Network Security 2 Module 8 PIX Security Appliance



![Viewing and Disabling Telnet ciscoasa# show running-config telnet [timeout] § Displays IP addresses permitted Viewing and Disabling Telnet ciscoasa# show running-config telnet [timeout] § Displays IP addresses permitted](https://slidetodoc.com/presentation_image/2f370a7ae3208869ee854cee37ac3202/image-5.jpg)
![Viewing, Disabling, and Debugging SSH ciscoasa# show ssh sessions [ip_address] § Enables you to Viewing, Disabling, and Debugging SSH ciscoasa# show ssh sessions [ip_address] § Enables you to](https://slidetodoc.com/presentation_image/2f370a7ae3208869ee854cee37ac3202/image-9.jpg)










- Slides: 38

Network Security 2 Module 8 – PIX Security Appliance Contexts, Failover, and Management © 2006 Cisco Systems, Inc. All rights reserved.

Module 8 – PIX Security Appliance Contexts, Failover, and Management Lesson 8. 4 PIX Security Appliance Management © 2006 Cisco Systems, Inc. All rights reserved.

Managing System Access © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -3

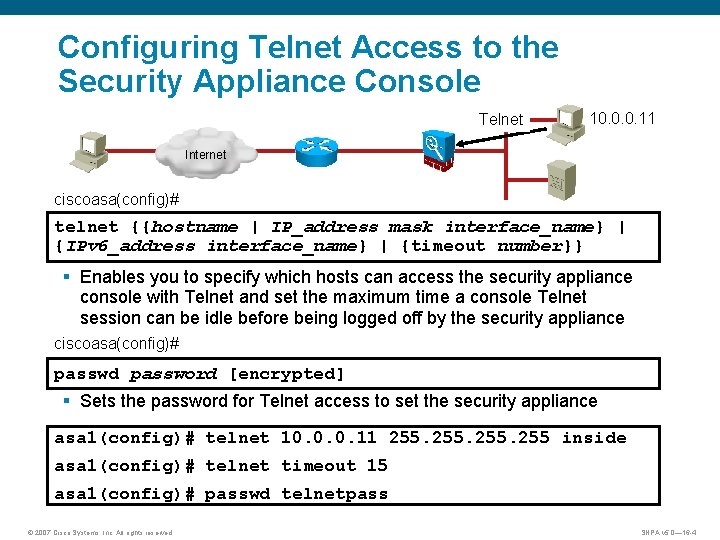
Configuring Telnet Access to the Security Appliance Console Telnet 10. 0. 0. 11 Internet ciscoasa(config)# telnet {{hostname | IP_address mask interface_name} | {IPv 6_address interface_name} | {timeout number}} § Enables you to specify which hosts can access the security appliance console with Telnet and set the maximum time a console Telnet session can be idle before being logged off by the security appliance ciscoasa(config)# passwd password [encrypted] § Sets the password for Telnet access to set the security appliance asa 1(config)# telnet 10. 0. 0. 11 255 inside asa 1(config)# telnet timeout 15 asa 1(config)# passwd telnetpass © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -4
![Viewing and Disabling Telnet ciscoasa show runningconfig telnet timeout Displays IP addresses permitted Viewing and Disabling Telnet ciscoasa# show running-config telnet [timeout] § Displays IP addresses permitted](https://slidetodoc.com/presentation_image/2f370a7ae3208869ee854cee37ac3202/image-5.jpg)
Viewing and Disabling Telnet ciscoasa# show running-config telnet [timeout] § Displays IP addresses permitted to access the security appliance via Telnet ciscoasa(config)# clear configure telnet § Removes the Telnet connection and the idle timeout from the configuration ciscoasa# who [local_ip] § Enables you to view which IP addresses are currently accessing the security appliance console via Telnet ciscoasa# kill telnet_id § Terminates a Telnet session © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -5

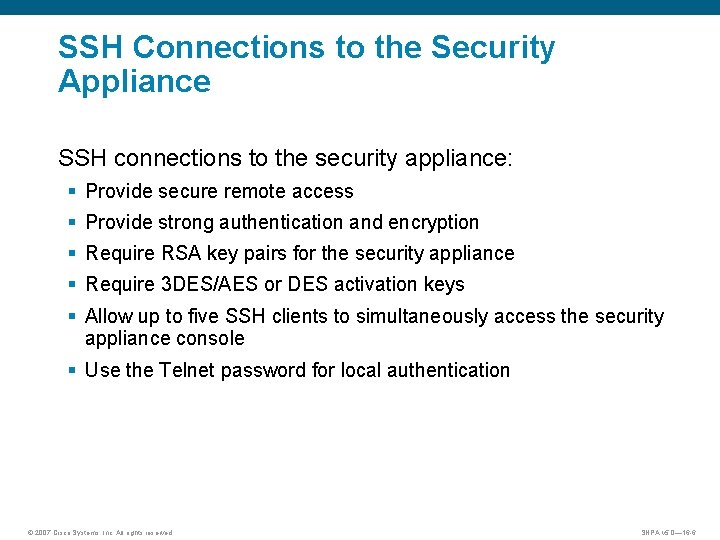
SSH Connections to the Security Appliance SSH connections to the security appliance: § Provide secure remote access § Provide strong authentication and encryption § Require RSA key pairs for the security appliance § Require 3 DES/AES or DES activation keys § Allow up to five SSH clients to simultaneously access the security appliance console § Use the Telnet password for local authentication © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -6

