Network and System Security Risk Assessment Firewall Review












- Slides: 44

Network and System Security Risk Assessment Firewall

Review n n Last week, we have talked about sniffer and firewall Sometimes, sniffer can sniff users’ private information q q n http, telnet…. Wireshark sniffing on the network Firewall can control a computer/network communication q Iptables, ufw

Review n Stateful firewall q Traditional: to allow outgoing website visiting and to drop other communication n n q To allow input tcp with source port 80 and ack Can’t visit websites on ports other than 80 To use stateful firewall n State tracking

Review n Iptables examples q Disable to be pinged, enable to ping q To limit the number of pings q To change the source IP of a ping packet sent out from our machine

Review n Iptables Examples q q q Prevent a machine from telneting to other machines Prevent a telnet server from being connected by other machines Prevent inner network from connecting a social network

Review n Iptables example q To force redirect n n 1. to change the output packet to a specific website 2. to change the incoming packet to a specific server or port

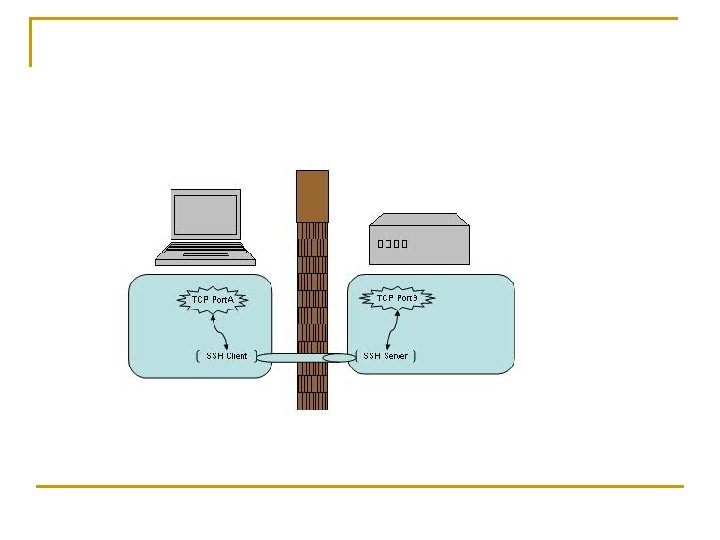
Review n Iptables example q q q the secure version of telnet: ssh Besides encryption, ssh has another function: port forwarding Using ssh port forwarding, firewall rules can be bypassed


Review n n Iptables example ftp server: only allows localhost ftp service q q q Also demonstrate ftp data and control connections On the server, ftp is blocked On the client, we try to do ssh port forwarding

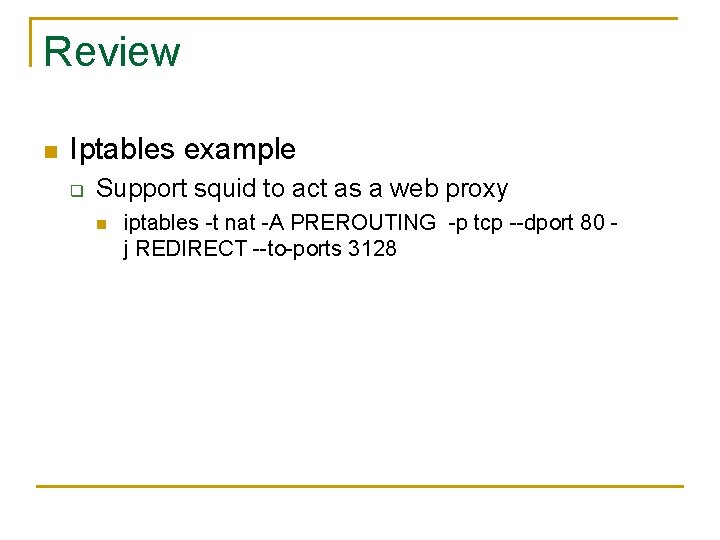
Review n Iptables example q Support squid to act as a web proxy n iptables -t nat -A PREROUTING -p tcp --dport 80 j REDIRECT --to-ports 3128

