Network Layer Chapter 5 Design Issues Routing Algorithms













- Slides: 49

Network Layer Chapter 5 • • • Design Issues Routing Algorithms Congestion Control Quality of Service Internetworking Network Layer of the Internet Revised: August 2011 CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

The Network Layer Responsible for delivering packets between endpoints over multiple links CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Application Transport Network Link Physical

Congestion Control (1) Handling congestion is the responsibility of the Network and Transport layers working together − We look at the Network portion here • • Traffic-aware routing » Admission control » Traffic throttling » Load shedding » CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

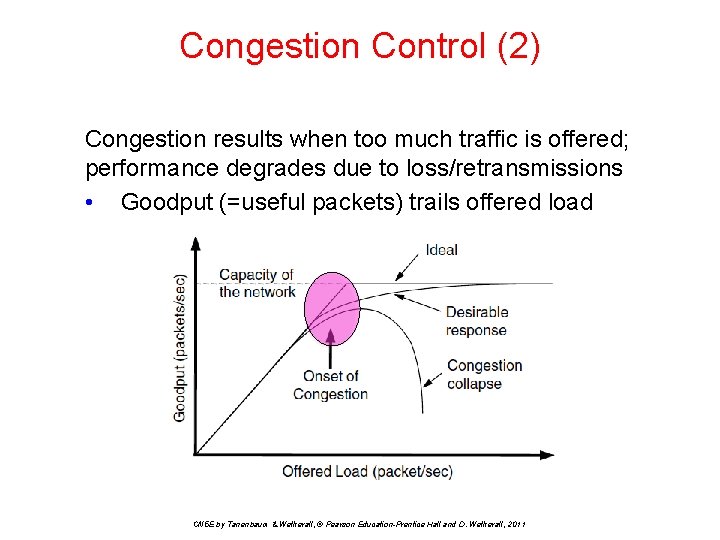
Congestion Control (2) Congestion results when too much traffic is offered; performance degrades due to loss/retransmissions • Goodput (=useful packets) trails offered load CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Factors causing congestion Streams of packets simultaneously begin arriving on several input lines that are headed for the same output line Slow processors Low-bandwidth lines Mismatch between parts of the system Feeding congestion upon itself • Retransmission of lost packets TUNALI 5 Computer Networks 1

Congestion Control versus Flow Control Congestion control • Making sure that the net is able to carry the offered traffic Flow control • Related to point-to-point traffic between the sender and the receiver • Making sure that a fast sender can not continually transmit data faster than the receiver can absorb it A sender may receive a ‘slow down’ message either due to − congestion in the subnet or − due to receiver not being able to handle the load TUNALI 6 Computer Networks 1

Congestion Control (3) – Approaches Network must do its best with the offered load • Different approaches at different timescales • Nodes should also reduce offered load (Transport) CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Congestion Control (4) – Approaches Network Provisioning: Build the network well matching traffic needs Traffic-aware routing: Routes may be changed dynamically by changing the shortest path weights Admission control: Refuse requests that would overload the network Load shedding: Discard packets CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

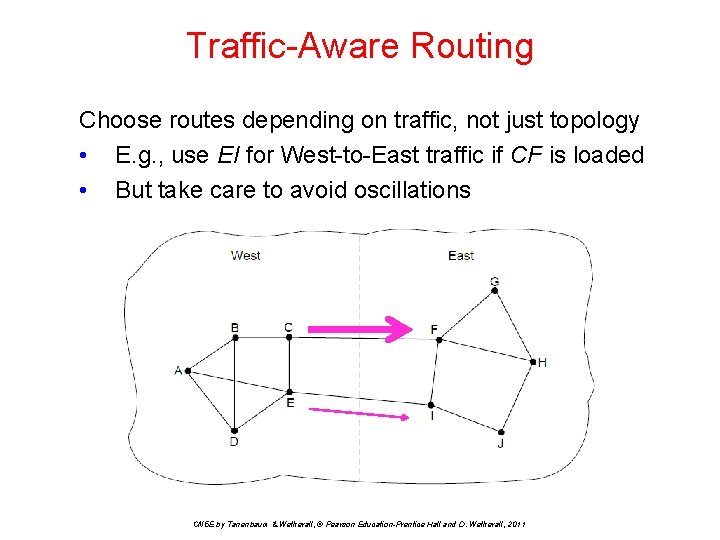
Traffic-Aware Routing Choose routes depending on traffic, not just topology • E. g. , use EI for West-to-East traffic if CF is loaded • But take care to avoid oscillations CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Traffic-Aware Routing 2 Choose weights to be a function of Bandwith (fixed) Delay (fixed) Load (variable) The parameters must be crafted carefully to avoid oscillations due to changing load. CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

