Network Layer Protocols CSIT 435 Spring 2002 4







- Slides: 39

Network Layer Protocols CSIT 435 Spring 2002 4: Network Layer 1

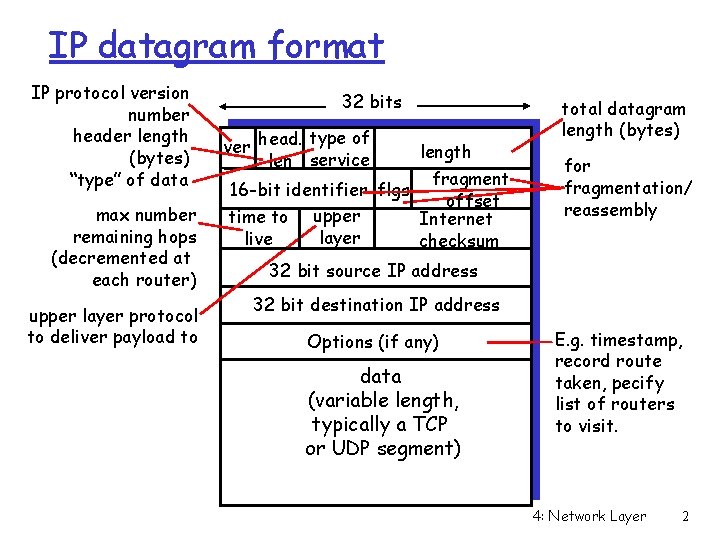
IP datagram format IP protocol version number header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to 32 bits type of ver head. len service length fragment 16 -bit identifier flgs offset time to upper Internet layer live checksum total datagram length (bytes) for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) E. g. timestamp, record route taken, pecify list of routers to visit. 4: Network Layer 2

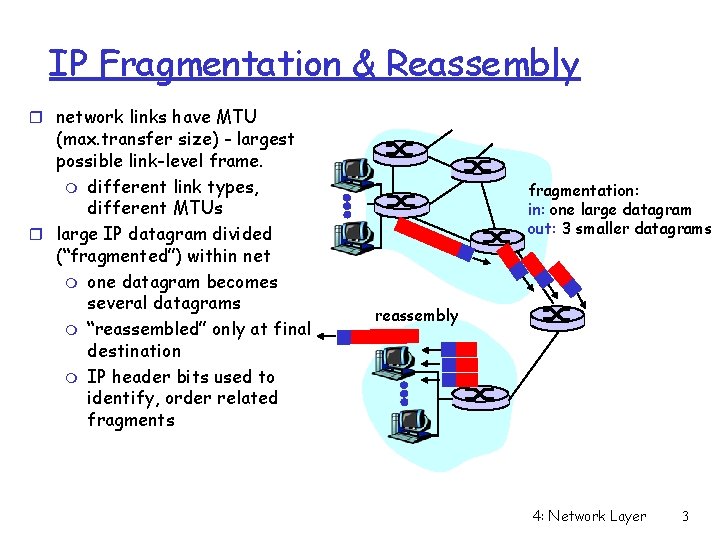
IP Fragmentation & Reassembly r network links have MTU (max. transfer size) - largest possible link-level frame. m different link types, different MTUs r large IP datagram divided (“fragmented”) within net m one datagram becomes several datagrams m “reassembled” only at final destination m IP header bits used to identify, order related fragments fragmentation: in: one large datagram out: 3 smaller datagrams reassembly 4: Network Layer 3

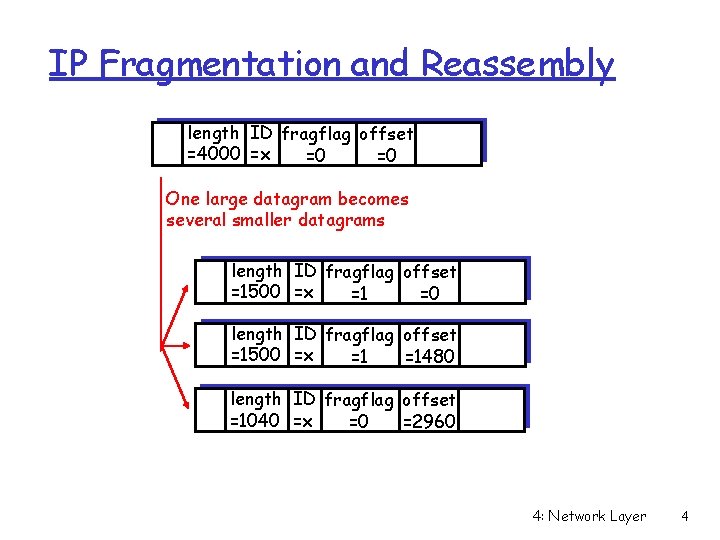
IP Fragmentation and Reassembly length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =1480 length ID fragflag offset =1040 =x =0 =2960 4: Network Layer 4