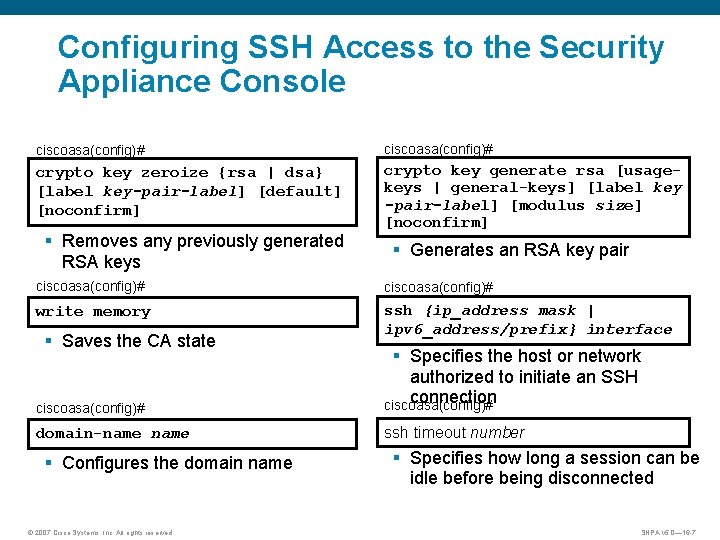
Configuring SSH Access to the Security Appliance Console ciscoasa(config)# crypto key zeroize {rsa | dsa} [label key-pair-label] [default] [noconfirm] crypto key generate rsa [usagekeys | general-keys] [label key -pair-label] [modulus size] [noconfirm] § Removes any previously generated RSA keys § Generates an RSA key pair ciscoasa(config)# write memory ssh {ip_address mask | ipv 6_address/prefix} interface § Saves the CA state ciscoasa(config)# § Specifies the host or network authorized to initiate an SSH connection ciscoasa(config)# domain-name ssh timeout number § Configures the domain name © 2007 Cisco Systems, Inc. All rights reserved. § Specifies how long a session can be idle before being disconnected SNPA v 5. 0— 16 -7

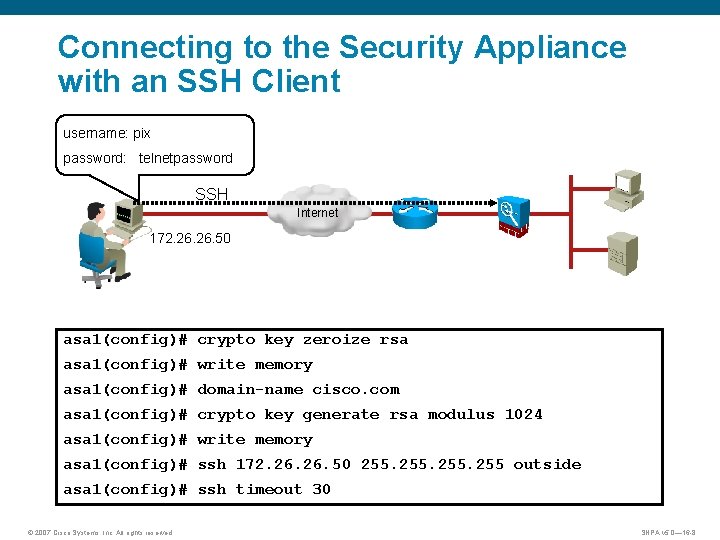
Connecting to the Security Appliance with an SSH Client username: pix password: telnetpassword SSH Internet 172. 26. 50 asa 1(config)# crypto key zeroize rsa asa 1(config)# write memory asa 1(config)# domain-name cisco. com asa 1(config)# crypto key generate rsa modulus 1024 asa 1(config)# write memory asa 1(config)# ssh 172. 26. 50 255 outside asa 1(config)# ssh timeout 30 © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -8
![Viewing Disabling and Debugging SSH ciscoasa show ssh sessions ipaddress Enables you to Viewing, Disabling, and Debugging SSH ciscoasa# show ssh sessions [ip_address] § Enables you to](https://slidetodoc.com/presentation_image/2f370a7ae3208869ee854cee37ac3202/image-9.jpg)
Viewing, Disabling, and Debugging SSH ciscoasa# show ssh sessions [ip_address] § Enables you to view the status of your SSH sessions ciscoasa# ssh disconnect session_id § Disconnects an SSH session ciscoasa(config)# clear configure ssh § Removes all SSH command statements from the configuration ciscoasa(config)# debug ssh § Enables SSH debugging © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -9

Managing User Access Levels © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -10

Command Authorization Overview The purpose of command authorization is to securely and efficiently administer the security appliance. You can configure the following types of command authorization: § Command authorization with password-protected privilege levels § Command authorization with username and password authentication © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -11

Command Authorization with Password. Protected Privilege Levels § The following tasks are required to configure command authorization with password-protected privilege levels: – Use the enable command to create privilege levels and assign passwords to them. – Use the privilege command to assign specific commands to privilege levels. – Use the aaa authorization command to enable the command authorization feature. § Users must complete the following steps to use command authorization with password-protected privilege levels: – Use the enable command with the level option to access the desired privilege level. – Provide the password for the privilege level when prompted. The user can then execute any command assigned to that privilege level or to a lower privilege level. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -12