MAKEFILE

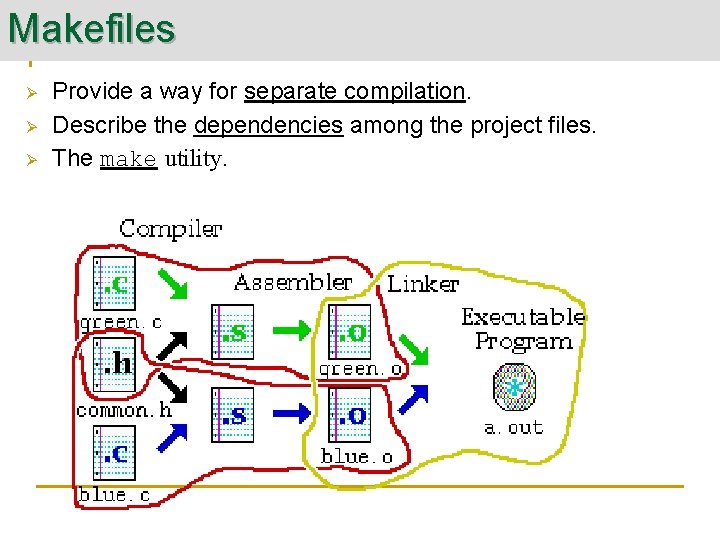
Makefiles Ø Ø Ø Provide a way for separate compilation. Describe the dependencies among the project files. The make utility.

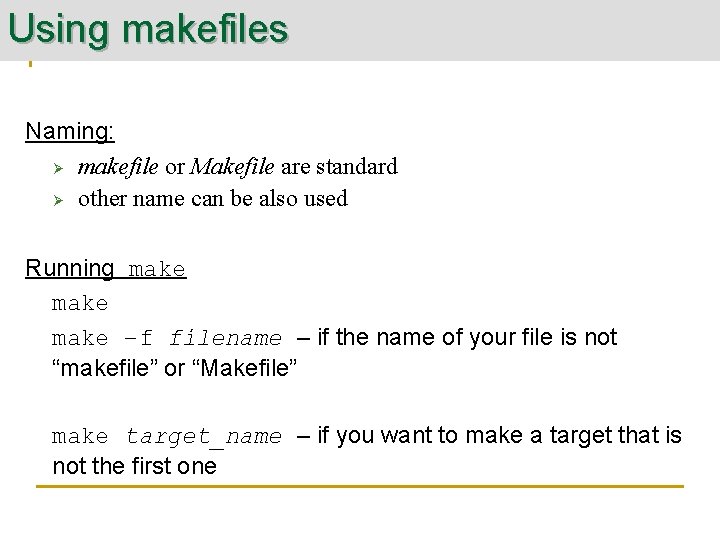
Using makefiles Naming: Ø makefile or Makefile are standard Ø other name can be also used Running make –f filename – if the name of your file is not “makefile” or “Makefile” make target_name – if you want to make a target that is not the first one

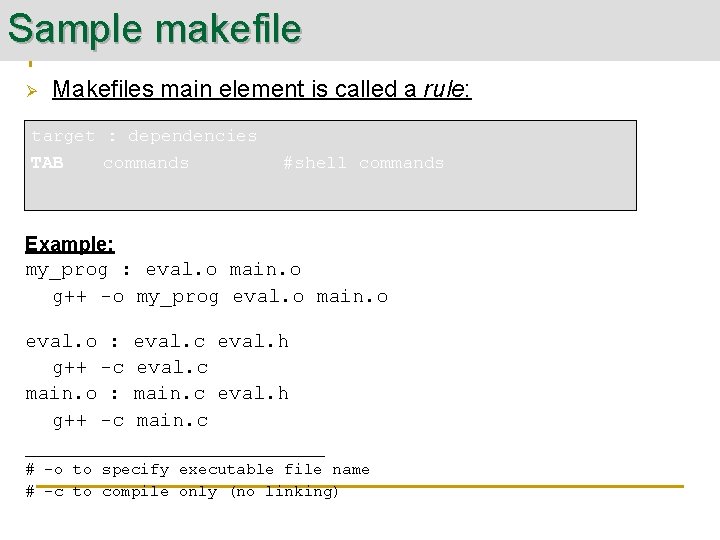
Sample makefile Ø Makefiles main element is called a rule: target : dependencies TAB commands #shell commands Example: my_prog : eval. o main. o g++ -o my_prog eval. o main. o eval. o : eval. c eval. h g++ -c eval. c main. o : main. c eval. h g++ -c main. c _____________ # -o to specify executable file name # -c to compile only (no linking)