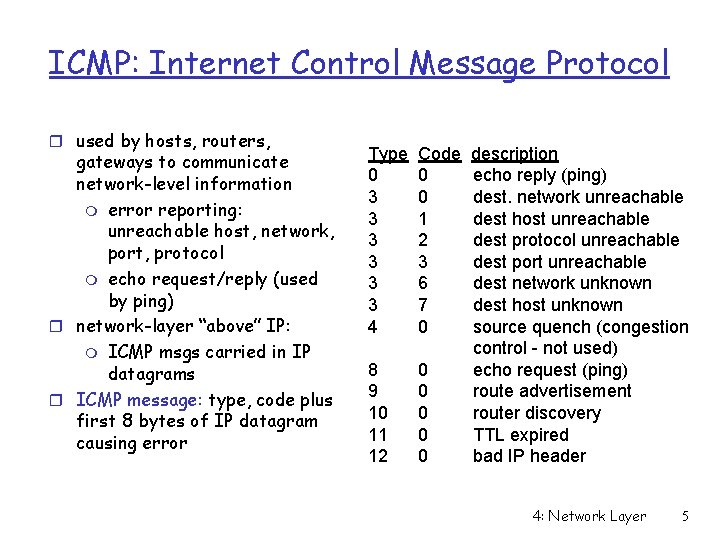
ICMP: Internet Control Message Protocol r used by hosts, routers, gateways to communicate network-level information m error reporting: unreachable host, network, port, protocol m echo request/reply (used by ping) r network-layer “above” IP: m ICMP msgs carried in IP datagrams r ICMP message: type, code plus first 8 bytes of IP datagram causing error Type 0 3 3 3 4 Code 0 0 1 2 3 6 7 0 8 9 10 11 12 0 0 0 description echo reply (ping) dest. network unreachable dest host unreachable dest protocol unreachable dest port unreachable dest network unknown dest host unknown source quench (congestion control - not used) echo request (ping) route advertisement router discovery TTL expired bad IP header 4: Network Layer 5

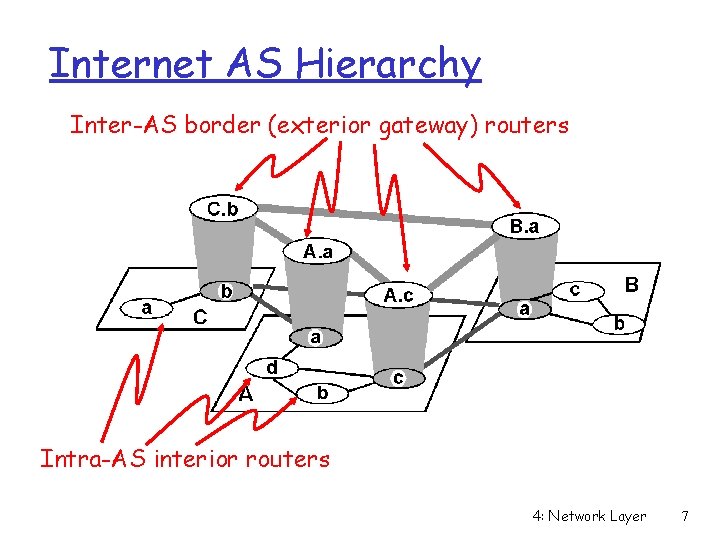
Routing in the Internet r The Global Internet consists of Autonomous Systems (AS) interconnected with each other: m m m Stub AS: small corporation Multihomed AS: large corporation (no transit) Transit AS: provider r Two-level routing: m Intra-AS: administrator is responsible for choice m Inter-AS: unique standard 4: Network Layer 6

Internet AS Hierarchy Inter-AS border (exterior gateway) routers Intra-AS interior routers 4: Network Layer 7

Intra-AS Routing r Also known as Interior Gateway Protocols (IGP) r Most common IGPs: m RIP: Routing Information Protocol m OSPF: Open Shortest Path First m IGRP: Interior Gateway Routing Protocol (Cisco propr. ) 4: Network Layer 8

RIP ( Routing Information Protocol) r Distance vector algorithm r Included in BSD-UNIX Distribution in 1982 r Distance metric: # of hops (max = 15 hops) r Distance vectors: exchanged every 30 sec via Response Message (also called advertisement) r Each advertisement: route to up to 25 destination nets 4: Network Layer 9

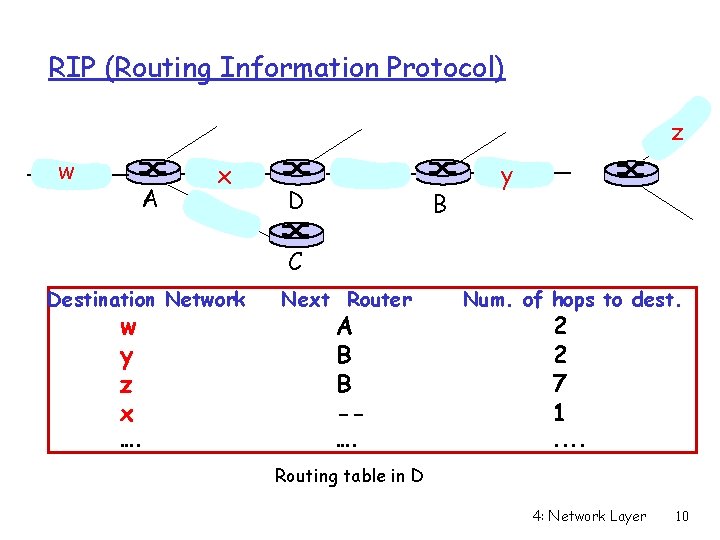
RIP (Routing Information Protocol) z w A x D B y C Destination Network w y z x …. Next Router Num. of hops to dest. …. . . A B B -- 2 2 7 1 Routing table in D 4: Network Layer 10

