Network Detection and Response in an Encrypted World





















- Slides: 47

Network Detection and Response in an Encrypted World Steve Porcello Sales Engineer, Gigamon Insight

Agenda 1. Everything is encrypted 2. What’s a security practitioner to do? 3. Metadata! 4. Use Cases! Confidential and Proprietary. For Internal Use Only. © 2018 Gigamon. All rights reserved. 2

(Mostly) Everything is Encrypted

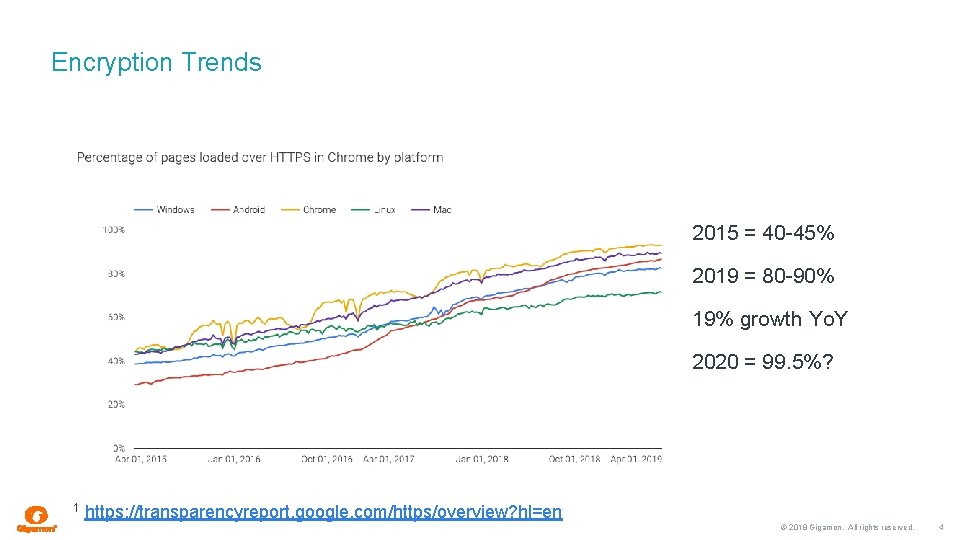
Encryption Trends 2015 = 40 -45% 2019 = 80 -90% 19% growth Yo. Y 2020 = 99. 5%? 1 https: //transparencyreport. google. com/https/overview? hl=en © 2018 Gigamon. All rights reserved. 4

Yay privacy …right? Attackers can encrypt stuff too Payloads C 2 channels Exfil / stolen goods APT laughs at your Suri/Snort rules © 2018 Gigamon. All rights reserved. 5

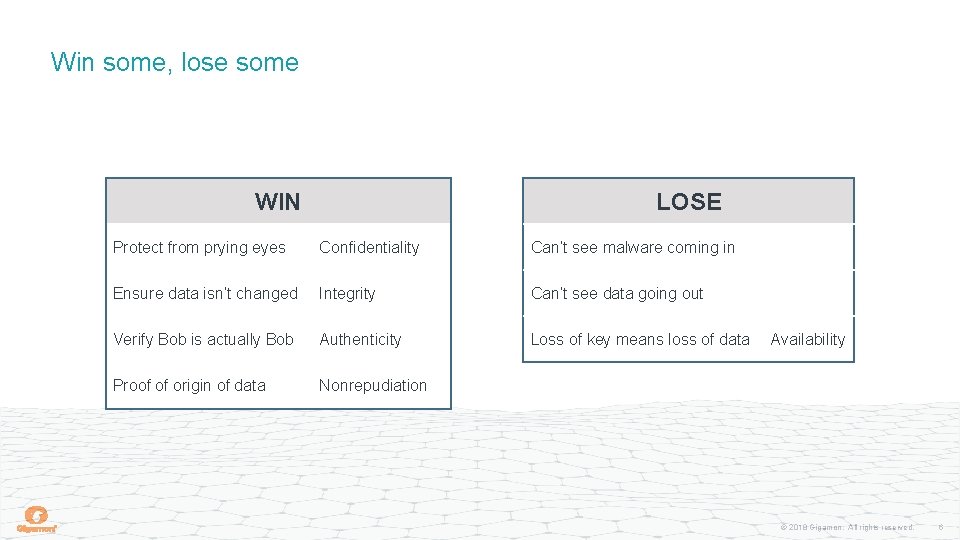
Win some, lose some LOSE WIN Protect from prying eyes Confidentiality Can’t see malware coming in Ensure data isn’t changed Integrity Can’t see data going out Verify Bob is actually Bob Authenticity Loss of key means loss of data Proof of origin of data Nonrepudiation Availability © 2018 Gigamon. All rights reserved. 6

So what’s a security practitioner to do? Analysis options

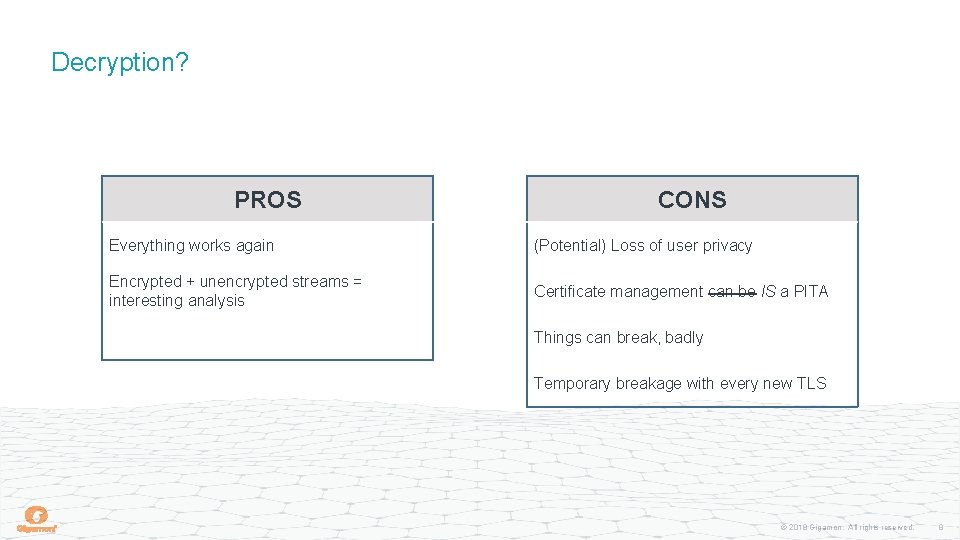
Decryption? PROS CONS Everything works again (Potential) Loss of user privacy Encrypted + unencrypted streams = interesting analysis Certificate management can be IS a PITA Things can break, badly Temporary breakage with every new TLS © 2018 Gigamon. All rights reserved. 8

