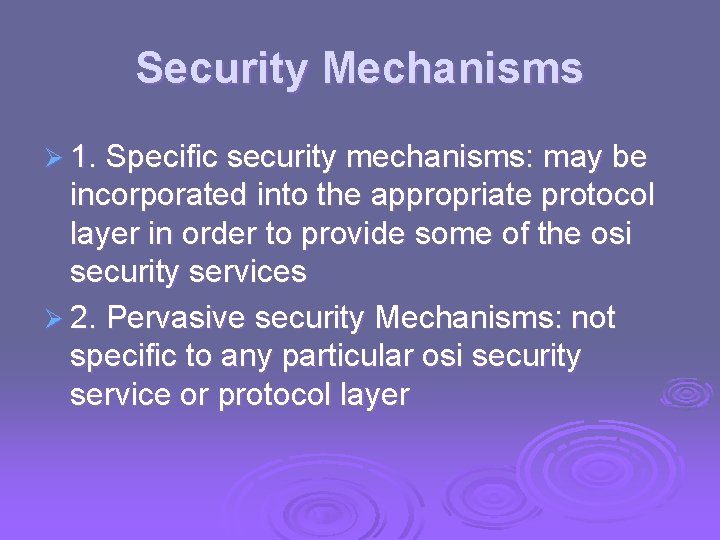
Security Mechanisms Ø 1. Specific security mechanisms: may be incorporated into the appropriate protocol layer in order to provide some of the osi security services Ø 2. Pervasive security Mechanisms: not specific to any particular osi security service or protocol layer

Specific Security Mechanisms Ø Encipherment Ø Digital signature Ø Access control Ø Data integrity Ø Authentication exchange Ø Traffic padding Ø Routing control

pervasive security mechanisms l trusted functionality, security labels, event detection, security audit trails, security recovery
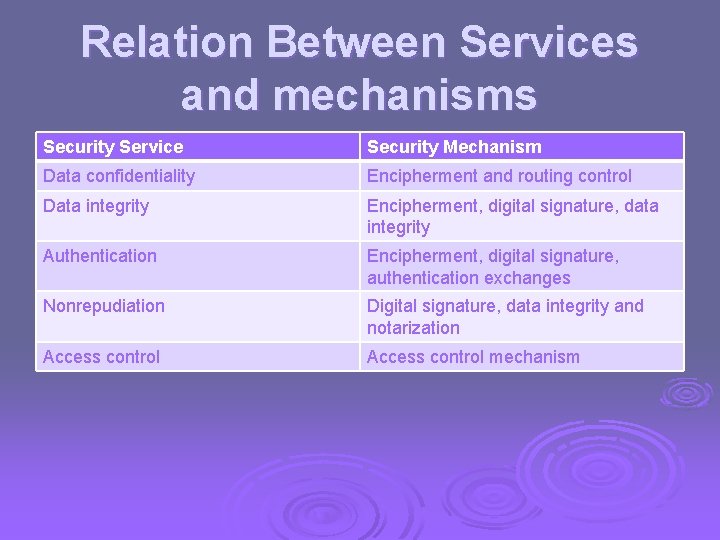
Relation Between Services and mechanisms Security Service Security Mechanism Data confidentiality Encipherment and routing control Data integrity Encipherment, digital signature, data integrity Authentication Encipherment, digital signature, authentication exchanges Nonrepudiation Digital signature, data integrity and notarization Access control mechanism

Security Mechanism Ø feature designed to detect, prevent, or recover from a security attack Ø no single mechanism that will support all services required Ø however one particular element underlies many of the security mechanisms in use: l cryptographic techniques Ø hence our focus on this topic