RIP: Link Failure and Recovery If no advertisement heard after 180 sec --> neighbor/link declared dead m routes via neighbor invalidated m new advertisements sent to neighbors m neighbors in turn send out new advertisements (if tables changed) m link failure info quickly propagates to entire net m poison reverse used to prevent ping-pong loops (infinite distance = 16 hops) m (POISON REVERSE: If Z needs to go through Y to reach X, Z keeps telling Y that it cannot reach X so Y will never try to use Z to reach X) 4: Network Layer 11

RIP Table processing r RIP routing tables managed by application-level process called route-d (daemon) r advertisements sent in UDP packets, periodically repeated 4: Network Layer 12

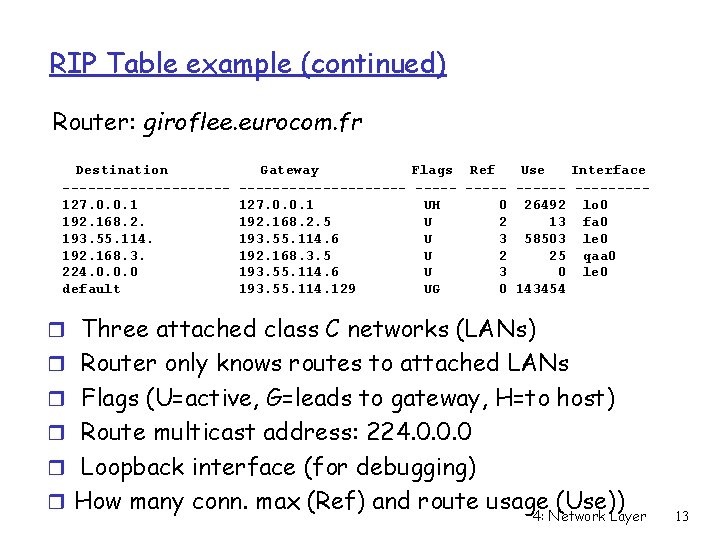
RIP Table example (continued) Router: giroflee. eurocom. fr Destination ----------127. 0. 0. 1 192. 168. 2. 193. 55. 114. 192. 168. 3. 224. 0. 0. 0 default Gateway Flags Ref Use Interface ---------- --------127. 0. 0. 1 UH 0 26492 lo 0 192. 168. 2. 5 U 2 13 fa 0 193. 55. 114. 6 U 3 58503 le 0 192. 168. 3. 5 U 2 25 qaa 0 193. 55. 114. 6 U 3 0 le 0 193. 55. 114. 129 UG 0 143454 r Three attached class C networks (LANs) r Router only knows routes to attached LANs r Flags (U=active, G=leads to gateway, H=to host) r Route multicast address: 224. 0. 0. 0 r Loopback interface (for debugging) r How many conn. max (Ref) and route usage (Use)) 4: Network Layer 13

OSPF (Open Shortest Path First) r “open”: publicly available r Uses Link State algorithm m LS packet dissemination m Complete topology map at each node m Route computation using Dijkstra’s algorithm (least cost) r OSPF advertisement carries one entry per neighbor router r Advertisements disseminated to entire AS (via flooding) 4: Network Layer 14

OSPF “advanced” features (not in RIP) r Security: all OSPF messages authenticated (to prevent malicious intrusion); TCP connections used r Multiple same-cost paths allowed (only one path in RIP) r For each link, multiple cost metrics for different TOS (eg, satellite link cost set “low” for best effort; high for real time) r Integrated uni- and multicast support: m Multicast OSPF (MOSPF) uses same topology data base as OSPF r Hierarchical OSPF in large domains. 4: Network Layer 15

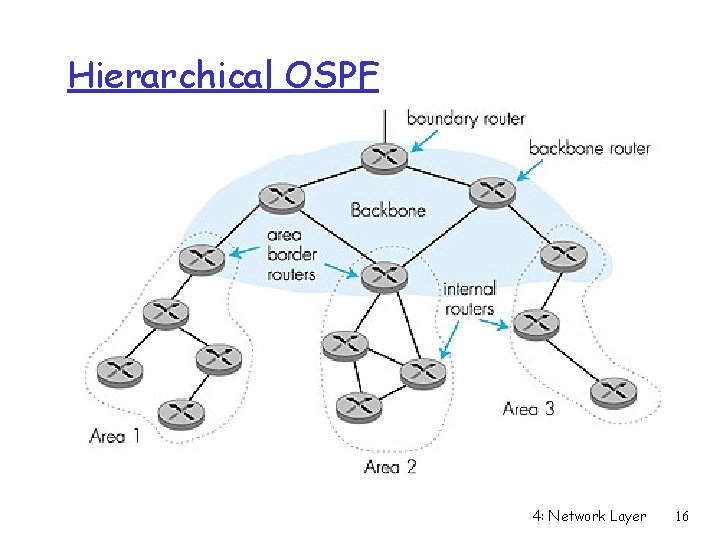
Hierarchical OSPF 4: Network Layer 16

Hierarchical OSPF r Two-level hierarchy: local area, backbone. m Link-state advertisements only in area m each node has detailed area topology; only knows direction (shortest path) to nets in other areas. r Area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. r Backbone routers: run OSPF routing limited to backbone. r Boundary routers: connect to other ASs. 4: Network Layer 17