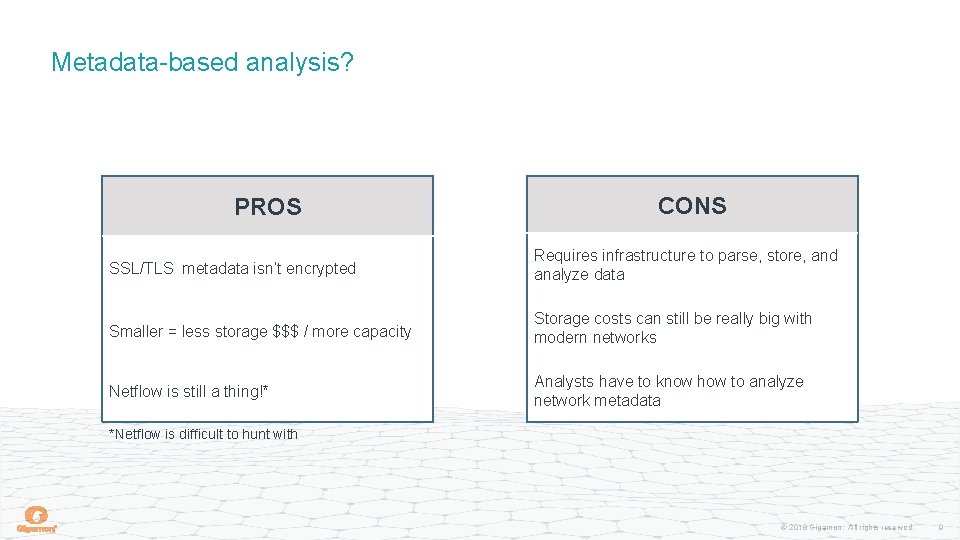
Metadata-based analysis? PROS CONS SSL/TLS metadata isn’t encrypted Requires infrastructure to parse, store, and analyze data Smaller = less storage $$$ / more capacity Storage costs can still be really big with modern networks Netflow is still a thing!* Analysts have to know how to analyze network metadata *Netflow is difficult to hunt with © 2018 Gigamon. All rights reserved. 9

Decrypt or Metadata, which one? Both! Metadata for HTTP + TLS Payload-level visibility and detection More data points == more analysis We know, we know… it’s hard Each has its own set of challenges – there is no easy or better answer The value of decryption / inspection is (hopefully) pretty clear Now let’s focus now on what you can do without decrypting © 2018 Gigamon. All rights reserved. 10

Analyzing TLS Metadata TLS 1. 3 Will Spoil Some of This!

TLS Metadata These fields can be parsed from TLS traffic using Bro Zeek Field Description version server’s choice of SSL/TLS cipher suite server’s choice of cipher suite SNI host / domain client wants server subject server certificate attributes server issuer attributes of the server cert issuer client subject client certificate attributes client issuer attributes of the client cert issuer ja 3 hash of Client Hello fields ja 3 s hash of Server Hello fields © 2018 Gigamon. All rights reserved. 12

TLS v 1. 3 Will Hinder Some of This

How is that metadata used? Our main use cases Detection Hunting Posture We’ll cover some examples later on… © 2018 Gigamon. All rights reserved. 14

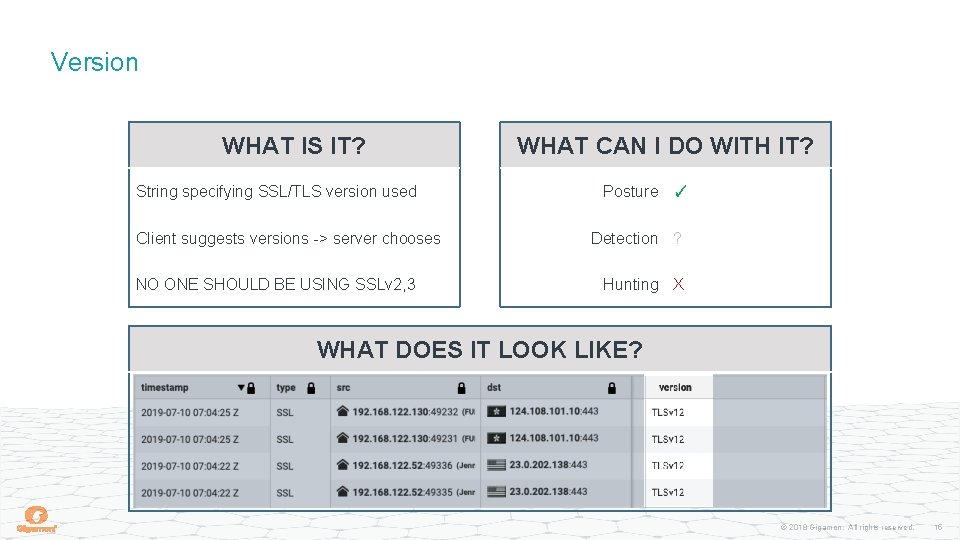
Version WHAT IS IT? String specifying SSL/TLS version used Client suggests versions -> server chooses NO ONE SHOULD BE USING SSLv 2, 3 WHAT CAN I DO WITH IT? Posture ✓ Detection ? Hunting X WHAT DOES IT LOOK LIKE? © 2018 Gigamon. All rights reserved. 15

