Network Security and Cryptography Topic 1 Lecture 3












- Slides: 20

Network Security and Cryptography Topic 1 – Lecture 3: Asymmetric Algorithms V 1. 1 © NCC Education Limited

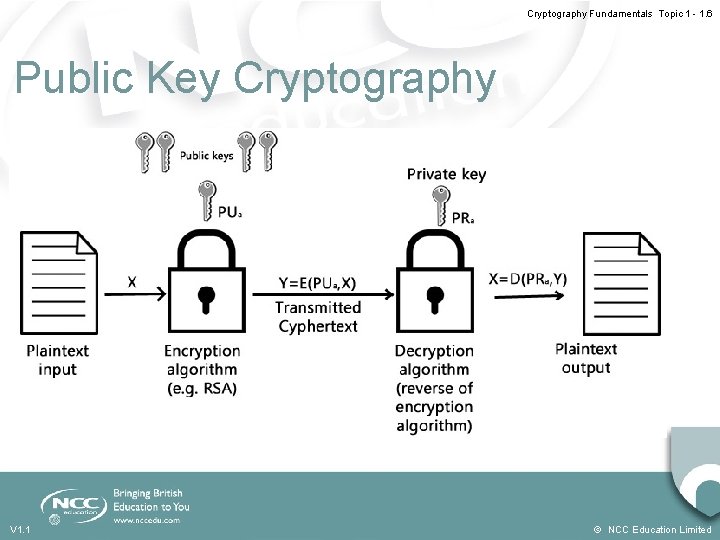
Cryptography Fundamentals Topic 1 - 1. 2 Public Key Cryptography - 1 • Uses asymmetric key algorithms • The key used to encrypt a message is not the same as the key used to decrypt it. • Each user has a pair of cryptographic keys: - a public encryption key, publicly available and widely distributed. - a private decryption key, known only to the recipient. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 3 Public Key Cryptography - 2 • Messages are encrypted with the recipient's public key and can only be decrypted with the corresponding private key. • The keys are related mathematically. • Parameters are chosen so that determining the private key from the public key is prohibitively expensive. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 4 Public Key Cryptography – The Steps 1. Each user generates a pair of keys to be used for encryption/decryption. 2. Each user places one of the keys (the public key) in a public register – each user maintains a collection of public keys obtained from others. 3. If Bob sends a message to Alice, he encrypts it using Alice’s public key. 4. Alice decrypts it using her private key that no-one else has access to. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 5 Public Key Cryptography - Analogy • An analogy to public-key encryption is that of a locked mailbox for an office. - The mail slot is exposed and accessible to the public. - Its location (the street address) is like the public key. - Anyone knowing the street address can go to the door and drop a written message through the slot. - Only the person who possesses the key can open the mailbox and read the message. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 6 Public Key Cryptography V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 7 Public Key Cryptography - Applications • Encryption/decryption: the sender encrypts a message with the recipient’s public key. • Digital signature (authentication): the sender “signs” the message with its private key; a receiver can verify the identity of the sender using sender’s public key. • Key exchange: both sender and receiver cooperate to exchange a (session) key. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 8 The RSA Algorithm • Stands for Rivest, Shamir and Adleman who first publicly described it. • The RSA algorithm involves three steps: - key generation - encryption - decryption V 1. 1 © NCC Education Limited