Summary r CIDR saves routing table space by aggregating routes and saves on IP addresses r ICMP is the official mail of the Internet. It is carried in “special envelops” i. e IP packets marked with ICMP as the upper protocol to deliver to r ping, traceroute generate ICMP packets r IPv 4 allows packet fragmentation by core routers and reassembly by destination r RIP is the first interior routing protocol (routed in UNIX) based on distance vector routing r RIP is becoming “rest in peace” 4: Network Layer 18

Summary r OSPF is the most popular interior routing protocol in the Internet r OSPF uses TCP to authenticate routers as trusted routers. r Otherwise, OSPF runs directly over IP r OSPF routers flood their link-state information to all the routers in an area r A two-level hierarchy is allowed in OSPF for large AS (autonomous systems) r An AS may have “areas” defined. Flooding will be limited to the routers inside one area only r BGP is the exterior routing protocol of choice based on path vector exchange 4: Network Layer 19

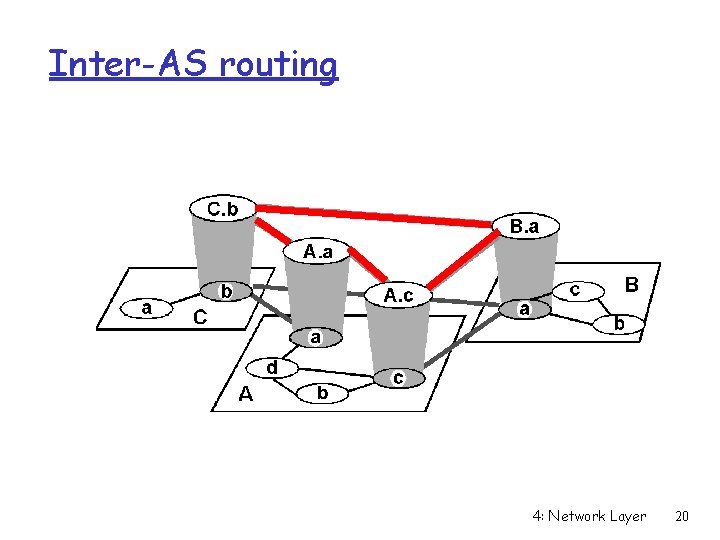
Inter-AS routing 4: Network Layer 20

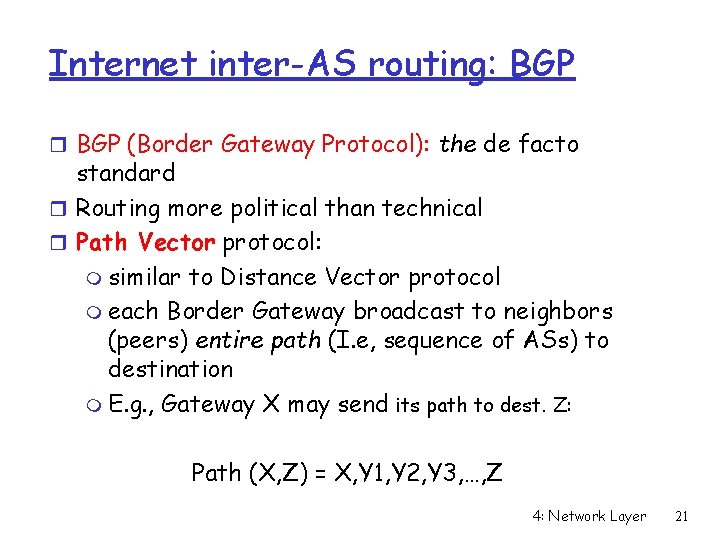
Internet inter-AS routing: BGP r BGP (Border Gateway Protocol): the de facto standard r Routing more political than technical r Path Vector protocol: m similar to Distance Vector protocol m each Border Gateway broadcast to neighbors (peers) entire path (I. e, sequence of ASs) to destination m E. g. , Gateway X may send its path to dest. Z: Path (X, Z) = X, Y 1, Y 2, Y 3, …, Z 4: Network Layer 21