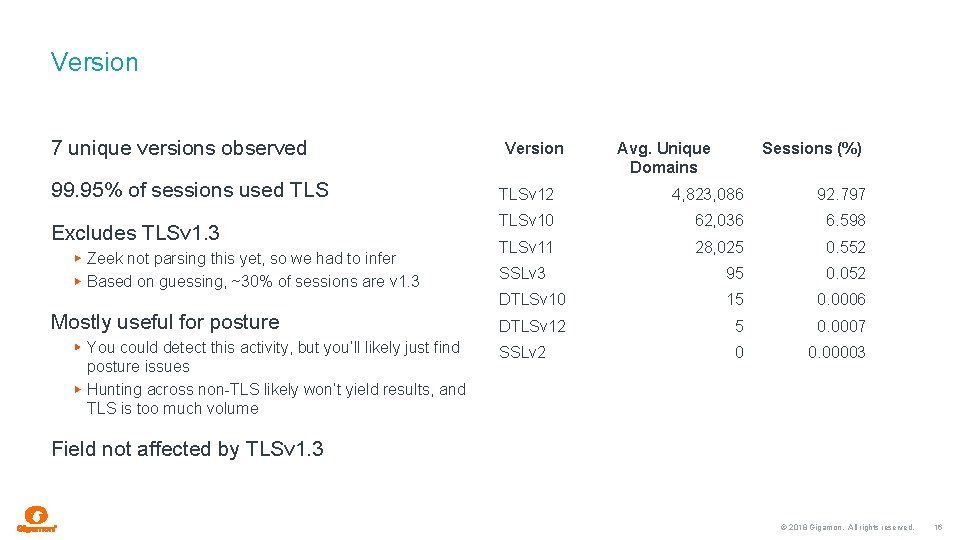
Version 7 unique versions observed 99. 95% of sessions used TLS Excludes TLSv 1. 3 Zeek not parsing this yet, so we had to infer Based on guessing, ~30% of sessions are v 1. 3 Mostly useful for posture You could detect this activity, but you’ll likely just find posture issues Hunting across non-TLS likely won’t yield results, and TLS is too much volume Version Avg. Unique Domains Sessions (%) TLSv 12 4, 823, 086 92. 797 TLSv 10 62, 036 6. 598 TLSv 11 28, 025 0. 552 SSLv 3 95 0. 052 DTLSv 10 15 0. 0006 DTLSv 12 5 0. 0007 SSLv 2 0 0. 00003 Field not affected by TLSv 1. 3 © 2018 Gigamon. All rights reserved. 16

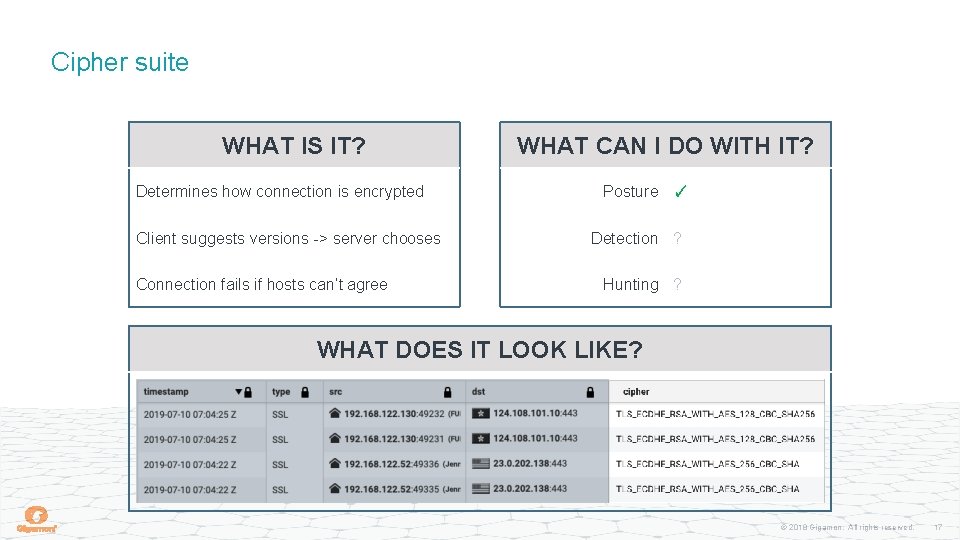
Cipher suite WHAT IS IT? Determines how connection is encrypted Client suggests versions -> server chooses Connection fails if hosts can’t agree WHAT CAN I DO WITH IT? Posture ✓ Detection ? Hunting ? WHAT DOES IT LOOK LIKE? © 2018 Gigamon. All rights reserved. 17