Variables The old way (no variables) A new way (using C = g++ OBJS = eval. o main. o HDRS = eval. h my_prog : eval. o main. o g++ -o my_prog eval. o main. o eval. o : eval. c eval. h g++ -c –g eval. c main. o : main. c eval. h g++ -c –g main. c my_prog : eval. o main. o $(C) -o my_prog $(OBJS) eval. o : eval. c $(C) –c –g eval. c main. o : main. c $(C) –c –g main. c $(OBJS) : $(HDRS) Defining variables on the command line: Take precedence over variables defined in the makefile. make C=cc

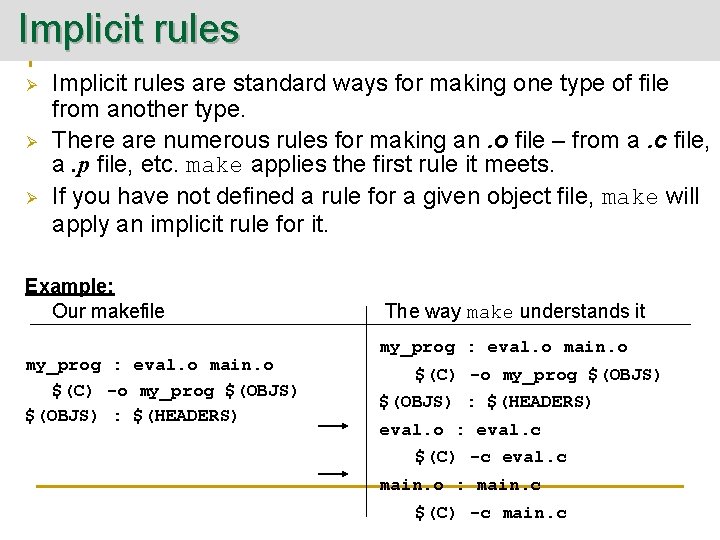
Implicit rules Ø Ø Ø Implicit rules are standard ways for making one type of file from another type. There are numerous rules for making an. o file – from a. c file, a. p file, etc. make applies the first rule it meets. If you have not defined a rule for a given object file, make will apply an implicit rule for it. Example: Our makefile my_prog : eval. o main. o $(C) -o my_prog $(OBJS) : $(HEADERS) The way make understands it my_prog : eval. o main. o $(C) -o my_prog $(OBJS) : $(HEADERS) eval. o : eval. c $(C) -c eval. c main. o : main. c $(C) -c main. c

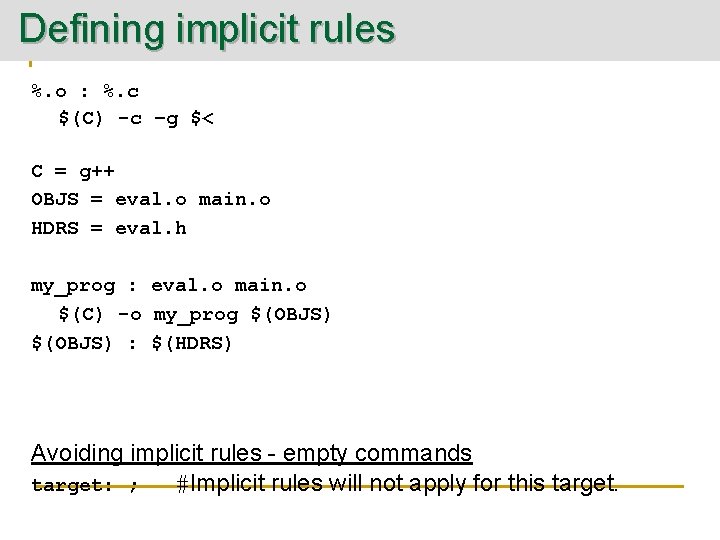
Defining implicit rules %. o : %. c $(C) -c –g $< C = g++ OBJS = eval. o main. o HDRS = eval. h my_prog : eval. o main. o $(C) -o my_prog $(OBJS) : $(HDRS) Avoiding implicit rules - empty commands target: ; #Implicit rules will not apply for this target.