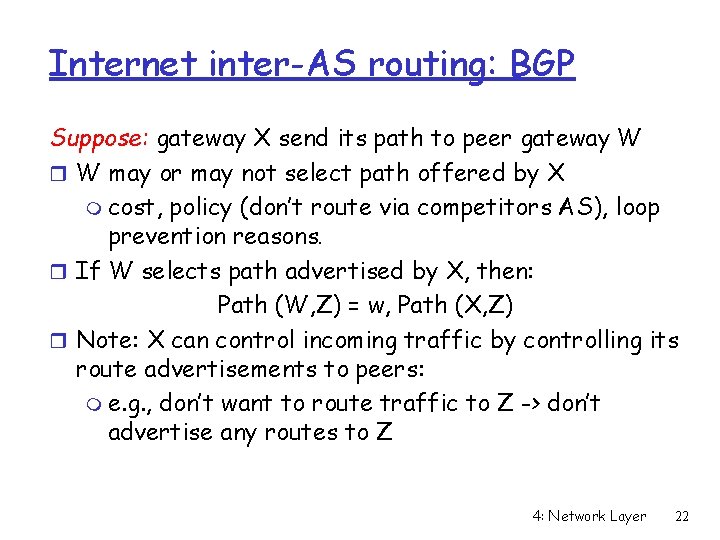
Internet inter-AS routing: BGP Suppose: gateway X send its path to peer gateway W r W may or may not select path offered by X m cost, policy (don’t route via competitors AS), loop prevention reasons. r If W selects path advertised by X, then: Path (W, Z) = w, Path (X, Z) r Note: X can control incoming traffic by controlling its route advertisements to peers: m e. g. , don’t want to route traffic to Z -> don’t advertise any routes to Z 4: Network Layer 22

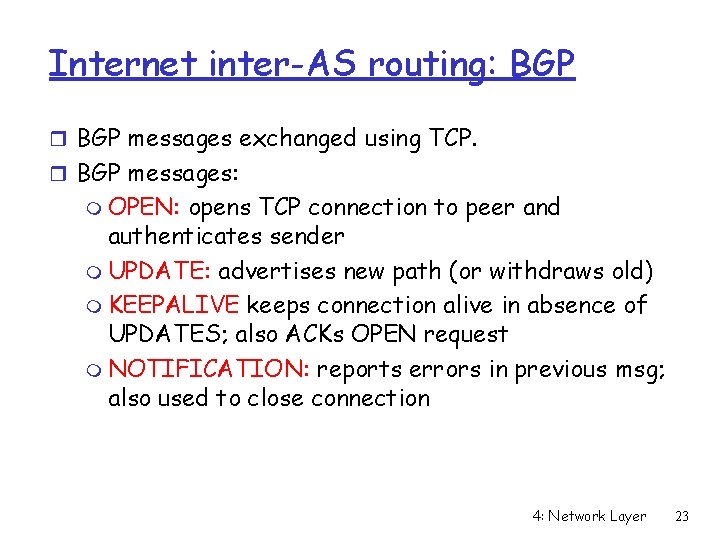
Internet inter-AS routing: BGP r BGP messages exchanged using TCP. r BGP messages: m OPEN: opens TCP connection to peer and authenticates sender m UPDATE: advertises new path (or withdraws old) m KEEPALIVE keeps connection alive in absence of UPDATES; also ACKs OPEN request m NOTIFICATION: reports errors in previous msg; also used to close connection 4: Network Layer 23

Why different Intra- and Inter-AS routing ? Policy: r Inter-AS: admin wants control over how its traffic routed, who routes through its net. r Intra-AS: single admin, so no policy decisions needed Scale: r hierarchical routing saves table size, reduced update traffic Performance: r Intra-AS: can focus on performance r Inter-AS: policy may dominate over performance 4: Network Layer 24

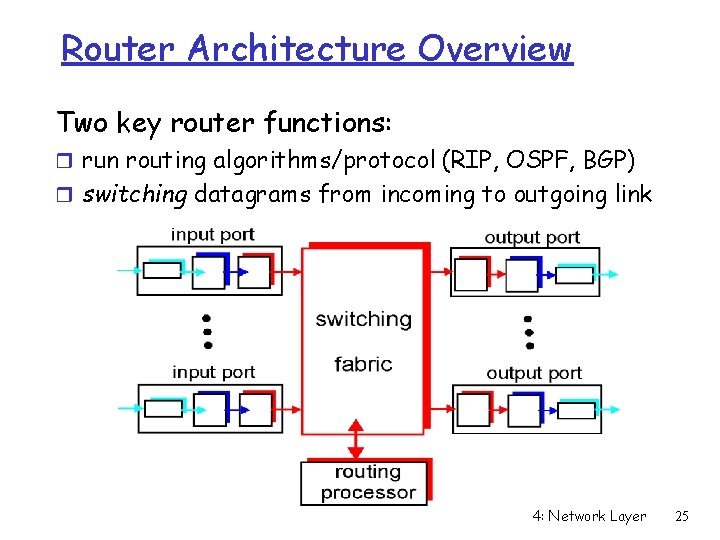
Router Architecture Overview Two key router functions: r run routing algorithms/protocol (RIP, OSPF, BGP) r switching datagrams from incoming to outgoing link 4: Network Layer 25