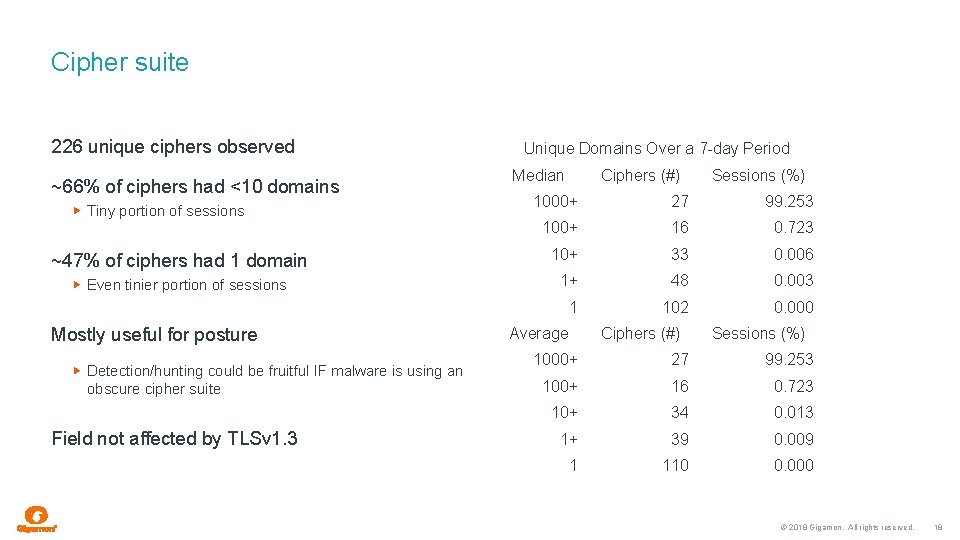
Cipher suite 226 unique ciphers observed ~66% of ciphers had <10 domains Tiny portion of sessions ~47% of ciphers had 1 domain Even tinier portion of sessions Mostly useful for posture Detection/hunting could be fruitful IF malware is using an obscure cipher suite Field not affected by TLSv 1. 3 Unique Domains Over a 7 -day Period Median Ciphers (#) Sessions (%) 1000+ 27 99. 253 100+ 16 0. 723 10+ 33 0. 006 1+ 48 0. 003 1 102 0. 000 Average Ciphers (#) Sessions (%) 1000+ 27 99. 253 100+ 16 0. 723 10+ 34 0. 013 1+ 39 0. 009 1 110 0. 000 © 2018 Gigamon. All rights reserved. 18

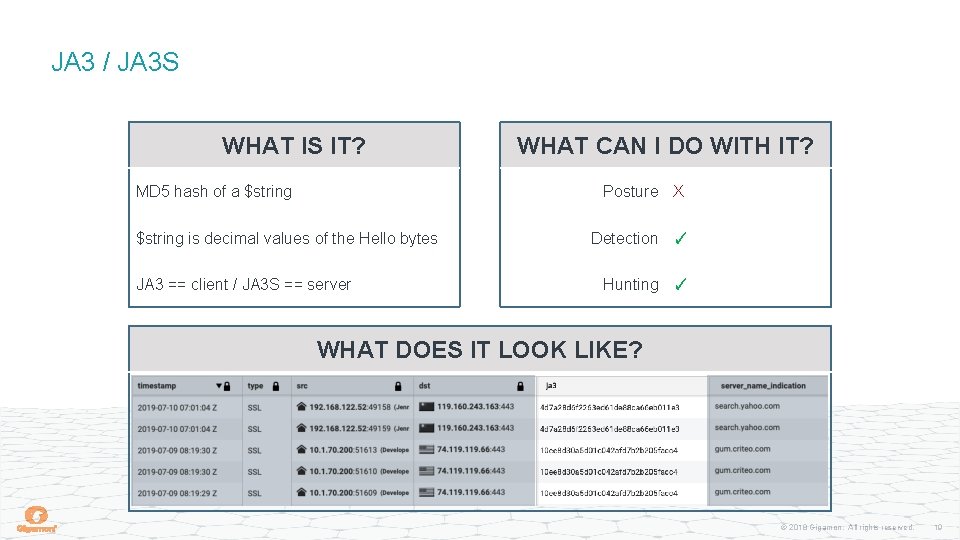
JA 3 / JA 3 S WHAT IS IT? MD 5 hash of a $string WHAT CAN I DO WITH IT? Posture X $string is decimal values of the Hello bytes JA 3 == client / JA 3 S == server Detection ✓ Hunting ✓ WHAT DOES IT LOOK LIKE? © 2018 Gigamon. All rights reserved. 19

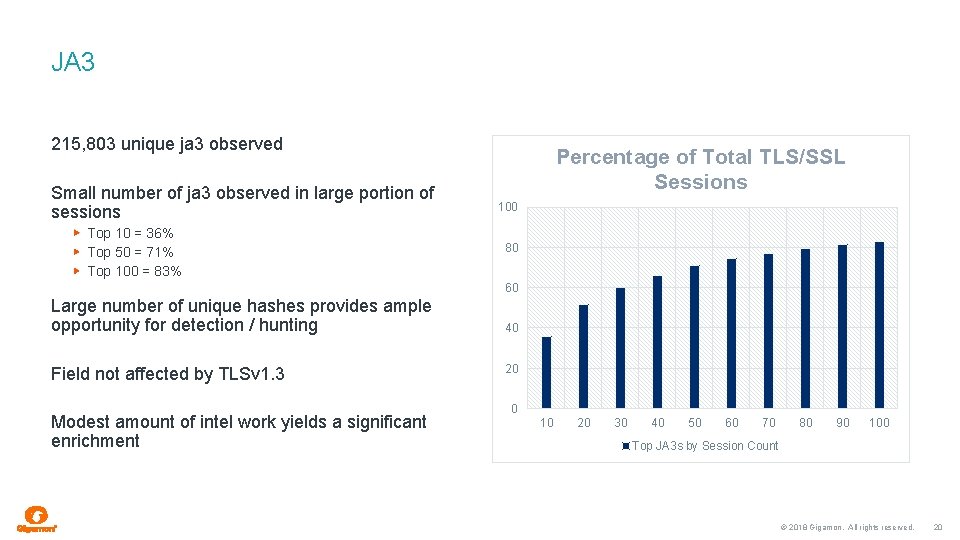
JA 3 215, 803 unique ja 3 observed Small number of ja 3 observed in large portion of sessions Top 10 = 36% Top 50 = 71% Top 100 = 83% Percentage of Total TLS/SSL Sessions 100 80 60 Large number of unique hashes provides ample opportunity for detection / hunting Field not affected by TLSv 1. 3 Modest amount of intel work yields a significant enrichment 40 20 0 10 20 30 40 50 60 70 80 90 100 Top JA 3 s by Session Count © 2018 Gigamon. All rights reserved. 20