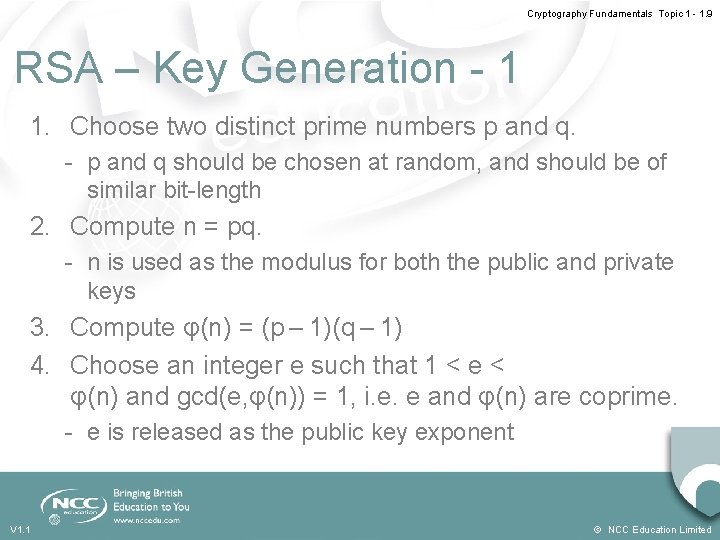
Cryptography Fundamentals Topic 1 - 1. 9 RSA – Key Generation - 1 1. Choose two distinct prime numbers p and q. - p and q should be chosen at random, and should be of similar bit-length 2. Compute n = pq. - n is used as the modulus for both the public and private keys 3. Compute φ(n) = (p – 1)(q – 1) 4. Choose an integer e such that 1 < e < φ(n) and gcd(e, φ(n)) = 1, i. e. e and φ(n) are coprime. - e is released as the public key exponent V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 10 RSA – Key Generation - 2 5. Determine d = e– 1 mod φ(n); i. e. d is the multiplicative inverse of e mod φ(n). - This is more clearly stated as solve for d given (d*e)mod φ(n) = 1, d is kept as the private key exponent. • V 1. 1 The public key consists of the modulus n and the public (or encryption) exponent e. The private key consists of the private (or decryption) exponent d which must be kept secret. © NCC Education Limited

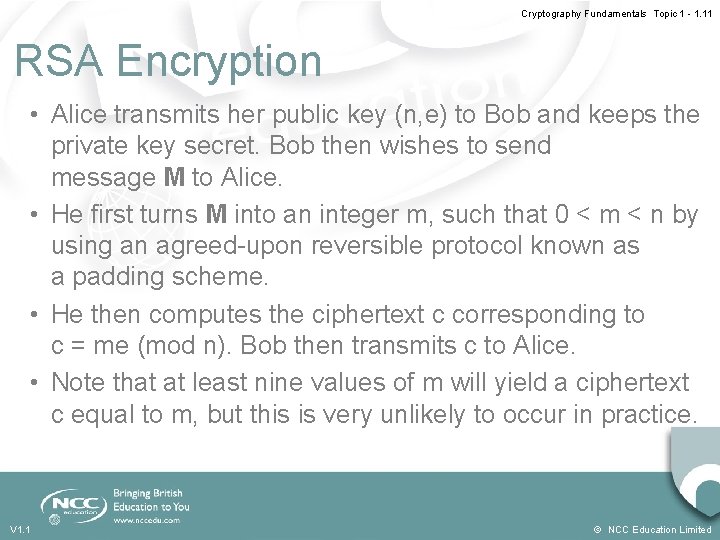
Cryptography Fundamentals Topic 1 - 1. 11 RSA Encryption • Alice transmits her public key (n, e) to Bob and keeps the private key secret. Bob then wishes to send message M to Alice. • He first turns M into an integer m, such that 0 < m < n by using an agreed-upon reversible protocol known as a padding scheme. • He then computes the ciphertext c corresponding to c = me (mod n). Bob then transmits c to Alice. • Note that at least nine values of m will yield a ciphertext c equal to m, but this is very unlikely to occur in practice. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 12 RSA Decryption • Alice can recover m from c by using her private key exponent d via computing m = cd (mod n). • Given m, she can recover the original message M by reversing the padding scheme. • A simplified example of the whole process is given in the laboratory exercises. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 13 RSA Security • Relies upon the complexity of the factoring problem. • Nobody knows how to factor big numbers in a reasonable time. • However, nobody has shown that the fast factoring is impossible! V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 14 Hash Functions • A hash function is a mathematical function that converts a large, possibly variably-sized amount of data into a small datum. • Hashing is a method of binding the file contents together to ensure integrity. - Like using sealing wax on an envelope. - Only by breaking the seal can the contents be accessed, and any tampering is readily apparent. V 1. 1 © NCC Education Limited