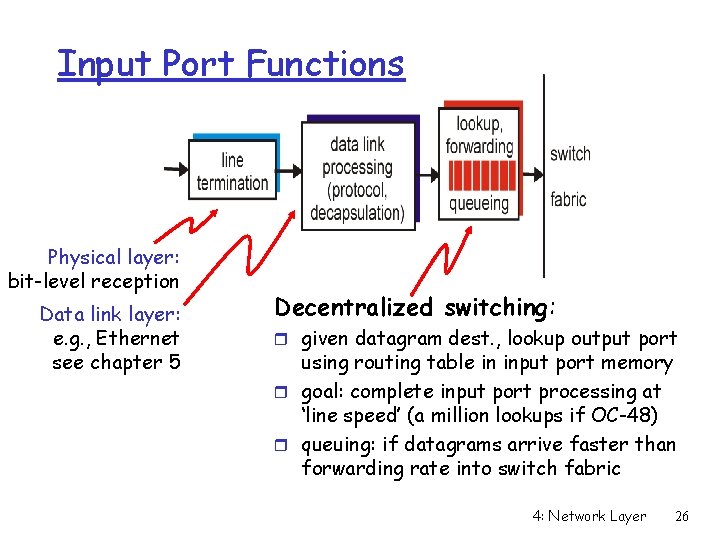
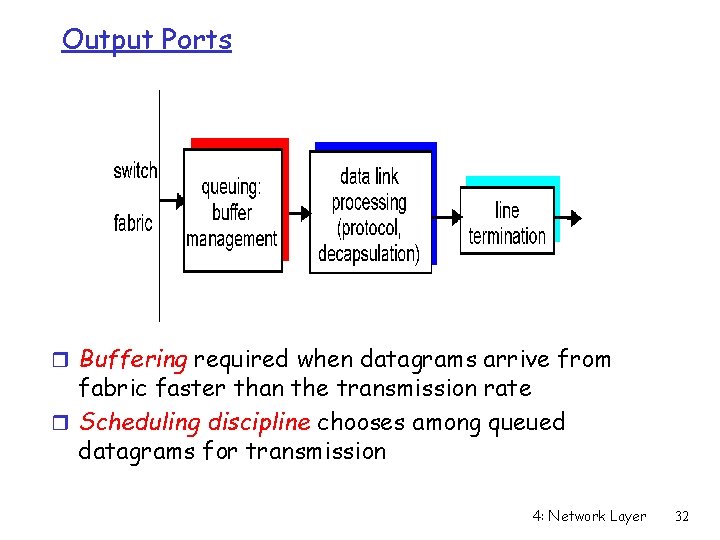
Input Port Functions Physical layer: bit-level reception Data link layer: e. g. , Ethernet see chapter 5 Decentralized switching: r given datagram dest. , lookup output port using routing table in input port memory r goal: complete input port processing at ‘line speed’ (a million lookups if OC-48) r queuing: if datagrams arrive faster than forwarding rate into switch fabric 4: Network Layer 26

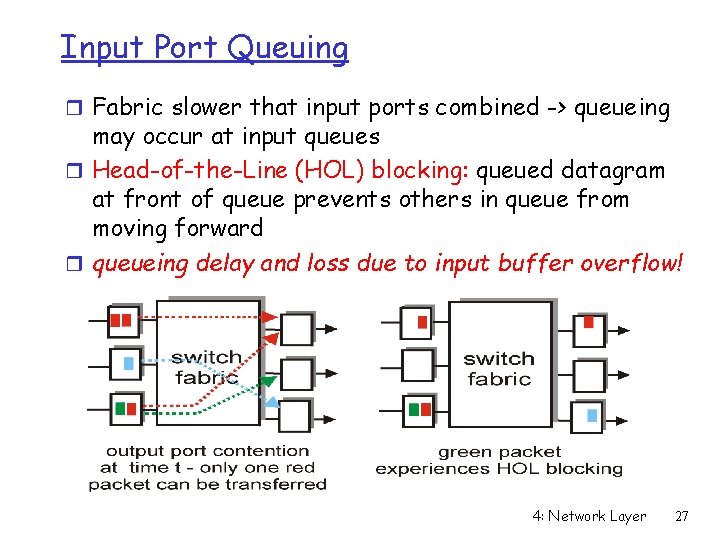
Input Port Queuing r Fabric slower that input ports combined -> queueing may occur at input queues r Head-of-the-Line (HOL) blocking: queued datagram at front of queue prevents others in queue from moving forward r queueing delay and loss due to input buffer overflow! 4: Network Layer 27

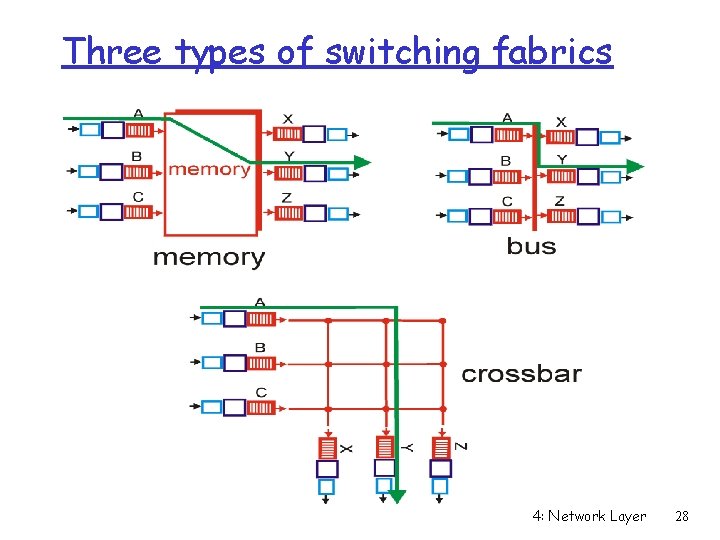
Three types of switching fabrics 4: Network Layer 28