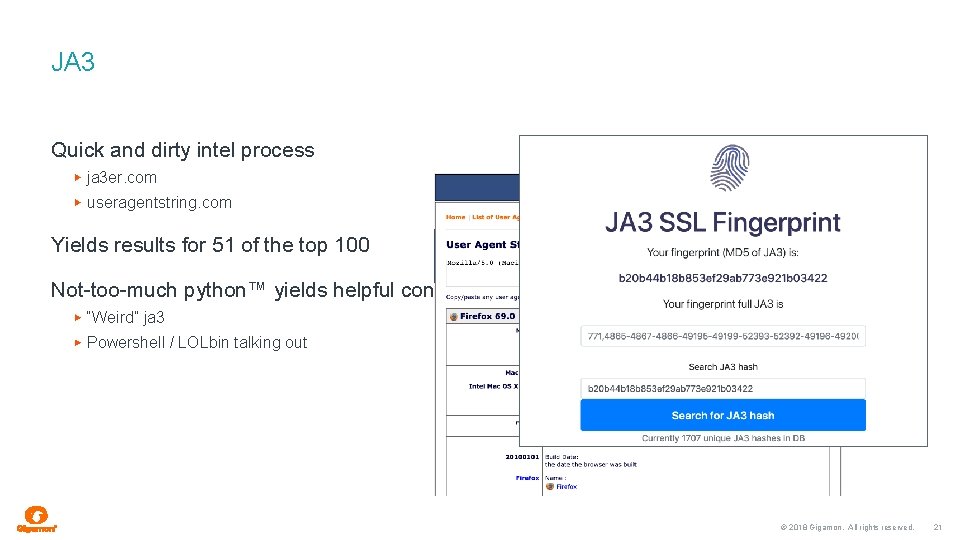
JA 3 Quick and dirty intel process ja 3 er. com useragentstring. com Yields results for 51 of the top 100 Not-too-much python™ yields helpful context “Weird” ja 3 Powershell / LOLbin talking out © 2018 Gigamon. All rights reserved. 21

JA 3 S 424 unique ja 3 s observed ~69% of ja 3 s had <10 domains Unique Domains Over a 7 -day Period Median JA 3 S (#) Sessions (%) 1000+ 47 99. 142 100+ 37 0. 779 ~40% of ja 3 s had 1 domain 10+ 46 0. 038 Even tinier portion of sessions 1+ 145 0. 038 1 149 0. 003 Tiny portion of sessions Very similar numbers to cipher suite Likely because JA 3 S is a fingerprint for the underlying software, which is likely to choose the same cipher suite consistently Same use case as cipher suite – posture Field not affected by TLSv 1. 3 Average JA 3 S (#) Sessions (%) 1000+ 47 99. 142 100+ 37 0. 779 10+ 46 0. 038 1+ 119 0. 038 1 175 0. 003 © 2018 Gigamon. All rights reserved. 22

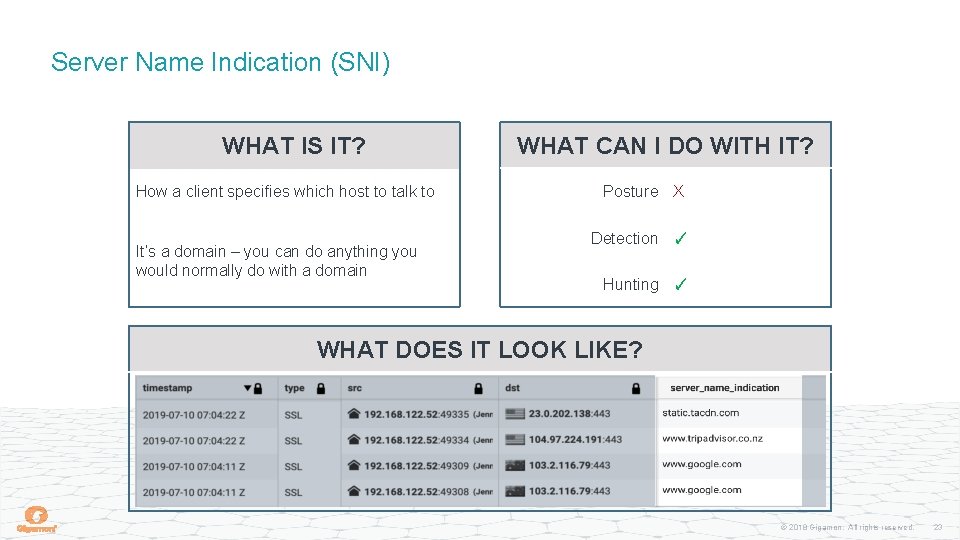
Server Name Indication (SNI) WHAT IS IT? How a client specifies which host to talk to It’s a domain – you can do anything you would normally do with a domain WHAT CAN I DO WITH IT? Posture X Detection ✓ Hunting ✓ WHAT DOES IT LOOK LIKE? © 2018 Gigamon. All rights reserved. 23

SNI + TLS 1. 3 SNI was always an optional extension – common, but optional TLS 1. 3 gives the option to encrypt the SNI Via DNS (it’s always DNS) This is why the certs are encrypted © 2018 Gigamon. All rights reserved. 24