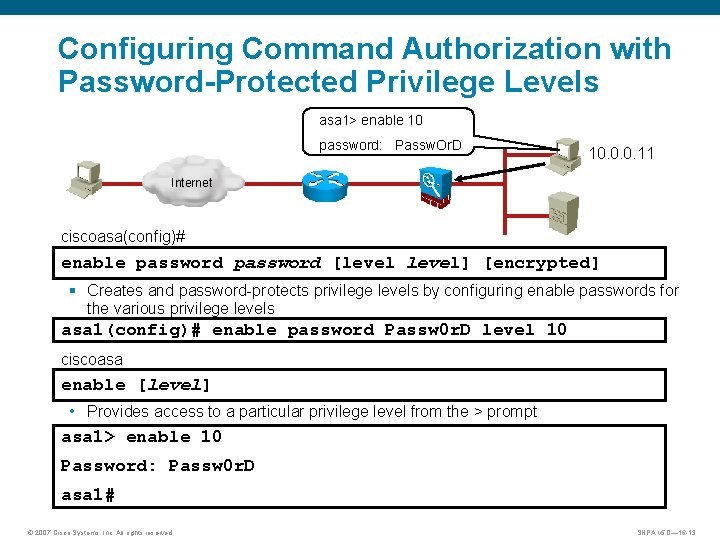
Configuring Command Authorization with Password-Protected Privilege Levels asa 1> enable 10 password: Passw. Or. D 10. 0. 0. 11 Internet ciscoasa(config)# enable password [level] [encrypted] § Creates and password-protects privilege levels by configuring enable passwords for the various privilege levels asa 1(config)# enable password Passw 0 r. D level 10 ciscoasa enable [level] • Provides access to a particular privilege level from the > prompt asa 1> enable 10 Password: Passw 0 r. D asa 1# © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -13

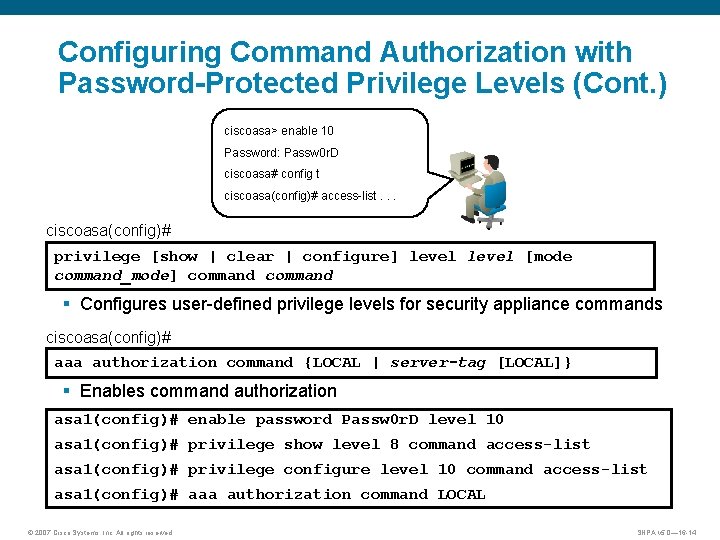
Configuring Command Authorization with Password-Protected Privilege Levels (Cont. ) ciscoasa> enable 10 Password: Passw 0 r. D ciscoasa# config t ciscoasa(config)# access-list. . . ciscoasa(config)# privilege [show | clear | configure] level [mode command_mode] command § Configures user-defined privilege levels for security appliance commands ciscoasa(config)# aaa authorization command {LOCAL | server-tag [LOCAL]} § Enables command authorization asa 1(config)# enable password Passw 0 r. D level 10 asa 1(config)# privilege show level 8 command access-list asa 1(config)# privilege configure level 10 command access-list asa 1(config)# aaa authorization command LOCAL © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -14

Command Authorization with Username and Password Authentication § The following tasks are required to configure command authorization with username and password authentication: – Use the privilege command to assign specific commands to privilege levels. – Use the username command to create user accounts in the local user database and assign privilege levels to the accounts. – Use the aaa authorization command to enable command authorization. – Use the aaa authentication command to enable authentication using the local database. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -15

Command Authorization with Username and Password Authentication § Users must complete one of the following tasks to use command authorization with username and password authentication: – Enter the login command at the > prompt and log in with a username and password. – Enter the enable command at the > prompt and log in with a username and password. The user can then execute any command assigned to the same privilege level as the user account or to a lower privilege level. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -16

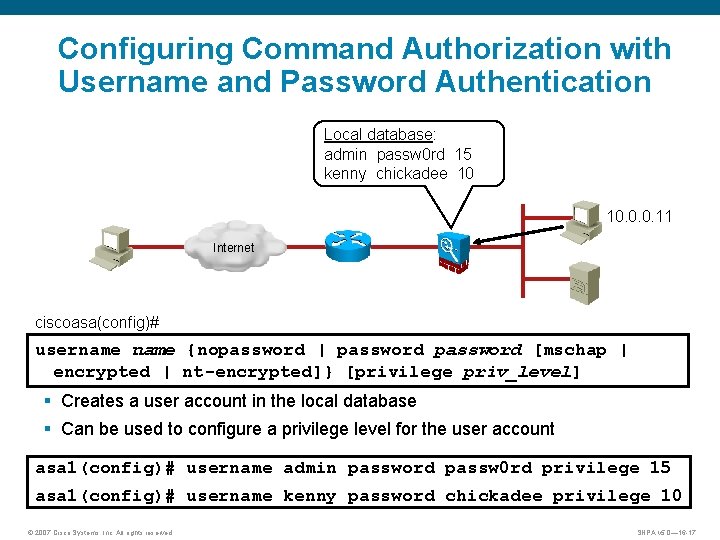
Configuring Command Authorization with Username and Password Authentication Local database: admin passw 0 rd 15 kenny chickadee 10 10. 0. 0. 11 Internet ciscoasa(config)# username {nopassword | password [mschap | encrypted | nt-encrypted]} [privilege priv_level] § Creates a user account in the local database § Can be used to configure a privilege level for the user account asa 1(config)# username admin password passw 0 rd privilege 15 asa 1(config)# username kenny password chickadee privilege 10 © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -17