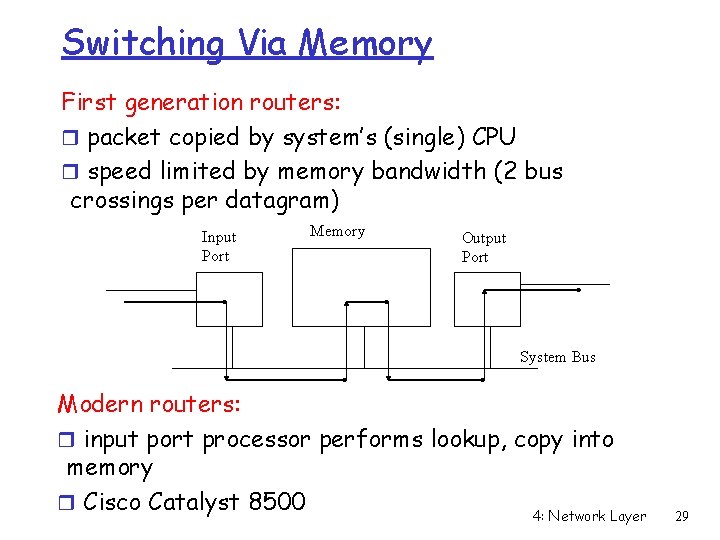
Switching Via Memory First generation routers: r packet copied by system’s (single) CPU r speed limited by memory bandwidth (2 bus crossings per datagram) Input Port Memory Output Port System Bus Modern routers: r input port processor performs lookup, copy into memory r Cisco Catalyst 8500 4: Network Layer 29

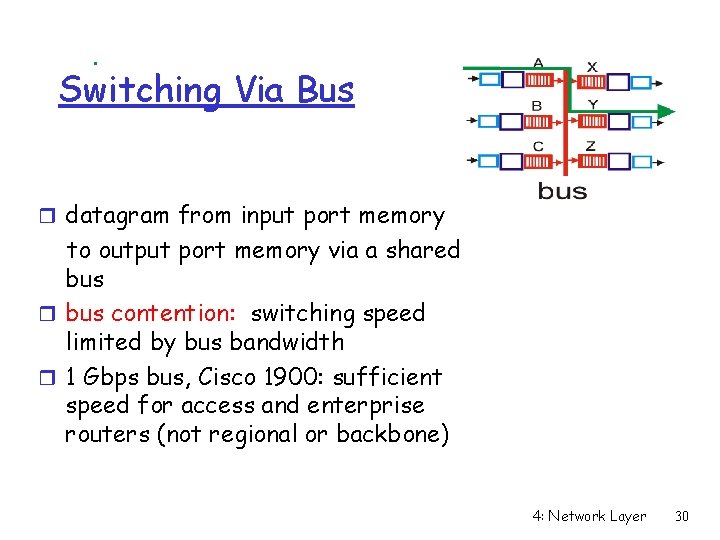
Switching Via Bus r datagram from input port memory to output port memory via a shared bus r bus contention: switching speed limited by bus bandwidth r 1 Gbps bus, Cisco 1900: sufficient speed for access and enterprise routers (not regional or backbone) 4: Network Layer 30

Switching Via An Interconnection Network r overcome bus bandwidth limitations r Banyan networks, other interconnection nets initially developed to connect processors in multiprocessor r Advanced design: fragmenting datagram into fixed length cells, switch cells through the fabric. r Cisco 12000: switches Gbps through the interconnection network 4: Network Layer 31

Output Ports r Buffering required when datagrams arrive from fabric faster than the transmission rate r Scheduling discipline chooses among queued datagrams for transmission 4: Network Layer 32

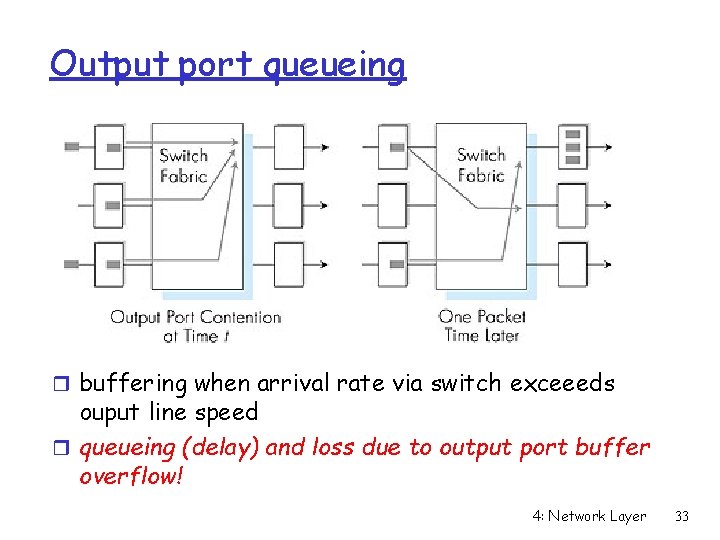
Output port queueing r buffering when arrival rate via switch exceeeds ouput line speed r queueing (delay) and loss due to output port buffer overflow! 4: Network Layer 33