Security Mechanisms (X. 800) Ø specific security mechanisms: l encipherment, digital signatures, access controls, data integrity, authentication exchange, traffic padding, routing control, notarization Ø pervasive security mechanisms: l trusted functionality, security labels, event detection, security audit trails, security recovery
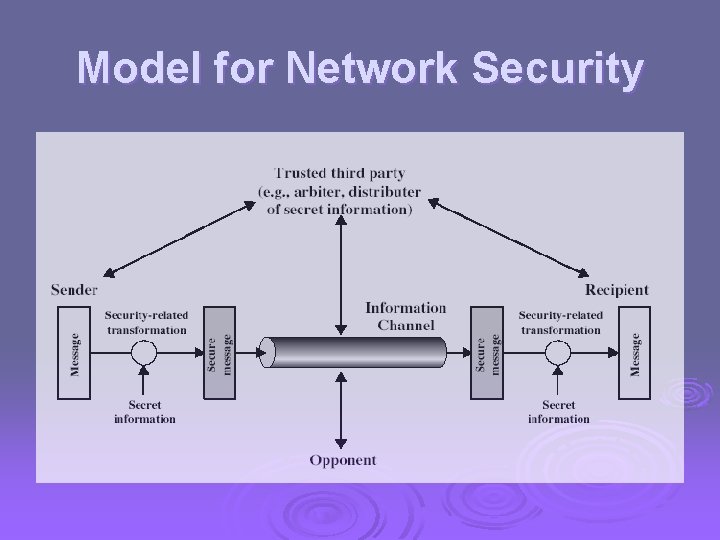
Model for Network Security
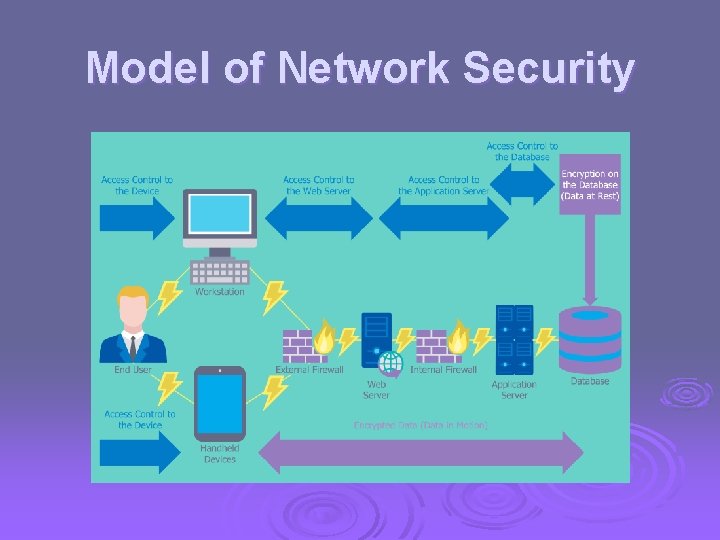
Model of Network Security
Model for Network Security Ø using this model requires us to: 1. 2. 3. 4. design a suitable algorithm for the security transformation generate the secret information (keys) used by the algorithm develop methods to distribute and share the secret information specify a protocol enabling the principals to use the transformation and secret information for a security service
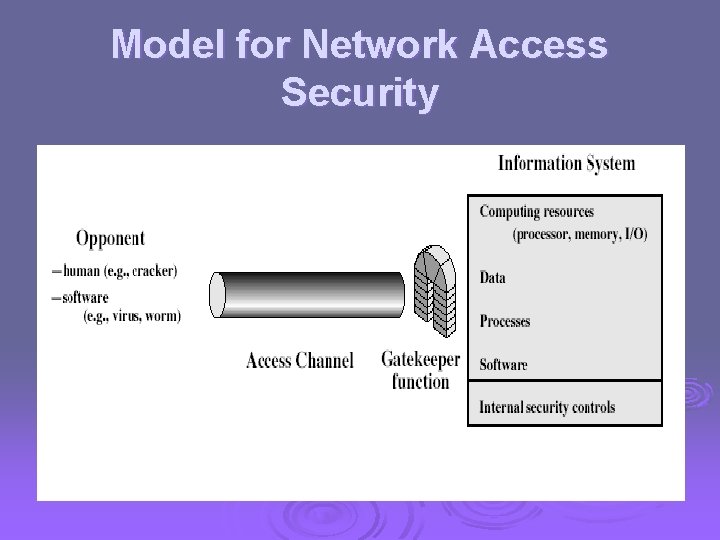
Model for Network Access Security
Model for Network Access Security Ø using this model requires us to: 1. 2. Ø select appropriate gatekeeper functions to identify users implement security controls to ensure only authorised users access designated information or resources trusted computer systems may be useful to help implement this model

Summary Ø have considered: l definitions for: • computer, network, internet security Ø X. 800 standard Ø security attacks, services, mechanisms Ø models for network (access) security
- Slides: 44