Network Based File Carving OR I know what

Network Based File Carving OR I know what you downloaded last night! By: GTKlondike

Who Am I? Oh hey, that guy…

I Am… �Hacker/independent security researcher/subspace halfninja �Several years of experience in network infrastructure and security consulting as well as systems administration (Routing, Switching, Firewalls, Servers) �Passionate about networking �I’m friendly, just come up and say hi Contact Info: �Email: gtklondike@gmail. com �Zombie-Blog: gtknetrunner. blogspot. com

What should you know already? �Assumed basic knowledge of: �Protocol analyzers (Wireshark/TCPdump) �OSI and TCP/IP model �Major protocols (I. e. DNS, HTTP(s), TCP, UDP, DHCP, ARP, IP, etc. )

Tools I Will Be Using �Wireshark �Network Miner �Hex editor �Scalpel �File Signature Database http: //www. garykessler. net/library/file_sigs. html

What Is File Carving? �It’s a word search on steroids!

Pcap Analysis Methodology 1. Pattern Matching – Identify and filter packets of interest by matching specific values or protocol meta-data 2. List Conversations – List all conversation streams within the filtered packet capture 3. Export - Isolate and export specific conversation streams of interest 4. Draw Conclusions – Extract files or data from streams and compile data
Demo Time! Yeah…. Security Onion: /opt/samples/fake_av. pcap
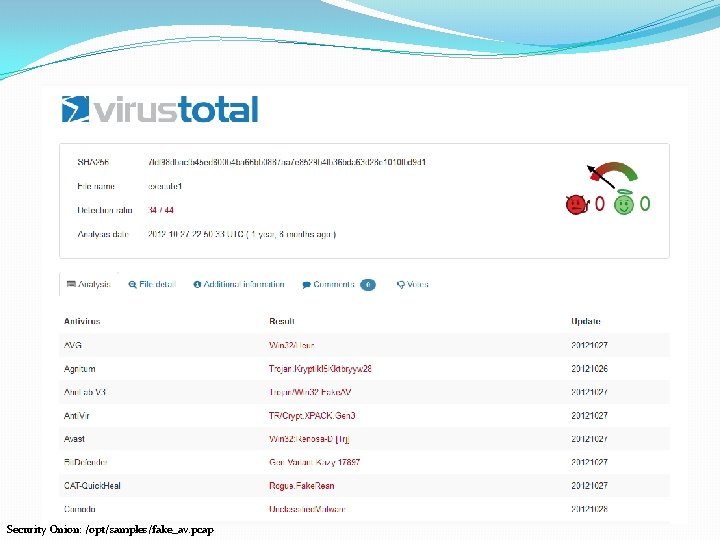
Security Onion: /opt/samples/fake_av. pcap

Security Onion: /opt/samples/fake_av. pcap

Additional Information (Pcap Files) �http: //www. netresec. com/? page=Pcap. Files �http: //forensicscontest. com/puzzles �http: //www. honeynet. org/node/504 �https: //www. evilfingers. com/repository/pcaps. php �http: //code. google. com/p/security-onion/wiki/Pcaps

Further Reading �Network-Based File Carving �http: //blogs. cisco. com/security/network-based-file-carving/ �Practical Packet Analysis: Using Wireshark to Solve Real. World Network Problems �By: Chris Sanders �Network Forensics: Tracking Hackers Through Cyberspace �By: Sherri Davidoff, Jonathan Ham �Guide to Integrating Forensic Techniques into Incident Response �http: //csrc. nist. gov/publications/nistpubs/800 -86/SP 800 - 86. pdf �File Signatures �http: //www. garykessler. net/library/file_sigs. html
- Slides: 12