IPv 6 r Initial motivation: 32 -bit address space completely allocated by 2008. (IPv 6 has 128 bit address, enough to allocate 7 X 1023 IP addresses to every square meter of earth) r Additional motivation: m m m header fixed format speeds up processing/forwarding header changes to facilitate Qo. S new “anycast” address: route to “best” of a group of replicated servers (nearest one) r IPv 6 datagram format: m fixed-length 40 byte header m no fragmentation allowed 4: Network Layer 34

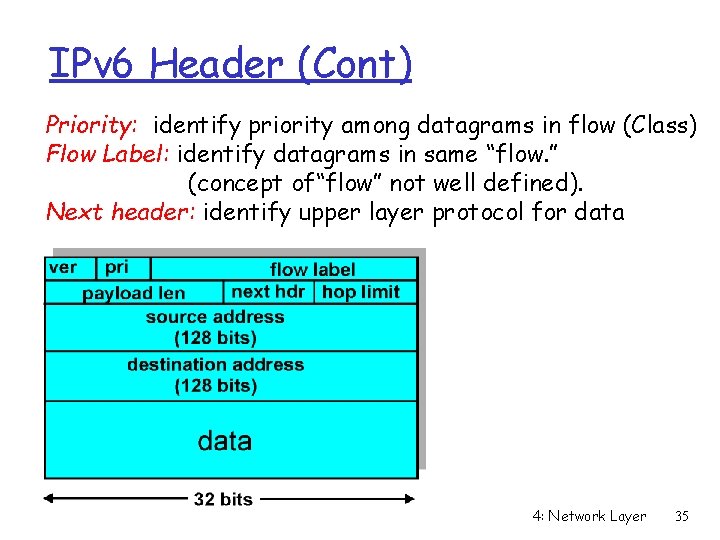
IPv 6 Header (Cont) Priority: identify priority among datagrams in flow (Class) Flow Label: identify datagrams in same “flow. ” (concept of“flow” not well defined). Next header: identify upper layer protocol for data 4: Network Layer 35

Other Changes from IPv 4 r Checksum: removed entirely to reduce processing time at each hop r Options: allowed, but outside of header, indicated by “Next Header” field r ICMPv 6: new version of ICMP m additional message types, e. g. “Packet Too Big” m multicast group management functions 4: Network Layer 36

Transition From IPv 4 To IPv 6 r Not all routers can be upgraded simultaneous m no “flag days” m How will the network operatewith mixed IPv 4 and IPv 6 routers? r Two proposed approaches: m Dual Stack: some routers with dual stack (v 6, v 4) can “translate” between formats m Tunneling: IPv 6 carried as payload n IPv 4 datagram among IPv 4 routers 4: Network Layer 37

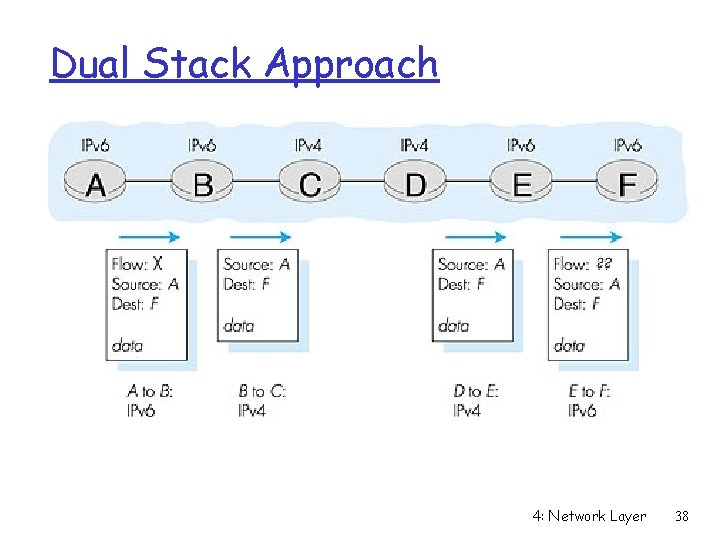
Dual Stack Approach 4: Network Layer 38

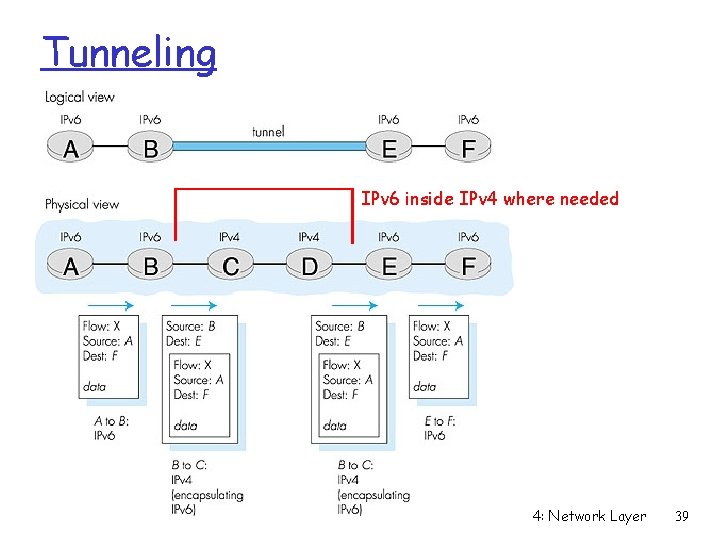
Tunneling IPv 6 inside IPv 4 where needed 4: Network Layer 39