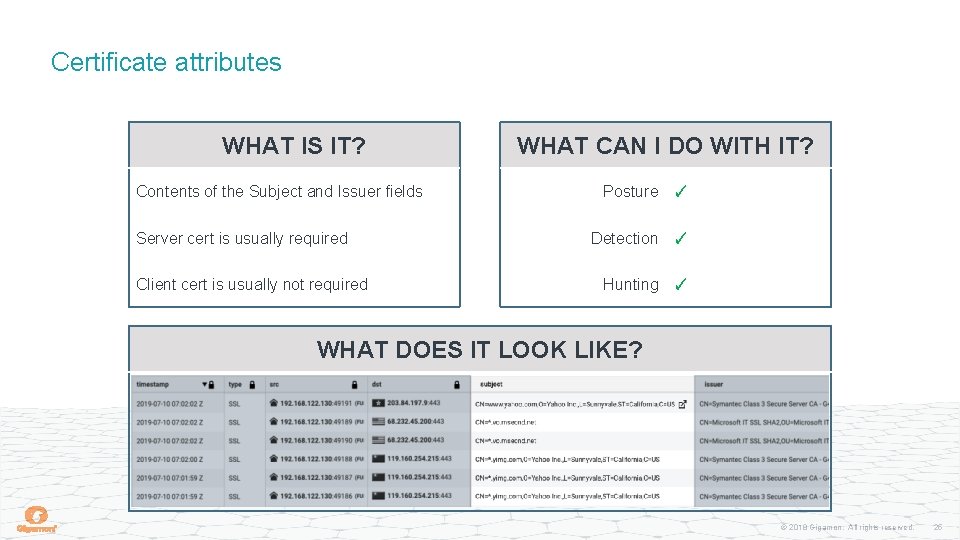
Certificate attributes WHAT IS IT? Contents of the Subject and Issuer fields Server cert is usually required Client cert is usually not required WHAT CAN I DO WITH IT? Posture ✓ Detection ✓ Hunting ✓ WHAT DOES IT LOOK LIKE? © 2018 Gigamon. All rights reserved. 25

Certificate attributes in TLSv 1. 3 There are many use cases for certificate attributes – naturally, this means TLSv 1. 3 will be taking them away Why encrypt the certificates? Same reasons as SNI, namely privacy Not encrypting the certificates would nullify encrypting the SNI © 2018 Gigamon. All rights reserved. 26

Use Cases Metadata analysis examples

Use Cases! We talked about using metadata in three use categories Detection Hunting Posture The next few slides will explore use cases for each © 2018 Gigamon. All rights reserved. 28

Detection Best applies to tracking known compromises Careful with lists of “OSINT” Is the value unique / uncommon If yes, detect! If no, false-positives galore! Upside: JA 3/cipher suites focus on how instead of who © 2018 Gigamon. All rights reserved. 29

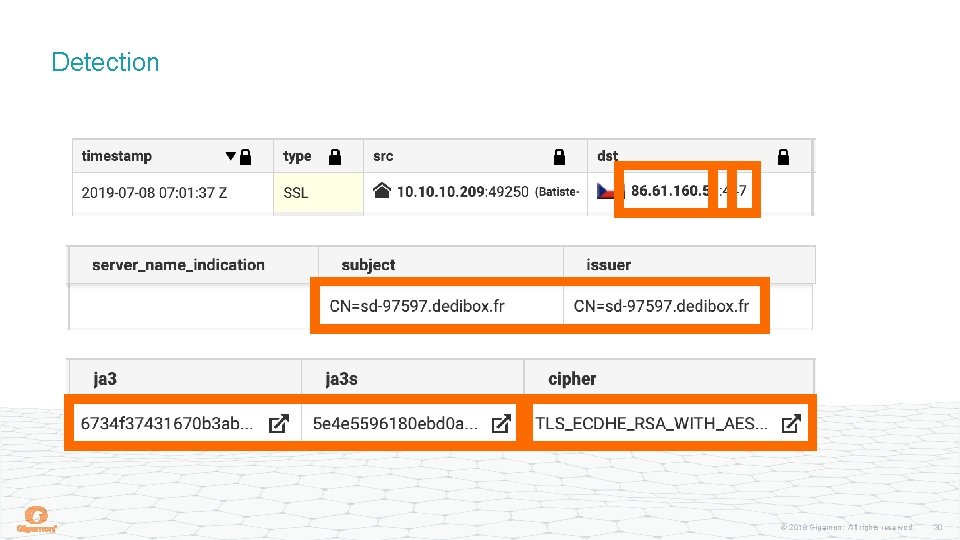
Detection © 2018 Gigamon. All rights reserved. 30

Detection Green. Cat Detection on HTTP fields Known User. Agents Specific URI patterns Would require decrypted HTTP proxy traffic © 2018 Gigamon. All rights reserved. 31

Detection Mack. Truck / Roadhouse Detection on SSL/TLS fields Specific subject Specific issuer Specific certificate SHA 1 Specific certificate serial number Detection on encrypted traffic �� © 2018 Gigamon. All rights reserved. 32

Detection Powershell is able to establish encrypted sessions Attackers / red-teamers commonly stand up infrastructure with Let’s Encrypt certificates Powershell has a unique JA 3 hash Detection on encrypted traffic �� © 2018 Gigamon. All rights reserved. 33

Detection Reductor Kaspersky recently published research on Reductor / COMpfun https: //securelist. com/compfun-successor-reductor/93633/ Watermarks the TLS handshake by subverting the browser’s PRNG BUT, the certificate has a unique SHA 1 hash Detection on encrypted traffic �� © 2018 Gigamon. All rights reserved. 34

Hunting The purpose of hunting is to find things you didn’t know about Typically looking for attackers / compromises Who are we interacting with? How are we interacting with them? May (probably will) uncover some security posture / hygiene issues © 2018 Gigamon. All rights reserved. 35

