Network Architecture NETWORK ARCHITECTURE PROTOCOLS STANDARD ORGANIZATIONS ISO









- Slides: 22

Network Architecture • • • NETWORK ARCHITECTURE PROTOCOLS STANDARD ORGANIZATIONS ISO OSI REFERENCE MODEL PHYSICAL LAYER DATA LINK LAYER NETWORK LAYER TRANSPORT LAYER SESSION LAYER PRESENTATION LAYER APPLICATION LAYER

Network Architecture • The term architecture means the formation of a structure, or an orderly, interconnected, complex arrangement of parts. • An architecture encompasses hardware, software, data link controls, standards, topologies, and protocols.

Protocols • The term protocol defines how network components establish communications, exchange data, and terminate communications. • Protocols are sets of rules and agreements; just as a diplomatic protocol defines the rules for social parlance. • Modern networks are implemented using the concept of layered protocols. • The OSI model was created in an attempt to unify direct network development, but many protocols were already in use (and quite popular) before the OSI model was developed.

Protocol • Since these existing networks were already functional, compliance with the model necessitated retrofitting. • Some vendors did this; some did not. Many are still working on the problem. • Although the introduction of the layered protocol did have a profound influence on newer protocols, the collection of protocols available today includes some that conform well to the OSI and some that do not.

Standards • We have seen that the world of protocols is somewhat messy. • Today's protocols demonstrate various degrees of conformance to the OSI model. • As many protocols exist, the standard organizations have to do something. In the context of networking, some protocols are standards. • For example, TCP/IP is the Department of Defense Standards. • This means that the Department of Defense has legislated the use of these standards in their environments. • Legislated standards are often referred to as de jure (by law) standards.

Standard • Standards that come into common use, or because everybody decides that they are good ideas, are called de facto (by fact) standards. • TCP/IP and related protocols are also de facto standards by virtue of their widespread commercial and educational use. • IBM's System Network Architecture (SNA), which defines how computers and terminals and printers can talk to each other, is an example of de facto standard. • MS-DOS 6. x, Novell's Net. Ware de facto standards because they hold important positions in the market.

De jure and de facto • In addition to the issue of de facto, de jure is the question of whether a standard is proprietary. • Proprietary standards are those that are invented and controlled by a single, private commercial organization. • Examples are SNA from IBM, DECnet from Digital and Net. Ware from Novell. • Standards developed by standard bodies and other committees are non-proprietary. • Examples include TCP/IP, IEEE 802. 3, and OSI protocols

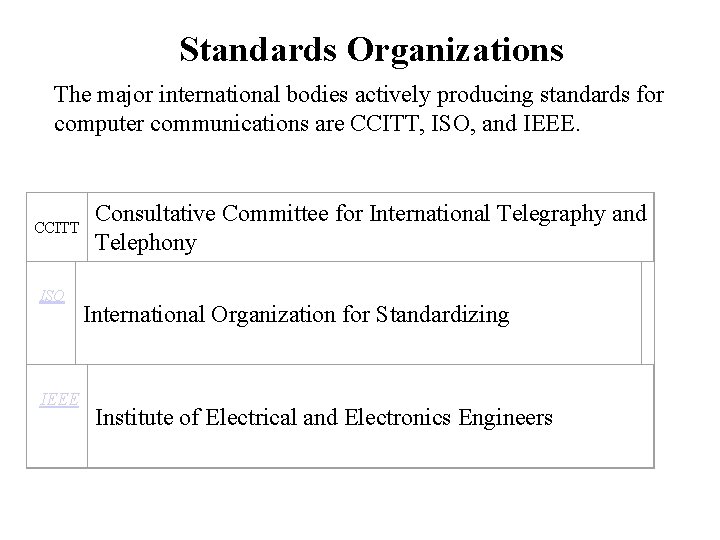
Standards Organizations The major international bodies actively producing standards for computer communications are CCITT, ISO, and IEEE. CCITT ISO IEEE Consultative Committee for International Telegraphy and Telephony International Organization for Standardizing Institute of Electrical and Electronics Engineers

CCITT & ISO • CCITT is the best-known standard organization in the world of telecommunications. • CCITT makes technical recommendations on telegraphy, telephone, and data communication interfaces. • One popular CCITT standard is V. 24 in Europe (which is the RS-232 -C standard in North America) • ISO is an international standard organization that defines and develops standards on vast variety of topics. i. e Networking. • The OSI protocols are well-known ISO standards.

IEEE • The IEEE is the largest professional organization in the world. • It sponsors a group that develops computing and electrical engineering standards. • The widely used IEEE 802 networking series of standards are examples of IEEE products. • • • IEEE 802. 3 Ethernet (CSMA/CD) IEEE 802. 4 Token bus IEEE 802. 5 Token ring IEEE 802. 6 MAN IEEE 802. 7 Broadband CATV IEEE 802. 8 Fiber-Optics

OSI Reference Model • In the network world today (and the next decade), the OSI RM is one of the most powerful architecture in use. • It provides a complete model of the functions of communications system so that two computers using OSI RM would be able to communicate, even if they were based on different hardware and software platforms. • So, do all people use the OSI model? • The answer is some do and some don't. • OSI does not fit everyone's needs and it isn't available on all manufacturer's computers. • Conformance refers to meeting the standards. • Conformance testing is the way conformance is established. • The conformance testing process is complicated and expensive.