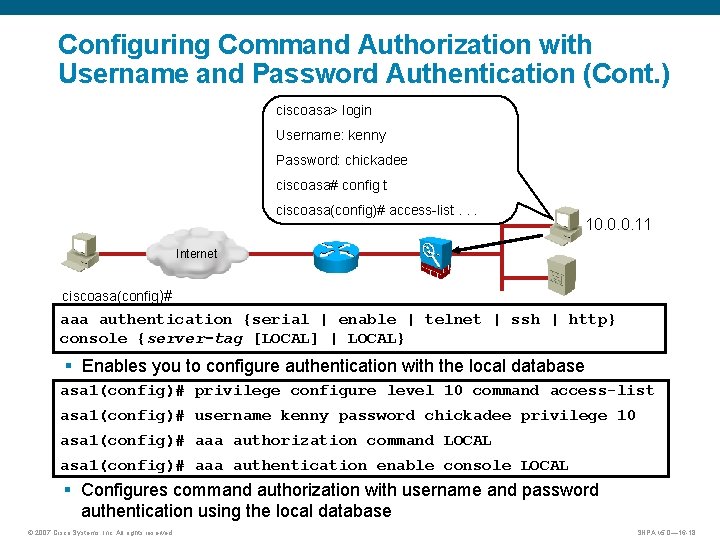
Configuring Command Authorization with Username and Password Authentication (Cont. ) ciscoasa> login Username: kenny Password: chickadee ciscoasa# config t ciscoasa(config)# access-list. . . 10. 0. 0. 11 Internet ciscoasa(config)# aaa authentication {serial | enable | telnet | ssh | http} console {server-tag [LOCAL] | LOCAL} § Enables you to configure authentication with the local database asa 1(config)# privilege configure level 10 command access-list asa 1(config)# username kenny password chickadee privilege 10 asa 1(config)# aaa authorization command LOCAL asa 1(config)# aaa authentication enable console LOCAL § Configures command authorization with username and password authentication using the local database © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -18

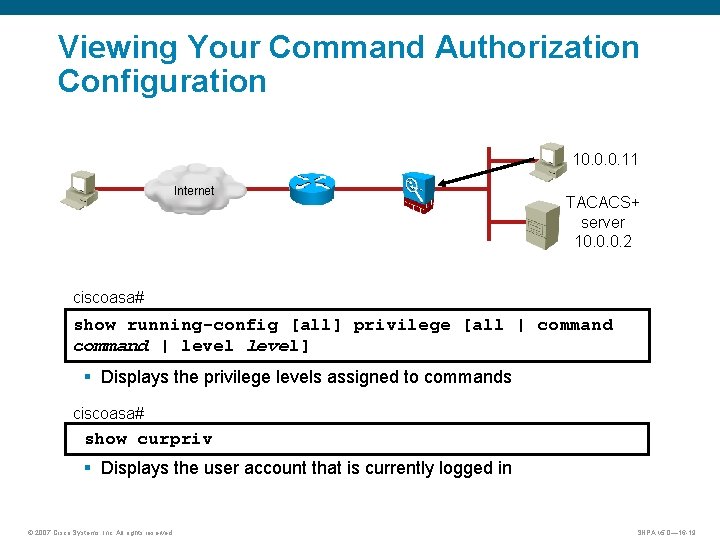
Viewing Your Command Authorization Configuration 10. 0. 0. 11 Internet TACACS+ server 10. 0. 0. 2 ciscoasa# show running-config [all] privilege [all | command § Displays the privileges for a command or set of commands. command | level] § Displays the privilege levels assigned to commands ciscoasa# show curpriv § Displays the user account that is currently logged in © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -19

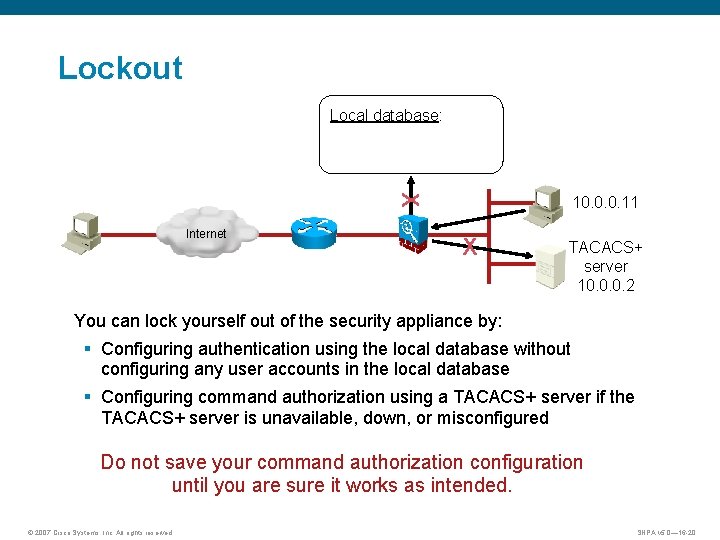
Lockout Local database: X Internet 10. 0. 0. 11 X TACACS+ server 10. 0. 0. 2 You can lock yourself out of the security appliance by: § Configuring authentication using the local database without configuring any user accounts in the local database § Configuring command authorization using a TACACS+ server if the TACACS+ server is unavailable, down, or misconfigured Do not save your command authorization configuration until you are sure it works as intended. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -20