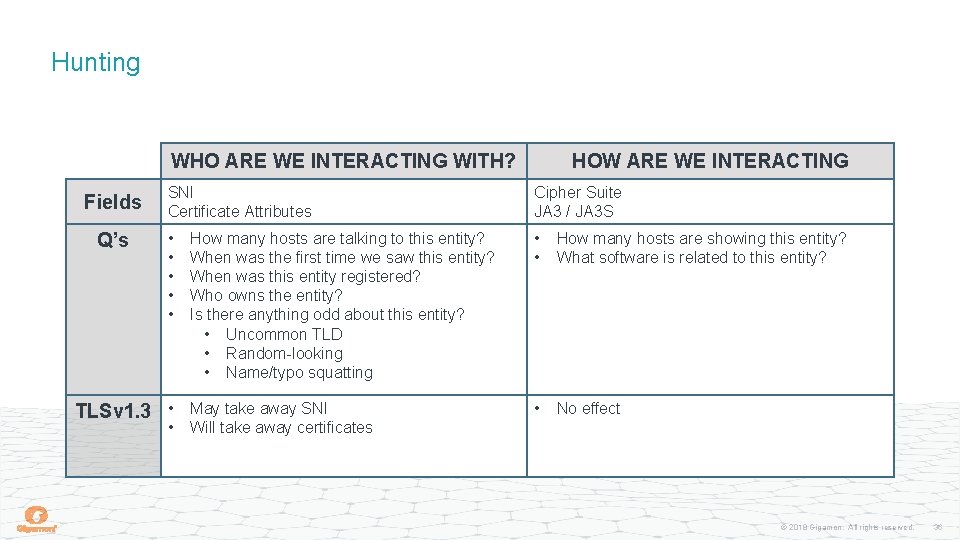
Hunting WHO ARE WE INTERACTING WITH? Fields Q’s HOW ARE WE INTERACTING SNI Certificate Attributes Cipher Suite JA 3 / JA 3 S • • • How many hosts are talking to this entity? When was the first time we saw this entity? When was this entity registered? Who owns the entity? Is there anything odd about this entity? • Uncommon TLD • Random-looking • Name/typo squatting • • How many hosts are showing this entity? What software is related to this entity? May take away SNI Will take away certificates • No effect TLSv 1. 3 • • © 2018 Gigamon. All rights reserved. 36

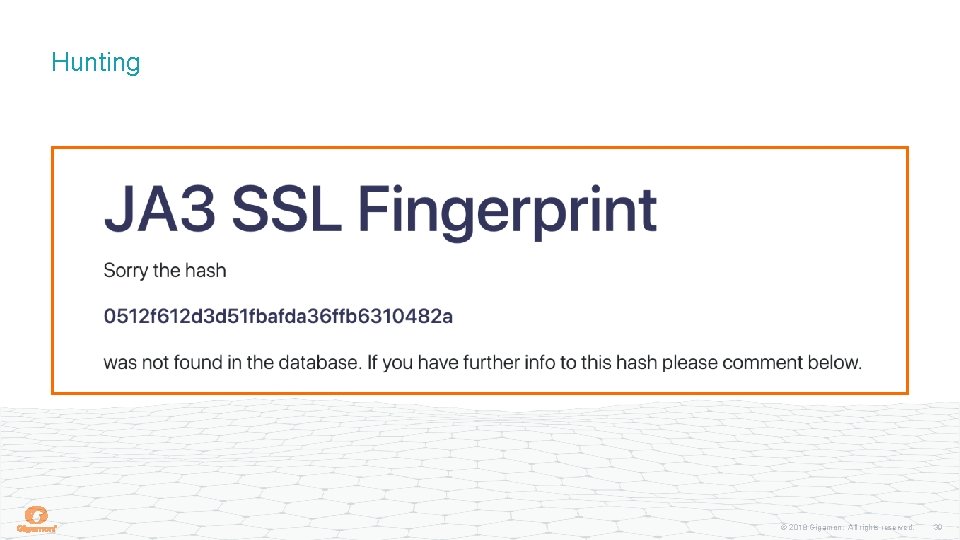
Hunting © 2018 Gigamon. All rights reserved. 37

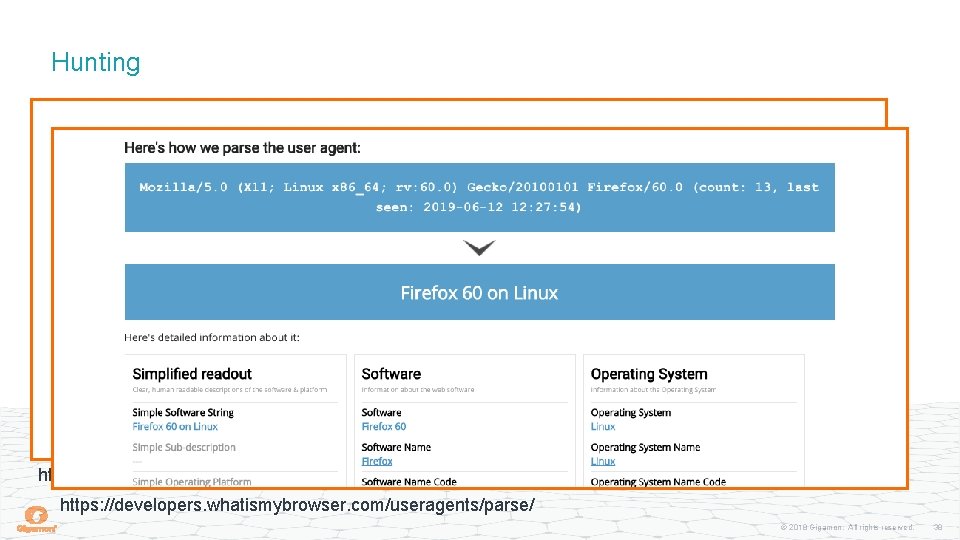
Hunting https: //ja 3 er. com/form https: //developers. whatismybrowser. com/useragents/parse/ © 2018 Gigamon. All rights reserved. 38

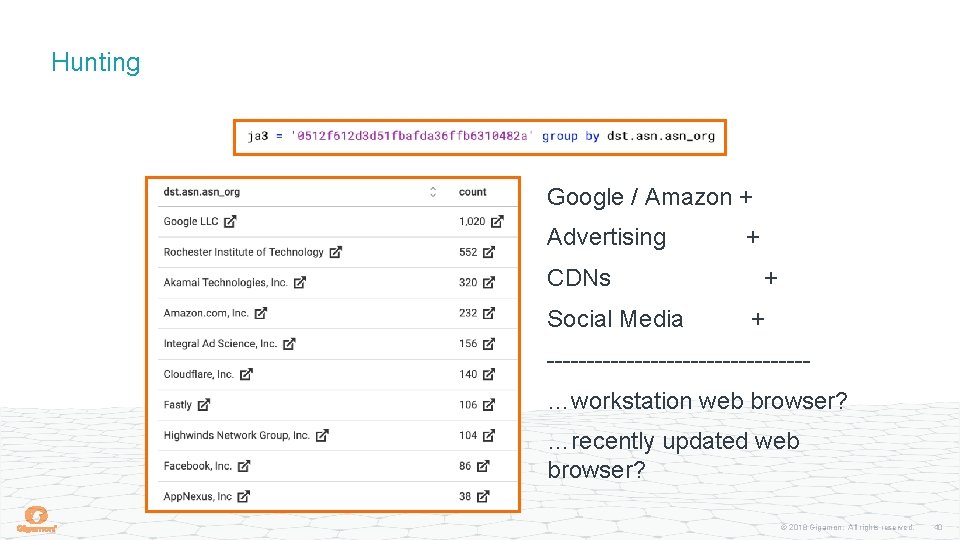
Hunting © 2018 Gigamon. All rights reserved. 39