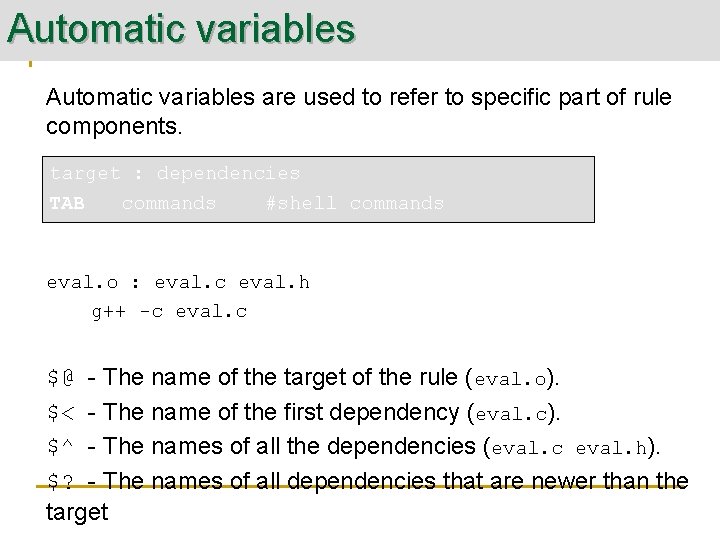
Automatic variables are used to refer to specific part of rule components. target : dependencies TAB commands #shell commands eval. o : eval. c eval. h g++ -c eval. c $@ - The name of the target of the rule (eval. o). $< - The name of the first dependency (eval. c). $^ - The names of all the dependencies (eval. c eval. h). $? - The names of all dependencies that are newer than the target

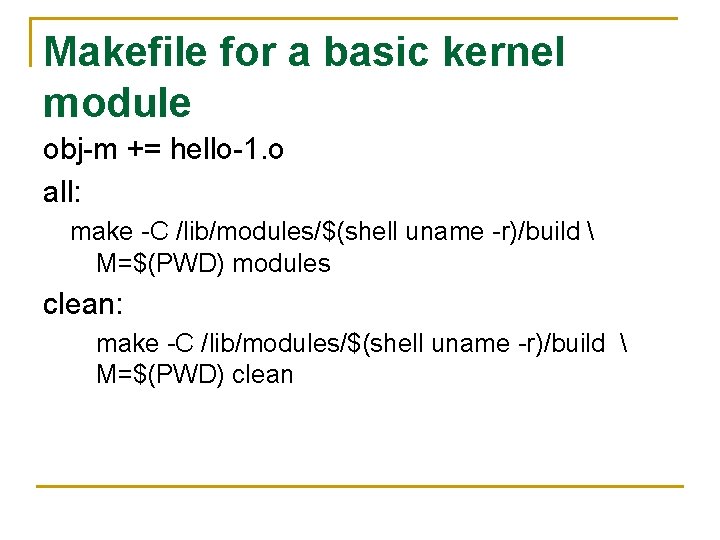
Makefile for a basic kernel module obj-m += hello-1. o all: make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules clean: make -C /lib/modules/$(shell uname -r)/build M=$(PWD) clean

Kernel Modules Giving your Linux more pop since 1995

History n n n Introduced in Linux version 1. 2 (1995) At the time, drivers were already designed to be somewhat modular, so not a lot of work was needed to revamp one driver for use as a LKM. There a lot of drivers, though. . . By 2000, most drivers and “module-able” things are converted.