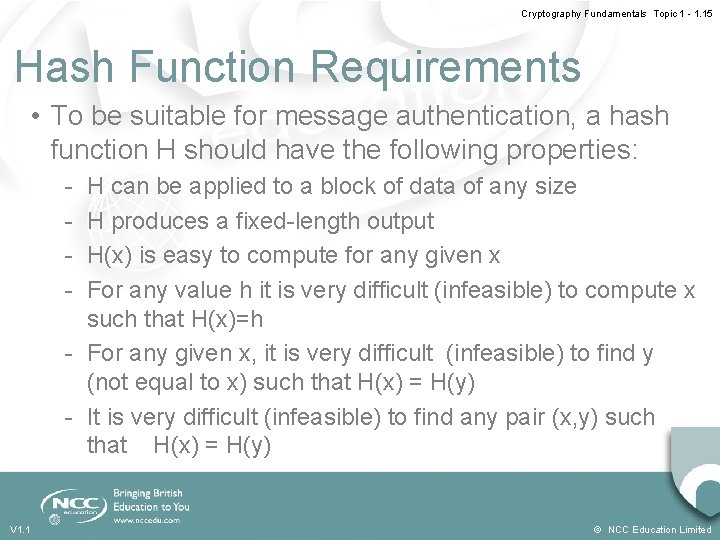
Cryptography Fundamentals Topic 1 - 1. 15 Hash Function Requirements • To be suitable for message authentication, a hash function H should have the following properties: - H can be applied to a block of data of any size H produces a fixed-length output H(x) is easy to compute for any given x For any value h it is very difficult (infeasible) to compute x such that H(x)=h - For any given x, it is very difficult (infeasible) to find y (not equal to x) such that H(x) = H(y) - It is very difficult (infeasible) to find any pair (x, y) such that H(x) = H(y) V 1. 1 © NCC Education Limited

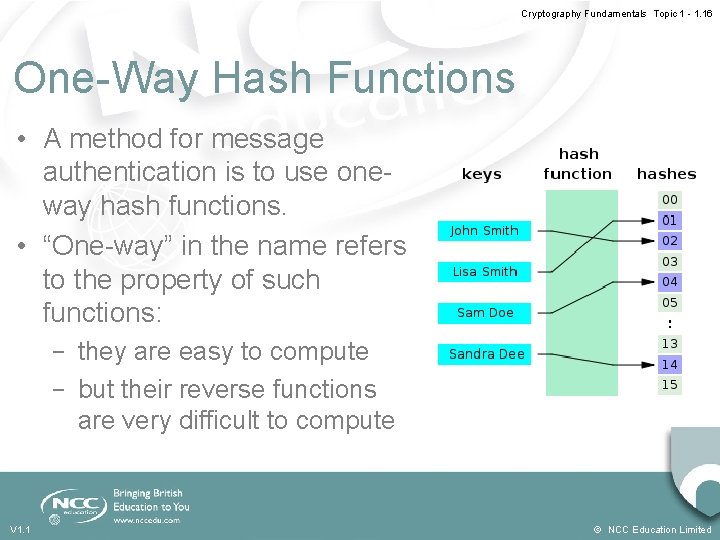
Cryptography Fundamentals Topic 1 - 1. 16 One-Way Hash Functions • A method for message authentication is to use oneway hash functions. • “One-way” in the name refers to the property of such functions: - they are easy to compute - but their reverse functions are very difficult to compute V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 17 The SHA-1 Secure Hash Algorithm • Takes as input a message with a maximum length less than 2 to power 64 bits and produces as output a 160 -bit message digest. • The input is processed in 512 -bit blocks. • Each bit of the output is computed using all bits of the input. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 18 SHA-1 Examples • SHA 1("The quick brown fox jumps over the lazy dog") = 2 fd 4 e 1 c 6 7 a 2 d 28 fc ed 849 ee 1 bb 76 e 739 1 b 93 eb 12 • A small change in the message will, with overwhelming probability, result in a completely different hash. • SHA 1("The quick brown fox jumps over the lazy cog") = de 9 f 2 c 7 f d 25 e 1 b 3 a fad 3 e 85 a 0 bd 17 d 9 b 100 db 4 b 3 V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 19 References • NIST (Feb. 2004). Standards for Security Categorization of Federal Information and Information Systems. FIPS 199. [Available Online] http: //csrc. nist. gov/publications/fips 199/FIPSPUB-199 -final. pdf • Stallings, W. (2010). Cryptography and Network Security: Principles and Practice. Pearson Education. V 1. 1 © NCC Education Limited

Cryptography Fundamentals Topic 1 - 1. 20 Topic 1 – Cryptography Fundamentals Any Questions? V 1. 1 © NCC Education Limited