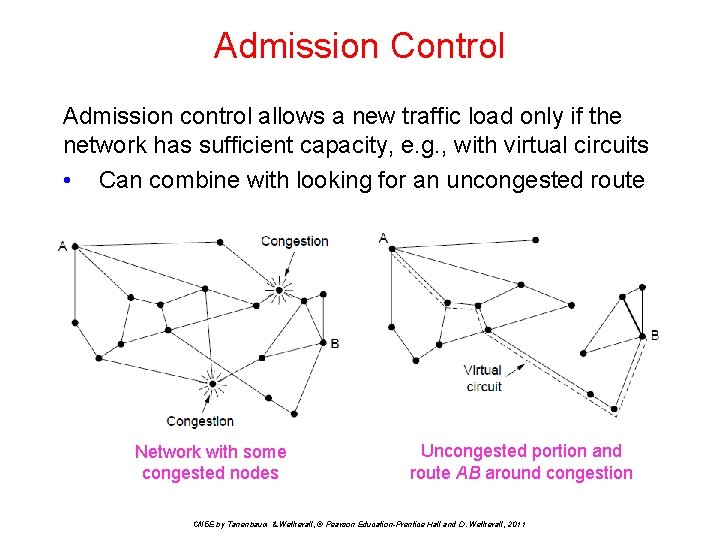
Admission Control Admission control allows a new traffic load only if the network has sufficient capacity, e. g. , with virtual circuits • Can combine with looking for an uncongested route Network with some congested nodes Uncongested portion and route AB around congestion CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Admission Control 2 To carry out admission control, one needs to characterize the network traffic. Two measures are used to do this: Average data rate Instantaneous burst size CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

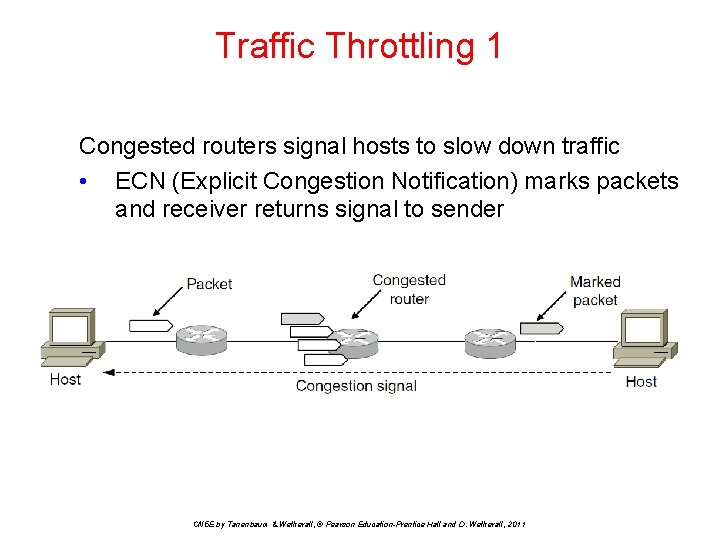
Traffic Throttling 1 Congested routers signal hosts to slow down traffic • ECN (Explicit Congestion Notification) marks packets and receiver returns signal to sender CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Traffic Throttling 2 The main idea is congestion avoidance. Routers diagnose upcoming congestion by monitoring: Queue lengths in buffers Compute queuing delay by using exponentially weighted moving average (EWMA) formula Utilization of the output links Number of packets lost CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Choke Packets If a newly arrived packet’s output line is in warning state, • a CHOKE PACKET is sent back to the source • The packet is forwarded to the destination The source receiving the choke packet is expected to reduce its traffic accordingly TUNALI 15 Computer Networks 1

Explicit Congestion Notification No extra packet generated Router tags the packet and forwards it to the destination Destination reading the tag informs the source about the problem CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Hop-by-Hop Backpressure At high speeds, choke packet reaction is slow Alternative: • Hop-by-Hop choke packets − Choke packets take effect at every hop it passes through TUNALI 17 Computer Networks 1

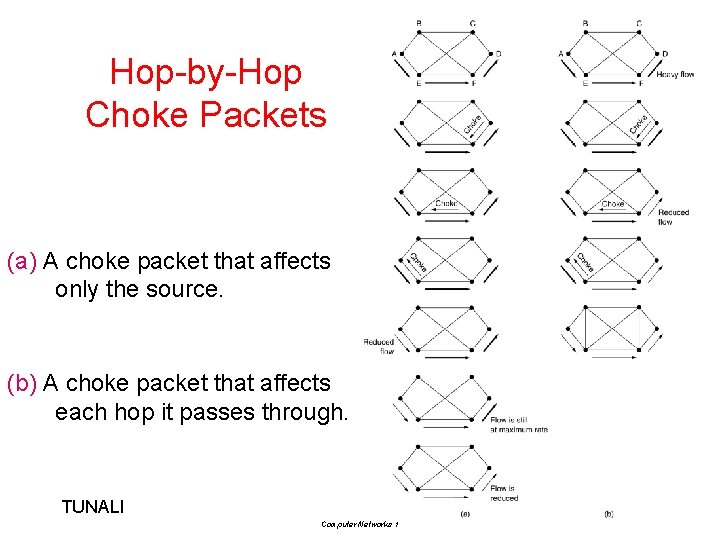
Hop-by-Hop Choke Packets (a) A choke packet that affects only the source. (b) A choke packet that affects each hop it passes through. TUNALI 18 Computer Networks 1