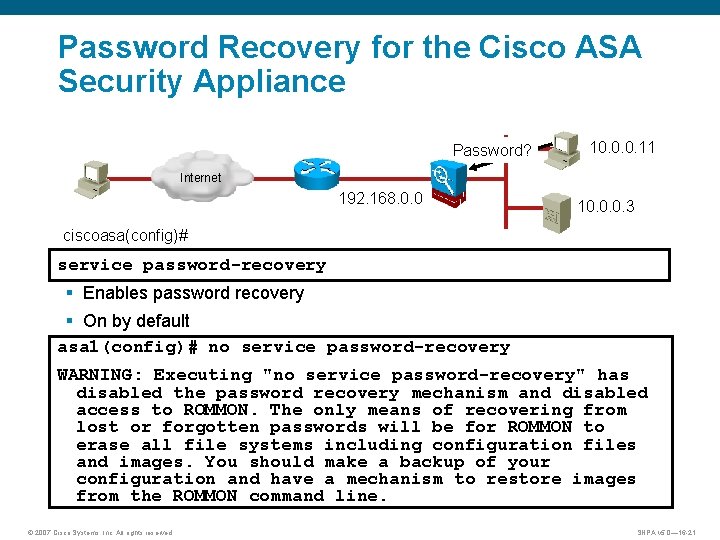
Password Recovery for the Cisco ASA Security Appliance Password? 10. 0. 0. 11 Internet 192. 168. 0. 0 10. 0. 0. 3 ciscoasa(config)# service password-recovery § Enables password recovery § On by default asa 1(config)# no service password-recovery WARNING: Executing "no service password-recovery" has disabled the password recovery mechanism and disabled access to ROMMON. The only means of recovering from lost or forgotten passwords will be for ROMMON to erase all file systems including configuration files and images. You should make a backup of your configuration and have a mechanism to restore images from the ROMMON command line. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -21

Password Recovery for the Cisco PIX Security Appliance § Download the following file from Cisco. com: np. XX. bin, where XX is the Cisco PIX security appliance image version number. § Reboot the system and break the boot process when prompted to go into monitor mode. § Set the interface, IP address, gateway, server, and file to access the previously downloaded image via TFTP. § Follow the directions displayed. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -22

Managing Software, Licenses, and Configurations © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -23

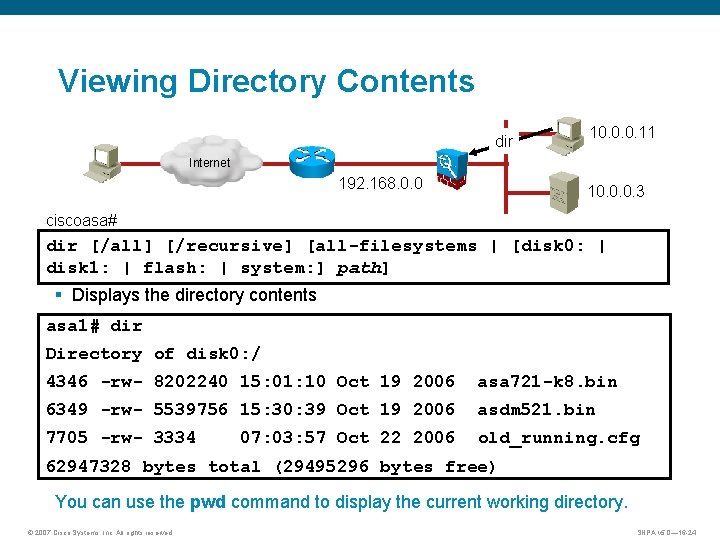
Viewing Directory Contents dir 10. 0. 0. 11 Internet 192. 168. 0. 0 10. 0. 0. 3 ciscoasa# dir [/all] [/recursive] [all-filesystems | [disk 0: | disk 1: | flash: | system: ] path] § Displays the directory contents asa 1# dir Directory of disk 0: / 4346 -rw- 8202240 15: 01: 10 Oct 19 2006 asa 721 -k 8. bin 6349 -rw- 5539756 15: 30: 39 Oct 19 2006 asdm 521. bin 7705 -rw- 3334 07: 03: 57 Oct 22 2006 old_running. cfg 62947328 bytes total (29495296 bytes free) You can use the pwd command to display the current working directory. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -24