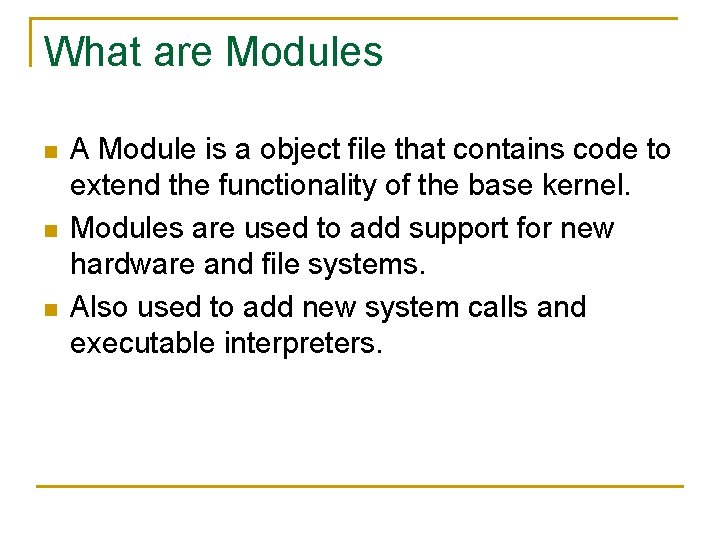
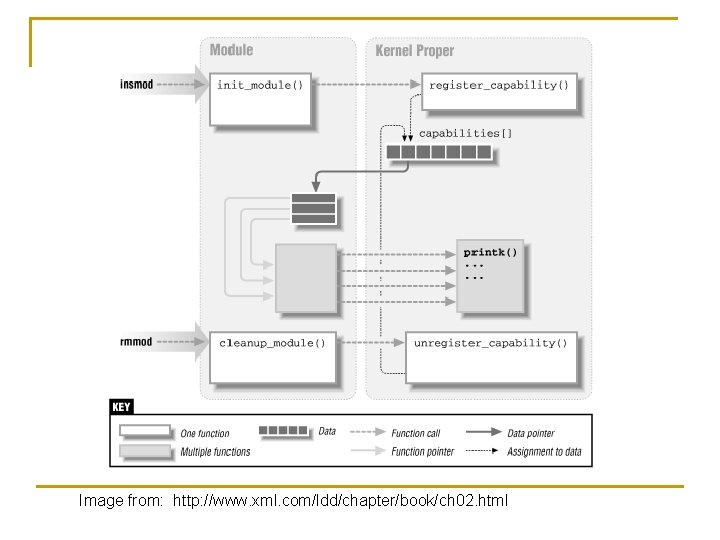
What are Modules n n n A Module is a object file that contains code to extend the functionality of the base kernel. Modules are used to add support for new hardware and file systems. Also used to add new system calls and executable interpreters.

Why are they Important? n If modules did not exist then adding new features to the kernel would be nearly impossible.

Pros and Cons n Pros: q q n Time savings Portability Memory savings Security (PAM) Cons q q No safeguards Security (rootkits)

Modules vs. Applications n n n Modules are really a part of the kernel and so run in kernel space. Apps just do their tasks and end. Modules sit in the kernel space waiting to be run. Apps can be linked to outside libraries; modules can only "see" in the kernel and other loaded modules.

Module Loading n n Kernel Symbol Table: references kernel functions that modules can use. When loaded, unresolved symbols in module are linked to system table EXPORT_SYMBOL() allows specified symbol to be used by kernel and other modules. Use cat /proc/kallsyms to get a list of all exported kernel symbols.

Image from: http: //www. xml. com/ldd/chapter/book/ch 02. html

Module HOW-TO n Some useful commands insmod insert module into kernel q rmmod remove kernel module q lsmod show currently loaded modules The above work, but are dumb. Instead, use modprobe [-r] which is aware of module dependencies and config settings. Use depmod to find module dependencies. File location: /lib/modules/version/modules. dep q n n

Writing a Kernel Module n Kernel modules have two basic functions: q q a "start" (initialization) function called init_module(), is called when the module is insmoded into the kernel an "end" (cleanup) function called cleanup_module(), is called just before it is rmmoded. Since kernel 2. 3. 13, you can use whatever name you like for the start and end functions of a module Module license

NETFILTER

Netfilter n n A framework for packet mangling in kernel Built in Linux 2. 4 kernel or higher version Independent of network protocol stack Provide an easy way to do firewall setting or packet filtering, network address translation and packet mangling 32

Netfilter II—how it works n Defines a set of hooks q q n Hooks are well defined point in the path of packets when these packets pass through network stack The protocol code will jump into netfilter framework when it hits the hook point. Registers Kernel functions to these hooks: q q q Called when a packet reaches at hook point Can decide the fate of the packets After the functions, the packet could continue its journey 33