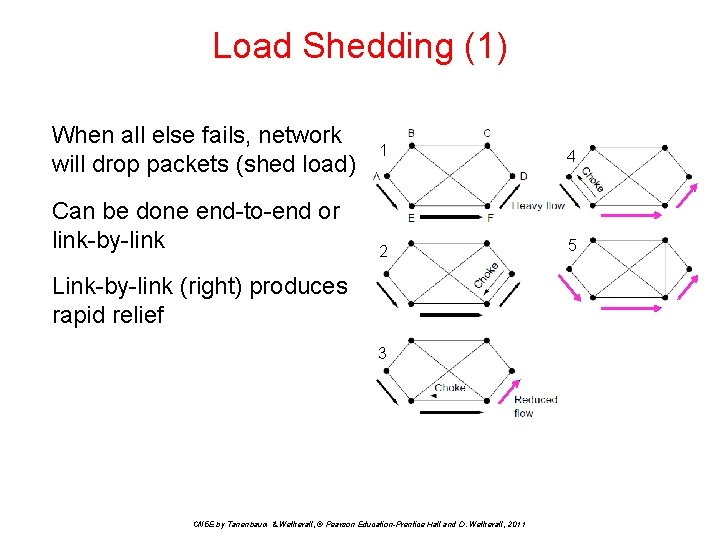
Load Shedding (1) When all else fails, network will drop packets (shed load) Can be done end-to-end or link-by-link 1 4 2 5 Link-by-link (right) produces rapid relief 3 CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

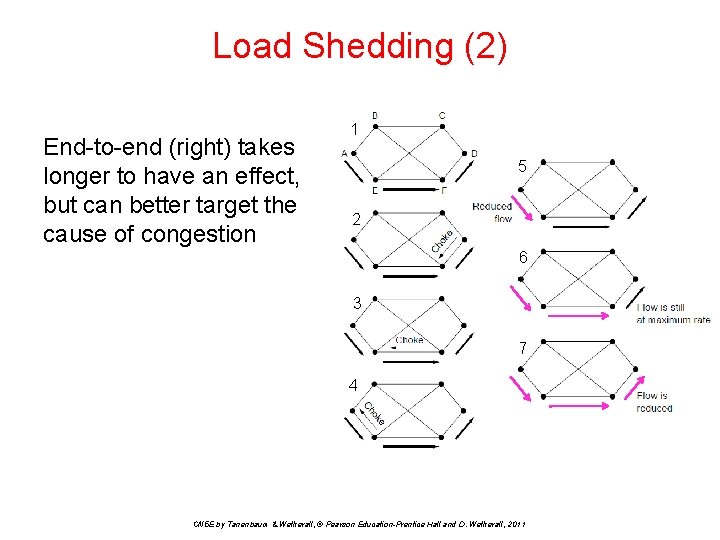
Load Shedding (2) End-to-end (right) takes longer to have an effect, but can better target the cause of congestion 1 5 2 6 3 7 4 CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Load Shedding 3 Random dropping can be done but there are better policies • Wine policy − Old is better than new » More efficient in go back n • Milk policy − New is better than old » More efficient in multimedia streaming • Priority policy − MPEG uses compression that has some frames carrying more important information TUNALI 21 Computer Networks 1

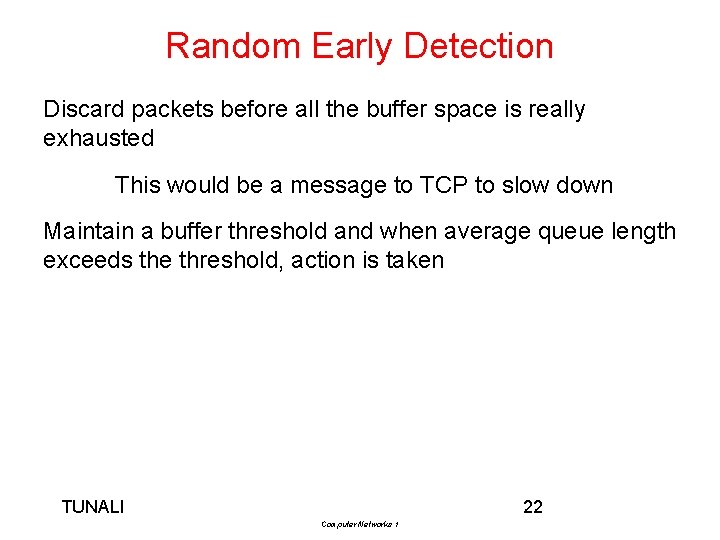
Random Early Detection Discard packets before all the buffer space is really exhausted This would be a message to TCP to slow down Maintain a buffer threshold and when average queue length exceeds the threshold, action is taken TUNALI 22 Computer Networks 1

Quality of Service • • • Application requirements » Traffic shaping » Packet scheduling » Admission control » Integrated services » Differentiated services » CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Overprovisioning • • Provide the necessary router capacity, buffer space and bandwidth to smoothly send the packets Expensive TUNALI 24 Computer Networks 1