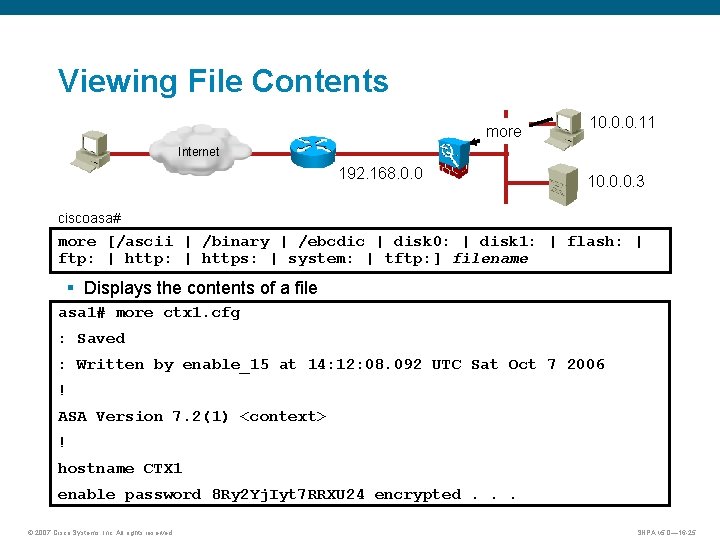
Viewing File Contents more 10. 0. 0. 11 Internet 192. 168. 0. 0 10. 0. 0. 3 ciscoasa# more [/ascii | /binary | /ebcdic | disk 0: | disk 1: | flash: | ftp: | https: | system: | tftp: ] filename § Displays the contents of a file asa 1# more ctx 1. cfg : Saved : Written by enable_15 at 14: 12: 08. 092 UTC Sat Oct 7 2006 ! ASA Version 7. 2(1) <context> ! hostname CTX 1 enable password 8 Ry 2 Yj. Iyt 7 RRXU 24 encrypted. . . © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -25

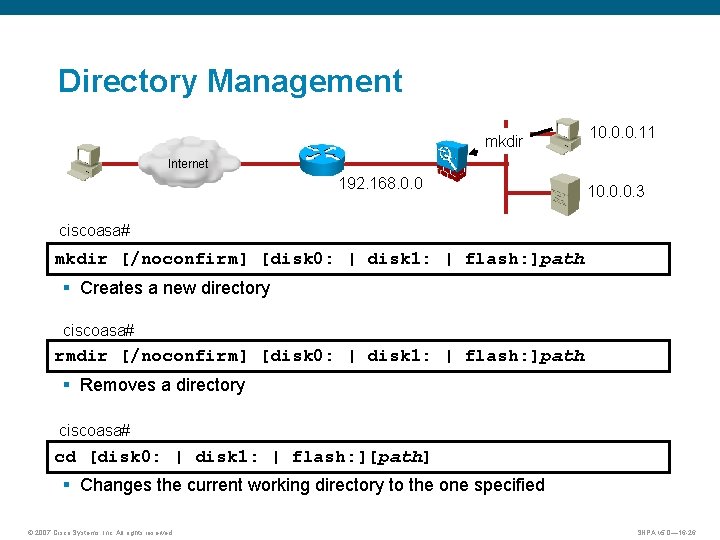
Directory Management mkdir 10. 0. 0. 11 Internet 192. 168. 0. 0 10. 0. 0. 3 ciscoasa# mkdir [/noconfirm] [disk 0: | disk 1: | flash: ]path § Creates a new directory ciscoasa# rmdir [/noconfirm] [disk 0: | disk 1: | flash: ]path § Removes a directory ciscoasa# cd [disk 0: | disk 1: | flash: ][path] § Changes the current working directory to the one specified © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -26

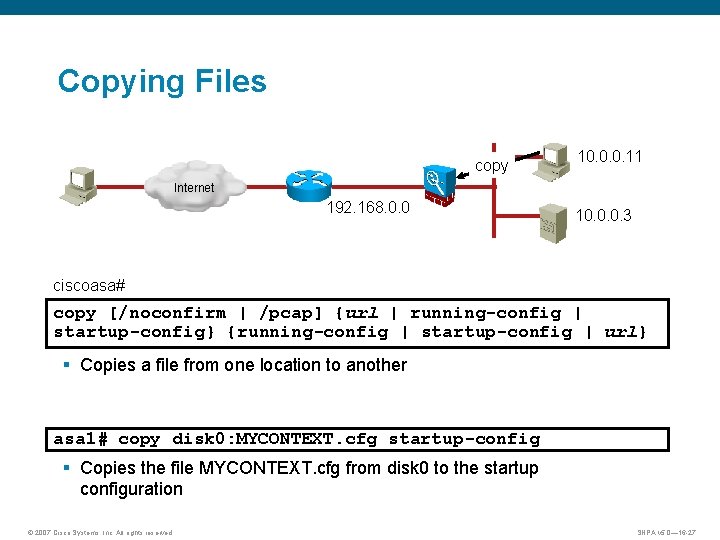
Copying Files copy 10. 0. 0. 11 Internet 192. 168. 0. 0 10. 0. 0. 3 ciscoasa# copy [/noconfirm | /pcap] {url | running-config | startup-config} {running-config | startup-config | url} § Copies a file from one location to another asa 1# copy disk 0: MYCONTEXT. cfg startup-config § Copies the file MYCONTEXT. cfg from disk 0 to the startup configuration © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -27