OSI reference Model • Different computer platforms exist, different networking products on the rise, networking is pervasive, so governments must do something. • They decided to select this model and issue a Government OSI Profile, usually called a GOSIP. • This means that if a vendor wants to sell communications system to, for example, U. S. , UK. French, or German government department, the vendor must adhere to the parts of OSI model specified by the country's GOSIP specification. • This is very important because it helps ensure that the communication systems from any vendor will communicate with products from any other vendor.

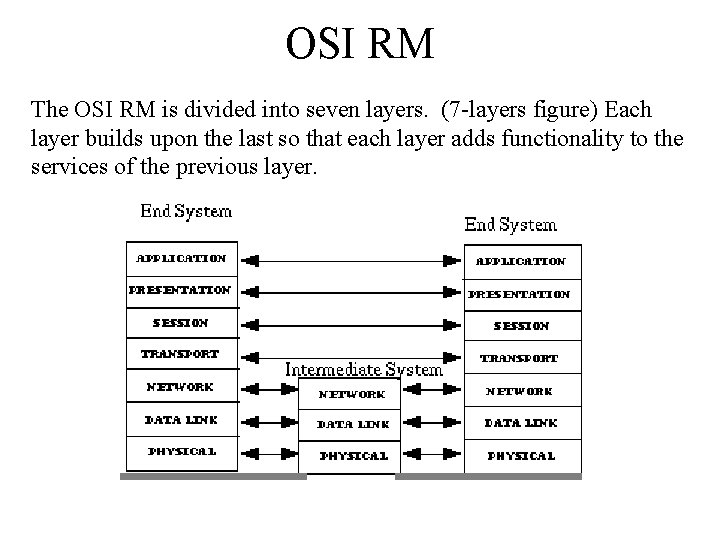
OSI RM The OSI RM is divided into seven layers. (7 -layers figure) Each layer builds upon the last so that each layer adds functionality to the services of the previous layer.

OSI RM • The important thing about the OSI RM is that it doesn't actually say how the layers will be built--it doesn't care what goes inside them, it concentrates on how the layers work with each other. • It means that the model is concerned with communication (the structure of passing messages) rather than implementation (what passes the messages). • Building a complex communication system in a structured way, means if you have to make changes after you have built your system well, you only have to change the details in a layer instead of redesigning the entire system.

Physical layer • The purpose of the physical layer is to deliver data from one computer to another. • Specifically, the physical layer translates bits of data into a format suitable for transmission or receives a transmission and translates it back into bits. • This layer sees all data as a stream of bits. • There are four areas covered by the physical layer: ØElectrical: what voltages and currents are used. ØMechanical: the physical shape and size of the connectors. ØFunctional: the significance of a connector pin and the voltage on that pin. ØProcedural: the sequence of functional changes that indicate event occurrences.

Physical layer • A very important concept to remember is that the physical layer is not the same as the physical media (the wires that connect the computers are not part of the physical layer). • Conceptually, they sit below the physical layer, and they aren't part of the physical layer specification. It is a network dependant layer.

Data Link layer • Responsible for the reliable transfer of information across the physical link. • Sends blocks of data (frames) with the necessary synchronization, flow control and error control. • It is a network dependant layer.

Network layer • Provides upper layers with independence from the data transmission and switching technologies used to connect systems. • Responsible for establishing, maintaining and the routing of data between addresses, assembling incoming frames into blocks of data and segmenting blocks of data to be sent into frames, and terminating connections. • A network dependant layer.

Transport Layer • Network independent layer. • It has three major functions that support the transparent transfer of data to and from the session layer above it: Ø Provides reliable transfer of data between end points. Ø Provides end-to-end error recovery and flow control Ø Releasing the connection. The reason for this apparent duplication of effort is that the data link layer deals with only a single, direct link, whereas the transport layer deals with a chain of network nodes and links.

Session layer • The session layer provides the mechanism for controlling the dialogue between the two end systems. • Example FTP session with discipline of half-duplex, TALK is also Full-duplex.

Presentation layer • The presentation layer defines the format of the data to be exchanged between applications. • Offers application programs a set of data transformation (presentation, syntax) services, such as graphics, binary or ASCII data. Data compression or data encryption could occur at this level.

Application layer • This layer provides support for the applications (processes) that use the Network. • Example: telnet grail. cba. csuohio. edu, the telnet process needs help from the application layer to resolve grail. cba. csuohio. edu into an address to pass it down the stack. • The Application layer has a function to go after some sort of name resolution procedure to service the telnet process. and so on, for other processes like FTP, http, and e-mail.