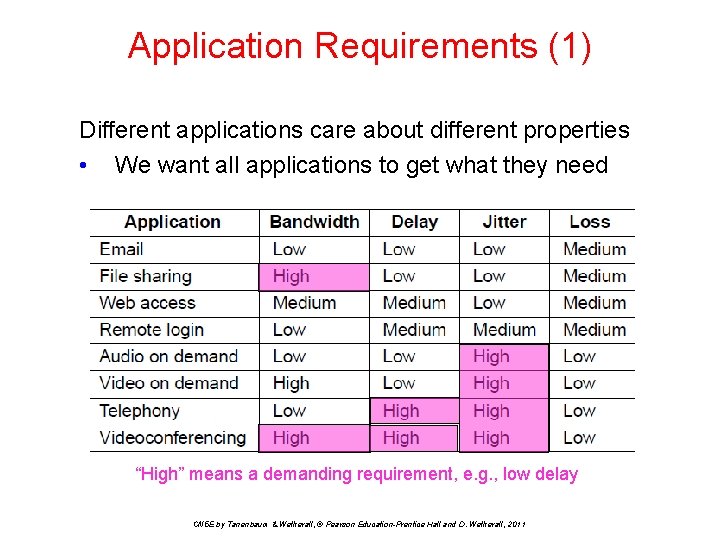
Application Requirements (1) Different applications care about different properties • We want all applications to get what they need. “High” means a demanding requirement, e. g. , low delay CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

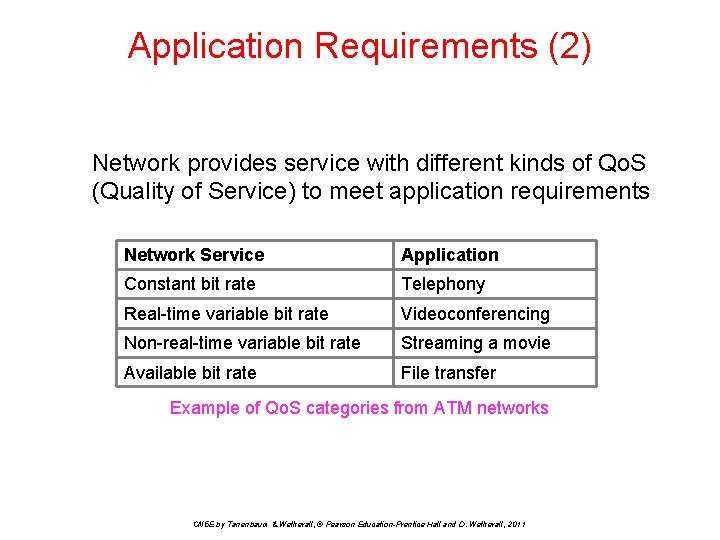
Application Requirements (2) Network provides service with different kinds of Qo. S (Quality of Service) to meet application requirements Network Service Application Constant bit rate Telephony Real-time variable bit rate Videoconferencing Non-real-time variable bit rate Streaming a movie Available bit rate File transfer Example of Qo. S categories from ATM networks CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Traffic Shaping 1 Bursty traffic is often the cause of congestion Traffic shaping regulates the average rate (and burstiness) of data transmission This is an open loop method to prevent congestion. When virtual circuit is set up, the user and the subnet agree on certain traffic pattern. As long as the user fulfills its contract, the carrier live up to its promise Traffic policing is the monitoring of user’s rate Carrier discards packets if the user breaks the contract TUNALI 27 Computer Networks 1

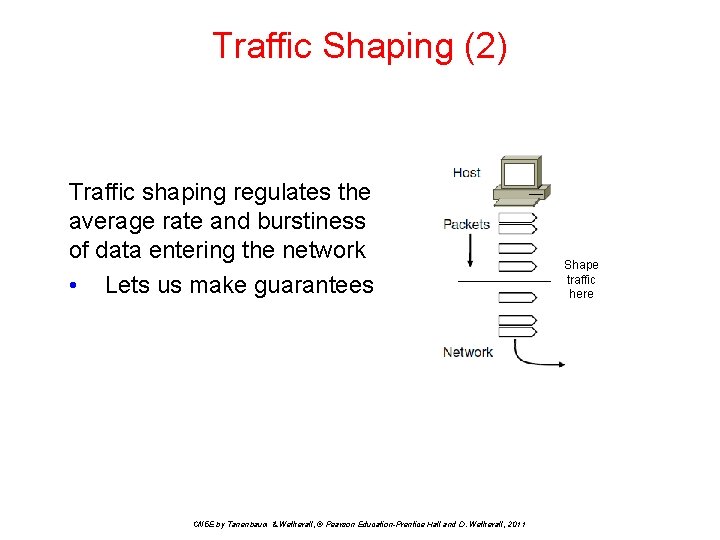
Traffic Shaping (2) Traffic shaping regulates the average rate and burstiness of data entering the network • Lets us make guarantees CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011 Shape traffic here