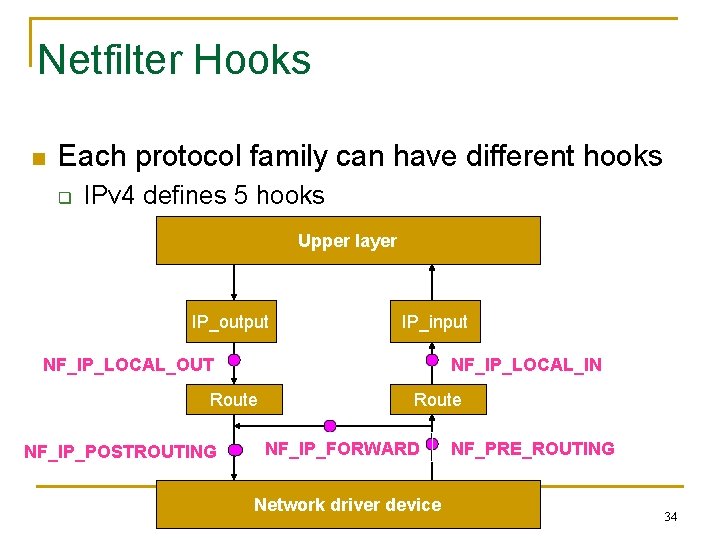
Netfilter Hooks n Each protocol family can have different hooks q IPv 4 defines 5 hooks Upper layer IP_output IP_input NF_IP_LOCAL_OUT NF_IP_LOCAL_IN Route NF_IP_POSTROUTING Route NF_IP_FORWARD Network driver device NF_PRE_ROUTING 34

Netfilter hook points n NF_IP_PRE_ROUTING: q n NF_IP_LOCAL_IN: q n Packets are not destined for this host but need to be forwarded to another interface NF_IP_LOCAL_OUT: q n After routing decisions, if the packet destines for this host NF_IP_FORWARD: q n After sanity checks, before routing decision All packets created from local host would come here before it is been sent out NF_IP_POST_ROUTING: q All packets have been routed and ready to hit the wire 35

Netfilter hook functions n Multiple functions could register to the same hook point q q q n Need to set priority The corresponding packet will path the hook points Each function registered for that hook point is called in the order of priority and is free to manipulate the packet What to do in hook functions q q The function could do anything it wants But need to tell netfilter to return one of the five values: n n n NF_ACCEPT NF_DROP NF_STOLEN NF_QUEUE NF_REPEAT 36


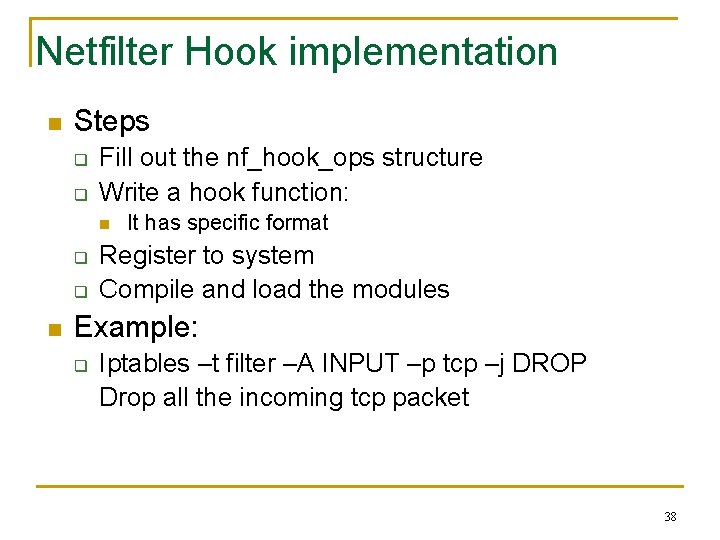
Netfilter Hook implementation n Steps q q Fill out the nf_hook_ops structure Write a hook function: n q q n It has specific format Register to system Compile and load the modules Example: q Iptables –t filter –A INPUT –p tcp –j DROP Drop all the incoming tcp packet 38