Hunting Google / Amazon + Advertising CDNs Social Media + + + ----------------…workstation web browser? …recently updated web browser? © 2018 Gigamon. All rights reserved. 40

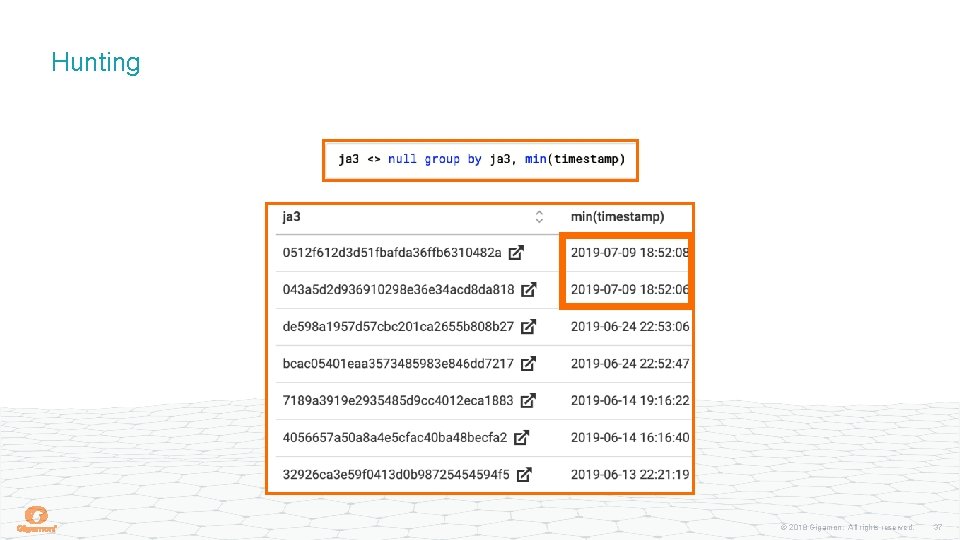
Hunting Recap Quick look at new JA 3 hashes Only covered 30 days of data We could have seen those hashes 40 days ago Better way: Intel team tracks all observed JA 3 hashes and alerts on hashes never seen before Software updates = new hashes (maybe) Prevalence is important Same could be done for certificates / domains © 2018 Gigamon. All rights reserved. 41

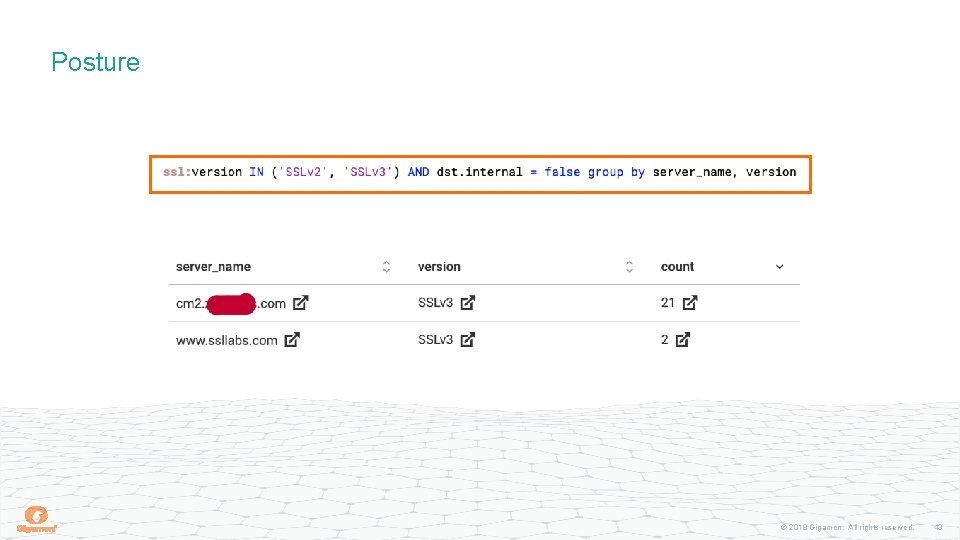
Posture No one should be using any version of SSL Do you have internal systems that support it? Do you have externally-facing systems that support it? Do any of your vendors support it? Could also look at deprecated cipher suites © 2018 Gigamon. All rights reserved. 42

Posture © 2018 Gigamon. All rights reserved. 43

Takeaways Encryption is here to stay Decryption + metadata is ideal, both have pros/cons There is plenty of analysis to be done on TLS metadata TLS v 1. 3 will hinder analysis on the who But, it won’t hinder the how, which is arguably better anyway But there will still be plenty of analysis to do! © 2018 Gigamon. All rights reserved. 44

To schedule a 30 -minute Web. Ex demo Please reach out to Ernie Mitchell (ernie. mitchell@gigamon. com) or Justin Kohler (justin. kohler@gigamon. com) For more information - https: //www. gigamon. com/products/detect-respond/gigamonthreatinsight. html © 2018 Gigamon. All rights reserved. 45

Thank you © 2018 Gigamon. All rights reserved. 46

Questions? © 2018 Gigamon. All rights reserved. 47