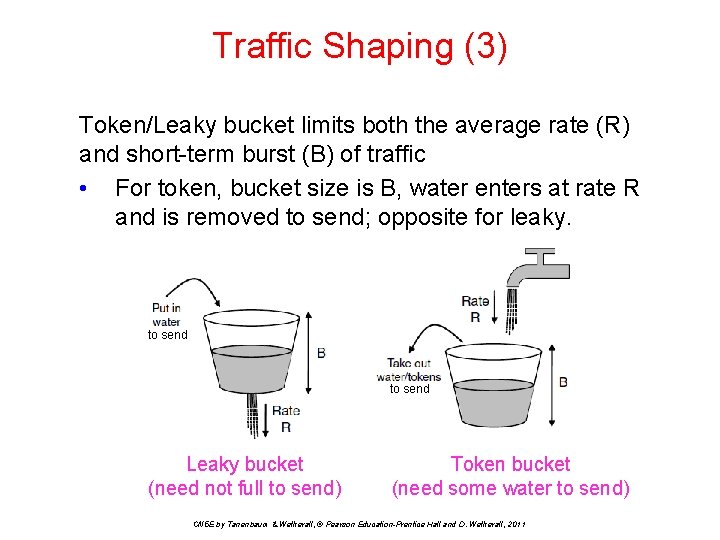
Traffic Shaping (3) Token/Leaky bucket limits both the average rate (R) and short-term burst (B) of traffic • For token, bucket size is B, water enters at rate R and is removed to send; opposite for leaky. to send Leaky bucket (need not full to send) Token bucket (need some water to send) CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

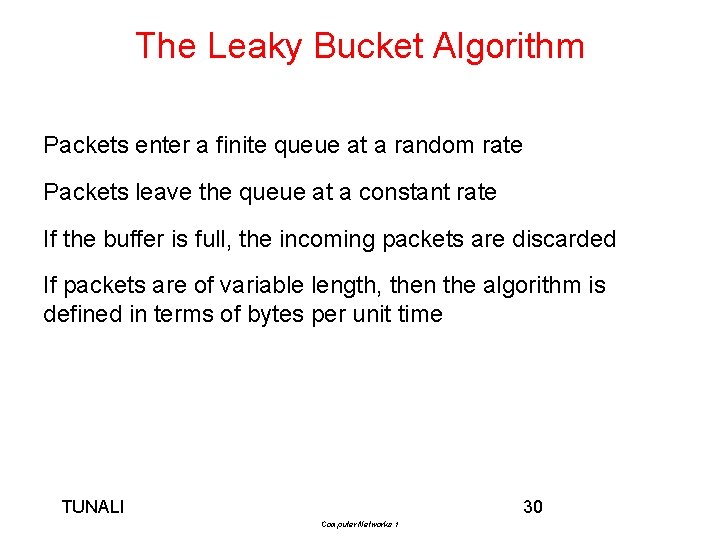
The Leaky Bucket Algorithm Packets enter a finite queue at a random rate Packets leave the queue at a constant rate If the buffer is full, the incoming packets are discarded If packets are of variable length, then the algorithm is defined in terms of bytes per unit time TUNALI 30 Computer Networks 1

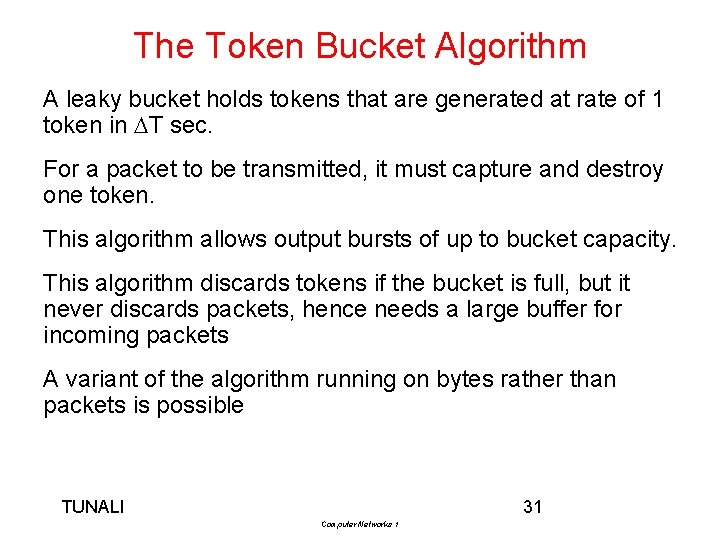
The Token Bucket Algorithm A leaky bucket holds tokens that are generated at rate of 1 token in T sec. For a packet to be transmitted, it must capture and destroy one token. This algorithm allows output bursts of up to bucket capacity. This algorithm discards tokens if the bucket is full, but it never discards packets, hence needs a large buffer for incoming packets A variant of the algorithm running on bytes rather than packets is possible TUNALI 31 Computer Networks 1