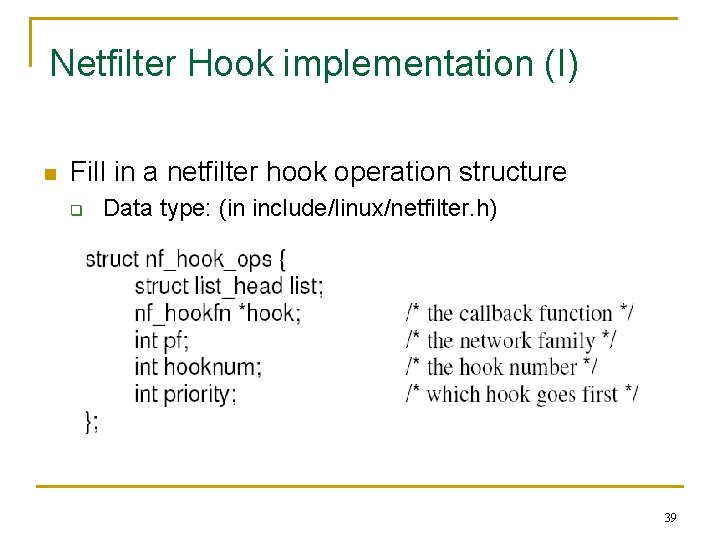
Netfilter Hook implementation (I) n Fill in a netfilter hook operation structure q Data type: (in include/linux/netfilter. h) 39

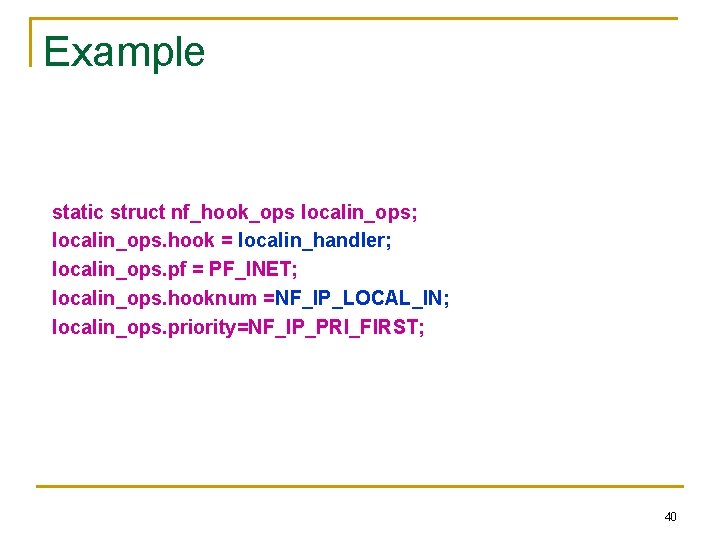
Example static struct nf_hook_ops localin_ops; localin_ops. hook = localin_handler; localin_ops. pf = PF_INET; localin_ops. hooknum =NF_IP_LOCAL_IN; localin_ops. priority=NF_IP_PRI_FIRST; 40

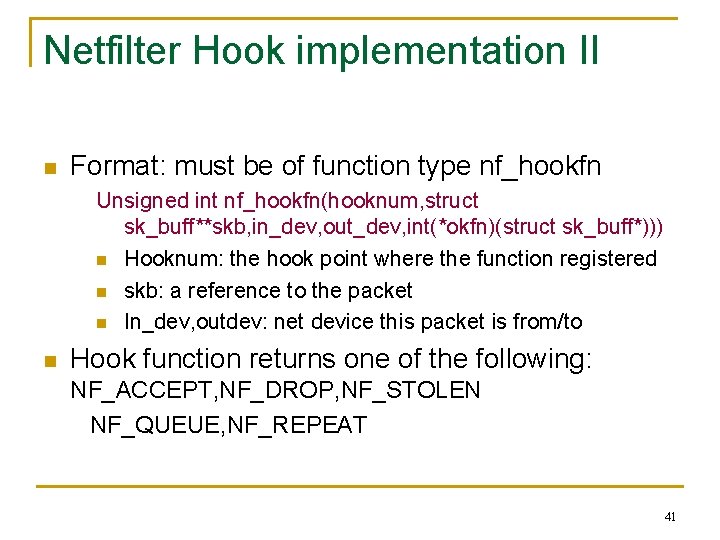
Netfilter Hook implementation II n Format: must be of function type nf_hookfn Unsigned int nf_hookfn(hooknum, struct sk_buff**skb, in_dev, out_dev, int(*okfn)(struct sk_buff*))) n Hooknum: the hook point where the function registered n skb: a reference to the packet n In_dev, outdev: net device this packet is from/to n Hook function returns one of the following: NF_ACCEPT, NF_DROP, NF_STOLEN NF_QUEUE, NF_REPEAT 41