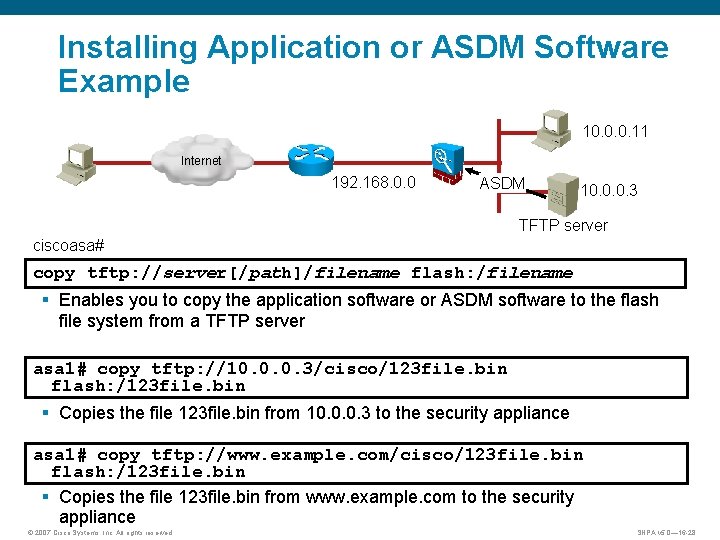
Installing Application or ASDM Software Example 10. 0. 0. 11 Internet 192. 168. 0. 0 ASDM 10. 0. 0. 3 TFTP server ciscoasa# copy tftp: //server[/path]/filename flash: /filename § Enables you to copy the application software or ASDM software to the flash file system from a TFTP server asa 1# copy tftp: //10. 0. 0. 3/cisco/123 file. bin flash: /123 file. bin § Copies the file 123 file. bin from 10. 0. 0. 3 to the security appliance asa 1# copy tftp: //www. example. com/cisco/123 file. bin flash: /123 file. bin § Copies the file 123 file. bin from www. example. com to the security appliance © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -28

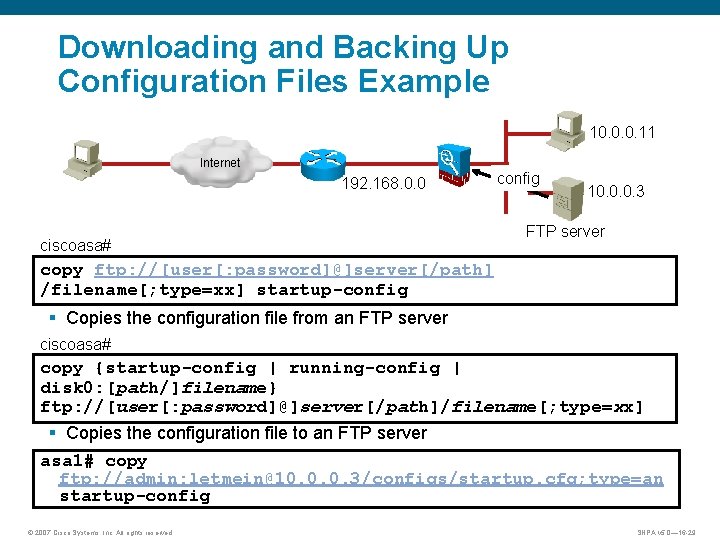
Downloading and Backing Up Configuration Files Example 10. 0. 0. 11 Internet 192. 168. 0. 0 config ciscoasa# 10. 0. 0. 3 FTP server copy ftp: //[user[: password]@]server[/path] /filename[; type=xx] startup-config § Copies the configuration file from an FTP server ciscoasa# copy {startup-config | running-config | disk 0: [path/]filename} ftp: //[user[: password]@]server[/path]/filename[; type=xx] § Copies the configuration file to an FTP server asa 1# copy ftp: //admin: letmein@10. 0. 0. 3/configs/startup. cfg; type=an startup-config © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -29

Image Upgrade and Activation Keys © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -30

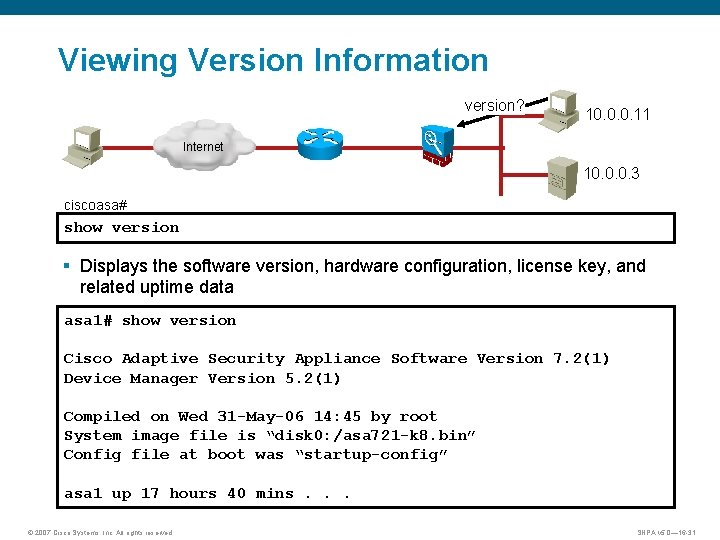
Viewing Version Information version? 10. 0. 0. 11 Internet 10. 0. 0. 3 ciscoasa# show version § Displays the software version, hardware configuration, license key, and related uptime data asa 1# show version Cisco Adaptive Security Appliance Software Version 7. 2(1) Device Manager Version 5. 2(1) Compiled on Wed 31 -May-06 14: 45 by root System image file is “disk 0: /asa 721 -k 8. bin” Config file at boot was “startup-config” asa 1 up 17 hours 40 mins. . . © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -31