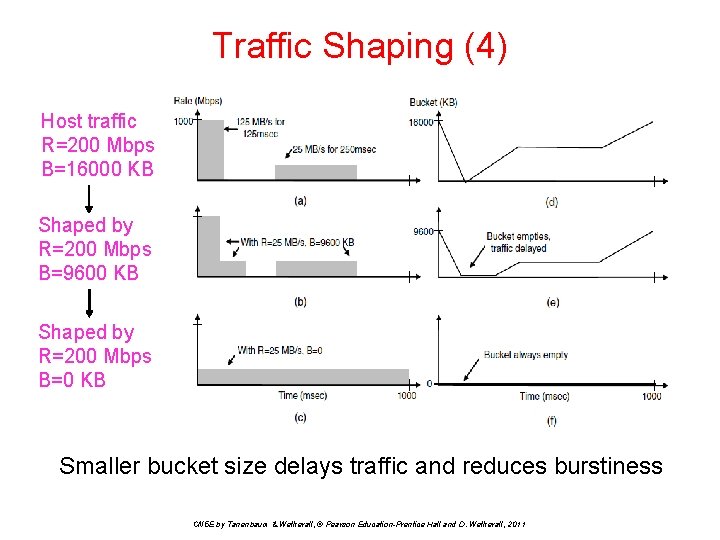
Traffic Shaping (4) Host traffic R=200 Mbps B=16000 KB Shaped by R=200 Mbps B=9600 KB Shaped by R=200 Mbps B=0 KB Smaller bucket size delays traffic and reduces burstiness CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

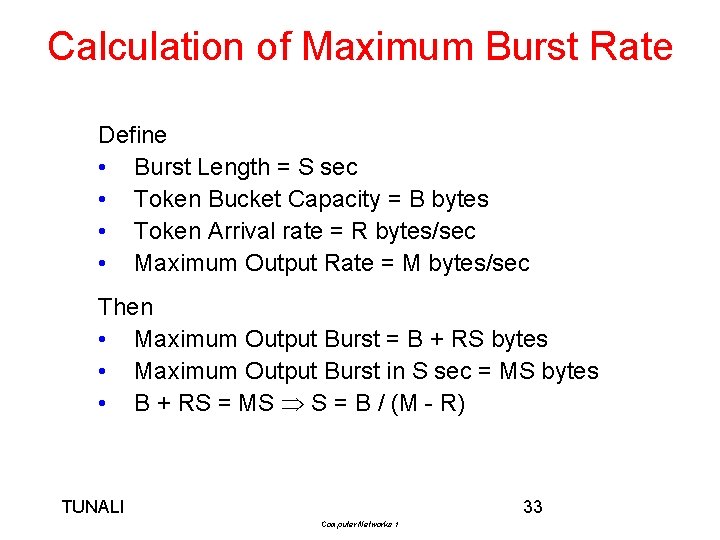
Calculation of Maximum Burst Rate Define • Burst Length = S sec • Token Bucket Capacity = B bytes • Token Arrival rate = R bytes/sec • Maximum Output Rate = M bytes/sec Then • Maximum Output Burst = B + RS bytes • Maximum Output Burst in S sec = MS bytes • B + RS = MS S = B / (M - R) TUNALI 33 Computer Networks 1

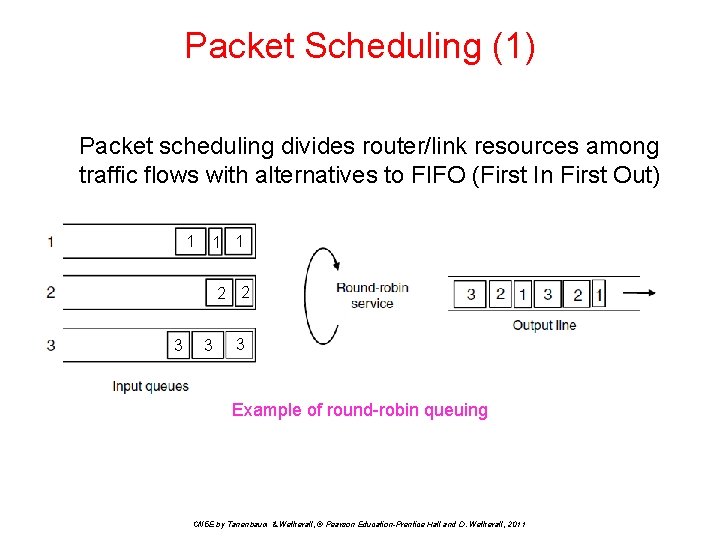
Packet Scheduling (1) Packet scheduling divides router/link resources among traffic flows with alternatives to FIFO (First In First Out) 1 1 1 2 2 3 3 3 Example of round-robin queuing CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Packet Scheduling (2) Resources reserved for different flows: Bandwidth Buffer space CPU cycles CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