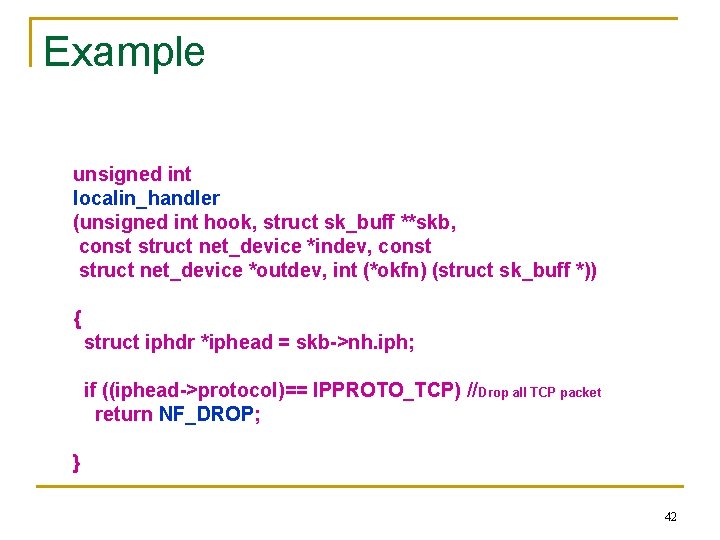
Example unsigned int localin_handler (unsigned int hook, struct sk_buff **skb, const struct net_device *indev, const struct net_device *outdev, int (*okfn) (struct sk_buff *)) { struct iphdr *iphead = skb->nh. iph; if ((iphead->protocol)== IPPROTO_TCP) //Drop all TCP packet return NF_DROP; } 42

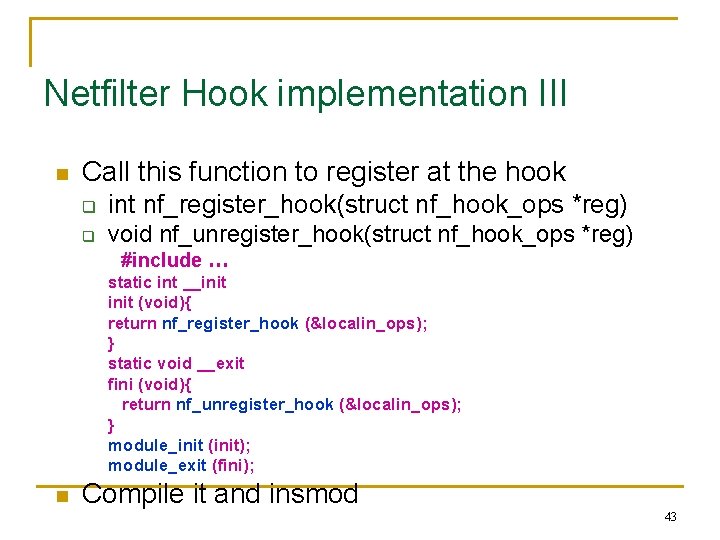
Netfilter Hook implementation III n Call this function to register at the hook q int nf_register_hook(struct nf_hook_ops *reg) q void nf_unregister_hook(struct nf_hook_ops *reg) #include … static int __init (void){ return nf_register_hook (&localin_ops); } static void __exit fini (void){ return nf_unregister_hook (&localin_ops); } module_init (init); module_exit (fini); n Compile it and insmod 43

Conclusion n Netfilter is a glue code between the protocol hooks and the kernel function modules Iptables is useful to set our firewall Provide a simple way to hack packet 44

References n n n n The Linux Kernel Module Programming Guide http: //www. faqs. org/docs/kernel/ Wikipedia: Linux Kernel http: //en. wikipedia. org/wiki/Linux_kernel Wikipedia: Linux Modules http: //en. wikipedia. org/wiki/Module_(Linux) Linux Device Drivers: Building and Running Modules http: //www. xml. com/ldd/chapter/book/ch 02. html Linux Loadable Kernel Module HOWTO http: //www. tldp. org/HOWTO/Module-HOWTO/ Linux PAM page http: //www. kernel. org/pub/linux/libs/pam/whatispam. html Linux Kernel Development. Ch. 16: Modules. pp. 279 -289 Linux Kernel Cross-Reference http: //lxr. linux. no/ https: //www. redhat. com/mirrors/LDP/lkmpg/2. 6/html/lkmpg. html