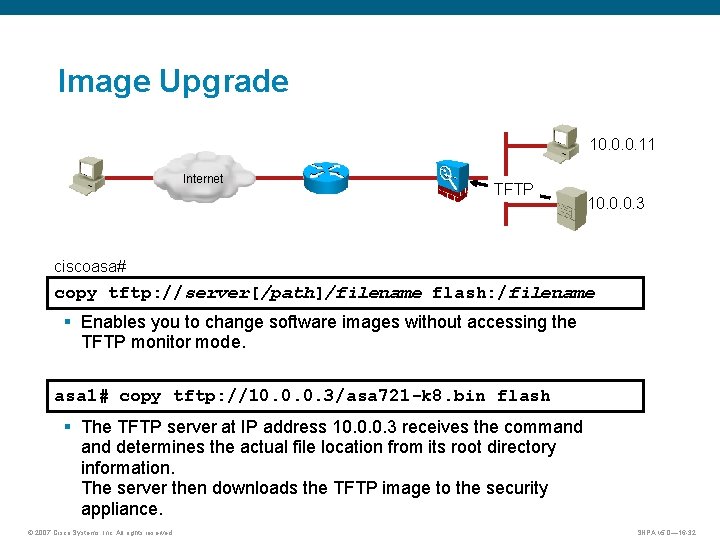
Image Upgrade 10. 0. 0. 11 Internet TFTP 10. 0. 0. 3 ciscoasa# copy tftp: //server[/path]/filename flash: /filename § Enables you to change software images without accessing the TFTP monitor mode. asa 1# copy tftp: //10. 0. 0. 3/asa 721 -k 8. bin flash § The TFTP server at IP address 10. 0. 0. 3 receives the command determines the actual file location from its root directory information. The server then downloads the TFTP image to the security appliance. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -32

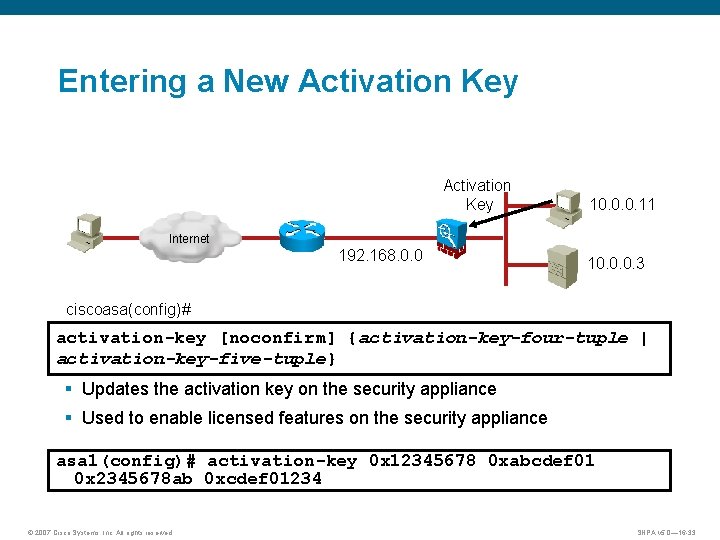
Entering a New Activation Key 10. 0. 0. 11 Internet 192. 168. 0. 0 10. 0. 0. 3 ciscoasa(config)# activation-key [noconfirm] {activation-key-four-tuple | activation-key-five-tuple} § Updates the activation key on the security appliance § Used to enable licensed features on the security appliance asa 1(config)# activation-key 0 x 12345678 0 xabcdef 01 0 x 2345678 ab 0 xcdef 01234 © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -33

Upgrading the Image and the Activation Key Complete the following steps to upgrade the image and the activation key at the same time: § Step 1: Install the new image. § Step 2: Reboot the system. § Step 3: Update the activation key. § Step 4: Reboot the system. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -34

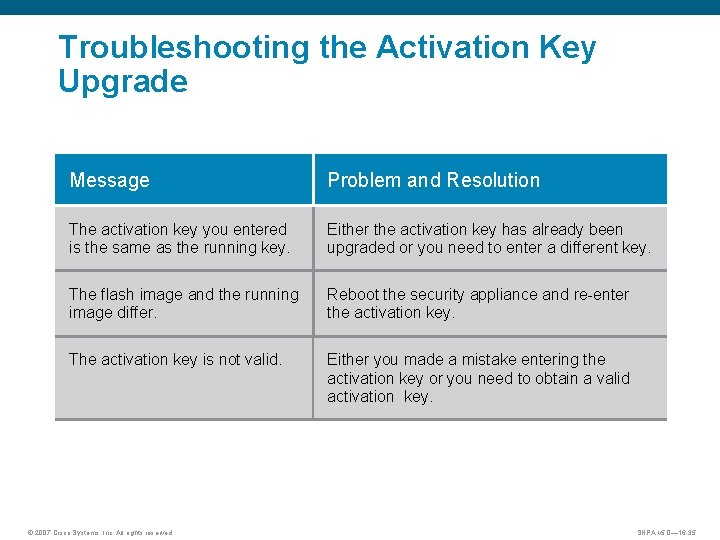
Troubleshooting the Activation Key Upgrade Message Problem and Resolution The activation key you entered is the same as the running key. Either the activation key has already been upgraded or you need to enter a different key. The flash image and the running image differ. Reboot the security appliance and re-enter the activation key. The activation key is not valid. Either you made a mistake entering the activation key or you need to obtain a valid activation key. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -35

Summary © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -36

Summary § SSH provides secure remote management of the security appliance. § TFTP is used to upgrade the software image on security appliances. § You can configure the following types of command authorization: – Command authorization with password-protected privilege levels – Command authorization with username and password authentication § The security appliance can be configured to permit multiple users to access its console simultaneously via Telnet. § You can enable Telnet to the security appliance on all interfaces. § Password recovery for the security appliance requires a TFTP server. © 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -37

© 2007 Cisco Systems, Inc. All rights reserved. SNPA v 5. 0— 16 -38