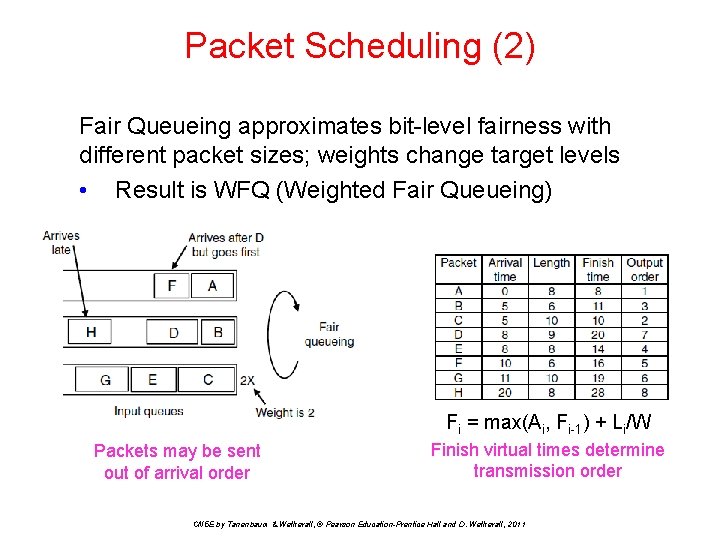
Packet Scheduling (2) Fair Queueing approximates bit-level fairness with different packet sizes; weights change target levels • Result is WFQ (Weighted Fair Queueing) Fi = max(Ai, Fi-1) + Li/W Packets may be sent out of arrival order Finish virtual times determine transmission order CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

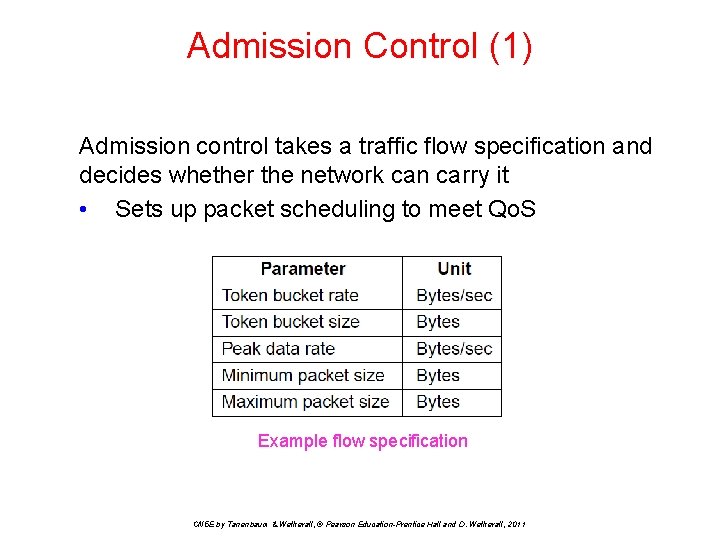
Admission Control (1) Admission control takes a traffic flow specification and decides whether the network can carry it • Sets up packet scheduling to meet Qo. S Example flow specification CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

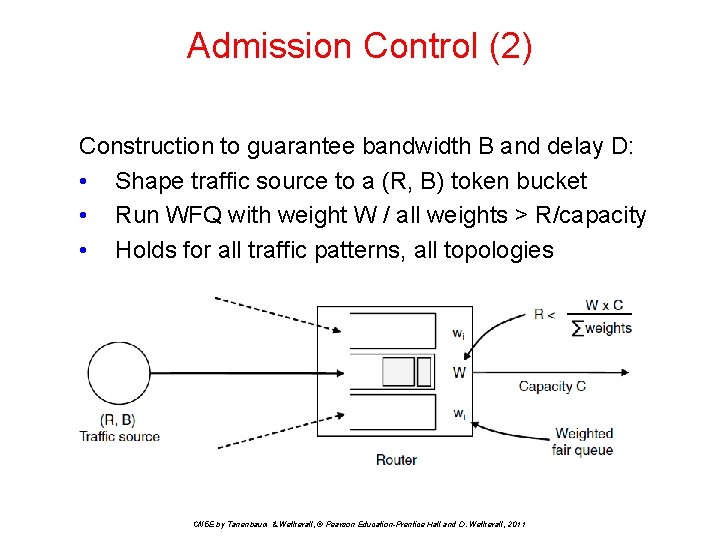
Admission Control (2) Construction to guarantee bandwidth B and delay D: • Shape traffic source to a (R, B) token bucket • Run WFQ with weight W / all weights > R/capacity • Holds for all traffic patterns, all topologies CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Integrated Services (1) Design with Qo. S for each flow; handles multicast traffic. Admission with RSVP (Resource re. Ser. Vation Protocol): • Receiver sends a request back to the sender • Each router along the way reserves resources • Routers merge multiple requests for same flow • Entire path is set up, or reservation not made CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

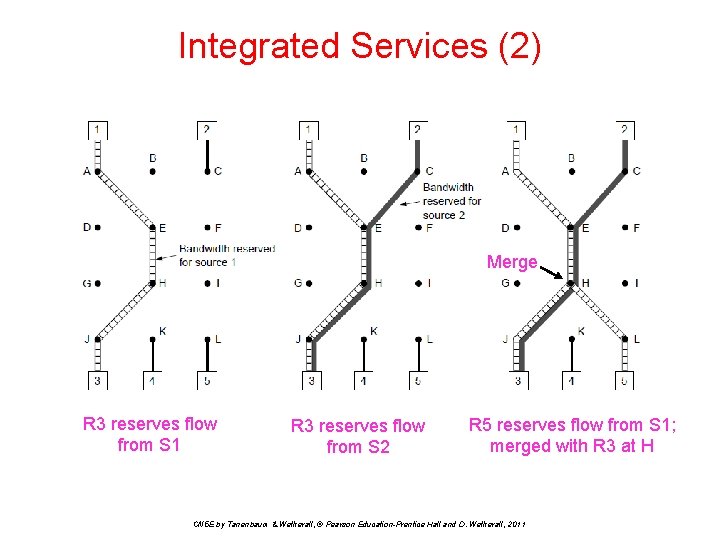
Integrated Services (2) Merge R 3 reserves flow from S 1 R 3 reserves flow from S 2 R 5 reserves flow from S 1; merged with R 3 at H CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

RSVP Resource Reservation Protocol Allows multiple senders to transmit to multiple groups of receivers Uses multicast routing with spanning trees Allows dynamic change of bandwidth Allows change of source once bandwidth is reserved TUNALI 41 Computer Networks 1

RSVP 2 Receivers send a reservation message up the tree to the sender Message propagates by reverse path forwarding At each hop, the router reserves the necessary bandwidth If there is no available bandwidth, it reports back failure By the time message arrives to the source, bandwidth has already been reserved TUNALI 42 Computer Networks 1

Differentiated Services Managing thousands of flows is a difficult task • Advance setup is required Differentiated services allow definition of a set of service classes Customers sign up for a particular class and receive the appropriate service No advance setup is required TUNALI 43 Computer Networks 1

Expedited Forwarding 1 Two classes of service are available • Regular • Expedited The routers could be programmed to have two output queues for each outgoing line to servive the above classes TUNALI 44 Computer Networks 1

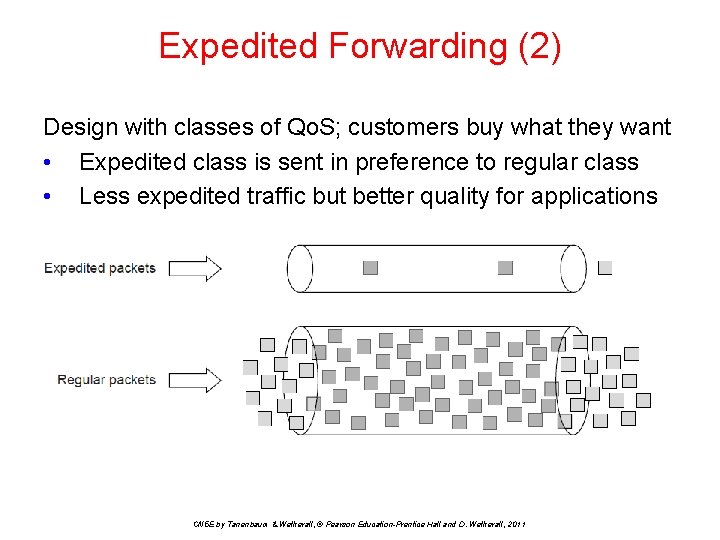
Expedited Forwarding (2) Design with classes of Qo. S; customers buy what they want • Expedited class is sent in preference to regular class • Less expedited traffic but better quality for applications CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Assured Forwarding 1 For priority classes each having its own resources For each class three discard probabilities are defined • Low • Medium • High TUNALI 46 Computer Networks 1

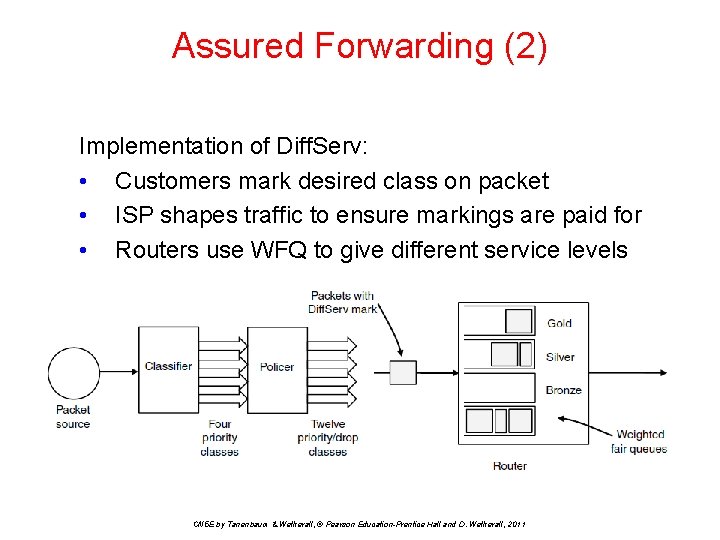
Assured Forwarding (2) Implementation of Diff. Serv: • Customers mark desired class on packet • ISP shapes traffic to ensure markings are paid for • Routers use WFQ to give different service levels CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Reading 5. 3 5. 4 CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011

Homework 13 (15) 16 Imagine a flow specification that has a maximum packet size of 1000 bytes, a token bucket rate of 10 million bytes/sec, a token bucket size of 1 million bytes and a maximum transmission rate of 50 million bytes/sec. How long can a burst at maximum speed last? 17 (20) CN 5 E by Tanenbaum & Wetherall, © Pearson Education-Prentice Hall and D. Wetherall, 2011